Enhanced Bit Repair IP Fast Reroute Mechanism for Rapid Network Recovery
Abstract
:1. Introduction
1.1. IP Fast Reroute Fundamentals
1.2. Link Versus Node Protection
2. Related Works
2.1. Loop-Free Alternates and Remote-LFA FRR
2.2. The Multicast Repair Mechanism (M-REP)
2.3. Problem Areas
2.4. Full Repair Coverage with Multiple Failures Support
2.5. Cost-Based Calculations
2.6. Per-Prefix Calculation
2.7. Research Goal (Research Aims and Objectives)
3. The B-REP Mechanism
4. The Proposal of the Enhanced B-REP Mechanism
The EB-REP State Diagrams
5. Evaluation of the Enhanced B-REP FRR Mechanism
6. Discussion of the Obtained Results
6.1. Speed Comparison of EB-REP and Existing FRR Mechanisms
6.1.1. Theoretical Comparison
6.1.2. Simulation Comparison
6.2. Testing in Real Networks
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ursini, E.L.; Santos, H.d.L.d.; Okano, M.T. Improving the Availability of Firewalls with a View to Increasing ICT Consumption Due Covid-19. In Proceedings of the 2020 11th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 4–7 November 2020; pp. 0647–0653. [Google Scholar] [CrossRef]
- Feldmann, A.; Gasser, O.; Lichtblau, F.; Pujol, E.; Poese, I.; Dietzel, C.; Wagner, D.; Wichtlhuber, M.; Tapiador, J.; Vallina-Rodriguez, N.; et al. The Lockdown Effect: Implications of the COVID-19 Pandemic on Internet Traffic. In Proceedings of the ACM Internet Measurement Conference; ACM: New York, NY, USA, 2020; pp. 1–18. [Google Scholar] [CrossRef]
- Abualhaj, M.M.; Hussein, A.H.; Kolhar, M.; AlHija, M.A. Survey and analysis of VoIP frame aggregation methods over A-MSDU IEEE 802.11n wireless networks. Comput. Mater. Contin. 2020, 66, 1283–1300. [Google Scholar] [CrossRef]
- Ahmadi, H.; Katzis, K.; Shakir, M.Z.; Avraneh, M.; Gatherer, A. Wireless Communication and the Pandemic: The Story So Far; IEEE ComSoc Technology News: New York, NY, USA, 2020. [Google Scholar]
- Kvist, F.; Urke, A.R.; Øvsthus, K. Energy efficient determinism in wsn through reverse packet elimination. Sensors 2020, 20, 2890. [Google Scholar] [CrossRef] [PubMed]
- Escobar, J.J.M.; Matamoros, O.M.; Reyes, I.L.; Tejeida-Padilla, R.; Hernández, L.C.; Durán, J.P.F.P. Energy-Efficient Industrial Internet of Things Software-Defined Network by Means of the Peano Fractal. Sensors 2020, 20, 2855. [Google Scholar] [CrossRef] [PubMed]
- Guerrero-Sanchez, A.E.; Rivas-Araiza, E.A.; Gonzalez-Cordoba, J.L.; Toledano-Ayala, M.; Takacs, A. Blockchain Mechanism and Symmetric Encryption in A Wireless Sensor Network. Sensors 2020, 20, 2798. [Google Scholar] [CrossRef] [PubMed]
- Fathallah, K.; Abid, M.A.; Hadj-Alouane, N.B. Enhancing Energy Saving in Smart Farming through Aggregation and Partition Aware IOT Routing Protocol. Sensors 2020, 20, 2760. [Google Scholar] [CrossRef]
- Karkazis, P.; Trakadas, P.; Zahariadis, T.; Hatziefremidis, A.; Leligou, H.C. RPL modeling in J-Sim platform. In Proceedings of the 2012 Ninth International Conference on Networked Sensing (INSS), Antwerp, Belgium, 11–14 June 2012. [Google Scholar] [CrossRef]
- Kim, M.; Park, Y.; Kotalwar, R. Robust and Agile System against Fault and Anomaly Traffic in Software Defined Networks. Appl. Sci. 2017, 7, 266. [Google Scholar] [CrossRef]
- Janech, J.; Kršák, E.; Toth, Š. The architecture of distributed database system in the VANET environment. Informatica 2014, 38, 205–211. [Google Scholar]
- Haseeb, K.; Almogren, A.; Din, I.U.; Islam, N.; Altameem, A. SASC: Secure and Authentication-Based Sensor Cloud Architecture for Intelligent Internet of Things. Sensors 2020, 20, 2468. [Google Scholar] [CrossRef]
- Lihakanga, R.; Ding, Y.; Medero, G.M.; Chapman, S.; Goussetis, G. A High-Resolution Open Source Platform for Building Envelope Thermal Performance Assessment Using a Wireless Sensor Network. Sensors 2020, 20, 1755. [Google Scholar] [CrossRef] [Green Version]
- Petija, R.; Michalko, M.; Jakab, F.; Fecilak, P. Convergence of Routing Protocols in Real and Simulated Environments. In ICETA 2018—16th IEEE International Conference on Emerging eLearning Technologies and Applications, Stary Smokovec, Slovakia, 15–16 November 2018; IEEE: New York, NY, USA, 2018; pp. 425–430. [Google Scholar] [CrossRef]
- Harada, Y.; Hui, W.; Fukushima, Y.; Yokohira, T. A reroute method to recover fast from network failure. In 2014 International Conference on Information and Communication Technology Convergence (ICTC), Busan, Korea, 22–24 October 2014; IEEE: New York, NY, USA, 2014; pp. 903–908. [Google Scholar] [CrossRef]
- Rak, J.; Pickavet, M.; Trivedi, K.S.; Lopez, J.A.; Koster, A.M.; Sterbenz, J.P.; Çetinkaya, E.K.; Gomes, T.; Gunkel, M.; Walkowiak, K.; et al. Future research directions in design of reliable communication systems. Telecommun. Syst. 2015, 60, 423–450. [Google Scholar] [CrossRef] [Green Version]
- Csikor, L.; Rétvári, G. On providing fast protection with remote loop-free alternates. Telecommun. Syst. 2015, 60, 485–502. [Google Scholar] [CrossRef]
- Misra, S.; Goswami, S. Reliability and Fault-Tolerant and Delay-Tolerant Routing. In Network Routing; John Wiley & Sons, Ltd.: Chichester, UK, 2017; pp. 377–410. [Google Scholar]
- Peñaranda, R.; Gómez, M.E.; López, P.; Gran, E.G.; Skeie, T. A fault-tolerant routing strategy for k-ary n-direct s-indirect topologies based on intermediate nodes. Concurr. Comput. Pract. Exp. 2017, 29, e4065. [Google Scholar] [CrossRef]
- Zhou, A.; Wang, S.; Hsu, C.-H.; Kim, M.H.; Wong, K. Network failure-aware redundant virtual machine placement in a cloud data center. Concurr. Comput. Pract. Exp. 2017, 29, e4290. [Google Scholar] [CrossRef]
- Robertson, G.; Roy, N.; Penumarthi, P.K.; Nelakuditi, S.; O’Kane, J.M. Loop-Free Convergence with Unordered Updates. IEEE Trans. Netw. Serv. Manag. 2017, 14, 373–385. [Google Scholar] [CrossRef]
