Analysis of Security Issues and Countermeasures for the Industrial Internet of Things
Abstract
:1. Introduction
1.1. Problem Statement and Motivation
1.2. Contributions
- We review the existing IIoT security issues in a systematic way. We consider broader aspects of an IIoT system (e.g., integration of IoT, Industry 4.0, and various communication and networking issues related to multi-organizational communications) and list a set of security issues for the IIoT systems.
- We discuss an example use case of IIoT architecture based on layers and examine the identified security issues in each layer. We provide a detailed discussion of the potential countermeasures against these security issues. It helps to understand the system-specific security needs in an IIoT architecture at a more fine-grained level.
- We discuss a set of unique open research issues and list the future research directions that require further study to ensure the security of an IIoT system at scale.
1.3. Paper Organization and Roadmap
2. IIoT Architecture
3. Security Issues in IIoT Systems
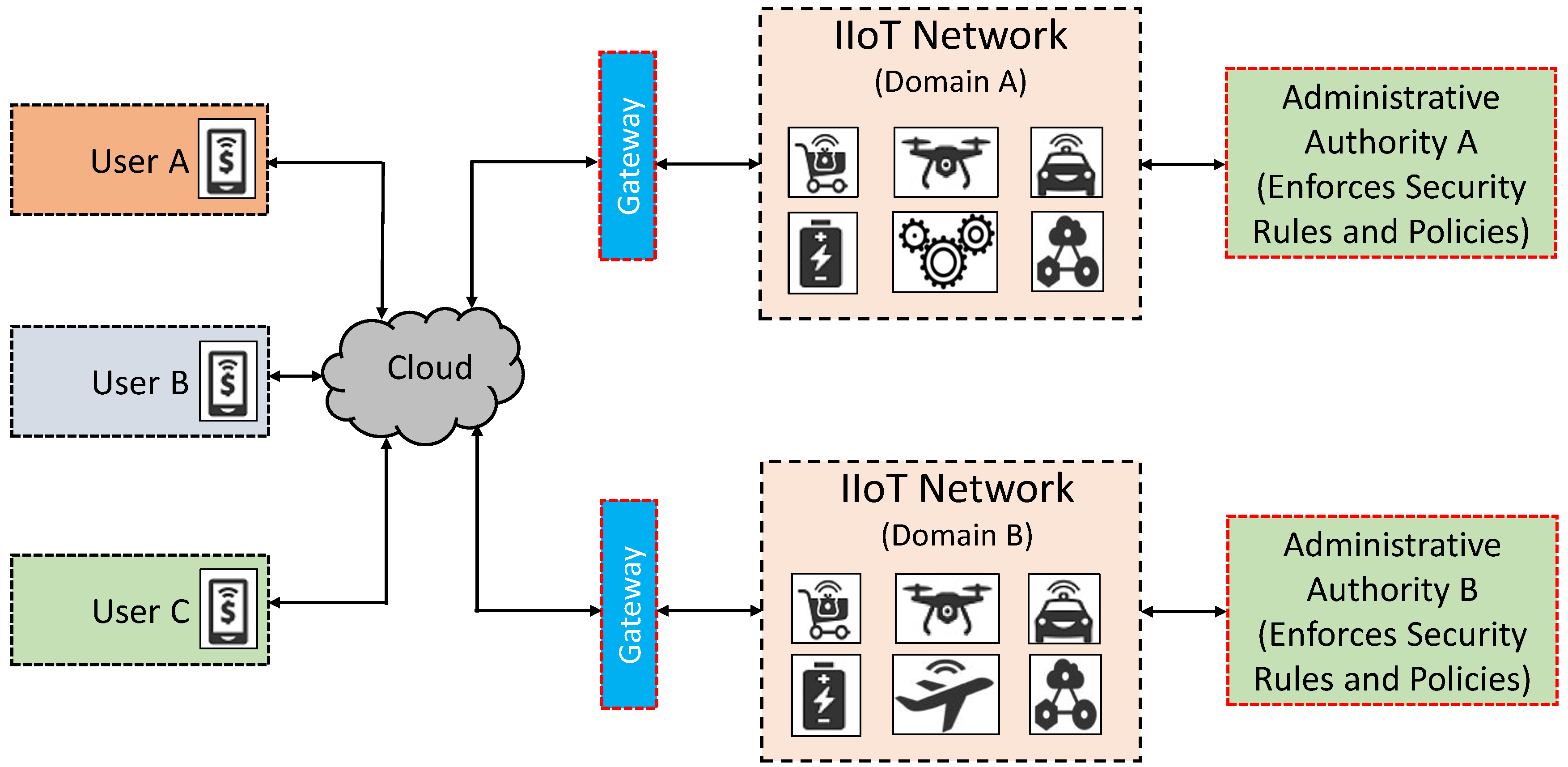
3.1. An Application Scenario
3.2. Security Issues
3.3. Security Issue 1—Controlling over Communication
3.4. Security Issue 2—Infecting Data Packets
3.5. Security Issue 3—Flooding Attack
3.6. Security Issue 4—Attack on Physical Devices
3.7. Security Issue 5—Impact on Devices’ Performance
3.8. Security Issue 6—Device Impersonation
3.9. Security Issue 7—Privacy
3.10. Security Issue 8—Data Confidentiality
3.11. Security Issue 9—Heterogeneity of Networks
3.12. Security Issue 10—Non-Trusted Network Connection
3.13. Security Issue 11—Dynamic Infrastructure
3.14. Security Issue 12—Anonymity
3.15. Security Issue 13—Cross-Domain Jurisdictions
3.16. Security Issue 14—Heterogeneous Infrastructure
3.17. Security Issue 15—Cascading Services
3.18. Security Issue 16—Emergence of Resources
4. Security Countermeasures in IIoT systems
4.1. Perception Layer
4.2. Network Layer
4.3. Support Layer
4.4. Application Layer
5. Discussion and Future Research Direction
- Training datasets for ML-based solutions: generating training datasets with sufficient numbers of possible attacks and benign traffic is challenging for ML algorithms in IIoT security. In addition, high-quality training data are required for ML methods, as the noisy nature of IIoT data can affect the performance of ML-based intrusion detection. Deep Learning (DL) methods can be used for large-scale, heterogeneous, and noisy datasets in IIoT networks [192].
- Exploiting ML and DL algorithms: studies have shown that more severe attacks are possible using these methods. For instance, convolutional neural networks (CNN) have been used to break many cryptographic algorithms. These security issues must be taken into account in the design of IIoT networks.
- Privacy concerns: ML and DL algorithms may cause potential leakage of private data. For example, DL classifications can be broken easily, and it potentially causes privacy breaches. In addition, there are some adversarial attacks possible against the DL process, which exploit the detection methods used in the DL. Therefore, more research in this space is essential.
