From 5G to 6G Technology: Meets Energy, Internet-of-Things and Machine Learning: A Survey
Abstract
:1. Introduction
- We discuss in detail the projected 6G system architecture. Also, the existing research literature reveals that providing full-dimensional advantages of the 6G technology; will 5G application types will be reconsidered by modifying the traditional URLLC, eMBB, and mMTC and providing new services.
- We discuss the primary aims, vision, and trends for 6G network dimensions that include our vision of 6G and IoT and machine learning applications for autonomous networks and revolutionary energy efficiency, which are discussed in detail throughout this paper.
- We highlight all the essential network elements of 6G system architecture and discuss defined issues that current generations of mobile networks are facing; the mobile industry should transition away from traditional strategies and toward some new ones, such as operation in shared spectrum bands, inter-operator spectrum sharing, indoor small cell networks, a large number of local network operators, and on-demand network slice leasing.
- To meet the requirements of the stage where the research results on ML are to be addressed, as well as the methodology used by 5G and 6G for the Internet of Things and energy transmissions. We overview six major categories, including network resource management, security, augmented reality, network scaling, resource allocation, and the smart grid.
- Towards the end, we discuss multiple challenges and research directions applications, issues, research questions, motivation, recommendation criteria, and open challenges of ML usage in incorporating energy and IoT in 5G and 6G.
2. Methodology
3. 6G State-of-the-Art
3.1. 6G Requirements and Trends
3.1.1. Self-X Network
3.1.2. Superior Energy Efficiency
3.1.3. Satellite Integration
3.1.4. e-Health
3.1.5. Smart Cityh
3.1.6. Smart Home
3.2. Evolution of 6G
3.2.1. Mobile Broadband Reliable Low-Latency
3.2.2. mURLLC
3.2.3. HCSs
4. Review and Survey Articles
5. Overview of Existing Technique
6. Internet of Things (IoT)
6.1. Resource Allocation
6.2. Security
6.3. Smart Cities
6.4. Virtual Reality
6.5. Other Machine Learning
7. Merging Energy and IoT in 5G, 6G
8. Discussion
8.1. Challenges
8.1.1. A New Internet Architecture
8.1.2. Widespread Adoption of Machine Learning at the Network Edge
8.1.3. 3D Coverage
8.1.4. A New Physical Layer That includes Subterahertz Bands as Well as VLC
8.1.5. Distributed Security Mechanisms
8.1.6. Quality of Service
8.1.7. Security
8.1.8. Intelligence
8.1.9. Qualified Service Provision End-to-End
8.1.10. Big Heterogeneous Data
8.2. Recommendations
8.2.1. Holographic Communications
8.2.2. Manufacturing with High Precision
8.2.3. Sustainable Development and Smart Environments
8.2.4. An Increase in Energy Efficiency
8.2.5. Quantum Communications and Computing
8.2.6. Molecular Communications and the Internet of Nano-Things (Molecular Communications and the Internet of Nano-Things)
8.3. Motivations
8.3.1. Big Data and 6G
8.3.2. The Internet of Things (IoT)
8.3.3. Energy Efficiency
8.3.4. Network Traffic Management
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 3GPP | Third Generation Partnership Project |
| mMTC | Massive Machine Type Communications |
| AI | Artificial Intelligence |
| mURLLC | Massive Ultrareliable Low Latency Communication |
| AR | Augmented reality |
| ML | Machine learning |
| B5G | Beyond 5G |
| m2m | machine to machine |
| BL | Bayesian learning |
| MR | Mixed reality |
| CU | Cellular mode |
| NB | Naïve Bayes |
| EDoS | Economic Denial of Sustainability |
| NR | New Radio |
| E2E | end to end |
| NFV | Network function virtualization |
| eMBB | Enhanced Mobile Broadband |
| NMA | Network management automation |
| EHD | Extremely high definition |
| NN | Neural networks |
| eTOM | Enhanced Telecom Operations Map |
| XR | Extended reality |
| FiWi | Fiber Wireless |
| xMBB | Extreme mobile broadband |
| FL | Fuzzy logic |
| RF | Random forests |
| GPT | General purpose technology |
| RA | Resource allocation |
| HCSs | Human Centric Services |
| RL | Reinforcement learning |
| DR | Deep learning |
| RNN | Recurrent Neural Networks |
| DT | Decision trees |
| SG | Smart grid |
| D2D | Device-to-device |
| SINR | Signal to interference plus noise ratio Service |
| DRL | Deep reinforcement learning |
| SLAs | Level Agreements |
| ITSs | Intelligent transportation systems |
| SHD | Super high definition |
| IoE | Internet of Everything |
| SGs | Smart grids |
| IoT | Internet of Things |
| SRS | Shopping recommender system |
| ITS | Intelligent transportation system |
| SON | Self organizing networks |
| IMD | Intelligent medical diagnosis |
| SVM | Support Vector Machine |
| LTE | Long Term Evolution |
| THz | Terahertz |
| QC | Quantum computing |
| TL | Transfer learning |
| QML | Quantum ML |
| UAVs | Unmanned aerial vehicles |
| QoE | Quality of experience |
| URLLC | Ultra reliable low latency communication |
| QoS | Quality of service |
| VNF | Virtual network function |
| KPIs | Key performance Indicators |
| VR | Virtual reality |
| MIMO | Multiple Input Multiple Output |
| HSR | Hyper high speed railway |
| mIoT | massive Internet of Things |
References
- Pouttu, A.; Burkhardt, F.; Patachia, C.; Mendes, L.; Brazil, G.R.; Pirttikangas, S.; Jou, E.; Kuvaja, P.; Heikkilä, M.; Päivärinta, T.; et al. 6G White Paper on Validation and Trials for Verticals towards 2030’s; 6G Research Visions. 2020. Available online: https://www.6gchannel.com/items/6g-white-paper-validation-trials/ (accessed on 15 July 2021).
- Series, M. IMT Vision–Framework and overall objectives of the future development of IMT for 2020 and beyond. Recomm. ITU Geneva 2015, 2083, 1–21. [Google Scholar]
- Castelli, M.; Vanneschi, L.; Popovič, A. Predicting burned areas of forest fires: An artificial intelligence approach. Fire Ecol. 2015, 11, 106–118. [Google Scholar] [CrossRef]
- Qi, Q.; Chen, X.; Zhong, C.; Zhang, Z. Integration of energy, computation and communication in 6G cellular internet of things. IEEE Commun. Lett. 2020, 24, 1333–1337. [Google Scholar] [CrossRef]
- Amgoune, H.; Mazri, T. 5G: Interconnection of Services and Security Approaches. In Proceedings of the 3rd International Conference on Smart City Applications, New York, NY, USA, 2–4 October 2018; pp. 1–7. [Google Scholar]
- Vidal, J.M.; Monge, M.A.S.; Villalba, L.J.G. Detecting Workload-based and Instantiation-based Economic Denial of Sustainability on 5G environments. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–8. [Google Scholar]
- Vreman, N.; Maggio, M. Multilayer distributed control over 5G networks: Challenges and security threats. In Proceedings of the Workshop on Fog Computing and the IoT, New York, NY, USA, 15 April 2019; pp. 31–35. [Google Scholar]
- Zhang, S.; Zhu, D. Towards artificial intelligence enabled 6G: State of the art, challenges, and opportunities. Comput. Netw. 2020, 183, 107556. [Google Scholar] [CrossRef]
- Sun, Y.; Liu, J.; Wang, J.; Cao, Y.; Kato, N. When machine learning meets privacy in 6g: A survey. IEEE Commun. Surv. Tutor. 2020, 22, 2694–2724. [Google Scholar] [CrossRef]
- Sheth, K.; Patel, K.; Shah, H.; Tanwar, S.; Gupta, R.; Kumar, N. A taxonomy of AI techniques for 6G communication networks. Comput. Commun. 2020, 161, 279–303. [Google Scholar] [CrossRef]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Sekaran, R.; Patan, R.; Raveendran, A.; Al-Turjman, F.; Ramachandran, M.; Mostarda, L. Survival Study on Blockchain Based 6G-Enabled Mobile Edge Computation for IoT Automation. IEEE Access 2020, 8, 143453–143463. [Google Scholar] [CrossRef]
- Akhtar, M.W.; Hassan, S.A.; Ghaffar, R.; Jung, H.; Garg, S.; Hossain, M.S. The shift to 6G communications: Vision and requirements. Hum.-Centric Comput. Inf. Sci. 2020, 10, 1–27. [Google Scholar] [CrossRef]
- Hewa, T.; Gür, G.; Kalla, A.; Ylianttila, M.; Bracken, A.; Liyanage, M. The role of blockchain in 6G: Challenges, opportunities and research directions. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Alam, I.; Sharif, K.; Li, F.; Latif, Z.; Karim, M.; Biswas, S.; Nour, B.; Wang, Y. A survey of network virtualization techniques for internet of things using sdn and nfv. ACM Comput. Surv. (CSUR) 2020, 53, 1–40. [Google Scholar] [CrossRef]
- Davids, C.; Gurbani, V.K.; Ormazabal, G.; Rollins, A.; Singh, K.; State, R. Research topics related to real-time communications over 5G networks. ACM SIGCOMM Comput. Commun. Rev. 2018, 46, 1–6. [Google Scholar] [CrossRef]
- Jun, S.-H.; Kim, J.-H. 5G will popularize virtual and augmented reality: KT’s trials for world’s first 5G olympics in Pyeongchang. In Proceedings of the International Conference on Electronic Commerce, Turku, Finland, 14–16 June 2017; pp. 1–8. [Google Scholar]
- Cherrared, S.; Imadali, S.; Fabre, E.; Gössler, G.; Yahia, I.G.B. A survey of fault management in network virtualization environments: Challenges and solutions. IEEE Trans. Netw. Serv. Manag. 2019, 16, 1537–1551. [Google Scholar] [CrossRef]
- Fourati, H.; Maaloul, R.; Chaari, L. Self-organizing cellular network approaches applied to 5G networks. In Proceedings of the 2019 Global Information Infrastructure and Networking Symposium (GIIS), Tunis, Tunisia, 18–20 December 2019; pp. 1–4. [Google Scholar]
- Klaine, P.V.; Imran, M.A.; Onireti, O.; Souza, R.D. A survey of machine learning techniques applied to self-organizing cellular networks. IEEE Commun. Surv. Tutor. 2017, 19, 2392–2431. [Google Scholar] [CrossRef] [Green Version]
- Gebremariam, A.A.; Usman, M.; Qaraqe, M. Applications of Artificial Intelligence and Machine Learning in the Area of SDN and NFV: A Survey. In Proceedings of the 2019 16th International Multi-Conference on Systems, Signals & Devices (SSD), Istanbul, Turkey, 21–24 March 2019; pp. 545–549. [Google Scholar]
- Buda, T.S.; Assem, H.; Xu, L.; Raz, D.; Margolin, U.; Rosensweig, E.; Lopez, D.; Corici, J.; Smirnov, M.; Mullins, R.; et al. Can machine learning aid in delivering new use cases and scenarios in 5G? In Proceedings of the NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 1279–1284. [Google Scholar]
- Mwanje, S.; Decarreau, G.; Mannweiler, C.; Naseer-ul-Islam, M.; Schmelz, L.C. Network management automation in 5G: Challenges and opportunities. In Proceedings of the 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–8 September 2016; pp. 1–6. [Google Scholar]
- Tham, M.-L.; Iqbal, A.; Chang, Y.C. Deep Reinforcement Learning for Resource Allocation in 5G Communications. In Proceedings of the 2019 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA ASC), Lanzhou, China, 18–21 November 2019; pp. 1852–1855. [Google Scholar]
- Lee, Y.L.; Qin, D. A survey on applications of deep reinforcement learning in resource management for 5G heterogeneous networks. In Proceedings of the 2019 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA ASC), Lanzhou, China, 18–21 November 2019; pp. 1856–1862. [Google Scholar]
- Sultan, K.; Ali, H. Where big data meets 5G? In Proceedings of the Second International Conference on Internet of things, Data and Cloud Computing, Cambridge, UK, 22–23 March 2017; pp. 1–4. [Google Scholar]
- Aldossari, S.M.; Chen, K.-C. Machine learning for wireless communication channel modeling: An overview. Wirel. Pers. Commun. 2019, 106, 41–70. [Google Scholar] [CrossRef]
- Tudzarov, A.; Gelev, S. 5G and software network paradigm. In Proceedings of the 2018 23rd International Scientific-Professional Conference on Information Technology (IT), Žabljak, Montenegro, 19–24 February 2018; pp. 1–5. [Google Scholar]
- Moysen, J.; Giupponi, L. From 4G to 5G: Self-organized network management meets machine learning. Comput. Commun. 2018, 129, 248–268. [Google Scholar] [CrossRef] [Green Version]
- Cayamcela, M.E.M.; Lim, W. Artificial intelligence in 5G technology: A survey. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 17–19 October 2018; pp. 860–865. [Google Scholar]
- Dormidontova, E.; Komarov, M. Quality of Services Provided for Users in Fifth Generation Wireless Networks. In Proceedings of the 8th International Conference on Information Communication and Management, Shenyang, China, 21–23 September 2018; pp. 32–38. [Google Scholar]
- Mulvey, D.; Foh, C.H.; Imran, M.A.; Tafazolli, R. Cell fault management using machine learning techniques. IEEE Access 2019, 7, 124514–124539. [Google Scholar] [CrossRef]
- Marquez, C.; Gramaglia, M.; Fiore, M.; Banchs, A.; Costa-Perez, X. How should I slice my network? A multi-service empirical evaluation of resource sharing efficiency. In Proceedings of the 24th Annual International Conference on Mobile Computing and Networking, Shenyang, China, 21–23 September 2018; pp. 191–206. [Google Scholar]
- Amgoune, H.; Mazri, T. Comparison between different 5G architectures for a better integration of these services and proposal of an improved architecture. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–7. [Google Scholar]
- Albreem, M.A.; Juntti, M.; Shahabuddin, S. Massive MIMO detection techniques: A survey. IEEE Commun. Surv. Tutor. 2019, 21, 3109–3132. [Google Scholar] [CrossRef] [Green Version]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Paoletti, E.; Zoppi, P.; Geli, S.; Dioniso, P. How 6G technology can change the future wireless healthcare. In Proceedings of the 2020 2nd 6G wireless summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–6. [Google Scholar]
- Nizzi, F.; Pecorella, T.; Bastianini, M.; Cerboni, C.; Buzzigoli, A.; Fratini, A. The role of network simulator in the 5G experimentation. In Proceedings of the 2019 Workshop on Next-Generation Wireless with ns-3, Florence, Italy, 21 June 2019; pp. 13–17. [Google Scholar]
- Dahlman, E.; Parkvall, S.; Peisa, J.; Tullberg, H. 5G evolution and beyond. In Proceedings of the 2019 IEEE 20th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Cannes, France, 2–5 July 2019; pp. 1–5. [Google Scholar]
- Arjoune, Y.; Faruque, S. Artificial Intelligence for 5G Wireless Systems: Opportunities, Challenges, and Future Research Direction. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 1023–1028. [Google Scholar]
- Jansevskis, M.; Osis, K. Machine Learning and on 5G Based Technologies Create New Opportunities to Gain Knowledge. In Proceedings of the 2018 2nd European Conference on Electrical Engineering and Computer Science (EECS), Bern, Switzerland, 20–22 December 2018; pp. 376–381. [Google Scholar]
- Morocho-Cayamcela, M.E.; Lee, H.; Lim, W. Machine learning for 5G/B5G mobile and wireless communications: Potential, limitations, and future directions. IEEE Access 2019, 7, 137184–137206. [Google Scholar] [CrossRef]
- Zhang, C.; Patras, P.; Haddadi, H. Deep learning in mobile and wireless networking: A survey. IEEE Commun. Surv. Tutor. 2019, 21, 2224–2287. [Google Scholar] [CrossRef] [Green Version]
- Ahmed, R.; Matin, M.A. Towards 6G wireless networks-challenges and potential technologies. J. Electr. Eng. 2020, 71, 290–297. [Google Scholar]
- Dogra, A.; Jha, R.K.; Jain, S. A survey on beyond 5G network with the advent of 6G: Architecture and emerging technologies. IEEE Access 2020, 9, 67512–67547. [Google Scholar] [CrossRef]
- Alsharif, M.H.; Kelechi, A.H.; Albreem, M.A.; Chaudhry, S.A.; Zia, M.S.; Kim, S. Sixth generation (6G) wireless networks: Vision, research activities, challenges and potential solutions. Symmetry 2020, 12, 676. [Google Scholar] [CrossRef]
- Hajiyat, Z.R.; Ismail, A.; Sali, A.; Hamidon, M.N. Antenna in 6G wireless communication system: Specifications, challenges, and research directions. Optik 2021, 231, 166415. [Google Scholar] [CrossRef]
- Aggarwal, S.; Kumar, N.; Tanwar, S. Blockchain Envisioned UAV Communication Using 6G Networks: Open issues, Use Cases, and Future Directions. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Salh, A.; Audah, L.; Shah, N.S.M.; Alhammadi, A.; Abdullah, Q.; Kim, Y.H.; Al-Gailani, S.A.; Hamzah, S.A.; Esmail, B.A.F.; Almohammedi, A.A. A Survey on Deep Learning for Ultra-Reliable and Low-Latency Communications Challenges on 6G Wireless Systems. IEEE Access 2021, 9, 55098–55131. [Google Scholar] [CrossRef]
- Piran, M.J.; Suh, D.Y. Learning-driven wireless communications, towards 6G. In Proceedings of the 2019 International Conference on Computing, Electronics & Communications Engineering (iCCECE), London, UK, 22–23 August 2019; pp. 219–224. [Google Scholar]
- Wikström, G.; Peisa, J.; Rugeland, P.; Johansson, N.; Parkvall, S.; Girnyk, M.; Mildh, G.; Da Silva, I. Challenges and technologies for 6G. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Mourad, A.; Yang, R.; Lehne, P.H.; de la Oliva, A. Towards 6G: Evolution of key performance indicators and technology trends. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Ajmal, S.; Muzammil, M.B.; Jamil, A.; Abbas, S.M.; Iqbal, U.; Touseef, P. Survey on cache schemes in heterogeneous networks using 5g internet of things. In Proceedings of the 3rd International Conference on Future Networks and Distributed Systems, Paris, France, 1–2 July 2019; pp. 1–8. [Google Scholar]
- Lu, Z.; Huang, Y.-C.; Bangjun, C. A Study for Application in Vehicle Networking and Driverless Driving. In Proceedings of the 2019 3rd International Conference on Computer Science and Artificial Intelligence, Normal, IL, USA, 6–8 December 2019; pp. 264–267. [Google Scholar]
- Tal, I.; Muntean, G.-M. Towards reasoning vehicles: A survey of fuzzy logic-based solutions in vehicular networks. ACM Comput. Surv. (CSUR) 2017, 50, 1–37. [Google Scholar] [CrossRef]
- Rahmani, R.; Kanter, T. Autonomous cooperative decision-making in massively distributed IoT via heterogenous networks. In Proceedings of the 1st International Conference on Internet of Things and Machine Learning, Liverpool, UK, 17–18 October 2017; pp. 1–5. [Google Scholar]
- Muhamedyev, R.I.; Kalimoldaev, M.N.; Uskenbayeva, R.K. Semantic network of ICT domains and applications. In Proceedings of the 2014 Conference on Electronic Governance and Open Society: Challenges in Eurasia, St. Petersburg, Russian, 18–20 November 2014; pp. 178–186. [Google Scholar]
- Nakamura, Y.; Shimonishi, H.; Kobayashi, Y.; Satoda, K.; Matsunaga, Y.; Kanetomo, D. Novel heterogeneous computing platforms and 5G communications for IoT applications. In Proceedings of the 2017 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Irvine, CA, USA, 13–16 November 2017; pp. 874–879. [Google Scholar]
- Suryanegara, M.; Arifin, A.S.; Asvial, M. The IoT-based transition strategy towards 5G. In Proceedings of the International Conference on Big Data and Internet of Thing, London, UK, 20–22 December 2017; pp. 186–190. [Google Scholar]
- Ding, J.; Nemati, M.; Ranaweera, C.; Choi, J. IoT connectivity technologies and applications: A survey. arXiv 2020, arXiv:2002.12646. [Google Scholar]
- Bithas, P.S.; Michailidis, E.T.; Nomikos, N.; Vouyioukas, D.; Kanatas, A.G. A survey on machine-learning techniques for UAV-based communications. Sensors 2019, 19, 5170. [Google Scholar] [CrossRef] [Green Version]
- Usman, M.; Asghar, M.R.; Granelli, F.; Qaraqe, K. Integrating smart city applications in 5G networks. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, Amman, Jordan, 26–27 June 2018; pp. 1–5. [Google Scholar]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of artificial intelligence and machine learning in smart cities. Comput. Commun. 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Rao, S.K.; Prasad, R. Impact of 5G technologies on industry 4.0. Wirel. Pers. Commun. 2018, 100, 145–159. [Google Scholar] [CrossRef]
