4.4.1. Cyber-Attack Scoring Result with Cyber Kill Chain
We analyzed in detail the cyber-attack techniques for each fileless cyber-attack.
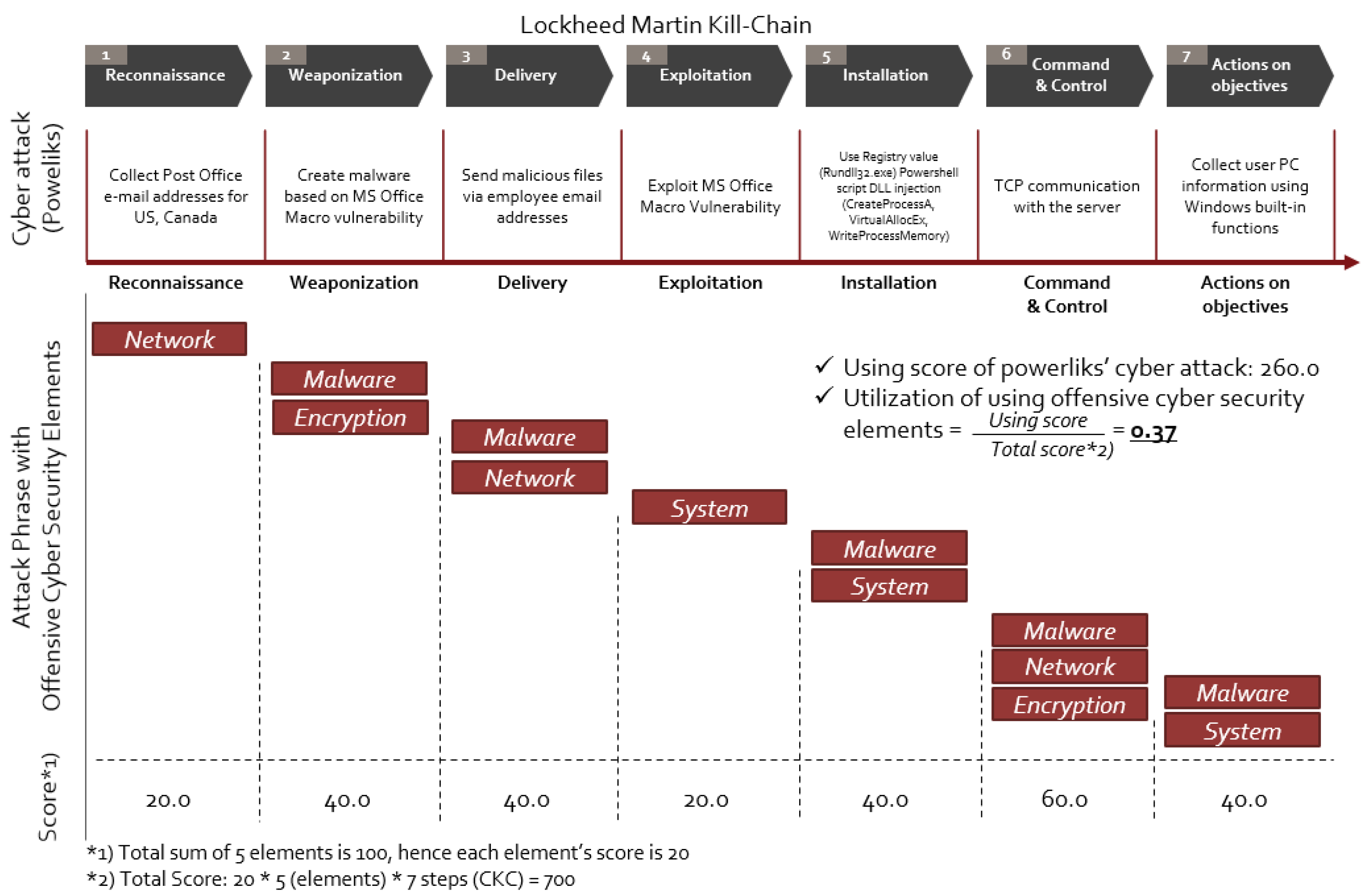
Figure 4 presents an example of the scoring result for a Poweliks fileless cyber-attack. For Powerliks, in the initial Reconnaissance phase of Cyber Kill Chain, the attackers obtained e-mail addresses of post office workers in the US and Canada. Then, in the Weaponization phase, the attacker created an MS Word document file and inserted malicious code using the Macro vulnerability inside. In the delivery stage, an email containing a malicious program was disguised as a normal email and delivered to the employee’s email address. In the Exploitation phase, malicious code was executed using the MS macro function vulnerability. It also inserted a malicious script into the registry and rendered the name of the registrar key unreadable. Additionally, the encoded registry value was executed using the JScript.Encode function. In the installation step, the Base64-encoded PowerShell script was executed. DLL injection was also performed using a PowerShell script, and the malicious DLL is packed with MPRESS. In addition, Poweliks registers malicious code in the automatic program startup registry to perform permanent attacks. In the Command and Control phase, TCP connections are transformed into the two IP addresses that are estimated to be servers. In the Action on objectives step, information about the user’s PC is collected and information is transmitted to the attacker’s server.