- Implementation of ML/DL at the edge: this is another challenging area that needs further research. In edge computing, these methods (i.e., ML and DL) can help minimize cloud dependency and delay processing. Further research in this area is required.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Aleksic, S. A survey on optical technologies for IoT, smart industry, and smart infrastructures. J. Sens. Actuator Netw. 2019, 8, 47. [Google Scholar] [CrossRef] [Green Version]
- Boyes, H.; Hallaq, B.; Cunningham, J.; Watson, T. The industrial internet of things (IIoT): An analysis framework. Comput. Ind. 2018, 101, 1–12. [Google Scholar] [CrossRef]
- Okano, M.T. IOT and industry 4.0: The industrial new revolution. Int. Conf. Manag. Inf. Syst. 2017, 25, 26. [Google Scholar]
- Industrial IoT Market by Device & Technology. Available online: https://www.marketsandmarkets.com/Market-Reports/industrial-internet-of-things-market-129733727.html (accessed on 5 July 2021).
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Iwanicki, K. A distributed systems perspective on industrial IoT. In Proceedings of the 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–6 July 2018; pp. 1164–1170. [Google Scholar]
- Lu, Y. Cyber physical system (CPS)-based industry 4.0: A survey. J. Ind. Integr. Manag. 2017, 2, 1750014. [Google Scholar] [CrossRef]
- Foukalas, F.; Pop, P.; Theoleyre, F.; Boano, C.A.; Buratti, C. Dependable wireless industrial iot networks: Recent advances and open challenges. In Proceedings of the 2019 IEEE European Test Symposium (ETS), Baden, Germany, 27–31 May 2019; pp. 1–10. [Google Scholar]
- Raposo, D.; Rodrigues, A.; Sinche, S.; Sá Silva, J.; Boavida, F. Industrial IoT monitoring: Technologies and architecture proposal. Sensors 2018, 18, 3568. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Satyanarayanan, M. Pervasive computing: Vision and challenges. IEEE Pers. Commun. 2001, 8, 10–17. [Google Scholar] [CrossRef]
- Abowd, G.D.; Mynatt, E.D. Charting Past, Present, and Future Research in Ubiquitous Computing. ACM Trans. Comput. Hum. Interact. 2000, 7, 29–58. [Google Scholar] [CrossRef]
- Khan, W.Z.; Rehman, M.; Zangoti, H.M.; Afzal, M.K.; Armi, N.; Salah, K. Industrial internet of things: Recent advances, enabling technologies and open challenges. Comput. Electr. Eng. 2020, 81, 106522. [Google Scholar] [CrossRef]
- Sari, A.; Lekidis, A.; Butun, I. Industrial networks and IIoT: Now and future trends. In Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2020; pp. 3–55. [Google Scholar]
- Jaidka, H.; Sharma, N.; Singh, R. Evolution of iot to iiot: Applications & challenges. In Proceedings of the International Conference on Innovative Computing & Communications (ICICC), Delhi, India, 18 May 2020. [Google Scholar]
- Pal, S.; Hitchens, M.; Varadharajan, V.; Rabehaja, T. Policy-based access control for constrained healthcare resources. In Proceedings of the 2018 IEEE 19th International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), Chania, Greece, 12–15 June 2018; pp. 588–599. [Google Scholar]
- Pal, S.; Hitchens, M.; Varadharajan, V. Towards a secure access control architecture for the Internet of Things. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks (LCN), Singapore, 9–12 October 2017; pp. 219–222. [Google Scholar]
- Pal, S. Limitations and Approaches in Access Control and Identity Management for Constrained IoT Resources. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 431–432. [Google Scholar]
- IIoT—The Industrial Internet of Things (IIoT) Explained. Available online: https://www.i-scoop.eu/ (accessed on 30 June 2021).
- Bansal, M.; Goyal, A.; Choudhary, A. Industrial Internet of Things (IIoT): A Vivid Perspective. In Inventive Systems and Control; Springer: Berlin/Heidelberg, Germany, 2021; pp. 939–949. [Google Scholar]
- Rabehaja, T.; Pal, S.; Hitchens, M. Design and implementation of a secure and flexible access-right delegation for resource constrained environments. Future Gener. Comput. Syst. 2019, 99, 593–608. [Google Scholar] [CrossRef]
- Luchian, R.A.; Stamatescu, G.; Stamatescu, I.; Fagarasan, I.; Popescu, D. IIoT Decentralized System Monitoring for Smart Industry Applications. In Proceedings of the 2021 29th Mediterranean Conference on Control and Automation (MED), Puglia, Italy, 22–25 June 2021; pp. 1161–1166. [Google Scholar]
- Sadeghi, A.R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial internet of things. In Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015; pp. 1–6. [Google Scholar]
- Tsiknas, K.; Taketzis, D.; Demertzis, K.; Skianis, C. Cyber Threats to Industrial IoT: A Survey on Attacks and Countermeasures. IoT 2021, 2, 9. [Google Scholar] [CrossRef]
- Ginter, A. The Top 20 Cyberattacks on Industrial Control Systems; Waterfall Security Solutions: 2017. Available online: https://waterfall-security.com/20-attacks (accessed on 30 August 2021).
- Ly, K.; Jin, Y. Security challenges in CPS and IoT: From end-node to the system. In Proceedings of the 2016 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Pittsburgh, PA, USA, 11–13 July 2016; pp. 63–68. [Google Scholar]
- Attri, T.; Bhushan, B. Enabling Technologies, Attacks, and Machine Learning-Based Countermeasures for IoT and IIoT. In Integration of WSNs into Internet of Things; CRC Press: Boca Raton, FL, USA, 2021; pp. 249–272. [Google Scholar]
- Pal, S. Wind energy—An innovative solution to global warming? In Proceedings of the 2009 1st International Conference on the Developements in Renewable Energy Technology (ICDRET), Dhaka, Bangladesh, 17–19 December 2009; pp. 1–3. [Google Scholar]
- Ghadge, A.; Kara, M.E.; Moradlou, H.; Goswami, M. The impact of Industry 4.0 implementation on supply chains. J. Manuf. Technol. Manag. 2020, 31, 669–686. [Google Scholar] [CrossRef]
- Müller, J.M.; Veile, J.W.; Voigt, K.I. Prerequisites and incentives for digital information sharing in Industry 4.0—An international comparison across data types. Comput. Ind. Eng. 2020, 148, 106733. [Google Scholar] [CrossRef]
- Bombardier Statement on Cybersecurity Breach. Available online: https://bombardier.com/en/media/news/bombardier-statement-cybersecurity-breach (accessed on 3 July 2021).
- School Cyber-Attack Affects 40,000 Pupils’ Email. Available online: https://www.bbc.com/news/technology-56569873 (accessed on 3 July 2021).
