Memory and Cache Contention Denial-of-Service Attack in Mobile Edge Devices
Abstract
:1. Introduction
- we introduce memory and cache contention denial-of-service attack and demonstrate how this attack threatens mobile edge computing systems in terms of both performance and energy;
- through our evaluations, we show our memory and cache contention attack can degrade system performance by 47.6% on average and also increase the system energy consumption by 2.1×;
- our proposed hardware-based detection method effectively detects the malicious codes by analyzing the intensiveness and steadiness of the shared resource accesses; and,
- with our countermeasure that reduces the instruction fetch bandwidth, one can recover performance degradation and exhaustive energy consumption by 92.4% and 94.7%, respectively, when compared to the case without our countermeasure.
2. Related Work
3. Memory and Cache Contention Denial-of-Service (DOS) Attack
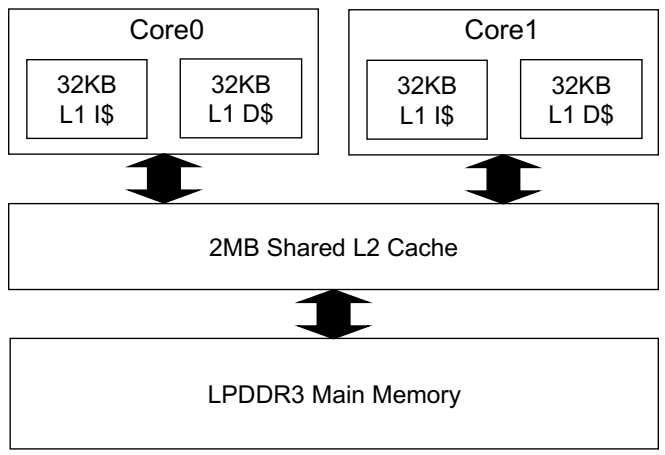
3.1. System Assumptions
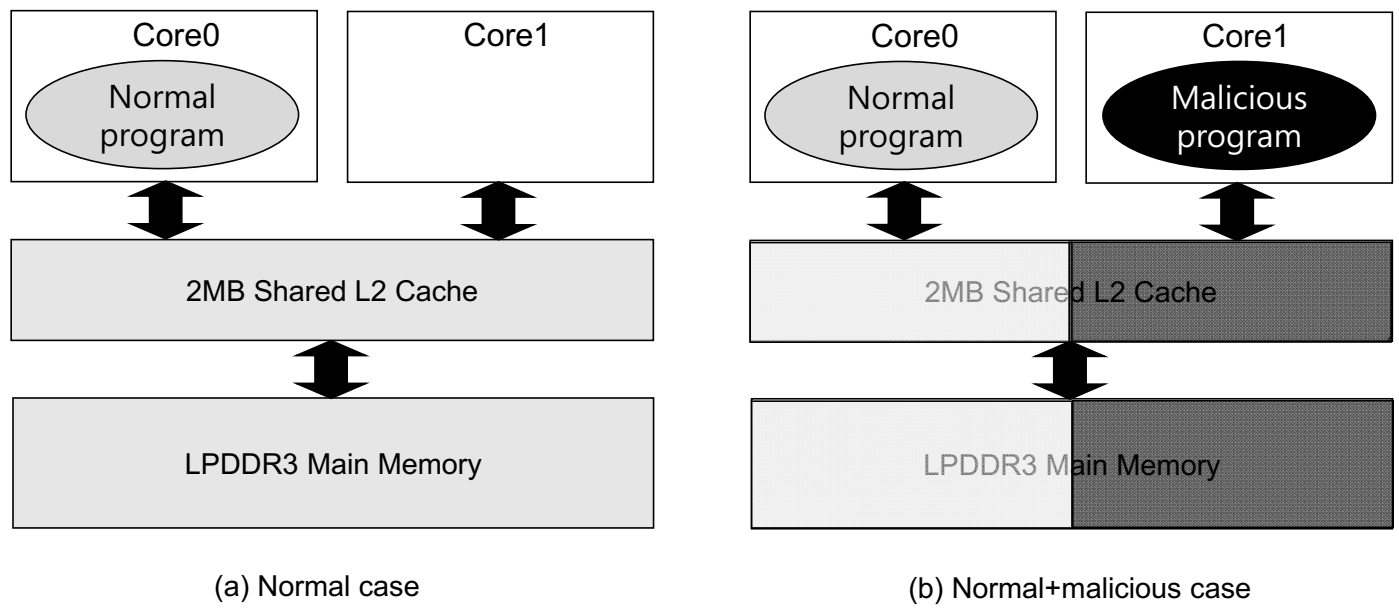
3.2. Our Attack and Threat Model
- a large number of repetitive access requests to the L2 cache incurred by the malicious code will consecutively prefetch the data of the malicious code into the L2 cache, evicting the data of the normal program from the L2 cache (i.e., higher L2 miss rate of the normal programs); and,
- a huge number of L2 prefetch requests that are caused by the malicious code will exhaust the effective main memory bandwidth, resulting in available memory bandwidth reduction and longer memory access latency of the normal program.