- Malik, S.U.; Srinivasan, S.K.; Khan, S.U. Convergence time analysis of open shortest path first routing protocol in internet scale networks. Electron. Lett. 2012, 48, 1188. [Google Scholar] [CrossRef]
- Pal, V.K.; Ramteke, S.M. A framework for fast IP rerouting. In International Conference on Information Communication and Embedded Systems (ICICES2014), Chennai, India, 27–28 February 2014; IEEE: New York, NY, USA, 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Zhani, M.F.; Boutaba, R. Survivability and Fault Tolerance in the Cloud. In Cloud Services, Networking, and Management; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2015; pp. 295–308. [Google Scholar]
- Sterbenz, J.P.; Hutchison, D.; Çetinkaya, E.K.; Jabbar, A.; Rohrer, J.P.; Schöller, M.; Smith, P. Redundancy, diversity, and connectivity to achieve multilevel network resilience, survivability, and disruption tolerance invited paper. Telecommun. Syst. 2014, 56, 17–31. [Google Scholar] [CrossRef]
- Wozniak, J. Mobility management solutions for current IP and future networks. Telecommun. Syst. 2016, 61, 257–275. [Google Scholar] [CrossRef] [Green Version]
- Cheng, Z.; Zhang, X.; Li, Y.; Yu, S.; Lin, R.; He, L. Congestion-Aware Local Reroute for Fast Failure Recovery in Software-Defined Networks. J. Opt. Commun. Netw. 2017, 9, 934. [Google Scholar] [CrossRef]
- Antonakopoulos, S.; Bejerano, Y.; Koppol, P. A simple IP fast reroute scheme for full coverage. In 2012 IEEE 13th International Conference on High Performance Switching and Routing, Belgrade, Serbia, 24–27 June 2012; IEEE: New York, NY, USA, 2012; pp. 15–22. [Google Scholar] [CrossRef]
- Csikor, L.; Retvari, G. IP fast reroute with remote Loop-Free Alternates: The unit link cost case. In 2012 IV International Congress on Ultra Modern Telecommunications and Control Systems, St. Petersburg, Russia, 3–5 October 2012; IEEE: New York, NY, USA, 2012; pp. 663–669. [Google Scholar] [CrossRef] [Green Version]
- Lemeshko, O.; Yeremenko, O.; Hailan, A.M. Two-level method of fast ReRouting in software-defined networks. In 2017 4th International Scientific-Practical Conference Problems of Infocommunications Science and Technology, Kharkov, Ukraine, 10–13 October 2017; IEEE: New York, NY, USA, 2018; pp. 376–379. [Google Scholar] [CrossRef]
- Chiesa, M.; Sedar, R.; Antichi, G.; Borokhovich, M.; Kamisiński, A.; Nikolaidis, G.; Schmid, S. Fast ReRoute on Programmable Switches. IEEE/ACM Trans. Netw. 2021. [Google Scholar] [CrossRef]
- Numata, N.; Ishigai, M.; Tarutani, Y.; Fukushima, Y.; Yokohira, T. An IP Fast Reroute Method against Multiple Node Failures. In International Conference on ICT Convergence, Jeju, Korea, 21–23 October 2020; IEEE: New York, NY, USA, 2020; pp. 714–719. [Google Scholar] [CrossRef]
- Tavernier, W.; Papadimitriou, D.; Colle, D.; Pickavet, M.; Demeester, P. Self-configuring loop-free alternates with high link failure coverage. Telecommun. Syst. 2014, 56, 85–101. [Google Scholar] [CrossRef]
- Papán, J.; Segeč, P.; Moravčík, M.; Kontšek, M.; Mikuš, L.U.; Uramová, J. Overview of IP Fast Reroute Solutions. In ICETA 2018—16th IEEE International Conference on Emerging eLearning Technologies and Applications, Proceedings, Stary Smokovec, Slovakia, 15–16 November 2018; IEEE: New York, NY, USA, 2018; pp. 417–424. [Google Scholar] [CrossRef]
- Elhourani, T.; Gopalan, A.; Ramasubramanian, S.; Elhourani, T.; Gopalan, A.; Ramasubramanian, S. IP Fast Rerouting for Multi-Link Failures. IEEE/ACM Trans. Netw. 2016, 24, 3014–3025. [Google Scholar] [CrossRef]
- Gopalan, A.; Ramasubramanian, S. IP Fast Rerouting and Disjoint Multipath Routing with Three Edge-Independent Spanning Trees. IEEE/ACM Trans. Netw. 2016, 24, 1336–1349. [Google Scholar] [CrossRef]
- Braun, W.; Menth, M. Loop-Free Alternates with Loop Detection for Fast Reroute in Software-Defined Carrier and Data Center Networks. J. Netw. Syst. Manag. 2016, 24, 470–490. [Google Scholar] [CrossRef]
- Elhourani, T.; Gopalan, A.; Ramasubramanian, S. IP fast rerouting for multi-link failures. In IEEE Infocom 2014—IEEE Conference on Computer Communications; IEEE: New York, NY, USA, 2014; Volume 24, pp. 2148–2156. [Google Scholar] [CrossRef]
- Papan, J.; Segec, P.; Yeremenko, O.; Bridova, I.; Hodon, M. A New Bit Repair Fast Reroute Mechanism for Smart Sensors IoT Network Infrastructure. Sensors 2020, 20, 5230. [Google Scholar] [CrossRef]
- Kim, M.; Chae, K. DMP: Detouring Using Multiple Paths against Jamming Attack for Ubiquitous Networking System. Sensors 2010, 10, 3626–3640. [Google Scholar] [CrossRef]
- Teng, R.; Sakano, T.; Suzuki, Y. Instantaneous Networking Service Availability for Disaster Recovery. Appl. Sci. 2020, 10, 9030. [Google Scholar] [CrossRef]
- Malik, A.; de Fréin, R.; Aziz, B. Rapid Restoration Techniques for Software-Defined Networks. Appl. Sci. 2020, 10, 3411. [Google Scholar] [CrossRef]
- Csikor, L.; Tapolcai, J.; Rétvári, G. Optimizing IGP link costs for improving IP-level resilience with Loop-Free Alternates. Comput. Commun. 2013, 36, 645–655. [Google Scholar] [CrossRef]
- Sarkar, P.; Hegde, S.; Bowers, C.; Gredler, H.; Litkowski, S. Remote-LFA Node Protection and Manageability. Request for Comments: 8102. Internet Engineering Task Force (IETF), 2017. Available online: https://tools.ietf.org/html/rfc8102 (accessed on 10 January 2021).
- Filsfils, C.; Francois, P.; Shand, M.; Decraene, B.; Uttaro, J.; Leymann, N.; Horneffer, M. Loop-Free Alternate (LFA) Applicability in Service Provider (SP) Networks. Request for Comments: 6571. Internet Engineering Task Force (IETF), 2012. Available online: https://tools.ietf.org/html/rfc6571 (accessed on 10 January 2021).
