Blockchain Based Trust Model Using Tendermint in Vehicular Adhoc Networks
Abstract
1. Introduction
2. Related Work
2.1. Byzantine Consensus
2.2. Centralized Trust Management
2.3. Blockchain Based Decentralized Data Management
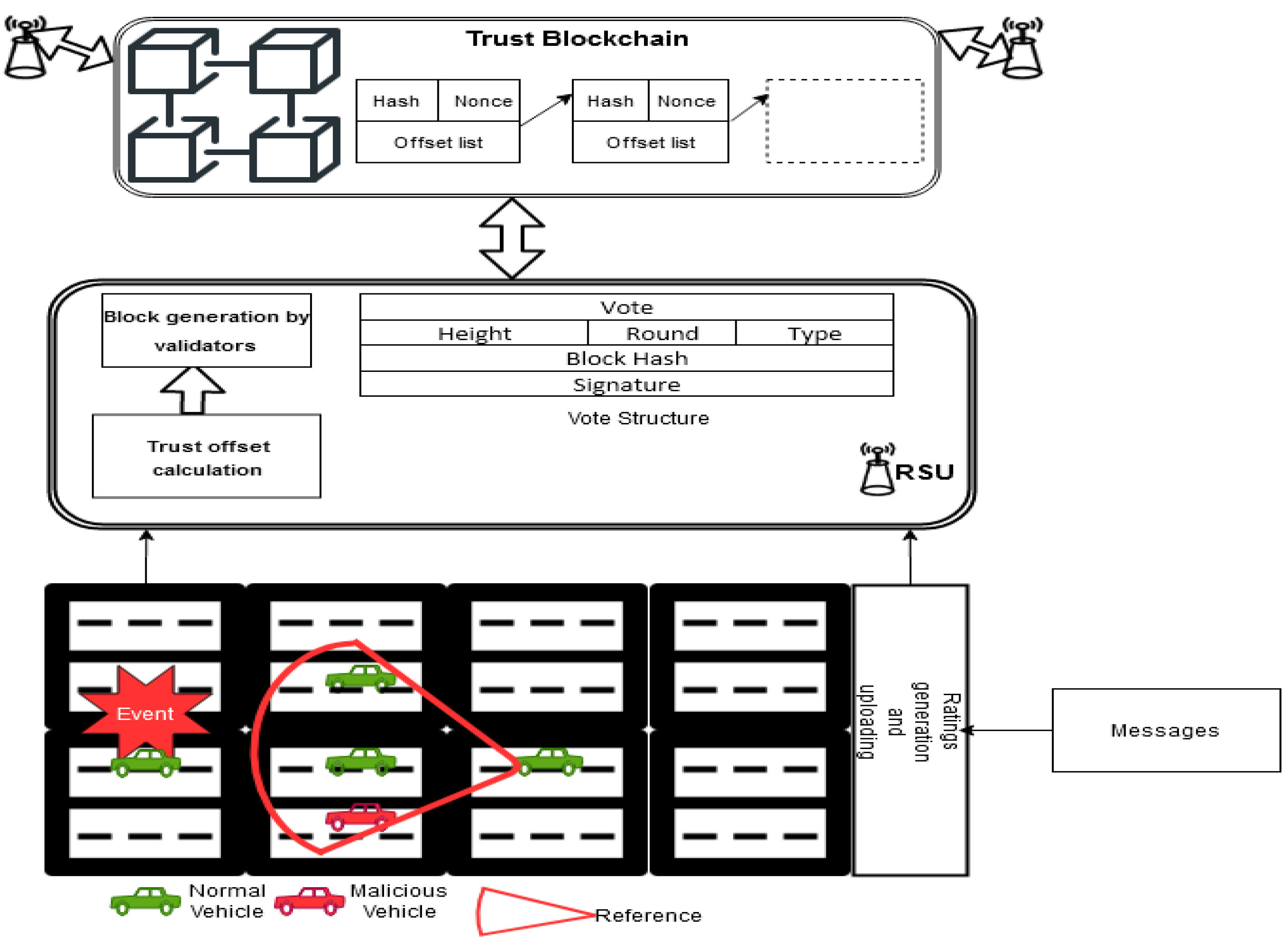
3. Proposed Approach
3.1. Road Side Unit
3.2. On-Board Unit
3.3. Trust Value Management
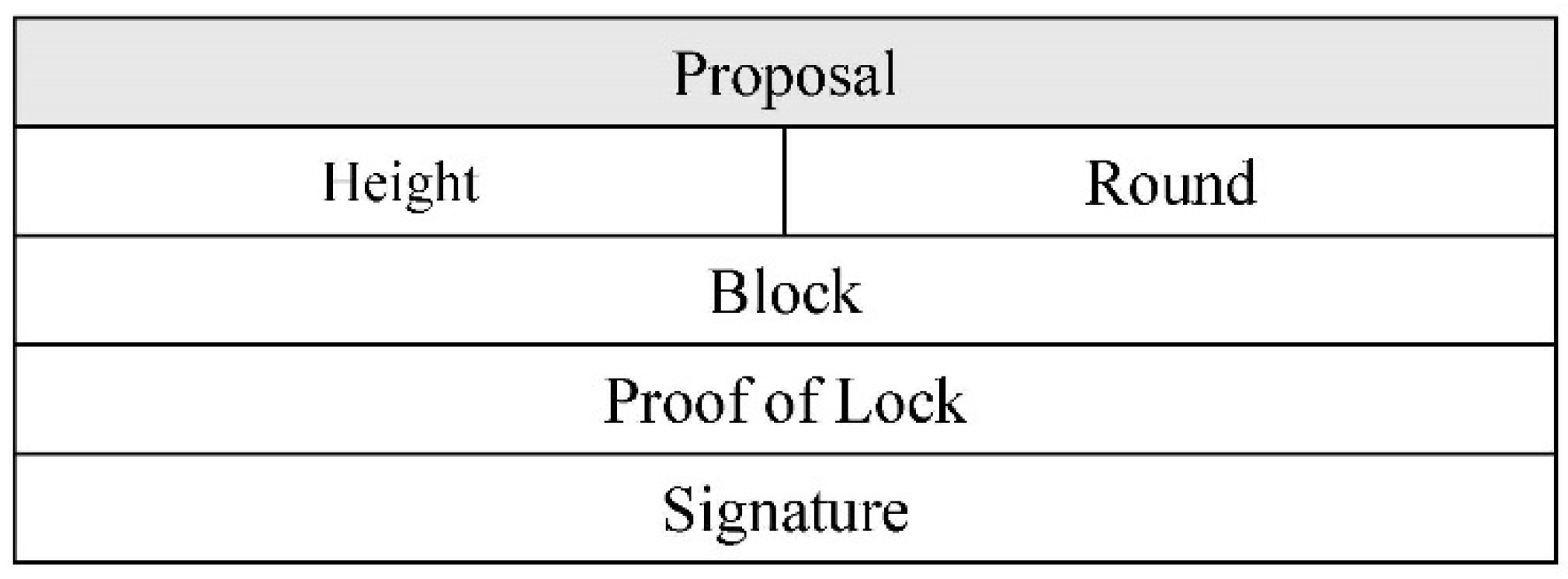
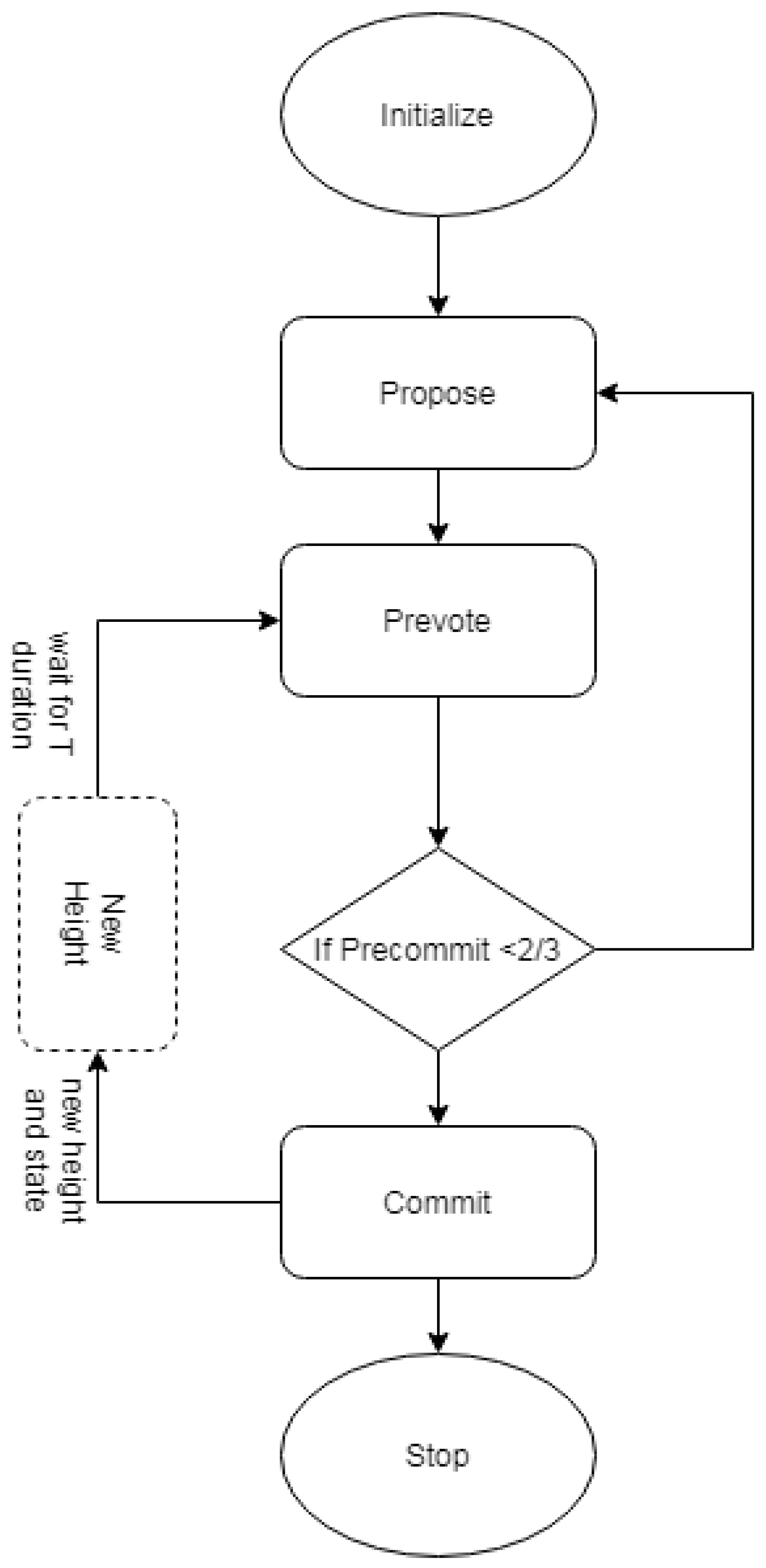
3.4. Main Procedures
4. Simulation Parameters
5. Implementation and Results
5.1. Performance Metrics
5.2. Packet Delivery Ratio (PDR)
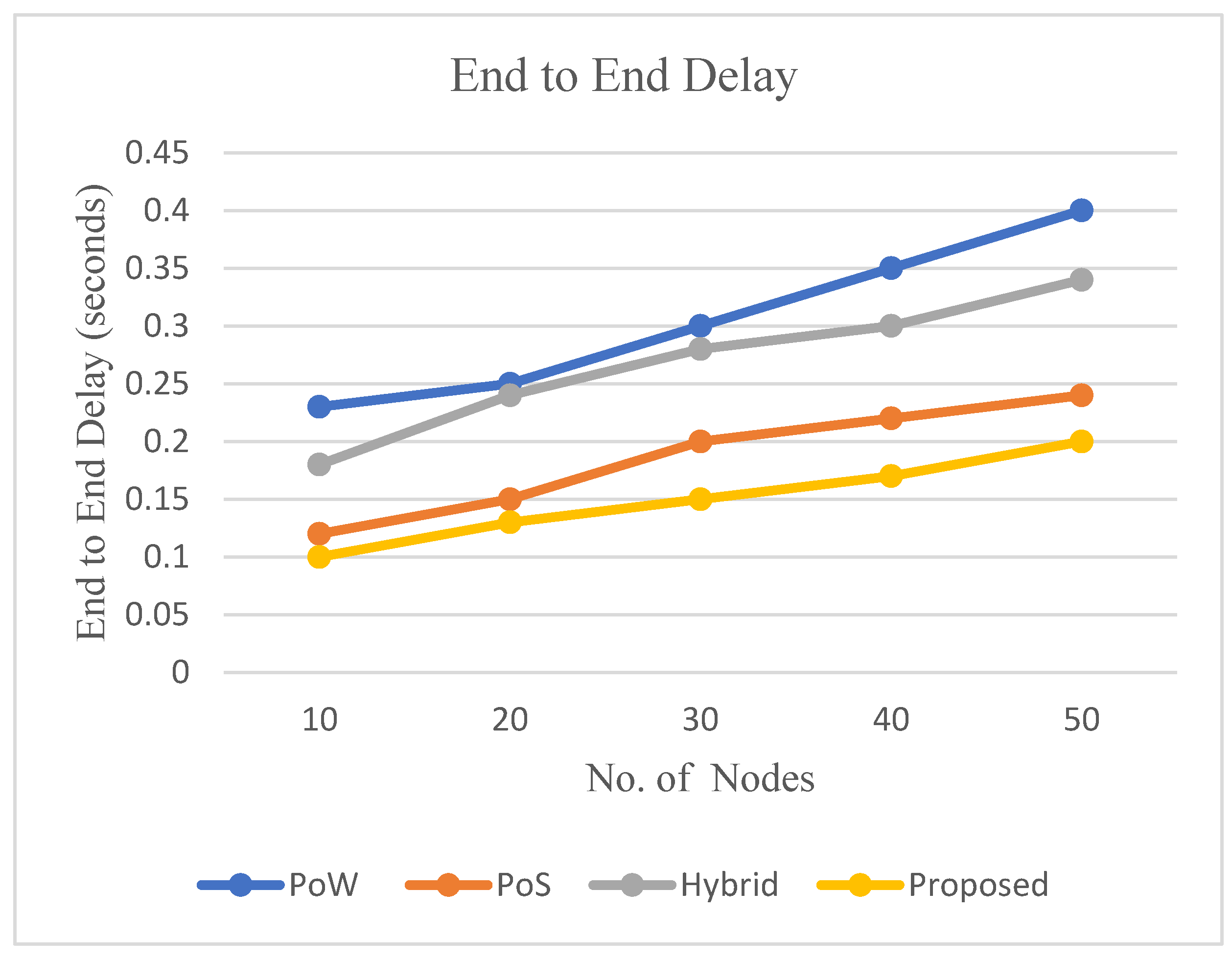
5.3. End-to-End Delay
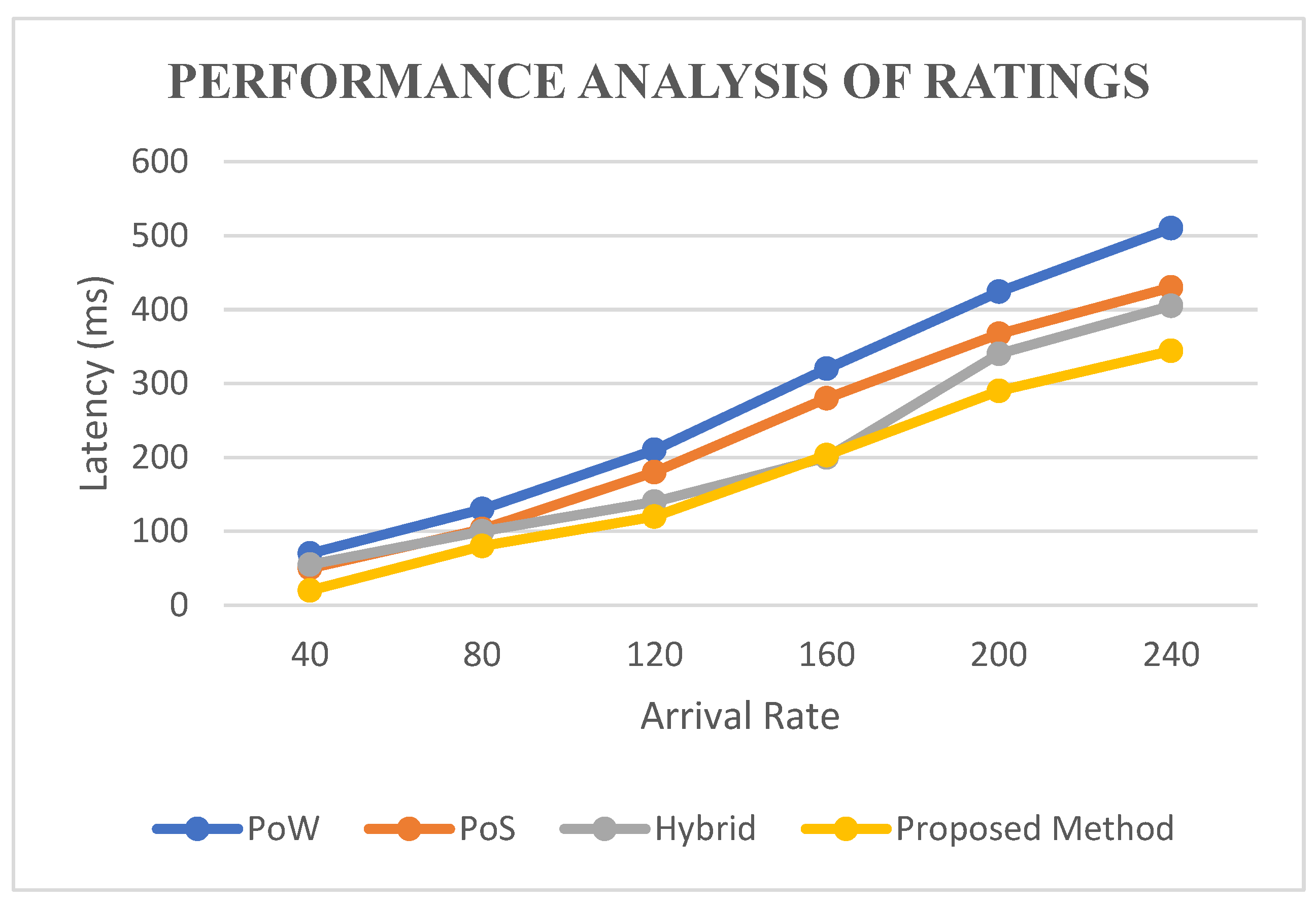
5.4. Performance Analysis of Ratings
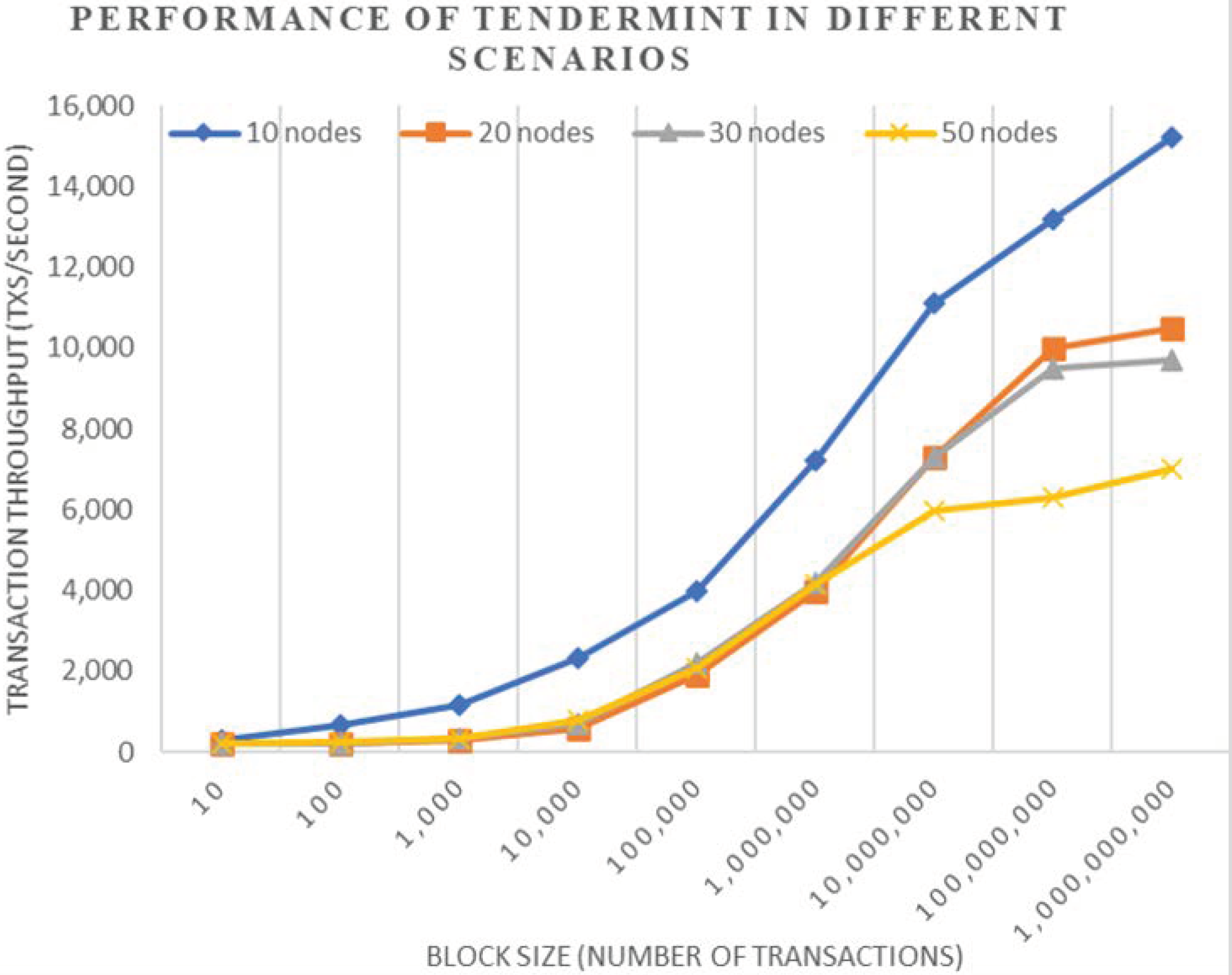
5.5. Comparitive Analysis of Results
6. Theoretical Analysis
6.1. Free from Deadlock
6.2. Message Spoofing Attack
6.3. Overwriting Proposed Blocks
6.4. Temperproof Environment
6.5. Strong Privacy