3.3. Malicious Code Examples
4. Hardware-Based Countermeasures for Memory and Cache Contention DoS Attack
4.1. Our Proposed Detection Method
4.2. Our Proposed Mitigation Method
4.2.1. Instruction Fetch Bandwidth Throttling
4.2.2. Throttling Periods
5. Evaluation
5.1. Evaluation Methodology
5.2. Performance
5.3. Energy Comparison
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Halpern, M.; Zhu, Y.; Reddi, V.J. Mobile CPU’s rise to power: Quantifying the impact of generational mobile CPU design trends on performance, energy, and user satisfaction. In Proceedings of the 2016 IEEE International Symposium on High Performance Computer Architecture (HPCA), Barcelona, Spain, 12–16 March 2016; pp. 64–76. [Google Scholar]
- Yang, S.H.; Lee, S.; Lee, J.Y.; Cho, J.; Lee, H.J.; Cho, D.; Heo, J.; Cho, S.; Shin, Y.; Yun, S.; et al. A 32nm high-k metal gate application processor with GHz multi-core CPU. In Proceedings of the 2012 IEEE International Solid-State Circuits Conference, San Francisco, CA, USA, 19–23 February 2012; pp. 214–216. [Google Scholar]
- Moscibroda, T.; Mutlu, O. Memory Performance Attacks: Denial of Memory Service in Multi-core Systems. In Proceedings of the 16th USENIX Security Symposium on USENIX Security Symposium, Boston, MA, USA, 6–10 August 2007; pp. 18:1–18:18. [Google Scholar]
- Woo, D.H.; Lee, H.H. Analyzing performance vulnerability due to resource denial of service attack on chip multiprocessors. In Proceedings of the Workshop on Chip Multiprocessor Memory Systems and Interconnects in conjunction with the 13th Annual International Conference on High-Performance Architecture, Phoenix, AZ, USA, 11 February 2007. [Google Scholar]
- Zhang, T.; Zhang, Y.; Lee, R.B. DoS Attacks on Your Memory in Cloud. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security (ASIA CCS’17), Abu Dhabi, United Arab Emirates, 2–6 April 2017; pp. 253–265. [Google Scholar]
- Bechtel, M.; Yun, H. Denial-of-Service Attacks on Shared Cache in Multicore: Analysis and Prevention. In Proceedings of the 2019 IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS), Montreal, QC, Canada, 16–18 April 2019; pp. 357–367. [Google Scholar]
- Bechtel, M.; Yun, H. Memory-Aware Denial-of-Service Attacks on Shared Cache in Multicore Real-Time Systems. arXiv 2020, arXiv:2005.10864. [Google Scholar]
- Hasan, J.; Jalote, A.; Vijaykumar, T.N.; Brodley, C.E. Heat stroke: Power-density-based denial of service in SMT. In Proceedings of the 11th International Symposium on High-Performance Computer Architecture, San Francisco, CA, USA, 12–16 February 2005; pp. 166–177. [Google Scholar]
- Kong, J.; John, J.K.; Chung, E.Y.; Chung, S.W.; Hu, J. On the Thermal Attack in Instruction Caches. IEEE Trans. Dependable Secur. Comput. 2010, 7, 217–223. [Google Scholar] [CrossRef]
- Aciicmez, O. Yet another microarchitectural attack: Exploiting i-cache. In Proceedings of the 2007 ACM Workshop on Computer Security Architecture, Fairfax, VA, USA, 2 November 2007; pp. 11–18. [Google Scholar]
- Spreitzer, R.; Griesmayr, S.; Korak, T.; Mangard, S. Exploiting Data Usage Statistics for Website Fingerprinting Attacks on Android. In Proceedings of the 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks, WISEC 2016, Darmstadt, Germany, 18–22 July 2016; pp. 49–60. [Google Scholar]
- Yarom, Y.; Genkin, D.; Heninger, N. CacheBleed: A Timing Attack on OpenSSL Constant Time RSA. In Proceedings of the Cryptographic Hardware and Embed ded Systems-CHES 2016-18th International Conference, Santa Barbara, CA, USA, 17–19 August 2016; pp. 346–367. [Google Scholar]
- Bernstein, D.J. Cache-timing attacks on AES. 2004. Available online: http://cr.yp.to/antiforgery/cachetiming-20050414.pdf (accessed on 4 January 2018).
