AAAA: SSO and MFA Implementation in Multi-Cloud to Mitigate Rising Threats and Concerns Related to User Metadata
Abstract
1. Introduction
- Deployment of a federated trust domain in a multi-cloud environment for internal and external connectivity.
- Definition of the risk model to separate user metadata used to access multi-cloud services.
- Third-party app Shibboleth IDP used to deploy a hybrid SSO-based model in a multi-cloud environment.
- Deployment of a mixed vendor-based MFA model to overcome rising security risks and threats.
- Services attack model to mitigate rising threats related to consumer metadata in the multi-cloud paradigm.
2. Related Work
- A.S. Anakath et al. [29] presented a privacy-based multifactor authentication mechanism to achieve trust in the de-centralization of remote locations in cloud computing. As the end user has no transparency or access to their key-vault data store in remote areas. User access control depends on the cloud-deployment model on both the consumer and provider end.
- Charanjeet Singh et al. [30] presented three-level MFA for cloud computing, where the first level involves OTP, the second as out-of-band (OOB) policy, and the third one screen clicks on a given image. The proposed technique is helpful for mitigating man-in-the-middle attacks (MIM).
3. Proposed Work
4. Methodology
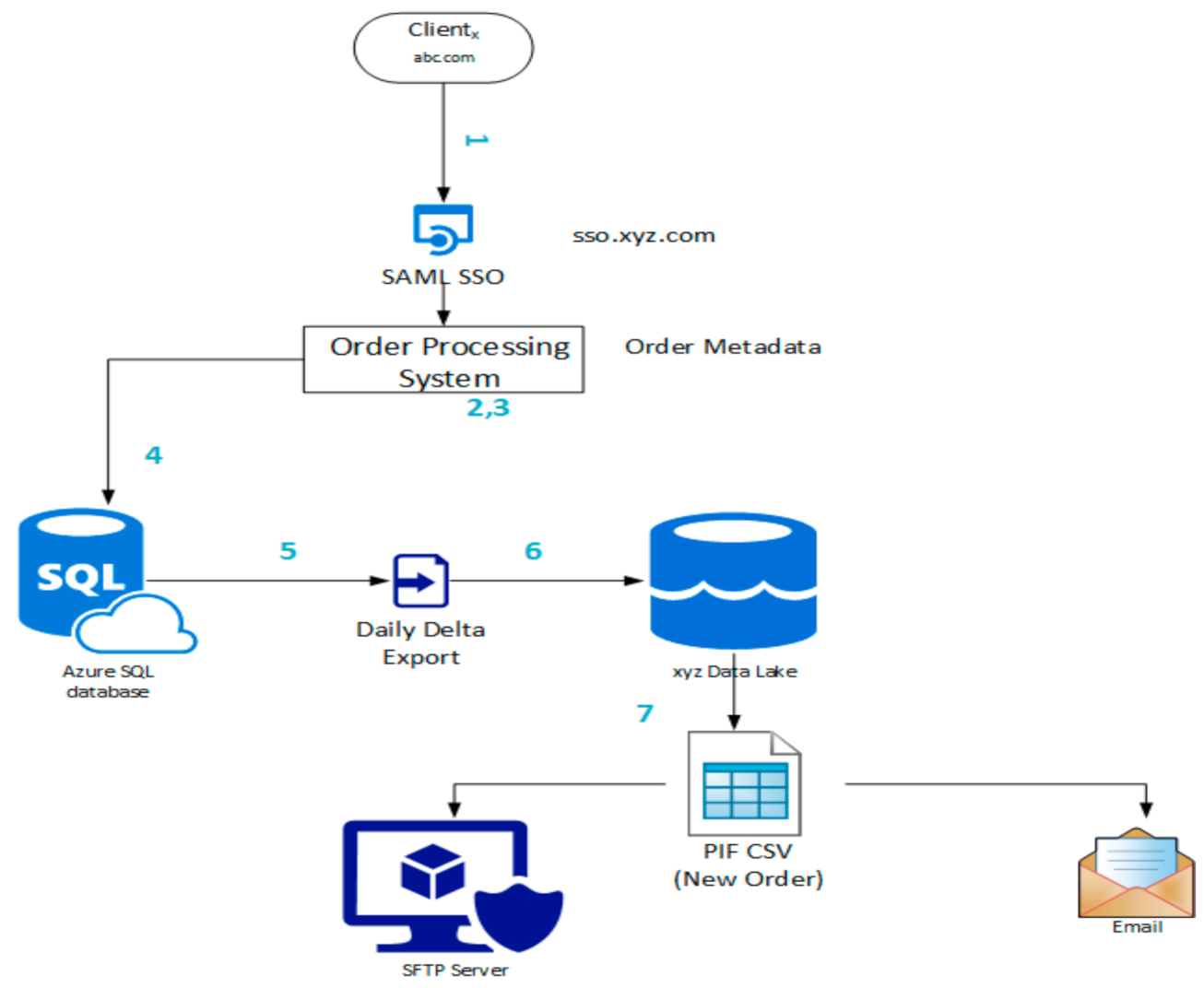
4.1. Example of the Order Process
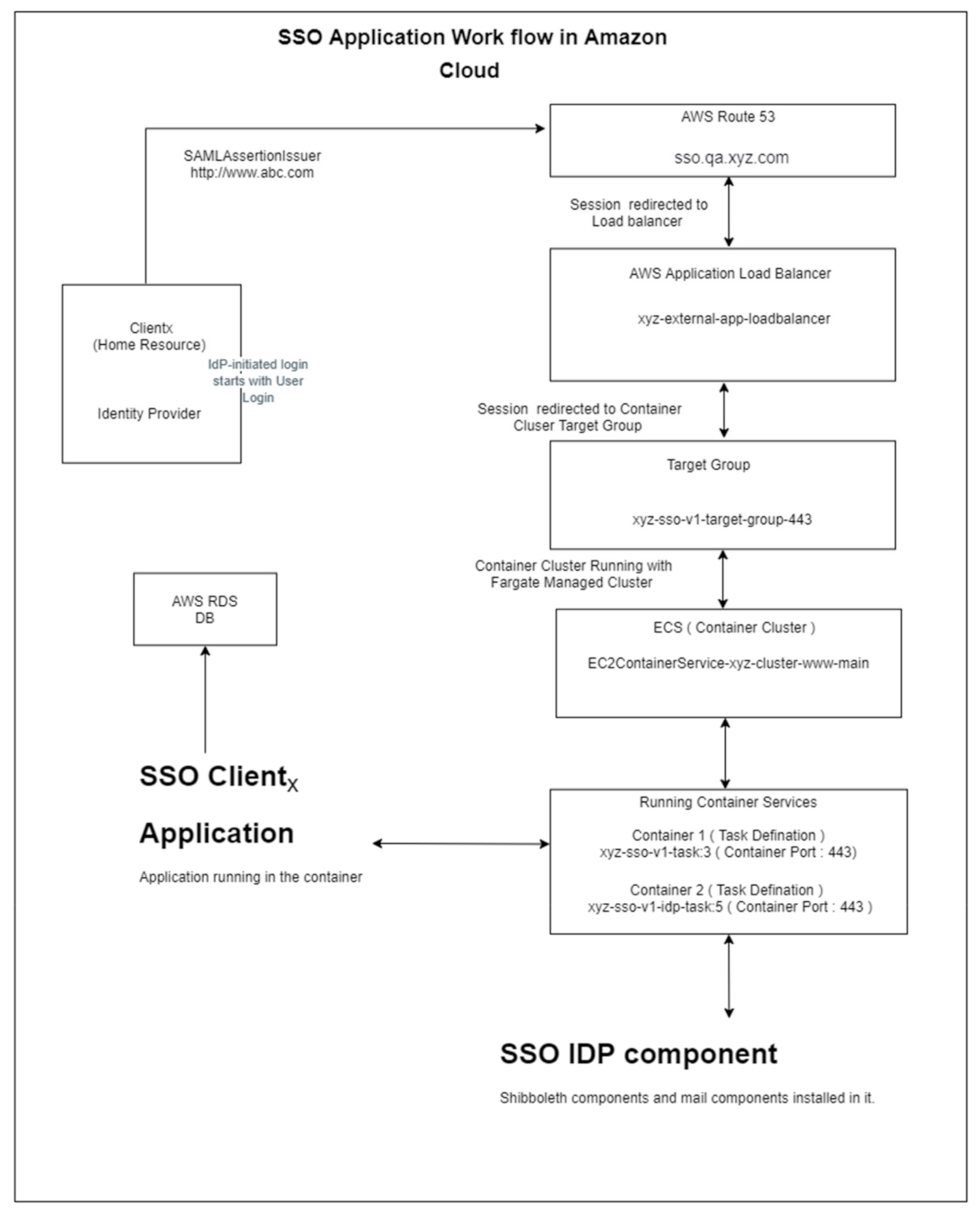
- Order initiated on clientx site “abc.com” and the SAML assertion issuer generates a SAML file to shift it to AWS Route 53 services for the next step.