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhou, H.; Liu, B.; Luan, T.H.; Hou, F.; Gui, L.; Li, Y.; Yu, Q.; Shen, X. ChainCluster: Engineering a cooperative content distribution framework for highway vehicular communica-tions. IEEE Trans. Intell. Transp. Syst. 2014, 15, 2644–2657. [Google Scholar] [CrossRef]
- He, S.; Shin, D.-H.; Zhang, J.; Chen, J.; Sun, Y. Full-view area coverage in camera sensor networks: Dimension reduction and near-optimal solutions. IEEE Trans. Veh. Technol. 2015, 65, 7448–7461. [Google Scholar] [CrossRef]
- Zheng, K.; Zheng, Q.; Chatzimisios, P.; Xiang, W.; Zhou, Y. Heterogeneous vehicular networking: A survey on architec-ture, challenges, and solutions. IEEE Commun. Surveys Tuts. 2015, 17, 2377–2396. [Google Scholar] [CrossRef]
- Wasef, R.; Lu, X.L.; Shen, X. Complementing public key infrastructure to secure vehicular ad hoc networks. IEEE Wirel. Commun. 2010, 17, 22–28. [Google Scholar] [CrossRef]
- De Angelis, D.S.; Aniello, L.; Leonardo, B.; Roberto, L.; Federico, M.; Margheri, A.; Sassone, V. PBFT vs proof-of-authority: Applying the CAP theorem to permissioned blockchain. In Proceedings of the Italian Conference on Cyber