Timed Colored Petri Net-Based Event Generators for Web Systems Simulation
Abstract
1. Introduction
2. Related Work
2.1. Early CPN Models of Generators
2.2. Early QPN Models of Generators
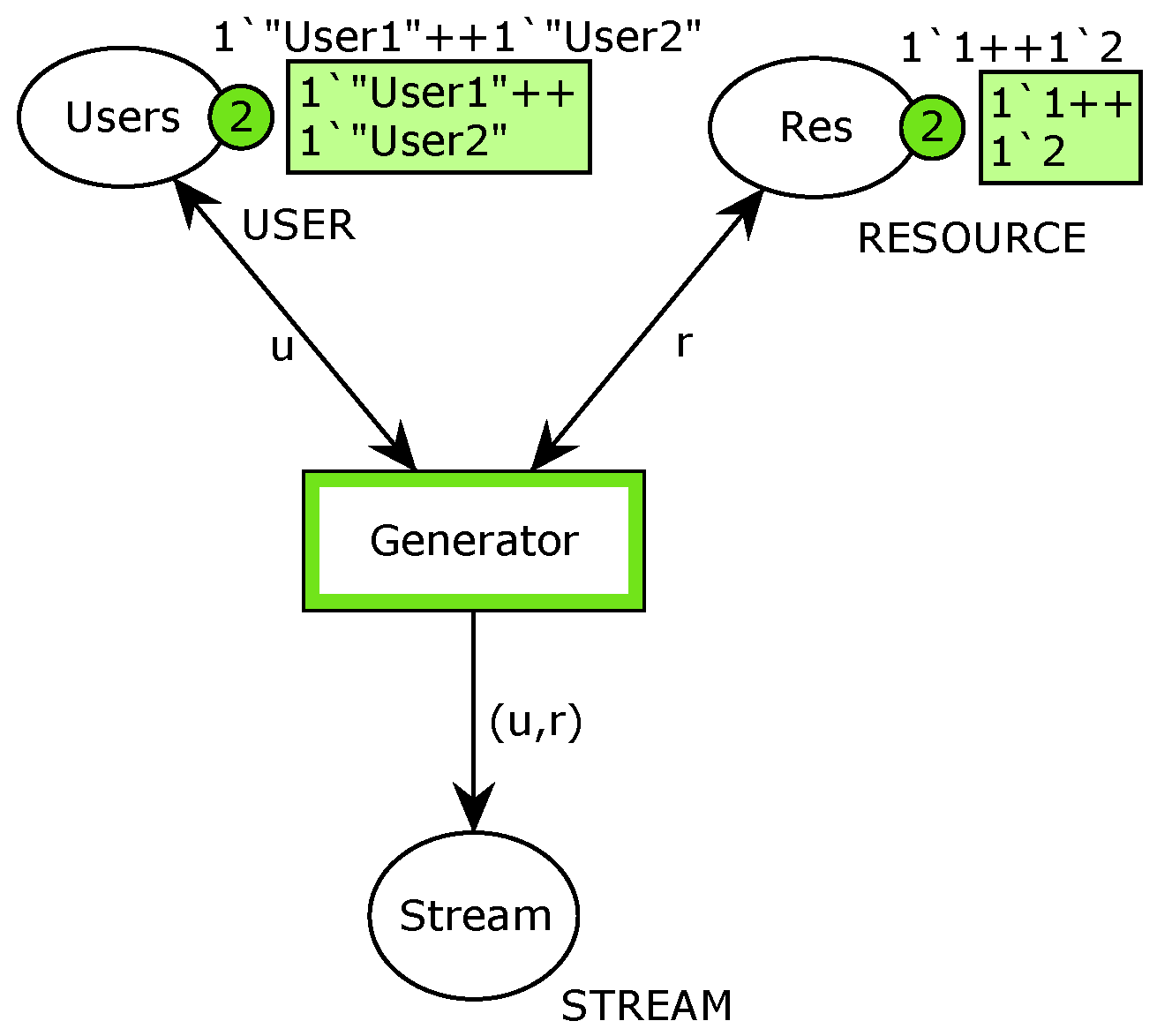
3. Systematization of the Generator Models
- untimed deterministic,
- untimed stochastic,
- timed deterministic,
- timed stochastic.