- Atlas, A.; Zinin, A. Basic Specification for IP Fast Reroute: Loop-Free Alternates. Request for Comments: 5286. Internet Engineering Task Force (IETF), 2008. Available online: https://tools.ietf.org/html/rfc5286 (accessed on 10 January 2021).
- Bryant, S.; Filsfils, C.; Previdi, S.; Shand, M.; So, N. Remote Loop-Free Alternate (LFA) Fast Reroute (FRR). Request for Comments: 7490. Internet Engineering Task Force (IETF), 2015. Available online: https://tools.ietf.org/html/rfc7490 (accessed on 10 January 2021).
- El-Serafy, M.A.; Elsayed, A.M.; Aly, M.H.; El-Badawy, E.-S.A.; Ghaleb, I.A. Multiple Routing Configurations for Datacenter Disaster Recovery Applicability and Challenges. In 2014 International Conference on Computer and Communication Engineering, Kuala Lumpur, Malaysia, 23–25 September 2014; IEEE: New York, NY, USA, 2014; pp. 146–149. [Google Scholar] [CrossRef]
- Limin, L.Z.; Zheqing, Z.L.; Hui, H.W.; Peiyu, P.L.; Xi, C.C. A new backup topology design method for IP fast recovery. In 2016 2nd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 14–17 October 2016; IEEE: New York, NY, USA, 2016; pp. 1992–1997. [Google Scholar] [CrossRef]
- Lemeshko, O.; Kinan, A.; Wahhab, M.A.j.A. Multicast fast re-route schemes for multiflow case. In The Experience of Designing and Application of CAD Systems in Microelectronics, Lviv, Ukraine, 24–27 February 2015; IEEE: New York, NY, USA, 2015; pp. 422–424. [Google Scholar] [CrossRef]
- Aman, A.H.M.; Hashim, A.-H.A.; Ramli, H.A.M. Mathematical Evaluation of Context Transfer and Multicast Fast Reroute in Multicast Enabled Network Mobility Management. Int. J. Control. Autom. 2017, 10, 207–216. [Google Scholar] [CrossRef]
- Envedi, G.; Csaszar, A.; Atlas, A.; Bowers, C.; Gopalan, A. An Algorithm for Computing IP/LDP Fast Reroute Using Maximally Redundant Trees (MRT-FRR). Request for Comments: 7811. Internet Engineering Task Force (IETF), 2016. Available online: https://tools.ietf.org/html/rfc7811 (accessed on 10 January 2021).
- Menth, M.; Braun, W. Performance comparison of not-via addresses and maximally redundant trees (MRTs). In 2013 IFIP/IEEE International Symposium on Integrated Network Management (IM 2013), Ghent, Belgium, 27–31 May 2013; IEEE: New York, NY, USA, 2013; pp. 218–225. [Google Scholar]
- Kuang, K.; Wang, S.; Wang, X. Discussion on the combination of Loop-Free Alternates and Maximally Redundant Trees for IP networks Fast Reroute. In 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; IEEE: New York, NY, USA, 2014; pp. 1131–1136. [Google Scholar] [CrossRef]
- Atlas, A.; Bowers, C.; Enyedi, G. An Architecture for IP/LDP Fast Reroute Using Maximally Redundant Trees (MRT-FRR); Request for Comments: 7812; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2016. [Google Scholar]
- François, P.; Filsfils, C.; Bashandy, A.; Decraene, B.; Litkowski, S. Topology Independent Fast Reroute Using Segment Routing. Network Working Group, Internet-Draft, 2020. Available online: https://tools.ietf.org/html/draft-ietf-rtgwg-segment-routing-ti-lfa-06 (accessed on 10 January 2021).
- Papan, J.; Segec, P.; Paluch, P.; Uramova, J.; Moravcik, M. The new Multicast Repair (M-REP) IP fast reroute mechanism. Concurr. Comput. 2018, 32. [Google Scholar] [CrossRef]
- Papan, J.; Segec, P.; Yeremenko, O.; Bridova, I.; Hodon, M. Enhanced Multicast Repair Fast Reroute Mechanism for Smart Sensors IoT and Network Infrastructure. Sensors 2020, 20, 3428. [Google Scholar] [CrossRef] [PubMed]
- Menth, M.; Hartmann, M.; Martin, R.; Čičić, T.; Kvalbein, A. Loop-free alternates and not-via addresses: A proper combination for IP fast reroute? Comput. Netw. 2010, 54, 1300–1315. [Google Scholar] [CrossRef]
- Chiesa, M.; Kamisínski, A.K.; Rak, J.; Rétvári, G.; Schmid, S. A Survey of Fast Recovery Mechanisms in the Data Plane. TechRxiv 2020. [Google Scholar] [CrossRef]
- Shand, M.; Bryant, S. IP Fast Reroute Framework. Request for Comments: 5714. Internet Engineering Task Force (IETF), 2010. Available online: http://www.rfc-editor.org/rfc/rfc5714.txt (accessed on 10 January 2021).
- Gjoka, M.; Ram, V.; Yang, X. Evaluation of IP Fast Reroute Proposals. In 2007 2nd International Conference on Communication Systems Software and Middleware; IEEE: New York, NY, USA, 2007; pp. 1–8. [Google Scholar] [CrossRef]
- Lor, S.S.; Rio, M. Enhancing Repair Coverage of Loop-Free Alternates; University College London: London, UK, 2010. [Google Scholar]
- Bhor, M.; Karia, D. Network recovery using IP fast rerouting for multi link failures. In Proceedings of the 2017 International Conference on Intelligent Computing and Control, I2C2, Coimbatore, India, 23–24 June 2018; IEEE: New York, NY, USA, 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Robertson, G.; Nelakuditi, S. Handling multiple failures in IP networks through localized on-demand link state routing. IEEE Trans. Netw. Serv. Manag. 2012, 9, 293–305. [Google Scholar] [CrossRef]
- Imahama, D.; Fukushima, Y.; Yokohira, T. A reroute method using multiple routing configurations for fast IP network recovery. In 2013 19th Asia-Pacific Conference on Communications, APCC, Denpasar, Indonesia, 29–31 August 2013; IEEE: New York, NY, USA, 2013; pp. 433–438. [Google Scholar] [CrossRef]
- Sobrinho, J.L. Algebra and algorithms for QoS path computation and hop-by-hop routing in the Internet. IEEE/ACM Trans. Netw. 2002, 10, 541–550. [Google Scholar] [CrossRef]
- Sobrinho, J.a.L. Network Routing with Path Vector Protocols: Theory and Applications. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications—SIGCOMM ’03; IEEE: New York, NY, USA, 2003; pp. 49–60. [Google Scholar] [CrossRef]
- Gouda, M.G.; Schneider, M. Maximizable routing metrics. IEEE/ACM Trans. Netw. 2003, 11, 663–675. [Google Scholar] [CrossRef]
- Litkowski, S.; Decraene, B.; Filsfils, C.; Raza, K.; Horneffer, M.; Sarkar, P. Operational Management of Loop-Free Alternates. Request for Comments: 7916. Internet Engineering Task Force (IETF), 2016. Available online: https://tools.ietf.org/html/rfc7916 (accessed on 10 January 2021).
