Enhancing the Privacy of Network Services through Trusted Computing
Abstract
:1. Introduction
- To enhance the security of DNS, we design a privacy-preserving and trustworthy addressing and discovering service based on TEE technology.
- To deal with the hardware limitations of SGX and reduce the cost of adopting the new framework, we build a novel compilation model for the widespread deployment of trusted services and the correctness of refactored code.
- To evaluate compatibility and compare our scheme with existing improvements, we implement a prototype system using Intel SGX. Experimental results show that the proposed DoTT can effectively maintain the low latency of DNS when preserving privacy.
2. Backgrounds and Related Work
2.1. The Addressing and Discovering Service
2.2. Intel SGX
2.3. The List of Abbreviations
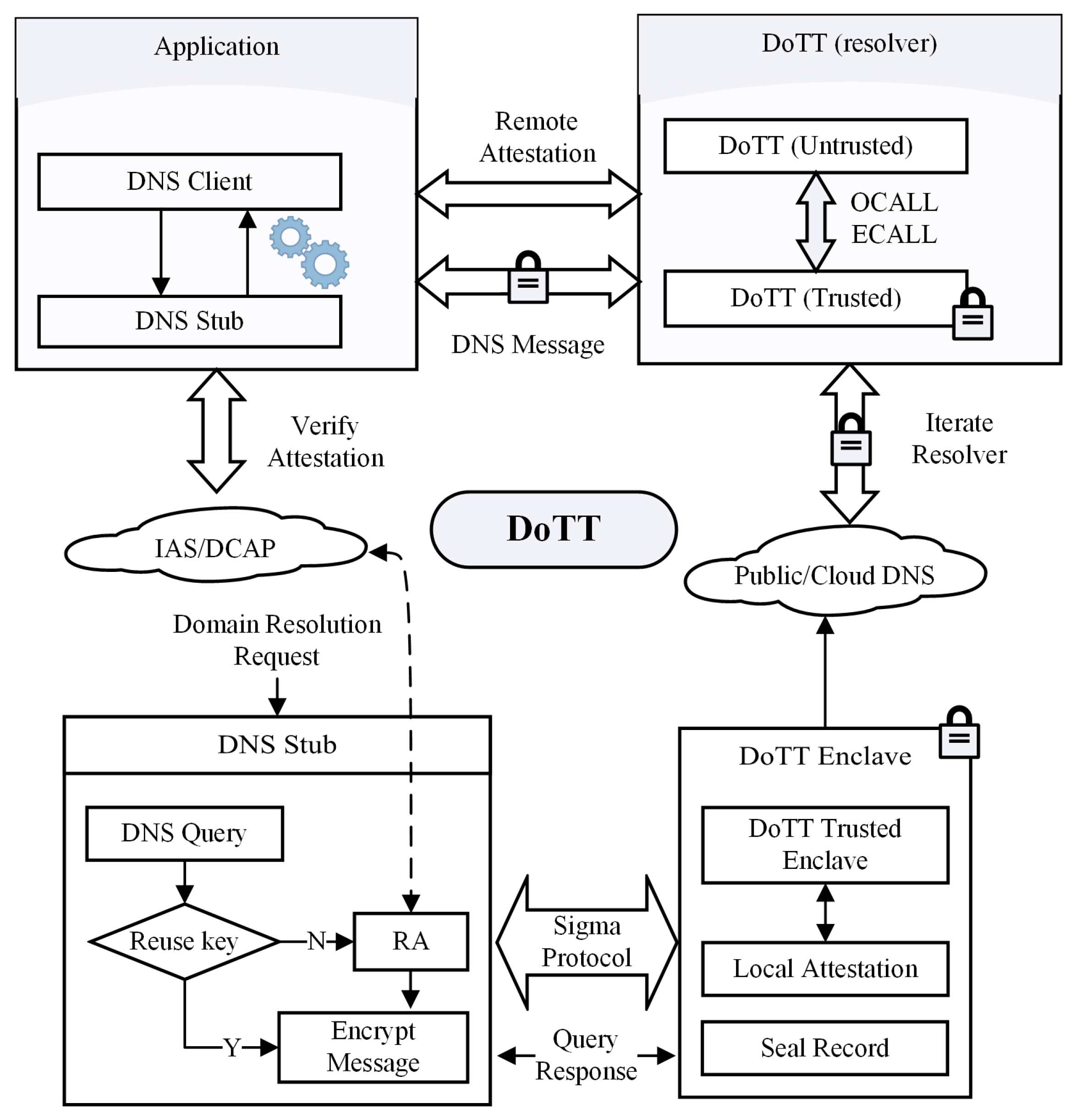
3. A Trusted and Backward-Compatible Addressing Service
3.1. Trusted Service
- When web applications initiate a DNS query (denoted as R), the S will check whether a TLS connection has been established.
