Abstract
Spectrum sensing (SS) has attracted much attention due to its important role in the improvement of spectrum efficiency. However, the limited sensing time leads to an insufficient sampling point due to the tradeoff between sensing time and communication time. Although the sensing performance of cooperative spectrum sensing (CSS) is greatly improved by mutual cooperation between cognitive nodes, it is at the expense of computational complexity. In this paper, efficient approximations of the N-out-of-K rule-based CSS scheme under heterogeneous cognitive radio networks are provided to obtain the closed-form expression of the sensing threshold at the fusion center (FC), where the false alarm probability and its corresponding detection probability are approximated by the Poisson distribution. The computational complexity required to obtain the optimal sensing threshold at the FC has greatly decreased and theoretical derivations state that the approximation error is negligible. The simulations validate the effectiveness of the proposed scheme.
1. Introduction
With the deep integration of the emerging information technology and wireless communication represented by mobile internet, the internet of things, and cloud computing, radio technology is widely used under the broadband, ubiquitous, and mobile application scenarios, which leads to the explosive growth of spectrum demand, resulting in an extreme shortage of spectrum resources [1]. How to improve the spectrum utilization has become a hot issue and has attracted much attention as a consequence.
Cognitive radio (CR), despite being universal, is one of the enabling technologies for the current internet of things (IoT) [2,3,4] because it is devoted to searching idle spectrum of the registered user and providing opportunistic access at any time if the radio spectrum of the registered user is unoccupied [5,6]. As a result, CR has made great contributions to improving spectrum utilization and has developed into an emerging technology. Heterogeneous cognitive radio network (HCRN) [7] denotes a type of network that runs on different protocols to support different functions or applications, due to the differences such as network device, the system, etc. As a result, HCRN is widely discussed for CR because of its universality. The most important procedure behind CR is to periodically detect the observed spectrum and determine the spectrum usage status, named spectrum sensing (SS) [8,9]. In SS, the registered user is defined as the primary user (PU) and the user waiting for opportunistic access is denoted as the secondary user (SU) [10]. In a SS cycle, if the spectrum of PU is idle, SU will quickly access this band. Once the PU is back, SU will immediately release the corresponding spectrum resources.
Generally, the performance of SS is evaluated by two metrics, detection probability and false alarm probability [11]. A higher detection probability corresponds to a stronger capacity of protecting PU from SU while a lower false alarm probability corresponds to a higher system throughput of SU. The CR system with a lower false alarm probability tends to have a higher throughput [12]. As a result, the combination of detection probability and false alarm probability always works as the performance evaluation index of SS [13].
In the literature, much work has been conducted for SS. Classical SS schemes mainly contain matched filtering [14], energy detection (ED) [15], cyclic spectrum detection [16], covariance matrix detection [17], cooperative spectrum sensing (CSS) [18,19,20,21,22,23], etc. When the prior information of the primary signal is known, the matching filtering is the optimal SS scheme. ED shows good characteristics in practical application, but its performance is limited by the time variation of noise power. Cyclic spectrum detection can effectively eliminate noise uncertainty and improve the performance of SS, but it requires a higher sampling rate and a longer spectrum sensing time. Covariance matrix detection is a broadband SS technology, which can effectively improve the efficiency of SS and improve the throughput of the CR system. However, its detection complexity is high and it is impossible to distinguish the number of users when multiple PUs coexist.
In the process of SS, the single-node detection is easily affected by channel fading, shadow effect, noise uncertainty, and other factors, resulting in a serious decline in detection performance. However, the influence may be decreased by the centralized data fusion or decision fusion for the CSS. To solve these issues, CSS [18,19,20,21,22,23] is proposed, which can significantly improve the sensitivity and the accuracy of SS by data fusion. CSS contains distributed CSS and centralized CSS based on the method of data fusion. In the distributed CSS, the sensing nodes communicate with each other and the sensing decision is made at each node based on the received decision from the other nodes. The centralized CSS makes the decision at the fusion center (FC) based on the sensing conditions of the other nodes. The sensing decision will be sent to each sensing node once the final decision is made at the FC. Distributed CSS can effectively improve the sensing accuracy of the CR system. However, it is at the expense of network burden and system overhead. In consequence, centralized CSS is mainly considered in this paper.
Classical centralized CSS contains the data fusion-based schemes and the decision fusion-based schemes. The data fusion-based schemes mainly contain equal gain combining (EGC) [24], selection combining (SC) [25], maximal ratio combining (MRC) [26], etc. The decision fusion-based schemes mainly contain the AND rule [27], the OR rule [28], the N-out-of-K rule [29], etc. The reason why the decision fusion-based schemes are considered in this paper is that the computational complexity of the decision fusion-based scheme is lower than that of the data fusion-based scheme.
For the decision fusion-based CSS schemes, under HCRN situations, the N-out-of-K rule is widely accepted due to its superb performance. However, the closed-form expression of its corresponding optimal sensing threshold is unavailable at the FC since the objective function of the sensing performance is non-convex on the sensing threshold [24]. To obtain the closed-form expression of the optimal sensing threshold for the N-out-of-K rule-based CSS scheme under the HCRN situation, this paper is devoted to an approximation evaluation of the false alarm probability and detection probability for N-out-of-K rule-based CSS schemes for the HCRNs within the error range allowed by the system. The proposed approximation scheme balances the sensing accuracy and the sensing complexity, which helps to obtain the closed-form expression of the optimal sensing threshold for the N-out-of-K rule-based CSS scheme under the HCRN situation at the FC. The main contribution of this paper is summarized as follows:
- We provide an effective approximation of the N-out-of-K rule for heterogeneous cognitive radio networks and give the closed-form solution of the detection probability and its corresponding false alarm probability. On this basis, the closed-form expression of the optimal sensing threshold for the N-out-of-K rule-based CSS scheme is obtained under the HCRN situation.
- Theoretical analysis is conducted on the approximation error and it is demonstrated that the approximation error is within the tolerance of the system.
- We conduct simulation experiments in the Rayleigh fading channel to validate our conclusions proposed in this paper.
The rest of this paper is organized as follows. Section 2 reviews the related work of SS. The main contribution of this paper is shown in Section 3, which contains the whole theoretical derivations. Simulation experiments and result analysis are accomplished in Section 4. Finally, Section 5 concludes this paper.
2. Related Work
In this section, the motivation of this paper is concluded and then the system model is provided thereafter.
