A Behavioral-Based Fingerprint Liveness and Willingness Detection System
Abstract
:1. Introduction
1.1. Contributions
- a novel micro-behavioral-based measurement component in fingerprint-based biometric systems to improve their resistance to sensor-level fingerprint attacks such as constructed and coerced fingerprints.
- a behavior-based fingerprint liveness detection.
- a behavior-based fingerprint willingness detection.
- a classification model that determines if a fingerprint is legitimate.
- a classification model that determines the willingness level of a user.
- a placement of the proposed components in fingerprint-based biometric systems.
- evaluating the potential of the proposed micro-behavioral component in detecting attacks on sensor-level fingerprint systems.
1.2. Scope
2. Literature Review
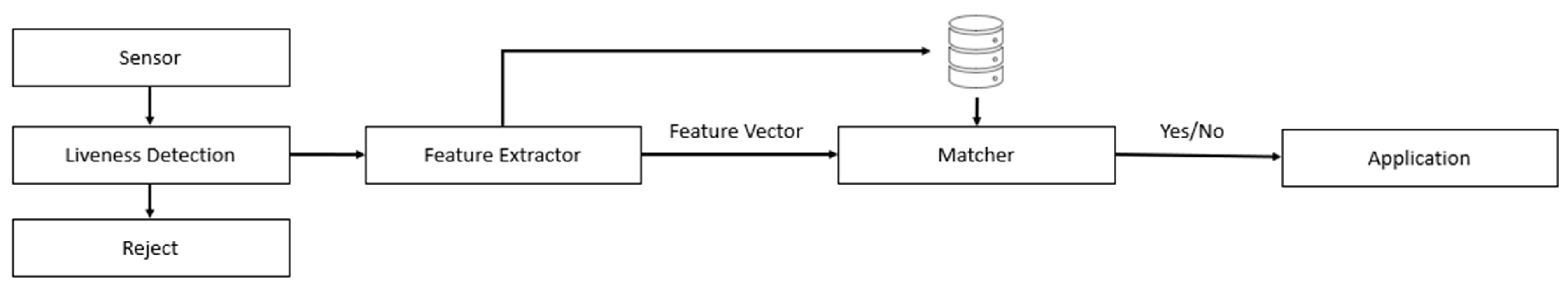
2.1. Liveness Detection as Sensor-Level Attack Mitigation in Fingerprint-Based Systems
2.2. Approaches for Fingerprint-Based Coerced User Attacks Detection on the Sensor Level
3. Hypotheses and Objectives
3.1. Hypotheses
3.2. Objectives
- To design the micro-behavioral fingerprint analysis system
- To test the first supporting hypothesis of whether the micro-behavior of fingertips, when placed on the sensor surface over time, shows a difference between skin and other materials
- To test the second supporting hypothesis of whether the micro-behavior of a fingertip, when placed on the sensor surface over time, shows a difference between the legitimate user placing their fingertip and an attacker using a constructed fingerprint