- AWS Route 53 provides a cloud domain name service to translate the name into a specified IP address. Therefore, it will decode SAML files and fetch the required information from metadata in digits format and redirect it to a load balancer for the next process.
- The application’s load balancer provides content-based and specific protocol-based routing and delivery of the content. The content is monitored in this section and separated into the required content in CSV format. This sorted content is redirected toward the application target group.
- A target group informs the load balancer where the traffic is routed to the load balancer with a specific amazon elastic compute cloud (EC2) container, lambda functions, and specific IP address. Content with name xyz-sso-v1-target-group-443 is redirected on port 443.
- AWS Fargate works as “elastic container service” (ECS) and makes it very simple to deploy AWS container services. In this step, AWS container services run with the help of AWS Fargate. The container cluster is configured as EC2ContainerService-xyz-cluster-www-main.
- Running container services performs two tasks. Firstly, the data are stored in the AWS database and required data are emailed to the specific email group. Container 1 (Task definition): xyz-sso-v1-task: 3 (Container Port: 443). Secondly, it transfers the data to Shibboleth IDP for further processing and assigns an authority certificate.
- Container 2 (Task definition): xyz-sso-v1-idp-task: 5 (Container Port: 443). Shibboleth IDP matches the private key of metadata with the public key stored and assigns the TLS certificate as an authority.
4.2. Coding Example
| Algorithm 1 AWS order workflow algorithm. |
| Function lambda handler Pass In: event, context Connect to database and store connection Create a temporary table in database to store the changed rows Open file handler to csv FOR every row in temporary table Store row data in csv file ENDFOR Save file on file system Remove temporary table Close database connection IF csv file not empty Connect to email client Compose, attach file and send email to specified address PRINT “Email Sent the required address” ELSE PRINT “No records to notify. No email sent” Pass out: nothing ENDFUNCTION |
4.3. Multifactor Authentication
4.4. Authentication Metrics
4.5. Designed Model MFA Methods
5. Results and Discussions
Services Attack Model
- Attack surface is defined according to the proposed model in multi-cloud.
- Impact in terms of severity level, which causes damage in the environment.
- Designed metrics define the parameters used by the particular technique to overcome the attack.
- Proposed solution is defined as the MFA, SSO, or combination of MFA and SSO deployment.