2.1. Motivation
In the literature, most of the CSS schemes are based on the assumption that the local sensing results are independent and identically distributed. However, the assumption is unrealistic in practical applications. As a result, the independent and non-identically distributed CSS, namely, HCRN, is discussed in this paper. For the state-of-the-art research on the HCRN, the N-out-of-K rule is widely considered due to its superb performance, compared with the AND rule and the OR rule. However, the closed-form expression for the optimal sensing threshold of the N-out-of-K rule-based HRCN, namely the optimal K, is difficult to obtain at present, according to the discussion in [24].
The sensing threshold at the FC directly determines the sensing performance of the N-out-of-K rule-based HRCN. How to obtain a closed-form expression for the optimal sensing threshold of the N-out-of-K rule-based HRCN seems significant for the further development of the HCRN and serves as the motivation for this paper.
2.2. System Model
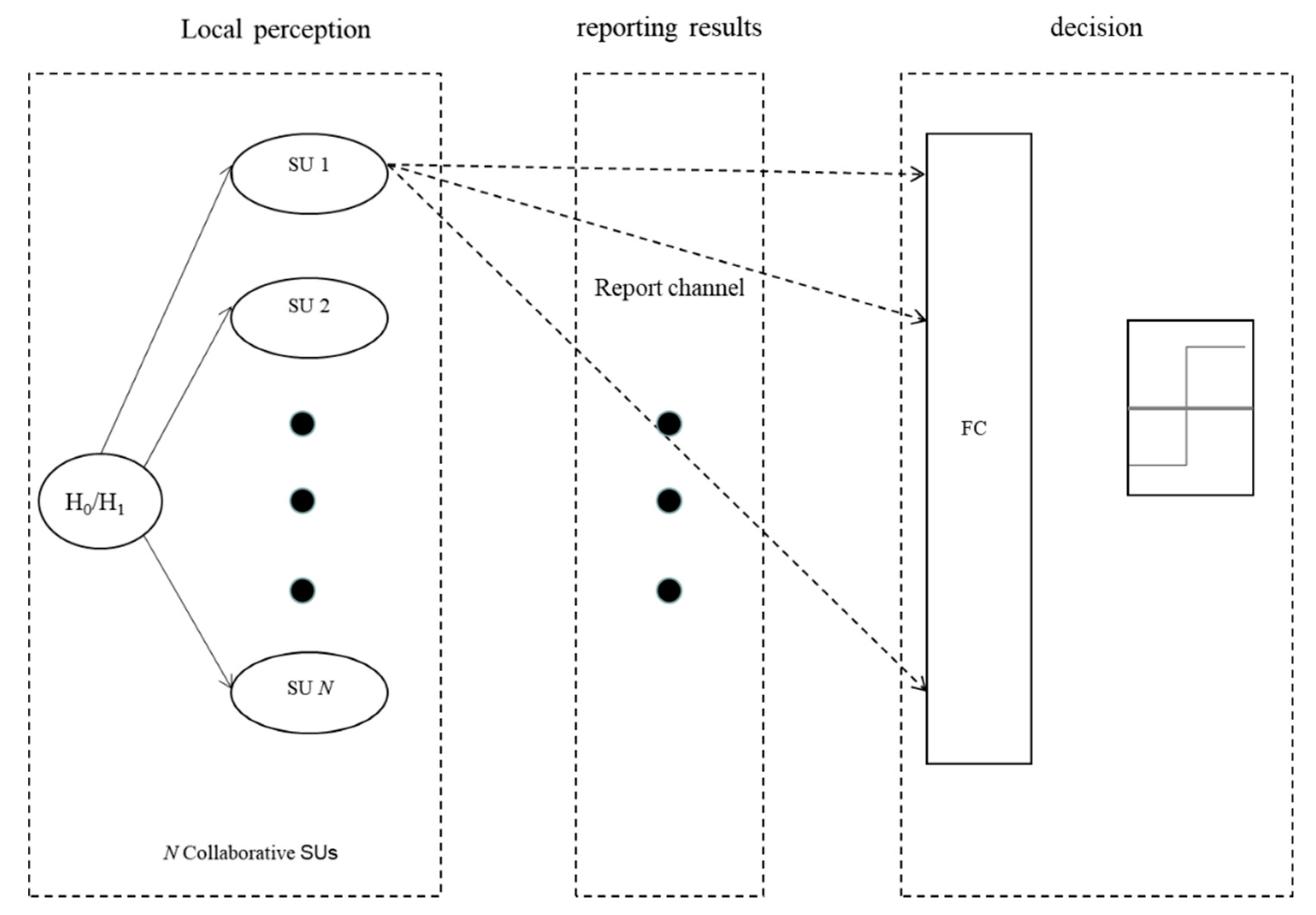
We consider a centralized CSS scenario, where there are K local detectors and an FC. The local detector makes a binary decision on the local SS result, based on ED, and the local sensing results are sent to the FC for the final decision on whether the observed spectrum is idle (Figure 1).
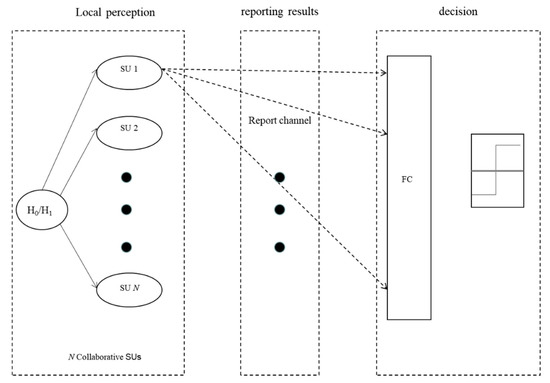
Figure 1.
System scenario.
For the local detector, the false alarm probability and detection probability are respectively denoted as and . We assume the channel between SU and FC is independent and identically distributed, and so stationary random process with error probability , the false alarm probability and detection probability of the local detector [30] at the FC can be formulated as it is shown in Equations (1) and (2):
We assume the judgment result of the local detector can be written as it is shown in Equation (3),
where denotes the observed spectrum band is idle while denotes the observed spectrum band is busy.
Then, the final false alarm probability and detection probability at the FC with N-out-of-K rule [31] can be denoted as it is shown in Equations (4) and (5):
This paper mainly considers the case where the local sensing results in Equations (4) and (5) are independent and non-identically distributed Bernoulli random variables, then the mass function probability at the FC on Di [30] can be described as it is shown in Equations (6) and (7):
Finally, the false alarm probability and its corresponding detection probability [32] can be reformulated as it is shown in Equations (8)–(10):
3. Proposed Strategy
In this section, the main work and contribution of this paper are provided, where the false alarm probability and the detection probability are approximate to a Poisson distribution. The approximation error is discussed and demonstrated therein.
