The Rise of Blockchain Internet of Things (BIoT): Secured, Device-to-Device Architecture and Simulation Scenarios
Abstract
:1. Introduction
- It discusses the latest papers investigating the intermingling of blockchain technology applications in the IoT.
- It discusses a summary of the blockchain infrastructure chosen and implemented for IoT in the literature.
- It analyses various problems of BIoT and how to address these issues using IoT inventions.
- It develops a novel energy-efficient and secure method for collecting and managing sensors’ data in BIoT applications.
- It develops a secure BIoT-device-only architecture that ensures data confidentiality, transparency, and authenticity.
- It proposes a new ECC-CRT algorithm to enhance performance in terms of latency, throughput, and resource consumption.
- It develops a BIoT-based architecture that achieves outstanding performance by meeting all the necessary security requirements.
- The proposed architecture for low-power IoT devices based on the Ethereum blockchain solves the power issue in IoT devices while communicating, validating transactions, and providing security.
2. Literature Survey
2.1. Background, Definitions, and Cryptographic Algorithms
2.2. Related Work
3. Proposed BIoT Architecture
4. Proposed Methodology and Simulation Scenarios
4.1. SHA-256 Algorithm
4.2. ECC-CRT Algorithm
- s is message
- K is random number
- Received encrypted message
- received original message
| // working of ECC-CRT #include<bits/stdc++.h> using namespace std; // k is size of num[] and rem[]. Returns the smallest // number x such that: // x % num(0) = rem(0), // x % num(1) = rem(1), // .................. // x % num(k – 2) = rem(k – 1) // Assumption: Numbers in num() are pairwise coprime // (gcd for every pair is 1) int findMinX(int num[], int rem[], int k) { int x = 1; // Initialize result // As per the Chinese remainder theorem, // this loop will always break. while (true) { // Check if remainder of x % num(j) is // rem[j] or not (for all j from 0 to k − 1) int j; for (j = 0; j < k; j++ ) if (x%num(j) != rem(j)) break; // If all remainders matched, found x if (j == k) return x; // Else try next number x++; } return x; } // Driver method int main(void) { int num() = {3, 4, 5}; int rem() = {2, 3, 1}; int k = sizeof(num)/sizeof(num[0]); cout << “x is ” << findMinX(num, rem, k); return 0; } |
5. Results and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bhushan, B.; Sahoo, C.; Sinha, P.; Khamparia, A. Unification of Blockchain and Internet of Things (BIoT): Requirements, working model, challenges and future directions. Wirel. Netw. 2021, 27, 55–90. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Haque, M.R.; Tan, S.C.; Yusoff, Z.; Nisar, K.; Lee, C.K.; Chowdhry, B.S.; Ali, S.; Memona, S.K.; Kaspin, R. SDN architecture for UAVs and EVs using satellite: A hypothetical model and new challenges for future. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; IEEE: New York, NY, USA, 2021; pp. 1–6. [Google Scholar]
- Abdelmaboud, A.; Ahmed, A.I.A.; Abaker, M.; Eisa, T.A.E.; Albasheer, H.; Ghorashi, S.A.; Karim, F.K. Blockchain for IoT Applications: Taxonomy, Platforms, Recent Advances, Challenges and Future Research Directions. Electronics 2022, 11, 630. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef] [Green Version]
- Rana, A.; Chakraborty, C.; Sharma, S.; Dhawan, S.; Pani, S.K.; Ashraf, I. Internet of Medical Things-Based Secure and Energy-Efficient Framework for Health Care. Big Data 2022, 10, 18–33. [Google Scholar] [CrossRef]
- Harada, S.; Yan, Z.; Park, Y.J.; Nisar, K.; Ibrahim, A.A.A. Data aggregation in named data networking. In Proceedings of the TENCON 2017—2017 IEEE Region 10 Conference, Penang, Malaysia, 5–8 November 2017; IEEE: New York, NY, USA, 2017; pp. 1839–1842. [Google Scholar]
- Rana, A.K.; Sharma, S. Enhanced energy-efficient heterogeneous routing protocols in WSNs for IoT application. IJEAT 2019, 9, 4415–4418. [Google Scholar] [CrossRef]
- Rao, A.R.; Clarke, D. Perspectives on emerging directions in using IoT devices in blockchain applications. Internet Things 2020, 10, 100079. [Google Scholar] [CrossRef]
- Rana, A.K.; Sharma, S. Industry 4.0 manufacturing based on IoT, cloud computing, and big data: Manufacturing purpose scenario. In Advances in Communication and Computational Technology; Springer: Singapore, 2021; pp. 1109–1119. [Google Scholar]
- Samaniego, M.; Deters, R. Using blockchain to push software-defined IoT components onto edge hosts. In Proceedings of the International Conference on Big Data and Advanced Wireless Technologies, Blagoevgrad, Bulgaria, 10–11 November 2016; pp. 1–9. [Google Scholar]
- Kravitz, D.W.; Cooper, J. Securing user identity and transactions symbiotically: IoT meets blockchain. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; IEEE: New York, NY, USA, 2017; pp. 1–6. [Google Scholar]
- Dua, D.; Taniskidou, E.K. UCI Machine Learning Repository; School of Information and Computer Sciences, University of California: Irvine, CA, USA, 2018; Available online: http://archive.ics.uci.edu/ml (accessed on 10 June 2021).