- To test the second supporting hypothesis of whether the micro-behavior of fingertips, when placed on the sensor surface over time, shows a difference between the legitimate user placing their fingertip and a coerced but legitimate user
- To evaluate the micro-behavioral fingertip analysis system in terms of its capability to improve liveness detection and the detection of the willingness of fingerprint placement
- To test the main hypothesis of whether a micro-behavioral fingertip analysis system in a fingerprint-based biometric system can mitigate attacks on the sensor level with a fake fingerprint or coerced user
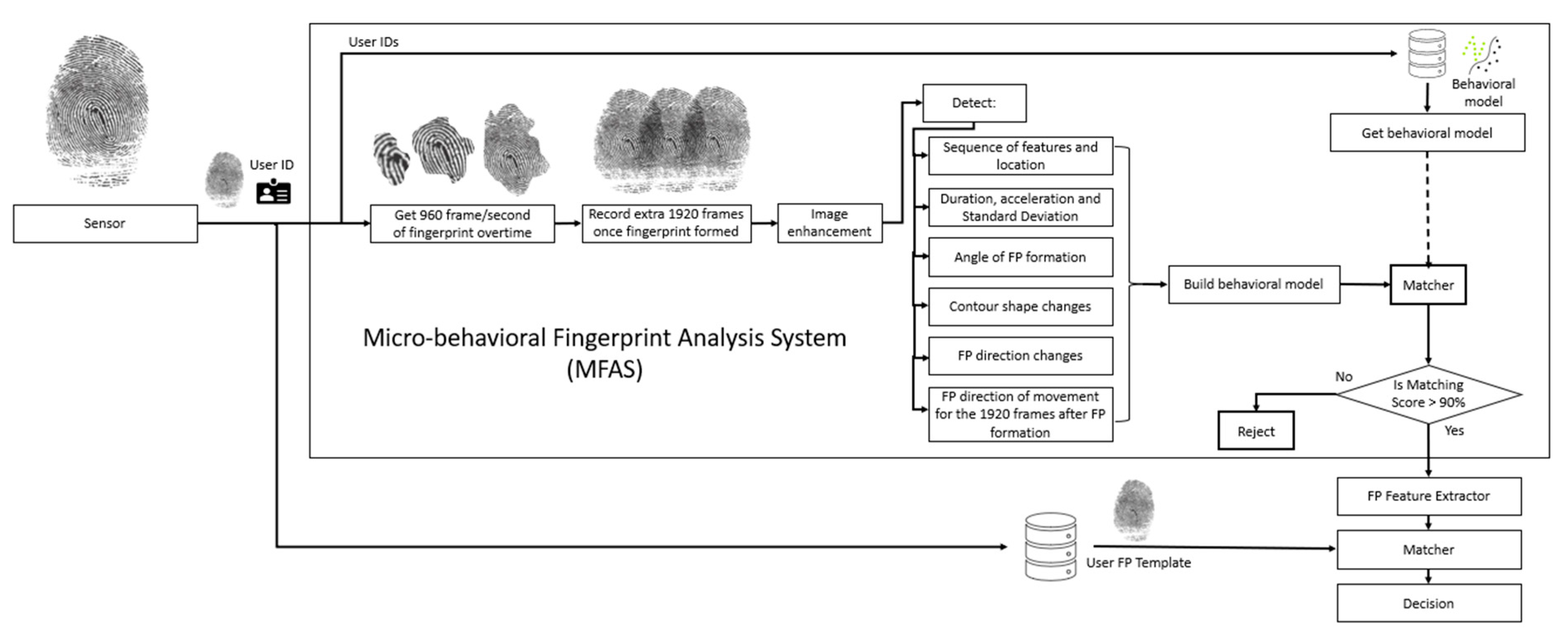
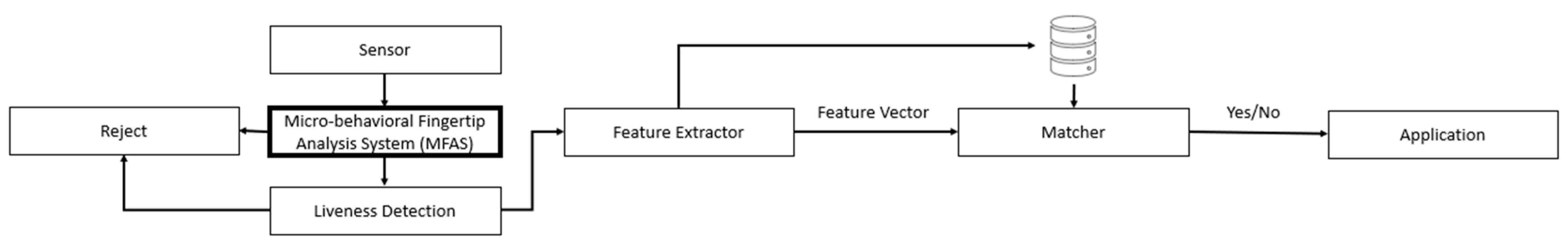
4. Micro-Behavioral Fingerprint Analysis System (MFAS) Design
- Sensor: The MFAS system is composed of a Samsung Note 20 smartphone camera placed under a clear thin glass surface with 330 dots per inch (dpi) resolution and 960 images per second.
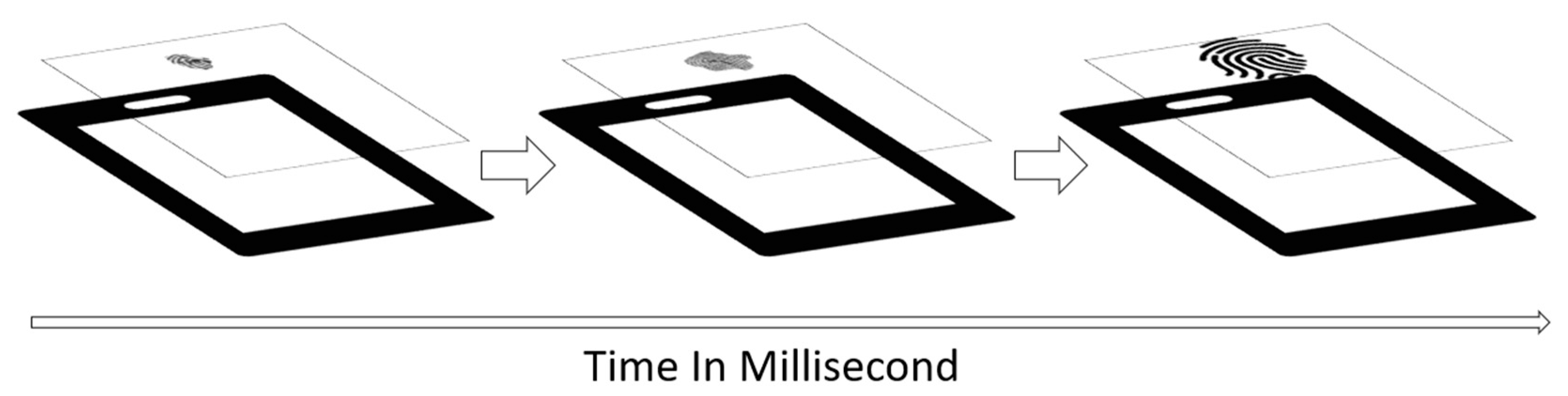
- Fingerprint capture: The capture component is an automated trigger to capture a print once a fingertip is in the scan frame, prior to touching the glass surface. It captures 960 images per second for 6 s. It captures the first touch of the fingertip on the sensor until the fingerprint is fully formed, with no changes, and then keeps on capturing for another 2 s while the fingerprint is stationary.