3.1. Main Contribution
According to Equations (6)–(10), the closed-form solutions of the optimal sensing threshold at the FC for the N-out-of-K based CSS under the HCRN situations cannot be obtained in the case where local sensing results are independent and non-identically distributed. As a result, reasonable approximations for the false alarm probability and detection probability in Equations (8) and (9) are needed to obtain the optimal solution on the sensing threshold at the FC.
In this paper, the detection probability and its corresponding false alarm probability in Equation (8) and (9) are respectively approximate to two Poisson distributions [33] as it is shown in Equations (11)–(14):
where denotes the sensing threshold of the N-out-of-K rule at the FC. and are the corresponding parameters of the two Poisson distributions. The approximation error will be discussed in the next section.
Then, the sensing threshold can be obtained by minimizing the error probability (the sum of false alarm probability and missed detection probability). The optimal sensing threshold can be obtained by the convex optimization and can be written as it is shown in Equation (15):
where denotes the rounding up function.
3.2. Approximation Error Analysis
We respectively define the judgment result of every local detector and the FC as , then can be written as it is shown in Equation (16):
where is the Bernoulli random variable.
Equations (17)–(20) are defined as follows:
where m denotes the nonnegative integer.
For every real-valued function f defined on the non-negative integers [34], Equations (21)–(24) is obtained:
We define:
Then, Equation (21) can be reformulated as it is shown in Equation (25):
To make this approximation more apparent, we define Equation (26) as follows:
where h is a bounded real-valued function on non-negative integers.
The solution of Equation (24) can be given by Equation (27):
We denote the solution of Equation (26) for by . According to Equations (21) and (27), Equation (28) can be obtained:
Theorem 1.
If are independent and , then for and , Equation (29) is obtained:
where C a constant [31].
Proof.
According to Equation (22), Equations (30) and (31) is obtained:
where and are two random indices. ☐
Equation (30) can be further denoted as it is shown in Equations (32)–(34):
Based on the Lemmas 5.2 and 5.3 in [31], Equation (32) can be written as it is shown in Equation (35):
According to Lemma 5.5 in [34], Equations (36) and (37) can be obtained:
Then, Equation (38) is obtained
Based on Jensen’s inequality, Equation (39) and (40) is obtained:
Theorem 1 states that the approximation error of W is small enough.
3.3. The Threats to Validity
In cognitive radio networks, Equation (41) holds:
According to Equation (41), Equation (42) can be obtained:
In extreme cases , the following conclusion can be drawn according to Theorem 1: the approximation error decrease with the rise of N, when the approximation error is below . If , the approximation error is lower than 2, even under the extreme case . If , the approximation error is lower than 2, even under the extreme case .
As a result, the approximation error decreases with the rise of SU. If the number of SU is very small, a possible scheme to reduce the approximation error is to improve the sampling points, which can make the detection probability at a high level and make the false alarm probability lower.
3.4. Complexity Analysis
Note that the closed-form expression of the optimal sensing threshold for the N-out-of-K rule-based CSS scheme under the HCRN situations is unavailable according to the discussion in [24]. The optimal sensing threshold at the FC of the classical N-out-of-K rule-based CSS scheme under the HCRN situation is obtained by iteration and comparison.
According to Equations (6) and (7), the required multiplication operation is while the required addition operation is for the mass function probability at the FC on . To obtain the optimal sensing threshold for Equations (8) and (9), N iterations are required. In consequence, the required multiplication operation is and the required addition operation is for the classical N-out-of-K rule-based CSS scheme.
For the proposed scheme, Equations (8) and (9) are respectively approximated to the Poisson distribution with the parameter and . As a result, the required operation for the proposed scheme is which is greatly reduced compared with the classical N-out-of-K rule-based CSS scheme.
4. Simulation and Discussion
In this section, simulations based on the MATLAB platform are used to examine the performance of the proposed sensing strategy for SS. In the simulation, the BPSK modulated signal is considered as the primary signal with the bandwidth 2000 Hz, the background noise is the additive white Gaussian noise (AWGN) [35] and the sampling frequency at the receiver of the local detector is the same as the bandwidth of the primary signal. ED is regarded as the local detector and the Rayleigh fading channel is considered. In the CR network, 15 SUs are considered. We assume that the time for each SU to send its sensing results to FC is much shorter than the sensing duration. Two different types of detectors are designed in the paper to simulate the situation of heterogeneous detectors, where the signal-to-noise ratio (SNR) of one kind of detector is and the SNR of the other detectors is . The number of the first types of detectors is denoted as .
In addition, the Rayleigh fading is generated based on the built-in function of MATLAB in Monte Carlo simulations, where the sampling frequency and the Doppler shift are fixed. As a result, an ensemble of fading random variables is made with the fixed parameters to get a sense of expected performance in the Monte Carlo experiment of this paper.
It states that the main contribution of this paper consists in the closed-form expression of the optimal sensing threshold at the FC for the N-out-of-K rule-based CSS scheme under the HCRN situations by Poisson distribution. In consequence, the comparisons of the optimal sensing threshold at the FC between the proposed scheme and the classical scheme are mainly considered in the simulations under various scenarios. For the proposed scheme, the optimal sensing threshold is obtained by the closed-form solution provided in this paper while the optimal sensing threshold of the classical scheme is obtained by iteration and comparison. The optimal sensing threshold of the classical scheme is the theoretical value and the optimal sensing threshold of the classical scheme is the evaluated value.
4.1. Simulation Results
Generally, the sensing threshold of the SU,, is evaluated under the scenarios as follows. Note that denotes the sensing threshold of the local energy detector, which is different from the sensing threshold at FC.
- (1)
- Scenario I: The SUs make the decisions at the same sensing threshold and the sensing threshold, , is determined by minimizing the total error rate at the FC.
- (2)
- Scenario II: The sensing threshold of the SU,, is calculated by minimizing the total error rate.
- (3)
- Scenario III: is determined by minimizing the local false alarm probability while detection probability is above the minimum requirements of the CR system.
- (4)
- Scenario IV: All the SUs make the decision by the fixed threshold.
