A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher
Abstract
:1. Introduction
1.1. Existing Solutions with Respect to Side-Channel Attacks and Their Countermeasures
1.2. Limitations
1.3. Our Contributions
- Setting to apply DPA attack. To execute the DPA attack on modern low-power FPGA devices, a large number of power traces are required. This results in an increase in the correlation calculation time. Therefore, to reduce this calculation time, we proposed our custom correlation technique (details are given in Section 3.1).
- Secret key identification using DPA attack. We applied the DPA attack (our custom correlation technique) on our FPGA implementation to obtain the secret key by measuring the power traces of the computations involved in the AES algorithm.
- Countermeasure to mitigate the DPA attacks. To provide resistance against DPA attacks, we provided a countermeasure using Boolean and multiplicative masking for the linear (i.e., ShiftRows, MixColumns, and AddRoundkey) and non-linear functions (i.e., SubBytes) of the AES, respectively. The descriptions are given in Section 3.2.
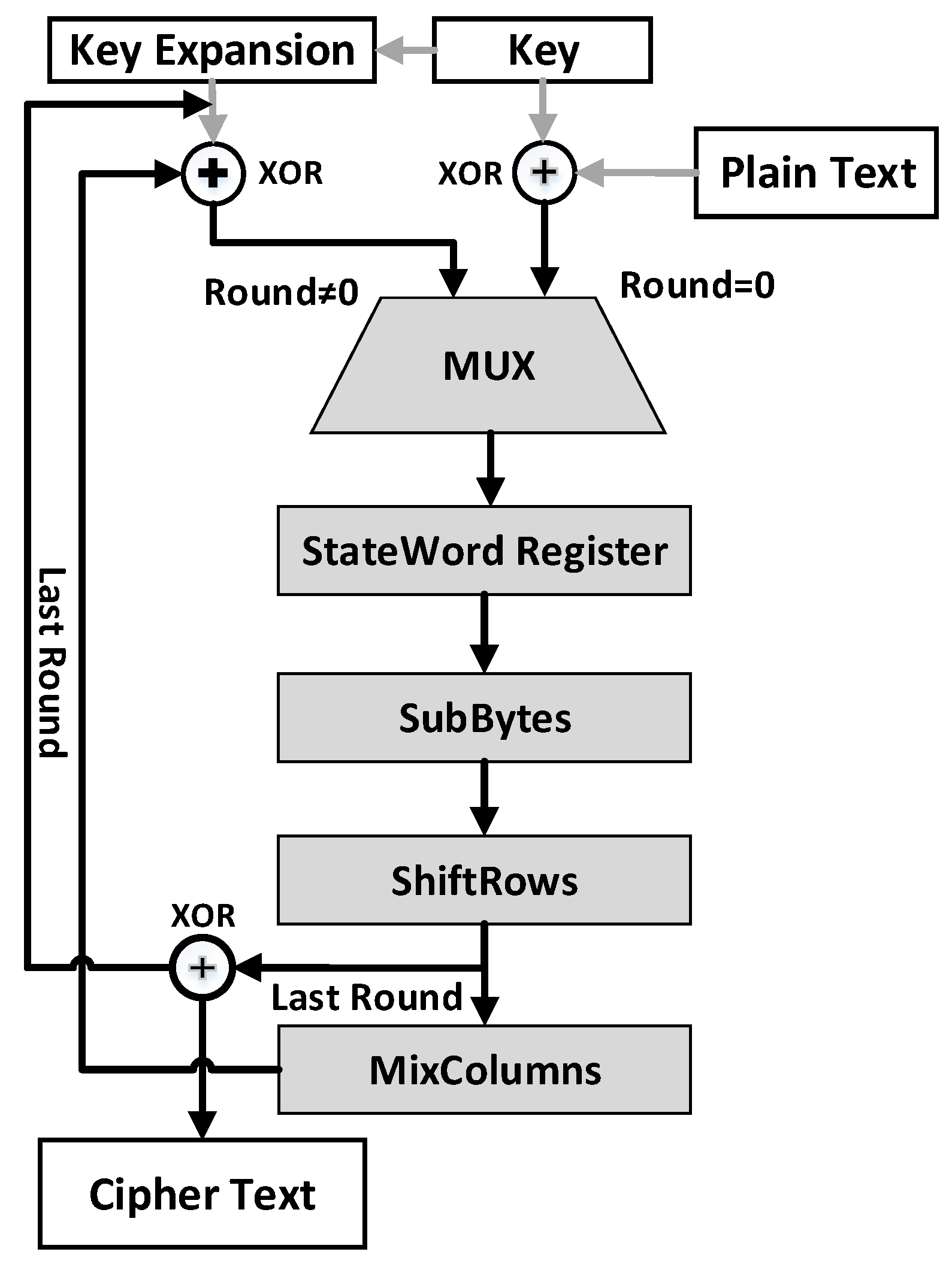
2. Preliminaries
- SubBytes splits the input data into bytes and then passes the input byte by byte through the substitution box (S-box). It is a non-linear substitution.