For the WannaCry case, it does not appear to have a separate Reconnaissance stage. In the Weaponization phase, the attacker creates a malicious program disguised as the icon of a normal program. In the delivery phase, the attacker uploads a malicious file disguised as a normal file online, and then the victim downloads it. In the Exploitation phase, the MSSecsvc 2.0 service is installed on the victim’s PC, and files hidden in the program’s resources are dropped and executed. In the installation phase, the dropped program is registered in the registry run key, and it is automatically executed whenever the PC is booted. In the Command and Control phase, communication occurs via the Tor network, and port 9050 is left open should communication with an external server be required. Actions on objectives encrypt all data except for data in a specific file path. The volume shadow file is deleted using Vssadmin on the infected PC. The peculiarity is that the SMB vulnerability also enables the shellcode to be transmitted to a computer on a shared network, and the vulnerability of the PC results in the same process being used to infect the ransomware.
We selected the Lazrus cyber-attack for the APT group from four countries.
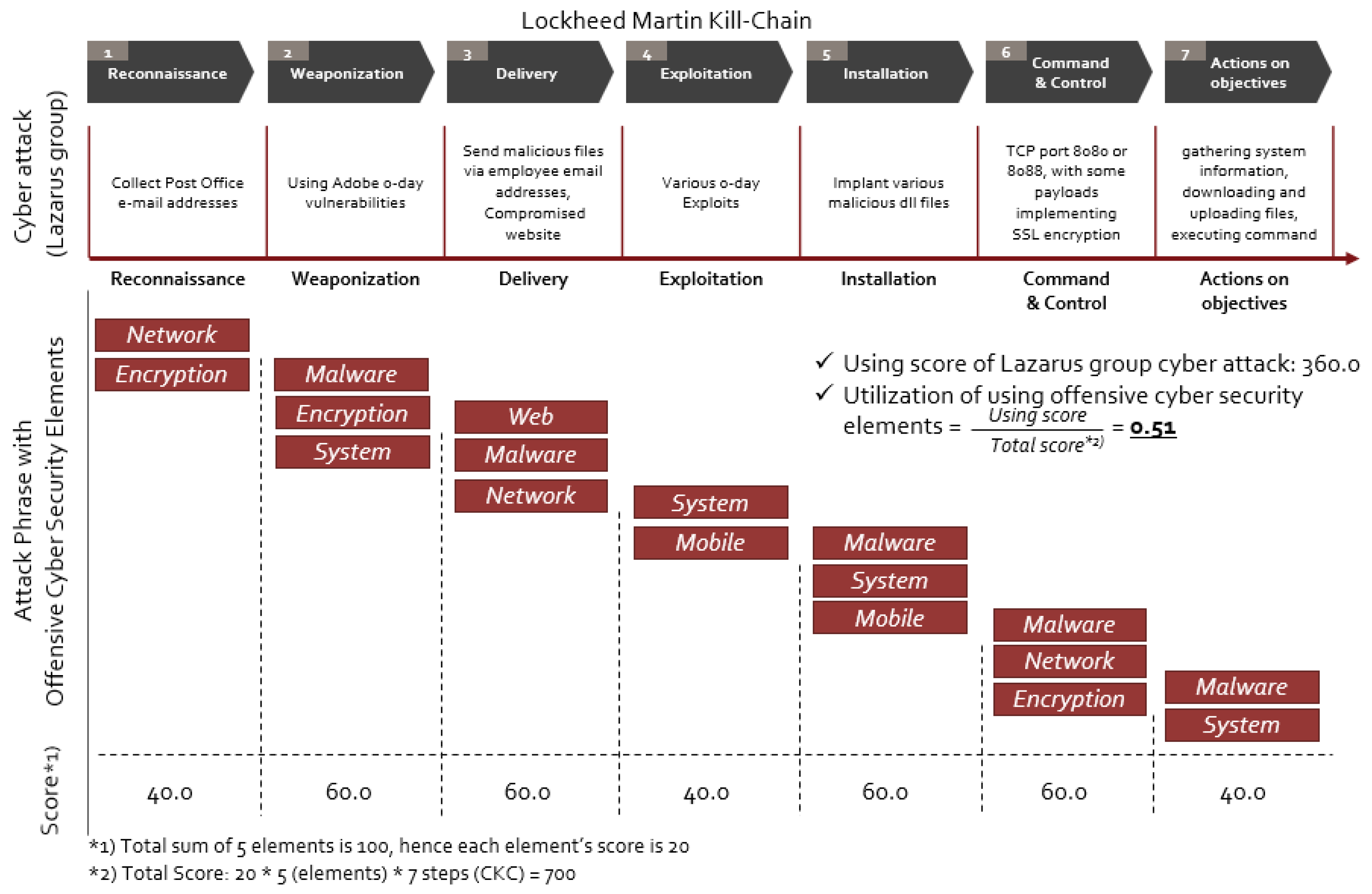
Figure 5 shows an example of the scoring result for the Lazarus APT cyber-attack. In the Lazarus case, the cyber-attack collected a post-office e-mail address and investigated specific targets with network proving techniques in the reconnaissance step. In the Weaponization step, Lazarus developed malware by exploiting the 0-day vulnerability of Adobe software. Many encryption techniques were adopted during