- Lawal, I.A.; Said, A.M.; Nisar, K.; Mu’azu, A.A.; Shah, P.A. Throughput enhancement for fixed WiMAX network using distributed model. In Proceedings of the 2014 International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 3–5 June 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Lawal, I.A.; Said, A.M.; Nisar, K.; Mu’azu, A.A.; Shah, P.A. A Distributed QoS-Oriented Model to Improve Network Performance for Fixed WiMAX. Int. J. Recent Trends Eng. Technol. 2014, 10, 186–202. [Google Scholar]
- Nauman, M.; Tanveer, T.A.; Khan, S.; Syed, T.A. Deep neural architectures for large scale android malware analysis. Clust. Comput. 2018, 21, 569–588. [Google Scholar] [CrossRef]
- Nisar, K.; Amphawan, A.; Hassan, S.B. Comprehensive structure of novel voice priority queue scheduling system model for VoIP over WLANs. Int. J. Adv. Pervasive Ubiquitous Comput. (IJAPUC) 2011, 3, 50–70. [Google Scholar] [CrossRef] [Green Version]
- Wee, X.L.; Yan, Z.; Park, Y.J.; Leau, Y.-B.; Nisar, K.; Ibrahim, A.A.A. Rom-p: Route optimization management of producer mobility in information-centric networking. In First International Conference on Intelligent Transport Systems; Springer: Cham, Switzerland, 2018; pp. 81–91. [Google Scholar]
- Wang, Q.; Zhu, X.; Ni, Y.; Gu, L.; Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet Things 2020, 10, 100081. [Google Scholar] [CrossRef]
- Kaplan, A. How Alibaba Is Championing the Application of Blockchain Technology in China and Beyond. 2018. Available online: https://smartereum.com/7630/how-alibaba-is-championing-the-application-of-blockchain-technology-in-china-and-beyond-sun-jun-09/ (accessed on 22 June 2018).
- Huang, Z. China’s Crackdown on Crypto Hasn’t Stopped Its Tech Giants from Flirting with Blockchain. 2018. Available online: https://twitter.com/qz/status/987179394966982656 (accessed on 30 March 2018).
- Levy, A. Why Mark Zuckerberg Just Put Some of His Best Execs on Blockchain. 2018. Available online: https://finance.yahoo.com/news/why-mark-zuckerberg-just-put-130100695.html (accessed on 10 May 2018).