- ShiftRows determines each row of the 128-bit internal state of the cipher shifted by the fixed amount.
- MixColumns provides diffusion to the AES. It performs linear transformation, which makes AES secure against many attacks.
- AddRoundKey is responsible for performing a bitwise exclusive-OR (XOR) operation in each round.
3. DPA Attack and Our Proposed Countermeasure
3.1. DPA Attack
3.1.1. Pearson Correlation
3.1.2. Our Proposed Custom Correlation Algorithm
| Algorithm 1: Proposed custom correlation algorithm. |
Input: a), b Output:
|
3.2. Our Proposed Countermeasure
3.2.1. Multiplicative Masking
3.2.2. Boolean Masking
4. Implementation Results
4.1. Experimental Setup
4.2. Area and Timing Results
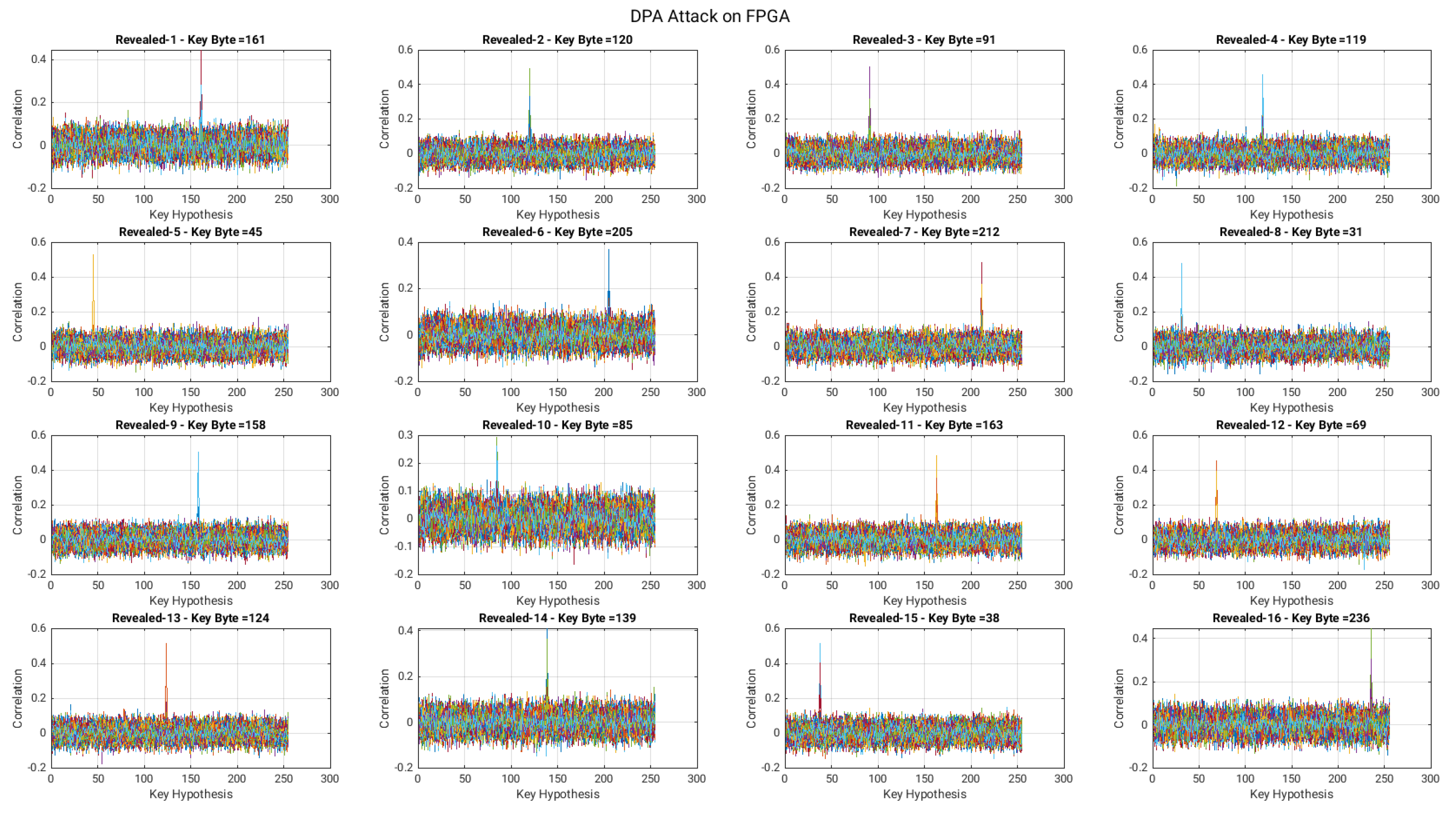
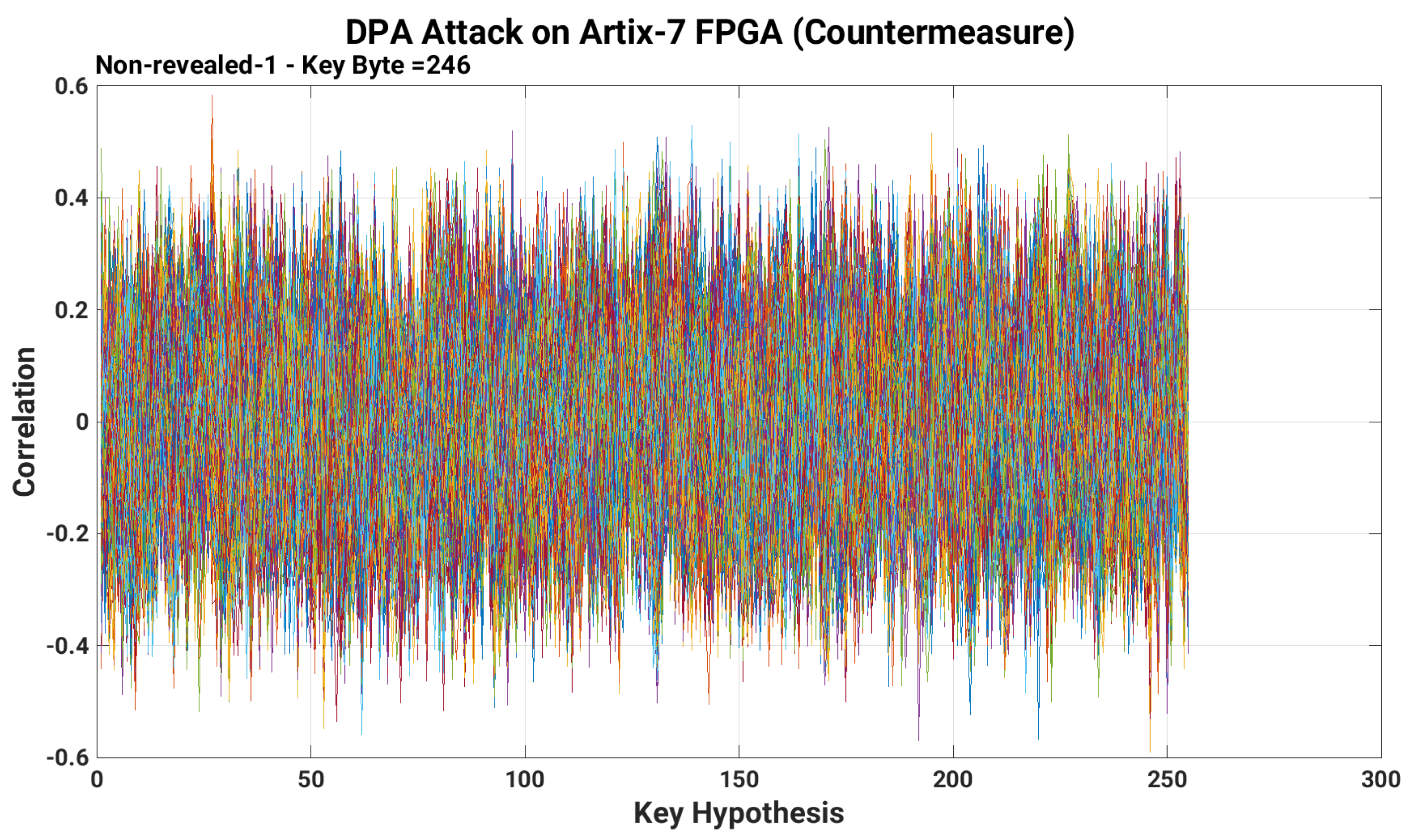
4.3. Secret Key Identification and Prevention against DPA Attacks
5. Limitations of This Work
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A. Retrieval and Prevention of a 128-Bit Secret Key

References
- Imran, M.; Rashid, M.; Raza Jafri, A.; Najam-ul-Islam, M. ACryp-Proc: Flexible Asymmetric Crypto Processor for Point Multiplication. IEEE Access 2018, 6, 22778–22793. [Google Scholar] [CrossRef]