- The S directly forwards R to D using the encrypted channel if the connection is established. When D receives the request, it will get the IP address corresponding to the request from the NS as the conventional recursive resolving method and return it to S.
- The S will challenge D by sending a nonce to it if the connection is not established. To convince R that it is a genuine Intel SGX enclave running on an authenticatable DNS resolver, D first performs the LA with the quoting enclave (donated as Q) in the local machine. If S succeeds in generating an authentication message (denoted as M), Q will sign the hash value of the authentication result, which comprises the public key of D.
- After receiving the report, S can forward it to the IAS, which is a public webserver to provision a message generated by genuine Intel hardware. We can also adopt the Intel SGX DCAP [31] (Data Center Attestation Primitives) as an alternative to provision attestation services into a user-side database. After registering the genuine information to DCAP during the deployment phase, the whole remote attention procedure can be finished without an Internet connection in DCAP. After validating the reported signature using the certificate of IAS, S will check the enclave identify (MRENCLAVE) is in the list L. Then, the DNS stub can assure that DoTT is running a genuine SGX enclave and uses the public key hash in M for the following TLS connection.
- Once S confirms the authentication and validation of M, it will exchange a symmetric session key (donated as K) to encrypt subsequent DNS queries. Therefore, S and D can communicate in an authenticated and privacy-preserving way with K.
3.2. Backward-Compatible Service
3.3. Optimization for SGX
3.4. Security Analysis
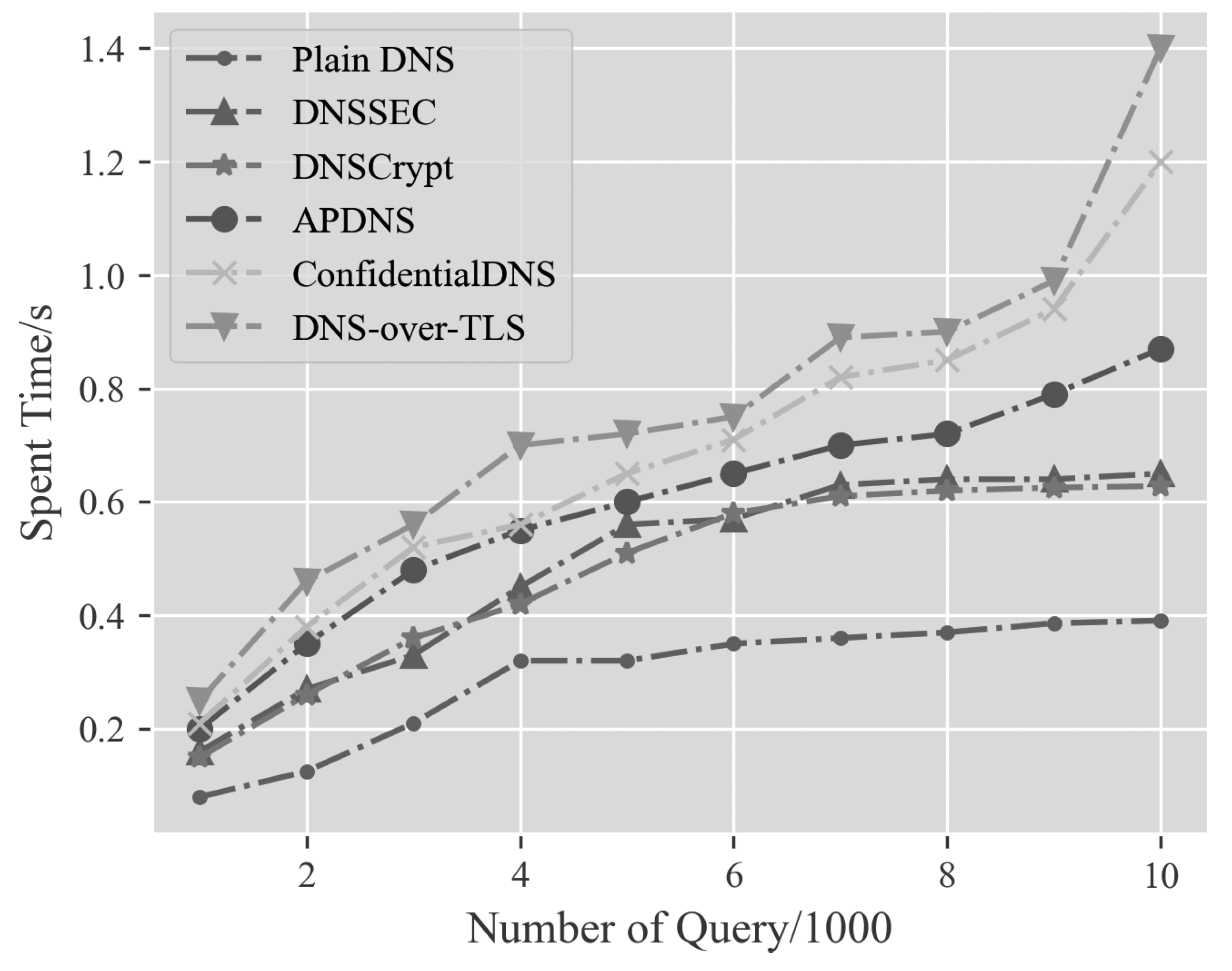
4. Experimental Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sahraoui, Y.; Kerrache, C.A.; Korichi, A.; Vegni, A.M.; Amadeo, M. LearnPhi: A Real-Time Learning Model for Early Prediction of Phishing Attacks in IoV. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022. [Google Scholar]
- Gu, Z.; Wang, L.; Chen, X.; Tang, Y.; Wang, X.; Du, X.; Guizani, M.; Tian, Z. Epidemic Risk Assessment by a Novel Communication Station Based Method. IEEE Trans. Netw. Sci. Eng. 2022, 9, 332–344. [Google Scholar] [CrossRef] [PubMed]
- He, X.; Wang, J.; Liu, J.; Han, Z.; Lv, Z.; Wang, W. DNS Rebinding Detection for Local Internet of Things Devices. In Frontiers in Cyber Security; Springer: Singapore, 2020; pp. 19–29. [Google Scholar] [CrossRef]
- Yan, Z.; Lee, J.H. The road to DNS privacy. Future Gener. Comput. Syst. 2020, 112, 604–611. [Google Scholar] [CrossRef]