- Dwyer, A. The NHS cyber-attack: A look at the complex environmental conditions of WannaCry. RAD Mag. 2018, 44, 25–26. [Google Scholar]
- Khujamatov, H.; Reypnazarov, E.; Khasanov, D.; Akhmedov, N. IoT, IIoT, and Cyber-Physical Systems Integration. In Emergence of Cyber Physical System and IoT in Smart Automation and Robotics; Springer: Berlin/Heidelberg, Germany, 2021; pp. 31–50. [Google Scholar]
- Yu, X.; Guo, H. A survey on IIoT security. In Proceedings of the 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS), Singapore, 28–30 August 2019; pp. 1–5. [Google Scholar]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. Towards a systematic survey of industrial IoT security requirements: Research method and quantitative analysis. In Proceedings of the Workshop on Fog Computing and the IoT, Montreal, QC, Canada, 15–18 April 2019; pp. 56–63. [Google Scholar]
- Valentin, V.; Mehaoua, A.; Guenane, F.A. Security Challenges and Requirements for Industrial IoT Systems; Chapman and Hall/CRC: Boca Raton, FL, USA, 2020; pp. 117–136. [Google Scholar]
- Panchal, A.C.; Khadse, V.M.; Mahalle, P.N. Security issues in IIoT: A comprehensive survey of attacks on IIoT and its countermeasures. In Proceedings of the 2018 IEEE Global Conference on Wireless Computing and Networking (GCWCN), Lonavala, India, 23–24 November 2018; pp. 124–130. [Google Scholar]
- Xu, H.; Yu, W.; Griffith, D.; Golmie, N. A survey on industrial Internet of Things: A cyber-physical systems perspective. IEEE Access 2018, 6, 78238–78259. [Google Scholar] [CrossRef]
- Jayalaxmi, P.; Saha, R.; Kumar, G.; Kumar, N.; Kim, T.H. A taxonomy of security issues in Industrial Internet-of-Things: Scoping review for existing solutions, future implications, and research challenges. IEEE Access 2021, 9, 25344–25359. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Saifullah, A.; Xu, Y.; Lu, C.; Chen, Y. Real-time scheduling for WirelessHART networks. In Proceedings of the 2010 31st IEEE Real-Time Systems Symposium, San Diego, CA, USA, 30 November–3 December 2010; pp. 150–159. [Google Scholar]
- Dirgantoro, K.P.; Nwadiugwu, W.P.; Lee, J.M.; Kim, D.S. Dual fieldbus industrial IoT networks using edge server architecture. Manuf. Lett. 2020, 24, 108–112. [Google Scholar] [CrossRef]
- Devan, P.; Hussin, F.A.; Ibrahim, R.; Bingi, K.; Khanday, F.A. A Survey on the Application of WirelessHART for Industrial Process Monitoring and Control. Sensors 2021, 21, 4951. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V. Access control for Internet of Things—Enabled assistive technologies: An architecture, challenges and requirements. In Assistive Technology for the Elderly; Suryadevara, N.K., Mukhopadhyay, S.C., Eds.; Academic Press: Cambridge, MA, USA, 2020; pp. 1–43. [Google Scholar] [CrossRef]
- Li, S.; Tryfonas, T.; Li, H. The Internet of Things: A security point of view. Internet Res. 2016, 26, 337–359. [Google Scholar] [CrossRef] [Green Version]
- Ray, P. A Survey on Internet of Things Architectures—ScienceDirect. J. King Saud Univ. Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef] [Green Version]
- Al-Qaseemi, S.A.; Almulhim, H.A.; Almulhim, M.F.; Chaudhry, S.R. IoT architecture challenges and issues: Lack of standardization. In Proceedings of the 2016 Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; pp. 731–738. [Google Scholar] [CrossRef]
- Yun, M.; Yuxin, B. Research on the architecture and key technology of Internet of Things (IoT) applied on smart grid. In Proceedings of the 2010 International Conference on Advances in Energy Engineering, Beijing, China, 19–20 June 2010; pp. 69–72. [Google Scholar]
- Silva, B.N.; Khan, M.; Han, K. Internet of things: A comprehensive review of enabling technologies, architecture, and challenges. IETE Tech. Rev. 2018, 35, 205–220. [Google Scholar] [CrossRef]
- Yang, Z.; Yue, Y.; Yang, Y.; Peng, Y.; Wang, X.; Liu, W. Study and application on the architecture and key technologies for IOT. In Proceedings of the 2011 International Conference on Multimedia Technology, Hangzhou, China, 26–28 July 2011; pp. 747–751. [Google Scholar] [CrossRef]
- CISCO: The Internet of Things Reference Model. Available online: http://cdn.iotwf.com/ (accessed on 4 October 2018).
- Sengupta, J.; Ruj, S.; Bit, S.D. A secure fog-based architecture for industrial Internet of Things and industry 4.0. IEEE Trans. Ind. Inform. 2020, 17, 2316–2324. [Google Scholar] [CrossRef]
- Pham, Q.V.; Dev, K.; Maddikunta, P.K.R.; Gadekallu, T.R.; Huynh-The, T. Fusion of federated learning and industrial internet of things: A survey. arXiv 2021, arXiv:2101.00798. [Google Scholar]
- Radanliev, P.; De Roure, D.; Nicolescu, R.; Huth, M. A Reference Architecture for Integrating the Industrial Internet of Things in the Industry 4.0; University of Oxford: Oxford, UK, 2019. [Google Scholar]
- Varga, P.; Peto, J.; Franko, A.; Balla, D.; Haja, D.; Janky, F.; Soos, G.; Ficzere, D.; Maliosz, M.; Toka, L. 5G support for Industrial IoT Applications—Challenges, Solutions, and Research gaps. Sensors 2020, 20, 828. [Google Scholar] [CrossRef] [Green Version]
- Civerchia, F.; Bocchino, S.; Salvadori, C.; Rossi, E.; Maggiani, L.; Petracca, M. Industrial Internet of Things monitoring solution for advanced predictive maintenance applications. J. Ind. Inf. Integr. 2017, 7, 4–12. [Google Scholar] [CrossRef]
- Da Xu, L.; He, W.; Li, S. Internet of things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar]
- Kumar, A.; Krishnamurthi, R.; Nayyar, A.; Sharma, K.; Grover, V.; Hossain, E. A novel smart healthcare design, simulation, and implementation using healthcare 4.0 processes. IEEE Access 2020, 8, 118433–118471. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Rabehaja, T.; Mukhopadhyay, S. Security requirements for the internet of things: A systematic approach. Sensors 2020, 20, 5897. [Google Scholar] [CrossRef] [PubMed]
- Gluhak, A.; Krco, S.; Nati, M.; Pfisterer, D.; Mitton, N.; Razafindralambo, T. A survey on facilities for experimental internet of things research. IEEE Commun. Mag. 2011, 49, 58–67. [Google Scholar] [CrossRef] [Green Version]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context Aware Computing for The Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 414–454. [Google Scholar] [CrossRef] [Green Version]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Madakam, S.; Date, H. Security Mechanisms for Connectivity of Smart Devices in the Internet of Things. In Connectivity Frameworks for Smart Devices; Mahmood, Z., Ed.; Computer Communications and Networks; Springer International Publishing: Berlin/Heidelberg, Germany, 2016; pp. 23–41. [Google Scholar] [CrossRef]