- Coron, J.S. What is cryptography? IEEE Secur. Priv. 2006, 4, 70–73. [Google Scholar] [CrossRef]
- Rashid, M.; Imran, M.; Jafri, A.R.; Al-Somani, T.F. Flexible Architectures for Cryptographic Algorithms—A Systematic Literature Review. J. Circuits Syst. Comput. 2019, 28, 1930003. [Google Scholar] [CrossRef]
- Chandra, S.; Paira, S.; Alam, S.S.; Sanyal, G. A comparative survey of Symmetric and Asymmetric Key Cryptography. In Proceedings of the 2014 International Conference on Electronics, Communication and Computational Engineering (ICECCE), Hosur, India, 17–18 November 2014; pp. 83–93. [Google Scholar] [CrossRef]
- Yilmaz, B.; Özdemİr, S. Performance comparison of cryptographic algorithms in internet of things. In Proceedings of the 2018 26th Signal Processing and Communications Applications Conference (SIU), Izmir, Turkey, 2–5 May 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Kumar, K.; Ramkumar, K.; Kaur, A.; Choudhary, S. A Survey on Hardware Implementation of Cryptographic Algorithms Using Field Programmable Gate Array. In Proceedings of the 2020 IEEE 9th International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 10–12 April 2020; pp. 189–194. [Google Scholar] [CrossRef]