- Liu, Y.; Jiang, Y.; Ge, N. Design of Personal Terminal DNS Agent. J. Commun. Inf. Netw. 2021, 6, 251–266. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A Malicious Bot-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques. IEEE Internet Things J. 2021, 8, 3242–3254. [Google Scholar] [CrossRef]
- Bhushan, K.; Gupta, B.B. Distributed denial of service (DDoS) attack mitigation in software defined network (SDN)-based cloud computing environment. Ambient. Intell. Hum. Comput. 2019, 10, 1985–1997. [Google Scholar] [CrossRef]
- Bumanglag, K.; Kettani, H. On the impact of DNS over HTTPS paradigm on cyber systems. In Proceedings of the 2020 3rd International Conference on Information and Computer Technologies (ICICT), San Jose, CA, USA, 9–12 March 2020; pp. 494–499. [Google Scholar] [CrossRef]
- Shah, S.L.; Abbasi, I.A.; Bashier Gism Elseed, A.; Ali, S.; Anwar, Z.; Rajpoot, Q.; Riaz, M. TAMEC: Trusted Augmented Mobile Execution on Cloud. Sci. Program. 2021, 2021, 5542852. [Google Scholar] [CrossRef]
- Gu, Z.; Li, H.; Deng, L.; Du, X.; Guizani, M.; Tian, Z. IEPSBP: A Cost-Efficient Image Encryption Algorithm Based on Parallel Chaotic System for Green IoT. IEEE Trans. Green Commun. Netw. 2022, 6, 89–106. [Google Scholar] [CrossRef]
- Zhang, J.; Tong, W.; Zhu, L.; Ou, W.; Li, X. Evaluating DNS Vulnerability to Cache Injection. In Proceedings of the 2019 IEEE International Conference on Computation, Communication and Engineering (ICCCE), Longyan, China, 8–10 November 2019; pp. 134–137. [Google Scholar] [CrossRef]
- Wang, W.T.; Hu, N.; Liu, B.; Liu, X.; Li, S.D. Survey on technology of security enhancement for DNS. J. Softw. 2020, 31, 7. [Google Scholar]
- Zhauniarovich, Y.; Khalil, I.; Yu, T.; Dacier, M. A Survey on Malicious Domains Detection through DNS Data Analysis. ACM Comput. Surv. 2018, 51, 67:1–67:36. [Google Scholar] [CrossRef]
- Aijaz, N.U.; Misbahuddin, M.; Raziuddin, S. Survey on DNS-Specific Security Issues and Solution Approaches. In Data Science and Security; Jat, D.S., Shukla, S., Unal, A., Mishra, D.K., Eds.; Springer: Singapore, 2021; Volume 132, pp. 79–89. [Google Scholar]
- Liang, H.; Li, M.; Chen, Y.; Yang, T.; Xie, Z.; Jiang, L. Architectural Protection of Trusted System Services for SGX Enclaves in Cloud Computing. IEEE Trans. Cloud Comput. 2021, 9, 910–922. [Google Scholar] [CrossRef]
- Gu, Z.; Hu, W.; Zhang, C.; Lu, H.; Yin, L.; Wang, L. Gradient Shielding: Towards Understanding Vulnerability of Deep Neural Networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 921–932. [Google Scholar] [CrossRef]
- Jin, Y.; Tomoishi, M.; Fujikawa, K.; Kafle, V.P. A Lightweight and Secure IoT Remote Monitoring Mechanism Using DNS with Privacy Preservation. In Proceedings of the 2019 16th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; p. 12. [Google Scholar] [CrossRef]