- Giorgetti, A.; Sgambelluri, A.; Paolucci, F.; Sambo, N.; Castoldi, P.; Cugini, F. Bit Index Explicit Replication (BIER) multicasting in transport networks. In 2017 21st International Conference on Optical Network Design and Modeling, Budapest, Hungary, 15–18 May 2017; IEEE: New York, NY, USA, 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Wijnands, I.J.; Rosen, E.; Dolganow, A.; Przygienda, T.; Aldrin, S. Multicast Using Bit Index Explicit Replication (BIER). Request for Comments: 8279. Internet Engineering Task Force (IETF), 2017. Available online: https://tools.ietf.org/html/rfc8279 (accessed on 10 January 2021).
- Eckert, T.; Cauchie, G.; Menth, M. Traffic Engineering for Bit Index Explicit Replication (BIER-TE). Network Working Group, Internet-Draft, 2021. Available online: https://tools.ietf.org/html/draft-ietf-bier-te-arch-09 (accessed on 9 January 2021).
- Merling, D.; Lindner, S.; Menth, M. P4-based implementation of BIER and BIER-FRR for scalable and resilient multicast. J. Netw. Comput. Appl. 2020, 102764. [Google Scholar] [CrossRef]
- Papán, J.; Segeč, P.; Dobrota, J.; Koncz, L.; Kubala, F.; Kontšek, M.; Yeremenko, O. Fast ReRoute error detection-implementation of BFD mechanism. In ICETA 2019—17th IEEE International Conference on Emerging eLearning Technologies and Applications, Starý Smokovec, Slovakia, 21–22 November 2019; IEEE: New York, NY, USA, 2019; pp. 593–599. [Google Scholar] [CrossRef]













| B-REP | EM-REP | MRC | MRT | Not-Via Addresses | LFA | R-LFA | D-LFA | TI-LFA | |
|---|---|---|---|---|---|---|---|---|---|
| 100% Repair Coverage | Yes | Yes | Yes | Yes | Yes | No | No | Yes | Yes |
| Custom Alternative Path | Yes | No | Yes | No | No | No | No | No | Yes |
| Precomputing | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Packet Modification | Yes | Yes | Yes | Yes | Yes | No | Yes | Yes | Yes |
| Link-State dependency | Yes | No | Yes | Yes | Yes | No | Yes | Yes | Yes |
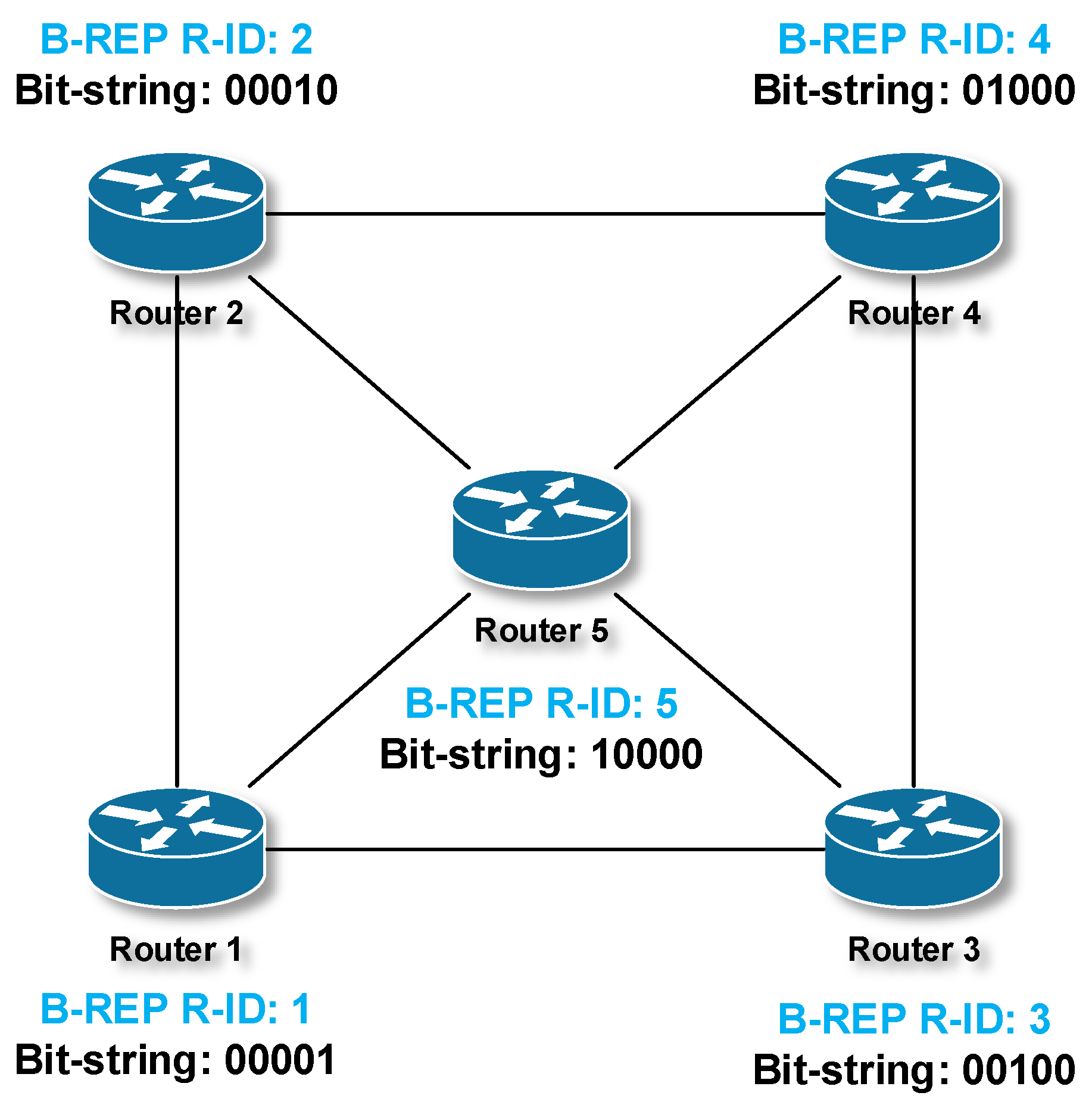
| Router | Router ID (OSPF) | B-REP R-ID | Bit-String Position (B-REP) |
|---|---|---|---|
| Router 1 | 1.1.1.1 | 1 | …00001 (LSB) |
| Router 2 | 2.2.2.2 | 2 | …00010 |
| Router 3 | 3.3.3.3 | 3 | …00100 |
| Router 4 | 4.4.4.4 | 4 | …01000 |
| Router 5 | 5.5.5.5 | 5 | …10000 |
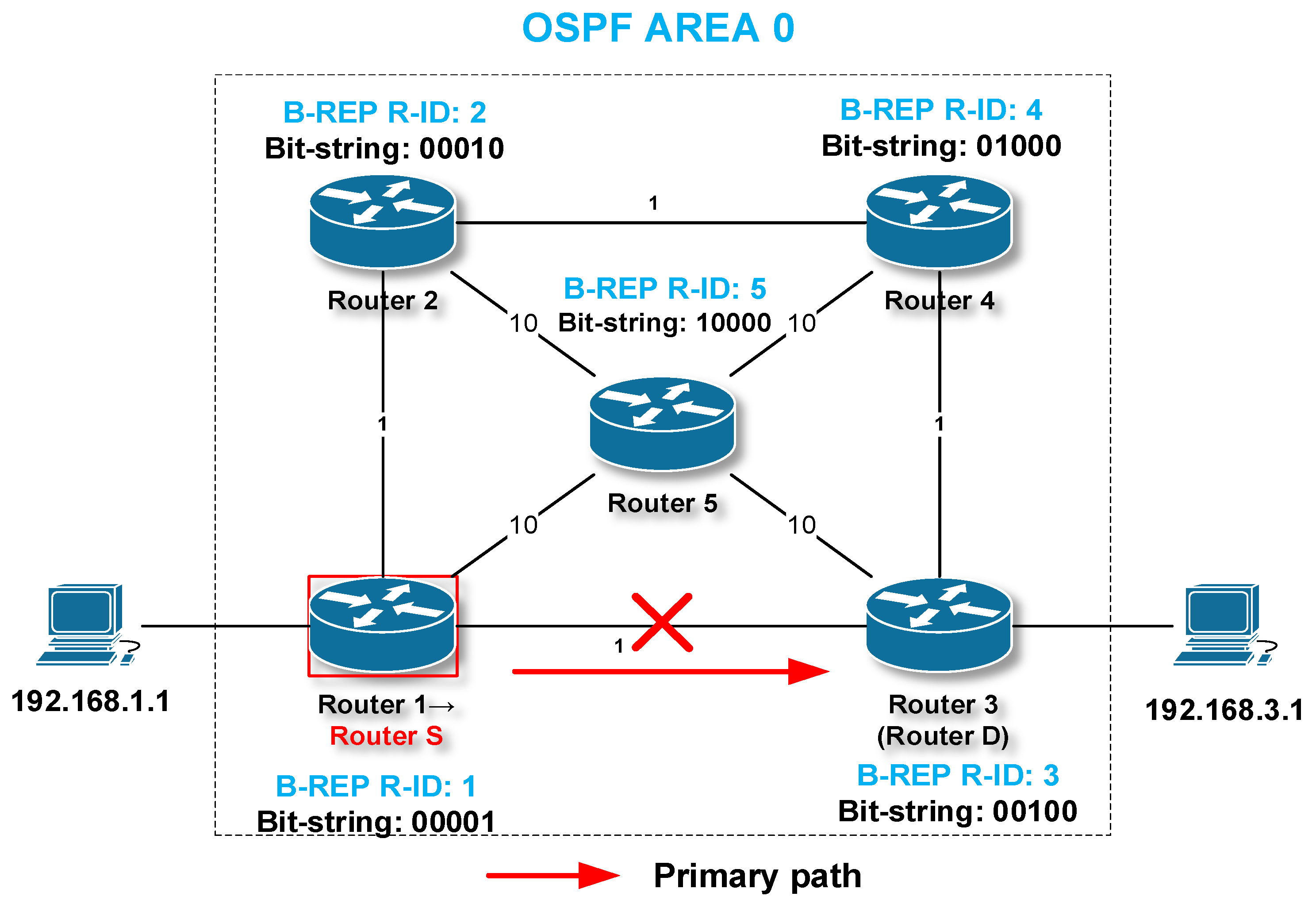
| Destination IP | Protected Interface | Destination B-REP R-ID (OSPF Router ID) | Bit-String Value |
|---|---|---|---|
| 192.168.2.1 | Interface R1–R3 | 3 (3.3.3.3) | …01110 (LSB) |
| 192.168.4.1 | Interface R1–R3 | 4 (4.4.4.4) | …01010 (LSB) |
| … | … | … |
| LS R-ID | EB-REP ID | Router Bit-String Position | |
|---|---|---|---|
| R1 | 1.1.1.1 | 1 | 0000 0001 |