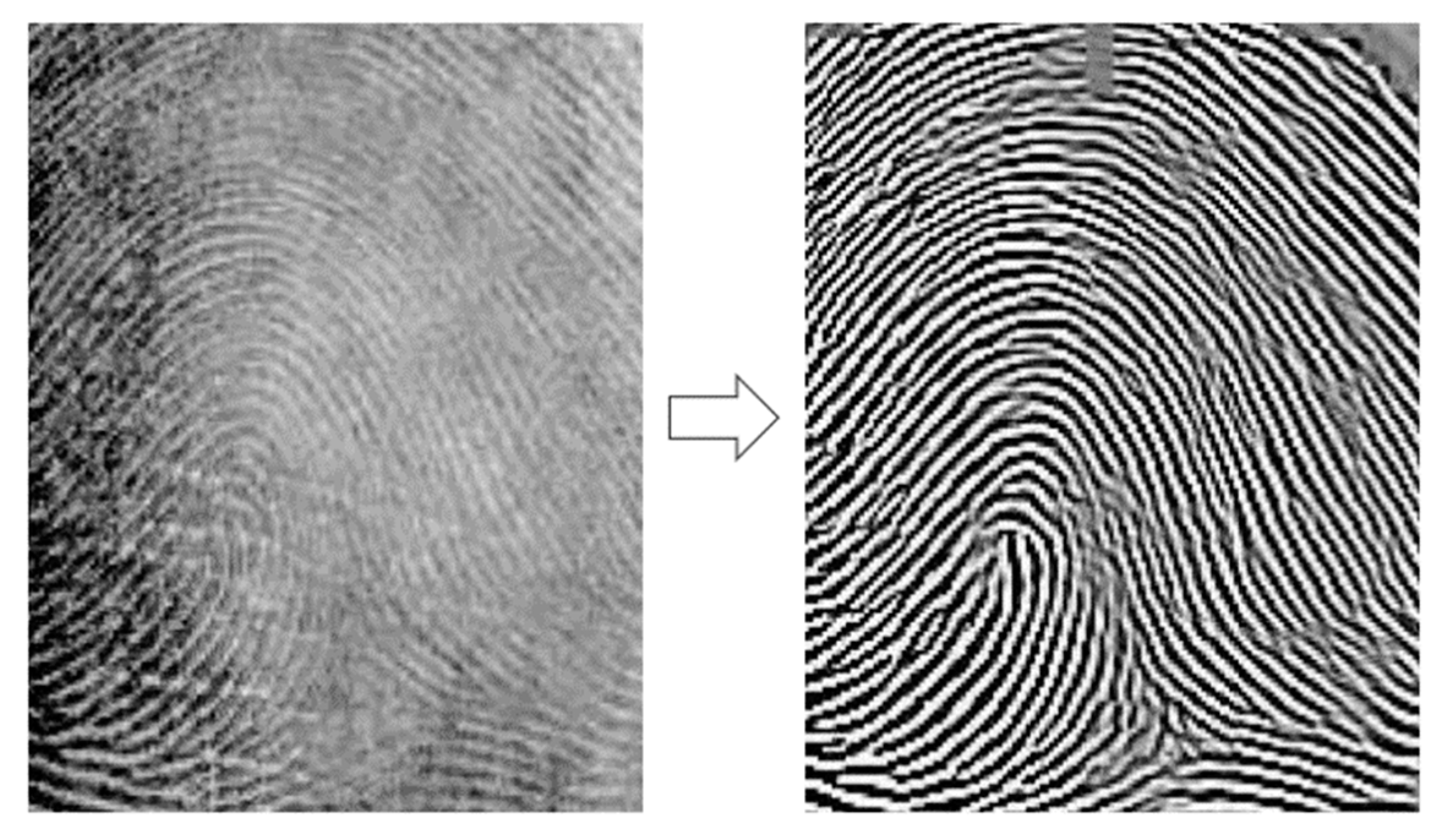
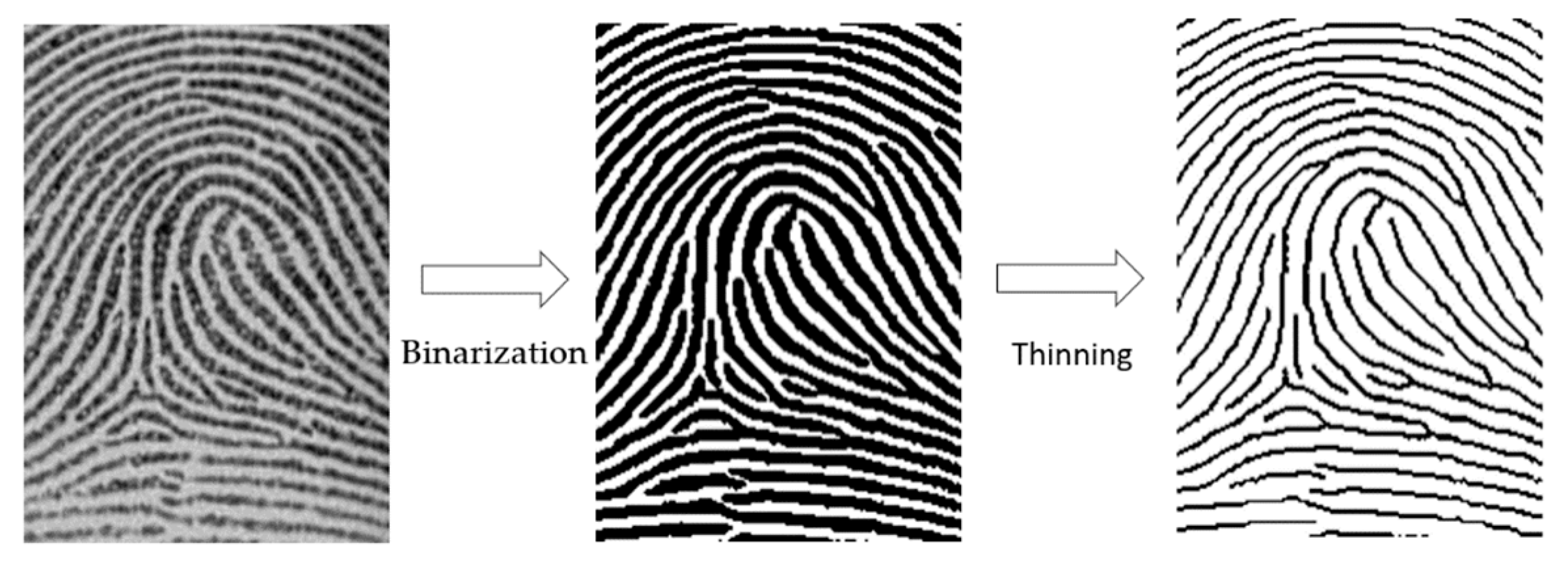
- Image enhancement: The component enhances all captured images by applying smoothing, segmentation, enhancement, digitization, and then thinning to allow the system to detect the minutiae on the fingerprint. This step is important in capturing and analyzing the formation of the ridges over time.
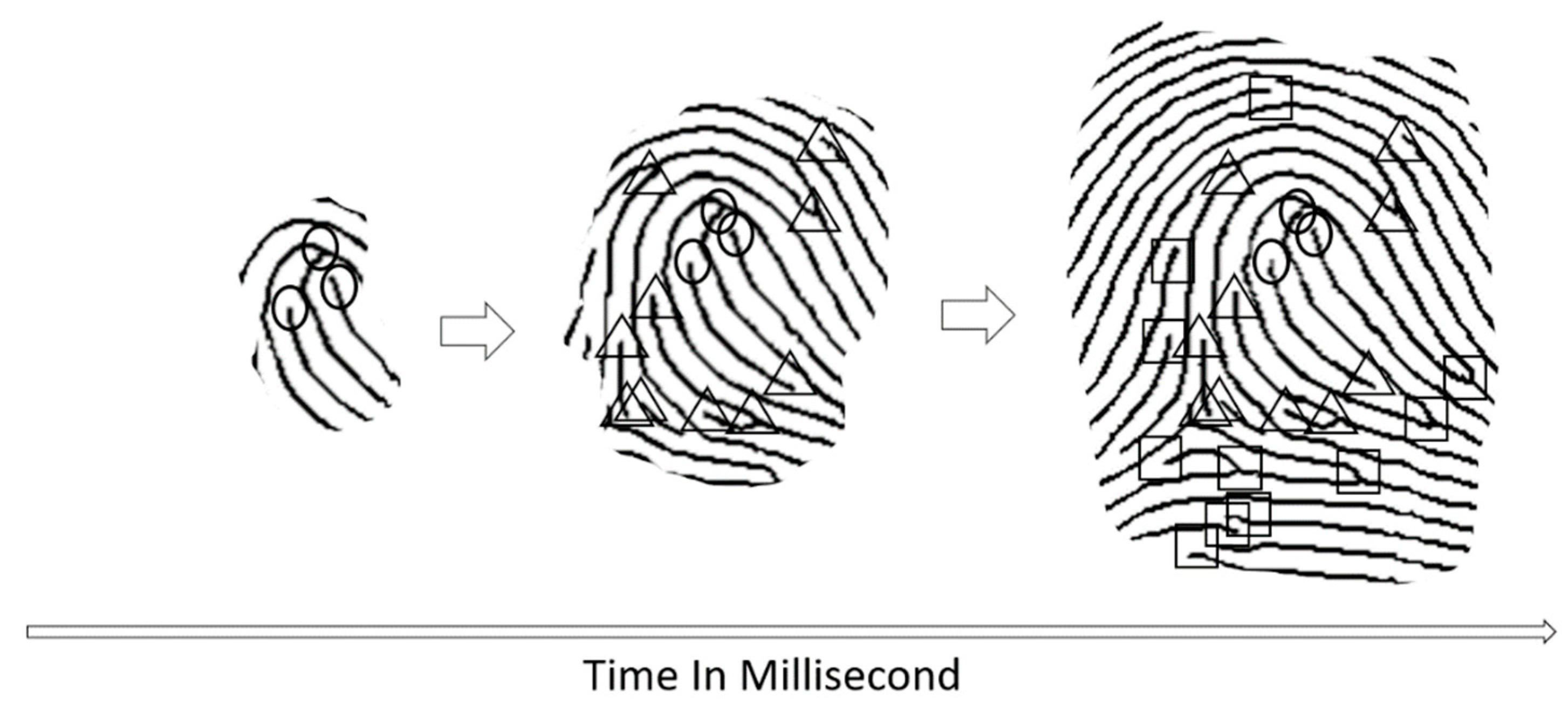
- Micro-behavioral-based Fingerprint Feature Extraction component: It detects six features from the captured images while a fingerprint is being formed on the surface of the sensor:
- The sequence of features appearing over time and the location of each feature
- Duration of fingerprint formation, acceleration between each captured image, and standard deviation
- The angle of the fingerprint formation
- Contour shape changes detection
- Fingerprint direction of changes
- Fingerprint micro-movement while stationary
- 5.