- Premalatha, J.; Rajasekar, V. Industrial Internet of Things Safety and Security. In Internet of Things; CRC Press: Boca Raton, FL, USA, 2020; pp. 135–152. [Google Scholar]
- Ghosh, S.; Gourisaria, M.K.; Routaray, S.S.; Pandey, M. IIoT: A Survey and Review of Theoretical Concepts. In Interoperability in IoT for Smart Systems; CRC Press: Boca Raton, FL, USA, 2020; pp. 223–236. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Security and privacy in the Internet of Things: Current status and open issues. In Proceedings of the International Conference on Privacy and Security in Mobile Systems (PRISMS), Aalborg, Denmark, 11–14 May 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Ahmed, M.; Jaidka, S.; Sarkar, N.I. Security in Decentralised Computing, IoT and Industrial IoT. In Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2020; pp. 191–211. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Secure routing for internet of things: A survey. J. Netw. Comput. Appl. 2016, 66, 198–213. [Google Scholar] [CrossRef]
- Wang, Y.; Wen, Q. A privacy enhanced DNS scheme for the Internet of Things. In Proceedings of the IET International Conference on Communication Technology and Application (ICCTA), Beijing, China, 14–16 October 2011; IET: London, UK, 2011; pp. 699–702. [Google Scholar] [CrossRef]
- Pongle, P.; Chavan, G. A survey: Attacks on RPL and 6LoWPAN in IoT. In Proceedings of the International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Kannhavong, B.; Nakayama, H.; Nemoto, Y.; Kato, N.; Jamalipour, A. A survey of routing attacks in mobile ad hoc networks. IEEE Wirel. Commun. 2007, 14, 85–91. [Google Scholar] [CrossRef]
- Ghafir, I.; Prenosil, V.; Alhejailan, A.; Hammoudeh, M. Social Engineering Attack Strategies and Defence Approaches. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 145–149. [Google Scholar] [CrossRef] [Green Version]
- Pal, S.; Hitchens, M.; Varadharajan, V.; Rabehaja, T. Policy-based access control for constrained healthcare resources in the context of the Internet of Things. J. Netw. Comput. Appl. 2019, 139, 57–74. [Google Scholar] [CrossRef]
- Mosteiro-Sanchez, A.; Barcelo, M.; Astorga, J.; Urbieta, A. Securing IIoT using defence-in-depth: Towards an end-to-end secure industry 4.0. J. Manuf. Syst. 2020, 57, 367–378. [Google Scholar] [CrossRef]
- Shah, D.P.; Shah, P.G. Revisting of elliptical curve cryptography for securing Internet of Things (IOT). In Proceedings of the 2018 Advances in Science and Engineering Technology International Conferences (ASET), Dubai, Sharjah, Abu Dhabi, United Arab Emirates, 6 February–5 April 2018; pp. 1–3. [Google Scholar]
- Kozlov, D.; Veijalainen, J.; Ali, Y. Security and Privacy Threats in IoT Architectures. In Proceedings of the 7th International Conference on Body Area Networks, Oslo, Norway, 24–26 February 2012; ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering): Brussels, Belgium, 2012; pp. 256–262. [Google Scholar]
- Sarma, A.; Girão, J. Identities in the Future Internet of Things. Wirel. Pers. Commun. 2009, 49, 353–363. [Google Scholar] [CrossRef]
- Welch, D.; Lathrop, S. Wireless security threat taxonomy. In Proceedings of the IEEE Systems, Man and Cybernetics SocietyInformation Assurance Workshop, West Point, NY, USA, 18–20 June 2003; pp. 76–83. [Google Scholar] [CrossRef]
- Pacheco, L.A.; Gondim, J.J.C.; Barreto, P.A.; Alchieri, E. Evaluation of Distributed Denial of Service threat in the Internet of Things. In Proceedings of the 15th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 31 October–2 November 2016; pp. 89–92. [Google Scholar] [CrossRef]
- Sharghivand, N.; Derakhshan, F. Data Security and Privacy in Industrial IoT. In AI-Enabled Threat Detection and Security Analysis for Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 21–39. [Google Scholar]
- Xiao, B.; Chen, W.; He, Y.; Sha, E.H.M. An Active Detecting Method Against SYN Flooding Attack. In Proceedings of the 11th International Conference on Parallel and Distributed Systems (ICPADS’05), Fukuoka, Japan, 20–22 July 2005; pp. 709–715. [Google Scholar] [CrossRef] [Green Version]
- Abosata, N.; Al-Rubaye, S.; Inalhan, G.; Emmanouilidis, C. Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications. Sensors 2021, 21, 3654. [Google Scholar] [CrossRef] [PubMed]
- Jing, Q.; Vasilakos, A.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Babar, S.; Mahalle, P.; Stango, A.; Prasad, N.; Prasad, R. Proposed Security Model and Threat Taxonomy for the Internet of Things (IoT). In Recent Trends in Network Security and Applications; Meghanathan, N., Boumerdassi, S., Chaki, N., Nagamalai, D., Eds.; Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 89, pp. 420–429. [Google Scholar] [CrossRef]
- Coppolino, L.; DAlessandro, V.; DAntonio, S.; Levy, L.; Romano, L. My Smart Home is under Attack. In Proceedings of the 18th International Conference on Computational Science and Engineering, Porto, Portugal, 21–23 October 2015; pp. 145–151. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V. On the design of security mechanisms for the Internet of Things. In Proceedings of the 2017 Eleventh International Conference on Sensing Technology (ICST), Sydney, Australia, 4–6 December 2017; pp. 1–6. [Google Scholar]
- Ronen, E.; Shamir, A. Extended Functionality Attacks on IoT Devices: The Case of Smart Lights. In Proceedings of the European Symposium on Security and Privacy (EuroS&P), Saarbruecken, Germany, 21–24 March 2016; pp. 3–12. [Google Scholar] [CrossRef]
- Pal, S. Internet of Things and Access Control: Sensing, Monitoring and Controlling Access in IoT-Enabled Healthcare Systems; Springer Nature: Berlin/Heidelberg, Germany, 2021; Volume 37. [Google Scholar]
- Pal, S. Extending Mobile Cloud Platforms Using Opportunistic Networks: Survey, Classification and Open Issues. J. Univ. Comput. Sci. 2015, 21, 1594–1634. [Google Scholar]