| R2 | 2.2.2.2 | 2 | 0000 0010 |
| R3 | 3.3.3.3 | 3 | 0000 0100 |
| R4 | 4.4.4.4 | 4 | 0000 1000 |
| R5 | 5.5.5.5 | 5 | 0001 0000 |
| R6 | 6.6.6.6 | 6 | 0010 0000 |
| R7 | 7.7.7.7 | 7 | 0100 0000 |
| R8 | 8.8.8.8 | 8 | 1000 0000 |
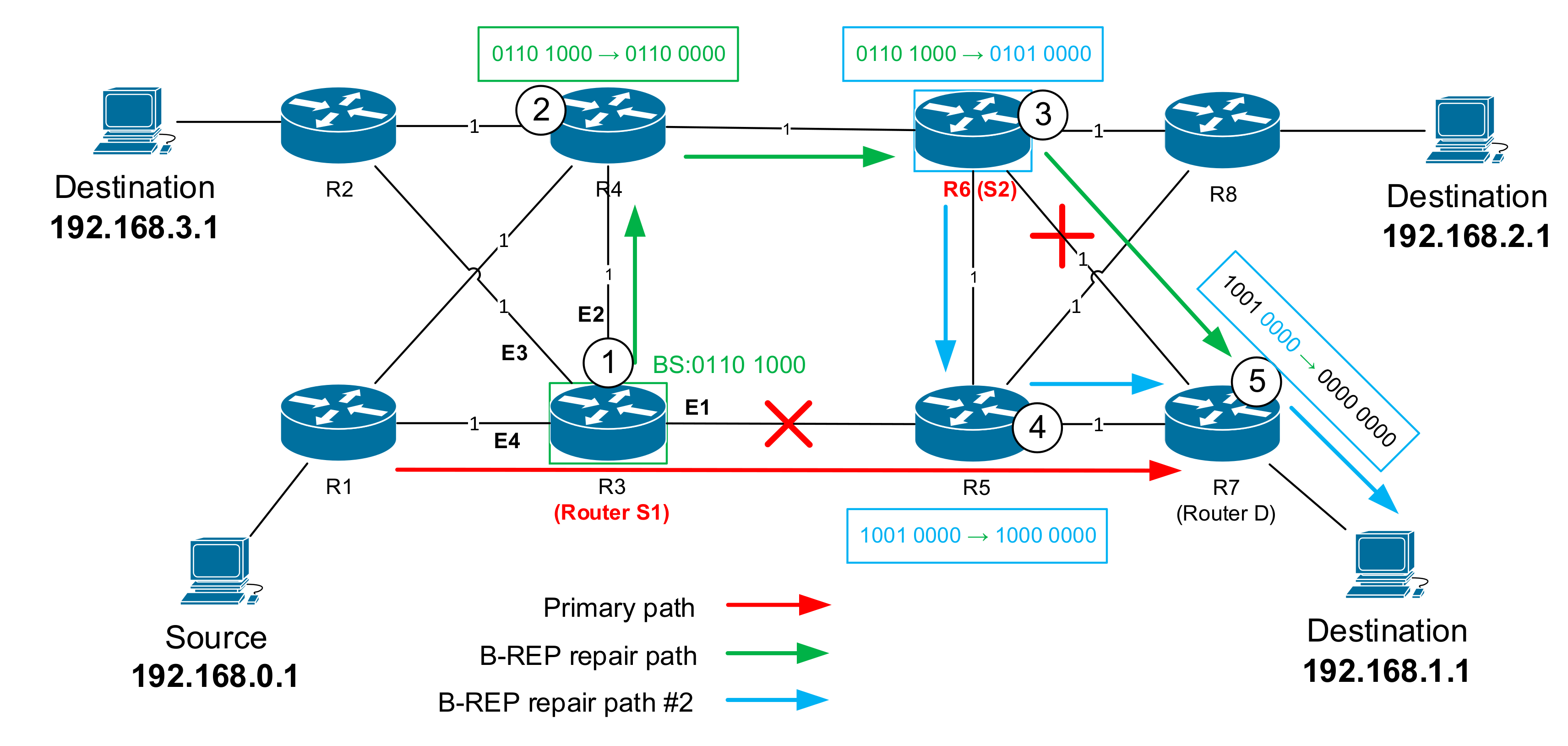
| Output Interface | Prefix | Path Bit-String Value |
|---|---|---|
| E1 | 192.168.1.0/24 | … 0110 1000 (LSB) |
| E2 | 192.168.2.0/24 | … 1001 0100 (LSB) |
| E3 | 192.168.3.0/24 | … 0000 1010 (LSB) |
| E4 | 192.168.0.0/24 | … 0000 1001 (LSB) |
| … | … |
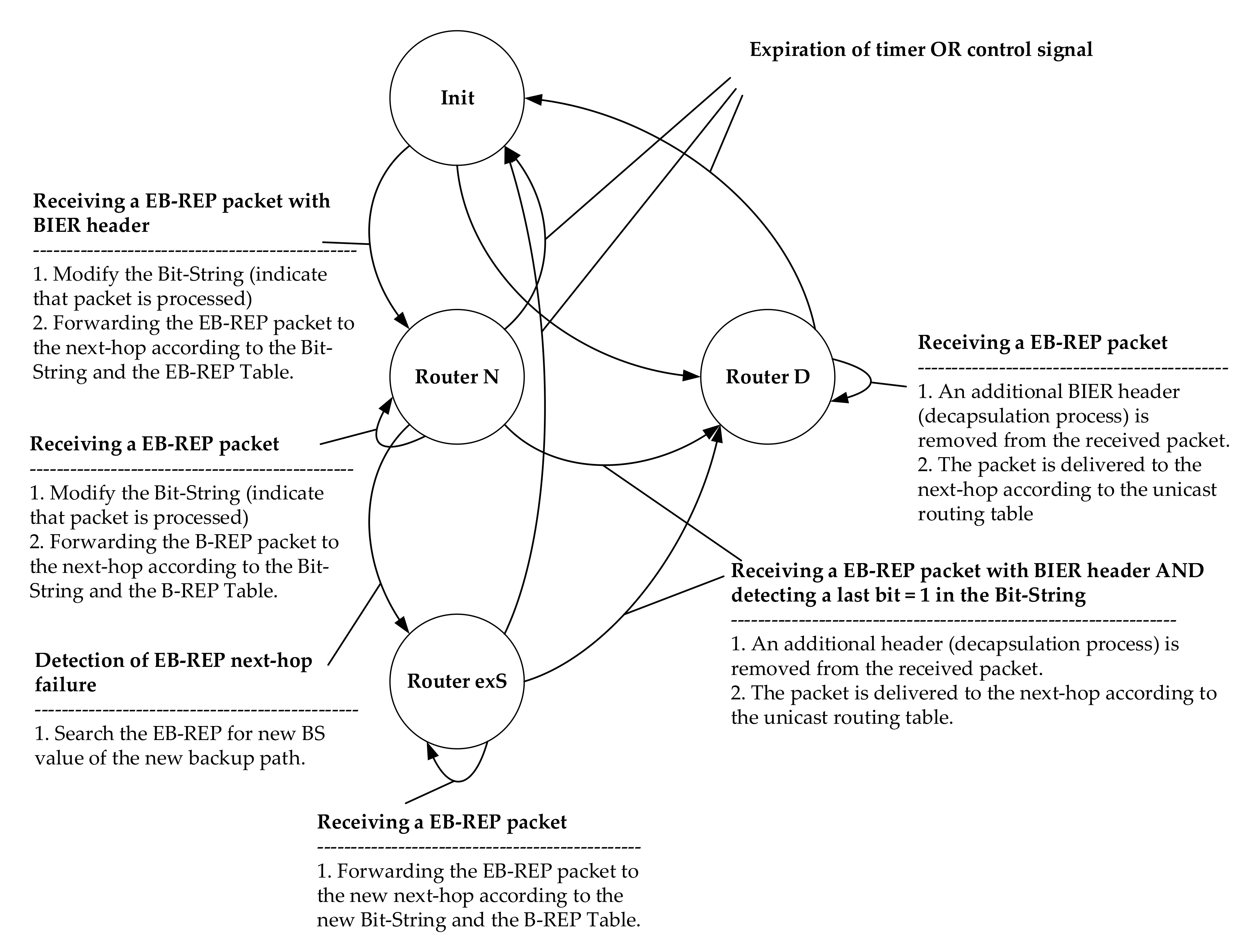
| State: | Any condition |
| Event: | Startup |
| New state: | Init |
| Action: | Initialization of the EB-REP process on the router. Initialization of the EB-REP table and designation of EB-REP R-IDs and corresponding Bit-String position values. Initialization of the EB-REP Backup Table. Reads the list of protected interfaces and for each network IP address, precalculates an alternative path. Assigns the Bit-String values. The mechanism is initialized for the first time and then after each routing convergence. After these activities, the EB-REP stays in the monitoring mode. |
| State: | Init |
| Event: | Detection of protected interface failure. |
| New state: | Router S |
| Action: | If the router detects a connectivity failure on the protected output interface, it becomes router S. Router S searches the EB-REP backup table for the affected destination IP address and the identity of the failed protected interface. Router S reads a given Bit-String value of the backup path. |
| State: | Router S |
| Event: | Process received affected packets OR convergence not finished OR control signal not received OR timer did not expire |
| New state: | - |
| Action: | Encapsulate the affected packet with a new EB-REP header (BIER) and the Bit-String value of the backup path. Send an encapsulated packet through an active interface to the precalculated next-hop EB-REP node. |
| State: | Router S |
| Event: | Recovery of connection on protected interface OR control signal received OR timer expired. |
| New state: | Init |
| Action: | The S router stops the EB-REP encapsulation of the protected flow and changes to the Init state. In the Init state, it must reinitialize the EB-REP table and EB-REP backup table. |
| State: | Init |
| Event: | Receiving an EB-REP packet with a BIER header. |
| New state: | Router N |
| Action: | A router has received a packet with a BIER header. Checks the Bit-String value. If BS has more bits set, the router becomes the N router. |
| State: | Router N |
| Event: | Process received EB-REP packets. |
| New state: | - |
