Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research
Abstract
1. Introduction
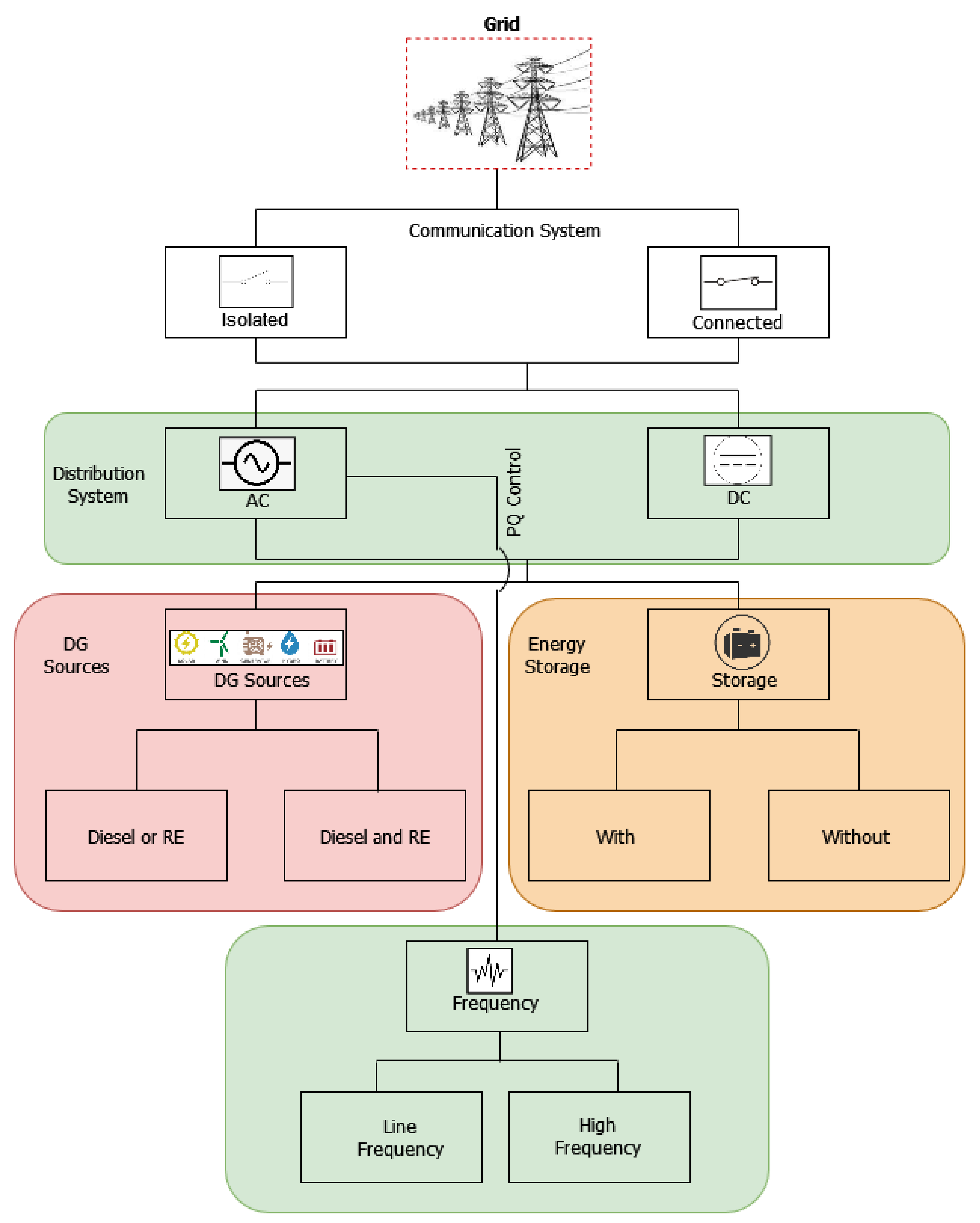
2. The Microgrid Architecture
- (A)
- Enclave 1: DG sourcesDG source refers to technologies that generate power such as:
- GeneratorOne of the sources of energy to a microgrid is the synchronous generator. Most of them are powered by natural gas or a diesel engine designed for stand-alone or backup applications. A generator has two control algorithms, namely, an (1) exciter, which handles the voltage of the generator, and the (2) reactive power generator that is commonly used to minimise power loss and improve the voltage profile of power systems.
- Natural gas turbineThe natural gas turbine is categorised based on the drive type, into single shaft and two shaft. The single-shaft light is generally used in microgrid systems as a distributed resource. To enhance the response speed, the governor control system uses an electronic control system. The gain and time are constantly monitored to achieve a reasonable response.
- Renewable energy sourceRenewable energy plays an essential role in maintaining the sustainability and survival of the microgrid. The prevalent sources of renewable energy are wind and photovoltaic. They are connected to the microgrid system through current-mode inverters, and can be operated at the maximum power point.
- (B)
- Enclave 2: Energy storageThe reliability of the operations, power generation, and load stabilisation of the microgrid is ensured through a sophisticated storage management system, an indispensable element of the microgrid. Disturbances in power supply may occur in the grid due to variations in the load in terms of a mismatch between load generation and load time. Mechanical wear and failure of the battery are some other causes of a terminal voltage fault. Energy storage in microgrid architecture refers to devices that perform the following functions [12]:
- (a)
- Balances the power in microgrid despite of load fluctuation and other transients.
