Homomorphic Encryption Based Privacy-Preservation for IoMT
Abstract
:1. Introduction
- A cluster of virtual nodes is designed around a group of IoMT devices, ensuring untrusted cloud service providers are unaware of computation tasks performed on data.
- IoT device data are shared using unsecured channels, resulting in delay and replay attacks. Timestamps and nonce values included in packets detect any eavesdroppers on the communication channel. A time synchronization protocol of the IoMT device clock ensures that no malicious node prevents the time reset process.
- Data transmission from IoMT devices is secured using homomorphic encryption, thus avoiding data manipulation by cyber attackers. Data intercepted by cyber attackers are in an encrypted ciphertext state, preventing any intruder from learning or manipulating the data.
- Computation of data is performed on the network’s edge layer using virtual nodes powered by resources from untrusted cloud services. Offloading operations from the Cloud to the edge prevents untrusted cloud servers from learning the computation process.
- Using a share-based virtual node selection process, homomorphic secret sharing prevents attackers from learning which selected virtual nodes are used for the computation process.
- A comparative analysis with existing research shows the proposed scheme provides data confidentiality, integrity, and a privacy-preserving secure computation process.
2. Related Works
2.1. Existing Research
- Key generation is based on security parameters (σ) taken as input, and the algorithm outputs an encryption ()/decryption () key pair.
- The encryption algorithm takes input () and is divided into bits () of 0 and 1s and ciphertext ().
- The decryption algorithm reveals data by receiving input to provide output .
- Evaluation of the algorithm takes input with function and reveals output .
- Partially homomorphic: A single type of mathematical operation is permissible on —either addition or multiplication performed without any limitation in execution.
- Somewhat homomorphic: There is a restriction on the execution limit, with only a certain number of times that either addition or multiplication are permissible.
- Fully homomorphic: Enables a larger subset of mathematical operations on the without any limit on the number of executions. There is a limitation on the number of users it supports; its implementation results in a significant computation overhead and increases network latency due to slow runtimes.
- A third entity requires a certain pre-fixed number of pieces of to make accessible.
- The possession of makes unaccessible, with the condition that each element of is by itself insufficient to reveal the message.
2.2. Key Considerations
- Data Confidentiality: Communication of data from IoMT devices to the edge layer transfers the ownership and control of the data. The physical security offered by the devices is lost when transmitted to external network layers, such as the base station at the edge layer. Data confidentiality schemes are required to ensure that any unauthorized entity viewing the data does not observe it in plaintext format. Information is required to be encrypted, preventing any form of identification of a user or device. Devices or applications supporting healthcare systems are needed to encrypt the data to a ciphertext, allowing data sharing on untrusted edge and cloud servers.
- Data Integrity: Data transferred from IoMT devices to insecure edge servers are vulnerable to foreign intrusion attempts, resulting in data manipulation and affecting the reliability of the final patient data computation results. It is essential to maintain data integrity during transmission and computation.
- Privacy-Preservation: Privacy is a significant challenge when transmitting sensitive and private user data using untrustworthy external networks such as cloud servers and edge nodes. Third-party edge and cloud service providers can learn much sensitive information about personal user data and sell it for profitable gains. Data sold to other entities allow fraudulent, targeted marketing campaigns and scams, resulting in further stress and financial loss to users. Encryption of patient identity and medical diagnosis information is essential using pseudo-random permutation and public-key encryption techniques.
- Secure Data Computation: Data shared across edge entities are often owned by external service providers that require information to be decrypted before performing mathematical operations. Encryption techniques such as homomorphic encryption allow edge service providers to perform computation operations without requiring the user to decrypt the data.
3. Proposed Scheme
3.1. Overview of the Proposed Scheme
- IoMT devices identify as the data owners (DO) responsible for generating data using embedded sensors in each patient. These machines include medical devices embedded in beds, machines deployed for scanning a patient’s vitals, and other smart sensors surrounded in the hospital.
- Virtual edge nodes (VEN) collect encrypted data shared by IoMT devices and use them to process and transmit output results to the healthcare application.