- Velev, D.; Zlateva, P.; Zong, X. Challenges of 5G usability in disaster management. In Proceedings of the 2018 International Conference on Computing and Artificial Intelligence, Chengdu, China, 12–14 March 2018; pp. 71–75. [Google Scholar]
- Muhamedyev, R.I.; Amirgaliyev, Y.N.; Kalimoldayev, M.N.; Khamitov, A.N.; Abdilmanova, A. Selection of the most prominent lines of research in ICT domain. In Proceedings of the 2015 Twelve International Conference on Electronics Computer and Computation (ICECCO), Almaty, Kazakhstan, 27–30 September 2015; pp. 1–7. [Google Scholar]
- Kim, J.H. 6G and Internet of Things: A survey. J. Manag. Anal. 2021, 8, 316–332. [Google Scholar]
- Shafique, K.; Khawaja, B.A.; Sabir, F.; Qazi, S.; Mustaqim, M. Internet of things (IoT) for next-generation smart systems: A review of current challenges, future trends and prospects for emerging 5G-IoT scenarios. IEEE Access 2020, 8, 23022–23040. [Google Scholar] [CrossRef]
- Sharma, S.K.; Wang, X. Towards massive machine type communications in ultra-dense cellular IoT networks: Current issues and machine learning-assisted solutions. IEEE Commun. Surv. Tutor. 2019. [Google Scholar] [CrossRef] [Green Version]
- Malik, U.M.; Javed, M.A.; Zeadally, S.; ul Islam, S. Energy efficient fog computing for 6G enabled massive IoT: Recent trends and future opportunities. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Nawaz, S.J.; Sharma, S.K.; Wyne, S.; Patwary, M.N.; Asaduzzaman, M. Quantum machine learning for 6G communication networks: State-of-the-art and vision for the future. IEEE Access 2019, 7, 46317–46350. [Google Scholar] [CrossRef]
- Usama, M.; Erol-Kantarci, M. A survey on recent trends and open issues in energy efficiency of 5G. Sensors 2019, 19, 3126. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Huo, Y.; Dong, X.; Xu, W.; Yuen, M. Enabling multi-functional 5G and beyond user equipment: A survey and tutorial. IEEE Access 2019, 7, 116975–117008. [Google Scholar] [CrossRef]
- Temesgene, D.A.; Núñez-Martínez, J.; Dini, P. Softwarization and optimization for sustainable future mobile networks: A survey. IEEE Access 2017, 5, 25421–25436. [Google Scholar] [CrossRef] [Green Version]
- Sultan, K.; Ali, H.; Zhang, Z. Big data perspective and challenges in next generation networks. Future Internet 2018, 10, 56. [Google Scholar] [CrossRef] [Green Version]
- Imoize, A.L.; Adedeji, O.; Tandiya, N.; Shetty, S. 6G Enabled Smart Infrastructure for Sustainable Society: Opportunities, Challenges, and Research Roadmap. Sensors 2021, 21, 1709. [Google Scholar] [CrossRef] [PubMed]
- Mahmood, N.H.; Alves, H.; López, O.A.; Shehab, M.; Osorio, D.P.M.; Latva-Aho, M. Six key features of machine type communication in 6G. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Xu, C.; Ishikawa, N.; Rajashekar, R.; Sugiura, S.; Maunder, R.G.; Wang, Z.; Yang, L.; Hanzo, L. Sixty years of coherent versus non-coherent tradeoffs and the road from 5G to wireless futures. IEEE Access 2019, 7, 178246–178299. [Google Scholar] [CrossRef]
- Wang, M.; Lin, Y.; Tian, Q.; Si, G. Transfer Learning Promotes 6G Wireless Communications: Recent Advances and Future Challenges. IEEE Trans. Reliab. 2021. [Google Scholar] [CrossRef]
- Zayas, A.D.; Rico, D.; García, B.; Merino, P. A coordination framework for experimentation in 5g testbeds: Urllc as use case. In Proceedings of the 17th ACM International Symposium on Mobility Management and Wireless Access, Miami Beach, FL, USA, 25–29 November 2019; pp. 71–79. [Google Scholar]
- Nikaein, N.; Marina, M.K.; Manickam, S.; Dawson, A.; Knopp, R.; Bonnet, C. OpenAirInterface: A flexible platform for 5G research. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 33–38. [Google Scholar] [CrossRef]
- Herculea, D.; Chen, C.S.; Haddad, M.; Capdevielle, V. Straight: Stochastic geometry and user history based mobility estimation. In Proceedings of the 8th ACM International Workshop on Hot Topics in Planet-Scale mObile Computing and Online Social neTworking, Paderborn, Germany, 5–8 July 2016; pp. 1–6. [Google Scholar]
- Mishra, P.K.; Pandey, S. A Method for Mode Selection in a dynamic network for Device-to-Device Communication for 5G. In Proceedings of the International Conference on Informatics and Analytics, Pondicherry, India, 25–26 August 2016; pp. 1–6. [Google Scholar]
- Huang, X.; Zhao, Z.; Zhang, H. Latency analysis of cooperative caching with multicast for 5G wireless networks. In Proceedings of the 2016 IEEE/ACM 9th International Conference on Utility and Cloud Computing (UCC), Shanghai, China, 6–9 December 2016; pp. 316–320. [Google Scholar]
- Panwar, G.; Tourani, R.; Mick, T.; Mtibaa, A.; Misra, S. DICE: Dynamic multi-RAT selection in the ICN-enabled wireless edge. In Proceedings of the Workshop on Mobility in the Evolving Internet Architecture, Los Angeles CA, USA, 25 August 2017; pp. 31–36. [Google Scholar]
- Ateya, A.A.; Muthanna, A.; Gudkova, I.; Vybornova, A.; Koucheryavy, A. Intelligent core network for Tactile Internet system. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017; pp. 1–6. [Google Scholar]
- Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Mobility management for TCP in mmWave networks. In Proceedings of the 1st ACM Workshop on Millimeter-Wave Networks and Sensing Systems 2017, Snowbird, UT, USA 16 October 2017; pp. 11–16. [Google Scholar]
- Seraoui, Y.; Belmekki, M.; Bellafkih, M.; Raouyane, B. eTOM mapping onto NFV framework: IMS use case. In Proceedings of the 2nd International Conference on Computing and Wireless Communication Systems, Larache Morocco, 14–16 November 2017; pp. 1–8. [Google Scholar]
- Liu, Y.-N.; Wang, X.-W.; Li, J.; Huang, M. A Wireless Spectrum Management Mechanism Based on the Theory of Double Auction in Cognitive Cellular Networks. In Proceedings of the 2017 International Conference on Wireless Communications, Networking and Applications, Shenzhen, China, 20–22 October 2017; pp. 16–23. [Google Scholar]
- Tranoris, C.; Denazis, S.; Guardalben, L.; Pereira, J.; Sargento, S. Enabling Cyber-Physical Systems for 5G networking: A case study on the Automotive Vertical domain. In Proceedings of the 2018 IEEE/ACM 4th International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS), Gothenburg, Sweden, 27 May–3 June 2018; pp. 37–40. [Google Scholar]
- Bojovic, B.; Lagen, S.; Giupponi, L. Implementation and evaluation of frequency division multiplexing of numerologies for 5G new radio in ns-3. In Proceedings of the 10th Workshop on ns-3, Surathkal, India, 13–14 June 2018; pp. 37–44. [Google Scholar]
- Zugno, T.; Polese, M.; Zorzi, M. Integration of carrier aggregation and dual connectivity for the ns-3 mmWave module. In Proceedings of the 10th Workshop on ns-3, Surathkal, India, 13–14 June 2018; pp. 45–52. [Google Scholar]
- Mukherjee, S.; Ravindran, R.; Raychaudhuri, D. A distributed core network architecture for 5G systems and beyond. In Proceedings of the 2018 Workshop on Networking for Emerging Applications and Technologies, Budapest, Hungary, 20 August 2018; pp. 33–38. [Google Scholar]
- Guija, D.; Siddiqui, M.S. Identity and access control for micro-services based 5G NFV platforms. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–10. [Google Scholar]
- Rosa, R.V.; Rothenberg, C.E. Blockchain-based decentralized applications meet multi-administrative domain networking. In Proceedings of the ACM SIGCOMM 2018 Conference on Posters and Demos, Budapest Hungary, 20–25 August 2018; pp. 114–116. [Google Scholar]
- De Oliveira, G.R.; Storck, C.R.; Duarte-Figueiredo, F. SoftH: Soft handover multicriteria mechanism. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing, Limassol, Cyprus, 8–12 April 2019; pp. 2422–2429. [Google Scholar]
- Kassem, M.M.; Marina, M.K.; Radunovic, B. DIY model for mobile network deployment: A step towards 5G for all. In Proceedings of the 1st ACM SIGCAS Conference on Computing and Sustainable Societies, Menlo Park and San Jose, CA, USA, 20–22 June 2018; pp. 1–5. [Google Scholar]
- Mesodiakaki, A.; Zola, E.; Kassler, A. Joint user association and backhaul routing for green 5G mesh millimeter wave backhaul networks. In Proceedings of the 20th ACM International Conference on Modelling, Analysis and Simulation of Wireless and Mobile Systems, Miami, FL, USA, 21–25 November 2017; pp. 179–186. [Google Scholar]
- Lv, Z.; Wang, Z.; Lv, Y.; Yuan, M. An AirSea Manta-Ray Robot in 5G OGCE. In Proceedings of the 2019 2nd International Conference on Service Robotics Technologies, Beijing, China, 22–24 March 2019; pp. 63–67. [Google Scholar]
- Raca, D.; Leahy, D.; Sreenan, C.J.; Quinlan, J.J. Beyond throughput, the next generation: A 5G dataset with channel and context metrics. In Proceedings of the 11th ACM Multimedia Systems Conference, Istanbul, Turkey, 8–11 June 2020; pp. 303–308. [Google Scholar]
- Aloqaily, M.; Balasubramanian, V.; Zaman, F.; Ridhawi, I.A.; Jararweh, Y. Congestion mitigation in densely crowded environments for augmenting qos in vehicular clouds. In Proceedings of the 8th ACM Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications, Montreal, QC, Canada, 28 October–2 November 2018; pp. 49–56. [Google Scholar]
- Makris, N.; Passas, V.; Korakis, T.; Tassiulas, L. Employing MEC in the Cloud-RAN: An Experimental Analysis. In Proceedings of the 2018 on Technologies for the Wireless Edge Workshop, New Delhi, India, 2 November 2018; pp. 15–19. [Google Scholar]
- Patané, G.M.; Valastro, G.C.; Sambo, Y.A.; Ozturk, M.; Hussain, S.; Imran, M.A.; Panno, D. Flexible SDN/NFV-based SON testbed for 5G mobile networks. In Proceedings of the 2019 IEEE/ACM 23rd International Symposium on Distributed Simulation and Real Time Applications (DS-RT), Cosenza, Italy, 7–9 October 2019; pp. 1–8. [Google Scholar]
- Subramanya, T.; Riggio, R.; Rasheed, T. Intent-based mobile backhauling for 5G networks. In Proceedings of the 2016 12th International Conference on Network and Service Management (CNSM), Montreal, QC, Canada, 31 October–4 November 2016; pp. 348–352. [Google Scholar]
- Park, K.H.; Kim, J.S.; Cha, S.H.; Chung, M.Y. System Capacity Analysis of Millimeter Wave Band with Polarized Antenna Structure. In Proceedings of the 12th International Conference on Ubiquitous Information Management and Communication, Langkawi, Malaysia, 5–7 January 2018; pp. 1–6. [Google Scholar]
- Lundgren, C.; Skoogh, A.; Johansson, B.; Stahre, J.; Friis, M. The value of 5G connectivity for maintenance in manufacturing industry. In Proceedings of the 2017 Winter Simulation Conference (WSC), Las Vegas, NV, USA, 3–6 December 2017; pp. 3964–3975. [Google Scholar]
- Beyranvand, H.; Lévesque, M.; Maier, M.; Salehi, J.A.; Verikoukis, C.; Tipper, D. Toward 5G: FiWi enhanced LTE-A HetNets with reliable low-latency fiber backhaul sharing and WiFi offloading. IEEE/ACM Trans. Netw. 2016, 25, 690–707. [Google Scholar] [CrossRef]
- Chirivella-Perez, E.; Calero, J.M.A.; Wang, Q.; Gutiérrez-Aguado, J. Towards a realistic 5G infrastructure emulator for experimental service deployment and performance evaluation. In Proceedings of the 2018 IEEE/ACM 22nd International Symposium on Distributed Simulation and Real Time Applications (DS-RT), Madrid, Spain, 15–17 October 2018; pp. 1–7. [Google Scholar]
- Kantor, M.; State, R.; Engel, T.; Ormazabal, G. A policy-based per-flow mobility management system design. In Proceedings of the Principles, Systems and Applications on IP Telecommunications, Chicago, IL, USA, 6–8 October 2015; pp. 35–42. [Google Scholar]
- Ginzboorg, P.; Niemi, V. Privacy of the long-term identities in cellular networks. In Proceedings of the 9th EAI International Conference on Mobile Multimedia Communications, Xi’an, China, 18–20 June 2016; pp. 167–175. [Google Scholar]
- Qaddus, A.; Aslam, S.; Minhas, A.A.; Almazyad, A. 5G Hetrogeneous Cellular Networks a Viable Mode for Implementing Future Smart Grid Networks. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017. [Google Scholar]
- Hussain, S.R.; Echeverria, M.; Singla, A.; Chowdhury, O.; Bertino, E. Insecure connection bootstrapping in cellular networks: The root of all evil. In Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, Miami, FL, USA, 15–17 May 2019; pp. 1–11. [Google Scholar]
- Blanc, G.; Kheir, N.; Ayed, D.; Lefebvre, V.; de Oca, E.M.; Bisson, P. Towards a 5G security architecture: Articulating software-defined security and security as a service. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–8. [Google Scholar]
- Annessi, R.; Fabini, J.; Zseby, T. To Trust or Not to Trust: Data Origin Authentication for Group Communication in 5G Networks. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–7. [Google Scholar]
- Adam, I.; Ping, J. Framework for security event management in 5G. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–7. [Google Scholar]
- Hanane, O.; Tomader, M. 4G and 5G: Security and privacy analysis. In Proceedings of the 4th International Conference on Big Data and Internet of Things, Rabat, Morocco, 23–24 October 2019; pp. 1–4. [Google Scholar]
- Basin, D.; Dreier, J.; Hirschi, L.; Radomirovic, S.; Sasse, R.; Stettler, V. A formal analysis of 5G authentication. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1383–1396. [Google Scholar]
- Ma, T.; Hu, F.; Ma, M. Securing 5G HetNets Using Mutual Physical Layer Authentication. In Proceedings of the 2019 7th International Conference on Information Technology: IoT and Smart City, Shanghai, China, 20–23 December 2019; pp. 275–278. [Google Scholar]
- Cho, J.Y.; Sergeev, A.; Zou, J. Securing ethernet-based optical fronthaul for 5g network. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; pp. 1–6. [Google Scholar]
- Mangiante, S.; Klas, G.; Navon, A.; GuanHua, Z.; Ran, J.; Silva, M.D. Vr is on the edge: How to deliver 360 videos in mobile networks. In Proceedings of the Workshop on Virtual Reality and Augmented Reality Network, Los Angeles, CA, USA, 25 August 2017; pp. 30–35. [Google Scholar]
- Chakareski, J. VR/AR immersive communication: Caching, edge computing, and transmission trade-offs. In Proceedings of the Workshop on Virtual Reality and Augmented Reality Network, Los Angeles, CA, USA, 25 August 2017; pp. 36–41. [Google Scholar]
- Reale, A.; Tóth, M.; Horváth, Z. Towards context aware computations offloading in 5G. In Proceedings of the 11th European Conference on Software Architecture: Companion Proceedings, Canterbury, UK, 11–15 September 2017; pp. 89–92. [Google Scholar]
- Sun, L.; Duanmu, F.; Liu, Y.; Wang, Y.; Ye, Y.; Shi, H.; Dai, D. Multi-path multi-tier 360-degree video streaming in 5G networks. In Proceedings of the 9th ACM Multimedia Systems Conference, Amsterdam, The Netherlands, 12–15 June 2018; pp. 162–173. [Google Scholar]
- Bujari, A.; Palazzi, C.E.; Perale, D. Addressing bandwidth demand in full-immersive virtual reality. In Proceedings of the 5th EAI International Conference on Smart Objects and Technologies for Social Good, Valencia, Spain, 25–27 September 2019; pp. 13–18. [Google Scholar]
- Foukas, X.; Marina, M.K.; Kontovasilis, K. Orion: RAN slicing for a flexible and cost-effective multi-service mobile network architecture. In Proceedings of the 23rd Annual International Conference on Mobile Computing and Networking, Snowbird, UT, USA, 16–20 October 2017; pp. 127–140. [Google Scholar]
- Kim, D.H.; Kazmi, S.A.; Hong, C.S. Cooperative slice allocation for virtualized wireless network: A matching game approach. In Proceedings of the 12th International Conference on Ubiquitous Information Management and Communication, Langkawi, Malaysia, 5–7 January 2018; pp. 1–6. [Google Scholar]
- Challa, R.; Jeon, S.; Raza, S.M.; Thorat, P.; Choo, H. Superflex: Network slicing based super flexible 5G architecture. In Proceedings of the 12th International Conference on Ubiquitous Information Management and Communication, Langkawi, Malaysia, 5–7 January 2018; pp. 1–4. [Google Scholar]
- Gramaglia, M.; Pavón, I.L.; Gringoli, F.; Garcia-Aviles, G.; Serrano, P. Design and Validation of a Multi-service 5G Network with QoE-aware Orchestration. In Proceedings of the 12th International Workshop on Wireless Network Testbeds, Experimental Evaluation & Characterization, New Delhi, India, 2 November 2018; pp. 11–18. [Google Scholar]
- Nikaein, N.; Schiller, E.; Favraud, R.; Katsalis, K.; Stavropoulos, D.; Alyafawi, I.; Zhao, Z.; Braun, T.; Korakis, T. Network store: Exploring slicing in future 5G networks. In Proceedings of the 10th International Workshop on Mobility in the Evolving Internet Architecture, Paris, France, 7 September 2015; pp. 8–13. [Google Scholar]
- Sathi, V.N.; Srinivasan, M.; Thiruvasagam, P.K.; Chebiyyam, S.R.M. A novel protocol for securing network slice component association and slice isolation in 5G networks. In Proceedings of the 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Montreal, QC, Canada, 28 October–2 November 2018; pp. 249–253. [Google Scholar]
- Oliveira, A.; Vazão, T. Adapting priority schemes to achieve network slice isolation. In Proceedings of the 35th Annual ACM Symposium on Applied Computing, Brno, Czech Republic, 30 March–3 April 2020; pp. 1164–1171. [Google Scholar]
- Martiradonna, S.; Abrardo, A.; Moretti, M.; Piro, G.; Boggia, G. Architecting RAN slicing for URLLC: Design decisions and open issues. In Proceedings of the 2019 IEEE/ACM 23rd International Symposium on Distributed Simulation and Real Time Applications (DS-RT), Cosenza, Italy, 7–9 October 2019; pp. 1–4. [Google Scholar]
- Nikaein, N.; Chang, C.-Y.; Alexandris, K. Mosaic5G: Agile and flexible service platforms for 5G research. ACM SIGCOMM Comput. Commun. Rev. 2018, 48, 29–34. [Google Scholar] [CrossRef]
- Akundi, S.; Prabhu, S.; K, N.U.B.; Mondal, S.C. Suppressing Noisy Neighbours in 5G networks: An end-to-end NFV-based framework to detect and suppress noisy neighbours. In Proceedings of the 21st International Conference on Distributed Computing and Networking, Kolkata, India, 4–7 January 2020; pp. 1–6. [Google Scholar]
- Xue, J.; Shao, H.; Ma, Q. Resource allocation for system throughput maximization based on mobile edge computing. In Proceedings of the 2018 International Conference on Electronics and Electrical Engineering Technology, Tianjin, China, 19–21 September 2018; pp. 177–181. [Google Scholar]
- Ferdouse, L.; Ejaz, W.; Anpalagan, A.; Khattak, A.M. Joint workload scheduling and BBU allocation in cloud-RAN for 5G networks. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 621–627. [Google Scholar]
- Mathur, R.P.; Pratap, A.; Misra, R. Distributed algorithm for resource allocation in uplink 5G networks. In Proceedings of the 7th ACM International Workshop on Mobility, Interference, and MiddleWare Management in HetNets, Chennai, India, 10–14 July 2017; pp. 1–6. [Google Scholar]
- Cao, T.; Xu, C.; Wang, M.; Jiang, Z.; Chen, X.; Zhong, L.; Grieco, L. Stochastic optimization for green multimedia services in dense 5G networks. ACM Trans. Multimed. Comput. Commun. Appl. (TOMM) 2019, 15, 1–22. [Google Scholar] [CrossRef]
- Dogo, E.; Salami, A.; Nwulu, N. Evaluative analysis of next generation mobile networks in future smart grid in developing countries. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–10. [Google Scholar]
- Hsiung, T.; Kanza, Y. Simct: Spatial simulation of urban evolution to test resilience of 5g cellular networks. In Proceedings of the 2nd ACM SIGSPATIAL International Workshop on GeoSpatial Simulation, Casablanca, Morocco, 2–4 October 2019; pp. 1–8. [Google Scholar]