- Zheng, W.; Wu, Y.; Wu, X.; Feng, C.; Sui, Y.; Luo, X.; Zhou, Y. A survey of Intel SGX and its applications. Front. Comput. Sci. 2020, 15, 3. [Google Scholar] [CrossRef]
- McKeen, F.; Rovich, A.I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. In Proceedings of the HASP ’13: The Second Workshop on Hardware and Architectural Support for Security and Privacy, Tel-Aviv, Israel, 23–24 June 2013. [Google Scholar]
- Saraj, T.; Yousaf, M. Design and implementation of a lightweight privacy extension of DNSSEC protocol. In Proceedings of the 2017 13th International Conference on Emerging Technologies (ICET), Islamabad, Pakistan, 27–28 December 2017; p. 16. [Google Scholar] [CrossRef]
- Anagnostopoulos, M.; Kambourakis, G.; Konstantinou, E.; Gritzalis, S. DNSSEC vs. DNSCurve: A side-by-side comparison. In Situational Awareness in Computer Network Defense: Principles, Methods and Applications; IGI Global: Hershey, PA, USA, 2012; pp. 201–220. [Google Scholar]
- Dickinson, S.; Gillmor, D.; Reddy, T. Usage Profiles for DNS over TLS and DNS over DTLS; RFC 7858; Internet Engineering Task Force (IETF); IETF: London, UK, 2018. [Google Scholar]
- Böttger, T.; Felix, C.; Gianni, A.; Leão Fernandes, E.; Tyson, G.; Castro, I.; Uhlig, S. An Empirical Study of the Cost of DNS-over-HTTPS. In Proceedings of the Internet Measurement Conference, Amsterdam, The Netherlands, 21–23 October 2019; pp. 15–21. [Google Scholar] [CrossRef]
- Sierra-Arriaga, F.; Branco, R.; Lee, B. Security issues and challenges for virtualization technologies. ACM Comput. Surv. 2020, 53, 1–37. [Google Scholar] [CrossRef]
- Pinto, S.; Santos, N. Demystifying arm trustzone: A comprehensive survey. ACM Comput. Surv. (CSUR) 2019, 51, 136. [Google Scholar] [CrossRef]
- Brenner, S.; Kapitza, R. Trust More, Serverless. In Proceedings of the 12th ACM International Conference on Systems and Storage, New York, NY, USA, 3–5 June 2019; pp. 33–43. [Google Scholar] [CrossRef]
- Shen, Y.; Chen, Y.; Chen, K.; Tian, H.; Yan, S. To Isolate, or to Share?: That is a Question for Intel SGX. In Proceedings of the 9th Asia-Pacific Workshop on Systems—APSys’18, Jeju Island, Korea, 27–28 August 2018; p. 18. [Google Scholar] [CrossRef]
- Priebe, C.; Muthukumaran, D.; Lind, J.; Zhu, H.; Cui, S.; Sartakov, V.A.; Pietzuch, P. SGX-LKL: Securing the Host OS Interface for Trusted Execution. arXiv 2019, arXiv:1908.11143. [Google Scholar]
- Lind, J.; Priebe, C.; Muthukumaran, D.; O’Keeffe, D.; Aublin, P.L.; Kelbert, F.; Reiher, T.; Goltzsche, D.; Eyers, D.; Kapitza, R.; et al. Glamdring: Automatic Application Partitioning for Intel SGX. In Proceedings of the 2017 USENIX Annual Technical Conference (USENIX ATC 17), Santa Clara, CA, USA, 12–14 July 2017; pp. 285–298. [Google Scholar]