Security, Milan, Italy, 6–9 February 2018; pp. 1–11. [Google Scholar]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and privacy in smart city applications: Challenges and solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance and proactive recovery. ACM Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Roosta, T.; Meingast, M.; Sastry, S. Distributed reputation system for tracking applications in sensor networks. In Proceedings of the 3rd Annual International Conference Mobile Ubiquitous System, San Jose, CA, USA, 17–21 July 2006; pp. 1–8. [Google Scholar]
- Li, S.; Wang, X. Quickest attack detection in multi-agent reputation systems. IEEE J. Sel. Top. Signal Process. 2014, 8, 653–666. [Google Scholar] [CrossRef]
- Mahmoud, M.E.; Shen, S. An integrated stimulation and punishment mechanism for thwarting packet dropping attack in multihop wireless networks. IEEE Trans. Veh. Technol. 2011, 60, 3947–3962. [Google Scholar] [CrossRef]
- Lai, C.; Zhang, K.; Cheng, N.; Li, H.; Shen, X. SIRC: A secure incentive scheme for reliable cooperative downloading in highway VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 18, 1–16. [Google Scholar] [CrossRef]
- Gurung, S.; Lin, D.; Squicciarini, A.; Bertino, J. Information oriented trustworthiness evaluation in vehicular ad-hoc networks. In Proceedings of the International Conference Network System Security, Madrid, Spain, 3–4 June 2013; pp. 94–108. [Google Scholar]
- Li, Z.; Chigan, C.T. On joint privacy and reputation assurance for vehicular ad hoc networks. IEEE Trans. Mob. Comput. 2014, 13, 2334–2344. [Google Scholar] [CrossRef]
- Huang, X.; Yu, R.; Kang, J.; Zhang, Y. Distributed reputation management for secure and efficient vehicular edge com-puting and networks. IEEE Access 2017, 5, 25408–25420. [Google Scholar] [CrossRef]
- Mattila, J. The blockchain phenomenon. In Proceedings of the Berkeley Roundtable of the International Economy, Berkeley, CA, USA, 24–26 June 2016. [Google Scholar]
- Kumar, N.; Misra, S.; Lqbal, R.; Rodrigues, J.J.P.C. Coalition games for spatio-temporal big data in internet of vehicles environment: A comparative analysis. IEEE Internet of Things J. 2015, 2, 310–320. [Google Scholar] [CrossRef]