the development of malware. Web, malware, and network techniques were used in the delivery step. In the Exploitation step, Lazarus used various 0-day exploits; thus, we evaluated the system and malware element in the exploitation step. Malware, system, and encryption techniques were used in the Installation step, which used TCP port 443 with some payloads for the implementation of SSL encryption. Actions on the Objectives step in the cyber kill chain were performed by gaining system information, downloading and uploading files, and using the execution command.
Through these methods, we calculated the scoring result of cyber-attacks with Cyber Kill Chain as listed in
Table 9. The result using Cyber Kill Chain shows Poweliks (0.3714), Rozena (0.3429), Duqu 2.0 (0.3429), Kovter (0.3429), Petya (0.4286), Sorebrect (0.2857), WannaCry (0.3714), Magniber (0.2857), Emotet (0.3429), and GandCrab (0.3429) for fileless cyber-attacks. For APT cyber-attacks, it shows APT1 (0.4000), Emissary Panda (0.4857), APT29 (0.4286), SectorJ04 (0.4571), Lazarus Group (0.5143), APT38 (0.4286), Chafer (0.4000), MuddyWater (0.4286). The average score for fileless and APT cyber-attacks is 0.3459, 0.4318, respectively. This shows that APT cyber-attacks use more Cyber Kill Chain techniques than fileless cyber-attacks.
4.4.2. Cyber-Attack Scoring Result with ATT&CK
Owing to the nature of cyber-attacks, increasingly complicated techniques are included in malicious code. Thus, when calculating the cyber-attack score, we conducted a more in-depth analysis of the malicious code. An analyze process was carried out on the 12 stages of the MITRE ATT&CK, and the results are shown in
Figure 6.
