1. Introduction
With the emergence of digital technology, the world is continuously evolving and rapidly changing. Today, Internet communication has bridged the gap between people. Communication over the Internet ensures an instant connection between people on different sides of the world. Therefore, many cloud service companies offer a cloud-based platform, application, or storage services that allow people to share photos, videos, messages, locations, etc. Among these services, photo sharing and tagging friends in pictures have always been the most popular features of social networks. People like to share or post photos of themselves, family, friends, their life or special activities on their social networks. The photo sharing market is growing at a good clip, and hence we have recently seen an explosion of services that specifically revolve around sharing photos.
Visual cryptography [
1,
2,
3,
4,
5,
6] and information hiding [
7,
8,
9,
10,
11,
12,
13,
14,
15] are proposed for image privacy protection. Social networks also provide some management to let image owners control photo permissions. Even though the account access permission limits only followers or who in the same group can see those photos, the photos could also be leaked by careless transmissions. We note that private information may become publicly available through illegal sources. It may threaten portrait rights and the personal privacy of people who also appeared in the same photo. The traditional mechanisms implement privacy protection only on the whole photo but not special regions and cannot set different privacy permission in one image. We should consider the different needs of protected privacy in different cases. Consequently, we need to develop a new mechanism to do privacy protection separately in a single photo on cloud-based services.
Nowadays, cloud computing is gaining popularity and confidence. Cloud computing has become a convenient and efficient way for companies to store, manage, and access data through the Internet instead of keeping the data on a local drive. Apart from being cost-effective, cloud computing provides elasticity and agility. Corporate cloud computing grows rapidly by more than 35% a year and reached
$55.5 billion in Q4 of 2020 [
16]. However, as the popularity of cloud computing grows, so will the potential security risks. We cannot completely trust cloud service providers (CSP) due to the fact that the success of accessing cloud services relies on network and authentication. Crashed network and unauthorized access disrupt the cloud-based services. Although CSPs are regulated by stringent regulations, assuming that the data owner and CSPs are in the same trusted domain may not be true since the CSPs may access sensitive information without authorization. Lapse in security risk management could lead to physical or financial harm.
Take celebrity photo leaks in 2014 [
17], for example. Almost 500 private pictures of various celebrities were posted on the imageboard website, and later disseminated by other people on social networks. These photos were leaked via the online storage provided by Apple’s cloud services suite iCloud for automatically backing up photos from iOS devices [
17]. Apple reported that the victims’ account information was cracked using brute-force attack in the Find My iPhone service which allowed hackers to make unlimited tries to guess victims’ passwords. Many celebrities pursued legal actions and claimed the leak to be a massive invasion of their privacy. It not only violated users’ privacy rights but damaged the company’s reputation.
Moreover, there were two serious data leaks caused by misconfigured Amazon Simple Storage Service (Amazon S3) [
18]. One was found by Noah Rotem and Ran Locar [
19]. The information of 1000 consultants and consulting firms was breached. The other data leak involved UK-based Fresh Film Productions, which exposed the sensitive data of crews, actors and collaborations [
20]. Amazon S3 is a public object storage service that provides management features so that you can configure access to your data to meet your specific business requirements. However, the two leaks indicated that the owners did not define clearly and make the proper settings.
CSP may also have uncovered flaws. In 2020, an authentication problem on Google cloud platform (GCP) shell was found. It could make hackers gain root access to reconfigure any containers [
21]. In 2021, Microsoft warned thousands of cloud computing customers that their Microsoft Azure Cosmos DB may have been exposed to intruders [
22]. The research team Wiz found that the customers’ primary keys were long-lived and allowed full permission access to customer data [
23]. As a result of these reports, we cannot rely on CSP completely.
CSP is semi-reliable; as a result, it is a challenge to accomplish a different permission of privacy protection in a single image. Almuflih et al. [
24] proposed a key exchange method by using identity-based encryption in a multipath TCP environment. They also presented the feature-map-based detection for adversarial attacks [
25]. Sultana [
26] presented a privacy-preserved face image recognition system on MSB encrypted face images. Kumari et al. [
27] proposed a secure biometrics-based multi-cloud-server authentication scheme. It used cloud storage and computing power while it did not let the cloud server know the content. They used an elliptic curve cryptosystem (ECC) to build keys among users, registration authorities and cloud servers, and proposed a biometric-based authentication system to make authentication much stricter. Registration authorities authenticate not only users but the cloud servers to make the whole process more secure.
In this paper, we present a privacy-preserved method that supports different access rights in a single image for privacy protection based on the difficulty of solving factoring problems and discrete logarithm problems. We use an access policy to decide who can decrypt the cipher blocks of the image to satisfy every privacy requirement in the original image. The privacy-preserved images with the access policy and authentication information are uploaded to the cloud server. When exploring the image, users follow the authentication information to confirm the blocks that are accessible in their permission to get a decryption key of the blocks to obtain the original image. With the designed strategy, the image management is executed by cloud servers such that cloud servers are not aware of the private information contained in the protected image.