- Catarinucci, L.; de Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-Aware Architecture for Smart Healthcare Systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Yang, J.; Fang, B. Security model and key technologies for the Internet of things. J. China Univ. Posts Telecommun. 2011, 18, 109–112. [Google Scholar] [CrossRef]
- Moscibroda, T.; Mutlu, O. Memory Performance Attacks: Denial of Memory Service in Multi-core Systems. In Proceedings of the 16th USENIX Security Symposium, Boston, MA, USA, 6–10 August 2007; USENIX Association: Berkeley, CA, USA, 2007. [Google Scholar]
- Ravi, N.; Scott, J.; Han, L.; Iftode, L. Context-aware Battery Management for Mobile Phones. In Proceedings of the Sixth Annual IEEE International Conference on Pervasive Computing and Communications (PerCom), Hong Kong, China, 17–21 March 2008; IEEE: Los Alamitos, CA, USA, 2008; pp. 224–233. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Y.; Chen, P. Authentication and Access Control in the Internet of Things. In Proceedings of the 32nd International Conference on Distributed Computing Systems Workshops, Macau, China, 18–21 June 2012; pp. 588–592. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V. Modeling identity for the internet of things: Survey, classification and trends. In Proceedings of the 2018 12th International Conference on Sensing Technology (ICST), Limerick, Ireland, 4–6 December 2018; pp. 45–51. [Google Scholar]
- Mahalle, P.; Babar, S.; Prasad, N.; Prasad, R. Identity Management Framework towards Internet of Things (IoT): Roadmap and Key Challenges. In Recent Trends in Network Security and Applications; Meghanathan, N., Boumerdassi, S., Chaki, N., Nagamalai, D., Eds.; Communications in Computer and Information Science, Chapter 43; Springer: Berlin/Heidelberg, Germany, 2010; Volume 89, pp. 430–439. [Google Scholar] [CrossRef]
- Suhardi; Ramadhan, A. A Survey of Security Aspects for Internet of Things in Healthcare. In Information Science and Applications (ICISA); Kim, K.J., Joukov, N., Eds.; Lecture Notes in Electrical Engineering; Springer: Singapore, 2016; Volume 376, pp. 1237–1247. [Google Scholar] [CrossRef]
- Perera, C.; McCormick, C.; Bandara, A.; Price, B.; Nuseibeh, B. Privacy-by-Design Framework for Assessing Internet of Things Applications and Platforms. arXiv 2016, arXiv:1609.04060v1. [Google Scholar]
- Condry, M.W.; Nelson, C.B. Using Smart Edge IoT Devices for Safer, Rapid Response with Industry IoT Control Operations. Proc. IEEE 2016, 104, 938–946. [Google Scholar] [CrossRef]
- Hwang, Y. IoT Security and Privacy: Threats and Challenges. In Proceedings of the 1st ACM Workshop on IoT Privacy, Trust, and Security, Singapore, 14–17 April 2015; ACM: New York, NY, USA, 2015; p. 1. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V.; Rabehaja, T. Fine-grained access control for smart healthcare systems in the Internet of Things. EAI Endorsed Trans. Ind. Netw. Intell. Syst. 2018, 4, e5. [Google Scholar] [CrossRef] [Green Version]
- Gupta, B.B.; Tewari, A.; Jain, A.; Agrawal, D. Fighting against phishing attacks: State of the art and future challenges. Neural Comput. Appl. 2017, 28, 3629–3654. [Google Scholar] [CrossRef]
- Mattern, F.; Floerkemeier, C. From the Internet of Computers to the Internet of Things. In From Active Data Management to Event-Based Systems and More; Sachs, K., Petrov, I., Guerrero, P., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6462, pp. 242–259. [Google Scholar] [CrossRef]
- Nahrstedt, K.; Li, H.; Nguyen, P.; Chang, S.; Vu, L. Internet of Mobile Things: Mobility-Driven Challenges, Designs and Implementations. In Proceedings of the First International Conference on Internet-of-Things Design and Implementation (IoTDI), Berlin, Germany, 4–8 April 2016; pp. 25–36. [Google Scholar] [CrossRef]
- Satyanarayanan, M.; Simoens, P.; Xiao, Y.; Pillai, P.; Chen, Z.; Ha, K.; Hu, W.; Amos, B. Edge Analytics in the Internet of Things. IEEE Pervasive Comput. 2015, 14, 24–31. [Google Scholar] [CrossRef] [Green Version]
- Ahmadian, Z.; Salmasizadeh, M.; Aref, M.R. Desynchronization attack on RAPP ultralightweight authentication protocol. Inf. Process. Lett. 2013, 113, 205–209. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef] [Green Version]
- Palattella, M.R.; Dohler, M.; Grieco, A.; Rizzo, G.; Torsner, J.; Engel, T.; Ladid, L. Internet of Things in the 5G Era: Enablers, Architecture, and Business Models. IEEE J. Sel. Areas Commun. 2016, 34, 510–527. [Google Scholar] [CrossRef] [Green Version]
- Guinard, D.; Trifa, V.; Karnouskos, S.; Spiess, P.; Savio, D. Interacting with the SOA-Based Internet of Things: Discovery, Query, Selection, and On-Demand Provisioning of Web Services. IEEE Trans. Serv. Comput. 2010, 3, 223–235. [Google Scholar] [CrossRef] [Green Version]
- Zhou, L.; Chao, H. Multimedia traffic security architecture for the internet of things. IEEE Netw. 2011, 25, 35–40. [Google Scholar] [CrossRef]
- Bhattacharya, D.; Canul, M.; Knight, S. Case study: Impact of the physical web and BLE beacons. In Proceedings of the 50th Hawaii International Conference on System Sciences, Village, HI, USA, 4–7 January 2017. [Google Scholar]
- Elkhodr, M.; Shahrestani, S.; Cheung, H. The Internet of Things: Vision & Challenges. In Proceedings of the Tencon-Spring, Sydney, Australia, 17–19 April 2013; pp. 218–222. [Google Scholar] [CrossRef]
- Wernke, M.; Skvortsov, P.; Dürr, F.; Rothermel, K. A Classification of Location Privacy Attacks and Approaches. Pers. Ubiquitous Comput. 2014, 18, 163–175. [Google Scholar] [CrossRef]
- Ho, G.; Leung, D.; Mishra, P.; Hosseini, A.; Song, D.; Wagner, D. Smart Locks: Lessons for Securing Commodity Internet of Things Devices. In Proceedings of the 11th Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016; pp. 461–472. [Google Scholar] [CrossRef]
- Christie, C.; Dill, E. Evaluating peers in cyberspace: The impact of anonymity. Comput. Hum. Behav. 2016, 55, 292–299. [Google Scholar] [CrossRef] [Green Version]
- Wright, M.K.; Adler, M.; Levine, B.N.; Shields, C. The Predecessor Attack: An Analysis of a Threat to Anonymous Communications Systems. ACM Trans. Inf. Syst. Secur. 2004, 7, 489–522. [Google Scholar] [CrossRef]