- Sun, P.; Naser, H. A Service Slicing Strategy with QoS for LTE-based Cellular Networks. In Proceedings of the 14th ACM International Symposium on QoS and Security for Wireless and Mobile Networks, Montreal, QC, Canada, 28 October–2 November 2018; pp. 63–69. [Google Scholar]
- Rony, R.I.; Lopez-Aguilera, E.; Garcia-Villegas, E. Access-aware backhaul optimization in 5G. In Proceedings of the 16th ACM International Symposium on Mobility Management and Wireless Access, Montreal, QC, Canada, 28 October–2 November 2018; pp. 124–127. [Google Scholar]
- Li, H.; Ren, H.; Wu, J. Domain specific compiler for coordinated signal processing in 5G testbed. In Proceedings of the Workshop on Smart Internet of Things, San Jose, CA, USA, 14 October 2017; pp. 1–5. [Google Scholar]
- Barros, V.A.; Junior, S.A.; Bruschi, S.M.; Monaco, F.J.; Estrella, J.C. An IoT multi-protocol strategy for the interoperability of distinct communication protocols applied to web of things. In Proceedings of the 25th Brazillian Symposium on Multimedia and the Web, Rio de Janeiro, Brazil, 29 October–1 November 2019; pp. 81–88. [Google Scholar]
- Cho, J.; der Merwe, J.V. Poster: A new scalable, programmable and evolvable mobile control plane platform. In Proceedings of the 23rd Annual International Conference on Mobile Computing and Networking, Snowbird, UT, USA, 16–20 October 2017; pp. 540–542. [Google Scholar]
- Mathur, S.; Saha, D.; Raychaudhuri, D. Poster: Cross-layer MAC/PHY protocol to support IoT traffic in 5G. In Proceedings of the 22nd Annual International Conference on Mobile Computing and Networking, MobiCom 2016, New York, NY, USA, 3–7 October 2016; pp. 467–468. [Google Scholar]
- Sagari, S.S.; Mathur, S.; Saha, D.; Amin, S.O.; Ravindran, R.; Seskar, I.; Raychaudhuri, D.; Wang, G. Realization of CDMA-based IoT services with shared band operation of LTE in 5G. In Proceedings of the Workshop on Mobile Edge Communications, Los Angeles, CA, USA, 21 August 2017; pp. 37–42. [Google Scholar]
- Ali, F.; Yigang, H. Spectrum for Next Generation Technologies. In Proceedings of the 2019 8th International Conference on Software and Information Engineering, Cairo, Egypt, 9–12 April 2019; pp. 188–191. [Google Scholar]
- Ruuskanen, J.; Peng, H.; Martins, A. Latency prediction in 5G for control with deadtime compensation. In Proceedings of the Workshop on Fog Computing and the IoT, Montreal, QC, Canada, 15 April 2019; pp. 51–55. [Google Scholar]
- Tsai, C.; Moh, M. Cache management for 5G cloud radio access networks. In Proceedings of the 12th International Conference on Ubiquitous Information Management and Communication, Langkawi, Malaysia, 5–7 January 2018; pp. 1–8. [Google Scholar]
- Meroni, G.; Mizmizi, M.; Plebani, P.; Reggiani, L. Improving Mobile Business Process Monitoring with Enhanced NFV MANO; Association for Computing Machinery: Brno, Czech Republic, 2020. [Google Scholar]
- Su, G.; Moh, M. Improving energy efficiency and scalability for IoT communications in 5G networks. In Proceedings of the 12th International Conference on Ubiquitous Information Management and Communication, Langkawi, Malaysia, 5–7 January 2018; pp. 1–8. [Google Scholar]
- Desikan, K.S.; Srinivasan, M.; Murthy, C.S.R. A novel distributed latency-aware data processing in fog computing-enabled iot networks. In Proceedings of the ACM Workshop on Distributed Information Processing in Wireless Networks, Chennai, India, 10–14 July 2017; pp. 1–6. [Google Scholar]
- Choudhari, T.; Moh, M.; Moh, T.-S. Prioritized task scheduling in fog computing. In Proceedings of the ACMSE 2018 Conference, Richmond, Kentucky, 29–31 March 2018; pp. 1–8. [Google Scholar]
- Pratap, A.; Concone, F.; Nadendla, V.S.S.; Das, S.K. Three-Dimensional Matching based Resource Provisioning for the Design of Low-Latency Heterogeneous IoT Networks. In Proceedings of the 22nd International ACM Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Miami Beach, FL, USA, 25–29 November 2019; pp. 79–86. [Google Scholar]
- Kaur, G.; Moh, M. Cloud computing meets 5G networks: Efficient cache management in cloud radio access networks. In Proceedings of the ACMSE 2018 Conference, Richmond, Kentucky, 29–31 March 2018; pp. 1–8. [Google Scholar]
- Roozbeh, A. Distributed cloud and de-centralized control plane: A proposal for scalable control plane for 5G. In Proceedings of the 2015 IEEE/ACM 8th International Conference on Utility and Cloud Computing (UCC), Limassol, Cyprus, 7–10 December 2015; pp. 348–353. [Google Scholar]
- Aftab, M.U.; Munir, Y.; Oluwasanmi, A.; Qin, Z.; Aziz, M.H.; Son, N.T. A Hybrid Access Control Model With Dynamic COI for Secure Localization of Satellite and IoT-Based Vehicles. IEEE Access 2020, 8, 24196–24208. [Google Scholar] [CrossRef]
- Najm, I.A.; Hamoud, A.K.; Lloret, J.; Bosch, I. Machine learning prediction approach to enhance congestion control in 5G IoT environment. Electronics 2019, 8, 607. [Google Scholar] [CrossRef] [Green Version]
- Guerrero-Pérez, A.D. Resource Management of IoT Devices in Restrictive Environments. In Proceedings of the 1st ACM Workshop on Emerging Smart Technologies and Infrastructures for Smart Mobility and Sustainability, Los Cabos, Mexico, 21 October 2019; pp. 33–38. [Google Scholar]
- Chahlaoui, F.; El-Fenni, M.R.; Dahmouni, H. Performance analysis of load balancing mechanisms in SDN networks. In Proceedings of the 2nd International Conference on Networking, Information Systems & Security, Rabat, Morocco, 27–29 March 2019; pp. 1–8. [Google Scholar]
- Luntovskyy, A.; Globa, L. Performance, Reliability and Scalability for IoT. In Proceedings of the 2019 International Conference on Information and Digital Technologies (IDT), Zilina, Slovakia, 25–27 June 2019; pp. 316–321. [Google Scholar]
- Vukobratovic, D.; Jakovetic, D.; Skachek, V.; Bajovic, D.; Sejdinovic, D.; Kurt, G.K.; Hollanti, C.; Fischer, I. CONDENSE: A reconfigurable knowledge acquisition architecture for future 5G IoT. IEEE Access 2016, 4, 3360–3378. [Google Scholar] [CrossRef]
- Baniata, M.; Ji, H.; Kim, Y.; Choi, J.; Hong, J. Energy-balancing unequal concentric chain clustering (MIMO-UCC) protocol for IoT system in 5G environment. In Proceedings of the 2018 Conference on Research in Adaptive and Convergent Systems, Honolulu, HI, USA, 9–12 October 2018; pp. 68–74. [Google Scholar]
- Ismail, D.; Rahman, M.; Saifullah, A. Low-power wide-area networks: Opportunities, challenges, and directions. In Proceedings of the Workshop Program of the 19th International Conference on Distributed Computing and Networking, Varanasi, India, 4–7 January 2018; pp. 1–6. [Google Scholar]
- Jsm, L.M.; Lokesh, V.; Polyzos, G.C. Energy efficient context based forwarding strategy in named data networking of things. In Proceedings of the 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 249–254. [Google Scholar]
- Haider, D.; Yang, X.; Abbasi, Q.H. Post-surgical fall detection by exploiting the 5 G C-Band technology for eHealth paradigm. Appl. Soft Comput. 2019, 81, 105537. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, Y.; Han, P.; Shao, Z.; Li, C. Virtual network embedding in fiber-wireless access networks for resource-efficient iot service provisioning. IEEE Access 2019, 7, 65506–65517. [Google Scholar] [CrossRef]
- Maier, M.; Ebrahimzadeh, A. Towards immersive Tactile Internet experiences: Low-latency FiWi enhanced mobile networks with edge intelligence. IEEE/OSA J. Opt. Commun. Netw. 2019, 11, B10–B25. [Google Scholar] [CrossRef]
- Sharma, S.K.; Wang, X. Collaborative distributed Q-learning for RACH congestion minimization in cellular IoT networks. IEEE Commun. Lett. 2019, 23, 600–603. [Google Scholar] [CrossRef] [Green Version]
- Sandoval, R.M.; Canovas-Carrasco, S.; Garcia-Sanchez, A.-J.; Garcia-Haro, J. Smart usage of multiple RAT in IoT-oriented 5G networks: A reinforcement learning approach. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–8. [Google Scholar]
- Loghin, D.; Cai, S.; Chen, G.; Dinh, T.T.A.; Fan, F.; Lin, Q.; Ng, J.; Chin Ooi, B.; Sun, X.; Ta, Q.T.; et al. The disruptions of 5G on data-driven technologies and applications. IEEE Trans. Knowl. Data Eng. 2020, 32, 1179–1198. [Google Scholar] [CrossRef] [Green Version]
- Messaoud, S.; Bradai, A.; Moulay, E. Online GMM Clustering and Mini-Batch Gradient Descent Based Optimization for Industrial IoT 4.0. IEEE Trans. Ind. Inform. 2019, 16, 1427–1435. [Google Scholar] [CrossRef]
- Vukobratovic, D.; Jakovetic, D.; Skachek, V.; Bajovic, D.; Sejdinovic, D. Network function computation as a service in future 5G machine type communications. In Proceedings of the 2016 9th International Symposium on Turbo Codes and Iterative Information Processing (ISTC), Brest, France, 5–9 September 2016; pp. 365–369. [Google Scholar]
- Din, S.; Ahmad, A.; Paul, A. Human enabled green IoT in 5G networks. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 208–213. [Google Scholar]
- Wang, W.; Mao, C.; Zhao, S.; Cao, Y.; Yi, Y.; Chen, S.; Liu, Q. A Smart Semipartitioned Real-Time Scheduling Strategy for Mixed-Criticality Systems in 6G-Based Edge Computing. Wirel. Commun. Mob. Comput. 2021, 2021, 6663199. [Google Scholar]
- Lin, K.; Li, Y.; Zhang, Q.; Fortino, G. AI-Driven Collaborative Resource Allocation for Task Execution in 6G-Enabled Massive IoT. IEEE Internet Things J. 2021, 8, 5264–5273. [Google Scholar] [CrossRef]
- Dong, W.; Xu, Z.-H.; Li, X.-X.; Xiao, S.-P. Low-cost subarrayed sensor array design strategy for iot and future 6g applications. IEEE Internet Things J. 2020, 7, 4816–4826. [Google Scholar] [CrossRef]
- Yang, Z.; Fang, Y.; Han, G.; Huq, K.M.S. Spatially-Coupled Protograph LDPC-Coded Hierarchical Modulated BICM-ID Systems: A Promising Transmission Technique for 6G-Enabled Internet of Things. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Liu, R.W.; Nie, J.; Garg, S.; Xiong, Z.; Zhang, Y.; Hossain, M.S. Data-driven trajectory quality improvement for promoting intelligent vessel traffic services in 6G-enabled maritime IoT systems. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Imran, M.; Han, Z.; Hong, C.S. 6G wireless systems: A vision, architectural elements and future directions. IEEE Access 2020, 8, 147029–147044. [Google Scholar] [CrossRef]
- Liu, C.; Feng, W.; Chen, Y.; Wang, C.-X.; Ge, N. Cell-free satellite-UAV networks for 6G wide-area Internet of Things. IEEE J. Sel. Areas Commun. 2020. [Google Scholar] [CrossRef]
- Mukherjee, A.; Goswami, P.; Khan, M.A.; Manman, L.; Yang, L.; Pillai, P. Energy Efficient Resource Allocation strategy in Massive IoT for Industrial 6G Applications. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Hazra, A.; Adhikari, M.; Amgoth, T.; Srirama, S.N. Stackelberg Game for Service Deployment of IoT-Enabled Applications in 6G-aware Fog Networks. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Jia, Z.; Sheng, M.; Li, J.; Zhou, D.; Han, Z. Joint HAP Access and LEO Satellite Backhaul in 6G: Matching Game based Approaches. IEEE J. Sel. Areas Commun. 2020. [Google Scholar] [CrossRef]
- Wang, W.; Liu, F.; Zhi, X.; Zhang, T.; Huang, C. An Integrated Deep Learning Algorithm for Detecting Lung Nodules with Low-dose CT and Its Application in 6G-enabled Internet of Medical Things. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Mardini, W.; Aljawarneh, S.; Al-Abdi, A. Using Multiple RPL Instances to Enhance the Performance of New 6G and Internet of Everything (6G/IoE)-Based Healthcare Monitoring Systems. Mob. Netw. Appl. 2021, 26, 952–968. [Google Scholar] [CrossRef]
- Qi, F.; Li, W.; Yu, P.; Feng, L.; Zhou, F. Deep learning-based BackCom multiple beamforming for 6G UAV IoT networks. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 50. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Y. Using cloud computing platform of 6G IoT in e-commerce personalized recommendation. Int. J. Syst. Assur. Eng. Manag. 2021, 12, 654–666. [Google Scholar] [CrossRef]
- Lin, J.C.-W.; Srivastava, G.; Zhang, Y.; Djenouri, Y.; Aloqaily, M. Privacy preserving multi-objective sanitization model in 6G IoT environments. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Liao, Z.; Peng, J.; Huang, J.; Wang, J.; Wang, J.; Sharma, P.K.; Ghosh, U. Distributed probabilistic offloading in edge computing for 6g-enabled massive internet of things. IEEE Internet Things J. 2021, 8, 5298–5308. [Google Scholar] [CrossRef]
- Wang, F.; Zhu, M.; Wang, M.; Khosravi, M.R.; Ni, Q.; Yu, S.; Qi, L. 6G-enabled short-term forecasting for large-scale traffic flow in massive IoT based on time-aware Locality-Sensitive Hashing. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Gao, Y. Using artificial intelligence approach to design the product creative on 6G industrial internet of things. Int. J. Syst. Assur. Eng. Manag. 2021, 12, 696–704. [Google Scholar] [CrossRef]
- Xu, L. Application of wearable devices in 6G internet of things communication environment using artificial intelligence. Int. J. Syst. Assur. Eng. Manag. 2021, 12, 741–747. [Google Scholar] [CrossRef]
- Ye, Z.; Su, L. The use of data mining and artificial intelligence technology in art colors and graph and images of computer vision under 6G internet of things communication. Int. J. Syst. Assur. Eng. Manag. 2021, 12, 689–695. [Google Scholar] [CrossRef]
- Han, G.; Tu, J.; Liu, L.; Martínez-García, M.; Peng, Y. Anomaly Detection Based on Multidimensional Data Processing for Protecting Vital Devices in 6G-Enabled Massive IIoT. IEEE Internet Things J. 2021, 8, 5219–5229. [Google Scholar] [CrossRef]
- Li, Q.; Xiao, R. The use of data mining technology in agricultural e-commerce under the background of 6G Internet of things communication. Int. J. Syst. Assur. Eng. Manag. 2021, 12, 813–823. [Google Scholar] [CrossRef]
- Chen, N.; Okada, M. Towards 6G Internet of Things and the Convergence with RoF System. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Manal, R.; Fatima, R.; Tomader, M. Authentication for e-health applications in IoT enabled 5G and proposed solution. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–6. [Google Scholar]
- Fatima, R.; Manal, R.; Tomader, M. Cryptography in e-Health using 5G based IOT: A comparison study. In Proceedings of the 4th International Conference on Big Data and Internet of Things, Rabat, Morocco, 23–24 October 2019; pp. 1–6. [Google Scholar]
- Rahimi, H.; Zibaeenejad, A.; Rajabzadeh, P.; Safavi, A.A. On the security of the 5G-IoT architecture. In Proceedings of the International Conference on Smart Cities and Internet of Things, Mashhad, Iran, 26–27 September 2018; pp. 1–8. [Google Scholar]
- Shaik, A.; Borgaonkar, R.; Park, S.; Seifert, J.-P. New vulnerabilities in 4G and 5G cellular access network protocols: Exposing device capabilities. In Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, Miami, FL, USA, 15–17 May 2019; pp. 221–231. [Google Scholar]
- Zenger, C.T.; Zimmer, J.; Pietersz, M.; Driessen, B.; Paar, C. Constructive and destructive aspects of adaptive wormholes for the 5g tactile internet. In Proceedings of the 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Darmstadt, Germany, 18–20 July 2016; pp. 109–120. [Google Scholar]
- Santos, B.; Do, V.T.; Feng, B.; Do, T.V. Identity federation for cellular internet of things. In Proceedings of the 2018 7th International Conference on Software and Computer Applications, Kuantan, Malaysia, 8–10 February 2018; pp. 223–228. [Google Scholar]
- Hsieh, E.; Wang, H.; Liu, C.; Chung, S.S.; Chen, T.; Huang, S.; Chen, J.; Cheng, O. Embedded PUF on 14nm HKMG FinFET Platform: A Novel 2-bit-per-cell OTP-based Memory Feasible for IoT Secuirty Solution in 5G Era. In Proceedings of the 2019 Symposium on VLSI Technology, Kyoto, Japan, 9–14 June 2019; pp. T118–T119. [Google Scholar]
- Abraham, S.; Weller, N. Next generation traffic event detection: A framework based on internet of vehicles (IoV). In Proceedings of the Second International Conference on Internet of things, Data and Cloud Computing, Cambridge, UK, 22–23 March 2017; pp. 1–3. [Google Scholar]
- Wang, N.; Jiao, L.; Wang, P.; Dabaghchian, M.; Zeng, K. Efficient identity spoofing attack detection for iot in mm-wave and massive mimo 5g communication. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Mao, B.; Kawamoto, Y.; Kato, N. AI-based joint optimization of QoS and security for 6G energy harvesting internet of things. IEEE Internet Things J. 2020, 7, 7032–7042. [Google Scholar] [CrossRef]
- Stergiou, C.L.; Psannis, K.E.; Gupta, B.B. IoT-based Big Data secure management in the Fog over a 6G Wireless Network. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Porambage, P.; Gür, G.; Osorio, D.P.M.; Liyanage, M.; Gurtov, A.; Ylianttila, M. The Roadmap to 6G Security and Privacy. IEEE Open J. Commun. Soc. 2021. [Google Scholar] [CrossRef]
- Gedeon, J.; Krisztinkovics, J.; Meurisch, C.; Stein, M.; Wang, L.; Mühlhäuser, M. A multi-cloudlet infrastructure for future smart cities: An empirical study. In Proceedings of the 1st International Workshop on Edge Systems, Analytics and Networking, Munich, Germany, 10–15 June 2018; pp. 19–24. [Google Scholar]
- Mahdi, F.E.; Habbani, A.; Bouamoud, B.; Souidi, M. Bootstrapping services availability through multipath routing for enhanced security in urban iot. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–9. [Google Scholar]
- Musabe, R.; Ngoga, S.R.; Manizabayo, E.; Katambire, V.N.; Yaramba, H. Assessment and optimization of cooperative MIMO system for smart city application. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–5. [Google Scholar]
- Slalmi, A.; Saadane, R.; Chaibi, H.; Aroussi, H.K. Improving call admission control in 5G for smart cities applications. In Proceedings of the 4th International Conference on Smart City Applications, Casablanca, Morocco, 2–4 October 2019; pp. 1–6. [Google Scholar]
- Benhaddou, D. Living building: A building block of smart cities. In Proceedings of the 2017 International Conference on Smart Digital Environment, Rabat, Morocco, 21–23 July 2017; pp. 182–188. [Google Scholar]
- Rajaei, H.; Mirzaei, F. IoT, smart homes, and zigbee simulation. In Proceedings of the Communications and Networking Symposium, Baltimore, Maryland, 15–18 April 2018; pp. 1–10. [Google Scholar]
- Mahjoubi, A.E.; Mazri, T.; Hmina, N. First Africa and Morocco NB-IoT experimental results and deployment scenario: New approach to improve main 5G KPIs for smart water management. In Proceedings of the Mediterranean Symposium on Smart City Application, Tangier, Morocco, 25–27 October 2017; pp. 1–6. [Google Scholar]
- Raza, N.; Jabbar, S.; Han, J.; Han, K. Social vehicle-to-everything (V2X) communication model for intelligent transportation systems based on 5G scenario. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, Amman, Jordan, 26–27 June 2018; pp. 1–8. [Google Scholar]
- Wang, J.-X.; Liu, Y.; Lei, Z.-B.; Wu, K.-H.; Zhao, X.-Y.; Feng, C.; Liu, H.; Shuai, X.; Tang, Z.; Wu, L.; et al. Smart water lora IoT system. In Proceedings of the 2018 International Conference on Communication Engineering and Technology, Singapore, 24–26 February 2018; pp. 48–51. [Google Scholar]
- Ding, A.Y.; Janssen, M. Opportunities for applications using 5G networks: Requirements, challenges, and outlook. In Proceedings of the Seventh International Conference on Telecommunications and Remote Sensing, Barcelona, Spain, 8–9 October 2018; pp. 27–34. [Google Scholar]
- Lorimer, P.A.; Diec, V.M.-F.; Kantarci, B. Participatory detection of identity theft on mobile social platforms. In Proceedings of the 2017 IEEE Global Conference on Signal and Information Processing (GlobalSIP), Montreal, QC, Canada, 14–16 November 2017; pp. 833–837. [Google Scholar]