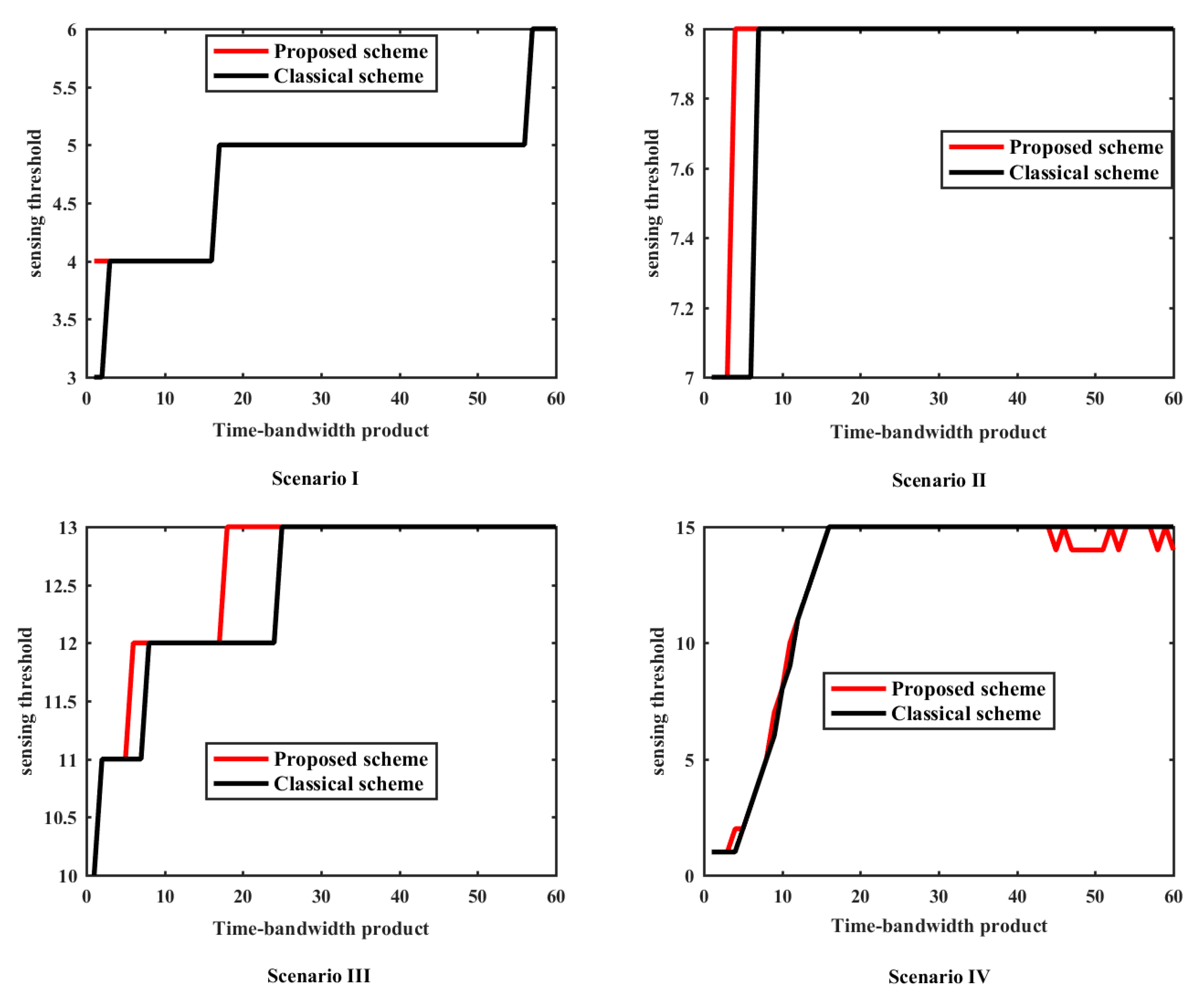
Figure 2 exhibits sensing threshold comparisons with different sensing times at the FC under various scenarios, where the four scenarios correspond with the mentioned above and . The time-bandwidth product [24] is the product of the duration of a signal and its spectral width. The time-bandwidth product measures how well we use the available bandwidth for a given channel, which is positively correlated with the sensing time in the simulation due to the fixed bandwidth. As a result, the time-bandwidth product is approximately equivalent to the sampling points of the local SS detectors in this paper. The classical scheme in Figure 2 denotes the scheme in Equations (8) and (9).
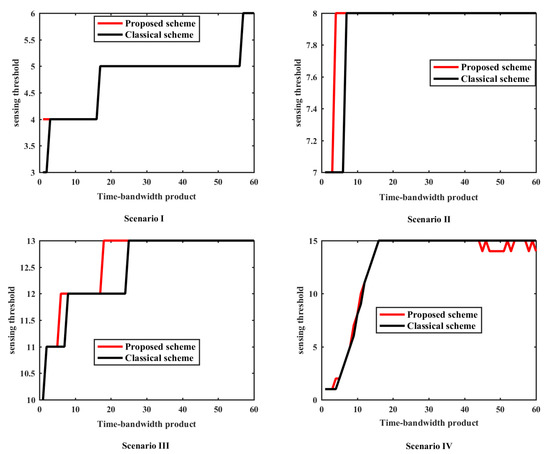
Figure 2.
The sensing threshold comparisons under various scenarios with the different time-bandwidth products. Scenario I, Scenario II, Scenario III and Scenario IV respectively corresponds with the scenarios mentioned above.