- (1)
- There is a place named Config. The initial marking of this place is a list and each element of this list describes one type of event generated by the model.
- (2)
- The element describing an event has the form of n-tuple in which the first element is a color representing the event type and the remaining elements specify in detail how this event is to be generated. This specification depends on the generator version.
- (3)
- Each generated event is represented by one token of type EVT (untimed models) or EVT_T (timed models). These tokens are collected in the place named Events.
3.1. Untimed Models
3.2. Timed Models
4. Case Study
5. Summary
Author Contributions
Funding
Conflicts of Interest
References
- Seshadri, K.; Pavana, C.; Sindhu, K.; Kollengode, C. Unsupervised Modeling of Workloads as an Enabler for Supervised Ensemble-based Prediction of Resource Demands on a Cloud; Verma, P., Charan, C., Fernando, X., Ganesan, S., Eds.; Advances in Data Computing, Communication and Security; Springer: Singapore, 2022; pp. 109–120. [Google Scholar]
- Rak, T.; Rzonca, D. Recommendations for Using QPN Formalism for Preparation of Incoming Request Stream Generator in Modeled System. Appl. Sci. 2021, 11, 11532. [Google Scholar] [CrossRef]
- Rzonca, D.; Rzasa, W.; Samolej, S. Consequences of the Form of Restrictions in Coloured Petri Net Models for Behaviour of Arrival Stream Generator Used in Performance Evaluation; Gaj, P., Sawicki, M., Suchacka, G., Kwiecień, A., Eds.; Computer Networks; Springer International Publishing: Cham, Switzerland, 2018; pp. 300–310. [Google Scholar] [CrossRef]
- Abad, C.L.; Yuan, M.; Cai, C.X.; Lu, Y.; Roberts, N.; Campbell, R.H. Generating request streams on Big Data using clustered renewal processes. Perform. Eval. 2013, 70, 704–719. [Google Scholar] [CrossRef]
- Rak, T.; Żyła, R. Using Data Mining Techniques for Detecting Dependencies in the Outcoming Data of a Web-Based System. Appl. Sci. 2022, 12, 6115. [Google Scholar] [CrossRef]
- Gonçalves, G.D.; Drago, I.; Vieira, A.B.; Couto da Silva, A.P.; Almeida, J.M.; Mellia, M. Workload models and performance evaluation of cloud storage services. Comput. Netw. 2016, 109, 183–199. [Google Scholar] [CrossRef]
- St-Onge, C.; Benmakrelouf, S.; Kara, N.; Tout, H.; Edstrom, C.; Rabipour, R. Generic SDE and GA-Based Workload Modeling for Cloud Systems. J. Cloud Comput. 2021, 10, 6. [Google Scholar] [CrossRef] [PubMed]
- Rak, T. Modeling Web Client and System Behavior. Information 2020, 11, 337. [Google Scholar] [CrossRef]
- An, C.; Zhou, J.t.; Mou, Z. A Generic Arrival Process Model for Generating Hybrid Cloud Workload; Sun, Y., Lu, T., Xie, X., Gao, L., Fan, H., Eds.; Computer Supported Cooperative Work and Social Computing; Springer: Singapore, 2019; pp. 100–114. [Google Scholar]
- Sun, J.; Zhao, H.; Mu, S.; Li, Z. Purchasing Behavior Analysis Based on Customer’s Data Portrait Model. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 1, pp. 352–357. [Google Scholar] [CrossRef]
- Liu, S.; Wang, J.; Wang, H.; Wang, H.; Liu, Y. WRT: Constructing Users’ Web Request Trees from HTTP Header Logs. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Magalhães, D.; Calheiros, R.N.; Buyya, R.; Gomes, D.G. Workload Modeling for Resource Usage Analysis and Simulation in Cloud Computing. Comput. Electr. Eng. 2015, 47, 69–81. [Google Scholar] [CrossRef]
- Daradkeh, T.; Agarwal, A.; Zaman, M.; S, R.M. Analytical Modeling and Prediction of Cloud Workload. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar] [CrossRef]