| Action: | Modify the Bit-String (indicate that packet is processed). Forward the EB-REP packet to the next-hop according to the Bit-String value. |
| State: | Init |
| Event: | Receiving an EB-REP packet with a BIER header with the last bit set |
| New state: | Router D |
| Action: | A router has received an EB-REP packet. Checks the Bit-String value and detects that values have only the last bit set, and at the same time, that the bit corresponds to itself. The router becomes the D router. |
| State: | Router D |
| Event: | Process received EB-REP packets. |
| New state: | - |
| Action: | Removes a BIER header (which means that packet is decapsulated and returned to its original state). Routes the original packet via the unicast routing table. |
| State: | Router N, Router D |
| Event: | The timer expires OR control signal received |
| New state: | Init |
| Action: | When EB-REP process is finished, returns to the Init state. In the Init state, it must reinitialize the EB-REP table and EB-REP backup table. |
| State: | Router N |
| Event: | Detection of EB-REP next-hop failure |
| New state: | Router exS |
| Action: | Looks for a new BS value in EB-REP BT. Replaces the BS value with the new one. Sends an encapsulated packet through an active interface to the precalculated next-hop EB-REP node. |
| State: | Router exS |
| Event: | Process received EB-REP packets. |
| New state: | - |
| Action: | Forwards the EB-REP packet to the new next-hop according to the new Bit-String and the B-REP Backup Table. |
| State: | Router exS |
| Event: | Recovery of connection on protected interface OR convergence finished OR control signal received OR timer expired. |
| New state: | Init |
| Action: | The exS router stops the EB-REP encapsulation of the protected flow and changes to the Init state. In the Init state, it must reinitialize the EB-REP table and EB-REP backup table. |
| State: | Router exS |
| Event: | Receiving an EB-REP packet with BIER header AND detecting a last bit = 1 in the Bit-String. |
| New state: | D |
| Action: | A BIER header (decapsulation process) is removed from the received packet. The packet is delivered to the next-hop according to the router D unicast routing table. |
| State: | Router N |
| Event: | Receiving an EB-REP packet with BIER header AND detecting a last bit = 1 in the Bit-String. |
| New state: | D |
| Action: | A BIER header (decapsulation process) is removed from the received packet. The packet is delivered to the next-hop according to the router D unicast routing table. |
| Time | Description of Action |
|---|---|
| <50 | The time necessary for the OSPF convergence and stabilization of network routing processes. |
| 64 | Source host begins generating the flow |