In this figure, each layer shows the stages of the cyber-attack in MITRE ATT&CK. The order of layers is the flow of an attack. The red line indicates the connection of a technique used by a malicious code with the previous techniques used. At each stage, the shade of blue plane indicates the cyber-attack techniques. In addition, the color of the circle indicates the number of cyber-attacks that use it. For instance, if the number of cyber-attack types is five or more, the circle’s color is dark brown; if it is three or four, it is orange, and if it is two or less, it shows an apricot color.
For example, the result of Duqu 2.0 mapping to ATT&CK is as follows. The initial access step used a spearphishing attachment. Signed binary and proxy execution were used in the Execution step. In the Persistence step, the scheduled task technique was used, and in the Privilege escalation step, exploitation for privilege escalation and access token manipulation techniques were used. In the Defense evasion step, disabling security tools were used, and in the Credential access step, credential dumping was used. In the Discovery step, process discovery, account discovery, network share discovery, and network service scanning were used. Data from local system technology was used in the Collection step, and a commonly used port was used in the Command and Control step. Data encrypted technology was used in the Exfiltration step.
Through these methods, we calculated the scoring result of cyber-attacks with the MITRE ATT&CK as listed in
Table 10. The following is a description of the results for Petya, which earned a score of 0.2581. In the initial access step, a spear phishing attachment and supply chain compromise technologies were used. Scripting, mshta, service execution, WMI, rundll32, and schedule tasks were used in the Execution step. In Persistence and Privilege escalation, no special technique was used. In the Defense evasion step, mshta, indicator removal on host technology was used. Credential dumping technology was used in the Credential access step, and file and directory discovery technology was used in the Discovery step. In the Lateral movement step, Petya used Windows admin shares and exploited remote services technology. In the Impact step, disk structure wipe and data encrypted for impact technologies were used.
In contrast, Magniber, with a score of 0.1774, operates as follows. In the initial access step, drive-by compromise technology was used. In the Execution step, scripting, exploitation for client execution, scheduled task, and WMI were used. No technique seems to have been used in the Persistence step. Process injection technology was used in the Privilege escalation step, and obfuscated files or information technology was used in the Defense evasion phase. In the Discovery phase, files and directory discovery technology was used. No technique was used in the Lateral movement and Collection stages. In the Command and Control phase, remote file copy technology was used. In the Impact phase, data encrypted for impact and inhibit system recovery technologies were used.
The technique that was used for Emissary Panda (0.6774), which holds the highest score after Lazarus, is as follows. In the Initial access stage, the drive-by compromise technique was used. In the Execution phase, PowerShell, the windows command shell, Exploitation for client execution, and WMI were used. In the Persistence phase, registry run keys, create or modify system process, and web shell technologies were used. In the Privilege escalation stage, bypass user access control, exploitation for privilege escalation, hijack execution flow, dll side-loading, and process hollowing techniques were used. In the Defense evasion phase, Windows event logging is disabled, file deletion, network share connection removal and obfuscated files or information were used. In the Credential access phase, OS credential dumping technique for LSA secrets, LSASS memory, and security account manager was used. In the Discovery phase, local account, network service scanning, and query registry methods were used. In the Lateral movement phase, the exploitation of remote services technique is used. In the Collection phase, automated collection is performed. In the Command and Control phase, web protocols, ingress tool transfer are used. In the Exfiltration step, archive via library is used.
Next, we analyzed APT38, which obtained a fairly low score; however, many techniques are used in the Impact step. APT38 used a drive-by compromise technique in the initial access step. In the Execution step, the Windows command shell was used. In the Defense evasion step, indicator removal on host, modify registry, and software-packing techniques were used. In the Credential access step, input capture technique was used. In the Collection step, clipboard data were executed. In the Command and Control step, web protocols and ingress tool transfer were used. In particular, in the Impact step, many techniques were used: data destruction, data encrypted for impact, data manipulation, disk structure wipe, and system shutdown techniques.