- Socha, P.; Brejník, J.; Bartik, M. Attacking AES implementations using correlation power analysis on ZYBO Zynq-7000 SoC board. In Proceedings of the 2018 7th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 10–14 June 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Bhunia, S.; Tehranipoor, M. Chapter 10: Physical Attacks and Countermeasures. In Hardware Security; Bhunia, S., Tehranipoor, M., Eds.; Morgan Kaufmann: Cambridge, MA, USA, 2019; pp. 245–290. [Google Scholar] [CrossRef]
- Mangard, S.; Oswald, E.; Popp, T. Revealing the Secrets of Smart Cards. In Power Analysis Attacks; Springer: Boston, MA, USA, 2007; p. XXIV–338. [Google Scholar] [CrossRef]
- Pammu, A.A.; Chong, K.; Ho, W.; Gwee, B. Interceptive side channel attack on AES-128 wireless communications for IoT applications. In Proceedings of the 2016 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), Jeju, Korea, 25–28 October 2016; pp. 650–653. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, K.; Zhang, Y.; Gui, W.; Li, L. Correlation power analysis for AES encryption device. In Proceedings of the 4th National Conference on Electrical, Electronics and Computer Engineering, Xi’an, China, 12–13 December 2015; pp. 7–12. Available online: https://www.atlantis-press.com/article/25847048.pdf (accessed on 3 September 2021).