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere-a use-case of blockchains in the pharma supply-chain. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; IEEE: New York, NY, USA, 2017; pp. 772–777. [Google Scholar]
- Ahmad, A. Integration of IoT Devices via a Blockchain-Based Decentralized Application. Master’s Thesis, University of Stuttgart, Stuttgart, Germany, 2018. [Google Scholar]
- Orenge, A.O. Blockchain-Based Provenance Solution for Handcrafted Jewellery. Ph.D. Thesis, University of Tartu, Tartu, Estonia, 2018. [Google Scholar]
- Brady, S.; Hava, A.; Perry, P.; Murphy, J.; Magoni, D.; Portillo-Dominguez, A.O. Towards an emulated IoT test environment for anomaly detection using NEMU. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; IEEE: New York, NY, USA, 2017; pp. 8–21. [Google Scholar]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A practical performance comparison of ECC and RSA for resource-constrained IoT devices. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; IEEE: New York, NY, USA, 2018; pp. 1–6. [Google Scholar]
- Chhabra, A.; Arora, S. An elliptic curve cryptography based encryption scheme for securing the cloud against eavesdropping attacks. In Proceedings of the 2017 IEEE 3rd International Conference on Collaboration and Internet Computing (CIC), San Jose, CA, USA, 15–17 October 2017; IEEE: New York, NY, USA, 2017; pp. 243–246. [Google Scholar]
- Hussain, I.; Negi, M.C.; Pandey, N. A secure IoT-based power plant control using RSA and DES encryption techniques in data link layer. In Proceedings of the 2017 International Conference on Infocom Technologies and Unmanned Systems (Trends and Future Directions) (ICTUS), Dubai, United Arab Emirates, 18–20 December 2017; IEEE: New York, NY, USA, 2017; pp. 464–470. [Google Scholar]
- Tsang, Y.P.; Choy, K.L.; Wu, C.H.; Ho, G.T.; Lam, H.Y. Blockchain-driven IoT for food traceability with an integrated consensus mechanism. IEEE Access 2019, 7, 129000–129017. [Google Scholar] [CrossRef]
- Wu, J.; Dong, M.; Ota, K.; Li, J.; Yang, W. Application-aware consensus management for software-defined intelligent blockchain in IoT. IEEE Netw. 2020, 34, 69–75. [Google Scholar] [CrossRef]
- Pavithran, D.; Shaalan, K.; Al-Karaki, J.N.; Gawanmeh, A. Towards building a blockchain framework for IoT. Clust. Comput. 2020, 23, 2089–2103. [Google Scholar] [CrossRef]
- Miraz Mahdi, H. Blockchain of Things (blockchainoT): The Fusion of Blockchain and IoT Technologies. In Advanced Applications of Blockchain Technology; Springer: Singapore, 2020; pp. 141–159. [Google Scholar]
- Rana, A.K.; Krishna, R.; Dhwan, S.; Sharma, S.; Gupta, R. Review on artificial intelligence with internet of things-problems, challenges and opportunities. In Proceedings of the 2019 2nd International Conference on Power Energy, Environment and Intelligent Control (PEEIC), Greater Noida, India, 18–19 October 2019; IEEE: New York, NY, USA, 2019; pp. 383–387. [Google Scholar]
- Kharif, O.; Bergen, M. Google Is Working on Its Own Blockchain-Related Technology. 2018. Available online: https://www.bloomberg.com/news/articles/2018-03-21/google-is-said-to-work-on-its-own-Blockchain-related-technology (accessed on 22 June 2021).