- Dinh, D.V.; Yoon, B.-N.; Le, H.N.; Nguyen, U.Q.; Phan, K.D.; Pham, L.D. ICT enabling technologies for smart cities. In Proceedings of the 2020 22nd International Conference on Advanced Communication Technology (ICACT), Phoenix Park, Korea, 16–19 February 2020; pp. 1180–1192. [Google Scholar]
- Xiao, K.; Zhao, J.; He, Y.; Yu, S. Trajectory prediction of UAV in smart city using recurrent neural networks. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Allam, Z.; Jones, D.S. Future (post-COVID) digital, smart and sustainable cities in the wake of 6G: Digital twins, immersive realities and new urban economies. Land Use Policy 2021, 101, 105201. [Google Scholar] [CrossRef]
- Woźniak, M.; Zielonka, A.; Sikora, A.; Piran, M.J.; Alamri, A. 6G-enabled IoT Home Environment control using Fuzzy Rules. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Janbi, N.; Katib, I.; Albeshri, A.; Mehmood, R. Distributed artificial intelligence-as-a-service (daiaas) for smarter ioe and 6g environments. Sensors 2020, 20, 5796. [Google Scholar] [CrossRef] [PubMed]
- Jamil, S.U.; Khan, M.A.; ur Rehman, S. Intelligent Task Off-Loading and Resource Allocation for 6G Smart City Environment. In Proceedings of the 2020 IEEE 45th Conference on Local Computer Networks (LCN), Sydney, NSW, Australia, 16–19 November 2020; pp. 441–444. [Google Scholar]
- Oleśków-Szłapka, J.; Stachowiak, A.; Pawłowski, G.; Ellefsen, A.P.M.T. Multi-Agent Systems: A Case Study in an Onshore Oilfield That Explores Opportunities and Future Perspectives in Terms of lot, AI and 5G Technology. In Proceedings of the 2019 3rd International Conference on E-Business and Internet, Prague, Czech Republic, 9–11 November 2019; pp. 29–35. [Google Scholar]
- Zhang, H.; Yang, Z.; Mohapatra, P. Wireless access to ultimate virtual reality 360-degree video. In Proceedings of the International Conference on Internet of Things Design and Implementation, Montreal, QC, Canada, 15–18 April 2019; pp. 271–272. [Google Scholar]
- Zhou, Y.; Liu, L.; Wang, L.; Hui, N.; Cui, X.; Wu, J.; Peng, Y.; Qi, Y.; Xing, C. Service aware 6G: An intelligent and open network based on convergence of communication, computing and caching. Digit. Commun. Netw. 2020, 6, 253–260. [Google Scholar] [CrossRef]
- Katz, M.; Ahmed, I. Opportunities and challenges for visible light communications in 6G. In Proceedings of the 2020 2nd 6G wireless summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar]
- Pawłowicz, B.; Salach, M.; Trybus, B. Smart city traffic monitoring system based on 5G cellular network, RFID and machine learning. In Proceedings of the KKIO Software Engineering Conference, Pułtusk, Poland, 1 September 2018; pp. 151–165. [Google Scholar]
- Lloret, J.; Parra, L.; Taha, M.; Tomás, J. An architecture and protocol for smart continuous eHealth monitoring using 5G. Comput. Netw. 2017, 129, 340–351. [Google Scholar] [CrossRef]
- Lorimer, P.A.; Diec, V.M.-F.; Kantarci, B. COVERS-UP: Collaborative Verification of Smart User Profiles for social sustainability of smart cities. Sustain. Cities Soc. 2018, 38, 348–358. [Google Scholar] [CrossRef]
- Han, Y.; Rao, B.D.; Lee, J. Massive uncoordinated access with massive MIMO: A dictionary learning approach. IEEE Trans. Wirel. Commun. 2019, 19, 1320–1332. [Google Scholar] [CrossRef]
- Tian, X.; Huang, Y.; Verma, S.; Jin, M.; Ghosh, U.; Rabie, K.M.; ThuanDo, D. Power allocation scheme for maximizing spectral efficiency and energy efficiency tradeoff for uplink NOMA systems in B5G/6G. Phys. Commun. 2020, 43, 101227. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Pirbhulal, S.; Zongwei, L.; Muhammad, K.; Zahid, N. Towards 6G Architecture for Energy Efficient Communication in IoT-Enabled Smart Automation Systems. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Ramírez-Arroyo, A.; Zapata-Cano, P.H.; Palomares-Caballero, Á.; Carmona-Murillo, J.; Luna-Valero, F.; Valenzuela-Valdés, J.F. Multilayer Network Optimization for 5G & 6G. IEEE Access 2020, 8, 204295–204308. [Google Scholar]
- Verma, S.; Kaur, S.; Khan, M.A.; Sehdev, P.S. Towards Green Communication in 6G-enabled Massive Internet of Things. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Krundyshev, V.; Kalinin, M. Hybrid neural network framework for detection of cyber attacks at smart infrastructures. In Proceedings of the 12th International Conference on Security of Information and Networks, Sochi, Russia, 12–15 September 2019; pp. 1–7. [Google Scholar]
- Fletcher, J.; Wallom, D. Using machine learning to orchestrate cloud resources in a RAN enabled edge environment. In Proceedings of the 17th Conference on Embedded Networked Sensor Systems, New York, NY, USA, 10–13 November 2019; pp. 452–453. [Google Scholar]
- Tseng, S.-C.; Liu, Z.-W.; Chou, Y.-C.; Huang, C.-W. Radio resource scheduling for 5G NR via deep deterministic policy gradient. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Tayyaba, S.K.; Khattak, H.A.; Almogren, A.; Shah, M.A.; Din, I.U.; Alkhalifa, I.; Guizani, M. 5G vehicular network resource management for improving radio access through machine learning. IEEE Access 2020, 8, 6792–6800. [Google Scholar]
- Ouyang, Y.; Li, Z.; Su, L.; Lu, W.; Lin, Z. APP-SON: Application characteristics-driven SON to optimize 4G/5G network performance and quality of experience. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 1514–1523. [Google Scholar]
- Han, Z.; Liang, J. The analysis of node planning and control logic optimization of 5G wireless networks under deep mapping learning algorithms. IEEE Access 2019, 7, 156489–156499. [Google Scholar] [CrossRef]
- Klautau, A.; Batista, P.; González-Prelcic, N.; Wang, Y.; Heath, R.W. 5G MIMO data for machine learning: Application to beam-selection using deep learning. In Proceedings of the 2018 Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 11–16 February 2018; pp. 1–9. [Google Scholar]
- Ho, C.-C.; Huang, B.-H.; Wu, M.-T.; Wu, T.-Y. Optimized Base Station Allocation for Platooning Vehicles Underway by Using Deep Learning Algorithm Based on 5G-V2X. In Proceedings of the 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 15–18 October 2019; pp. 1–2. [Google Scholar]
- Joseph, S.; Misra, R.; Katti, S. Towards self-driving radios: Physical-layer control using deep reinforcement learning. In Proceedings of the 20th International Workshop on Mobile Computing Systems and Applications, Santa Cruz, CA, USA, 27–28 February 2019; pp. 69–74. [Google Scholar]
- Liu, Q.; Han, T. When network slicing meets deep reinforcement learning. In Proceedings of the 15th International Conference on emerging Networking EXperiments and Technologies, Orlando, FL, USA, 9–12 December 2019. [Google Scholar] [CrossRef]
- Villacrés, J.L.C.; Zhao, Z.; Braun, T.; Li, Z. A particle filter-based reinforcement learning approach for reliable wireless indoor positioning. IEEE J. Sel. Areas Commun. 2019, 37, 2457–2473. [Google Scholar] [CrossRef]
- Zhang, X.; Liang, Y.-C.; Fang, J. Bayesian Inference Algorithms for Multiuser Detection in M2M Communications. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–6. [Google Scholar]
- Awan, D.A.; Cavalcante, R.L.; Yukawa, M.; Stanczak, S. Detection for 5G-NOMA: An online adaptive machine learning approach. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Asadi, A.; Müller, S.; Sim, G.H.; Klein, A.; Hollick, M. FML: Fast machine learning for 5G mmWave vehicular communications. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 1961–1969. [Google Scholar]
- Guo, Y.; Wang, Z.; Li, M.; Liu, Q. Machine learning based mmWave channel tracking in vehicular scenario. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Sullivan, K.; Tolan, M. Machine Learning for Terahertz Communication with Human-Implantable Devices. In Proceedings of the 2018 European Conference on Networks and Communications (EuCNC), Ljubljana, Slovenia, 18–21 June 2018; pp. 293–297. [Google Scholar]
- Guo, L.; Jin, B.; Yu, R.; Yao, C.; Sun, C.; Huang, D. Multi-label classification methods for green computing and application for mobile medical recommendations. IEEE Access 2016, 4, 3201–3209. [Google Scholar] [CrossRef]
- Mohanta, B.; Das, P.; Patnaik, S. Healthcare 5.0: A paradigm shift in digital healthcare system using Artificial Intelligence, IOT and 5G Communication. In Proceedings of the 2019 International Conference on Applied Machine Learning (ICAML), Bhubaneswar, India, 25–26 May 2019; pp. 191–196. [Google Scholar]
- Elkourdi, M.; Mazin, A.; Gitlin, R.D. Performance analysis for virtual-cell based CoMP 5G networks using deep recurrent neural nets. In Proceedings of the 2019 Wireless Telecommunications Symposium (WTS), New York, NY, USA, 9–12 April 2019; pp. 1–6. [Google Scholar]
- Motade, S.N.; Kulkarni, A.V. Channel estimation and data detection using machine learning for MIMO 5G communication systems in fading channel. Technologies 2018, 6, 72. [Google Scholar] [CrossRef] [Green Version]
- Balevi, E.; Gitlin, R.D. Synergies between cloud-fag-thing and brain-spinal cord-nerve networks. In Proceedings of the 2018 Information theory and applications workshop (ITA), San Diego, CA, USA, 11–16 February 2018; pp. 1–9. [Google Scholar]
- Balevi, E.; Gitlin, R.D. Unsupervised machine learning in 5G networks for low latency communications. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–2. [Google Scholar]
- Shen, Y.; Fang, W.; Ye, F.; Kadoch, M. EV charging behavior analysis using hybrid intelligence for 5G smart grid. Electronics 2020, 9, 80. [Google Scholar] [CrossRef] [Green Version]
- Yan, S.; Jiao, M.; Zhou, Y.; Peng, M.; Daneshmand, M. Machine-Learning Approach for User Association and Content Placement in Fog Radio Access Networks. IEEE Internet Things J. 2020, 7, 9413–9425. [Google Scholar] [CrossRef]
- Li, Y.; Chai, K.K.; Chen, Y.; Loo, J. Smart duty cycle control with reinforcement learning for machine to machine communications. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), London, UK, 8–12 June 2015; pp. 1458–1463. [Google Scholar]
- Xu, F.; Hong, T.; Zhao, J.; Yang, T. Detection and identification technology of rotor unmanned aerial vehicles in 5G scene. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719853990. [Google Scholar] [CrossRef] [Green Version]
- Healy, M.; Walsh, P. Detecting demeanor for healthcare with machine learning. In Proceedings of the 2017 IEEE International Conference on Bioinformatics and Biomedicine (BIBM), Kansas City, MO, USA, 13–16 November 2017; pp. 2015–2019. [Google Scholar]
- Sim, G.H.; Klos, S.; Asadi, A.; Klein, A.; Hollick, M. An online context-aware machine learning algorithm for 5G mmWave vehicular communications. IEEE/ACM Trans. Netw. 2018, 26, 2487–2500. [Google Scholar] [CrossRef]
- Falkenberg, R.; Sliwa, B.; Piatkowski, N.; Wietfeld, C. Machine learning based uplink transmission power prediction for LTE and upcoming 5G networks using passive downlink indicators. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–7. [Google Scholar]
- Yan, M.; Chen, B.; Feng, G.; Qin, S. Federated cooperation and augmentation for power allocation in decentralized wireless networks. IEEE Access 2020, 8, 48088–48100. [Google Scholar] [CrossRef]
- Zhen, L.; Bashir, A.K.; Yu, K.; Al-Otaibi, Y.D.; Foh, C.H.; Xiao, P. Energy-efficient random access for LEO satellite-assisted 6G Internet of remote things. IEEE Internet Things J. 2020. [Google Scholar] [CrossRef]
- Kouroshnezhad, S.; Peiravi, A.; Haghighi, M.S.; Jolfaei, A. Energy-Efficient Drone Trajectory Planning for the Localization of 6G-enabled IoT Devices. IEEE Internet Things J. 2020, 8, 5202–5210. [Google Scholar] [CrossRef]
- Pokhrel, S.R. Federated learning meets blockchain at 6G edge: A drone-assisted networking for disaster response. In Proceedings of the 2nd ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and Beyond, London, UK, 25 September 2020; pp. 49–54. [Google Scholar]
- Deng, J.; Zeng, J.; Mai, S.; Jin, B.; Yuan, B.; You, Y.; Lu, S.; Yang, M. Analysis and prediction of ship energy efficiency using 6G big data internet of things and artificial intelligence technology. Int. J. Syst. Assur. Eng. Manag. 2021, 12, 824–834. [Google Scholar] [CrossRef]
- Hadi, M.S.; Lawey, A.Q.; El-Gorashi, T.E.; Elmirghani, J.M. Patient-centric HetNets powered by machine learning and big data analytics for 6G networks. IEEE Access 2020, 8, 85639–85655. [Google Scholar] [CrossRef]
- Liu, S.; Alfadhli, Y.M.; Shen, S.; Tian, H.; Chang, G.-K. Mitigation of multi-user access impairments in 5G A-RoF-based mobile fronthaul utilizing machine learning for an artificial neural network nonlinear equalizer. In Proceedings of the 2018 Optical Fiber Communications Conference and Exposition (OFC), San Diego, CA, USA, 11–15 March 2018; pp. 1–3. [Google Scholar]
- Bega, D.; Gramaglia, M.; Banchs, A.; Sciancalepore, V.; Costa-Pérez, X. A machine learning approach to 5G infrastructure market optimization. IEEE Trans. Mob. Comput. 2019, 19, 498–512. [Google Scholar] [CrossRef]
- Jia, Z.; Cheng, W.; Zhang, H. A partial learning-based detection scheme for massive MIMO. IEEE Wirel. Commun. Lett. 2019, 8, 1137–1140. [Google Scholar] [CrossRef]
- Meng, Q.; Fang, X.; Yue, W.; Meng, Y.; Wei, J. Bayesian Network Prediction of Mobile User Throughput in 5G Wireless Networks. In Proceedings of the 2018 10th International Conference on Communications, Circuits and Systems (ICCCAS), Chengdu, China, 22–24 December 2018; pp. 291–295. [Google Scholar]
- Yahia, I.G.B.; Bendriss, J.; Samba, A.; Dooze, P. CogNitive 5G networks: Comprehensive operator use cases with machine learning for management operations. In Proceedings of the 2017 20th Conference on Innovations in Clouds, Internet and Networks (ICIN), Paris, France, 7–9 March 2017; pp. 252–259. [Google Scholar]
- Luo, H.; Xu, J.; Zhang, J.; Zhang, P.; Huang, L. Deep Learning Based Antenna Selection Aided Space-Time Shift Keying Systems. In Proceedings of the Proceedings of the 2019 International Conference on Artificial Intelligence and Computer Science, Wuhan, China, 12–13 July 2019; pp. 409–413. [Google Scholar]
- Maimó, L.F.; Clemente, F.J.G.; Pérez, M.G.; Pérez, G.M. On the performance of a deep learning-based anomaly detection system for 5G networks. In Proceedings of the 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), San Francisco, CA, USA, 4–8 August 2017; pp. 1–8. [Google Scholar]
- Khunteta, S.; Chavva, A.K.R. Deep learning based link failure mitigation. In Proceedings of the 2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA), Cancun, Mexico, 18–21 December 2017; pp. 806–811. [Google Scholar]
- Borgerding, M.; Schniter, P.; Rangan, S. AMP-inspired deep networks for sparse linear inverse problems. IEEE Trans. Signal Process. 2017, 65, 4293–4308. [Google Scholar] [CrossRef]
- Kim, K.; Lee, J.; Choi, J. Deep learning based pilot allocation scheme (DL-PAS) for 5G massive MIMO system. IEEE Commun. Lett. 2018, 22, 828–831. [Google Scholar] [CrossRef]
- Bega, D.; Gramaglia, M.; Fiore, M.; Banchs, A.; Costa-Perez, X. DeepCog: Cognitive network management in sliced 5G networks with deep learning. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 280–288. [Google Scholar]
- Thantharate, A.; Paropkari, R.; Walunj, V.; Beard, C. Deepslice: A deep learning approach towards an efficient and reliable network slicing in 5G networks. In Proceedings of the 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 10–12 October 2019; pp. 762–767. [Google Scholar]
- Hughes, B.; Bothe, S.; Farooq, H.; Imran, A. Generative adversarial learning for machine learning empowered self organizing 5G networks. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 282–286. [Google Scholar]
- Yan, M.; Feng, G.; Zhou, J.; Sun, Y.; Liang, Y.-C. Intelligent resource scheduling for 5G radio access network slicing. IEEE Trans. Veh. Technol. 2019, 68, 7691–7703. [Google Scholar] [CrossRef]
- Hao, H.; Xu, C.; Wang, M.; Xie, H.; Liu, Y.; Wu, D.O. Knowledge-centric proactive edge caching over mobile content distribution network. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 450–455. [Google Scholar]
- Cao, J.; Peng, T.; Dong, W.; Liu, X.; Wang, W. An association rules based conflict-graph construction approach for ultra-dense networks. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–7. [Google Scholar]
- Schwarzmann, S.; Marquezan, C.C.; Bosk, M.; Liu, H.; Trivisonno, R.; Zinner, T. Estimating video streaming QoE in the 5G architecture using machine learning. In Proceedings of the Proceedings of the 4th Internet-QoE Workshop on QoE-based Analysis and Management of Data Communication Networks, Los Cabos, Mexico, 21 October 2019; pp. 7–12. [Google Scholar]
- Kao, W.-C.; Zhan, S.-Q.; Lee, T.-S. AI-Aided 3-D Beamforming for Millimeter Wave Communications. In Proceedings of the 2018 International Symposium on Intelligent Signal Processing and Communication Systems (ISPACS), Ishigaki, Japan, 27–30 November 2018; pp. 278–283. [Google Scholar]
- Imtiaz, S.; Ghauch, H.; Rahman, M.M.U.; Koudouridis, G.; Gross, J. Learning-based resource allocation scheme for TDD-based 5G CRAN system. In Proceedings of the 19th ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Malta, Malta, 13–17 November 2016; pp. 176–185. [Google Scholar]
- VKafle, P.; Fukushima, Y.; Martinez-Julia, P.; Miyazawa, T. Consideration on automation of 5G network slicing with machine learning. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–8. [Google Scholar]
- Ma, B.; Yang, B.; Zhu, Y.; Zhang, J. Context-aware proactive 5G load balancing and optimization for urban areas. IEEE Access 2020, 8, 8405–8417. [Google Scholar] [CrossRef]
- Jiang, W.; Strufe, M.; Schotten, H.D. A SON decision-making framework for intelligent management in 5G mobile networks. In Proceedings of the 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; pp. 1158–1162. [Google Scholar]
- Jiang, W.; Strufe, M.; Gundall, M.; Schotten, H.D. An SDN/NFV Proof-of-Concept Test-Bed for Machine Learning-Based Network Management. In Proceedings of the 2018 IEEE 4th International Conference on Computer and Communications (ICCC), Chengdu, China, 7–10 December 2018; pp. 1966–1971. [Google Scholar]
- Careglio, D.; Spadaro, S.; Cabellos, A.; Lazaro, J.; Perelló, J.; Barlet, P.; Gené, J.M.; Paillissé, J. ALLIANCE Project: Architecting a knowledge-defined 5G-enabled network infrastructure. In Proceedings of the 2018 20th International Conference on Transparent Optical Networks (ICTON), Bucharest, Romania, 1–5 July 2018; pp. 1–6. [Google Scholar]
- Balapuwaduge, I.A.; Li, F.Y. Hidden Markov Model Based Machine Learning for mMTC Device Cell Association in 5G Networks. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Bosneag, A.-M.; Wang, M.X. Intelligent network management mechanisms as a step towards SG. In Proceedings of the 2017 8th International Conference on the Network of the Future (NOF), London, UK, 22–24 November 2017; pp. 52–57. [Google Scholar]
- Ahmed, I.; Khammari, H. Joint machine learning based resource allocation and hybrid beamforming design for massive MIMO systems. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Yazar, A.; Arslan, H. Selection of waveform parameters using machine learning for 5G and beyond. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; pp. 1–6. [Google Scholar]
- Strodthoff, N.; Göktepe, B.; Schierl, T.; Samek, W.; Hellge, C. Machine learning for early HARQ feedback prediction in 5G. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Perez, J.S.; Jayaweera, S.K.; Lane, S. Machine learning aided cognitive RAT selection for 5G heterogeneous networks. In Proceedings of the 2017 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Istanbul, Turkey, 5–8 June 2017; pp. 1–5. [Google Scholar]