- (b)
- Provides ride-through capability and allows DGs to operate as dispatchable units during dynamic variations in intermittent energy sources.
- (c)
- Provides the initial energy during the transition between grid connected or/from microgrid island.
Maintaining the stability of the microgrid is a challenging task because the system has various types of distributed generation, and demands for reactive and active power based on the needs of customers. Thus, the energy storage management system of the microgrid plays a vital role in stabilising its frequency and voltage for both the short and the long term [13]. The energy storage is connected to the grid through a micro-source, and absorbs power via the electronic converter. Subsequently, the energy storage exports power to the network in the island mode, enhancing the system’s quality and stability [14]. The energy storage can be distributed via two applications: utilisation-scale and small-scale applications. Other than maintaining the management and control function of the storage device, the distributed energy storage system can help maintain maximal system safety, efficiency, and life. It also performs communication with the Supervisory Control and Data Acquisition (SCADA) system in larger management applications. - (C)
- Enclave 3: the distribution systemDistribution systems refers to transmission and distribution technologies, specifically line frequency AC, high frequency AC and DC technologies, whose main role is to transmit and distribute electricity in microgrid systems.
- (D)
- Enclave 4: control and communication systemControl and communication system in microgrid architecture refers to technologies that handle the output data from microgrid and deliver them for further analysis by different applications, and microgrid controls and management. Two communication media, i.e., wired and wireless, support the communication technologies for power control and protection.Microgrid controls and management includes:
- Microgrid Central Controller (MGCC)The MGCC facilitates communication between the Distribution Management System (DMS) and the microgrid to detect and control blackout procedures. The MGCC was also introduced to improve the voltage profile and handle tripping problems.
- Supervisory Control And Data Acquisition (SCADA)In a microgrid application, SCADA as a computer-based application plays an important role in acquiring data, and monitoring and controlling operations, including the adjustment of signal alarms. It also enhances the safety, reliability, and economic benefits of the microgrid, and reduces the burden on the dispatchers. Moreover, it employs the automation and modernisation of electrical power dispatch to improve the efficacy and level of information of the system [15].
2.1. Communication Protocols and Standards of Microgrid
- (A)
- IEC 61850IEC 61850 is the most widely used standard of communication owing to its speed, excellent reliability, and security. The IEC 61850 standard is an international standard developed for substation automation. It is composed of three levels, namely, the process, bay, and substation. The IEC 61850 is built with different data attributes and functionalities to ensure interoperability, introducing some latencies in communication. This protocol is suitable to be applied in a microgrid, particularly in distribution automation [20].
- (B)
- ModbusAs reported in [21], Modbus is widely used in microgrids due to its simplicity. It can be transmitted over the different physical networks of RS 485, RS 232, and the Ethernet TCP/IP. However, the Modbus protocol is inefficient for large-scale data transmission from/to the network. It has high latency, making it unsuitable for a communication system, especially one involving emergency control. Such microgrid architectures such as PrInCE Lab use hard-wired networks if long delays occur in communication [16].
- (C)
- Distributed Network Protocol 3.0 (DNP3)DNP3 is a power communication protocol originally developed by General Electric that was made public in 1993. Use in SCADA applications was the initial purpose for the design of DNP3. It is used mainly in the oil and gas, security, water infrastructure, and electrical industries in Asia, North America, South America, Australia, and South Africa [22]. The initial design of DNP3 comprises four layers: the transport, application, data link, and physical layers. Serial communication protocols such as the RS-232, RS-422, and RS-485 became the basis for designing the original physical layer. The DNP3 has been moved over to the TCP/IP layer to support current communication technologies. Therefore, it can be considered a three-layer network protocol that operates on the TCP/IP layer [22] in supporting end-to-end communication. Contrary to Modbus, the slave of DNP3 can produce feedback with unsolicited responses to the master. Single DNP3 messages can demonstrate time-stamped tasks and information on data quality and various data types [17].
2.2. Cyberattacks on Microgrid
- ReconnaissanceReconnaissance for attacks is carried out in the form of social engineering and traffic analysis. Social engineering (SE) relies on social skills and human interaction rather than technical skills. In this stage, the attacker uses communication and persuasion to win the trust of a legitimate user. This is done to obtain the user’s credentials and confidential information, such as passwords or PIN numbers, to log on into a particular system. Some examples of popular techniques used in SE are phishing and password pilfering [33]. In a traffic analysis-based attack, the traffic is listened to and analysed to determine the device and hosts connected to the network, together with their IP addresses. In traffic analysis and social engineering, the compromise primarily involves confidential information.