- The intelligent healthcare application, behaving as the data user (DU), monitors the data shared by IoMT devices. The DU manages the homomorphic decryption process and the number of shares generated during the homomorphic secret sharing computation process.
- Step 1.
- Several varying IoMT devices present in the hospital collect data from patients and transmit it to the DU that manages the intelligent healthcare application.
- Step 2.
- The DU forwards the data to the base station, which encrypts the plaintext data (x) to produce an encrypted ciphertext (c) using homomorphic encryption. Here, represents data being encrypted.
- Step 3.
- The edge-based base station provides several VENs around hospital zones for various computation services assigned by the DU for different tasks. A cluster is designed that provides support to IoMT devices that behave as cluster members along with VENs.
- Step 4.
- A cluster head (CH) behaves as the centroid of each cluster, and the one closest to the physical set of IoMT devices is selected. CH enables a line of sight with cluster node members based on distance proximity, providing better connectivity. In our paper, the base station maintains the geographical coordinates of each device and assigns a selected VEN as the CH closest to the set of devices using k-nearest neighbors.
- Step 5.
- Data transmission from the IoMT device is sent to the base station using unsecured channels, which exposes them to replay and delay attacks. Timestamp and nonce value-based scheme alerts the device to an attacker present in the communication channel.
- Step 6.
- Time clocks on devices are subject to being reset by attackers, and a time resynchronization scheme on the VENs and the cluster head VEN securely resets the time clock.
- Step 7.
- Data is encrypted from plaintext to ciphertext using a homomorphic encryption scheme at the base station and prevents cyber attackers from accessing the encrypted data.
- Step 8.
- Homomorphic secret sharing schemes rely on the number of computational operation queries requested by the DU to generate an n number of shares () distributed to each cluster head VEN. Data received at each node is previously encrypted using the homomorphic encryption algorithm.
- Step 9.
- Each cluster head VEN evaluates and computes data using cloud service resources allocated by the base station. Allocation of resources is equally distributed to each VEN, preventing an untrusted cloud service from learning the computation operations.
- Step 10.
- The DU receives the output data from the various cluster member VENs via the base station and performs the final decryption process of converting the results from the VENs ciphertext to plaintext.
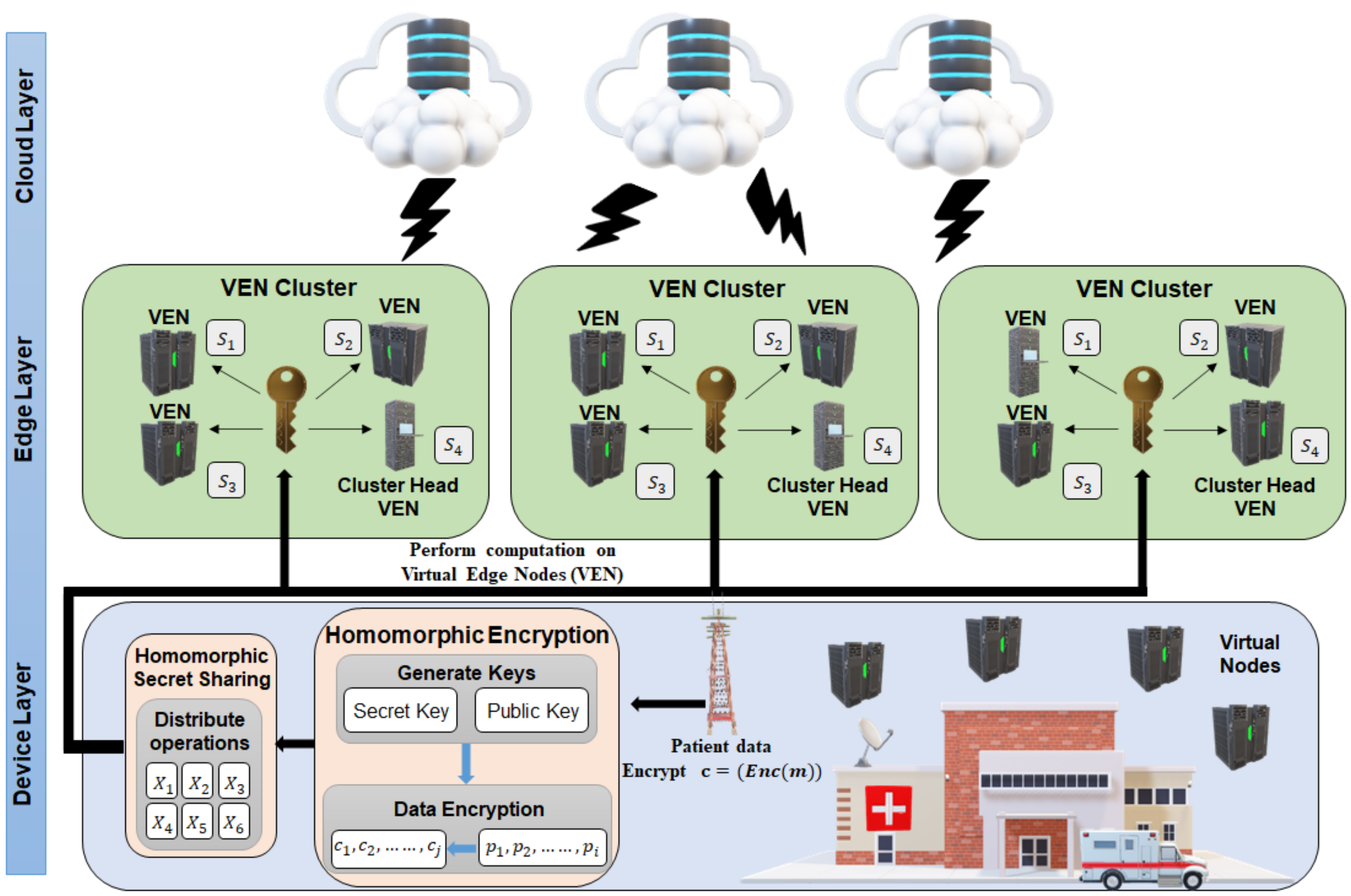