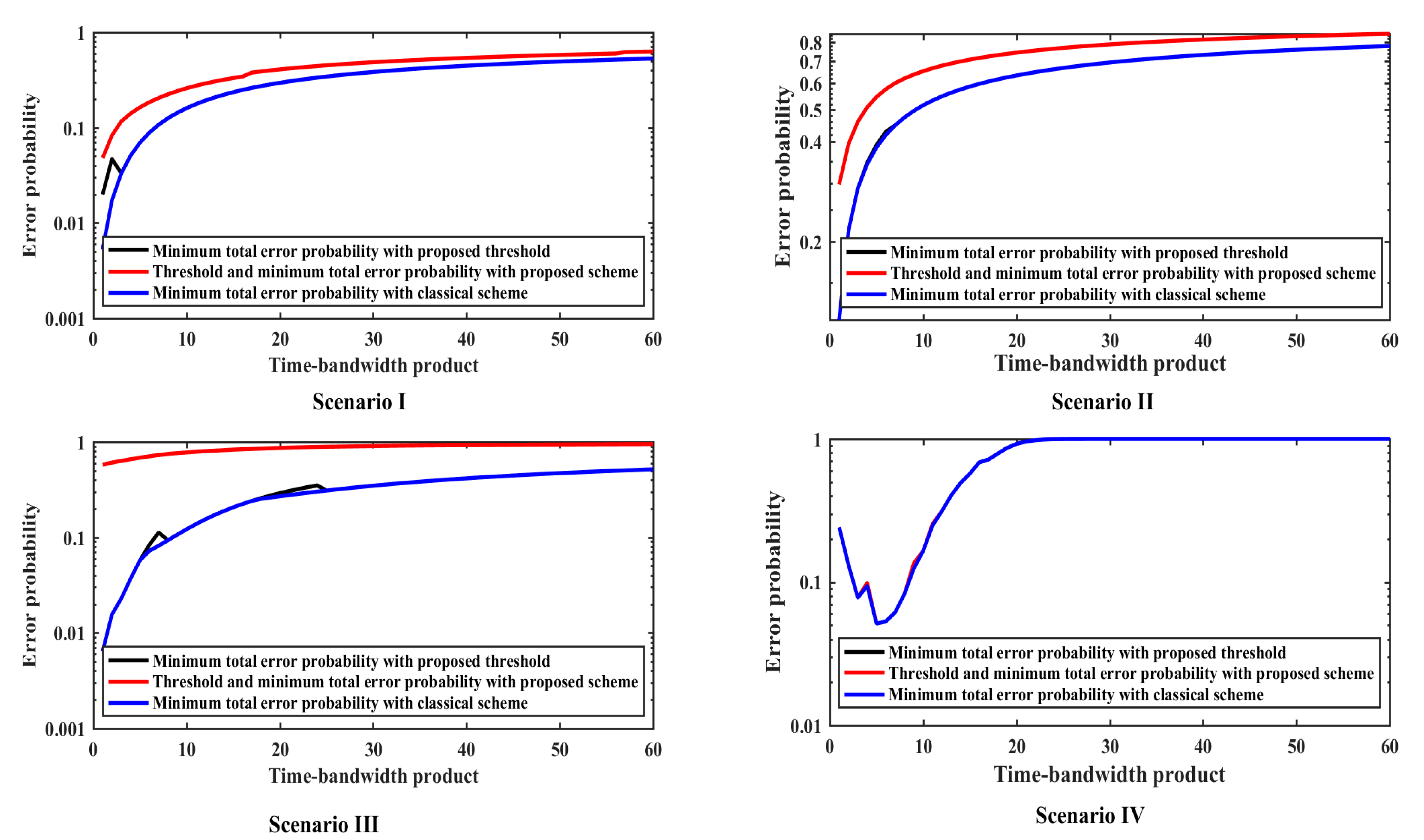
The total error probability is shown in Figure 3 under four scenarios. The red line denotes the proposed scheme, where both the sensing threshold and the minimum total error probability are with the proposed scheme. The black line denotes the minimum total error probability with the classical scheme. The blue line denotes the real minimum total error probability with the proposed sensing threshold. The main difference between the red line and the green line is that the minimum total error probability of the red line is evaluated by the proposed scheme in this paper and the minimum total error probability of the green line is calculated by the evaluated sensing threshold in this paper.