- The efficacy of the proposed technique to avoid the particular attack in multi-cloud paradigm is defined in terms of the efficiency and cost effectiveness. Efficacy is measured in terms of how the proposed technique justifies and overcome attacks in terms of percentage.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Atat, R.; Liu, L.; Wu, J.; Li, G.; Ye, C.; Yang, Y.; Yi, Y. Big Data Meet Cyber-Physical Systems: A Panoramic Survey. IEEE Access 2018, 6, 73603–73636. [Google Scholar] [CrossRef]
- Akinrolabu, O.; New, S.; Martin, A. Assessing the Security Risks of Multicloud SaaS Applications: A Real-World Case Study. In Proceedings of the 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Paris, France, 21–23 June 2019; pp. 81–88. [Google Scholar]
- Akinrolabu, O.; Nurse, J.R.; Martin, A.; New, S. Cyber risk assessment in cloud provider environments: Current models and future needs. Comput. Secur. 2019, 87, 101600. [Google Scholar] [CrossRef]
- Kumar, R.; Goyal, R. On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Integration of blockchain and cloud of things: Architecture, applications and challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2521–2549. [Google Scholar] [CrossRef]
- Singh, M.M.; Ching, K.W.; Manaf, A.A. A novel out-of-band biometrics authentication scheme for wearable devices. Int. J. Comput. Appl. 2018, 42, 589–601. [Google Scholar] [CrossRef]
- Vehniä, V.J. Implementing Azure Active Directory Integration with an Existing Cloud Service. Master’s Thesis, University of VAASA, Vaasa, Finland, 2020. [Google Scholar]
- Arunarani, A.R.; Manjula, D.; Sugumaran, V. Task scheduling techniques in cloud computing: A literature survey. Future Gener. Comput. Syst. 2019, 91, 407–415. [Google Scholar] [CrossRef]
- Bhagyoday, R.; Kamani, C.; Bhojani, D.; Parmar, V. Comprehensive Study of E-Health Security in Cloud Computing. Int. Res. J. Eng. Technol. (IRJET) 2019, 1216–1228. [Google Scholar]
- Bendiab, G.; Shiaeles, S.; Boucherkha, S.; Ghita, B. FCMDT: A novel fuzzy cognitive maps dynamic trust model for cloud federated identity management. Comput. Secur. 2019, 86, 270–290. [Google Scholar] [CrossRef]
- Yıldırım, M.; Mackie, I. Encouraging users to improve password security and memorability. Int. J. Inf. Secur. 2019, 18, 741–759. [Google Scholar] [CrossRef]
- Pilar, D.R.; Jaeger, A.; Gomes, C.F.A.; Stein, L.M. Passwords Usage and Human Memory Limitations: A Survey across Age and Educational Background. PLoS ONE 2012, 7, e51067. [Google Scholar] [CrossRef] [PubMed][Green Version]
- Cheng, H.; Rong, C.; Qian, M.; Wang, W. Accountable Privacy-Preserving Mechanism for Cloud Computing Based on Identity-Based Encryption. IEEE Access 2018, 6, 37869–37882. [Google Scholar] [CrossRef]
- Jegadeesan, S.; Azees, M.; Kumar, P.M.; Manogaran, G.; Chilamkurti, N.; Varatharajan, R.; Hsu, C.-H. An efficient anonymous mutual authentication technique for providing secure communication in mobile cloud computing for smart city applications. Sustain. Cities Soc. 2019, 49, 101522. [Google Scholar] [CrossRef]
- Faheem, M.; Akram, U.; Khan, I.; Naqeeb, S.; Shahzad, A.; Ullah, A.; Mushtaq, M.F. Cloud Computing Environment and Security Challenges: A Review. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 183–195. [Google Scholar] [CrossRef]
- Veerabathiran, V.K.; Mani, D.; Kuppusamy, S.; Subramaniam, B.; Velayutham, P.; Sengan, S.; Krishnamoorthy, S. Improving secured ID-based authentication for cloud computing through novel hybrid fuzzy-based homomorphic proxy re-encryption. Soft Comput. 2020, 24, 18893–18908. [Google Scholar] [CrossRef]