- Gilchrist, A. Industry 4.0: The Industrial Internet of Things; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Weber, R.H. Internet of Things—New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Kalmar, E.; Kertesz, A.; Varadi, S.; Garg, R.; Stiller, B. Legal and Regulative Aspects of IoT Cloud Systems. In Proceedings of the 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 15–20. [Google Scholar] [CrossRef] [Green Version]
- Bader, A.; Ghazzai, H.; Kadri, A.; Alouini, M.S. Front-end intelligence for large-scale application-oriented internet-of-things. IEEE Access 2016, 4, 3257–3272. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Huang, X. Security and privacy techniques for the industrial Internet of Things. In Security and Privacy Trends in the Industrial Internet of Things; Springer: Berlin/Heidelberg, Germany, 2019; pp. 245–268. [Google Scholar]
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; et al. A View of Cloud Computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef] [Green Version]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 13–17 August 2012; ACM: New York, NY, USA, 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Giurgiu, I.; Riva, O.; Juric, D.; Krivulev, I.; Alonso, G. Calling the cloud: Enabling mobile phones as interfaces to cloud applications. In Proceedings of the ACM/IFIP/USENIX 10th International Conference on Middleware, Urbana, IL, USA, 30 November–4 December 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 83–102. [Google Scholar]
- Willig, A.; Matheus, K.; Wolisz, A. Wireless Technology in Industrial Networks. Proc. IEEE 2005, 93, 1130–1151. [Google Scholar] [CrossRef] [Green Version]
- Zeadally, S.; Isaac, J.; Baig, Z. Security Attacks and Solutions in Electronic Health (E-health) Systems. J. Med. Syst. 2016, 40, 263. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V.; Rabehaja, T. On design of a fine-grained access control architecture for securing iot-enabled smart healthcare systems. In Proceedings of the 14th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Melbourne, Australia, 7–10 November 2017; pp. 432–441. [Google Scholar]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- Chang, C.; Srirama, S.N.; Buyya, R. Mobile Cloud Business Process Management System for the Internet of Things: A Survey. ACM Comput. Surv. 2016, 49, 1–42. [Google Scholar] [CrossRef] [Green Version]
- Lhaksmana, K.; Murakami, Y.; Ishida, T. Analysis of Large-Scale Service Network Tolerance to Cascading Failure. IEEE Internet Things J. 2016, 3, 1159–1170. [Google Scholar] [CrossRef]
- Lhaksmana, K.M.; Murakami, Y.; Ishida, T. Cascading Failure Tolerance in Large-Scale Service Networks. In Proceedings of the International Conference on Services Computing, New York, NY, USA, 27 June–2 July 2015; pp. 1–8. [Google Scholar] [CrossRef]
- Yu, S.; Liu, M.; Dou, W.; Liu, X.; Zhou, S. Networking for Big Data: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 531–549. [Google Scholar] [CrossRef]
- Gupta, P.; Alam, M.A. “Challenges in the Adaptation of IoT Technology”—A Fusion of Artificial Intelligence and Internet of Things for Emerging Cyber Systems; Springer: Cham, Switzerland, 2022; pp. 347–369. [Google Scholar]
- O’Leary, D.E. ‘Big data’, the ‘internet of things’ and the ‘internet of signs’. Intell. Syst. Account. Financ. Manag. 2013, 20, 53–65. [Google Scholar] [CrossRef]
- Di Pietro, R.; Guarino, S.; Verde, N.V.; Ferrer, J.D. Review: Security in Wireless Ad-hoc Networks—A Survey. Comput. Commun. 2014, 51, 1–20. [Google Scholar] [CrossRef]
- Li, S.; Xu, L.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V. Towards the design of a trust management framework for the Internet of Things. In Proceedings of the 2019 13th International Conference on Sensing Technology (ICST), Sydney, Australia, 2–4 December 2019; pp. 1–7. [Google Scholar]
- Liu, L.; Liu, T.; Guan, Y.W.; Yan, Y.Q.; Deng, Q.C. A WSN-Oriented Key Agreement Protocol in Internet of Things. Frontiers of Manufacturing Science and Measuring Technology III. Trans Tech Publications. Appl. Mech. Mater. 2013, 401, 1792–1795. [Google Scholar] [CrossRef]
- Kubler, S.; Främling, K.; Buda, A. A standardized approach to deal with firewall and mobility policies in the IoT. Pervasive Mob. Comput. 2015, 20, 100–114. [Google Scholar] [CrossRef]
- Heer, T.; Garcia, O.; Hummen, R.; Keoh, S.; Kumar, S.; Wehrle, K. Security Challenges in the IP-based Internet of Things. Wirel. Pers. Commun. 2011, 61, 527–542. [Google Scholar] [CrossRef] [Green Version]
- Ward, B.T.; Sipior, J.C. The Internet Jurisdiction Risk of Cloud Computing. Inf. Syst. Manag. 2010, 27, 334–339. [Google Scholar] [CrossRef]
- Ren, K.; Lou, W.; Kim, K.; Deng, R. A Novel Privacy Preserving Authentication and Access Control Scheme for Pervasive Computing Environments. IEEE Trans. Veh. Technol. 2006, 55, 1373–1384. [Google Scholar] [CrossRef]
- Wang, F.; Hu, L.; Hu, J.; Zhou, J.; Zhao, K. Recent Advances in the Internet of Things: Multiple Perspectives. IETE Tech. Rev. 2016, 34, 122–132. [Google Scholar] [CrossRef]
- Dong, P.; Guan, J.; Xue, X.; Wang, H. Attack Resistant Trust Management Model Based on Beta Function for Distributed Routing in Internet of Things. China Commun. 2012, 9, 89–98. [Google Scholar]
- Chze, P.; Leong, K. A secure multi-hop routing for IoT communication. In Proceedings of the World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 428–432. [Google Scholar] [CrossRef]
- Chze, P.; Yan, W.; Leong, K. A User-Controllable Multi-Layer Secure Algorithm for MANET. In Proceedings of the 8th International Wireless Communications and Mobile Computing Conference (IWCMC), Limassol, Cyprus, 27–31 August 2012; pp. 1080–1084. [Google Scholar] [CrossRef]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar] [CrossRef]
- Peng, L.; Ruchuan, W.; Xiaoyu, S.; Long, C. Privacy Protection Based on Key-changed Mutual Authentication Protocol in Internet of Things. In Advances in Wireless Sensor Networks; Sun, L., Ma, H., Hong, F., Eds.; Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 418, pp. 345–355. [Google Scholar] [CrossRef]
- Huang, X.; Fu, R.; Chen, B.; Zhang, T. User interactive Internet of things privacy preserved access control. In Proceedings of the 7th International Conference for Internet Technology and Secured Transactions, London, UK, 10–12 December 2012; pp. 597–602. [Google Scholar]