- Zheng, Z.; Zou, X.; Liu, Z.; Chen, Y. Security Analysis and Optimization of AES S-Boxes Against CPA Attack in Wireless Sensor Network. In Proceedings of the 2007 International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 21–25 September 2007; pp. 2608–2612. [Google Scholar] [CrossRef]
- Benhadjyoussef, N.; Mestiri, H.; Machhout, M.; Tourki, R. Implementation of CPA analysis against AES design on FPGA. In Proceedings of the 2012 International Conference on Communications and Information Technology (ICCIT), Hammamet, Tunisia, 26–28 June 2012; pp. 124–128. [Google Scholar] [CrossRef]
- Jaffe, J. A First-Order DPA Attack Against AES in Counter Mode with Unknown Initial Counter. In Cryptographic Hardware and Embedded Systems—CHES 2007; Paillier, P., Verbauwhede, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–13. Available online: https://www.iacr.org/archive/ches2007/47270001/47270001.pdf (accessed on 19 September 2021).
- Lu, J.; Pan, J.; den Hartog, J. Principles on the Security of AES against First and Second-Order Differential Power Analysis. In Applied Cryptography and Network Security; Zhou, J., Yung, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 168–185. Available online: https://link.springer.com/chapter/10.1007/978-3-642-13708-2_11 (accessed on 7 August 2021).
- Kamoun, N.; Bossuet, L.; Ghazel, A. Experimental implementation of DPA attacks on AES design with Flash-based FPGA technology. In Proceedings of the 2009 6th International Multi-Conference on Systems, Signals and Devices, Djerba, Tunisia, 23–26 March 2009; pp. 1–4. [Google Scholar] [CrossRef]
- Han, Y.; Zou, X.; Zhenglin, L.; Chen, Y. Efficient DPA Attacks on AES Hardware Implementations. IJCNS 2008, 1, 68–73. [Google Scholar] [CrossRef] [Green Version]
- Bu, A.; Dai, W.; Lu, M.; Cai, H.; Shan, W. Correlation-Based Electromagnetic Analysis Attack Using Haar Wavelet Reconstruction with Low-Pass Filtering on an FPGA Implementaion of AES. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1897–1900. [Google Scholar] [CrossRef]
- Wang, H.; Dubrova, E. Tandem Deep Learning Side-Channel Attack Against FPGA Implementation of AES. In Proceedings of the 2020 IEEE International Symposium on Smart Electronic Systems (iSES) (Formerly iNiS), Chennai, India, 14–16 December 2020; pp. 147–150. [Google Scholar] [CrossRef]
- Khelil, F.; Hamdi, M.; Guilley, S.; Danger, J.L.; Selmane, N. Fault Analysis Attack on an FPGA AES Implementation. In Proceedings of the 2008 New Technologies, Mobility and Security, Tangier, Morocco, 5–7 November 2008; pp. 1–5. [Google Scholar] [CrossRef]
- Kaps, J.P.; Velegalati, R. DPA Resistant AES on FPGA Using Partial DDL. In Proceedings of the 2010 18th IEEE Annual International Symposium on Field-Programmable Custom Computing Machines, Charlotte, NC, USA, 2–4 May 2010; pp. 273–280. [Google Scholar] [CrossRef]
- Zhang, S.; Zhong, W. A New Type of Countermeasure against DPA in Multi-Sbox of Block Cipher. Wirel. Commun. Mob. Comput. 2018, 2018, 5945312. [Google Scholar] [CrossRef] [Green Version]
- Babu, G.D.; Anandakumar, N.N.; Muralidharan, D. Countermeasures Against DPA Attacks on FPGA Implementation of AES. J. Artif. Intell. 2012, 5, 186–192. [Google Scholar] [CrossRef]
- Attaran, A.; Mirhassani, M. An embedded low-overhead PLL-based countermeasure against DPA side channel attack. In Proceedings of the 2015 International Symposium on Signals, Circuits and Systems (ISSCS), Iasi, Romania, 9–10 July 2015; pp. 1–4. [Google Scholar] [CrossRef]