- Li, J.; Zhao, Z.; Li, R. Machine learning-based IDS for software-defined 5G network. IET Netw. 2017, 7, 53–60. [Google Scholar] [CrossRef] [Green Version]
- Khan, T.A.; Mehmood, A.; Rivera, J.J.D.; Song, W.-C. Machine learning approach for automatic configuration and management of 5g platforms. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–6. [Google Scholar]
- Salhab, N.; Rahim, R.; Langar, R.; Boutaba, R. Machine learning based resource orchestration for 5g network slices. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Gupta, R.K.; Misra, R. Machine Learning-based Slice allocation Algorithms in 5G Networks. In Proceedings of the 2019 International Conference on Advances in Computing, Communication and Control (ICAC3), Mumbai, India, 20–21 December 2019; pp. 1–4. [Google Scholar]
- Ahmadi, H.; Fontanesi, G.; Katzis, K.; Shakir, M.Z.; Zhu, A. Resilience of airborne networks. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 1–2. [Google Scholar]
- Ali-Tolppa, J.; Kocsis, S.; Schultz, B.; Bodrog, L.; Kajo, M. Self-healing and resilience in future 5G cognitive autonomous networks. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–8. [Google Scholar]
- Li, Y.; Piao, X.; Zhang, H.; Lei, K. NDN producer mobility management based on echo state network: A lightweight machine learning approach. In Proceedings of the 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS), Singapore, 11–13 December 2018; pp. 275–282. [Google Scholar]
- Mwanje, S.S.; Mannweiler, C. Towards cognitive autonomous networks in 5g. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–8. [Google Scholar]
- Bashir, A.K.; Arul, R.; Basheer, S.; Raja, G.; Jayaraman, R.; Qureshi, N.M.F. An optimal multitier resource allocation of cloud RAN in 5G using machine learning. Trans. Emerg. Telecommun. Technol. 2019, 30, e3627. [Google Scholar] [CrossRef]
- Murudkar, C.V.; Gitlin, R.D. User-centric approaches for next-generation self-organizing wireless communication networks using machine learning. In Proceedings of the 2019 IEEE International Conference on Microwaves, Antennas, Communications and Electronic Systems (COMCAS), Tel-Aviv, Israel, 4–6 November 2019; pp. 1–6. [Google Scholar]
- Awan, D.A.; Cavalcante, R.L.; Stanczak, S. Robust Cell-Load Learning With a Small Sample Set. IEEE Trans. Signal Process. 2019, 68, 270–283. [Google Scholar] [CrossRef]
- Mozaffari, M.; Kasgari, A.T.Z.; Saad, W.; Bennis, M.; Debbah, M. Beyond 5G with UAVs: Foundations of a 3D wireless cellular network. IEEE Trans. Wirel. Commun. 2018, 18, 357–372. [Google Scholar] [CrossRef] [Green Version]
- Zhang, J.; Xu, X.; Zhang, K.; Zhang, B.; Tao, X.; Zhang, P. Machine learning based flexible transmission time interval scheduling for eMBB and uRLLC coexistence scenario. IEEE Access 2019, 7, 65811–65820. [Google Scholar] [CrossRef]
- Ibarrola, E.; Davis, M.; Voisin, C.; Close, C.; Cristobo, L. A machine learning management model for qoe enhancement in next-generation wireless ecosystems. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–8. [Google Scholar]
- Zhu, G.; Zan, J.; Yang, Y.; Qi, X. A supervised learning based QoS assurance architecture for 5G networks. IEEE Access 2019, 7, 43598–43606. [Google Scholar] [CrossRef]
- Qin, M.; Yang, Q.; Cheng, N.; Zhou, H.; Rao, R.R.; Shen, X. Machine learning aided context-aware self-healing management for ultra dense networks with QoS provisions. IEEE Trans. Veh. Technol. 2018, 67, 12339–12351. [Google Scholar] [CrossRef]
- Martin, A.; Egaña, J.; Flórez, J.; Montalbán, J.; Olaizola, I.G.; Quartulli, M.; Viola, R.; Zorrilla, M. Network resource allocation system for QoE-aware delivery of media services in 5G networks. IEEE Trans. Broadcast. 2018, 64, 561–574. [Google Scholar] [CrossRef]
- Ilievski, G.; Latkoski, P. Efficiency of Supervised Machine Learning Algorithms in Regular and Encrypted VoIP Classification within NFV Environment. Radioengineering 2020, 29, 243–250. [Google Scholar] [CrossRef]
- Sciancalepore, V.; Costa-Perez, X.; Banchs, A. RL-NSB: Reinforcement learning-based 5G network slice broker. IEEE/ACM Trans. Netw. 2019, 27, 1543–1557. [Google Scholar] [CrossRef] [Green Version]
- Vita, F.D.; Bruneo, D.; Puliafito, A.; Nardini, G.; Virdis, A.; Stea, G. A deep reinforcement learning approach for data migration in multi-access edge computing. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–8. [Google Scholar]
- Shahriari, B.; Moh, M.; Moh, T.-S. Generic Online Learning for Partial Visible Dynamic Environment with Delayed Feedback: Online Learning for 5G C-RAN Load-Balancer. In Proceedings of the 2017 International Conference on High Performance Computing & Simulation (HPCS), Genoa, Italy, 17–21 July 2017; pp. 176–185. [Google Scholar]
- Wang, X.; Li, J.; Wang, L.; Yang, C.; Han, Z. Intelligent user-centric network selection: A model-driven reinforcement learning framework. IEEE Access 2019, 7, 21645–21661. [Google Scholar] [CrossRef]
- Zineb, A.B.; Ayadi, M.; Tabbane, S. A novel cognitive architecture for QoS/QoE management in NextG Networks based on Q-learning and R-MLP approaches. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference (IWCMC), Paphos, Cyprus, 5–9 September 2016; pp. 892–897. [Google Scholar]
- Murudkar, C.V.; Gitlin, R.D. Optimal-capacity, shortest path routing in self-organizing 5G networks using machine learning. In Proceedings of the 2019 IEEE 20th Wireless and Microwave Technology Conference (WAMICON), Cocoa Beach, FL, USA, 8–9 April 2019; pp. 1–5. [Google Scholar]
- Puspita, R.H.; Shah, S.D.A.; Lee, G.-m.; Roh, B.-h.; Oh, J.; Kang, S. Reinforcement learning based 5G enabled cognitive radio networks. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 16–18 October 2019; pp. 555–558. [Google Scholar]
- Troia, S.; Alvizu, R.; Maier, G. Reinforcement learning for service function chain reconfiguration in NFV-SDN metro-core optical networks. IEEE Access 2019, 7, 167944–167957. [Google Scholar] [CrossRef]
- Bikov, E.; Botvich, D. Smart concurrent learning scheme for 5G network: QoS-aware radio resource allocation. In Proceedings of the 2017 IVth International Conference on Engineering and Telecommunication (EnT), Moscow, Russia, 29–30 November 2017; pp. 99–103. [Google Scholar]
- Abiko, Y.; Saito, T.; Ikeda, D.; Ohta, K.; Mizuno, T.; Mineno, H. Flexible resource block allocation to multiple slices for radio access network slicing using deep reinforcement learning. IEEE Access 2020, 8, 68183–68198. [Google Scholar] [CrossRef]
- Sreedevi, A.; Rao, T.R. Reinforcement learning algorithm for 5G indoor device-to-device communications. Trans. Emerg. Telecommun. Technol. 2019, 30, e3670. [Google Scholar] [CrossRef]
- Imtiaz, S.; Koudouridis, G.P.; Ghauch, H.; Gross, J. Random forests for resource allocation in 5G cloud radio access networks based on position information. EURASIP J. Wirel. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef]
- Imtiaz, S.; Ghauch, H.; Koudouridis, G.P.; Gross, J. Random forests resource allocation for 5G systems: Performance and robustness study. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Barcelona, Spain, 15–18 April 2018; pp. 326–331. [Google Scholar]
- Daga, H.; Nicholson, P.K.; Gavrilovska, A.; Lugones, D. Cartel: A system for collaborative transfer learning at the edge. In Proceedings of the ACM Symposium on Cloud Computing, Santa Cruz, CA, USA, 20–23 November 2019; pp. 25–37. [Google Scholar]
- Chergui, H.; Tourki, K.; Lguensat, R.; Benjillali, M.; Verikoukis, C.; Debbah, M. Classification algorithms for semi-blind uplink/downlink decoupling in sub-6 GHz/mmwave 5G networks. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 2031–2035. [Google Scholar]
- Yang, Y.; Deng, X.; He, D.; You, Y.; Song, R. Machine learning inspired codeword selection for dual connectivity in 5G user-centric ultra-dense networks. IEEE Trans. Veh. Technol. 2019, 68, 8284–8288. [Google Scholar] [CrossRef]
- Dai, L.; Zhang, H.; Zhuang, Y. Propagation-model-free coverage evaluation via machine learning for future 5G networks. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 1–5. [Google Scholar]
- Gebrie, H.; Farooq, H.; Imran, A. What machine learning predictor performs best for mobility prediction in cellular networks? In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Xie, Y.; Ji, W.; Li, T.; Liang, Y.; Li, F. Location Aided and Machine Learning-Based Beam Allocation for 3D Massive MIMO Systems. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 836–841. [Google Scholar]
- Sun, D.; Willmann, S. Deep learning-based dependability assessment method for industrial wireless network. IFAC-PapersOnLine 2019, 52, 219–224. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. A deep learning method with wrapper based feature extraction for wireless intrusion detection system. Comput. Secur. 2020, 92, 101752. [Google Scholar] [CrossRef]
- Lin, J.; Feng, S.; Zhang, Y.; Yang, Z.; Zhang, Y. A novel deep neural network based approach for sparse code multiple access. Neurocomputing 2020, 382, 52–63. [Google Scholar] [CrossRef] [Green Version]
- Asghar, M.Z.; Abbas, M.; Zeeshan, K.; Kotilainen, P.; Hämäläinen, T. Assessment of deep learning methodology for self-organizing 5g networks. Appl. Sci. 2019, 9, 2975. [Google Scholar] [CrossRef] [Green Version]
- Zorzi, M.; Zanella, A.; Testolin, A.; Grazia, M.D.F.D.; Zorzi, M. Cognition-based networks: A new perspective on network optimization using learning and distributed intelligence. IEEE Access 2015, 3, 1512–1530. [Google Scholar] [CrossRef]
- Mo, J.; Ng, B.L.; Chang, S.; Huang, P.; Kulkarni, M.N.; AlAmmouri, A.; Zhang, J.; Lee, J.; Choi, W.-J. Beam codebook design for 5G mmWave terminals. IEEE Access 2019, 7, 98387–98404. [Google Scholar] [CrossRef]
- Wang, H.; Wu, Y.; Min, G.; Xu, J.; Tang, P. Data-driven dynamic resource scheduling for network slicing: A deep reinforcement learning approach. Inf. Sci. 2019, 498, 106–116. [Google Scholar] [CrossRef]
- Strodthoff, N.; Göktepe, B.; Schierl, T.; Hellge, C.; Samek, W. Enhanced machine learning techniques for early HARQ feedback prediction in 5G. IEEE J. Sel. Areas Commun. 2019, 37, 2573–2587. [Google Scholar] [CrossRef] [Green Version]
- Huang, J.; Wang, C.-X.; Bai, L.; Sun, J.; Yang, Y.; Li, J.; Tirkkonen, O.; Zhou, M. A big data enabled channel model for 5G wireless communication systems. IEEE Trans. Big Data 2018, 6, 211–222. [Google Scholar] [CrossRef] [Green Version]
- Ha, C.-B.; You, Y.-H.; Song, H.-K. Machine learning model for adaptive modulation of multi-stream in MIMO-OFDM system. IEEE Access 2018, 7, 5141–5152. [Google Scholar] [CrossRef]
- Thrane, J.; Zibar, D.; Christiansen, H.L. Model-aided deep learning method for path loss prediction in mobile communication systems at 2.6 GHz. IEEE Access 2020, 8, 7925–7936. [Google Scholar] [CrossRef]
- Cho, Y.-J.; Kim, Y.-S.; Kim, S.; Sim, D.; Kwak, D.; Lee, J. AI-Enabled Wireless KPI Monitoring and DiagnosisSystem for 5G Cellular Networks. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 16–18 October 2019; pp. 899–901. [Google Scholar]
- Subramanya, T.; Harutyunyan, D.; Riggio, R. Machine learning-driven service function chain placement and scaling in MEC-enabled 5G networks. Comput. Netw. 2020, 166, 106980. [Google Scholar] [CrossRef]
- AbdelMoniem, M.; Gasser, S.M.; El-Mahallawy, M.S.; Fakhr, M.W.; Soliman, A. Enhanced NOMA system using adaptive coding and modulation based on LSTM neural network channel estimation. Appl. Sci. 2019, 9, 3022. [Google Scholar] [CrossRef] [Green Version]
- Cao, J.; Liu, X.; Dong, W.; Peng, T.; Duan, R.; Yuan, Y.; Wang, W. A neural network based conflict-graph construction approach for ultra-dense networks. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Huang, C.-W.; Chiang, C.-T.; Li, Q. A study of deep learning networks on mobile traffic forecasting. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–6. [Google Scholar]
- Hussain, B.; Du, Q.; Ren, P. Deep learning-based big data-assisted anomaly detection in cellular networks. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Le, L.-V.; Sinh, D.; Tung, L.-P.; Lin, B.-S.P. A practical model for traffic forecasting based on big data, machine-learning, and network KPIs. In Proceedings of the 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–4. [Google Scholar]
- Nurminen, J.K.; Mfula, H. A unified framework for 5G network management tools. In Proceedings of the 2018 IEEE 11th Conference on Service-Oriented Computing and Applications (SOCA), Paris, France, 20–22 November 2018; pp. 41–48. [Google Scholar]
- Chiu, P.; Reunanen, J.; Luostari, R.; Holma, H. Big Data Analytics for 4.9 G and 5G Mobile Network Optimization. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, NSW, Australia, 4–7 June 2017; pp. 1–4. [Google Scholar]
- Tung, L.-P.; Lin, B.-S.P. Big data and machine learning driven handover management and forecasting. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 4–7 June 2017; pp. 214–219. [Google Scholar]
- Baştuğ, E.; Bennis, M.; Zeydan, E.; Kader, M.A.; Karatepe, I.A.; Er, A.S.; Debbah, M. Big data meets telcos: A proactive caching perspective. J. Commun. Netw. 2015, 17, 549–557. [Google Scholar] [CrossRef] [Green Version]
- Keshavamurthy, B.; Ashraf, M. Conceptual design of proactive SONs based on the big data framework for 5G cellular networks: A novel machine learning perspective facilitating a shift in the son paradigm. In Proceedings of the 2016 International Conference System Modeling & Advancement in Research Trends (SMART), Moradabad, India, 25–27 November 2016; pp. 298–304. [Google Scholar]
- Kader, M.A.; Bastug, E.; Bennis, M.; Zeydan, E.; Karatepe, A.; Er, A.S.; Debbah, M. Leveraging big data analytics for cache-enabled wireless networks. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6-10 December 2015; pp. 1–6. [Google Scholar]
- López-Pires, F.; Barán, B. Machine learning opportunities in cloud computing data center management for 5G services. In Proceedings of the 2018 ITU Kaleidoscope: Machine Learning for a 5G Future (ITU K), Santa Fe, Argentina, 26–28 November 2018; pp. 1–6. [Google Scholar]
- Le, L.-V.; Lin, B.-S.P.; Tung, L.-P.; Sinh, D. SDN/NFV, machine learning, and big data driven network slicing for 5G. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Silicon Valley, CA, USA, 9–11 July 2018; pp. 20–25. [Google Scholar]
- Le, L.-V.; Sinh, D.; Lin, B.-S.P.; Tung, L.-P. Applying big data, machine learning, and SDN/NFV to 5G traffic clustering, forecasting, and management. In Proceedings of the 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), Montreal, QC, Canada, 25–29 June 2018; pp. 168–176. [Google Scholar]
- Paul, U.; Liu, J.; Troia, S.; Falowo, O.; Maier, G. Traffic-profile and machine learning based regional data center design and operation for 5G network. J. Commun. Netw. 2019, 21, 569–583. [Google Scholar] [CrossRef]
- Maimó, L.F.; Gómez, Á.L.P.; Clemente, F.J.G.; Pérez, M.G.; Pérez, G.M. A self-adaptive deep learning-based system for anomaly detection in 5G networks. IEEE Access 2018, 6, 7700–7712. [Google Scholar] [CrossRef]
- Zhao, G.; Yang, H.; Yu, A.; Zhu, Y.; Li, K.; Zhang, J. Leveraging Deep Learning to Predict Cyberattack with Traffic Whitelist for Optical Fronthaul Networks in 5G and Beyond. In Proceedings of the Asia Communications and Photonics Conference, Chengdu, China, 2–5 November 2019; p. S3C.5. [Google Scholar]
- Munisankaraiah, S.; Kumar, A.A. Physical layer security in 5G wireless networks for data protection. In Proceedings of the 2016 2nd International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 14–16 October 2016; pp. 883–887. [Google Scholar]
- Covaci, S.; Repetto, M.; Risso, F. Towards Autonomous Security Assurance in 5G Infrastructures. IEICE Trans. Commun. 2018. [Google Scholar] [CrossRef]
- Ravi, N.; Rani, P.V.; Shalinie, S.M. Secure Deep Neural (SeDeN) Framework for 5G Wireless Networks. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; pp. 1–6. [Google Scholar]
- Sim, M.S.; Lim, Y.-G.; Park, S.H.; Dai, L.; Chae, C.-B. Deep learning-based mmWave beam selection for 5G NR/6G with sub-6 GHz channel information: Algorithms and prototype validation. IEEE Access 2020, 8, 51634–51646. [Google Scholar] [CrossRef]
- Lauridsen, M.; Mogensen, P.; Sorensen, T.B. Estimation of a 10 gb/s 5G receiver’s performance and power evolution towards 2030. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference (VTC2015-Fall), Boston, MA, USA, 6–9 September 2015; pp. 1–5. [Google Scholar]
- Zong, B.; Fan, C.; Wang, X.; Duan, X.; Wang, B.; Wang, J. 6G technologies: Key drivers, core requirements, system architectures, and enabling technologies. IEEE Veh. Technol. Mag. 2019, 14, 18–27. [Google Scholar] [CrossRef]
- Elmeadawy, S.; Shubair, R.M. Enabling technologies for 6G future wireless communications: Opportunities and challenges. arXiv 2020, arXiv:2002.06068. [Google Scholar]
- Lu, Y.; Zheng, X. 6G: A survey on technologies, scenarios, challenges, and the related issues. J. Ind. Inf. Integr. 2020, 19, 100158. [Google Scholar] [CrossRef]
- Xu, X.; Li, D.; Dai, Z.; Li, S.; Chen, X. A heuristic offloading method for deep learning edge services in 5G networks. IEEE Access 2019, 7, 67734–67744. [Google Scholar] [CrossRef]
- Qian, B.; Zhou, H.; Ma, T.; Yu, K.; Yu, Q.; Shen, X. Multi-Operator Spectrum Sharing for Massive IoT Coexisting in 5G/B5G Wireless Networks. IEEE J. Sel. Areas Commun. 2020. [Google Scholar] [CrossRef]
- Liu, B.; Liu, C.; Peng, M. Resource allocation for energy-efficient MEC in NOMA-enabled massive IoT networks. IEEE J. Sel. Areas Commun. 2020. [Google Scholar] [CrossRef]
- Jiang, N.; Deng, Y.; Nallanathan, A.; Kang, X.; Quek, T.Q. Analyzing random access collisions in massive IoT networks. IEEE Trans. Wirel. Commun. 2018, 17, 6853–6870. [Google Scholar] [CrossRef] [Green Version]
- Kim, T.; Jung, B.C. Performance analysis of grant-free multiple access for supporting sporadic traffic in massive IoT networks. IEEE Access 2019, 7, 166648–166656. [Google Scholar] [CrossRef]
- Qi, Q.; Chen, X.; Ng, D.W.K. Robust beamforming for NOMA-based cellular massive IoT with SWIPT. IEEE Trans. Signal Process. 2019, 68, 211–224. [Google Scholar] [CrossRef]
- Alsharif, M.H.; Kim, J.; Kim, J.H. Green and sustainable cellular base stations: An overview and future research directions. Energies 2017, 10, 587. [Google Scholar] [CrossRef]
- Memon, M.L.; Saxena, N.; Roy, A.; Shin, D.R. Backscatter communications: Inception of the battery-free era—A comprehensive survey. Electronics 2019, 8, 129. [Google Scholar] [CrossRef] [Green Version]
- Huang, C.; Hu, S.; Alexandropoulos, G.C.; Zappone, A.; Yuen, C.; Zhang, R.; Renzo, M.D.; Debbah, M. Holographic MIMO surfaces for 6G wireless networks: Opportunities, challenges, and trends. IEEE Wirel. Commun. 2020, 27, 118–125. [Google Scholar] [CrossRef]
- Liu, Q.; Wu, J.; Xia, P.; Zhao, S.; Chen, W.; Yang, Y.; Hanzo, L. Charging unplugged: Will distributed laser charging for mobile wireless power transfer work? IEEE Veh. Technol. Mag. 2016, 11, 36–45. [Google Scholar] [CrossRef]
- Huynh, N.V.; Hoang, D.T.; Lu, X.; Niyato, D.; Wang, P.; Kim, D.I. Ambient backscatter communications: A contemporary survey. IEEE Commun. Surv. Tutor. 2018, 20, 2889–2922. [Google Scholar] [CrossRef] [Green Version]