- Kumar, A.; Sharma, S.; Goyal, N.; Singh, A.; Cheng, X.; Singh, P. Secure and energy-efficient smart building architecture with emerging technology IoT. Comput. Commun. 2021, 176, 207–217. [Google Scholar] [CrossRef]
- Shoker, A. Sustainable blockchain through proof of exercise. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; IEEE: New York, NY, USA, 2017; pp. 1–9. [Google Scholar]
- Kumar, A.; Sharma, S. IFTTT rely based a semantic web approach to simplifying trigger-action programming for end-user application with IoT applications. In Semantic IoT: Theory and Applications; Springer: Cham, Switzerland, 2021; pp. 385–397. [Google Scholar]
- Zhang, Y.; Wen, J. An IoT electric business model based on the protocol of bitcoin. In Proceedings of the 2015 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; IEEE: New York, NY, USA, 2015; pp. 184–191. [Google Scholar]
- Kumar, A.; Sharma, S.; Singh, A.; Alwadain, A.; Choi, B.-J.; Manual-Brenosa, J.; Ortega-Mansilla, A.; Goyal, N. Revolutionary Strategies Analysis and Proposed System for Future Infrastructure in Internet of Things. Sustainability 2022, 14, 71. [Google Scholar] [CrossRef]
- Ateniese, G.; Goodrich, M.; Lekakis, V.; Papamanthou, C.; Paraskevas, E.; Tamassia, R. Accountable Storage. In Proceedings of the International Conference on Applied Cryptography and Network Security, Kanazawa, Japan, 10–12 July 2017. [Google Scholar]
- Jimson, E.R.; Nisar, K.; Hijazi, M.H.A. The state of the art of software defined networking (SDN) issues in current network architecture and a solution for network management using the SDN. Int. J. Technol. Diffus. (IJTD) 2019, 10, 33–48. [Google Scholar] [CrossRef] [Green Version]
- Huang, X.; Dong, Y.; Zhu, H.; Ye, G. Visually asymmetric image encryption algorithm based on SHA-3 and compressive sensing by embedding encrypted image. Alex. Eng. J. 2022, 61, 7637–7647. [Google Scholar] [CrossRef]
- Suman, R.R.; Mondal, B.; Mandal, T. A secure encryption scheme using a Composite Logistic Sine Map (CLSM) and SHA-256. Multimed. Tools Appl. 2022, 22, 1–22. [Google Scholar] [CrossRef]
- Esai Malar, E.; Paramasivan, B. Enhancing Security and Privacy Preserving of Data in Cloud Using SHA and Genetic Algorithm. In Computational Intelligence in Pattern Recognition; Springer: Singapore, 2022; pp. 401–411. [Google Scholar]
- Rana, S.K.; Kim, H.C.; Pani, S.K.; Rana, S.K.; Joo, M.I.; Rana, A.K.; Aich, S. Blockchain-Based Model to Improve the Performance of the Next-Generation Digital Supply Chain. Sustainability 2021, 13, 10008. [Google Scholar] [CrossRef]
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data sharing system integrating access control mechanism using blockchain-based smart contracts for IoT devices. Appl. Sci. 2020, 10, 488. [Google Scholar] [CrossRef] [Green Version]
- Laurent, A.; Brotcorne, L.; Fortz, B. Transactions fees optimization in the Ethereum blockchain. Blockchain Res. Appl. 2022, 100074. [Google Scholar] [CrossRef]
- Dhawan, S.; Chakraborty, C.; Frnda, J.; Gupta, R.; Rana, A.K.; Pani, S.K. SSII: Secured and high-quality steganography using intelligent hybrid optimization algorithms for IoT. IEEE Access 2021, 9, 87563–87578. [Google Scholar] [CrossRef]
- Thai, Q.T.; Ko, N.; Byun, S.H.; Kim, S.M. Design and implementation of NDN-based Ethereum blockchain. J. Netw. Comput. Appl. 2022, 200, 103329. [Google Scholar] [CrossRef]