- Silva, R.; Barbosa, P.; Brito, A. DynSGX: A Privacy Preserving Toolset for Dynamically Loading Functions into Intel (R) SGX Enclaves. In Proceedings of the 2017 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Hong Kong, 11–14 December 2017; pp. 314–321. [Google Scholar] [CrossRef]
- Sardar, M.U.; Faqeh, R.; Fetzer, C. Formal Foundations for Intel SGX Data Center Attestation Primitives. In Formal Methods and Software Engineering; Springer: Cham, Switzerland, 2020; pp. 268–283. [Google Scholar] [CrossRef]
- Liu, X.; Guo, Z.; Ma, J.; Song, Y. A Secure Authentication Scheme for Wireless Sensor Networks Based on DAC and Intel SGX. IEEE Internet Things J. 2021, 9, 3533–3547. [Google Scholar] [CrossRef]
- Chen, Y.; Luo, F.; Li, T.; Xiang, T.; Liu, Z.; Li, J. A training-integrity privacy-preserving federated learning scheme with trusted execution environment. Inf. Sci. 2020, 522, 69–79. [Google Scholar] [CrossRef]
- Tsai, C.C.; Porter, D.E.; Vij, M. Graphene-SGX: A Practical Library OS for Unmodified Applications on SGX. In Proceedings of the 2017 USENIX Annual Technical Conference (USENIX ATC 17), Santa Clara, CA, USA, 12–14 July 2017; pp. 645–658. [Google Scholar]
- Shen, Y.; Tian, H.; Chen, Y.; Chen, K.; Wang, R.; Xu, Y.; Xia, Y.; Yan, S. Occlum: Secure and Efficient Multitasking Inside a Single Enclave of Intel SGX. In Proceedings of the 25th International Conference on Architectural Support for Programming Languages and Operating Systems, Lausanne, Switzerland, 16–20 March 2020; pp. 955–970. [Google Scholar] [CrossRef]
- Liu, G.; Yan, Z.; Feng, W.; Jing, X.; Chen, Y.; Atiquzzaman, M. SeDID: An SGX-enabled decentralized intrusion detection framework for network trust evaluation. Inf. Fusion 2021, 70, 100–114. [Google Scholar] [CrossRef]
- Tramer, F.; Boneh, D. Slalom: Fast, Verifiable and Private Execution of Neural Networks in Trusted Hardware. In Proceedings of the International Conference on Learning Representations, Orleans, LO, USA, 6–9 May 2019. [Google Scholar]
- Qiang, W.; Dong, Z.; Jin, H. Se-Lambda: Securing Privacy-Sensitive Serverless Applications Using SGX Enclave. In Security and Privacy in Communication Networks; Springer: Cham, Switzerland, 2018; pp. 451–470. [Google Scholar] [CrossRef]
- Ahmad, A.; Kim, K.; Sarfaraz, M.I.; Lee, B. OBLIVIATE: A Data Oblivious Filesystem for Intel SGX. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 18–21 February 2018. [Google Scholar] [CrossRef]
- Oh, H.; Ahmad, A.; Park, S.; Lee, B.; Paek, Y. TRUSTORE: Side-Channel Resistant Storage for SGX using Intel Hybrid CPU-FPGA. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 9–13 November 2020; pp. 1903–1918. [Google Scholar] [CrossRef]