- Christodorescu, M.; Jha, S. Static Analysis of Executables to Detect Malicious Patterns. In Proceedings of the 12th Conference on USENIX Security Symposium, Washington, DC, USA, 4–8 August 2003; Volume 12, pp. 1–18. [Google Scholar]
- Christodorescu, M.; Jha, S.; Seshia, S.A.; Song, D.; Bryant, R.E. Semantics-aware malware detection. In Proceedings of the 2005 IEEE Symposium on Security and Privacy (S&P’05), Oakland, CA, USA, 8–11 May 2005; pp. 32–46. [Google Scholar]
- Kinder, J.; Katzenbeisser, S.; Schallhart, C.; Veith, H. Detecting Malicious Code by Model Checking. In Proceedings of the Second International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Vienna, Austria, 7–8 July 2005; pp. 174–187. [Google Scholar]
- Kolter, J.Z.; Maloof, M.A. Learning to Detect and Classify Malicious Executables in the Wild. J. Mach. Learn. Res. 2006, 7, 2721–2744. [Google Scholar]
- Schmidt, A.D.; Bye, R.; Schmidt, H.G.; Clausen, J.; Kiraz, O.; Yuksel, K.A.; Camtepe, S.A.; Albayrak, S. Static Analysis of Executables for Collaborative Malware Detection on Android. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar]
- Demme, J.; Maycock, M.; Schmitz, J.; Tang, A.; Waksman, A.; Sethumadhavan, S.; Stolfo, S. On the Feasibility of Online Malware Detection with Performance Counters. In Proceedings of the 40th Annual International Symposium on Computer Architecture, Tel-Aviv, Israel, 23–27 June 2013; pp. 559–570. [Google Scholar]
- Ozsoy, M.; Donovick, C.; Gorelik, I.; Abu-Ghazaleh, N.; Ponomarev, D. Malware-aware processors: A framework for efficient on-line malware detection. In Proceedings of the 2015 IEEE 21st International Symposium on High Performance Computer Architecture (HPCA), Burlingame, CA, USA, 7–11 February 2015; pp. 651–661. [Google Scholar]
- Eklov, D.; Nikoleris, N.; Black-Schaffer, D.; Hagersten, E. Cache Pirating: Measuring the Curse of the Shared Cache. In Proceedings of the 2011 International Conference on Parallel Processing, Taipei, Taiwan, 13–16 September 2011; pp. 165–175. [Google Scholar]
- Eklov, D.; Nikoleris, N.; Black-Schaffer, D.; Hagersten, E. Bandwidth Bandit: Quantitative characterization of memory contention. In Proceedings of the 2013 IEEE/ACM International Symposium on Code Generation and Optimization (CGO), Shenzhen, China, 23–27 February 2013; pp. 1–10. [Google Scholar]
- Subramanian, L.; Seshadri, V.; Ghosh, A.; Khan, S.; Mutlu, O. The application slowdown model: Quantifying and controlling the impact of inter-application interference at shared caches and main memory. In Proceedings of the 2015 48th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO), Waikiki, HI, USA, 5–9 December 2015; pp. 62–75. [Google Scholar]
- ARM Processor Introduction. Cortex-A15 MPCore Processor. 2011. Available online: http://www.arm.com/products/processors/cortex-a/cortex-a15.php (accessed on 15 July 2017).
- Choi, H.; Kim, Y. Large-Scale Analysis of Remote Code Injection Attacks in Android Apps. Secur. Commun. Netw. 2018, 2018, 1–17. [Google Scholar] [CrossRef]
- Wang, J.; Liu, K.; Pan, J. Online UAV-Mounted Edge Server Dispatching for Mobile-to-Mobile Edge Computing. IEEE Internet Things J. 2020, 7, 1375–1386. [Google Scholar] [CrossRef]
- Reddi, V.J. Mobile SoCs: The Wild West of Domain Specific Architectures. ACM SigArch, Computer Architecture Today. Available online: https://www.sigarch.org/mobile-socs/ (accessed on 18 April 2020).
- Binkert, N.; Beckmann, B.; Black, G.; Reinhardt, S.K.; Saidi, A.; Basu, A.; Hestness, J.; Hower, D.R.; Krishna, T.; Sardashti, S.; et al. The Gem5 Simulator. SIGARCH Comput. Archit. News 2011, 39, 1–7. [Google Scholar] [CrossRef]
- Spradling, C.D. SPEC CPU2006 Benchmark Tools. SIGARCH Comput. Archit. News 2007, 35, 130–134. [Google Scholar] [CrossRef]
- Li, S.; Ahn, J.H.; Strong, R.D.; Brockman, J.B.; Tullsen, D.M.; Jouppi, N.P. McPAT: An Integrated Power, Area, and Timing Modeling Framework for Multicore and Manycore Architectures. In Proceedings of the 42nd Annual IEEE/ACM International Symposium on Microarchitecture, New York, NY, USA, 12–16 December 2009; pp. 469–480. [Google Scholar]
- Jin, X.; Hu, X.; Ying, K.; Du, W.; Yin, H.; Peri, G.N. Code Injection Attacks on HTML5-based Mobile Apps: Characterization, Detection and Mitigation. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (CCS’14), Scottsdale, AZ, USA, 3–7 November 2014. [Google Scholar]
- 5 Ways Your Mobile Device Can Get Malware. Available online: https://www.securitymetrics.com/blog/5-ways-your-mobile-device-can-get-malware (accessed on 24 February 2021).