To make this paper self-contained, in
Section 2 we introduce the basic concepts of RSA public-key cryptography [
28] and ElGamal public-key cryptography [
29].
Section 3 explains the proposed scheme consisting of image protection method and image management method. Experimental results and their security analysis appear in
Section 4. We also demonstrate how to perform different access rights in a single image for privacy protection. Finally, the paper is concluded in
Section 5.
3. Proposed Scheme
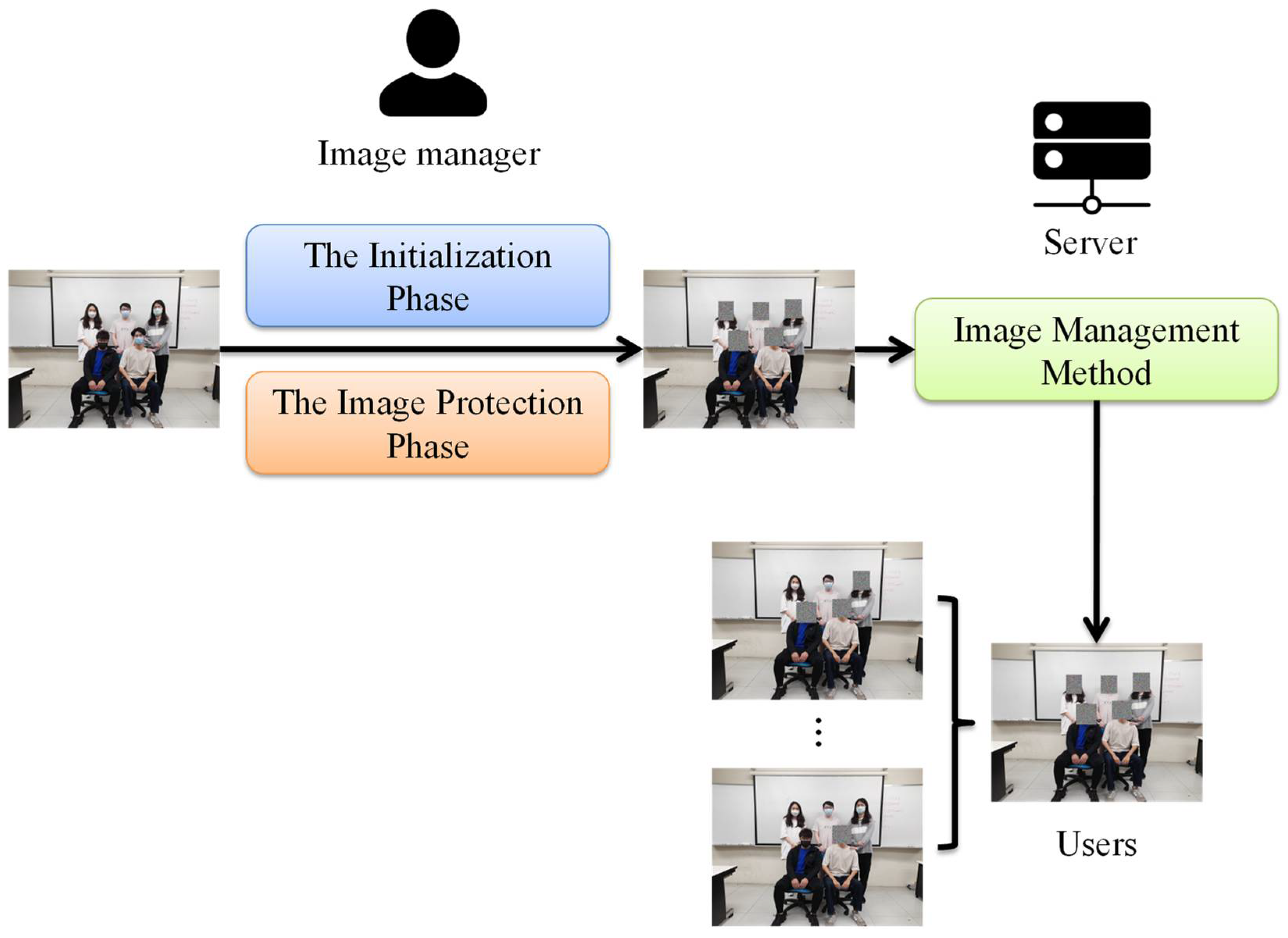
We propose a privacy-preserved scheme that supports different privacy-preserved access rights in a single image based on the difficulty of solving the factorization problem and the discrete logarithm problem. As shown in
Figure 1, the image manager can formulate the access policy for specific users in the initialization phase. According to the access policy, specific users can read the original part of authorized blocks in a single image. To prevent private content from being exposed to unauthorized access, the image manager first encrypts the original image in the image protection phase before sending it to the cloud server. The protected images with the access policy will be uploaded to the cloud server. When a user performs image retrieval, the cloud server will provide the user with corresponding authorized images and authentication information according to the access policy. In the image management method, the authorized user can compute the decrypted keys to recover the original content of image blocks. The proposed schemes consisting of an image protection method and an image management method are described as follows.