- Kumar, N.; Misra, S.; Lqbal, R.; Rodrigues, J.J.P.C. Bayesian coalition game for contention-aware reliable data forwarding in vehicular mobile cloud. Future Gener. Comput. Syst. 2015, 48, 60–72. [Google Scholar] [CrossRef]
- Kim, T.-H.; Kumar, G.; Saha, R.; Rai, M.K.; Buchanan, W.J.; Thomas, R.; Alazab, M. A privacy preserving distributed ledger framework for global human resource record management: The blockchain aspect. IEEE Access 2020, 8, 96455–96467. [Google Scholar] [CrossRef]
- Goyat, R.; Kumar, G.; Rai, M.K.; Saha, R.; Thomas, R.; Kim, T.H. Blockchain powered secure range-free localization in wireless sensor networks. Arab. J. Sci. Eng. 2020, 45, 6139–6155. [Google Scholar] [CrossRef]
- Kumar, N.; Iqbal, R.; Misra, S.; Rodrigues, J.J. An intelligent approach for building a secure decentralized public key infrastructure in VANET. J. Comput. Syst. Sci. 2015, 81, 1042–1058. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O.; Pentland, A. ’Sandy’ decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef]
- Cai, C.; Yuan, X.; Wang, C. Towards trustworthy and private keyword search in encrypted decentralized storage. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Cai, C.; Yuan, X.; Wang, C. Hardening distributed and encrypted keyword search via blockchain. In Proceedings of the 2017 IEEE Symposium on Privacy-Aware Computing (PAC), Washington, DC, USA, 1–4 August 2017; pp. 119–128. [Google Scholar] [CrossRef]
- Tschorsch, F.; Scheuermann, B. Bitcoin and beyond: A technical survey on decentralized digital currencies. IEEE Commun. Surv. Tutorials 2016, 18, 2084–2123. [Google Scholar] [CrossRef]
- Cachin, C.; Vukolic, M. Blockchains consensus protocols in the wild. ArXiv 2017, 1707, 01873. [Google Scholar]
- Clique. Available online: https://github.com/ethereum/EIPs/issues/225 (accessed on 2 July 2020).
- Federico, A.S. The Crowd Jury, A Crowdsourced Justice System for the Collaboration Era. Available online: https://medium.com/the-crowdjury/the-crowdjury-a-crowdsourced-court-system-for-the-collaboration-era66da002750d8 (accessed on 2 January 2021).
- Jacynycz, V.; Calvo, A.; Hassan, S.; Sánchez-Ruiz, A.A. Betfunding: A distributed bounty-based crowdfunding platform over ethereum. In Proceedings of the Distributed Computing and Artificial Intelligence, 13th International Conference, Sevilla, Spain, 1–3 June 2016; Volume 474, pp. 403–411. [Google Scholar]
- Zhu, H.; Zhou, Z.Z. Analysis and outlook of applications of blockchain technology to equity crowdfunding in China. Financ. Innov. 2016, 2, 29. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C.M. Blockchain-based decentralized trust management in vehicular networks. IEEE Internet Things J. 2019, 6, 1495–1505. [Google Scholar] [CrossRef]
- Sangeetha, S.; Sathappan, S. Self-organized gradient boosting key authentication for secured data communication in mobile adhoc network. Int. J. Appl. Eng. Res. 2017, 12, 7823–7832. [Google Scholar]
- Study on LTE-Based V2X Services, V1.0.0: TSG RAN 3GPP; TR 36.885; European Telecommunications Standards Institute: Sophia Antipolis, France, 2016.