| 70 | R1–R6 link failure |
| 80 | R10 failure |
| 90 | Restoration of failed elements |
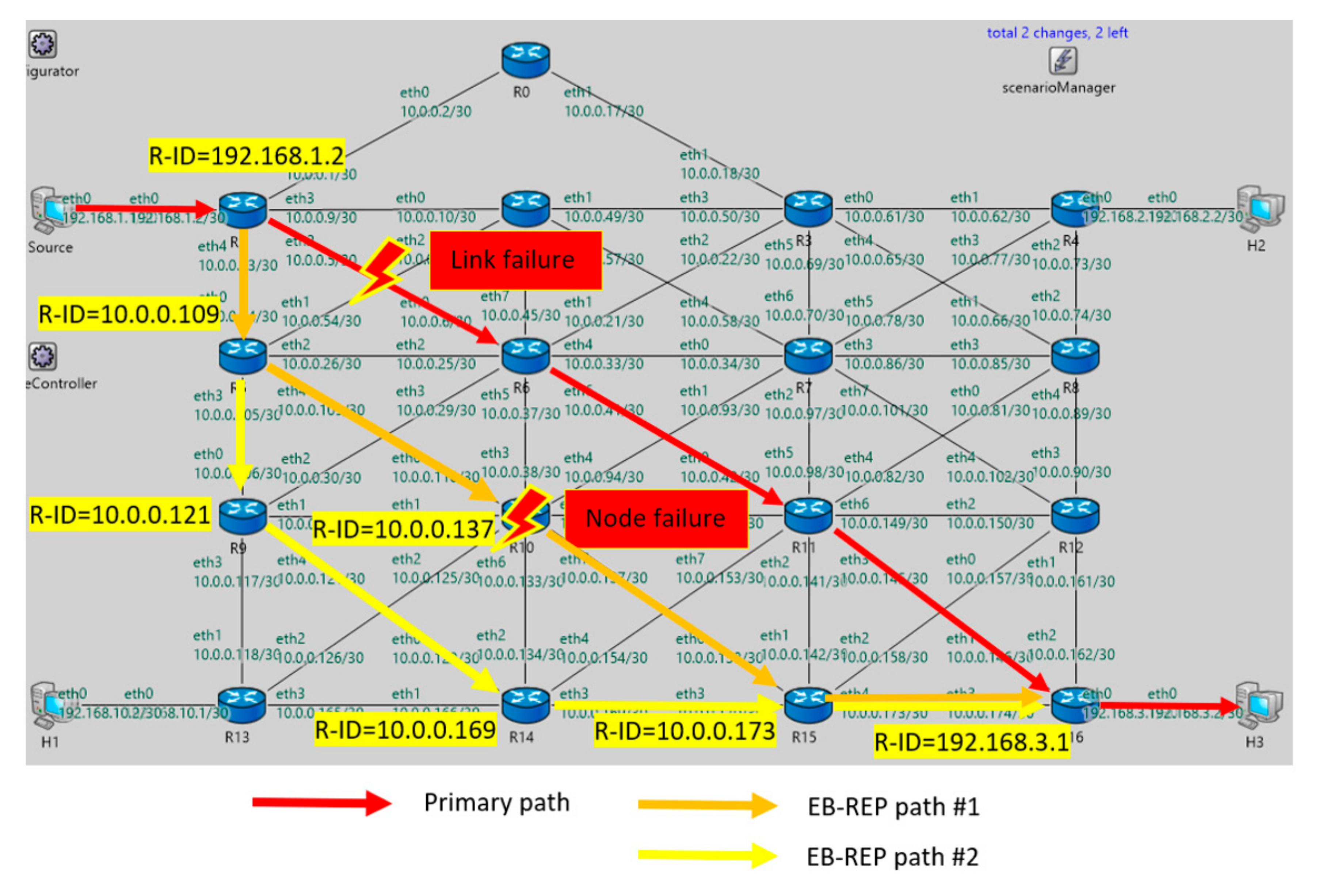
| OSPF R-ID | B-REP ID | Bit-String Position | |
|---|---|---|---|
| R7 | 10.0.0.101 | 1 | 0 0000 0000 0000 0001 |
| R5 | 10.0.0.109 | 2 | 0 0000 0000 0000 0010 |
| R9 | 10.0.0.121 | 3 | 0 0000 0000 0000 0100 |
| R10 | 10.0.0.137 | 4 | 0 0000 0000 0000 1000 |
| R11 | 10.0.0.149 | 5 | 0 0000 0000 0001 0000 |
| R12 | 10.0.0.161 | 6 | 0 0000 0000 0010 0000 |
| R14 | 10.0.0.169 | 7 | 0 0000 0000 0100 0000 |
| R0 | 10.0.0.17 | 8 | 0 0000 0000 1000 0000 |
| R15 | 10.0.0.173 | 9 | 0 0000 0001 0000 0000 |
| R6 | 10.0.0.45 | 10 | 0 0000 0010 0000 0000 |
| R2 | 10.0.0.57 | 11 | 0 0000 0100 0000 0000 |
| R3 | 10.0.0.69 | 12 | 0 0000 1000 0000 0000 |
| R8 | 10.0.0.89 | 13 | 0 0001 0000 0000 0000 |
| R1 | 192.168.1.2 | 14 | 0 0010 0000 0000 0000 |
| R13 | 192.168.10.2 | 15 | 0 0100 0000 0000 0000 |
| R4 | 192.168.2.1 | 16 | 0 1000 0000 0000 0000 |
| R16 | 192.168.3.1 | 17 | 1 0000 0000 0000 0000 |
| Output Interface | Destination IP | Bit-String Value |
|---|---|---|
| Eth2 | 192.168.3.0/24 | 1 0000 0001 0000 1010 (LSB) |
| Eth4 | 192.168.10.0/24 | 0 0100 0010 0000 0100 (LSB) |
| … | … |
| Time | Source/Destination | Name | Destination Address | |
|---|---|---|---|---|
| 0.079848721815 | R12 → R16 | OSPF_HelloPacket | IPv4: 10.0.0.161 > 224.0.0.5 | Network convergence |
| 0.079921539817 | R15 → R16 | OSPF_HelloPacket | IPv4: 10.0.0.173 > 224.0.0.5 | |
| 0.081934165641 | R1 → R6 | OSPF_HelloPacket | IPv4: 10.0.0.5 > 224.0.0.5 | |
| 0.081237815377 | R10 → R13 | OSPF_HelloPacket | IPv4: 10.0.0.125 > 224.0.0.5 | |
| 0.082016734148 | R6 → R9 | OSPF_HelloPacket | IPv4: 10.0.0.29 > 224.0.0.5 | |
| 0.082336121152 | R14 → R10 | OSPF_HelloPacket | IPv4: 10.0.0.134 > 224.0.0.5 | |
| 0.079899871815 | R12 → R16 | OSPF_HelloPacket | IPv4: 10.0.0.161 > 224.0.0.5 | |
| 0.079931579817 | R15 → R16 | OSPF_HelloPacket | IPv4: 10.0.0.173 > 224.0.0.5 | |
| 64.00006842 | →R1 | UDPBasicAppData-185 | 192.168.3.2 | Network without errors |
| 64.00008084 | R01 → R06 | UDPBasicAppData-185 | 192.168.3.2 | |
| 64.00009326 | R06 → R11 | UDPBasicAppData-185 | 192.168.3.2 | |
| 64.00010648 | R11 → R16 | UDPBasicAppData-185 | 192.168.3.2 | |
| 64.0001181 | R16 → H3 | UDPBasicAppData-185 | 192.168.3.2 | |
| 68.00007242 | →R1 | UDPBasicAppData-185 | 192.168.3.2 | |
| 68.00008484 | R1 → R06 | UDPBasicAppData-185 | 192.168.3.2 | |
| 68.00009726 | R06 → R11 | UDPBasicAppData-185 | 192.168.3.2 | |
| 68.00010968 | R11 → R16 | UDPBasicAppData-185 | 192.168.3.2 | |
| 68.0001221 | R16 → H3 | UDPBasicAppData-185 | 192.168.3.2 | |