- ScanningScanning is performed to identify live hosts and devices of the network. According to [33], there are four types of scans: those on ports, IPs, vulnerabilities, and services. Typically, an IP scan is conducted first to identify the hosts connected to the network together with their IP addresses. This is followed by the scanning of ports to identify an open port. Each host on the network is scanned. The attacker then performs a service scan to identify the system or service that operates behind each open port. For instance, if port 102 is detected as open on a system, the hacker can infer that this system is used for substation automation control or messaging. On the contrary, the phasor measurement unit (PMU) is the target system if port 4713 is open. Identifying vulnerabilities and weaknesses related to each service on the target machine for further exploitation is the aim of the vulnerability scan, which is the final step of scanning.The DNP3 and Modbus are two industrial protocols that are susceptible to scanning attacks. The Modbus/TCP is susceptible to an attack known as Modbus network scanning because it is designed for communication rather than security. In this attack, a benign message is sent to all devices connected to the network to collect information on them. An open Modbus/TCP is detected and slave IDs of the device together with their IP addresses are identified by Modscan, which is a SCADA Modbus network scanner [34]. Modscan scans the DNP3 protocol and determines the hosts: in particular, the slaves, their DNP3 addresses, and their corresponding master. It is thus clear that the target of these attacks is primarily confidential information on the smart grid.
- ExploitationExploitation features harmful activities to exploit the smart grid’s vulnerable components and gain control of it. Popping the human–machine interface (HMI), Trojan horse, integrity violation, man-in-the-middle (MITM) attack, jamming the channel, privacy violation, worm, virus, replay attack, and DOS attack are examples of harmful activities. The infection attack on a particular system or device in a smart grid is performed using a program called the virus. On the contrary, a worm is a self-replicating program, and spreads by copying itself to infect other devices and systems by using the network. Another example involves a program that appears to carry out a legitimate task on the target system, yet operates a malicious code in the background; this is known as a Trojan horse. The attacker uses this form of malware to upload a worm or a virus to the target system [35]. The first cyberattack against a physical industrial control system was launched using Stuxnet.
- Maintaining accessSpecial forms of attack, including the backdoor, virus, and Trojan horse, are used in this final step to maintain permanent access to the target. The backdoor, which is an undetectable stealthy program, is installed on the target by the attacker for easier and faster use in the future. The successful embedding of a backdoor into the server of the SCADA control centre allows the attacker to launch several attacks against the power system that damage it. The security parameters of an IT network are classified based on their order of importance: confidentiality, integrity, accountability, and availability. However the order of precedence of the security parameters of a smart grid is as follows: availability, integrity, accountability, and confidentiality [36]. Thus, we can say that attacks that compromise the availability of smart grid systems are the most severe, while those targeting its confidentiality are the least severe. In addition to severity, the likelihood of each attack to be carried out is important. Although attacks based on Duqu and Stuxnet, for example, are highly destructive due to their ability to bypass all security boundaries and vandalise the industrial control system, they are complex and sophisticated. Hence, even though the severity of these viruses is high, they have a low likelihood of being launched.The HMI popping attack is an example of a highly severe. However, its execution does not demand outstanding experience in security and industrial control systems, or a high level of networking skill. The public availability of vulnerability documentation on devices enables the use of open-source tools, such as Metasploit and Meterpreter, or the so-called script-kiddies, by a hacker to launch an attack. Thus, this attack is considered to be highly severe as well as highly likely [35].Table 2 summarises common cyberattacks on microgrid based on the four steps identified above: reconnaissance, scanning, exploitation, and maintaining access. Each step includes the attack categories, examples, the component compromised in the smart grid due to each attack, the impact of each attack, and the appropriate countermeasures. It can be concluded that the use of secure network protocols, such as secure-DNP3, as well as the enabling of authentication and encryption mechanisms can help prevent most attacks.
3. The Cybersecurity Aspects of Microgrid
3.1. Traditional Security Tools in Microgrid Systems
3.2. Vulnerabilities and Threats in Microgrid
3.2.1. Common Vulnerabilities in Microgrid
- Wireless communication. Such communication uses radio frequency, which makes it challenge to prevent physical access to users, especially in case of public access to the network. Although it has several advantages, it faces the risk of attacks, including interception and intrusion, that can be larger than in a wired network.
- Heterogeneous communication technology. Modern power systems are deployed through the use of various technologies. These technologies, which are either wired or wireless, create challenges for a robust and uniformed cybersecurity policy due to the need to protect the communication infrastructure.
- Increased communication to external networks. This occurs in a microgrid because communication to the external network helps maintain its performance and safety through continuous data exchange with the main operator. However, it exposes the created communication line to outsider threats.
- Internet Exposure. The exchange of data through the Internet plays an important role in providing ancillary services for the microgrid, including data on fuel prices and weather forecasts. This environment exposes the system to attacks through the Internet.
- Increased system automation. System automation improves the effectiveness and flexibility of operation by preventing the likelihood of human error. However, this creates new vulnerabilities, where the system has more access points, thus increasing the possibility of attacks.
- Increased use of automation device and distributed control. The possibility for a security breach is created through the heightened penetration of monitoring and control capabilities of the system. The boundaries of a microgrid have been extended and stretched in the digital era.
- Cohabitation between legacy and new systems. The sharing of a common infrastructure during contact between the microgrid controller and the operators of different distributions can introduce new vulnerabilities to the system.
- Multiple independent systems. Because the microgrid consists of such essential systems as computers, actuators, sensors, and emergency systems, it faces difficulty in guaranteeing uninterrupted communication, interfacing, and security between heterogeneous and independent systems.