- Varghese, B.; Buyya, R. Next generation cloud computing: New trends and research directions. Futur. Gener. Comput. Syst. 2018, 79, 849–861. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. On the Design of Provably Secure Lightweight Remote User Authentication Scheme for Mobile Cloud Computing Services. IEEE Access 2017, 5, 25808–25825. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Li, H.; Yang, K.; Cheng, N.; Shen, X.S. PROTECT: Efficient Password-based Threshold Single-sign-on Authentication for Mobile Users against Perpetual Leakage. IEEE Trans. Mobile Comput. 2020. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Kumari, S.; Huang, X.; Wazid, M. Provably secure authenticated key agreement scheme for distributed mobile cloud computing services. Futur. Gener. Comput. Syst. 2017, 68, 74–88. [Google Scholar] [CrossRef]
- Zahra, S.; Alam, M.; Javaid, Q.; Wahid, A.; Javaid, N.; Malik, S.U.R.; Khan, M.K. Fog Computing Over IoT: A Secure Deployment and Formal Verification. IEEE Access 2017, 5, 27132–27144. [Google Scholar] [CrossRef]
- Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-Factor Authentication: A Survey. Cryptography 2018, 2, 1. [Google Scholar] [CrossRef]
- Ramachandran, S.; Shanmugam, V. A two way authentication using bilinear mapping function for wireless sensor networks. Comput. Electr. Eng. 2017, 59, 242–249. [Google Scholar] [CrossRef]
- Fang, L.; Yin, C.; Zhou, L.; Li, Y.; Su, C.; Xia, J. A physiological and behavioral feature authentication scheme for medical cloud based on fuzzy-rough core vector machine. Inf. Sci. 2020, 507, 143–160. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Futur. Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Irshad, A.; Sher, M.; Ahmad, H.F.; Alzahrani, B.A.; Chaudhry, S.A.; Kumar, R. An improved Multi-server Authentication Scheme for Distributed Mobile Cloud Computing Services. TIIS 2016, 10, 5529–5552. [Google Scholar]
- Soni, P.; Pal, A.K.; Islam, S.H. An improved three-factor authentication scheme for patient monitoring using WSN in remote health-care system. Comput. Methods Programs Biomed. 2019, 182, 105054. [Google Scholar] [CrossRef]
- Patel, S.C.; Jaiswal, S.; Singh, R.S.; Chauhan, J. Access Control Framework Using Multi-Factor Authentication in Cloud Computing. Int. J. Green Comput. 2018, 9, 1–15. [Google Scholar] [CrossRef]
- Anakath, A.S.; Rajakumar, S.; Ambika, S. Privacy preserving multi factor authentication using trust management. Clust. Comput. 2019, 22, 10817–10823. [Google Scholar] [CrossRef]
- Singh, C.; Singh, D. A 3-Level Multifactor Authentication Scheme for Cloud Computing. Int. J. Comput. Eng. Technol. 2019, 10, 184–195. [Google Scholar] [CrossRef]
- Mohsin, J.K.; Han, L.; Hammoudeh, M.; Hegarty, R. Two Factor Vs Multi-factor, an Authentication Battle in Mobile Cloud Computing Environments. In Proceedings of the International Conference on Big Data and Internet of Thing—BDIOT2017, London, UK, 20–22 December 2017; p. 39. [Google Scholar]
- Kumar, M.; Sharma, S.C.; Goel, A.; Singh, S.P. A comprehensive survey for scheduling techniques in cloud computing. J. Netw. Comput. Appl. 2019, 143, 1–33. [Google Scholar] [CrossRef]
- Kim, A.; Wang, C.; Seo, S.-H. PCA-CIA Ensemble-based Feature Extraction for Bio-Key Generation. KSII Trans. Internet Inf. Syst. 2020, 14, 2919–2937. [Google Scholar] [CrossRef]
- Fernandez-Carames, T.M.; Fraga-Lamas, P. Towards Post-Quantum Blockchain: A Review on Blockchain Cryptography Resistant to Quantum Computing Attacks. IEEE Access 2020, 8, 21091–21116. [Google Scholar] [CrossRef]
- Petrache, A.L.; Suciu, G. Security in Quantum Computing. Ann. Disaster Risk Sci. ADRS 2020, 3, 43–50. [Google Scholar]
- Challagidad, P.S.; Birje, M.N. Multi-dimensional dynamic trust evaluation scheme for cloud environment. Comput. Secur. 2020, 91, 101722. [Google Scholar] [CrossRef]