3.2. Workflow of the Proposed Scheme
3.2.1. Assigning Clusters
- Step 1.
- Initially, all VENs are generated and dispersed randomly to cover the entire coverage area of a hospital. Each VEN contains and stores the distance from the virtual node to the central physical base station. Each VEN has equivalently distributed computing resources received from the cloud environment services.
- Step 2.
- Several clusters are designed for each group of IoMT devices and their respective VENs. Each cluster includes a boundary area that consists of selected VENs and sensors using k-nearest neighbors (KNN) based on a preset distance. The objective is to prevent any two clusters from including the same sensor device in their group.
- Step 3.
- Geolocation data of each device and their distance from the central base station is used to include it in the cluster. Each cluster has a unique identity and each device registered with the cluster cannot join another cluster.
- Step 4.
- Communication overhead is a problem when dividing devices into multiple clusters. Each device may transmit data using VENs with a longer distance from the physical base station than other VENs. A centroid () node is selected as a midpoint in the cluster using geolocation data and ensure each device is equidistant from the centroid. Each centroid is a part of the set of VENs included in each cluster and is represented as . The centroid VEN is selected as the cluster head and provides an equivalent data communication distance for each IoMT device in the cluster.
3.2.2. Secure Data Transmission
- Step 1.
- The device communicates with nodes that are part of its local cluster to correctly reset the time and ignores other devices as they can provide incorrect timestamps.
- Step 2.
- The device sends a message to a VEN included in the cluster and requests for an ACK reply. The selection of VEN to communicate with is based on the distance to the physical device.
- Step 3.
- The VEN records both the timestamps of when the packet was sent by the device, recorded as and when the message is received as . The second timestamp indicates that the message received is within the acceptable threshold value.
- Step 4.
- The ACK reply message sent back by the VEN to the device includes which indicates when the VEN sent the ACK message. The device records the received ACK message as .
- Step 5.
- The clock difference calculated by the device measures , received during its communication with the VEN. The difference is calculated as:
- Step 6.
- The VEN further sends a message to the cluster head node for time confirmation and requests an ACK message as a reply.
- Step 7.
- The cluster head node receives the message and records . The ACK reply message sent back to the VEN now includes both and .