- Gentry, C. Computing arbitrary functions of encrypted data. Commun. ACM 2010, 53, 97–105. [Google Scholar] [CrossRef] [Green Version]
- Ferraro, P.; King, C.; Shorten, R. Distributed ledger technology for smart cities, the sharing economy, and social compliance. IEEE Access 2018, 6, 62728–62746. [Google Scholar] [CrossRef]
- Silver, D.; Schrittwieser, J.; Simonyan, K.; Antonoglou, I.; Huang, A.; Guez, A.; Hubert, T.; Baker, L.; Lai, M.; Bolton, A.; et al. Mastering the game of go without human knowledge. Nature 2017, 550, 354–359. [Google Scholar] [CrossRef] [PubMed]
- Letaief, K.B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.-J.A. The roadmap to 6G: AI empowered wireless networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef] [Green Version]
- David, K.; Berndt, H. 6G vision and requirements: Is there any need for beyond 5G? IEEE Veh. Technol. Mag. 2018, 13, 72–80. [Google Scholar] [CrossRef]
- Li, R. Towards a new internet for the year 2030 and beyond. In Proceedings of the 3rd Annu. ITU IMT-2020/5G Workshop Demo Day, Geneva, Switzerland, 18 July 2018; pp. 1–21. [Google Scholar]
- Berardinelli, G.; Mahmood, N.H.; Rodriguez, I.; Mogensen, P. Beyond 5G wireless IRT for industry 4.0: Design principles and spectrum aspects. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Botsinis, P.; Alanis, D.; Babar, Z.; Nguyen, H.V.; Chandra, D.; Ng, S.X.; Hanzo, L. Quantum search algorithms for wireless communications. IEEE Commun. Surv. Tutor. 2018, 21, 1209–1242. [Google Scholar] [CrossRef] [Green Version]
- Akan, O.B.; Ramezani, H.; Khan, T.; Abbasi, N.A.; Kuscu, M. Fundamentals of molecular information and communication science. Proc. IEEE 2016, 105, 306–318. [Google Scholar] [CrossRef] [Green Version]
- Katz, M.; Matinmikko-Blue, M.; Latva-Aho, M. 6Genesis flagship program: Building the bridges towards 6G-enabled wireless smart society and ecosystem. In Proceedings of the 2018 IEEE 10th Latin-American Conference on Communications (LATINCOM), Guadalajara, Mexico, 14–16 November 2018; pp. 1–9. [Google Scholar]
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Hawilo, H.; Shami, A.; Mirahmadi, M.; Asal, R. NFV: State of the art, challenges, and implementation in next generation mobile networks (vEPC). IEEE Netw. 2014, 28, 18–26. [Google Scholar] [CrossRef] [Green Version]
- Miyazawa, M.; Hayashi, M.; Stadler, R. vNMF: Distributed fault detection using clustering approach for network function virtualization. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 640–645. [Google Scholar]
- Bolla, R.; Lombardo, C.; Bruschi, R.; Mangialardi, S. DROPv2: Energy efficiency through network function virtualization. IEEE Netw. 2014, 28, 26–32. [Google Scholar] [CrossRef] [Green Version]
- Quittek, J.; Bauskar, P.; BenMeriem, T.; Bennett, A.; Besson, M. Network functions virtualisation (nfv)-management and orchestration. In ETSI NFV ISG; White Paper; European Telecommunications Standards Institute: Sophia Antipolis, France, 2014; pp. 733–8716. [Google Scholar]
- Mahdi, M.N.; Mohamed, K.S.; Ahmad, A.R.; Subhi, M.A. The Vision of 5G and Cell-Free Communication Networks in Malaysia. In Proceedings of the 2020 8th International Conference on Information Technology and Multimedia (ICIMU), Selangor, Malaysia, 24–26 August 2020; pp. 156–161. [Google Scholar]
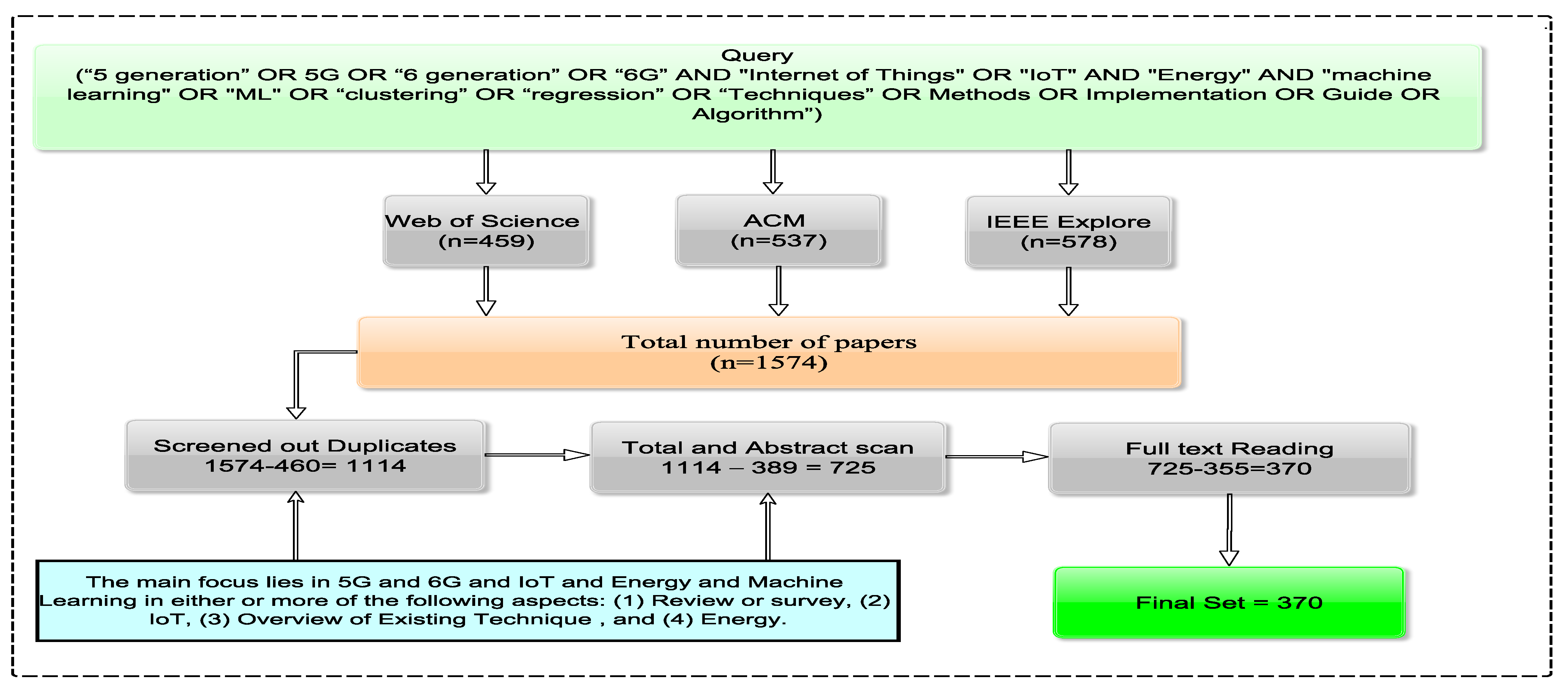



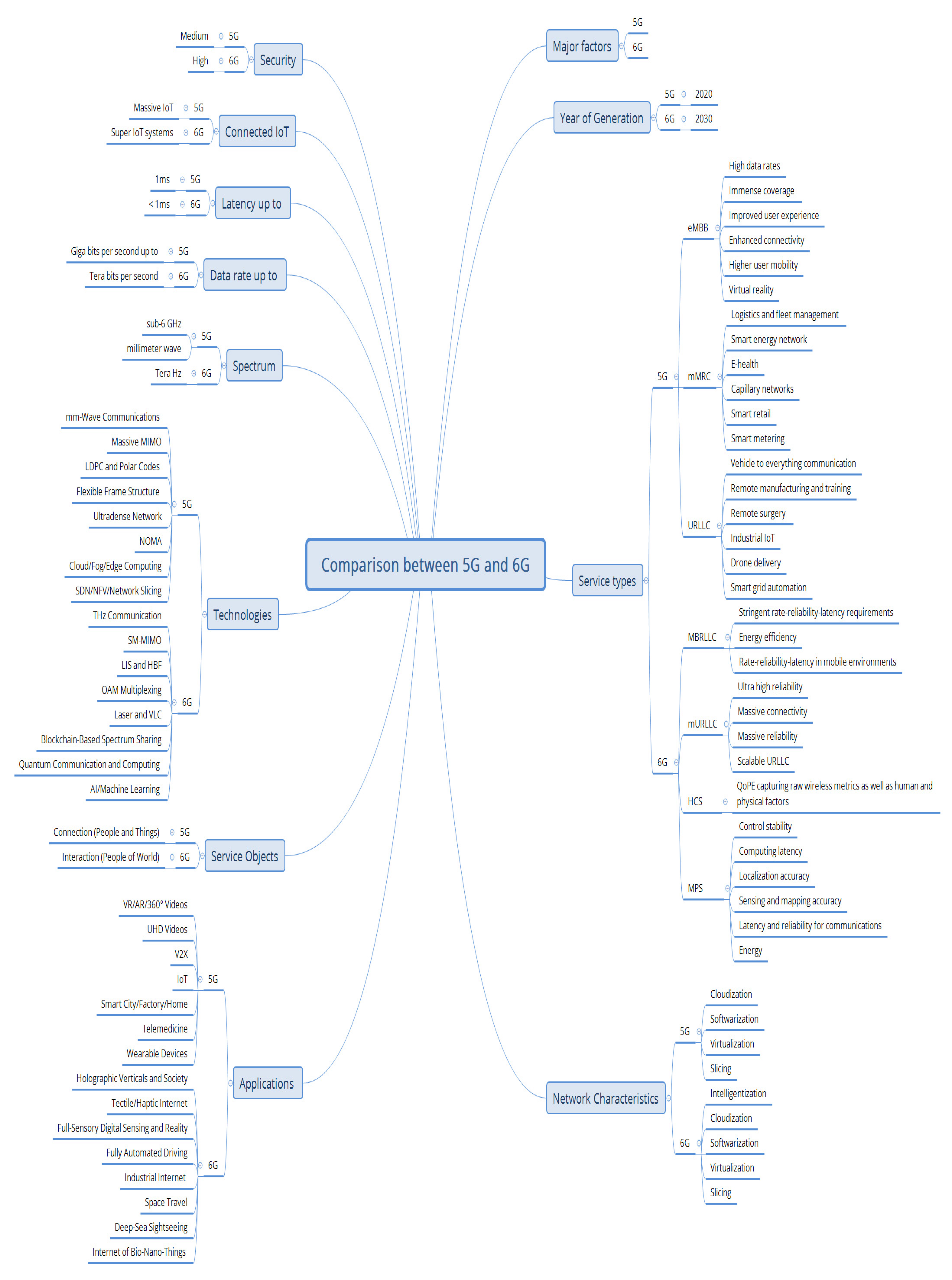



| Ref. | Summary | Machine Leaning | IoT | Security Approaches | VR & AR | Energy | Network Architectures | |
|---|---|---|---|---|---|---|---|---|
| Deep Learning | Other ML Methods | |||||||
| [5] | Made it more robust against various attacks. | ✓ | ✓ | |||||
| [6] | Workload-based EDoS and Instantiation-based. | ✓ | ✓ | |||||
| [7] | Threats and sketches to mitigate the security concerns. | ✓ | ✓ | ✓ | ||||
| [15] | Virtualization explicitly designed for IoT networks. | ✓ | ✓ | ✓ | ✓ | |||
| [16] | 5G and Real-Time Communications. | ✓ | ✓ | ✓ | ✓ | |||
| [17] | Various virtual and AR for the world first 5G. | ✓ | ✓ | |||||
| [18] | Fault management techniques. | ✓ | ✓ | ✓ | ||||
| [19] | Basic concepts of SON. | ✓ | ✓ | ✓ | ||||
| [20] | Self-organizing networks solutions. | ✓ | ✓ | ✓ | ✓ | |||
| [21] | Application areas of AI/ML in SDN and NFV based networks. | ✓ | ✓ | ✓ | ||||
| [22] | Use cases and scenarios of 5G in which ML. | ✓ | ✓ | ✓ | ✓ | |||
| [23] | Challenges from these 5G features and present several technological. | ✓ | ✓ | ✓ | ||||
| [24] | DRL to address the RA problems. | ✓ | ✓ | ✓ | ||||
| [25] | DRL based resource management schemes for 5G HetNets. | A | ✓ | ✓ | ||||
| [26] | Big data analytics solution for 5G network. | ✓ | ✓ | |||||
| [27] | ML to assist channel modelling and estimation has been introduced. | ✓ | ✓ | ✓ | ||||
| [28] | AI and ML for 5G network. | ✓ | ✓ | ✓ | ||||
| [29] | 5G network management, which takes an end-to-end view of the network. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [30] | Improve the efficiency, latency, and reliability of the current and real-time network applications. | ✓ | ✓ | ✓ | ||||
| [31] | QoS for Users in 5G. | ✓ | ✓ | ✓ | ||||
| [32] | Capabilities of DL systems to explain to network operators are described below. | ✓ | ✓ | ✓ | ||||
| [33] | Capabilities of DL systems to explain and justify their suggestions to network operators. | ✓ | ✓ | ✓ | ✓ | |||
| [34] | Slice Network. | ✓ | ✓ | ✓ | ||||
| [35] | Detection principles that are optimal or near-optimal for huge MIMO systems. | ✓ | ✓ | ✓ | ✓ | |||
| [37] | Outlined the current 5G testbed in Prato. | ✓ | ✓ | ✓ | ✓ | |||
| [38] | Effectively integrating SDN/NFV. | ✓ | ✓ | |||||
| [39] | AI for 5G wireless communication systems. | A | ✓ | ✓ | ✓ | ✓ | ||
| [40] | ML in conjunction with proximity to real-time information technology solutions. | ✓ | ✓ | ✓ | ✓ | |||
| [41] | Investigates the potential features of B5G. | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| [42] | Mobile and wireless networking research based on DL. | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| [52] | To enhance the productivity of the system and to avoid the delays. | ✓ | ✓ | ✓ | ✓ | |||
| [53] | Inductive analysis of the technology required for driverless driving and 5G technology. | ✓ | ✓ | ✓ | ||||
| [54] | Explains FL ideas with an emphasis on their implementation in automotive networks. | ✓ | ✓ | ✓ | ✓ | |||
| [55] | Control may be delegated to clusters of IoT nodes beyond the edge gateway. | ✓ | ✓ | |||||
| [56] | Offered network is the foundation of the semantics of a technological level of egovernment. | ✓ | ✓ | ✓ | ✓ | |||
| [57] | IoT systems and services. | ✓ | ✓ | ✓ | ✓ | |||
| [58] | Financial related issues. | ✓ | ✓ | |||||
| [59] | View existing wireless IoT connectivity technologies can be effectively used to enable massive connectivity for IoT. | ✓ | ✓ | ✓ | ✓ | |||
| [60] | ML approaches to UAV-based communications has the potential to improve a variety of design aspects. | ✓ | ✓ | ✓ | ✓ | |||
| [61] | IoT devices are designed to transmit little data packets with good energy efficiency. | ✓ | ✓ | ✓ | ✓ | |||
| [62] | ITSs cyber-security, energy-efficient utilization of SGs, effective use of UAVs to assure the best services of 5G. | ✓ | ✓ | ✓ | ✓ | |||
| [63] | 5G technologies are listed and described how these features effect the industries of the future. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [64] | Investigate the 5G usability in disasters. | ✓ | ✓ | ✓ | ||||
| [65] | Construction of a semantic network comprising the most recent concepts in the information. | ✓ | ✓ | ✓ | ✓ | |||
| [67] | IoT technology is examined from a high-level perspective. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [68] | Application of a low-complexity Qlearning approach in the mMTC situation. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [71] | Energy efficiency of radio access, which is at the heart of wireless networks. | ✓ | ✓ | ✓ | ||||
| [73] | Big data and the promise of ML for optimization and decision-making in 5G networks. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [74] | Classified these three pillars, softwarization, energy harvesting, and optimization. | ✓ | ✓ | ✓ | ||||
| [8] | AI into 6G and state of the art in ML. | ✓ | ✓ | ✓ | ✓ | |||
| [9] | ML and privacy in 6G. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [10] | AI integrated into localization, UAV communication, surveillance, security and privacy preservation. | ✓ | ✓ | ✓ | ✓ | |||
| [12] | Addressing the shortcomings and limitations of IoT and Blockchain. | ✓ | ✓ | ✓ | ✓ | |||
| [13] | Dimensions of a 6G network, including the air interface. | ✓ | ✓ | ✓ | ✓ | |||
| [43] | Requirements and challenges of 6G. | ✓ | ✓ | ✓ | ✓ | |||
| [44] | Added features and key performance indicators of 5G NR. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [45] | Highlighting energy efficiency spectral efficiency security, secrecy, and privacy adorability and customization. | ✓ | ✓ | ✓ | ✓ | |||
| [46] | THz band antenna, fabrication and measurement are presented. | ✓ | ✓ | ✓ | ||||
| [47] | Blockchain-Envisioned UAV Communication. | ✓ | ✓ | ✓ | ✓ | |||
| [66] | 6G to IoT technologies and service areas. | A | ✓ | ✓ | ✓ | |||
| [75] | Vision and requirements of 6G. | ✓ | ✓ | ✓ | ✓ | |||
| [11] | Investigations security and privacy problems associated with 6G technologies. | ✓ | ✓ | ✓ | ✓ | |||
| [48] | Application of learning, prediction, and decision-making to manage the stream of humans. | ✓ | ✓ | ✓ | ✓ | |||
| [72] | Analyze hardware reuse and multiplexing solution to ease the design of UEs that are both cost-effective and energy-efficient. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [77] | Ability to triple the adaptivity of mmWave and THz. | ✓ | ✓ | ✓ | ✓ | |||
| [76] | Vision for machine type communication in 6G. | ✓ | ✓ | ✓ | ✓ | |||
| [69] | Vision for machine type communication in 6G. | ✓ | ✓ | ✓ | ✓ | |||
| [70] | ML, QC, and QML identify their potential benefits, issues in the B5G networks. | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [49] | 6G challenges, requirements, and trends. | ✓ | ✓ | ✓ | ✓ | |||
| [78] | Applying TL to future 6G communications. | ✓ | ✓ | ✓ | ✓ | |||
| [51] | Evolution of KPIs and technology trends towards 6G. | ✓ | ✓ | |||||
| [14] | Explore the role of blockchain to address formidable challenges in 6G. | ✓ | ✓ | ✓ | ✓ | |||
| [50] | Potential challenge and propose possible technical components in a future 6G system. | ✓ | ✓ | ✓ | ✓ | |||
| [36] | Deals with the answers to those questions for the health vertical of 6G. | ✓ | ✓ | ✓ | ✓ |
| Ref. | Technique | Core Term | Core Idea | Solution | Drawbacks |
|---|---|---|---|---|---|
| 1- | Network | Resource | Management | ||
| [79] | URLLC. | Functions needed for defining and automating 5G experiments. | E2E configuration of 5G testbeds is supervised throughout. | Framework deployment, control, management, monitoring, analytics, and security in 5G testbeds. | Vertical should select a test case from a list of test cases for a separate KPI. |
| [80] | OpenAirInterface. | Performance. | OAI is essential to the development of the key 5G technologies. | 3GPP-compliant LTE systems for real-time indoor/outdoor testing and demonstration. | Demands adaptable and realistic experimentation platforms that support a wide range of experimentation modalities. |
| [81] | STRAIGHT. | Mobility state estimation. | UE mobility which complies with UE historical information standards. | Compensate for varying mobility classes, both low and high. | Complex networks with overlapping cells of varied sizes. |
| [82] | D2D mode. | SINR proximity distance and battery consumption. | Dynamic network’s mode selection method. | Delivered a better outcome than conventional mode selection up to 30%. | Mode selection applied at the BS, and device-centric principles should be employed to accomplish 5G network goals. |
| [83] | CMAC. | Cooperative caching. | CMAC method to lower the average delay of providing material. | Attentively monitor QoE and content-access latency. | Various trace-driven simulations show that CMAC offers up to 13% less average content-access latency. |
| [84] | DICE. | Network protocol design. | The DICE ICN forwarding strategy. | Delivered up to 2X more successful delivery and incurs just a tenth of the network overhead. | To optimise the energy consumption of different wireless technologies. |
| [85] | Tactile Internet. | Network components. | Internet system using SDN in the core of the cellular network and MEC in multilevels. | Even though 1ms round-trip latency can be a challenge, Tactile Internet has proven to be a success. | To reduce the round-trip latency is to limit the number of network nodes engaged in the communication process. |
| [86] | Mobility Management. | Transport protocols. | Performance evaluation of TCP on mmWave cellular systems with mobility management. | Increasing network density can greatly enhance the performance of TCP with respect to both throughput and latency in mobile environments with blocking. | Expand the simulation and put it in the real world. Both create network topologies that lower the end-to-end latency of a connection and implement a performance-boosting proxy. |
| [87] | eTOM. | QoS. | Build a virtualized architecture for dynamic delivery of services, QoS, and increased resource performance. | All of these functionalities were implemented using modules within the OpenStack cloud manager. | To complete the OSR end-to-end process grouping and the automation and support for FAB framework functional blocks implementation. |
| [88] | Wireless Spectrum Management. | Network algorithms. | Cognitive cellular network-oriented wireless spectrum management technique, based on cognitive radio technology. | Before allocating resources, design a double pricing model that charges cognitive users lower fees. | A convenient mechanism, better suited to day-to-day scenarios. |
| [89] | Cyber-Physical Systems. | Network services. | OSM, a popular 5G management and orchestration platform was used to deploy virtual network functionalities. | Scenarios showing how 5G technologies might help the CPS sector. | Virtual services plus networking will be created by PNFs that can be made to the device quickly. |
| [90] | NR access technology. | QoS. | Numerology FDM Simulate FDM numerology in the ns-3 network simulator. | Followed the 3GPP specifications to configure the time/frequency resource units automatically. | Puncturing the resources already committed for eMBB and designating processes to identify so would be essential. |
| [91] | Integration of Carrier Aggregation. | Network simulations. | Implementation for the mmWave ns-3 multi-connectivity techniques for 3GPP New Radio. | DC-implementation illustrated, along with details on the integration with CA. | To research additional CC management policies, which could benefit from a PHY-MAC cross-layer with additional channel information used in resource allocation. |
| [92] | Mobile core. | Network Architecture | Distributed core network architecture for future cellular networks. | Architecture mitigates latency and performance issues in essential network control and data gateways. | Experimental results on orbit radio testbed latency and mobility. |
| [93] | NFV MANO. | NFV MANO. | Proposing a 5G platform-oriented solution amid alternative authentication and authorisation techniques. | Integrate procedures for authentication and authorisation to build a scalable and secure solution in a 5G platform. | Integrate well-known procedures for authentication and authorisation to build a scalable and secure solution in a 5G platform. |
| [94] | Multi Administrative Domain Networking. | Networking components. | Prototype based on various open source components showcasing blockchain DApp abilities. | Open-source software ecosystem promotes concepts while sparking conversation on difficult practical elements of multi-administrative. | Open conversations about speculative technology and ongoing research and development. |
| [95] | SoftH. | Network mobility. | SoftH: an SDN-based handover decision criterion model. | Mechanism seeks to let the cell transfer decisions assert their position at the SDN controller | Decisions are made dynamic according to the changing conditions of the network. |
| [96] | DIY model | Mobile networks. | Constructing mobile networks in places where prior community cellular networks were focused on low end service provisioning. | 5G to spread to more rural and non-urban areas by empowering small-scale local operators and communities to create and run contemporary networks. | Subscriber base can have recurring costs under $1 USD per month. |
| [97] | C-RAN. | Network resources allocation. | Energy-efficient joint workload scheduling and BBU allocation algorithm, utilising queueing theory. | C-RAN controller distributes workload allocation among BBU servers in a time slot basis. | For restricted power and cost budgets, the scheduling strategy is suitable. |
| [98] | AirSea. | Robotics. | Clever manufacturing facility in the sea. | Sea-based, land-based, air-based, and space-based linkages are incorporated into the design of an air and sea manta ray robot. | Seaplane, WIG effect, and manta ray robots will significantly benefit ocean engineering and resource and energy development. |
| [99] | Throughput 5G. | Wireless access networks. | Offered a 5G multi-cell ns-3 simulation framework. | 5G trace dataset, and a large-scale multi-cell 5G/mmwave simulation framework. | Incorporate mmwave and sub-6GHz as shown in actual-world next-generation 5G networks. |
| [100] | Augmenting QoS. | QoS. | V3I Cloud SDK toolchains support creating complex automated cloud. | Executed an experimental system in which automobiles formed a cloud resource unit. | Under investigation and outcomes. |
| [101] | MEC in the Cloud-RAN. | Core Network. | Situation where disaggregated base stations capable of provisioning MEC capabilities in per-packet. | Developed a signalling for communication between DUs and a MEC agent, which has access to container-based services. | Test how service replication via edge nodes serves different base stations’ technology mix. |
| [102] | OpenAirInterface. | Cloud-RAN. | Modular SDN/NFV-based SON testbed for future 5G mobile networks. | A CDSA-based testbed is required to enable examination of the NG-SON capabilities for practical implementations. | |
| [103] | Network function virtualization. | Intent–based networking. | Pondered an Intent-based approach to mobile backhauling for 5G networks. | Backhaul interface based on intent. Wireless controllers should have little contact with the wired backhaul controller. | Incorporate VNF migration, path restoration, and telemetry support for the Intent interface. |
| [104] | Network simulations. | Network performance analysis. | Investigated 5G mobile communication system performance, MAS with polarized antenna based BS system is applied. | Simulation results reveal that the misaligned polarisation causes more power loss for the polarised antenna structure. | As a result, system capacity increases when the polarised antenna arrangement is implemented. |
| [105] | DES. | Maintenance performance. | These principles were used to give real-world industrial 5G pilot deployment assessments. | Inputs will be used in the requirement definition for 5G networks, such as mission-critical clouds and analytics services, as well as other network services. | It is vital to use DES in tandem with establishing business justifications for investments. |