- Micro-behavior model creation: The MFAS then captures the feature vector and creates a one-to-one behavioral matching model for the user.
- 6.
- Matcher: The matcher component is fed the stored behavioral model and the newly created behavioral model and returns a matching score.
- 7.
- Decision maker: The decision-maker component allows the user to pass to the next checkpoint on the fingerprint-based biometric system if the matching score of micro-behavior is above a specific threshold or rejects the sample on a non-matched behavior basis, which could be due to a fake fingerprint or a coerced submission of a fingerprint.
5. Methodology, Experiment Design, and Data Analysis
5.1. Methodology
5.2. Experiment
5.2.1. Experiment Goal
5.2.2. Subjects
5.2.3. Procedure and Discussion
- Enrollment with willingness behavior
- Fake fingerprint used by the legitimate user
- Fake fingerprint used by an attacker
- Unwillingness fingerprint behavior
- The sequence and location of the features appearing over time
- The duration of fingerprint formation, the acceleration between each captured image, and the standard deviation
- The angle of the fingerprint formation
- Contour shape changes detection
- Fingerprint direction of changes
- Fingerprint micro-movement while stationary
5.3. Data Analysis
5.3.1. Data Analysis for a Traditional Fingerprint-Based Biometric System Using the Experimental Data
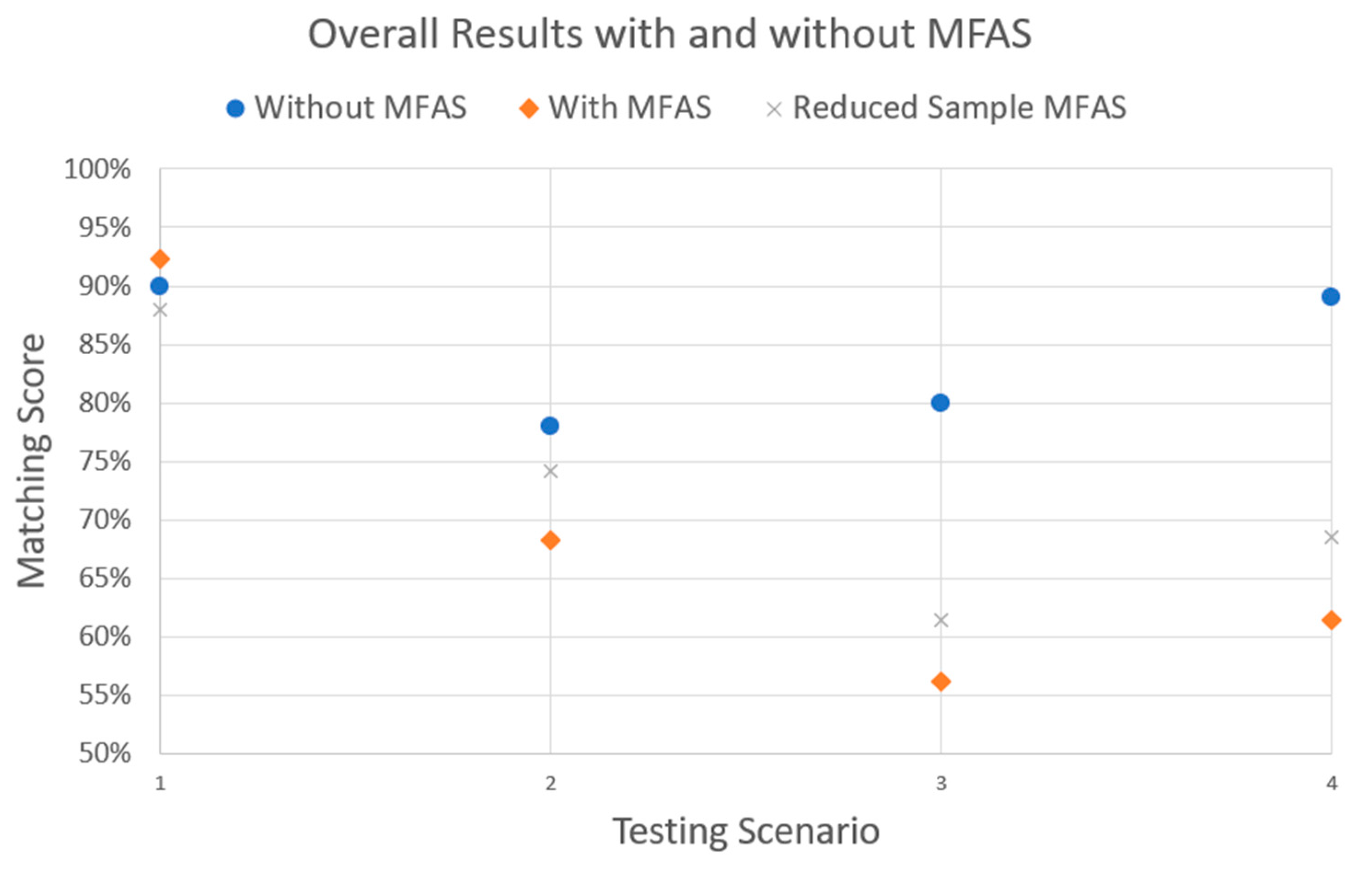
5.3.2. Data Analysis for a Traditional Fingerprint-Based Biometric System Using the Experiment Data with MFAS
- A legitimate user providing their fingerprint.