- Ferraiolo, D.; Sandhu, R.; Gavrila, S.; Kuhn, R.; Chandramouli, R. Proposed NIST Standard for Role-based Access Control. ACM Trans. Inf. Syst. Secur. 2001, 4, 224–274. [Google Scholar] [CrossRef]
- Li, S.; Gong, P.; Yang, Q.; Li, M.; Kong, J.; Li, P. A secure handshake scheme for mobile-hierarchy city intelligent transportation system. In Proceedings of the Fifth International Conference on Ubiquitous and Future Networks (ICUFN), Da Nang, Vietnam, 2–5 July 2013; pp. 190–191. [Google Scholar] [CrossRef]
- Diro, A.; Reda, H.; Chilamkurti, N.; Mahmood, A.; Zaman, N.; Nam, Y. Lightweight authenticated-encryption scheme for Internet of Things based on publish-subscribe communication. IEEE Access 2020, 8, 60539–60551. [Google Scholar] [CrossRef]
- Isa, M.; Mohamed, N.; Hashim, H.; Adnan, S.; Manan, J.; Mahmod, R. A lightweight and secure TFTP protocol for smart environment. In Proceedings of the International Symposium on Computer Applications and Industrial Electronics (ISCAIE), Kota Kinabalu, Malaysia, 3–4 December 2012; pp. 302–306. [Google Scholar] [CrossRef]
- Bao, F.; Chen, I. Dynamic Trust Management for Internet of Things Applications. In Proceedings of the International Workshop on Self-aware Internet of Things, Grenoble, France, 7–10 July 2012; ACM: New York, NY, USA, 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Su, J.; Cao, D.; Zhao, B.; Wang, X.; You, I. ePASS: An expressive attribute-based signature scheme with privacy and an unforgeability guarantee for the Internet of Things. Future Gener. Comput. Syst. 2014, 33, 11–18. [Google Scholar] [CrossRef]
- Carminati, B.; Ferrari, E.; Cao, J.; Tan, K. A Framework to Enforce Access Control over Data Streams. ACM Trans. Inf. Syst. Secur. 2010, 13, 1–31. [Google Scholar] [CrossRef] [Green Version]
- Jun, M.; Yuanbo, G.; Jianfeng, M.; Jinbo, X.; Tao, Z. A Hierarchical Access Control Scheme for Perceptual Layer of IoT. J. Comput. Res. Dev. 2013, 50, 1267–1275. [Google Scholar]
- Ukil, A.; Bandyopadhyay, S.; Pal, A. IoT-Privacy: To be private or not to be private. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 27 April–2 May 2014; pp. 123–124. [Google Scholar] [CrossRef]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brünig, M.; Carle, G. DTLS based security and two-way authentication for the Internet of Things. Ad Hoc Netw. 2013, 11, 2710–2723. [Google Scholar] [CrossRef]
- Jebri, S.; Abid, M.; Bouallegue, A. An efficient scheme for anonymous communication in IoT. In Proceedings of the 11th International Conference on Information Assurance and Security (IAS), Marrakech, Morocco, 14–16 December 2015; pp. 7–12. [Google Scholar] [CrossRef]
- Hernandez-Ramos, J.; Jara, A.; Marın, L.; Skarmeta, A. Distributed Capability-based Access Control for the Internet of Things. J. Internet Serv. Inf. Secur. 2013, 3, 1–16. [Google Scholar]
- Mahalle, P.N.; Anggorojati, B.; Prasad, N.R.; Prasad, R. Identity Authentication and Capability Based Access Control (IACAC) for the Internet of Things. J. Cyber Secur. Mobil. 2013, 1, 309–348. [Google Scholar]
- Hong, N. A Security Framework for the Internet of Things Based on Public Key Infrastructure. In Information Technologies in Construction and Industry; Huang, Y., Bao, T., Wang, H., Eds.; Trans Tech Publications Ltd.: Freinbach, Switzerland, 2013; Volume 671, pp. 3223–3226. [Google Scholar]
- Hassaballah, M.; Hameed, M.A.; Awad, A.I.; Muhammad, K. A Novel Image Steganography Method for Industrial Internet of Things Security. IEEE Trans. Ind. Inform. 2021, 17, 7743–7751. [Google Scholar] [CrossRef]
- Prinsloo, J.; Sinha, S.; von Solms, B. A review of industry 4.0 manufacturing process security risks. Appl. Sci. 2019, 9, 5105. [Google Scholar] [CrossRef] [Green Version]
- Xenofontos, C.; Zografopoulos, I.; Konstantinou, C.; Jolfaei, A.; Khan, M.K.; Choo, K.K.R. Consumer, commercial and industrial iot (in) security: Attack taxonomy and case studies. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Ainsworth, T.; Brake, J.; Gonzalez, P.; Toma, D.; Browne, A.F. A Comprehensive Survey of Industry 4.0, IIoT and Areas of Implementation. In Proceedings of the SoutheastCon 2021, Atlanta, GA, USA, 10–13 March 2021; pp. 1–6. [Google Scholar]
- Bécue, A.; Praça, I.; Gama, J. Artificial intelligence, cyber-threats and Industry 4.0: Challenges and opportunities. Artif. Intell. Rev. 2021, 54, 3849–3886. [Google Scholar] [CrossRef]
- Leng, J.; Wang, D.; Shen, W.; Li, X.; Liu, Q.; Chen, X. Digital twins-based smart manufacturing system design in Industry 4.0: A review. J. Manuf. Syst. 2021, 60, 119–137. [Google Scholar] [CrossRef]
- Horak, T.; Strelec, P.; Huraj, L.; Tanuska, P.; Vaclavova, A.; Kebisek, M. The vulnerability of the production line using industrial IoT systems under ddos attack. Electronics 2021, 10, 381. [Google Scholar] [CrossRef]
- Zelbst, P.J.; Green, K.W.; Sower, V.E.; Bond, P.L. The impact of RFID, IIoT, and Blockchain technologies on supply chain transparency. J. Manuf. Technol. Manag. 2019, 31, 441–457. [Google Scholar] [CrossRef]
- Iqbal, A.; Amir, M.; Kumar, V.; Alam, A.; Umair, M. Integration of next generation IIoT with Blockchain for the development of smart industries. Emerg. Sci. J. 2020, 4, 1–17. [Google Scholar] [CrossRef]
- Seitz, A.; Henze, D.; Miehle, D.; Bruegge, B.; Nickles, J.; Sauer, M. Fog computing as enabler for blockchain-based IIoT app marketplaces-A case study. In Proceedings of the 2018 Fifth International Conference on Internet of Things: Systems, Management and Security, Valencia, Spain, 15–18 October 2018; pp. 182–188. [Google Scholar]
- Puri, V.; Priyadarshini, I.; Kumar, R.; Kim, L.C. Blockchain meets IIoT: An architecture for privacy preservation and security in IIoT. In Proceedings of the 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA), Gunupur, India, 13–14 March 2020; pp. 1–7. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetrò, A.; Martin, J.C.D. Blockchain for the Internet of Things: A systematic literature review. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Dhar, S.; Bose, I. Securing IoT Devices Using Zero Trust and Blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Vanickis, R.; Jacob, P.; Dehghanzadeh, S.; Lee, B. Access control policy enforcement for zero-trust-networking. In Proceedings of the 2018 29th Irish Signals and Systems Conference (ISSC), Belfast, UK, 21–22 June 2018; pp. 1–6. [Google Scholar]