| References | IoT Levels | Affected Layers | Implications | Propose Solutions | Blockchain Technology Used |
|---|---|---|---|---|---|
| D. W. Kravitz and J. Cooper [13] | Intermediate level | Network layer | Privacy violation | Permissioned blockchain has been proposed as an efficient way to protect and control these networks. | Private Blockchain |
| Jawad Ali et al. [16] | Intermediate level | Adaptation layer, network layer | Disruption and denial-of-service | In terms of fundamental security priorities, i.e., secrecy, integrity, and availability, the proposed IoT-blockchain architecture is sufficiently secure. | Private Blockchain |
| Liu et al. [19] | Low level | 6LoWPAN adaptation layer, and network layer | Privacy violation | Numerous performances have been studied for different types of features and offer an efficient solution for the detection of malware on Android devices. | Hybrid Blockchain |
| Mearian et al. [20] | Low level | Network layer | Disruption and denial-of-service | For this situation, the information is accessible; however, the accessibility for doing exchanges might be halted by the assailant that controls the blockchain. | Blockchain Consortium |
| Cabrera et al. [22] | Low level | Adaptation layer, network layer | Privacy violation and denial-of-service | Protection was progressively confounded in BIoT conditions, because BIoT gadgets may find extraordinary client information that can be spared in a blockchain whose security necessities are unique about a nation to another nation. | Private Blockchain |
| Thomas Boceket al. [26] | Low level | Network layer | Privacy violation | Modum.io, a start-up that uses IoT sensor sensors to exploit blockchain technologies to claim temperature record data immutability and public visibility while reducing operating costs in the supply chain of pharmaceuticals, is presented. | Blockchain Consortium |
| Afzaal Ahmad [27] | High level, Intermediate level | Adaptation layer, and network layer | Privacy violation and denial-of-service | An idea was presented to incorporate IoT networks dependent on Ethereum via a blockchain-based decentralized framework. | Private Blockchain |
| Antony oroko orange [28] | Application layer, and network layer | Privacy violation | The study findings will lead to the creation of context management structures. | Public Blockchain | |
| Shane Brady et al. [29] | Intermediate level | Application layer, and network layer | Disruption and denial-of-service | A novel approach to simulating an IoT ecosystem was suggested. | Public Blockchain |
| Suárez-Albela et al. [30] | High level, Intermediate level | Adaptation layer, and network layer | Privacy violation | Its specific mechanisms help establish data confidentiality, integrity, and privacy. | Private Blockchain |
| Chhabra et al. [31] | Intermediate level | Adaptation layer, and network layer | Privacy violation and denial-of-service | A security scheme based on RSA and ECC for IoT data has been proposed that used RSA security blocks to promote the security level. | Blockchain Consortium |
| Hussain et al. [32] | High level, Intermediate level | Application layer, and network layer | Privacy violation and denial-of-service | RSA is used to enhance cryptography and privacy processes. | Hybrid Blockchain |