3.2.2. Threats against Microgrid
- Physical attacks occurring from intentional offensive actions. These are targeted to perform distractions at the maximum level by gaining unauthorised access to assets of the microgrid and destroying them.
- Eavesdropping. This category of threats is realised by adjusting communication between parties without installing tools on the victim’s side.
- Nefarious Atrocious Activities. This category is performed through cyberattacks or deliberate harmful activities which aims at system digital assets. Here, the attackers would use additional tools/software to attack the victim’s software or IT infrastructure.
3.2.3. Potential Threat Agents against Microgrid
- Hostile threat agents. Companies or organisations may be correlated to offensive tactics. These companies usually have a high capability of intelligence in technology or human beings.
- Cyber-criminals. This category is a hostile threat by nature, and targets financial gain at a high level of skill. This criminal act can be coordinated at a national, local, or international level.
- Threat agents from the inside, including employees and third party. The employees of a microgrid include the operational staff as well as contractors. Other, third parties, also help at the power facilities. All of these agents can access the private system of the microgrid and expose it to attacks on sensitive assets.
- Hacktivists. This type of threat is created by individuals who protest against political or social agendas, and promote their cause by hacking intelligence agencies, corporations, websites, and military institutions.
- Capabilities of offensive cyber in nation-states. This attack is considered a cyber-weapon. Nation states have high skill and expertise in malware, and use them to attack adversaries.
- Terrorists. Their activities have been expanded to include cyberattacks targeting critical infrastructure, including public health agencies, energy production facilities, and telecommunication infrastructures. This type of threat may have a severe impact on the government and society.
- Cyber-fighters. This is an emerging threat agent. It is composed of a group of patriotically motivated citizens who have the potential to initiate cyberattacks. There may be a conflict between their activities and those of other groups (e.g., hacktivists).
- Insider Threat. A cyberattack occurs when intruders use false system information to deceive the operators. Such operations cause the power system to become unstable. This situation obtains because insiders have knowledge of the power grid, especially its vulnerabilities. The detection and prevention of attacks initiated by insiders is challenging.
3.3. Security Issues in Microgrid
3.4. Efforts and Initiatives for Smart Grid and Microgrid Security
4. Potential Future Work and Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hassan, M.; Abido, M.; Rahim, A. Optimal design of autonomous microgrid using particle swarm optimization. In Proceedings of the International Symposium on Power Electronics Power Electronics, Electrical Drives, Automation and Motion, Sorrento, Italy, 20–22 June 2012; pp. 152–157. [Google Scholar]
- Abdulkarim, A.; Faruk, N.; Oloyode, A.; Olawoyin, L.A.; Popoola, S.I.; Abdullateef, A.; Ibrahim, O.; Surajudeen-Bakinde, N.; Abdelkader, S.; Morrow, J.D.; et al. State of the art in research on optimum design, reliability and control of renewable energy microgrids. Elektr. J. Electr. Eng. 2018, 17, 23–35. [Google Scholar] [CrossRef][Green Version]
- Villalón, A.; Rivera, M.; Salgueiro, Y.; Muñoz, J.; Dragičević, T.; Blaabjerg, F. Predictive control for microgrid applications: A review study. Energies 2020, 13, 2454. [Google Scholar] [CrossRef]
- Leon, G. Smart Planning for Smart Grid AMI Mesh Networks. EDX Wireless. Available online: https://www.smartgrid.gov/files/documents/Smart_Planning_for_Smart_Grid_AMI_Mesh_Networks_201109.pdf (accessed on 2 November 2011).
- Bani-Ahmed, A.; Weber, L.; Nasiri, A.; Hosseini, H. Microgrid communications: State of the art and future trends. In Proceedings of the 2014 International Conference on Renewable Energy Research and Application (ICRERA), Milwaukee, WI, USA, 19–22 October 2014; pp. 780–785. [Google Scholar]
- Cagnano, A.; De Tuglie, E.; Mancarella, P. Microgrids: Overview and guidelines for practical implementations and operation. Appl. Energy 2020, 258, 114039. [Google Scholar] [CrossRef]
- Nederland, N. Privacy and Security of the Advanced Metering Infrastructure; Technical Report; Chalmers University of Technology: Gothenburg, Sweden, 2010. [Google Scholar]
- Brown, B.; Singletary, B.; Willke, B.; Bennett, C.; Highfill, D.; Houseman, D.; Cleveland, F.; Lipson, H.; Ivers, J.; Gooding, J.; et al. AMI System Security Requirements. AMI-SEC TF. 2008. Available online: https://www.energy.gov/sites/prod/files/oeprod/DocumentsandMedia/14-AMI_System_Security_Requirements_updated.pdf (accessed on 7 October 2021).