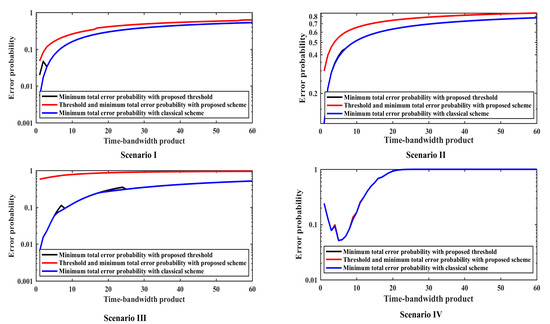
Figure 3.
The total error probability comparisons under various scenarios. Scenario I, Scenario II, Scenario III and Scenario IV respectively corresponds with the scenarios mentioned above.
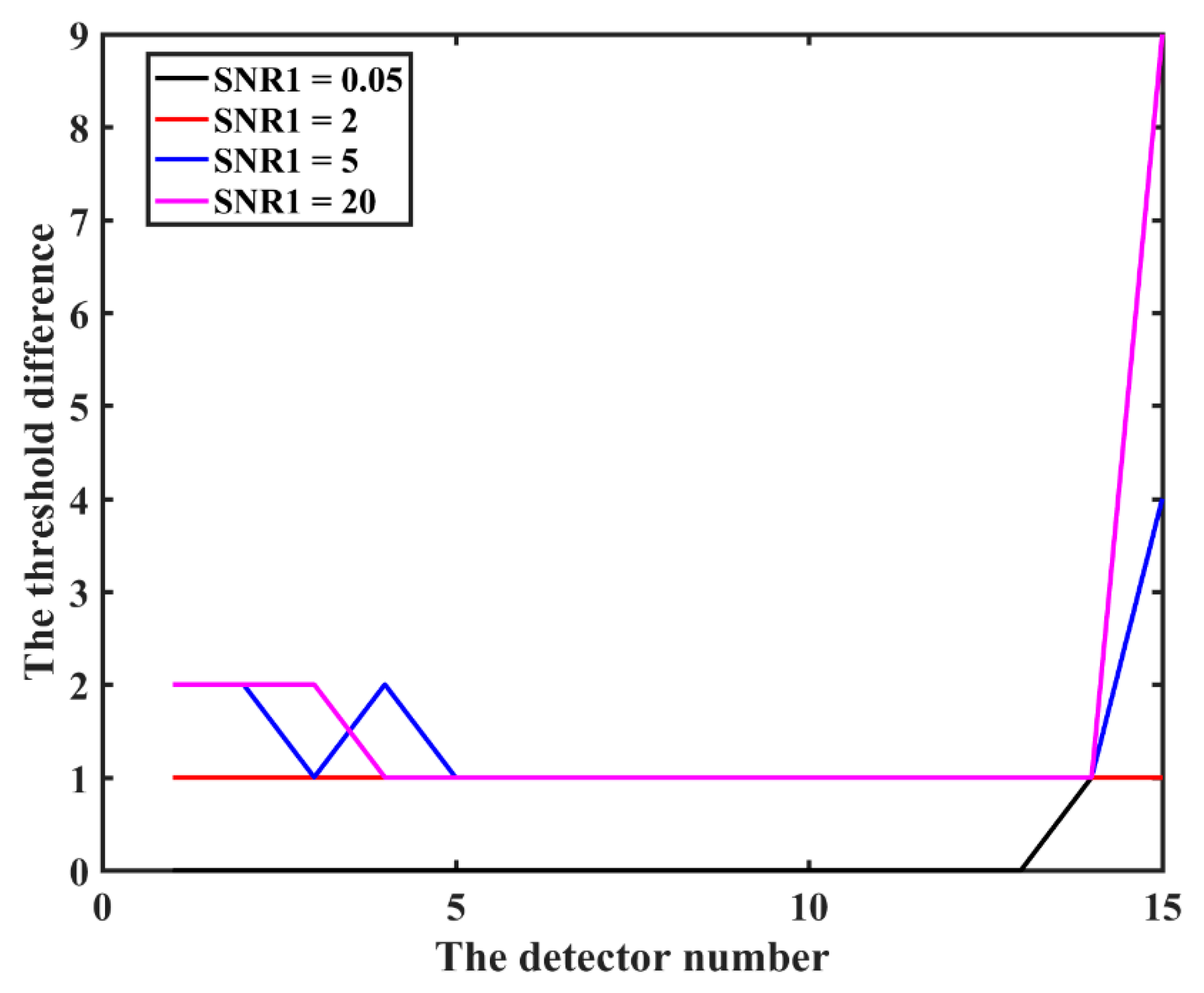
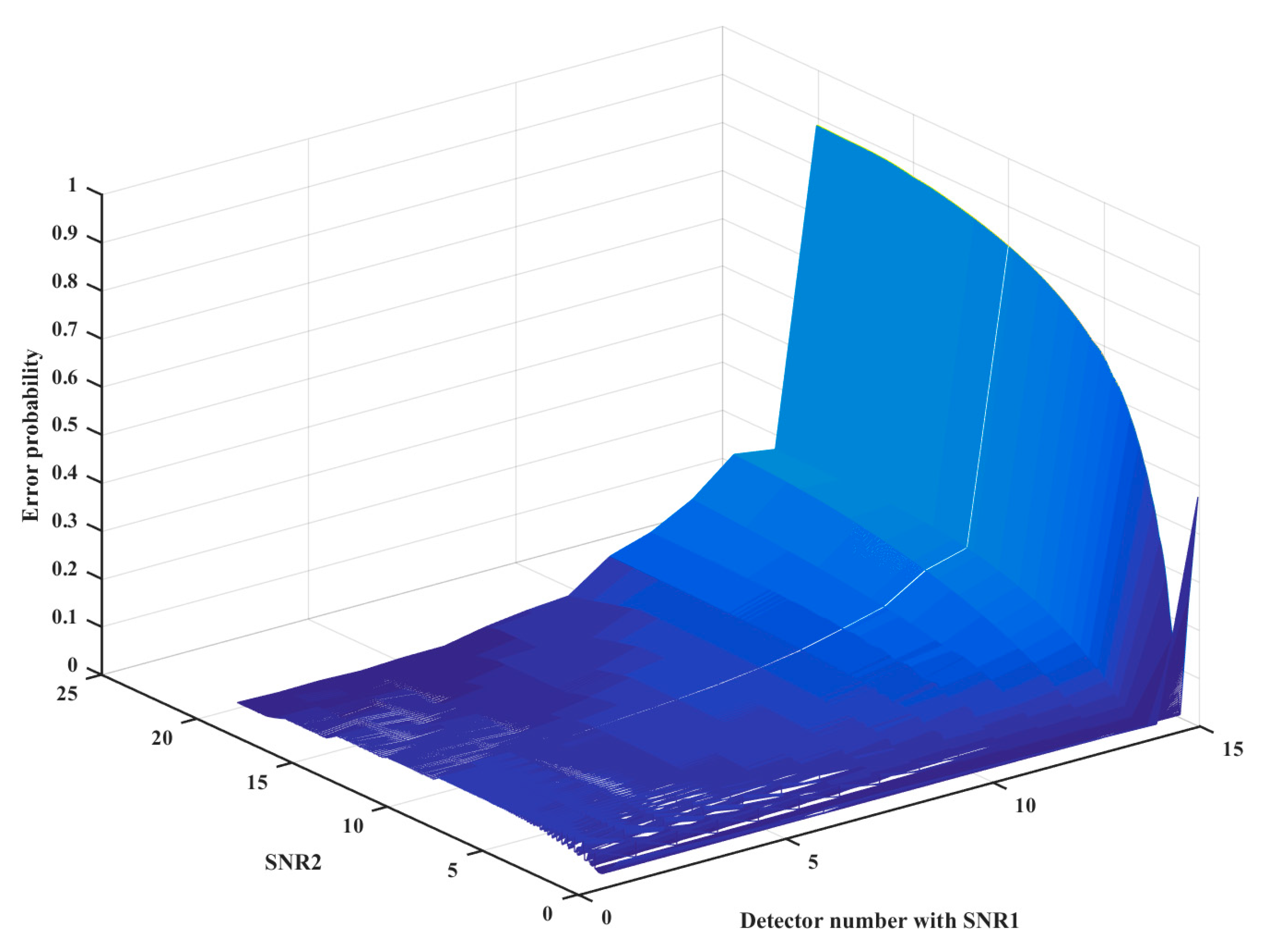
Figure 4 provides the influence of and on the threshold error for the same , where x denotes the number of the detector with and y denotes the threshold difference between the proposed scheme and the classical one in Figure 3.
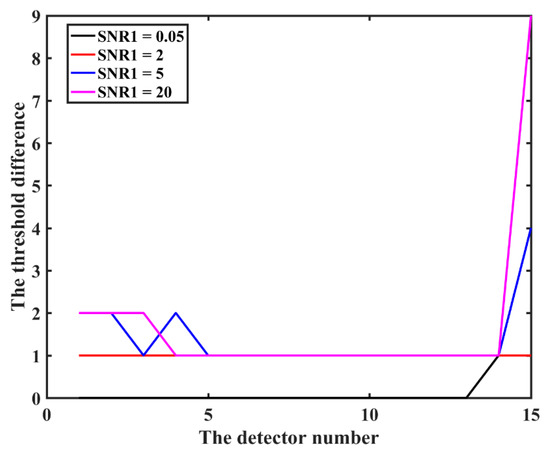
Figure 4.
The influence from and on the threshold error for the same .