- Mohana, P.; Srinivasan, R.; Kanchana Bhaaskaran, V.S. An energy recovery logic level countermeasure for power analysis attacks on AES. In Proceedings of the International Conference on Smart Structures And Systems (ICSSS’13), Chennai, India, 28–29 March 2013; pp. 164–170. [Google Scholar] [CrossRef]
- Lo, O.; Buchanan, W.J.; Carson, D. Power analysis attacks on the AES-128 S-box using differential power analysis (DPA) and correlation power analysis (CPA). J. Cyber Secur. Technol. 2017, 1, 88–107. [Google Scholar] [CrossRef] [Green Version]
- Kavi priya, S.; Arunmani, G. Advanced Logic Level Design Methodology for a Secure DPA Resistant FPGA. In Proceedings of the 2019 IEEE International Conference on Intelligent Techniques in Control, Optimization and Signal Processing (INCOS), Tamilnadu, India, 11–13 April 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Yu, W.; Köse, S. A Voltage Regulator-Assisted Lightweight AES Implementation Against DPA Attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2016, 63, 1152–1163. [Google Scholar] [CrossRef]
- Tiri, K.; Verbauwhede, I. Securing Encryption Algorithms against DPA at the Logic Level: Next Generation Smart Card Technology. In Cryptographic Hardware and Embedded Systems—CHES 2003; Walter, C.D., Koç, Ç.K., Paar, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 125–136. Available online: https://link.springer.com/chapter/10.1007/978-3-540-45238-6_11 (accessed on 10 July 2021).
- Discretix Technologies Ltd. Known Attacks against Smart Cards. 2021. Available online: http://www.infosecwriters.com/text_resources/pdf/Known_Attacks_Against_Smartcards.pdf (accessed on 19 October 2021).
- Eduard Kovacs. Researchers Disclose New Side-Channel Attacks Affecting All AMD CPUs. 2021. Available online: https://www.securityweek.com/researchers-disclose-new-side-channel-attacks-affecting-all-amd-cpus?quicktabs_1=0 (accessed on 19 October 2021).
- Zybo Z7. AES (Rijndael) IP Core. 2018. Available online: https://opencores.org/projects/aes_core (accessed on 3 May 2021).
- Daemen, J.; Rijmen, V. The Design of Rijndael: AES—The Advanced Encryption Standard; Springer: Berlin/Heidelberg, Germany, 2002; p. XVII–238. Available online: https://www.springer.com/gp/book/9783540425809 (accessed on 24 July 2021).
- Pitchaiah, M.; Daniel, D. Implementation of Advanced Encryption Standard Algorithm. Int. J. Sci. Eng. Res. 2012, 3, 14–17. Available online: https://www.ijser.org/researchpaper/Implementation-of-Advanced-Encryption-Standard-Algorithm.pdf (accessed on 21 July 2021).
- Miškovský, V.; Kubátová, H.; Novotný, M. Influence of fault-tolerant design methods on differential power analysis resistance of AES cipher: Methodics and challenges. In Proceedings of the 2016 5th Mediterranean Conference on Embedded Computing (MECO), Bar, Montenegro, 12–16 June 2016; pp. 14–17. [Google Scholar] [CrossRef]
- Ordu, L.; Ors, B. Power Analysis Resistant Hardware Implementations of AES. In Proceedings of the 2007 14th IEEE International Conference on Electronics, Circuits and Systems, Marrakech, Morocco, 11–14 December 2007; pp. 1408–1411. [Google Scholar] [CrossRef]
- Ming, J.; Zhou, Y.; Li, H.; Zhang, Q. A secure and highly efficient first-order masking scheme for AES linear operations. Cybersecurity 2021, 4, 1408–1411. [Google Scholar] [CrossRef]
- Trichina, E.; De Seta, D.; Germani, L. Simplified Adaptive Multiplicative Masking for AES. In Cryptographic Hardware and Embedded Systems—CHES 2002; Kaliski, B.S., Koç, Ç.K., Paar, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 187–197. Available online: https://link.springer.com/content/pdf/10.1007%2F3-540-36400-5_15.pdf (accessed on 11 May 2021).