- International Electrotechnical Commission. Electricity Metering Data Exchange—The DLMS/COSEM Suite—Part 5-3: DLMS/COSEM Application Layer; IEC 62056-5-3: 2016; Technical Report; International Electrotechnical Commission (IEC): Geneva, Switzerland, 2016. [Google Scholar]
- Berrio, L.; Zuluaga, C. Concepts, standards and communication technologies in smart grid. In Proceedings of the 2012 IEEE 4th Colombian Workshop on Circuits and Systems (CWCAS), Barranquilla, Colombia, 1–2 November 2012; pp. 1–6. [Google Scholar]
- Mariam, L.; Basu, M.; Conlon, M.F. Microgrid: Architecture, policy and future trends. Renew. Sustain. Energy Rev. 2016, 64, 477–489. [Google Scholar] [CrossRef]
- Priyadharshini, N.; Gomathy, S.; Sabarimuthu, M. A review on microgrid architecture, cyber security threats and standards. Mater. Today Proc. 2020. [Google Scholar] [CrossRef]
- Zhao, J.; Wang, C.; Zhao, B.; Lin, F.; Zhou, Q.; Wang, Y. A review of active management for distribution networks: Current status and future development trends. Electr. Power Components Syst. 2014, 42, 280–293. [Google Scholar] [CrossRef]
- Zhang, X.; Hao, M.; Liu, F.; Yu, C.; Zhao, W. Analysis and control of energy storage systems in microgrid. In Proceedings of the 2012 Second International Conference on Intelligent System Design and Engineering Application, Sanya, China, 6–7 January 2012; pp. 1375–1379. [Google Scholar]
- Win, K.T.Z.; Tun, H.M. Design and implementation of SCADA system based power distribution for primary substation (control system). Int. J. Electron. Comput. Sci. Eng 2014, 3, 254–261. [Google Scholar]
- Usman, A.; Shami, S.H. Evolution of communication technologies for smart grid applications. Renew. Sustain. Energy Rev. 2013, 19, 191–199. [Google Scholar] [CrossRef]
- Segall, A. Distributed network protocols. IEEE Trans. Inf. Theory 1983, 29, 23–35. [Google Scholar] [CrossRef]
- Cagnano, A.; De Tuglie, E.; Cicognani, L. Prince—Electrical Energy Systems Lab: A pilot project for smart microgrids. Electr. Power Syst. Res. 2017, 148, 10–17. [Google Scholar] [CrossRef]
- Palma-Behnke, R.; Ortiz, D.; Reyes, L.; Jimenez-Estevez, G.; Garrido, N. A social SCADA approach for a renewable based microgrid—The Huatacondo project. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–28 July 2011; pp. 1–7. [Google Scholar]
- Chlela, M.; Joos, G.; Kassouf, M. Impact of cyber-attacks on islanded microgrid operation. In Proceedings of the Workshop on Communications, Computation and Control for Resilient Smart Energy Systems, Waterloo, ON, Canada, 21–24 June 2016; pp. 1–5. [Google Scholar]
- Martin-Martínez, F.; Sánchez-Miralles, A.; Rivier, M. A literature review of Microgrids: A functional layer based classification. Renew. Sustain. Energy Rev. 2016, 62, 1133–1153. [Google Scholar] [CrossRef]
- Bracco, S.; Delfino, F.; Pampararo, F.; Robba, M.; Rossi, M. The University of Genoa smart polygeneration microgrid test-bed facility: The overall system, the technologies and the research challenges. Renew. Sustain. Energy Rev. 2013, 18, 442–459. [Google Scholar] [CrossRef]
- Loix, T. Distributed Generation—Micro Grids; Alternative Energy: San Diego, CA, USA, 2009. [Google Scholar]
- Qu, M. Microgrid Policy Review of Selected Major Countries, Regions, and organizations. 2012. Available online: https://escholarship.org/uc/item/51q0g9p8 (accessed on 7 October 2021).
- Barnes, M.; Dimeas, A.; Engler, A.; Fitzer, C.; Hatziargyriou, N.; Jones, C.; Papathanassiou, S.; Vandenbergh, M. Microgrid laboratory facilities. In Proceedings of the 2005 International Conference on Future Power Systems, Amsterdam, The Netherlands, 18 November 2005; p. 6. [Google Scholar]
- Katiraei, F.; Abbey, C.; Tang, S.; Gauthier, M. Planned islanding on rural feeders—Utility perspective. In Proceedings of the 2008 IEEE Power and Energy Society General Meeting-Conversion and Delivery of Electrical Energy in the 21st Century, Pittsburgh, PA, USA, 20–24 July 2008; pp. 1–6. [Google Scholar]
- Kyriakarakos, G.; Piromalis, D.D.; Dounis, A.I.; Arvanitis, K.G.; Papadakis, G. Intelligent demand side energy management system for autonomous polygeneration microgrids. Appl. Energy 2013, 103, 39–51. [Google Scholar] [CrossRef]