- Step 8.
- The message is forwarded at the received time to the device. The device records the received message’s .
- Step 9.
- The device now has further knowledge of the clock time difference between the cluster head and the device based on the received . The clock difference is measured as follows:

3.2.3. Homomorphic Encryption
- KeyGen (): The Key Generation algorithm uses a KeyGen () function to construct three keys, the public key (), secret key (), and a verification key ().
- Enc (): The encryption algorithm generates the ciphertext () using parameters including the , the dataset (), and the label () of the dataset. The Enc () function is represented as
- Eval (): The evaluation algorithm at the physical base station receives a query from the intelligent healthcare application (DU) to perform computational operations. The Eval () function includes parameters, , the homomorphic function (), the ciphertext () and is represented as .
- Dec (): The DU using the decryption algorithm verifies the computed data received from the base station and chooses to accept or reject it. The Dec () function is represented as , where is the query sent by the DU.
3.2.4. Homomorphic Secret Sharing
- Step 1.
- The base station encrypts the data using the ENC () function as part of the homomorphic encryption process.
- Step 2.
- Different data bits collected from varying IoMT devices (DO) have separate computation processes required by the DU. The encrypted ciphertext, using Enc (), is forwarded to each cluster head VEN and other nodes in different clusters.
- Step 3.
- The selection of clusters is based on the distance measured from the physical base station. As the number of computation tasks grows, other cluster heads are selected based on their distance proximity with the previous cluster head. If the resources required for computation is high, then the computation is shared with other virtual nodes present within the same cluster.
- Step 4.
- The threshold value for share () generation is based on the computation requests generated by the DU where .
- Step 5.
- The base station stores the assigned cluster heads assigned as shared to perform the computation tasks.
- Step 6.
- Data computation results are transmitted back to the base station, which is aware of each assigned node required to return computed data. Data received from other VENs are rejected as unauthorized packets.
4. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Javed, A.R.; Sarwar, M.U.; Beg, M.O.; Asim, M.; Baker, T.; Tawfik, H. A collaborative healthcare framework for shared healthcare plan with ambient intelligence. Hum.-Cent. Comput. Inf. Sci. 2020, 10, 1–21. [Google Scholar] [CrossRef]
- Singh, V.K.; Chandna, H.; Kumar, A.; Kumar, S.; Upadhyay, N.; Utkarsh, K. IoT-Q-Band: A low cost internet of things based wearable band to detect and track absconding COVID-19 quarantine subjects. EAI Endorsed Trans. Internet Things 2020, 6, 4. [Google Scholar] [CrossRef] [Green Version]
- Caring Home, 3 Best Medical Alerts Systems for Those with Pacemakers. Available online: https://www.caring.com/best-medical-alert-systems/best-medical-alert-systems-for-those-with-pacemakers/ (accessed on 6 September 2021).
- Triax Technologies, Contact Tracing IoT Solution. Available online: https://directory.newequipment.com/classified/contact-tracing-iot-solution-253439.html (accessed on 2 February 2021).
- COVID-19 Vaccine: The Role of IoT. Available online: https://www.iotforall.com/the-role-of-iot-for-the-covid-19-vaccine (accessed on 2 February 2019).
- Cyberattacks Cost Hospitals Millions during COVID-19. Available online: https://www.wsj.com/articles/cyberattacks-cost-hospitals-millions-during-covid-19-11614346713 (accessed on 2 February 2021).
- As Hospitals Cope with a COVID-19 Surge, Cyber Threats Loom. Available online: https://apnews.com/article/us-news-vermont-coronavirus-pandemic-burlington-hacking-28af71f3861d245df052f06e12475c2d (accessed on 2 February 2021).