In Figure 5, the error is proved with the variation of and , where z denotes the error probability difference between the proposed scheme with the classical scheme. Obviously, the error, z, increases with the error increase of the decision threshold, which corresponds to the theoretical analysis in Section 3.
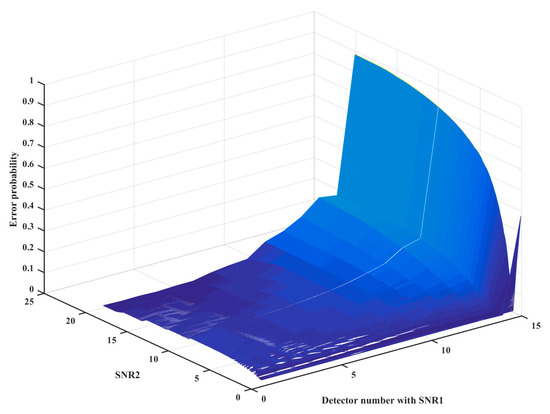
Figure 5.
The error with the variation of and .
4.2. Analysis and Discussion
As shown in Figure 2, the sensing threshold of the FC increases with the rise of the sensing point, which is the same as the classical scheme. Additionally, the sensing threshold of the proposed scheme is always higher than that of the classical scheme. The reason for this phenomenon is that when Poisson approximation is applied to the results of different independent Bernoulli variables, a high-order small quantity is always produced. The possible reason is that the rounding operation is needed for the evaluated decision threshold since the decision threshold is always an integer, which increases the decision threshold at the FC.
Note that the sensing threshold of the proposed scheme is closer to that of the classical scheme compared with the AND rule and the OR rule. This is because that when the probability of the Poisson approximation is less than 0.5, the λ produced by Poisson approximation will be very small, and the corresponding high-order small quantity will be even smaller. Therefore, the decision threshold obtained by this method will be much better than the threshold error produced by other methods.
As shown in Figure 3, the minimum error probability of the proposed scheme is basically identical to the classical scheme. This is because the threshold obtained by the proposed method is basically the same as that obtained by the classical scheme, and the error occurs only at a few jump points. As a result, if the proposed method is different from the classical scheme, the error probability at the bifurcation point will be greater than that calculated by the classical scheme. In addition, the trend of the three lines in Scenario I, II, III always increases gradually from left to right. This is because the performance of the CSS increases as the optimal N value decreases. However, the minimum total error probability under scenario IV decreases at first and then increases.
As shown in Figure 4, when x is small or large, the maximum deviation increases, because when is larger or smaller, the is farther away from 1, thus increasing the deviation. In comparison, when is too large, the deviation is larger. This is because , and the geometric mean is used in Poisson approximation, which leads to a greater error caused by a larger when also deviates from 1. Similarly, when increases, the maximum deviation will increase due to the rise of the average value. Consequently, if it is possible to screen the population within the detectors, one should try to ensure that the is close to 1, and at the same time, try to select an SNR with a small deviation to form the detector group.
5. Conclusions
The N-out-of-K rule-based CSS scheme is approximate to the Poisson distribution for the closed-form expression of the optimal sensing threshold at the FC under the heterogeneous cognitive radio networks in this paper, where the closed-form solutions of the false alarm probability and the detection probability are provided. The theoretical derivation is made for the approximation error, which states that the approximation error is within the tolerance of the system. The computational complexity to obtain the optimal sensing threshold at the FC has decreased from to by the efficient approximation of the N-out-of-K rule-based CSS scheme under the heterogeneous cognitive radio networks. The simulation experiments under the Rayleigh fading channel validate the conclusions drawn in this paper.
Author Contributions
Conceptualization, Y.T. and X.J.; methodology, Y.T.; validation, Y.T.; formal analysis, Y.T.; investigation, Y.T.; data curation, Y.T.; writing—original draft preparation, Y.T.; writing—review and editing, X.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author. The data are not publicly available due to the commercial purpose.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Federal Communications Commission. Spectrum Policy Task Force Report; FCC Document ET Docket No. 02-155; Federal Communications Commission: Washington, DC, USA, 2002.
- Yu, H.; Bin Zikria, Y. Cognitive radio networks for internet of things and wireless sensor networks. Sensors 2020, 20, 5288. [Google Scholar] [CrossRef]
- Ahmed, B.S.; Bures, M.; Frajtak, K.; Cerny, T. Aspects of quality in internet of things (IoT) solutions: A systematic mapping study. IEEE Access 2019, 7, 13758–13780. [Google Scholar] [CrossRef]
- Javed, F.; Afzal, M.K.; Sharif, M.; Kim, B.-S. Internet of things (IoT) operating systems support, networking technologies, applications, and challenges: A comparative review. IEEE Commun. Surv. Tutorials 2018, 20, 2062–2100. [Google Scholar] [CrossRef]
- Rawat, P.; Singh, K.D.; Bonnin, J.M. Cognitive Radio for M2M and Internet of Things: A survey. Comput. Commun. 2016, 94, 1–29. [Google Scholar] [CrossRef]
- Stevenson, C.R.; Chouinard, G.; Lei, Z.; Hu, W.; Shellhammer, S.J.; Caldwell, W. IEEE 802.22: The first cognitive radio wireless regional area network standard. IEEE Commun. Mag. 2009, 47, 130–138. [Google Scholar] [CrossRef]
- Xie, R.; Yu, F.R.; Ji, H.; Li, Y. Energy-efficient resource allocation for heterogeneous cognitive radio networks with femtocells. IEEE Trans. Wirel. Commun. 2012, 11, 3910–3920. [Google Scholar]
- Ghasemi, A.; Sousa, E.S. Spectrum sensing in cognitive radio networks: Requirements, challenges and design trade-offs. IEEE Commun. Mag. 2008, 46, 32–39. [Google Scholar] [CrossRef]