- Draz, U.; Ali, T.; Yasin, S.; Shaf, A. Evaluation based analysis of packet delivery ratio for AODV and DSR under UDP and TCP environment. In Proceedings of the 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 3–4 March 2018; pp. 1–7. [Google Scholar]
- Shorfuzzaman, M.; Masud, M.; Rahman, M. Characterizing end-to-end delay performance of randomized TCP using an analytical model. Int. J. Adv. Comput. Sci. Appl. 2016, 7, 406–412. [Google Scholar] [CrossRef][Green Version]
- Kumar, N.; Kaur, K.; Misra, S.C.; Iqbal, R. An intelligent RFID-enabled authentication scheme for healthcare applications in vehicular mobile cloud. Peer Peer Netw. Appl. 2015, 9, 824–840. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.K.H.; Biswas, G.P.; Khan, M.K.; Kumar, N. An efficient and practical smart card based anonymity preserving user authentication scheme for TMIS using elliptic curve cryptography. J. Med. Syst. 2015, 39, 180. [Google Scholar] [CrossRef]
- Pukale, P.; Gupta, P. Analysis of end-to-end delay in vehicular networks. Int. J. Sci. Res. 2015, 5, 1122–1125. [Google Scholar]
- Thin, W.Y.M.M.; Dong, N.; Bai, G.; Dong, J.S. Formal analysis of a proof-of-stake blockchain. In Proceedings of the 2018 23rd International Conference on Engineering of Complex Computer Systems (ICECCS), Melbourne, Australia, 12–14 December 2018; pp. 197–200. [Google Scholar]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An efficient decentralized key management mechanism for VANET with blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5836–5849. [Google Scholar] [CrossRef]
- Tan, H.; Chung, I. Secure authentication and key management with blockchain in VANETs. IEEE Access 2019, 8, 2482–2498. [Google Scholar] [CrossRef]
- Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure trust-based blockchain architecture to prevent attacks in VANET. Sensors 2019, 19, 4954. [Google Scholar] [CrossRef] [PubMed]
- Kim, T.H.; Goyat, R.; Kumar, G. A novel trust evaluation process for secure localization using a decentralized block-chain in wireless sensor networks. IEEE Access 2019, 7, 184133–184144. [Google Scholar] [CrossRef]



| Parameter | Value |
|---|---|
| No. of Nodes | 50 |
| Maximum Vehicle Speed | 40 m/s |
| Length of Vehicle | 3 m |
| Width of Vehicle | 2 m |
| Number of RSUs | 7 |
| RSU coverage | 1 Km |
| Consensus Scheme | Latency |
|---|---|
| 1. PoW | High |
| 2. PoS | High |
| 3. Hybrid | Moderate |
| 4. Proposed Scheme | Low |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Arora, S.K.; Kumar, G.; Kim, T.-h. Blockchain Based Trust Model Using Tendermint in Vehicular Adhoc Networks. Appl. Sci. 2021, 11, 1998. https://doi.org/10.3390/app11051998
Arora SK, Kumar G, Kim T-h. Blockchain Based Trust Model Using Tendermint in Vehicular Adhoc Networks. Applied Sciences. 2021; 11(5):1998. https://doi.org/10.3390/app11051998
Chicago/Turabian StyleArora, Sandeep Kumar, Gulshan Kumar, and Tai-hoon Kim. 2021. "Blockchain Based Trust Model Using Tendermint in Vehicular Adhoc Networks" Applied Sciences 11, no. 5: 1998. https://doi.org/10.3390/app11051998
APA StyleArora, S. K., Kumar, G., & Kim, T.-h. (2021). Blockchain Based Trust Model Using Tendermint in Vehicular Adhoc Networks. Applied Sciences, 11(5), 1998. https://doi.org/10.3390/app11051998