| 70.00001829 | →R1 | UDPBasicAppData-185 | 192.168.3.2 | EB-REP FAST REROUTE |
| 70.00003071 | R1 → R5 | EB-REP-Data | 192.168.3.2 | |
| 70.00004313 | R5 → R10 | EB-REP-Data | 192.168.3.2 | |
| 70.00005555 | R10 → R15 | EB-REP-Data | 192.168.3.2 | |
| 70.00006797 | R15 → R16 | EB-REP-Data | 192.168.3.2 | |
| 70.00008039 | R16→ H3 | UDPBasicAppData-185 | 192.168.3.2 | |
| 80.00008729 | →R1 | UDPBasicAppData-185 | 192.168.3.2 | EB-REP FAST REROUTE |
| 80.00009971 | R1 → R5 | EB-REP-Data | 192.168.3.2 | |
| 80.00011213 | R5 → R9 | EB-REP-Data | 192.168.3.2 | |
| 80.00012455 | R9 → R14 | EB-REP-Data | 192.168.3.2 | |
| 80.00013697 | R14 → R15 | EB-REP-Data | 192.168.3.2 | |
| 80.00014939 | R15 → R16 | EB-REP-Data | 192.168.3.2 | |
| 80.00016181 | R16 → H3 | UDPBasicAppData-185 | 192.168.3.2 |
| Advantages | Disadvantages |
|---|---|
| Multiple failure protection Per-prefix calculation of backup paths Suitable for networks of any size | Precomputation |
| Applicable for an OSPF/IS-IS link-state routing protocol | Encapsulation packet overhead |
| 100% repair coverage | Consumption of system resources |
| Support for explicitly defined alternative paths Possibility to define a custom backup path | |
| Use of standardized BIER headers (Bit-String) |
| EB-REP | EM-REP | D-LFA | LFA | MRC | MRT | Not-Via Addresses | R-LFA | TI-LFA | |
|---|---|---|---|---|---|---|---|---|---|
| 100% Repair Coverage | Yes | Yes | Yes | No | Yes | Yes | Yes | No | Yes |
| Custom Alternative Path | Yes | No | Yes | No | Yes | No | No | No | No |
| Precomputing | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Packet Modification | Yes | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes |
| Link-State dependency | Yes | No | Yes | No | Yes | Yes | Yes | Yes | Yes |
| EB-REP | LFA | R-LFA | EM-REP | |
|---|---|---|---|---|
| Time of Fast Reroute Process | 0.035144 | 0.035044 | 0.035148 | 0.035358 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Papan, J.; Segec, P.; Kvet, M. Enhanced Bit Repair IP Fast Reroute Mechanism for Rapid Network Recovery. Appl. Sci. 2021, 11, 3133. https://doi.org/10.3390/app11073133
Papan J, Segec P, Kvet M. Enhanced Bit Repair IP Fast Reroute Mechanism for Rapid Network Recovery. Applied Sciences. 2021; 11(7):3133. https://doi.org/10.3390/app11073133
Chicago/Turabian StylePapan, Jozef, Pavel Segec, and Michal Kvet. 2021. "Enhanced Bit Repair IP Fast Reroute Mechanism for Rapid Network Recovery" Applied Sciences 11, no. 7: 3133. https://doi.org/10.3390/app11073133
APA StylePapan, J., Segec, P., & Kvet, M. (2021). Enhanced Bit Repair IP Fast Reroute Mechanism for Rapid Network Recovery. Applied Sciences, 11(7), 3133. https://doi.org/10.3390/app11073133