- Loix, T.; Leuven, K. The first micro grid in the Netherlands: Bronsbergen. Retrieved Dec. 2009, 27, 2012. [Google Scholar]
- Eto, J.; Lasseter, R.; Schenkman, B.; Stevens, J.; Klapp, D.; VolkommeRr, H.; Linton, E.; Hurtado, H.; Roy, J. Overview of the CERTS microgrid laboratory test bed. In Proceedings of the 2009 CIGRE/IEEE PES Joint Symposium Integration of Wide-Scale Renewable Resources Into the Power Delivery System, Calgary, AB, Canada, 29–31 July 2009; p. 1. [Google Scholar]
- Mohagheghi, S.; Stoupis, J.; Wang, Z. Communication protocols and networks for power systems-current status and future trends. In Proceedings of the 2009 IEEE/PES Power Systems Conference and Exposition, Seattle, WA, USA, 15–18 March 2009; pp. 1–9. [Google Scholar]
- Majdalawieh, M.; Parisi-Presicce, F.; Wijesekera, D. DNPSec: Distributed network protocol version 3 (DNP3) security framework. In Advances in Computer, Information, and Systems Sciences, and Engineering; Springer: Berlin/Heidelberg, Germany, 2007; pp. 227–234. [Google Scholar]
- Lim, I.; Hong, S.; Choi, M.; Lee, S.; Kim, T.; Lee, S.; Ha, B. Security protocols against cyber attacks in the distribution automation system. IEEE Trans. Power Deliv. 2009, 25, 448–455. [Google Scholar] [CrossRef]
- Engebretson, P. The Basics of Hacking and Penetration Testing: Ethical Hacking and Penetration Testing Made Easy, 1st ed.; Syngress Publishing: Rockland, MA, USA, 2011. [Google Scholar]
- Khelifa, B.; Abla, S. Security concerns in smart grids: Threats, vulnerabilities and countermeasures. In Proceedings of the 2015 3rd International Renewable and Sustainable Energy Conference (IRSEC), Marrakech, Morocco, 10–13 December 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Knapp, E.D.; Samani, R. Applied Cyber Security and the Smart Grid: Implementing Security Controls into the Modern Power Infrastructure; Elsevier: Amsterdam, The Netherlands, 2013. [Google Scholar]
- Gilchrist, G. Secure authentication for DNP3. In Proceedings of the 2008 IEEE Power and Energy Society General Meeting-Conversion and Delivery of Electrical Energy in the 21st Century, Pittsburgh, PA, USA, 20–24 July 2008; pp. 1–3. [Google Scholar]
- Al-Dalky, R.; Abduljaleel, O.; Salah, K.; Otrok, H.; Al-Qutayri, M. A Modbus traffic generator for evaluating the security of SCADA ystems. In Proceedings of the 2014 9th International Symposium on Communication Systems, Networks Digital Sign (CSNDSP), Manchester, UK, 23–25 July 2014; pp. 809–814. [Google Scholar] [CrossRef]
- Rodofile, N.R.; Radke, K.; Foo, E. DNP3 network scanning and reconnaissance for critical infrastructure. In Proceedings of the Australasian Computer Science Week Multiconference, Canberra, Australia, 2–5 February 2016. [Google Scholar]
- Faisal, M.A.; Aung, Z.; Williams, J.R.; Sanchez, A. Data-Stream-Based Intrusion Detection System for Advanced Metering Infrastructure in Smart Grid: A Feasibility Study. IEEE Syst. J. 2015, 9, 31–44. [Google Scholar] [CrossRef]
- Reyes, H.; Kaabouch, N. Jamming and Lost Link Detection in Wireless Networks with Fuzzy Logic. Int. J. Sci. Eng. Res. 2013, 4, 1–7. [Google Scholar]
- Shahzad, A.; Musa, S.; Aborujilah, A.; Irfan, M. Industrial control systems (ICSs) vulnerabilities analysis and SCADA security enhancement using testbed encryption. In Proceedings of the ICUIMC ’14, Siem Reap, Cambodia, 9–11 January 2014. [Google Scholar]
- Phan, R.C.W. Authenticated Modbus Protocol for Critical Infrastructure Protection. IEEE Trans. Power Deliv. 2012, 27, 1687–1689. [Google Scholar] [CrossRef]
- Song, K.Y.; Yu, K.S.; Lim, D. Secure frame format for avoiding replay attack in Distributed Network Protocol (DNP3). In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 28–30 October 2015; pp. 344–349. [Google Scholar] [CrossRef]
- Marinos, L. ENISA Threat Taxonomy: A Tool for Structuring Threat Information; ENISA: Heraklion, Greece, 2016. [Google Scholar]
- Pritzker, P. Guidelines for Smart Grid Cybersecurity, Volume 1—Smart Grid Cybersecurity Strategy, Architecture, and High-Level Requirements; U.S. Department of Commerce: Washington, DC, USA, 2014.