3.1. Image Protection Method
The image protection method supporting different access rights in a single image for privacy protection is mainly composed of the initialization phase and image protection phase. In the initialization phase, the image manager can configure system parameters and generate keys for every user according to the access policy. In the image protection phase, the image in need of protection is set access rights on blocks to generate the corresponding encrypted image and authentication information. The initialization phase and the image protection phase are presented in the following.
3.1.1. The Initialization Phase
Based on the users’ intention, the image manager institutes the access policy T which comprises α disjoint authorized classes Cj for j = 1, 2, …, α. Each user Ui should belong to a single authorized class Cj, and each authorized class may contain one or several users. The access policy defines Cw ≤ Cr if Cr can access the data of Cw.
First, the image manager chooses two prime numbers
p and
q and
g which is the primitive root modulo
n, where
n =
p ×
q. Then, the image manager executes Key Generation Algorithm (Algorithm 1). After
Cj generates a public key
ej, an encrypted key
SKj, a derivative key
DKj and partial authorized information
PTj, the image manager sends
PTj= {
Cr |
Cr ≤
Cj},
DKj, and {
er |
Cr ≤
Cj and
Cr ∈ {
C1,
C2,…,
Cα}} to user
Ui ∈
Cj through a secure channel. The image manager keeps
SKj secret and sends
T and
ej to the cloud server. The initialization phase is given in Key Generation Algorithm (Algorithm 1).
| Algorithm 1 Key Generation Algorithm. |
| Input: T |
| Output: ej, SKj, DKj, and PTj for j = 1, 2, …, α |
- Step 1.
For j = 1, 2, …, α, choose ej, where gcd(ej, ϕ(n)) = 1 and er ≠ ew when r ≠ w; - Step 2.
For j = 1, 2, …, α, compute dj such that dj × ej ≡ 1 (mod ϕ(n)); - Step 3.
For j = 1, 2, …, α, compute SKj = ; - Step 4.
For j = 1, 2, …, α, compute DKj = ; - Step 5.
According to T, generate PTj = {Cr |Cr < Cj} for j = 1, 2, …, α.
|
3.1.2. The Image Protection Phase
In order to protect data privacy, the privacy-preserved image should be processed before sending to the cloud server. The image manager executes Image Protection Algorithm (Algorithm 2) to generate an encrypted image
EI, image map
IM, authentication information
AI, and the number of authorized classes
δ. Then,
EI,
IM,
AI and
δ are uploaded to the cloud server. The flowchart of the Image Protection Algorithm (Algorithm 2) is shown in
Figure 2.
Image Protection Algorithm (Algorithm 2) consists of Image Map and Authentication Information Generation Algorithm (Algorithm 3), Coding Algorithm (Algorithm 4), and Image Encryption Algorithm Algorithm (Algorithm 5). First of all, the image manager defines the mapping between pixels and authorized classes. Image Map and Authentication Information Generation Algorithm (Algorithm 3) and Coding Algorithm (Algorithm 4) are then performed to compute the number of total authorized classes
δ to generate the image map
IM and the authentication information
AI = {(
C1′,
Code1), (
C2′,
Code2), …, (
Cδ′,
Codeδ)}. The image map
IM, authentication information
AI, and the number of authorized classes
δ are used to execute Image Encryption Algorithm (Algorithm 5) to obtain the encrypted image
EI. Note that simple exclusive-or operation or symmetric encryption can be used for encryption in Image Encryption Algorithm (Algorithm 5). Using symmetric encryption for encryption is better due to the high-level security, however the fixed-length groups of bits are required in block cipher algorithms, such as AES and 3DES.
| Algorithm 2 Image Protection Algorithm. |
| Input: An original image and SKj for j = 1, 2, …, α |
| Output: The encrypted image EI, image map IM, authentication information AI, the number δ of the involved access rights |
- Step 1.
Define the protection pixels of the original image and the corresponding classes; - Step 2.
Execute Image Map and Authentication Information Generation Algorithm (Algorithm 3) with a protection-pixel-defined image and the corresponding classes as input to get image map IM, authentication information AI, and the number δ of the involved access rights, where AI = {(C1′, Code1), (C2′, Code2), …, (Cδ′, Codeδ)}; - Step 3.