- Karie, N.M.; Kebande, V.R.; Ikuesan, R.A.; Sookhak, M.; Venter, H.S. Hardening SAML by Integrating SSO and Multi-Factor Authentication (MFA) in the Cloud. In Proceedings of the 3rd International Conference on Networking, Information Systems & Security, Marrakech, Morocco, 15 December 2020; pp. 1–6. [Google Scholar]
- Singh, S.; Ra, I.H.; Meng, W.; Kaur, M.; Cho, G.H. SH-BlockCC: A secure and efficient Internet of things smart home architecture based on cloud computing and blockchain technology. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719844159. [Google Scholar] [CrossRef]
- Khine, P.P.; Wang, Z.S. Data lake: A new ideology in big data era. In Proceedings of the 4th Annual International Conference on Wireless Communication and Sensor Network, EDP Sciences. Wuhan, China, 15–17 December 2017; Volume 17, p. 03025. [Google Scholar]
- Acar, A.; Liu, W.; Beyah, R.; Akkaya, K.; Uluagac, A.S. A privacy preserving multi factor authentication using trust management. Secur. Priv. 2019, 2, e88. [Google Scholar]
- Kaleeswari, C.; Maheswari, P.; Kuppusamy, K.; Jeyabalu, M. A brief review on cloud security scenarios. Int. J. Sci. Res. Sci. Technol. 2018, 4, 46–50. [Google Scholar]
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef]
- Devi, B.T.; Shitharth, S.; Jabbar, M.A. An Appraisal over Intrusion Detection Systems in Cloud Computing Security Attacks. In Proceedings of the 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 722–727. [Google Scholar]
- Idhammad, M.; Afdel, K.; Belouch, M. Distributed Intrusion Detection System for Cloud Environments based on Data Mining techniques. Procedia Comput. Sci. 2018, 127, 35–41. [Google Scholar] [CrossRef]
- Albladi, S.M.; Weir, G.R. User characteristics that influence judgment of social engineering attacks in social networks. Human-centric Comput. Infor. Sci. 2018, 8, 1–24. [Google Scholar] [CrossRef]
- Schechter, S.; Tian, Y.; Herley, C. StopGuessing: Using Guessed Passwords to Thwart Online Guessing. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; pp. 576–589. [Google Scholar]



| Author(s) | Concerns | Impact Vector | Proposed Solution | Method |
|---|---|---|---|---|
| Cheng et al. [13] IEEE Access (2018) | Privacy, adversary attacks, security | Accountability, audit, logical statistic model | Identity-based model to preserve acceptability and privacy of cloud computing | SSO |
| Jegadeesan [14] Sustainable Cities and Society (2019) | Authentication, SSL-based encryption | Cost, session key exchange | Diverse mutual authentication model | MFA |
| Veerabathiran et al. [16] Soft Computing (2020) | Remote information sharing | access control mechanism, confidentially data | ID-based homomorphic proxy and re-encryption | SSO |
| Zhang et al. [19] IEEE Transactions on Mobile Computing (2020) | Identity provider (IDP) authentication | Computational cost, storage cost | Inception password-based SSO model | SSO |
| Ometov et al. [22] Cryptography (2018) | Industrial and educational aspects | Adopting MFA | Survey based on factors currently applied for multifactor authentication | MFA |
| Fang et al. [24] Information Sciences (2020) | Medical cloud MFA technique | Vector machine is used to classify and categorize a fuzzy data in medical cloud | Fuzzy set-based physiological and behavioral feature authentication system | MFA |
| Zhou et al. [25] Future Generation Computer Systems (2019) | Authentication in IoT-based smart devices | security and computational limited smart device | security protocol to enhance authentication in cloud-based IoT | MFA |
| Soni et al. [27] Computer methods and programs in biomedicine (2019) | MFA in remote sensor network | Patient data’s health care safety and security | Three-factors authentication on behavioral and biomedical logic | MFA |