- Venkataramanan, V.; Hahn, A.; Srivastava, A. CyPhyR: A cyber-physical analysis tool for measuring and enabling resiliency in microgrids. IET Cyber-Phys. Syst. Theory Appl. 2019, 4, 313–321. [Google Scholar] [CrossRef]
- Mell, P.; Scarfone, K.; Romanosky, S. Common vulnerability scoring system. IEEE Secur. Priv. 2006, 4, 85–89. [Google Scholar] [CrossRef]
- Sterbenz, J.P.; Çetinkaya, E.K.; Hameed, M.A.; Jabbar, A.; Qian, S.; Rohrer, J.P. Evaluation of network resilience, survivability, and disruption tolerance: Analysis, topology generation, simulation, and experimentation. Telecommun. Syst. 2013, 52, 705–736. [Google Scholar] [CrossRef]
- Francis, R.; Bekera, B. A metric and frameworks for resilience analysis of engineered and infrastructure systems. Reliab. Eng. Syst. Saf. 2014, 121, 90–103. [Google Scholar] [CrossRef]
- Zhao, K.; Kumar, A.; Harrison, T.P.; Yen, J. Analyzing the resilience of complex supply network topologies against random and targeted disruptions. IEEE Syst. J. 2011, 5, 28–39. [Google Scholar] [CrossRef]
- Pandit, A.; Crittenden, J.C. Index of network resilience (INR) for urban water distribution systems. Nature 2012, 12, 120–142. [Google Scholar]
- Bakken, D.E.; Bose, A.; Hauser, C.H.; Whitehead, D.E.; Zweigle, G.C. Smart Generation and Transmission With Coherent, Real-Time Data. Proc. IEEE 2011, 99, 928–951. [Google Scholar] [CrossRef]
- Lasseter, R.H.; Eto, J.H.; Schenkman, B.; Stevens, J.; Vollkommer, H.; Klapp, D.; Linton, E.; Hurtado, H.; Roy, J. CERTS microgrid laboratory test bed. IEEE Trans. Power Deliv. 2010, 26, 325–332. [Google Scholar] [CrossRef]
- Mariam, L.; Basu, M.; Conlon, M.F. A review of existing microgrid architectures. J. Eng. 2013, 2013, 937614. [Google Scholar] [CrossRef]
- Dempsey, K.L.; Witte, G.A.; Rike, D. Summary of NIST SP 800-53, Revision 4: Security and Privacy Controls for Federal Information Systems and Organizations. 2014. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.02192014.pdf (accessed on 7 October 2021).
- International Electrotechnical Commission. IEC 62443: Industrial Communication Networks—Network and System Security; IEC Central Office: Geneva, Switzerland, 2010. [Google Scholar]
- International Electrotechnical Commission. Power Systems Management and Associated Information Exchange—Data and Communications Security. Part 1: Communication Network and System Security—Introduction to Security Issues; IEC Technical Specification; IEC Central Office: Geneva, Switzerland, 2007; p. 62351. [Google Scholar]
- Andersson, R.; Sandelin, A.; Danko, C.G. A unified architecture of transcriptional regulatory elements. Trends Genet. 2015, 31, 426–433. [Google Scholar] [CrossRef]
- Mohan, A.; Brainard, G.; Khurana, H.; Fischer, S. A cyber security architecture for microgrid deployments. In International Conference on Critical Infrastructure Protection; Springer: Berlin/Heidelberg, Germany, 2015; pp. 245–259. [Google Scholar]
- Lasseter, R.; Akhil, A.; Marnay, C.; Stephens, J.; Dagle, J.; Guttromsom, R.; Meliopoulous, A.S.; Yinger, R.; Eto, J. Integration of distributed energy resources. The CERTS Microgrid Concept; Technical Report; Lawrence Berkeley National Lab. (LBNL): Berkeley, CA, USA, 2002. [Google Scholar]
- Stamp, J. The SPIDERS project-smart power infrastructure demonstration for energy reliability and security at US military facilities. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012. [Google Scholar]
- Mueller, F. Cyber-Physical Aspects of Energy Systems for the 21st Century: A Perspective from the Nsf Erc Freedm Project; (moss. csc. ncsu. edu/mueller/ftp/pub/mueller/papers/cps09.pdf); Department of Computer Science, North Carolina State University: Raleigh, NC, USA, 2009. [Google Scholar]
| Study | Year | Media | Protocol | Advantages | Limitations |
|---|---|---|---|---|---|
| Korea- KEPRI Microgrid [18] | 2014, 2017 | Optical fiber | N.A. | High-speed communication, low latency time, high reliability | Cover short distances |
| Huatacondo [19] | 2011 | NA. | Modbus TCP/IP | Easy to implement, Low installation cost, Supported by different, communication links | High latency time |
| Am Steinweg [23] | 2009 | NA. | Modbus TCP/IP | Easy to implement, Low installation cost, Supported by different, communication links | High network delay; Low security level against cyber attacks |
| Kythnos [24] | 2013, 2014 | Power line | NA. | High speed communication, Adopts existing electrical, network, Low installation cost, High data transfer rate | Minimum security level, Data attenuation, Great amount of noise |
| Smart Polygeneration, Microgrid [22] | 2013 | NA. | IEC 61850 | High reliability, High-speed communication, High security level, especially, against cyber attacks, High interoperability | Low redundancy level, High implementation cost, Requires change or upgrade of both, communication interface of already installed components and the existing IT network |
| DeMoTec [25] | 2005 | Ethernet | XLM-RPC | Improved reliability, Enhanced security level | High computational cost, High installation cost |
| Bornholm Island [24] | 2014 | Optical fiber | NA. | High-speed communication, Low latency time, High reliability | Cover short distances |