- Daoud, W.B.; Obaidat, M.S.; Meddeb-Makhlouf, A.; Zarai, F.; Hsiao, K.F. TACRM: Trust access control and resource management mechanism in fog computing. Hum.-Cent. Comput. Inf. Sci. 2019, 9, 1–18. [Google Scholar] [CrossRef] [Green Version]
- Megouache, L.; Zitouni, A.; Djoudi, M. Ensuring user authentication and data integrity in multi-cloud environment. Hum.-Cent. Comput. Inf. Sci. 2020, 10, 1–20. [Google Scholar] [CrossRef]
- Yang, J. Low-latency cloud-fog network architecture and its load balancing strategy for medical big data. J. Ambient Intell. Humaniz. Comput. 2020, 1–10. [Google Scholar] [CrossRef]
- Pham, Q.V.; Fang, F.; Ha, V.N.; Piran, M.J.; Le, M.; Le, L.B.; Hwang, W.J.; Ding, Z. A survey of multi-access edge computing in 5G and beyond: Fundamentals, technology integration, and state-of-the-art. IEEE Access 2020, 8, 116974–117017. [Google Scholar] [CrossRef]
- Mazi, H.; Arsene, F.N.; Dissanayaka, A.M. The influence of black market activities through dark web on the economy: A survey. In Proceedings of the Midwest Instruction and Computing Symposium, Milwaukee, WI, USA, 3–4 April 2020. [Google Scholar]
- Salavi, R.R.; Math, M.M.; Kulkarni, U.P. A Survey of Various Cryptographic Techniques: From Traditional Cryptography to Fully Homomorphic Encryption. In Lecture Notes in Networks and Systems, Proceedings of the Innovations in Computer Science and Engineering, Singapore, 16–17 August 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 295–305. [Google Scholar]
- Agwa, N.A.; Kobayashi, T.; Sugimoto, C.; Kohno, R. Security of Patient’s Privacy in E-Health using Secret Sharing and Homomorphism Encryption Scheme. In Proceedings of the 2020 35th International Technical Conference on Circuits/Systems, Computers and Communications (ITC-CSCC), Nagoya, Japan, 3–6 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 155–160. [Google Scholar]
- Sun, X.; Yu, F.R.; Zhang, P.; Xie, W.; Peng, X. A survey on secure computation based on homomorphic Encryption in vehicular Ad Hoc networks. Sensors 2020, 20, 4253. [Google Scholar] [CrossRef] [PubMed]
- Zhou, S.; Yu, Z.; Nasr, E.S.A.; Mahmoud, H.A.; Awwad, E.M.; Wu, N. Homomorphic encryption of supervisory control systems using automata. IEEE Access 2020, 8, 147185–147198. [Google Scholar] [CrossRef]
- Cominetti, E.L.; Simplicio, M.A. Fast additive partially homomorphic Encryption from the approximate common divisor problem. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2988–2998. [Google Scholar] [CrossRef]
- Acar, A.; Aksu, H.; Uluagac, A.S.; Conti, M. A survey on homomorphic encryption schemes: Theory and implementation. ACM Comput. Surv. (CSUR) 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Chen, Y.C.; Hung, T.H.; Hsieh, S.H.; Shiu, C.W. A new reversible data hiding in encrypted image based on multi-secret sharing and lightweight cryptographic algorithms. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3332–3343. [Google Scholar] [CrossRef]
- Lin, H.; Garg, S.; Hu, J.; Wang, X.; Piran, M.J.; Hossain, M.S. Privacy-enhanced data fusion for COVID-19 applications in intelligent Internet of medical Things. IEEE Internet Things J. 2020, 1. [Google Scholar] [CrossRef]
- Vizitiu, A.; Niƫă, C.I.; Puiu, A.; Suciu, C.; Itu, L.M. Applying deep neural networks over homomorphic encrypted medical data. Comput. Math. Methods Med. 2020, 2020, 26. [Google Scholar] [CrossRef] [PubMed]
- Cheng, W.; Ou, W.; Yin, X.; Yan, W.; Liu, D.; Liu, C. A Privacy-Protection Model for Patients. Secur. Commun. Netw. 2020, 2020, 12. [Google Scholar] [CrossRef]
- Yang, Y.; Xiao, X.; Cai, X.; Zhang, W. A secure and high visual-quality framework for medical images by contrast-enhancement reversible data hiding and homomorphic Encryption. IEEE Access 2019, 7, 96900–96911. [Google Scholar] [CrossRef]
- Cano, M.D.; Cañavate-Sanchez, A. Preserving data privacy in the internet of medical things using dual signature ECDSA. Secur. Commun. Netw. 2020, 2020, 4960964. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. BEdgeHealth: A Decentralized Architecture for Edge-based IoMT Networks Using Blockchain. IEEE Internet Things J. 2021, 8, 11743–11757. [Google Scholar] [CrossRef]