| [106] | FiWi. | FiWi access networks | Focus on very low latency and ultra-high reliability of 5G and study how they can be obtained in FiWi upgraded LTE-A HetNets. | DOFR’s proposed routing technique helped increase the aggregate FiWi enhanced LTE-A throughput substantially. | |
| [107] | 5G infrastructure emulator. | Service Deployment. | 5G infrastructure emulator capable of emulating a realistic 5G network on a small number of commercial-off-the-shelf servers via virtualization. | Proposed approach provides an emulator of 5G infrastructures, which can accurately replicate 5G infrastructure. | Emulation platform and empirical data reported in terms of 5G service rollout times on bare metals. |
| 2- | Security | Approaches | |||
| [108] | Mobility management system design. | Virtualized network. | Virtual to physical address encapsulation empowers mobility capabilities, and mobility is implemented through a flow table entry. | User and mobile node independence rendered changes in network availability undetectable to the user. | Better control of heterogeneity and service scalability are provided by service decoupling. |
| [109] | Data privacy. | Communication system security. | Discussed the reasons why IMSI catcher protection is not given in 3G or 4G networks. | These might become adversaries against identity and location privacy. | In both situations, it is the same security, but since it is for different networks, there are different reasons for offering the protection. |
| [110] | 5GReasoner. | Security models. | Control-plane protocol protocols spanning across various layers of the 5G protocol stack. | Behaviour-specific abstraction enables an automated analysis of 5G Reasoner. | To integrate additional critical control-layer protocols. |
| [111] | Bootstrapping in Cellular Networks. | Security and privacy. | Precomputation-based digital signature creation techniques and three-dimensional optimizations DPKI technique, protocol, and cryptographic scheme. | Examine cryptography-backed authentication mechanisms to prevent adversaries from enticing unsuspecting cellular devices to connect to malicious base stations. | To create a tailored cellular IoT scheme with 5G URLLC protocol. |
| [112] | Software-Defined Security. | Software-Defined Security. | Proposed to integrate security into the slice life cycle, effecting the administration and orchestration of the virtualization/softwarization architecture. | Security architecture is made up of built-in security features based on the ability to combine enforcement and monitoring operations within the software-defined network infrastructure. | The problem is in properly connecting network and computing resource control with network control. |
| [113] | Data Origin Authentication. | Trust. | Studied the security provided for group communication in 5G networks. | Two attack scenarios were created to highlight an opponent that gains illegitimate data access via a stated source of authenticity. | Deferred signing class might be used to conserve computing resources but increasing communication costs. |
| [114] | Security Event Management. | Security and privacy. | To deliver security monitoring and correlation capabilities to mobile network operators, infrastructure service providers, and tenants, verticals, and horizontal applications. | Ensured automatic security operations and security services management using 5G network automated SLA. | Find strategies to control security in network slices. concentrate on metrics to estimate deployment and configuration impact on performance needs. |
| [115] | Privacy | Network, architecture. | Presented a detailed analysis comparing the security of 5G wireless network systems to 4G cellular networks. | Proposing a study on a security sharing method for 5G | Security is not required, so saying that it is a disadvantage would not hinder the system in checking for it. |
| [116] | AKA protocol. | Security and privacy. | Models in the AKA family: 5G AKA. Extract 5G requirements from the 3GPP standards and discover missing security targets. | Utilize Tamarin to perform a complete security audit of the model with respect to the 5G security goals. | To see if AKA protocol versions such as 3G and 4G can deliver security benefits as compared to 5G AKA |
| [117] | 5G HetNets. | Security and privacy. | Designing a new handover authentication method for SDN aided 5G HetNets. | Proposed a mutual physical layer handover authentication system for 5G HetNets. | Weighing parameters differ in simulations. Additionally, an evaluation is conducted using different SNRs and weighting parameters to examine proposed authentication technique. |
| [118] | WireGuard. | Security and privacy. | Alternative to IPsec, WireGuard is proposed. Based on the analysis, the influence of security mechanisms on latency is insignificant. | Tested the eCPRI transportation in-depth. Even though overhead from security protocols has minor impact on latency, it is important to keep reduced latency in mind. | Interesting to use hardware to minimise the latency of 5G fronthaul. 5G can be maintained without compromising security by using a Quantum-secure version of MACsec, IPsec, and WireGuard. |
| 3- | Augmented | Reality | |||
| [119] | Mobility management system design. | Virtualized network. | Virtual to physical address encapsulation empowers mobility capabilities, and mobility is implemented through a flow table entry. | User and mobile node independence rendered changes in network availability undetectable to the user. | Better control of heterogeneity and service scalability are provided by service decoupling. |
| [120] | 5G VR/AR. | Human-centered computing. | An effective representation method for constructing the 360 films is needed in order to avoid sending a huge 360. | Ascertaining huge operational efficiency improvements over state-of-the-art caching and 360◦ video representation techniques is extraordinarily promising. | |
| [121] | AR application. | Network architectures. | Investigate both dynamic and hybrid profiling, as well as adaptive partitioning, to address a demanding augmented reality scenario. | The key role of edge computing in the effective deployment of AR apps. | |
| [122] | VR and AR. | Mobile networks. | The usage of multi-path, multi-tier 360° video streaming solutions are created to deal with both bandwidth and viewer motion. | Multimodal 360° video streaming solutions for 5G wireless networks. Use a 5G network to its full capacity and deal with bandwidth volatility. | Real-world traces of the 5G wireless network and user FoV analysis can be utilised to direct the design of future 360° video streaming systems in 5G networks. |
| [123] | AR and VR. | Network services. | 5G virtualized architecture focused on a network function which might relieve bandwidth constraints of immersive application scenarios. | Potential feature that might be used to relieve network resource utilisation. | The datasets were actual, with tag information focused on the needs of users. |
| 4- | Network | Scaling | |||
| [124] | Orion. | RAN slicing. | a RAN slicing technology that enables the dynamic on-the-fly virtualization of base stations, as well as the customisation of slices to match their particular service needs, was unveiled. | A low-powered yet flexible RAN virtualization tool for LTE was built as a proof of concept. | Orion is built for single-RAT setups but might be expanded to handle multi-RAT situations. |
| [125] | Slice Allocation. | Network resource Allocation. | Solves an actual problem by combining several infrastructure providers. | A slice allocation mechanism proposed based on matching game theory. | Dynamic pricing and power levels on a slice. |
| [126] | SuperFlex. | Network architectures. | SuperFlex, a network slicing architecture that delivers tailor-made treatment for subscribers without increasing capital and operating expenses. | A pluggable multidomain, dual-layered slicing based efficient, scalable, and extensible 5G wireless network architecture providing universal connectivity in a sliced environment. | Concentrate on efficient chaining across multiple slices while enforcing rigorous latency constraints. |
| [127] | Multi-service 5G Network. | Network management. | Described implementation experiences when deploying a small-scale multi-service network prototype, used to demonstrate some selected advanced features of 5G Networking. | Two heterogeneous services over two independent slices, namely, video streaming and AR, showcasing key features such as multi-slice orchestration RAN slicing and support for local breakout. | Software is based on open source components, and most of it is also released as open-source on public repositories. |
| [128] | NSRA. | Heterogeneous Network. | A cache-enabled content delivery system for the 5G heterogeneous network uses base stations and the macro cell as connected servers to host caches. | 5G heterogeneous system model method minimise the absolute gap between the data rate necessary and the rate obtained for all users in the system. | Future studies will incorporate densely-populated urban network simulations with higher-order MIMO. |
| [129] | IMAKE-GA. | Security and privacy. | Proposed an implicit mutual authentication and key exchange with group anonymity via proxy re-encryption on elliptic curve. | IMAKE-GA protocol secures distributed, the secure association between network slice NSC pairs. It employs proxy re-encryption utilising bilinear pairing on an elliptic curve. | |
| [130] | SLAs. | KPIs. | A solution that introduces a preemption mechanism to cut low-latency traffic while addressing the issue of flexible traffic that necessitates a higher throughput is provided. | The suggested solution’s primary acting element is PASS, an inter-slice scheduler that supplies services to each traffic type based on SLA demands. | The next step is to integrate this method with grant-less uplink transmission schemes, as the scheduler has outdated views of the UE uplink. |
| [131] | URRLC. | Architecting RAN Slicing. | This study outlines certain crucial architecture design parameters, system components, and interactions that enable RAN slicing for URLLC. | High-level architecture to tackle the URLLC and network slicing problems via a MEC system, focusing on design criteria, system components, and basic interactions. | These crucial outstanding issues set the path for future research initiatives in this direction. |
| [132] | Agile and flexible service platforms. | Mobile networks. | TPresented Mosaic5G, a community-led consortium for sharing platforms, featuring the software components FlexRAN, LL-MEC, and JOX on top of OpenAirInterface platform. | Mosaic5G, a community-led partnership for platform sharing. It offers the software components FlexRAN, LL-MEC, JOX, and Store, all of which are designed to help produce an open-source 5G research environment. | |
| [133] | End-to-end NFV. | Noisy Neighbor. | Proposed an approach that reduces noise by applying dynamic CPU pinning coupled with load balancing dependent on dynamic network slicing. | TDemonstrated an end-to-end framework for noisy neighbour situations, regardless of NFV deployment model. | Must employ tools that imitate the actual world infrastructure to gauge the framework’s effect. |
| 5- | Resource | Allocation | |||
| [134] | System Throughput Maximization. | Resource allocation. | Study the topic of underutilised 5G heterogeneous network spectrum resources. | Perform offloading in a multi-channel context. So, in order to optimise total system throughput, a solution is devised that incorporates power regulation and interference. | |
| [135] | Network resources allocation. | SLAs. | Aimed to reduce energy consumption in the network by simultaneously solving the user association and backhaul routing problems. | A possible solution is point-to-point networks with enormous bandwidth available in the mmWave frequency spectrum. | Work on a case when both base stations and backhaul lines are disabled to obtain even more energy savings. |
| [136] | QoS. | Network resources allocation. | To assign resources to the uplink transmitters will result in increased spectral efficiency and maximum data rate for all users. | Modeled heterogeneous multi-tier networks with the concept of stable matching. | The proposed technique can be expanded to the forthcoming 5G cellular networks. |
| [137] | SOGMS. | Network performance analysis. | Applications have an impact on the exponential growth of multimedia services in mobile networks. | SOGMS approach is offered for multimedia services, focusing on efficient utilisation, system capacity, and sustainability requirements. | Future 5G networks should look to put in place proactive edging caching with video popularity to help with the users’ QoE during video delivery. |
| 6- | Smart | Grid | |||
| [138] | Future Smart Grid. | Smart grid. | Loss of ARPU in emerging countries in the context of 4G LTE and 5G networks are analysed. | More equipment and software applications will be required on the grid, including as sensors, faster processors, and stronger algorithms, in order to achieve greater efficiency and dependability in the distribution system. | Issues around standardisation, interoperability, security, and of course, cost are among the growing 5G’s priorities, but the long-term rewards are enticing. |
| [139] | SimCT. | Computing methodologies. | Designed a tool to test the spatial resiliency of 5G networks. | Demonstrated how urban growth impacts 5G network coverage and quality of service. | Need to simulate seasonal effects like vegetation, rain, and snow. It incorporates data on travel patterns and simulations of city expansion. |
| Core Idea | Limitations | Ref. | |
|---|---|---|---|
| 1- | Network Resource Management | ||
| Framework | Dynamic network’s mode selection method. Also Distributed core network architecture for future cellular networks. | Framework deployment, control, management, monitoring, analytics, and security in 5G test beds. Also provides an emulator of 5G infrastructures, which can accurately replicate5G infrastructure. | [79,82,92,95,96,99,103,106,107] |
| Performance | Build a virtualized architecture for dynamic delivery of services, QoS, and increased resource performance. Also, Proposing a 5G platform-oriented solution amid alternative authentication and authorisation techniques. | All of these functionalities were implemented using modules within the OpenStack cloud manager. | [80,81,83,87,89,90,93,97,98,100,104] |
| Network components | Internet system using SDN in the core of the cellular network and MEC in multilevels. Cognitive cellular network-oriented wireless spectrum management technique, based on cognitive radio technology. | Delivered up to 2X more successful delivery and incurs just a tenth of the network overhead. Open-source software ecosystem promotes concepts while sparking conversation on difficult practical elements of multi-administrative. | [84,85,86,88,91,94,101,102,105] |
| 2- | Security Approaches | ||
| Framework | To integrate security into the slice life cycle, effecting the administration and orchestration of the virtualization/softwarization architecture. | Security architecture is made up of built-in security features based on the ability to combine enforcement and monitoring operations within the software-defined network infrastructure. | [110,112,114,115] |
| Performance | Precomputation-based digital signature creation techniques and three-dimensional optimizations DPKI technique, protocol, and cryptographic scheme. | Examine cryptography-backed authentication mechanisms to prevent adversaries from enticing unsuspecting cellular devices to connect to malicious base stations. | [111,118] |
| Network components | Virtual to physical address encapsulation empowers mobility capabilities, and mobility is implemented through a flow table entry. | User and mobile node independence rendered changes in network availability undetectable to the user. | [108,109,113,116,117] |
| 3- | Augmented Reality | ||
| Framework | 5G virtualized architecture focused on a network function which might relieve bandwidth constraints of immersive application scenarios. | Potential feature that might be used to relieve network resource utilisation. | [119,121,123] |
| Performance | The usage of multi-path, multi-tier 360° video streaming solutions are created to deal with both bandwidth and viewer motion. | Multimodal 360° video streaming solutions for 5G wireless networks. Use a 5G network to its full capacity and deal with bandwidth volatility. | [122] |
| Network components | An effective representation method for constructing the 360 films is needed in order to avoid sending a huge 360. | Ascertaining huge operational efficiency improvements over state-of-the-art caching and 360◦ video representation techniques is extraordinarily promising. | [120] |
| 4- | Network Scaling | ||
| Framework | 5G Solves an actual problem by combining several infrastructure providers. | A slice allocation mechanism proposed based on matching game theory. | [125,126,128,132,133] |
| Performance | RAN slicing technology that enables the dynamic on-the-fly virtualization of base stations, as well as the customisation of slices to match their particular service needs, was unveiled. | A low-powered yet flexible RAN virtualization tool for LTE was built as a proof of concept. | [124,129] |
| Network components | Described implementation experiences when deploying a small-scale multi-service network prototype, used to demonstrate some selected advanced features of 5G Networking. | Two heterogeneous services over two independent slices, namely, video streaming and AR, showcasing key features such as multi-slice orchestration RAN slicing and support for local breakout. | [127,130,131] |
| 5- | Resource Allocation | ||
| Framework | Study the topic of underutilised 5G heterogeneous network spectrum resources. | Perform offloading in a multi-channel context. So, in order to optimise total system throughput, a solution is devised that incorporates power regulation and interference. | [134] |
| Performance | To assign resources to the uplink transmitters will result in increased spectral efficiency and maximum data rate for all users. Modeled heterogeneous multi-tier networks with the concept of stable matching. | The proposed technique can be expanded to the forthcoming 5G cellular networks. | [136,137] |
| Network components | Applications have an impact on the exponential growth of multimedia services in mobile networks. | SOGMS approach is offered for multimedia services, focusing on efficient utilisation, system capacity, and sustainability requirements. | [135] |
| 6- | Smart Grid | ||
| Framework | Loss of ARPU in emerging countries in the context of 4G LTE and 5G networks are analysed. | More equipment and software applications will be required on the grid, including as sensors, faster processors, and stronger algorithms, in order to achieve greater efficiency and dependability in the distribution system. | [138] |
| Performance | Designed a tool to test the spatial resiliency of 5G networks. | Demonstrated how urban growth impacts 5G network coverage and quality of service. | [139] |
| Security and Privacy Issues | Key Technology Contribution | Ref. |