| Tsang et al. [33] | Intermediate level | Network layer | Privacy violation and denial-of-service | The blockchain data flow is then linked to the IoT technology deployment based on the number of traceable resource units. | Hybrid Blockchain |
| Wu et al. [34] | Intermediate level | Adaptation layer, and network layer | Disruption and denial-of-service | A consensus virtualization technique of application-aware workflow is then proposed, which can abstract and handle several tools of consensus. | Private Blockchain |
| Pavithran et al. [35] | High level and Intermediate level | Adaptation layer, and network layer | Privacy violation | Researchers discussed a recent literature review with their design requirements and challenges. | Public Blockchain |
| Miraz et al. [36] | Intermediate level | 6LoWPAN adaptation layer, and network layer | IP spoofing | This paper acutely addressed the possibility of security parameters combining blockchain with IoT technologies. | Private Blockchain |
| Lee et al. [37] | High level and Intermediate level | Application layer, and network layer | Privacy violation and denial-of-service | Researchers discussed the use of blockchain in-home gateway. | Private Blockchain |
| Proposed work in this paper | High level and Intermediate level | Physical layer, application layer, and network layer | Highly secured due to ECC-CRT in BIoT network | ECC-CRT enhances performance in terms of latency, throughput, resource consumption, and IoT-device-only architecture ensures data confidentiality, transparency, and authenticity. | Ethereum Blockchain |
| Parameter | Value |
|---|---|
| Operating System | Contiki 2.7 |
| Simulator | COOJA |
| Computer | RAM 8GB |
| Transmission Range | 50 m |
| Interference Range | 55 m |
| Simulation Time | 90 min |
| Routing Protocol | 6LoWPAN |
| Number of Nodes | 06, 12, 24, 48 |
| Topology | Random |
| MAC Layer | 802.15.4 |
| Node Type | Z-mote |
| Parameter | ECC-CRT | SHA-256 |
|---|---|---|
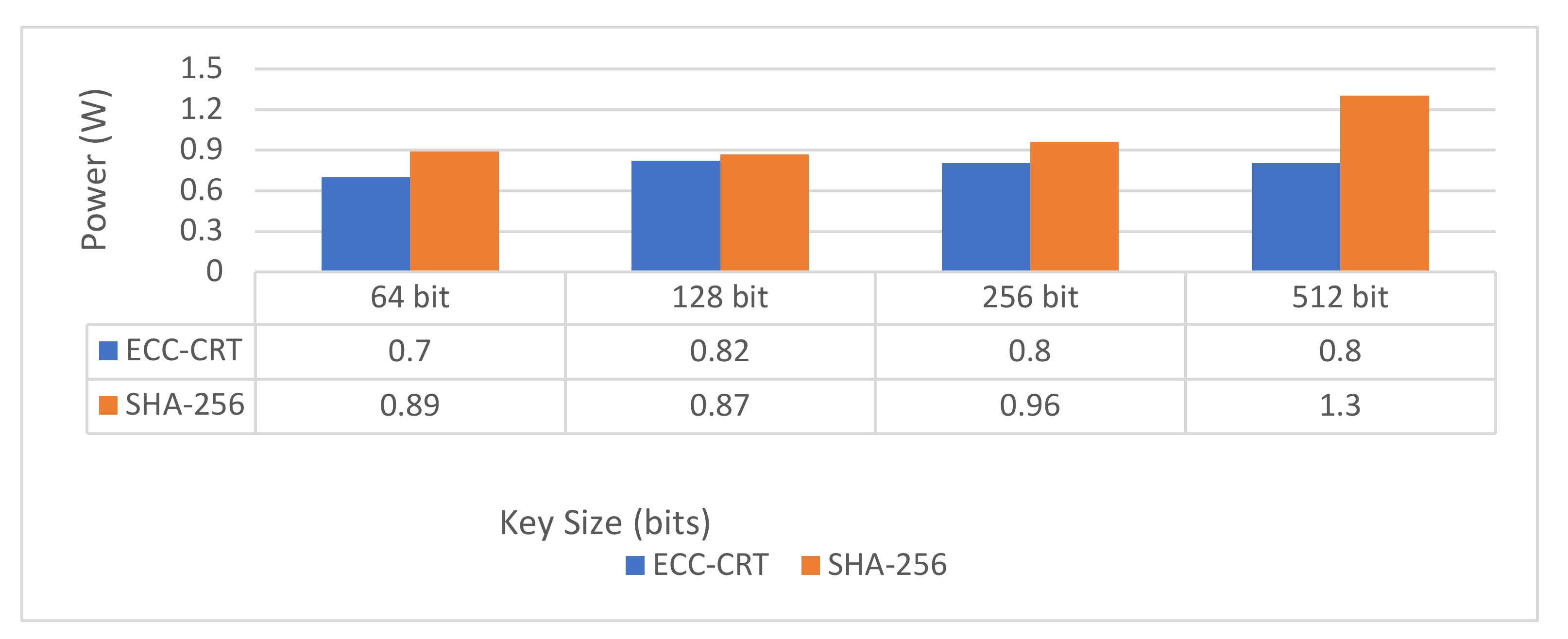
| Power Consumption | Less | High |
| Life Time | High | Less |
| Security | High | Less |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rana, A.; Sharma, S.; Nisar, K.; Ibrahim, A.A.A.; Dhawan, S.; Chowdhry, B.; Hussain, S.; Goyal, N. The Rise of Blockchain Internet of Things (BIoT): Secured, Device-to-Device Architecture and Simulation Scenarios. Appl. Sci. 2022, 12, 7694. https://doi.org/10.3390/app12157694
Rana A, Sharma S, Nisar K, Ibrahim AAA, Dhawan S, Chowdhry B, Hussain S, Goyal N. The Rise of Blockchain Internet of Things (BIoT): Secured, Device-to-Device Architecture and Simulation Scenarios. Applied Sciences. 2022; 12(15):7694. https://doi.org/10.3390/app12157694
Chicago/Turabian StyleRana, Arun, Sharad Sharma, Kashif Nisar, Ag. Asri Ag. Ibrahim, Sachin Dhawan, Bhawani Chowdhry, Samreen Hussain, and Nitin Goyal. 2022. "The Rise of Blockchain Internet of Things (BIoT): Secured, Device-to-Device Architecture and Simulation Scenarios" Applied Sciences 12, no. 15: 7694. https://doi.org/10.3390/app12157694
APA StyleRana, A., Sharma, S., Nisar, K., Ibrahim, A. A. A., Dhawan, S., Chowdhry, B., Hussain, S., & Goyal, N. (2022). The Rise of Blockchain Internet of Things (BIoT): Secured, Device-to-Device Architecture and Simulation Scenarios. Applied Sciences, 12(15), 7694. https://doi.org/10.3390/app12157694