| Patel et al. [28] International Journal of Green Computing (2018) | Mobile phone, software token, and one-time password | Characteristic and biological behavior to access cloud | Access control-based framework focusing on the characteristic and biological behavior | SSO |
| Anakath et al. [29] Cluster Computing (2019) | De-centralization of remote locations | Transparency and access on key-vault | Privacy-based multifactor authentication mechanism to achieve trust | MFA |
| Charanjeet et al. [30] International Journal of Computer Engineering and Technology (2019) | Mitigating man-in-the-middle (MIM) attacks | One-time password (OTP), out-of-band (OOB), and image click | Three-level MFA for cloud computing | MFA |
| Kim et al. [33] KSII Transactions on Internet and Information Systems (2020) | Storage size and CPU cycle for the signature authentication | Post-quantum computing methods and blockchain authentication | Secret key prevention technique for any third party using the multivariate biometric key functions | SSO and MFA |
| Fernandez et al. [34] IEEE Access (2020) | Privacy and authentication in quantum computing | Post-quantum cryptosystems | Public-key cryptography and hash functions-based model | SSO and MFA |
| Attack Name | Attack Surface | Impact | Designed Metrics | Proposed Solution | Efficacy | |
|---|---|---|---|---|---|---|
| 1 | Honeypot attacks | Email traps, malware honeypot, decay database, spider honeypot | High | User credentials and identity | Hybrid (MFA and SSO) | 95% |
| 2 | Dictionary attacks | Auto login, auto fill, remember password, secondary access code | Medium | User metadata and schema | SSO | 96% |
| 3 | Brute force attacks | Spam ads, tracking malware, website redirection | Medium | Credentials stuffing | MFA | 98% |
| 4 | Traffic interception attacks | Credentials theft, intrusion traps | Low | Metadata scamming | MFA | 93% |
| 5 | Man-in-the-middle attacks | Intrusion detection traps, traffic analyzer, scamming | Low | Traffic header, attached metadata, redirection | MFA | 96% |
| 6 | Key logger attacks | Key stork, login information | Medium | Information estimation | SSO | 97% |
| 7 | Social engineering attacks | Victim identification, track covering, foothold expanding, story sapping | Medium | Background information gathering, target engagement, data siphoning | Hybrid (MFA and SSO) | 94% |
| 8 | Thwarting password attacks | Dictionary, brute force, man-in-the-middle, social engineering, key logger, traffic interception | High | User, information, credentials and metadata | Hybrid (MFA and SSO) | 96% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hussain, M.I.; He, J.; Zhu, N.; Sabah, F.; Zardari, Z.A.; Hussain, S.; Razque, F. AAAA: SSO and MFA Implementation in Multi-Cloud to Mitigate Rising Threats and Concerns Related to User Metadata. Appl. Sci. 2021, 11, 3012. https://doi.org/10.3390/app11073012
Hussain MI, He J, Zhu N, Sabah F, Zardari ZA, Hussain S, Razque F. AAAA: SSO and MFA Implementation in Multi-Cloud to Mitigate Rising Threats and Concerns Related to User Metadata. Applied Sciences. 2021; 11(7):3012. https://doi.org/10.3390/app11073012
Chicago/Turabian StyleHussain, Muhammad Iftikhar, Jingsha He, Nafei Zhu, Fahad Sabah, Zulfiqar Ali Zardari, Saqib Hussain, and Fahad Razque. 2021. "AAAA: SSO and MFA Implementation in Multi-Cloud to Mitigate Rising Threats and Concerns Related to User Metadata" Applied Sciences 11, no. 7: 3012. https://doi.org/10.3390/app11073012
APA StyleHussain, M. I., He, J., Zhu, N., Sabah, F., Zardari, Z. A., Hussain, S., & Razque, F. (2021). AAAA: SSO and MFA Implementation in Multi-Cloud to Mitigate Rising Threats and Concerns Related to User Metadata. Applied Sciences, 11(7), 3012. https://doi.org/10.3390/app11073012