- Qiu, T.; Liu, X.; Han, M.; Ning, H.; Wu, D.O. A secure time synchronization protocol against fake timestamps for large-scale internet of things. IEEE Internet Things J. 2017, 4, 1879–1889. [Google Scholar] [CrossRef]

| References | Mechanism | Data Confidentiality | Data Integrity | Privacy-Preservation | Secure Data Computation |
|---|---|---|---|---|---|
| Lin et al. [21] (2020) | Homomorphic encryption and mobile edge computing. | Ciphertext output is secured using homomorphic encryption. | Encrypted medical data prevents attackers from manipulation. | Privacy of ciphertext is preserved, however, operations are exposed on public nodes. | Data computation takes place at untrusted edge nodes. |
| Vizitiu et al. [22] (2020) | Homomorphic encryption | Encryption protects data from being exposed to malicious entities. | Weak encryption keys are vulnerable using an optimization problem. | Exposed keys enable attackers to decrypt data and acquire private medical data. | Arithmetic operations are performed over an untrusted cloud server exposing computation process. |
| Cheng et al. [23] (2020) | Homomorphic encryption, blockchain, federated learning | Homomorphic encrypted data and local computation using federated learning protects device data. | Encryption prevents attackers modifying data without decryption. | Federated learning preserves privacy by computing data locally on IoT devices. | Weak IoT device security and vulnerability to cyberattacks compromises future computation operation capability. |
| Yang et al. [24] (2019) | Homomorphic encryption using chaotic mapping | Medical images are encrypted using homomorphic encryption. | Encrypted image data is safe from malicious users. | Image data is only accessible to healthcare services. | The research does not identify any means of preserving computational privacy and only addresses encrypting data. |
| Cano et al. [25] (2020) | Dual signatures using Elliptic Curve Digital Signature Algorithm | The dual signature scheme does not encrypt medical data but only the identities of patients. | Data is exposed both on the Cloud and the edge, risking manipulation. | Privacy of users is maintained by verifying identities at both the edge and the cloud layer using dual signatures and identifiers. | Any computation of data on untrusted servers requires prior decryption. Data computational privacy is not preserved. |
| Nguyen et al. [26] (2021) | Blockchain and smart contracts | Data is exposed on public blockchain networks. | Data stored in blocks prevents manipulation as it would alter the hash value. | Privacy of user data is compromised at public blockchain-based networks. Mobile edge computing-based computation exposes mathematical operations performed on data. | Computational operations are exposed at the mobile edge computing layer. Data is required to be decrypted before any operation is performed. |
| Proposed scheme | Homomorphic encryption and secret sharing | Data is encrypted using homomorphic encryption maintaining confidentiality of collected private medical data. | Data manipulation is not possible on encrypted data, preventing attackers from reading and altering data. | Data privacy is maintained as it is in the form of a ciphertext, preserving both medical data and user identity. | Computations are performed using secret sharing on nodes at the edge layer. Mathematical operations are distributed and performed on hidden nodes. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Salim, M.M.; Kim, I.; Doniyor, U.; Lee, C.; Park, J.H. Homomorphic Encryption Based Privacy-Preservation for IoMT. Appl. Sci. 2021, 11, 8757. https://doi.org/10.3390/app11188757
Salim MM, Kim I, Doniyor U, Lee C, Park JH. Homomorphic Encryption Based Privacy-Preservation for IoMT. Applied Sciences. 2021; 11(18):8757. https://doi.org/10.3390/app11188757
Chicago/Turabian StyleSalim, Mikail Mohammed, Inyeung Kim, Umarov Doniyor, Changhoon Lee, and Jong Hyuk Park. 2021. "Homomorphic Encryption Based Privacy-Preservation for IoMT" Applied Sciences 11, no. 18: 8757. https://doi.org/10.3390/app11188757