Execute Image Encryption Algorithm (Algorithm 5) with the original image, IM, AI = {(C1′, Code1), (C2′, Code2), …, (Cδ′, Codeδ)}, and SKj′ of Cj′ for j = 1, 2, ..., δ as input to get the encrypted image EI.
|
| Algorithm 3 Image Map and Authentication Information Generation Algorithm. |
| Input: A protection-pixel-defined image and the corresponding classes |
| Output: Image map IM, authentication information AI, and the number δ of the involved access rights |
- Step 1.
Determine the number δ of the involved classes Cj′’s, where Cj′ ∈ {C1, C2, …, Cα}; - Step 2.
Compute φ = ; - Step 3.
Execute Coding Algorithm (Algorithm 4) to get (Cj′, Codej) for j = 1, 2, ..., δ; - Step 4.
Set AI = {(C1′, Code1), (C2′, Code2), …, (Cδ′, Codeδ)}; - Step 5.
With AI, read the protection-pixel-defined image pixel by pixel from left to right and from top to down, and generate a tile of φ bits in IM with the code of the related class for each read pixel. If the pixel does not need to be protected, the code for the tile will be 00...02 of φ bits.
|
| Algorithm 4 Coding Algorithm. |
| Input: φ and δ involved classes Cj′ for j = 1, 2, ..., δ |
| Output: (Cj′, Codej) for j = 1, 2, ..., δ |
| For j = 1, 2, ..., δ, generate the code Codej of φ bits for Cj′ by setting Codej = j2, where j2 denotes the binary representation of j. |
| Algorithm 5 Image Encryption Algorithm. |
| Input: The original image, IM, AI = {(C1′, Code1), (C2′, Code2), …, (Cδ′, Codeδ)}, and SKj′ of Cj′ for j = 1, 2, ..., δ |
| Output: The encrypted image EI |
- Step 1.
According to tiles in IM with Codej, get the corresponding pixels in the original image to form the bit string Plaintextj for j = 1, 2, ..., δ; - Step 2.
For j = 1, 2, ..., δ, encrypt Plaintextj with SKj′ to get Ciphertextj and replace Plaintextj in the original image with Ciphertextj; - Step 3.
Obtain EI.
|
3.2. Image Management Method
The cloud server can provide privacy-preserved image retrieval without knowing the data privacy. The user Ui (Ui ∈ Cw) sends a request to the cloud server to ask to see an encrypted image EI. The cloud server can determine whether the user has rights to access this image or not according to the access policy T. The user Ui has the access rights if Cj′ < Cw in T and then the cloud server will send EI, IM, AI and δ to Ui. Since the image manager sends PTj= {Cr |Cr ≤ Cj}, DKj, and {er |Cr ≤ Cj and Cr ∈ {C1, C2,…, Cα}} to user Ui ∈ Cj through a secure channel in the initialization phase of the image protection method, Ui can execute the following steps to recover the original content of accessible blocks.
- Step 1.
For each accessible Cj′ in EI, Ui computes SKj′ = according to PTw;
- Step 2.
For each accessible Cj′ in EI, Ui uses Codej and IM to find the region of the authorized pixels in EI;
- Step 3.
For the region of the authorized pixels of Cj′, Ui uses SKj′ to decrypt the encrypted pixels to recover the original content.
5. Conclusions
In this paper, we proposed a privacy protection scheme that supports different access rights in a single image based on the difficulty of solving factoring problems and discrete logarithm problems. The image manager can institute a different access policy in a single image for specific users. The access policy specifies who has access rights to read the original content of authorized regions. In the image protection method, the image in need of protection is set access rights on blocks to generate the corresponding encrypted image and authentication information. According to the access policy, we used different public keys and private keys built on RSA [
28] to generate secret keys and derivative keys followed by ElGamal [
29] to encrypt or decrypt the image blocks with AES. Moreover, the AES encryption and decryption are fast.
The encrypted images with the access policy will be uploaded to the cloud server. In the image management method, according to the access policy, the cloud server can determine whether the user has rights to access this image or not, without knowing the privacy information of images. The authorized users can read the original content of encrypted regions according to their access rights. The main benefit is that the proposed method allows users to securely share images across CSPs in semi-trusted cloud environments. Additionally, our method provides flexible access control in a single image for specific users making CSPs authenticate the image without accessing the privacy-preserved content. Performance evaluation results show that our method has no significant computation cost for CSPs and users. Security analysis shows that our image protection method based on the difficulty of solving factoring problems and discrete logarithm problems is secure, and our access control method can resist unauthorized access. Therefore, the proposed scheme not only provides image protection with different privacy-preserved access rights but also prevents the cloud server from leaking private information from the image.