- Zhang, D.; Wang, G.; Xu, W.; Gao, K. SGXPy: Protecting Integrity of Python Applications with Intel SGX. In Proceedings of the 2019 26th Asia-Pacific Software Engineering Conference (APSEC), Putrajaya, Malaysia, 2–5 December 2019; pp. 418–425. [Google Scholar] [CrossRef]
- Maudoux, G.; Mens, K. Correct, efficient, and tailored: The future of build systems. IEEE Softw. 2018, 35, 32–37. [Google Scholar] [CrossRef]
- McKeen; Alexandrovich, F.; Anati, I.; Caspi, I.; Johnson, D.; Leslie-Hurd, S.; Rozas, C. Intel Software Guard Extensions (Intel SGX) Support for Dynamic Memory Management Inside an Enclave. In Proceedings of the Hardware and Architectural Support for Security and Privacy 2016, New York, NY, USA, 18 June 2016; p. 19. [Google Scholar] [CrossRef]
- Scarlata, V.; Johnson, S.; Beaney, J.; Zmijewski, P. Supporting Third Party Attestation for Intel® SGX with Intel® Data Center Attestation Primitives; White Paper; Intel Corp.: Santa Clara, CA, USA, 2018. [Google Scholar]




| Scheme | Privacy | Authentication | Performance | Deployability |
|---|---|---|---|---|
| Plain DNS | ✗ | ✗ | ✓ | ✓ |
| DNSSEC | ✗ | ✓ | ✗ | ✓ |
| DNSCrypt/DNSCurve | ✓ | ✓ | ✗ | ✓ |
| ConfidentialDNS | ✓ | ✓ | ✗ | ✗ |
| DNS-over-TLS | ✓ | ✗ | ✗ | ✓ |
| DNS-over-HTTPS | ✓ | ✗ | ✗ | ✓ |
| DoTT (Our) | ✓ | ✓ | ✗ | ✓ |
| Abbreviation | Term |
|---|---|
| DNS | Domain Name System |
| IoT | Internet of Things |
| IoV | Internet of Vehicles |
| TEE | Trusted Computing Environment |
| SGX | Software Guard Extensions |
| TLS | Transport Layer Security |
| DoTT | Domain service over Trusted Transport Layer Security |
| DoT | DNS-over-TLS |
| DoH | DNS-over-HTTPS |
| ECALL | Enclave Calls |
| OCALL | Outside Calls |
| NS | Name Server |
| RA | Remote Attestation |
| QE | Quoting Enclave |
| IAS | Intel Attestation Service |
| DCAP | Data Center Attestation Primitives |
| mDNS | Multicast DNS |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, D.; Ren, L.; Gu, Z. Enhancing the Privacy of Network Services through Trusted Computing. Appl. Sci. 2022, 12, 9191. https://doi.org/10.3390/app12189191
Zhang D, Ren L, Gu Z. Enhancing the Privacy of Network Services through Trusted Computing. Applied Sciences. 2022; 12(18):9191. https://doi.org/10.3390/app12189191
Chicago/Turabian StyleZhang, Denghui, Lijing Ren, and Zhaoquan Gu. 2022. "Enhancing the Privacy of Network Services through Trusted Computing" Applied Sciences 12, no. 18: 9191. https://doi.org/10.3390/app12189191
APA StyleZhang, D., Ren, L., & Gu, Z. (2022). Enhancing the Privacy of Network Services through Trusted Computing. Applied Sciences, 12(18), 9191. https://doi.org/10.3390/app12189191