- Pal, S.; Rabehaja, T.; Hitchens, M.; Varadharajan, V.; Hill, A. On the design of a flexible delegation model for the Internet of Things using blockchain. IEEE Trans. Ind. Inform. 2019, 16, 3521–3530. [Google Scholar] [CrossRef]
- Pal, S.; Rabehaja, T.; Hill, A.; Hitchens, M.; Varadharajan, V. On the integration of blockchain to the internet of things for enabling access right delegation. IEEE Internet Things J. 2019, 7, 2630–2639. [Google Scholar] [CrossRef]
- Banaie, F.; Hashemzadeh, M. Complementing IIoT Services through AI: Feasibility and Suitability. In AI-Enabled Threat Detection and Security Analysis for Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 7–19. [Google Scholar]
- Angelopoulos, A.; Michailidis, E.T.; Nomikos, N.; Trakadas, P.; Hatziefremidis, A.; Voliotis, S.; Zahariadis, T. Tackling faults in the industry 4.0 era—A survey of machine-learning solutions and key aspects. Sensors 2020, 20, 109. [Google Scholar] [CrossRef] [Green Version]
- Sharma, P.; Jain, S.; Gupta, S.; Chamola, V. Role of machine learning and deep learning in securing 5G-driven industrial IoT applications. Ad Hoc Netw. 2021, 123, 102685. [Google Scholar] [CrossRef]
- Khoda, M.E.; Imam, T.; Kamruzzaman, J.; Gondal, I.; Rahman, A. Robust malware defense in industrial IoT applications using machine learning with selective adversarial samples. IEEE Trans. Ind. Appl. 2019, 56, 4415–4424. [Google Scholar] [CrossRef]
- Aboelwafa, M.M.; Seddik, K.G.; Eldefrawy, M.H.; Gadallah, Y.; Gidlund, M. A machine-learning-based technique for false data injection attacks detection in industrial IoT. IEEE Internet Things J. 2020, 7, 8462–8471. [Google Scholar] [CrossRef]
- Geluvaraj, B.; Satwik, P.; Kumar, T.A. The future of cybersecurity: Major role of artificial intelligence, machine learning, and deep learning in cyberspace. In International Conference on Computer Networks and Communication Technologies; Springer: Berlin/Heidelberg, Germany, 2019; pp. 739–747. [Google Scholar]







| IIoT Architectural Layer | Security Issues | Potential Countermeasures |
|---|---|---|
| Perception | Attack on Physical Devices | The devices’ hardware must be checked and evaluated frequently [140]. In addition, the hardware components should meet the standard (e.g., NIST, FIPS, etc.). |
| Impact on Devices’ Performance | Employment of identity0based trust management model for trusted data sharing is beneficial [143]. | |
| Anonymity | Mobility-aware policy-based security techniques, e.g., Quantum Lifecycle Management (QLM), can be employed [144], and IP-based security management protocols that are usable to a distributed system can be used for achieving end-to-end encryption [145]. | |
| Cross-Domain Jurisdictions | Privacy-preserving authentication and data control schemes can be employed for cross-domain jurisdictions [147]. | |
| Network | Controlling Over Communication | An attack-resistance trust-management-based routing protocol can be employed for a reliable trust relationship [149], and a context-aware, secure multi-hop routing protocol can also be employed [150]. |
| Infecting Data Packets | Intrusion detection system (IDS)-based security architecture can be used [152]. | |
| Flooding Attacks | Privacy-preserving data mining (PPDM) techniques can be placed [153]. | |
| Heterogeneity of Networks | A privacy preserved access control protocol can be employed [154]. | |
| Non-Trusted Network Connections | A secure mobile handshake mechanism that verifies insecure mobile nodes over an insecure channel using attribute-based encryption matching handshaking scheme can be used [156]. | |
| Dynamic Infrastructure | A lightweight and end-to-end security mechanism with less overheads, e.g., [157], can be used. | |
| Support | Flooding Attacks | A light weight security and privacy enhanced middleware infrastructure can be employed [158]. |
| Impact on Devices’ Performance | A secure and dynamic trust-management system based on a dynamic trust management protocol can be used [159]. | |
| Device Impersonation | An attribute-based signature scheme that supports user’s privacy can be employed [160]. | |
| Data Confidentiality | Policy-based access control mechanisms e.g., [161], can be enforced. | |
| Heterogeneity of Networks | A privacy-preserving access control protocol can be employed [154]. | |
| Cascading Services | A hierarchical access control model, e.g., [162], can be exercised for resource-limited devices. | |
| Application | Privacy | A privacy-preserving data mining technique that helps to minimize sensitive data disclosure can be employed [163]. |
| Heterogeneity of Networks | A two-way authentication scheme can be used that absorbs the existing Internet standards, specifically the Datagram Transport Layer Security (DTLS) protocol [164]. | |
| Anonymity | An identity-based encryption scheme, e.g., [165] can be used that helps to detect anonymous communications. | |
| Heterogeneous Infrastructure | A distributed capability-based access control (DCapBAC) framework for IIoT devices can be employed [166]. | |
| Cascading Services | A capability-based delegation model for the federated networks can be employed [167]. | |
| Emergence of Resources | Cryptography-based security mechanism, for instance, that involves public key infrastructure (PKI), can be used [168]. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pal, S.; Jadidi, Z. Analysis of Security Issues and Countermeasures for the Industrial Internet of Things. Appl. Sci. 2021, 11, 9393. https://doi.org/10.3390/app11209393
Pal S, Jadidi Z. Analysis of Security Issues and Countermeasures for the Industrial Internet of Things. Applied Sciences. 2021; 11(20):9393. https://doi.org/10.3390/app11209393
Chicago/Turabian StylePal, Shantanu, and Zahra Jadidi. 2021. "Analysis of Security Issues and Countermeasures for the Industrial Internet of Things" Applied Sciences 11, no. 20: 9393. https://doi.org/10.3390/app11209393
APA StylePal, S., & Jadidi, Z. (2021). Analysis of Security Issues and Countermeasures for the Industrial Internet of Things. Applied Sciences, 11(20), 9393. https://doi.org/10.3390/app11209393