- De Meyer, L.; Reparaz, O.; Bilgin, B. Multiplicative Masking for AES in Hardware. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 431–468. [Google Scholar] [CrossRef]
- O’Donnell, R. Analysis of Boolean Functions. 2014. Available online: https://www.cs.tau.ac.il/~amnon/Classes/2016-PRG/Analysis-Of-Boolean-Functions.pdf (accessed on 18 October 2021).
- Zybo Z7. Zybo Z7: Zynq-7000 ARM/FPGA SoC Development Board. 2020. Available online: https://digilent.com/reference/_media/reference/programmable-logic/zybo-z7/zybo_z7_sch-public.pdf (accessed on 19 August 2021).
- Mulani, A.O.; Mane, P.B. High-Speed Area-Efficient Implementation of AES Algorithm on Reconfigurable Platform, 2019. In Computer and Network Security; IntechOpen: London, UK, 2019; Available online: https://www.intechopen.com/chapters/67728 (accessed on 20 July 2020). [CrossRef] [Green Version]
- Kamoun, N.; Bossuet, L.; Ghazel, A. SRAM-FPGA implementation of masked S-Box based DPA countermeasure for AES. In Proceedings of the 2008 3rd International Design and Test Workshop, Monastir, Tunisia, 20–22 December 2008; pp. 74–77. [Google Scholar] [CrossRef]



| Designs | Freq. | Utilized Area | Clock Cycles | |||
|---|---|---|---|---|---|---|
| Slices | LUTs | FFs | ENC | DEC | ||
| DESIGN-I | 250 | 424 | 1314 | 538 | 12 | 12 |
| DESIGN-II | 205 (−18%) | 714 (+68%) | 2110 (+60%) | 1089 (+102%) | 12 | 12 |
| # of KeyBytes | Key Values (In Different Representations) | Correlation | |
|---|---|---|---|
| (In Decimal) | (In Hexadecimal) | ||
| KeyByte 1 | 161 | A1 | 0.445 |
| KeyByte 2 | 120 | 78 | 0.493 |
| KeyByte 3 | 91 | 5B | 0.502 |
| KeyByte 4 | 119 | 77 | 0.45 |
| KeyByte 5 | 45 | 2D | 0.525 |
| KeyByte 6 | 205 | CD | 0.356 |
| KeyByte 7 | 212 | D4 | 0.481 |
| KeyByte 8 | 31 | 1F | 0.478 |
| KeyByte 9 | 158 | 9E | 0.505 |
| KeyByte 10 | 85 | 55 | 0.293 |
| KeyByte 11 | 163 | A3 | 0.481 |
| KeyByte 12 | 69 | 45 | 0.45 |
| KeyByte 13 | 124 | 7C | 0.513 |
| KeyByte 14 | 139 | 8B | 0.41 |
| KeyByte 15 | 38 | 26 | 0.512 |
| KeyByte 16 | 236 | EC | 0.447 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Asfand Hafeez, M.; Mazyad Hazzazi , M.; Tariq, H.; Aljaedi, A.; Javed, A.; Alharbi, A.R. A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher. Appl. Sci. 2021, 11, 10314. https://doi.org/10.3390/app112110314
Asfand Hafeez M, Mazyad Hazzazi M, Tariq H, Aljaedi A, Javed A, Alharbi AR. A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher. Applied Sciences. 2021; 11(21):10314. https://doi.org/10.3390/app112110314
Chicago/Turabian StyleAsfand Hafeez, Muhammad, Mohammad Mazyad Hazzazi , Hassan Tariq, Amer Aljaedi, Asfa Javed, and Adel R. Alharbi. 2021. "A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher" Applied Sciences 11, no. 21: 10314. https://doi.org/10.3390/app112110314
APA StyleAsfand Hafeez, M., Mazyad Hazzazi , M., Tariq, H., Aljaedi, A., Javed, A., & Alharbi, A. R. (2021). A Low-Overhead Countermeasure against Differential Power Analysis for AES Block Cipher. Applied Sciences, 11(21), 10314. https://doi.org/10.3390/app112110314