| Specification | ||
|---|---|---|
| Processor core | Branch predictor | Bimodal predictor, 2 K BTB |
| L1 data cache | 32 KB, 2-way set-associative, 2-cycle, LRU | |
| L1 instruction cache | 32 KB, 2-way set-associative, 1-cycle, LRU | |
| Fetch width | 3 | |
| Issue width | 8 | |
| Commit width | 8 | |
| Clock frequency | 2 GHz | |
| L2 cache | 2 MB, 8-way set-associative, 12-cycle, LRU, Stride-prefetcher | |
| Memory | LPDDR3, 800 MHz, 1-channel, 1-rank, 8-bank | |
| Values Used in This Work | |
|---|---|
| Thresint | 100,000 |
| Threslower | 600 |
| Thresupper | 1200 |
| Thresacc | 500 |
| spec+mal_t1_ft | spec+mal_t2_ft | spec+mal_t3_ft | spec+mal_t4_ft | |
|---|---|---|---|---|
| gemsFDTD | 95.1% | 95.1% | 95.2% | 95.1% |
| bwaves | 95.0% | 95.0% | 95.0% | 95.0% |
| bzip2 | 95.7% | 95.7% | 94.1% | 93.7% |
| gcc | 91.1% | 91.3% | 91.0% | 91.5% |
| h264ref | 90.5% | 88.5% | 81.9% | 88.7% |
| lbm | 94.8% | 94.7% | 94.8% | 90.6% |
| leslie3d | 85.2% | 83.9% | 94.5% | 92.5% |
| mcf | 94.6% | 94.6% | 94.6% | 94.6% |
| milc | 93.9% | 93.8% | 93.9% | 93.9% |
| namd | 75.6% | 97.3% | 97.4% | 74.3% |
| perlbench | 94.0% | 93.9% | 93.9% | 93.9% |
| xalancbmk | 94.1% | 93.4% | 94.1% | 93.3% |
| sjeng | 94.3% | 94.3% | 94.3% | 94.3% |
| Geomean | 91.7% | 93.1% | 93.4% | 91.5% |
| spec+mal_t1_ft | spec+mal_t2_ft | spec+mal_t3_ft | spec+mal_t4_ft | |
|---|---|---|---|---|
| gemsFDTD | 97.4% | 97.4% | 97.3% | 97.4% |
| bwaves | 96.5% | 96.5% | 96.4% | 96.5% |
| bzip2 | 97.7% | 97.7% | 97.0% | 96.8% |
| gcc | 89.9% | 89.9% | 89.4% | 89.8% |
| h264ref | 93.4% | 92.1% | 87.4% | 92.1% |
| lbm | 96.6% | 96.6% | 96.5% | 94.3% |
| leslie3d | 92.6% | 92.2% | 97.1% | 96.1% |
| mcf | 97.3% | 97.3% | 97.2% | 97.2% |
| milc | 94.1% | 94.0% | 93.8% | 94.1% |
| namd | 83.1% | 94.9% | 94.7% | 82.6% |
| perlbench | 95.7% | 96.5% | 96.4% | 95.7% |
| xalancbmk | 98.4% | 98.3% | 98.4% | 98.3% |
| sjeng | 95.2% | 95.2% | 95.0% | 95.1% |
| Geomean | 94.4% | 95.3% | 95.1% | 94.2% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, W.; Kong, J. Memory and Cache Contention Denial-of-Service Attack in Mobile Edge Devices. Appl. Sci. 2021, 11, 2385. https://doi.org/10.3390/app11052385
Cho W, Kong J. Memory and Cache Contention Denial-of-Service Attack in Mobile Edge Devices. Applied Sciences. 2021; 11(5):2385. https://doi.org/10.3390/app11052385
Chicago/Turabian StyleCho, Won, and Joonho Kong. 2021. "Memory and Cache Contention Denial-of-Service Attack in Mobile Edge Devices" Applied Sciences 11, no. 5: 2385. https://doi.org/10.3390/app11052385
APA StyleCho, W., & Kong, J. (2021). Memory and Cache Contention Denial-of-Service Attack in Mobile Edge Devices. Applied Sciences, 11(5), 2385. https://doi.org/10.3390/app11052385