- Wang, X.; Ekin, S.; Serpedin, E. Joint spectrum sensing and resource allocation in multi-band-multi-user cognitive radio networks. IEEE Trans. Commun. 2018, 66, 3281–3293. [Google Scholar] [CrossRef]
- Ren, J.; Hu, J.; Zhang, D.; Guo, H.; Zhang, Y.; Shen, X. RF energy harvesting and transfer in cognitive radio sensor networks: Opportunities and challenges. IEEE Commun. Mag. 2018, 56, 104–110. [Google Scholar] [CrossRef]
- Chen, Y.; Xiong, Y.; Wang, Q.; Yin, X.; Li, B. Ensuring minimum spectrum requirement in matching-based spectrum allocation. IEEE Trans. Mob. Comput. 2018, 17, 2028–2040. [Google Scholar] [CrossRef]
- Leaves, P.; Moessner, K.; Tafazolli, R.; Grandblaise, D.; Bourse, D.; Tonjes, R.; Breveglieri, M. Dynamic spectrum allocation in composite reconfigurable wireless networks. IEEE Commun. Mag. 2004, 42, 72–81. [Google Scholar] [CrossRef]
- Etkin, R.; Parekh, A.; Tse, D. Spectrum sharing for unlicensed bands. In Proceedings of the First IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Dublin, Ireland, 17–20 April 2007. [Google Scholar]
- Ranjan, A.; Singh, B. Design and analysis of spectrum sensing in cognitive radio based on energy detection. In Proceedings of the International Conference on Signal and Information Processing, Vishnupuri, India, 6–8 October 2016; pp. 1–5. [Google Scholar]
- Ilyas, I.; Paul, S.; Rahman, A.; Kundu, R.K. Comparative evaluation of cyclostationary detection based cognitive spectrum sensing. In Proceedings of the Ubiquitous Computing, Electronics, and Mobile Communication Conference, New York, NY, USA, 20–22 October 2016; pp. 1–7. [Google Scholar]
- Zeng, Y.; Liang, Y.C. Spectrum-sensing algorithms for cognitive radio based on statistical covariances. IEEE Trans. Veh. Technol. 2009, 58, 1804–1815. [Google Scholar] [CrossRef]
- Ganesan, G.; Li, Y. Cooperative spectrum sensing in cognitive radio networks. In Proceedings of the IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, MD, USA, 8–11 November 2005. [Google Scholar]
- Digham, F.F.; Alouini, M.-S.; Simon, M.K. On the energy detection of unknown signals over fading channels. IEEE Trans. Commun. 2007, 55, 21–24. [Google Scholar] [CrossRef]
- Kozłowski, S. Implementation and verification of cyclostationary feature detector for DVB-T signals. IET Signal Process. 2016, 10, 162–167. [Google Scholar] [CrossRef]
- Jin, M.; Guo, Q.; Xi, J.; Li, Y.; Yu, Y.; Huang, D. Spectrum sensing using weighted covariance matrix in rayleigh fading channels. IEEE Trans. Veh. Technol. 2015, 64, 5137–5148. [Google Scholar] [CrossRef]
- Zhou, X.; Ma, J.; Li, G.Y.; Kwon, Y.H.; Soong, A.C. Probability-based combination for cooperative spectrum sensing. IEEE Trans. Commun. 2010, 58, 463–466. [Google Scholar] [CrossRef]
- Letaief, K.B.; Wei, Z. Cooperative spectrum sensing. In Cognitive Wireless Communication Networks; Springer: Berlin/Heidelberg, Germany, 1970. [Google Scholar]
- Li, Z.; Yu, F.R.; Huang, M.A. Distributed consensus-based cooperative spectrum-sensing scheme in cognitive radios. IEEE Trans. Veh. Technol. 2010, 59, 383–393. [Google Scholar]
- Banavathu, N.R.; Khan, M.Z.A. Optimization of N-out-of-K rule for heterogeneous cognitive radio networks. IEEE Signal Process. Lett. 2019, 26, 445–449. [Google Scholar] [CrossRef]
- Maleki, S.; Leus, G.; Chatzinotas, S.; Ottersten, B. To AND or to OR: On energy-efficient distributed spectrum sensing with combined censoring and sleeping. IEEE Trans. Wirel. Commun. 2015, 14, 4508–4521. [Google Scholar] [CrossRef]
- Umebayashi, K.; Lehtomaki, J.J.; Yazawa, T.; Suzuki, Y. Efficient decision fusion for cooperative spectrum sensing based on OR-rule. IEEE Trans. Wirel. Commun. 2012, 11, 2585–2595. [Google Scholar] [CrossRef]
- Nallagonda, S.; Bandari, S.K.; Roy, S.D. Cooperative spectrum sensing with censoring of cognitive radios in presence of log-normal shadowing under majority logic fusion. In Proceedings of the International Conference on Communications, Budapest, Hungary, 9–13 June 2013. [Google Scholar]
- Yang, G.; Wang, J.; Luo, J.; Wen, O.Y.; Li, H.; Li, Q.; Li, S. Cooperative spectrum sensing in heterogeneous cognitive radio networks based on normalized energy detection. IEEE Trans. Veh. Technol. 2016, 65, 1452–1463. [Google Scholar] [CrossRef]
- Mamidi, R.; Sundru, A. Throughput analysis in proposed cooperative spectrum sensing network with an improved energy detector scheme over rayleigh fading channel. AEU Int. J. Electron. Commun. 2017, 83, 416–426. [Google Scholar] [CrossRef]
- Al Hammadi, A.; Alhussein, O.; Sofotasios, P.C.; Muhaidat, S.; Al-Qutayri, M.; Al-Araji, S.; Liang, J. Unified analysis of cooperative spectrum sensing over composite and generalized fading channels. IEEE Trans. Veh. Technol. 2015, 65, 6949–6961. [Google Scholar] [CrossRef]
- Pandit, S.; Singh, G. Spectrum sensing in cognitive radio networks: Potential challenges and future perspective. In Spectrum Sharing in Cognitive Radio Networks; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Peh, E.C.Y.; Liang, Y.C.; Guan, Y.L. Optimization of cooperative sensing in cognitive radio networks: A sensing-throughput tradeoff view. IEEE Trans. Veh. Technol. 2009, 58, 5294–5299. [Google Scholar] [CrossRef]
- Zhang, D.; Chen, Z.; Ren, J.; Zhang, N.; Awad, M.K.; Zhou, H.; Shen, X.S. Energy harvesting-aided spectrum sensing and data transmission in heterogeneous cognitive radio sensor network. IEEE Trans. Veh. Technol. 2016, 66, 831–843. [Google Scholar] [CrossRef]
- Teerapabolarn, K. New non-uniform bounds on poisson approximation for dependent bernoulli trials. Bull. Malays. Math. Sci. Soc. 2015, 38, 231–248. [Google Scholar] [CrossRef]
- Liang, Y.C.; Zeng, Y.; Peh, E.C.; Hoang, A.T. Sensing-throughput tradeoff for cognitive radio networks. IEEE Trans. Wirel. Commun. 2008, 7, 1326–1337. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).