- A legitimate user providing their Play-Doh fingerprint.
- An attacker providing the legitimate user’s Play-Doh fingerprint.
- A legitimate user unwillingly providing their fingerprint.
- Dry surface, dry skin.
- Dry surface, wet skin.
- Wet surface, dry skin.
- Wet surface, wet skin.
6. Results
MFAS Results
7. Discussions and Limitations
8. Conclusions and Future Work
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| MFAS | Micro-behavioral Fingerprint Analysis System |
| LD | Liveliness Detection |
| CNN | Convolutional Neural Networks |
| TKT | Tangible Key Technique |
| IFA | Intentional False Authentication |
| FMM | Facial Micro-movement |
| TPE | Thermoplastic Elastomers |
| TPU | Thermoplastic Polyurethane |
| DPI | Dots Per Inch |
| AFIS | Automated Fingerprint Identification System |
| OCSVM | One Class Support Vector Machine |
References
- Kim, J.; Teoh, A.B.J. One-factor Cancellable Biometrics based on Indexing-First-Order Hashing for Fingerprint Authentication. In Proceedings of the 24th International Conference on Pattern Recognition (ICPR), Beijing, China, 20–24 August 2018; pp. 3108–3113. [Google Scholar] [CrossRef]
- Syarif, M.A.; Nen, L.M.; Goh, A.; Win, L.K.; Ng, K.S.; Tiong, L.C.O. Challenge response interaction for biometric liveness establishment and template protection. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 698–701. [Google Scholar] [CrossRef]
- Cappelli, R.; Maio, D.; Lumini, A.; Maltoni, D. Fingerprint Image Reconstruction from Standard Templates. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 1489–1503. [Google Scholar] [CrossRef] [PubMed]
- Memon, S.; Manivannan, N.; Balachandran, W. Active pore detection for liveness in fingerprint identification system. In Proceedings of the 2011 19th Telecommunications Forum (TELFOR), Belgrade, Serbia, 22–24 November 2011; pp. 619–622. [Google Scholar] [CrossRef]
- Johnson, P.; Schuckers, S. Fingerprint pore characteristics for liveness detection. In Proceedings of the 2014 International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 10–12 September 2014; pp. 1–8. [Google Scholar]
- Lu, M.; Chen, Z.; Sheng, W. A Pore-Based Method for Fingerprint Liveness Detection. In Proceedings of the 2015 International Conference on Computer Science and Applications (CSA), Wuhan, China, 20–22 November 2015; pp. 77–81. [Google Scholar] [CrossRef]
- Marcialis, G.L.; Roli, F.; Tidu, A. Analysis of Fingerprint Pores for Vitality Detection. In Proceedings of the 2010 20th International Conference on Pattern Recognition, Istanbul, Turkey, 23–26 August 2010; pp. 1289–1292. [Google Scholar] [CrossRef]
- Nuraisha, S.; Shidik, G.F. Evaluation of Normalization in Fake Fingerprint Detection with Heterogeneous Sensor. In Proceedings of the 2018 International Seminar on Application for Technology of Information and Communication, Semarang, Indonesia, 21–22 September 2018; pp. 83–86. [Google Scholar] [CrossRef]
- Baek, Y. The fake fingerprint detection system using a novel color distribution. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016; pp. 1111–1113. [Google Scholar] [CrossRef]
- Matthew, P.; Anderson, M. Developing coercion detection solutions for biometrie security. In Proceedings of the 2016 SAI Computing Conference (SAI), London, UK, 13–15 July 2016; pp. 1123–1130. [Google Scholar] [CrossRef]
- Li, Q.; Chan, P.P.K. Fingerprint liveness detection based on binarized statistical image feature with sampling from Gaussian distribution. In Proceedings of the 2014 International Conference on Wavelet Analysis and Pattern Recognition, Lanzhou, China, 13–16 July 2014; pp. 13–17. [Google Scholar] [CrossRef]
- Bhanarkar, A.; Doshi, P.; Abhyankar, A.; Bang, A. Joint time frequency analysis based liveness fingerprint detection. In Proceedings of the 2013 IEEE Second International Conference on Image Information Processing (ICIIP-2013), Shimla, India, 9–11 December 2013; pp. 166–169. [Google Scholar] [CrossRef]
- Kumar, A.K.T.; Vinayakumar, R.; Variyar, S.V.V.; Sowmya, V.; Soman, K.P. Convolutional Neural Networks for Fingerprint Liveness Detection System. In Proceedings of the 2019 International Conference on Intelligent Computing and Control Systems (ICCS), Madurai, India, 15–17 May 2019; pp. 243–246. [Google Scholar] [CrossRef]