|---|---|---|
| 1- | THz | |
| Authentication | attacks that can exist in the 5G.then the security requirements in the 5G | [5,46,48,116,201,207,208] |
| Privacy | Describes these threats and sketches future research on how to mitigate the security concerns that a modern distributed control infrastructure poses. | [7,53,109,111,115] |
| Malicious behavior | Privacy and confidentiality issues. | [29,68,75,114] |
| 2- | AI | |
| Communication | vision of AI-enabled 6G system, the driving forces of introducing AI into 6G and the state of the art in machine learning. | [8,10,22,62,112,113,203,204] |
| Privacy | Secure ML structure, or the correct application of ML, can protect privacy in 6G. | [9,11,21,37,61] |
| Access control | Identify fascinating services and use-cases of 6G, which can not be supported by 5G appropriately.. | [49,60] |
| 3- | Quantum communication | |
| Communication | Highlight the use cases and applications of the proposed 6G networks in various dimensions. | [13,65,118,209] |
| 4- | Blockchain | |
| Communication | Challenges and canvassed the key role of blockchain. | [14,44,47,66] |
| 5- | Molecular communication | |
| Privacy | Preserving the privacy of the users is the primary concern of mobile and service providers. | [39,41,42,52,54,56,57,67,202] |
| Encryption | Several challenges pertaining to resource allocation, task offloading, energy efficiency, latency reduction, fairness and security based 6G enabled massive IoT. | [69,70] |
| Authentication | Securing 5G hetNets using mutual physical layer authentication | [117,200] |
| 6- | VLC | |
| Communication | Overview of the first five generations of wireless systems. | [43,45,63,64,198] |
| Malicious behavior | how to ensure seamless operability (including, but not limited to, authorization, security, service provisioning, accounting, etc.). | [76,108,206] |
| ML | 5G, 6G-Based Applications Energy and IoT |
|---|---|
| ANN | Their primary advantages have been identified, and the feasibility of their implementation in tackling the problem of accurate attack detection in m2m adhoc self-organizing networks has been assessed [239]. |
| DL | looked into the challenges involved in trying to blend MEC with C-RAN, specifically regarding cloud resources. energy-reduction [240,241]. |
| DL | Implemented a modern vehicle-internet infrastructure-aware ML architecture. It has made managing network slicing difficult in the context of 5G-enabled networks [242]. |
| DL | Has provided an APP-SON system which optimises 4G/5G network performance and user QoE. App-son offers a scalable big data platform for targeted optimization by evaluating cell application features in temporal space [243,244]. |
| DL | proposed to apply DL algorithm based on 5G-V2X for AI-based 5G base station allocation for platooning cars [245,246]. |
| RL | Found an E2E network slicing system that uses deep reinforcement learning to manage many resources to efficiently generate network slices [247,248,249]. |
| Bayesian | Bayesian learning was used to identify the broadcast signals for LA-CDMA uplink access. Using the sparse signals, this proposed strategy leverages our ignorance about user activities. Furthermore, introduce Gaussian mixture model approach to calculate the transmitted signals [250]. |
| ML | Proposed an online learning detection approach for the NOMA uplink. Build an online adaptive filter in the sum space of linear and Gaussian reproducing kernel Hilbert spaces. So, this approach is robust to dynamic wireless networks that can degrade the efficacy of a nonlinear adaptive filter [251]. |
| ML | Proposed the first online learning method designed to aid beam selection in mmWave vehicular systems. in particular, see this as a multi-armed bandit problem. Next, developed a lightweight context-aware online learning algorithm, known as FML, with proven performance and assured convergence [252,253]. |
| ML | Investigated healthcare scenarios where communication is conducted at THz frequencies. Combined with an ML mechanism, THz communications protocols result in fewer signal route losses in the system [254,255,256]. |
| ML | The new algorithm that incorporated a change in the hidden layer of the RNN is known as GRUs. The RNN-GRU model is used for determining whether or not to enable the VC mode. Received signal strength measurements were utilised to train the RNN-GRU model [257,258]. |
| ML | Most notable similarities between the cloud-fog node architecture and the human brain-spinal cord-nerve network model involve the presence of fog nodes [259,260,261]. |
| RL | The user association problem is tackled with a reinforcement learning method that considers content placement profiles and frontal constraints [262,263,264]. |
| ML | Detected the mood of patients by implementing an intelligent real-sense camera system prototype. ML, an SVM, and the RealSense facial detection system can be utilised to track patient demeanour for pain monitoring [265]. |
| ML | Developed a lightweight context-aware online learning method called FML with performance and convergence guaranteed. Using coarse location information and aggregating the data, FML learns from and adapts to its environment. Furthermore, propose a standard-compliant protocol that utilises the existing cellular network architecture and the future 5G characteristics [266,267,268]. |
| ML | Focused on designing and detecting RA preamble for 6G IoT satellite-assisted 6G an energy-conscious course for big IoT devices [269]. The drone follows the shortest path across a connected graph. This path decides the visiting order of devices. According to system identification theory, and with the use of neural networks, the model is constructed based on the results [270,271]. |
| NN | FA neural network combined with system identification theory is used, and the model is created based on the gathered data [272]. |
| ML | Enriched standard HetNets with a user-centric ML dimension [273]. |
| ML | Core Idea | Limitations | Ref. |
|---|---|---|---|
| 1- | Networks Architectures | ||
| ANN | Ensure the accuracy and simplify channel estimate. | How to increase the algorithm’s accuracy, and hence its estimating performance. | [274] |
| ANN | Use SMDP for the decision-making. | N3AC scales to huge scenarios and is useful in real applications. | [275,276] |
| BL | Used for the forecast of throughput. Parameter estimation forecasts future test results. | Converts probability distributions into images and applies assumptions of conditional independence to decrease the computational load of probabilistic reasoning. | [277,278] |
| DL | Proposed a DNN-based AS/STSK MIMO system. | Only the simulation shows that NN. | [279] |
| DL | 5G-oriented architecture in which to analyse network traffic. | Only TensorFlow was tested, and an in-depth comparison of deep learning frameworks would be essential. | [280] |
| DL | Using ML methods to minimise link failure at handover. | It might enable cellular systems to escape threshold-based handover decisions and follow ML-based methods. | [281,282,283] |
| DL | Reduce network load and availability. | Need to include mimicking the created model in a real production environment once the 5G ecosystem is accessible for customers. | [284,285] |
| DL | Create realistic synthetic data by exploiting the GAN’s capacity to generate and separate data. | Proactive SON algorithms run by GAN generated synthetic CDRs. | [286,287] |
| DL | Semantic edge cache optimization for multimedia services in 5G, which online improves caching settings depending on user playing behaviour. | Sharing the cache resource across many BSs is essential for heterogeneous networks. | [288,289] |
| ML | Verification of quality of experience. | Add more diverse and difficult scenarios, like deployment, client movement, and dynamic video and client attributes. | [290,291] |
| ML | Distributing resources to high mobility users while utilising only their position estimates. | Training the ML unit of the proposed approach will help alleviate inaccurately position information availability-related performance loss. | [292] |
| ML | Consider the case of 5G network slicing, and elaborate on the design, construction, deployment, operation, control, and management of slices. | Extend this inquiry to examine representative ML strategies for autonomic allocation and adjustment of computing and network resources on the basis of service requirements. | [293,294] |
| ML | 5G challenges and the importance of a changed management paradigm for 5G. | Next steps include actions such as checking the proposed algorithms at scale on commercial networks to validate the idea of adaptive SDN route planning in context. | [295,296,297,298,299] |
| ML | MIMO mmWave-assisted downlink for multiple users and Massive MIMO beamforming. | Compared ML-based with CVX-based optimal RRM. | [300,301,302] |
| ML | It is possible to learn basic state representations, minimising the complexity of the fundamental network design requirements. | Comparative simulation results demonstrated the suggested decision framework in multi-agent settings. | [303,304] |
| ML | Used ML to construct a framework for 5G network orchestration. | ML approaches use Decision Maker building blocks using neural networks for optimization. | [305,306] |
| ML | Allocation of the slice is explored and solved using ML approaches. | Solve for scalability. | [307] |
| ML | Found features that alter NFP resiliency. Many of these features are design and engineering features, therefore are difficult to measure. | ML and blockchain can improve the resilience of aerial networks. | [308] |
| ML | Presented a comprehensive self-healing mechanism as an enabler for a truly holistic and resilient solution. | TL strategies will be researched in regards to self-healing, which focuses on applying corrective measures. | [309] |
| ML | Flow of thinking led to this assumption, which is then used to define the journey towards CAN and a functional design of a typical CAN system. | Concurrently design and assemble a comprehensive CAN-based architecture. | [310,311,312] |
| ML | Research approaches for SON functions for anomaly detection, load balancing, and capacity optimization. | Next-generation SON networks should be built using ML-based user-centric techniques in order to achieve a linked eco-system with enhanced user experience. | [313,314] |
| ML | Plotted the locations of the drone-BSs and calculated the frequency reuse factor based on an octahedron-shaped structure. | Proposed approach drastically lowers the latency of drone-user UEs. | [315,316] |
| RL | Feature-learning was applied to mine and understand the complex correlation between multi-RMIs and link quality. | To anticipate the movement, apply strategy learning, and regard the location as the input. | [325,326] |
| RL | Methodology is shown using a network simulation in ns-3 and the ML implementation in Python. | In autonomous and user-centric networks where the system can provide the most effective path for end-users when going from a given source to a destination, there is the potential to implement OCSP. | [327] |
| RL | Provided insight into the learning challenge of cognitive radio networks and highlights methodologies such as RL used in cognitive radio networks. | 5G network slicing-based design that integrates with the ML-based CRN to maximise the use of the restricted spectrum. | [328,329] |
| RL | Research towards a ML-based remote local (D2D) communication network focused on effective connectivity and minimum latency. | Q-learning offers a perspective on D2D, and in combination with RL-LCDC, offers a practical algorithm for decision making under uncertain network conditions. | [332,333] |
| RF | Designing a learning-based resource allocation strategy which incorporates simply position information is utilised. | Design parameter modifications, the suggested system is fairly resilient to inaccurate user positioning. | [334] |
| RF | Cartel, a collaborative learning platform in edge clouds. | Add other ML models to the system. | [335] |
| TL | Presented an ML approach that enables semi-blind UL and DL decoupling in mixed sub-6 GHz/mmWave cell-free 5G networks. | 95% of accuracy in just a few training samples, with a quick and reliable solution to UL and DL decoupling in 5G networks. | [336,337] |
| SVM | Evaluate the predictive performance of four significant predictors that are crucial to achieve mobile traffic management, manage mobility, and conserve energy in future cellular networks. | Study robustness of these predictors versus varying training dataset sizes. Benchmark performances base on mobility traces from network CDRs. | [338,339,340] |
| SVM | In order to develop a deep encoder model, a preliminary experimental environment is constructed to collect data on the Multi faces. | Designing an algorithm to discover the ideal deep auto-encoder model and improving the proposed dependability assessment method. | [341] |
| DL | Following positive DL assisted communication results, committed to exploring a unique DL-based strategy for SCMA systems, motivated to increase BER performance. | Proposed schemes must be implemented and verified in a real environment system. An in-depth study of the structure of the learnt codebook may result in a higher decoding accuracy. | [342,343] |
| DL | Proposed an unsupervised DL strategy for cell outage detection and compared the results to a technique termed the nearest neighbour. | Mobility load balancing and intrusion detection are both DL concerns. | [344,345,346] |
| DL | Important problems with regard to dynamic resource scheduling design and offered a data-driven scheduling strategy. | Additionally, improving the physical network’s resource usage while guaranteeing QoS. | [347,348] |
| DL | ANN models include feed-forward NN and radial basis function neural networks. | Validation of simulation findings has proven that ML algorithms can be powerful analytical tools for future measurement-based channel modelling. | [349,350] |
| DL | Path loss prediction with better generalisation using satellite pictures can be done with twisted NN. | Proposal stands to benefit from increased data since more information can be used to quantify the generalisation reached. | [351,352] |
| K-means | Proposed two NN-based MLP models to aid in proactive auto-scaling of VNFs using commercial traffic traces. | To tackle the above mapping problem, ILP is able to solve it in seconds rather than hours. | [353] |
| NN | Binomial distribution-based power coefficient allocation procedure; Pascal’s triangle. | Adaptive modulation and coding techniques significantly enhanced the system’s BER performance. | [354] |
| NN | Facilitate automatic network adjustment and intelligent resource allocation optimization. | Downlink communications and the interference-elimination resource allocation mechanisms that go along with it will be examined. | [355] |
| 2- | Quality of Service (QoS) | ||
| ML | Results on how the model functions in the real world are provided. | N3AC scales to huge scenarios and is useful in real applications. | [317] |
| ML | To test the suggested framework architecture, a case study of QoS anomaly root cause tracking was given. | ML mechanisms, with the skills to train a computer to learn knowledge and concepts from data, can react intelligently to changing environments. | [318,319] |
| ML | Shows that ML can be integrated into an SDN controller to estimate resource need and behave appropriately, which this one is learning to implement by way of KPIs. | Design and implement new QoE measures specifically related to delay stall time, and the number of quality transitions. | [320,321] |
| ML | System, based on RL algorithms, allowing online learning of a dynamic and partially visible environment with delayed feedbacks. | Improving the GOL architecture includes employing fuzzy numbers and fuzzy RL. | [322,323,324] |
| RL | Developed a distributed approach for managing QoS radio resources in a dense heterogeneous network. | To dynamically react to changing traffic types. | [330,331] |
| 3- | Big Data | ||
| ANN | Tests show that CNN and RNN can find spatial and temporal traffic information. | More accurately projected traffic loads for proactive management are found in 5G networks. | [356] |
| DL | Implies the unnecessary waste of valuable resources, which ultimately disrupts operations. | Implemented algorithms must be faster, more efficient, and less complex: attempts can be made to study ameliorative strategies in the future. | [357] |
| ML | Traffic forecasting, thanks to big data, ML, and network KPIs, can estimate accurate statistical traffic characteristics of different types of cells over both short- and long-term forecasts. | The model makes use of a few critical network KPIs, yet it is effective and does not affect the model’s cost during training and forecasting. | [358,359] |
| ML | Found a substantial association between cell load and the user quality of a cell. It can be used to identify and implement interference pairings using ML approaches. | More powerful More data analytics methods are being researched to solve the issues of 4.9G and 5G mobile network optimization. | [360,361,362] |
| ML | Used proactive caching techniques to collect large amounts of existing data and use ML to ascertain content popularity. | Cache location at base stations is also essential in the design of ML tools. | [363,364,365] |
| ML | Documented a powerful framework for 5G network slicing and the architecture of 5G. | Edge computing, CORD applications, and SDN-based E-CORD, RCORD, and M-CORD must be given priority. | [366,367,368] |
| ML | 5G-oriented cyberdefense architecture to swiftly and efficiently identify cyberthreats in 5G mobile networks. | To detection and classification to help establish which DL models from a set and the optimal hyperparameters are more appropriate for each configuration and throughput need. | [369,370] |
| DL | Estimate a power delay profile of a sub-6 GHz channel, which is an input to the DNN. | Developing multi-user beam selection, perform a comparative investigation of other DL-based beam selection algorithms as well. | [374] |
| 4- | Security | ||
| DL | Huge antenna arrays as well as millimetre Wave antenna arrays are being utilised. | Solid set of coding algorithms is available. | [371,372,373] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mahdi, M.N.; Ahmad, A.R.; Qassim, Q.S.; Natiq, H.; Subhi, M.A.; Mahmoud, M. From 5G to 6G Technology: Meets Energy, Internet-of-Things and Machine Learning: A Survey. Appl. Sci. 2021, 11, 8117. https://doi.org/10.3390/app11178117
Mahdi MN, Ahmad AR, Qassim QS, Natiq H, Subhi MA, Mahmoud M. From 5G to 6G Technology: Meets Energy, Internet-of-Things and Machine Learning: A Survey. Applied Sciences. 2021; 11(17):8117. https://doi.org/10.3390/app11178117
Chicago/Turabian StyleMahdi, Mohammed Najah, Abdul Rahim Ahmad, Qais Saif Qassim, Hayder Natiq, Mohammed Ahmed Subhi, and Moamin Mahmoud. 2021. "From 5G to 6G Technology: Meets Energy, Internet-of-Things and Machine Learning: A Survey" Applied Sciences 11, no. 17: 8117. https://doi.org/10.3390/app11178117
APA StyleMahdi, M. N., Ahmad, A. R., Qassim, Q. S., Natiq, H., Subhi, M. A., & Mahmoud, M. (2021). From 5G to 6G Technology: Meets Energy, Internet-of-Things and Machine Learning: A Survey. Applied Sciences, 11(17), 8117. https://doi.org/10.3390/app11178117