| NTUA [25] | 2005 | NA. | XLM | High operational flexibility, High readability | High load of communication challenges |
| BC Hydro [26] | 2002, 2008 | Telephone | NA. | Easy to be integrated | Low reliability, High implementation cost |
| University of Manchester, Microgrid [27] | 2013 | Power line | NA. | Adopts existing electrical, network, Low installation cost, High data transfer rate | Minimum security level, Data attenuation, Great amount of noise |
| Bronsbergen Holiday Park [27] | 2013, 2009 | GSM | NA. | High reliability, Cost effective | Limited transmission bandwidth |
| CESI Ricerca DER [28] | 2013, 2009 | Ethernet | NA. | High reliability | Low security level, High installation cost |
| CERTS [29] | 2009, 2011, 2013 | NA. | Modbus TCP/IP | Easy to implement, Low installation cost, Supported by different, communication links | High network delay, Low security level against cyber attacks |
| Sendai Project [24] | 2014, 2014 | GPS | NA. | Easy to integrate, Low installation cost, Global accessibility | Reduced accuracy, Low reliability due to battery life, Low security level, Low privacy. |
| Prince Lab [18] | 2017 | Ethernet | Modbus TCP/IP | Easy to implement, Low installation cost, Supported by different, communication links | High network delay, Low security level against cyber attacks, Involve partial upgrade and expansion of existing, IT network |
| Attacking Steps | Attack Categories | Attack Examples | Compromised Element | Compromised Security Parameters | Possible Countermeasures |
|---|---|---|---|---|---|
| Reconnaissance | Traffic analysis, Social Engineering | [35] | Modbus protocol, DNP3 Protocol | Confidentiality | Secure DNP3, PKI, TLS, SSL, Encryption, Authentication [35] |
| Scanning | Scanning IP, Port, Service, Vulnerabilities | Modbus network scanning [37], DNP3 network scanning [38] | Modbus Protocol, DNP3 Protocol | Confidentiality | IDS [39], SIEM, Automated security compliance checks |
| Exploitation | Virus, worms, Trojan Horse | Stuxnet, Duqu | SCADA PMU, Control device | Confidentiality Integrity Availability Accountability | DLP, SIEM, Anti-virus, IDS |
| Denial of service (DoS) | Puppet attack, TSA | AMI, PMU, smart grid equipment GPS | Availability | SIEM, flow entropy, signal strength, sensing time measurement, transmission failure count, pushback, reconfiguration methods, IDS | |
| Privacy violation | [39] | Smart meters | Confidentiality | Secure DNP3, PKI, TLS, SSL, encryption, authentication | |
| Man-in-the-middle (MITM) | Intercept/alter, active eavesdropping attack | HMI, PLC, SCADA, AMI, DNP3 | Confidentiality Integrity | Secure DNP3, PKI, TLS, SSL, encryption, authentication | |
| Replay attack | [35] | IED, SCADA, PLC, authentication scheme in AMI | Integrity | Secure DNP3, PKI, TLS, SSL, encryption, authentication | |
| Jamming channel | [40], MAS-SJ | PMU, CRN in WSGN | Availability | Anti-jamming [40] | |
| Popping the HMI | [35] | SCADA, EMS, substations | Confidentiality Integrity Availability Accountability | DLP, SIEM, Anti-virus, automated security compliance checks, IDS | |
| Masquerade attack | [35] | PLC | Confidentiality Integrity Availability Accountability | DLP, Secure DNP3, PKI, SIEM, TLS, SSL, encryption, authentication, IDS | |
| Integrity violation | [35] | Smart meter, RTU | Integrity Availability | DLP, Secure DNP3, PKI, SIEM, TLS, SSL, encryption, authentication, IDS | |
| Maintaining access | Backdoor | [35] | SCADA | Confidentiality Integrity Availability Accountability | IDS, SIEM, Anti-virus |
| Enclave | Characteristic | Attributes | Potential Security Issues |
|---|---|---|---|
| DG sources | In terms of availability, most of DG sources such as solar and wind are geographical location dependent, it is not the case for diesel. DG sources such as solar, wind and hydro are uncontrollable. Diesel is controllable [12]. |
|
|
| Energy storage |
|
|
|
| Distribution system | Three power electronics interfaces available for connecting the energy generated from the distributed sources to the distribution network. |
|
|
| Communication system |
|
|
|
| Level | Potential R&D Topic in Microgrid |
|---|---|
| Device/hardware level |
|
| System level |
|
| Communication/Network level |
|
| Software and application level |
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jamil, N.; Qassim, Q.S.; Bohani, F.A.; Mansor, M.; Ramachandaramurthy, V.K. Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research. Appl. Sci. 2021, 11, 9812. https://doi.org/10.3390/app11219812
Jamil N, Qassim QS, Bohani FA, Mansor M, Ramachandaramurthy VK. Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research. Applied Sciences. 2021; 11(21):9812. https://doi.org/10.3390/app11219812
Chicago/Turabian StyleJamil, Norziana, Qais Saif Qassim, Farah Aqilah Bohani, Muhamad Mansor, and Vigna Kumaran Ramachandaramurthy. 2021. "Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research" Applied Sciences 11, no. 21: 9812. https://doi.org/10.3390/app11219812
APA StyleJamil, N., Qassim, Q. S., Bohani, F. A., Mansor, M., & Ramachandaramurthy, V. K. (2021). Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research. Applied Sciences, 11(21), 9812. https://doi.org/10.3390/app11219812