- Lazimul, L.T.P.; Binoy, D.L. Fingerprint liveness detection using convolutional neural network and fingerprint image enhancement. In Proceedings of the 2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), Chennai, India, 1–2 August 2017; pp. 731–735. [Google Scholar] [CrossRef]
- Zhang, Y.; Shi, D.; Zhan, X.; Cao, D.; Zhu, K.; Li, Z. Slim-ResCNN: A Deep Residual Convolutional Neural Network for Fingerprint Liveness Detection. IEEE Access 2019, 7, 91476–91487. [Google Scholar] [CrossRef]
- Nogueira, R.F.; Lotufo, R.D.; Machado, R.C. Evaluating software-based fingerprint liveness detection using Convolutional Networks and Local Binary Patterns. In Proceedings of the 2014 IEEE Workshop on Biometric Measurements and Systems for Security and Medical Applications (BIOMS), Rome, Italy, 17 October 2014; pp. 22–29. [Google Scholar] [CrossRef] [Green Version]
- Jian, W.; Zhou, Y.; Liu, H. Densely Connected Convolutional Network Optimized by Genetic Algorithm for Fingerprint Liveness Detection. IEEE Access 2021, 9, 2229–2243. [Google Scholar] [CrossRef]
- Nogueira, R.F.; Lotufo, R.D.; Machado, R.C. Fingerprint Liveness Detection Using Convolutional Neural Networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1206–1213. [Google Scholar] [CrossRef]
- Jung, H.Y.; Heo, Y.S.; Lee, S. Fingerprint Liveness Detection by a Template-Probe Convolutional Neural Network. IEEE Access 2019, 7, 118986–118993. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, C.; Pan, S.; Li, Z.; Xu, Y.; Qiu, H. A Score-Level Fusion of Fingerprint Matching with Fingerprint Liveness Detection. IEEE Access 2020, 8, 183391–183400. [Google Scholar] [CrossRef]
- Komeili, M.; Armanfard, N.; Hatzinakos, D. Liveness Detection and Automatic Template Updating Using Fusion of ECG and Fingerprint. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1810–1822. [Google Scholar] [CrossRef]
- Jian, W.; Zhou, Y.; Liu, H. 2-layer Parallel SVM Network Based on Aggregated Local Descriptors for Fingerprint Liveness Detection. In Proceedings of the 2021 13th International Conference on Communication Software and Networks (ICCSN), Chongqing, China, 4–7 June 2021; pp. 296–304. [Google Scholar] [CrossRef]
- Ibrahim, Y.; Mu’Azu, M.B.; Adedokun, A.E.; Sha’Aban, Y.A. A performance analysis of logistic regression and support vector machine classifiers for spoof fingerprint detection. In Proceedings of the 2017 IEEE 3rd International Conference on Electro-Technology for National Development (NIGERCON), Owerri, Nigeria, 7–10 November 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Sayette, M.A.; Cohn, J.F.; Wertz, J.M.; Perrott, M.a.; Parrott, D.J. A psychometric evaluation of the facial action coding system for assessing spontaneous expression. J. Nonverbal Behav. 2001, 25, 167–185. [Google Scholar] [CrossRef]
- Küsters, R.; Truderung, T.; Vogt, A. Verifiability, Privacy, and Coercion-Resistance: New Insights from a Case Study. In Proceedings of the 2011 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 22–25 May 2011; pp. 538–553. [Google Scholar] [CrossRef] [Green Version]
- Priesnitz, J.; Rathgeb, C.; Buchmann, N.; Busch, C.; Margraf, M. An overview of touchless 2D fingerprint recognition. J. Image Video Proc. 2021, 2021, 8. [Google Scholar] [CrossRef]
- Davis, M.E.; Dyor, M.G.; Gerrity, D.A.; Huang, X.; Hyde, R.A.; Levien, R.A.; Lord, R.T.; Lord, R.W.; Malamud, M.A.; Myhrvold, N.P.; et al. Tegreene. RPX Corp. U.S. Patent 8,713,704, 19 April 2014. [Google Scholar]
- Deutschmann, I.; Costigan, N.; Libell, T.; Nordström, P. Behaviometrics AB. U.S. Patent 9,531,710, 27 December 2016. [Google Scholar]
- Fei, J.; Xia, Z.; Yu, P.; Xiao, F. Adversarial attacks on fingerprint liveness detection. J. Image Video Proc. 2020, 2020, 1. [Google Scholar] [CrossRef] [Green Version]
- Borza, D.; Itu, R.; Danescu, R. Real-time micro-expression detection from high speed cameras. In Proceedings of the 2017 13th IEEE International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 7–9 September 2017; pp. 357–361. [Google Scholar] [CrossRef]
- D’Angelo, L.T.; Neuhaeuser, J.; Zhao, Y.; Lueth, T.C. SIMPLE-Use—Sensor Set for Wearable Movement and Interaction Research. IEEE Sens. J. 2014, 14, 1207–1215. [Google Scholar] [CrossRef]
- Jia, J.; Cai, L.; Zhang, K.; Chen, D. A new approach to fake finger detection based on skin elasticity analysis. In International Conference on Biometrics; Springer: Berlin/Heidelberg, Germany, 2007; pp. 309–318. [Google Scholar]
- Baldisserra, D.; Franco, A.; Maio, D.; Maltoni, D. Fake Fingerprint Detection by Odor Analysis. In Advances in Biometrics; Zhang, D., Jain, A.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3832, pp. 265–272. [Google Scholar]
- Antonelli, A.; Cappelli, R.; Maio, D.; Maltoni, D. A New Approach to Fake Finger Detection Based on Skin Distortion. In Advances in Biometrics; Zhang, D., Jain, A.K., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3832, pp. 221–228. [Google Scholar]
- Cappelli, R.; Maio, D.; Maltoni, D. Modeling Plastic Distortion in Fingerprint Images. In Lecture Notes in Computer Science; Singh, S., Murshed, N., Kropatsch, W.G., Eds.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2013, pp. 369–376. [Google Scholar]






| Method | Accuracy | Ref. |
|---|---|---|
| Binarized statistical image feature with sampling from Gaussian distribution | 91% | [11] |
| Joint time frequency analysis | 100% | [12] |
| CNN | 95% | [13] |
| CNN-Enhanced | 98% | [14] |
| Slim-ResCNN | 95.25% | [15] |
| CNN | 95.2% | [16] |
| Density-connected CNN | 98.22% | [17] |
| CNN | 95.5% | [18] |
| Template-probe CNN | 97.24% | [19] |
| Score-level fusion | 96.88% | [20] |
| ECG Fusion | 97.4% | [21] |
| 2-Layer Parallel SVM | 95.32% | [22] |
| SVM | 100% | [23] |
| Trial | Condition | |||
|---|---|---|---|---|
| Dry Skin Dry Surface | Dry Skin Wet Surface | Wet Skin Dry Surface | Wet Skin Wet Surface | |
| Enrollment with willingness behavior | 24 | 24 | 24 | 24 |
| Fake fingerprint used by the legitimate user | 24 | 24 | 24 | 24 |
| Fake fingerprint used by an attacker | 24 | 24 | 24 | 24 |
| Unwillingness fingerprint behavior | 17 | 17 | 17 | 17 |
| Total trials | 89 | 89 | 89 | 89 |
| Trial | Condition | Average | ||||
|---|---|---|---|---|---|---|
| Dry Skin Dry Surface | Dry Skin Wet Surface | Wet Skin Dry Surface | Wet Skin Wet Surface | All | Optimal (One Wet) | |
| Enrollment with willingness behavior | 79% | 100% | 100% | 83% | 90% | 100% |
| Fake fingerprint used by the legitimate user | 61% | 96% | 91% | 64% | 78% | 93.5% |
| Fake fingerprint used by an attacker | 64% | 94% | 97% | 65% | 80% | 95.5% |
| Unwillingness fingerprint behavior | 77% | 100% | 100% | 81% | 89% | 100% |
| Trial | Condition | Average | ||||
|---|---|---|---|---|---|---|
| Dry Skin Dry Surface | Dry Skin Wet Surface | Wet Skin Dry Surface | Wet Skin Wet Surface | All | Optimal (One Wet) | |
| Enrollment with willingness behavior | 88% | 96% | 94% | 91% | 92.25% | 95% |
| Fake fingerprint used by a legitimate user | 68% | 72% | 71% | 62% | 68.25% | 71.5% |
| Fake fingerprint used by an attacker | 52% | 57% | 61% | 55% | 56.25% | 59% |
| Unwillingness fingerprint behavior | 59% | 64% | 67% | 56% | 61.5% | 65.5% |
| Trial | Condition | Average | ||||
|---|---|---|---|---|---|---|
| Dry Skin Dry Surface | Dry Skin Wet Surface | Wet Skin Dry Surface | Wet Skin Wet Surface | All | Optimal (One Wet) | |
| Enrollment with willingness behavior | 83% | 90% | 92% | 87% | 88% | 91% |
| Fake fingerprint used by the legitimate user | 73% | 78% | 77% | 69% | 74.25% | 77.5% |
| Fake fingerprint used by an attacker | 59% | 62% | 68% | 57% | 61.5% | 65% |
| Unwillingness fingerprint behavior | 64% | 72% | 76% | 62% | 68.5% | 74% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almehmadi, A. A Behavioral-Based Fingerprint Liveness and Willingness Detection System. Appl. Sci. 2022, 12, 11460. https://doi.org/10.3390/app122211460
Almehmadi A. A Behavioral-Based Fingerprint Liveness and Willingness Detection System. Applied Sciences. 2022; 12(22):11460. https://doi.org/10.3390/app122211460
Chicago/Turabian StyleAlmehmadi, Abdulaziz. 2022. "A Behavioral-Based Fingerprint Liveness and Willingness Detection System" Applied Sciences 12, no. 22: 11460. https://doi.org/10.3390/app122211460
APA StyleAlmehmadi, A. (2022). A Behavioral-Based Fingerprint Liveness and Willingness Detection System. Applied Sciences, 12(22), 11460. https://doi.org/10.3390/app122211460