- An, C.; Zhou, J.t. Resource Demand Forecasting Approach Based on Generic Cloud Workload Model. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence and Computing, Advanced and Trusted Computing, Scalable Computing and Communications, Cloud and Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; pp. 554–563. [Google Scholar] [CrossRef]
- Rizothanasis, G.; Carlsson, N.; Mahanti, A. Identifying User Actions from HTTP(S) Traffic. In Proceedings of the 2016 IEEE 41st Conference on Local Computer Networks (LCN), Dubai, United Arab Emirates, 7–10 November 2016; pp. 555–558. [Google Scholar] [CrossRef]
- Grohmann, J.; Eismann, S.; Bauer, A.; Spinner, S.; Blum, J.; Herbst, N.; Kounev, S. SARDE: A Framework for Continuous and Self-Adaptive Resource Demand Estimation. ACM Trans. Auton. Adapt. Syst. 2021, 15, 1–31. [Google Scholar] [CrossRef]
- Ajwani, D.; Ali, S.; Katrinis, K.; Li, C.H.; Park, A.J.; Morrison, J.P.; Schenfeld, E. A Flexible Workload Generator for Simulating Stream Computing Systems. In Proceedings of the 2011 IEEE 19th Annual International Symposium on Modelling, Analysis, and Simulation of Computer and Telecommunication Systems, Singapore, 25–27 July 2011; pp. 409–417. [Google Scholar] [CrossRef]
- Bikmukhamedov, R.F.; Nadeev, A.F. Multi-Class Network Traffic Generators and Classifiers Based on Neural Networks. In Proceedings of the 2021 Systems of Signals Generating and Processing in the Field of on Board Communications, Moscow, Russia, 16–18 March 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Guarnieri, T.; Drago, I.; Cunha, Í.; Almeida, B.; Almeida, J.M.; Vieira, A.B. Modeling large-scale live video streaming client behavior. Multimed. Syst. 2021, 27, 1101–1124. [Google Scholar] [CrossRef]
- Curiel, M.; Pont, A. Workload Generators for Web-Based Systems: Characteristics, Current Status, and Challenges. IEEE Commun. Surv. Tutorials 2018, 20, 1526–1546. [Google Scholar] [CrossRef]
- Braga, V.G.; Correa, S.L.; Cardoso, K.V.; Viana, A.C. Data-Driven Characterization and Modeling of Web Map System Workload. IEEE Access 2021, 9, 26983–27002. [Google Scholar] [CrossRef]
- Gozhyj, A.; Kalinina, I.; Gozhyj, V.; Vysotska, V. Web Service Interaction Modeling with Colored Petri Nets. In Proceedings of the 2019 10th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Metz, France, 18–21 September 2019; Volume 1, pp. 319–323. [Google Scholar] [CrossRef]
- Gaur, N.; Joshi, P.; Jain, V.; Srivastava, R. Coloured Petri Nets Model for Web Architectures of Web and Database Servers. Int. J. Comput. Inf. Eng. 2015, 9, 2066–2075. [Google Scholar]
- Rak, T.; Samolej, S. Distributed Internet Systems Modeling Using TCPNs. In Proceedings of the International Multiconference on Computer Science and Information Technology, Wisla, Poland, 20–22 October 2008; pp. 515–522. [Google Scholar] [CrossRef]
- Samolej, S.; Rak, T. Simulation and Performance Analysis of Distributed Internet Systems Using TCPNs. Inform.-J. Comput. Inform. 2009, 33, 405–415. [Google Scholar]
- Rak, T. Response Time Analysis of Distributed Web Systems Using QPNs. Math. Probl. Eng. 2015, 2015, 490835. [Google Scholar] [CrossRef]
- Jensen, K.; Kristensen, L.M. Coloured Petri Nets: Modelling and Validation of Concurrent Systems; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Rezig, S.; Achour, Z.; Rezg, N.; Kammoun, M.A. Supervisory control based on minimal cuts and Petri net sub-controllers coordination. Int. J. Syst. Sci. 2016, 47, 3425–3435. [Google Scholar] [CrossRef]
- Rezig, S.; Rezg, N.; Hajej, Z. Online Activation and Deactivation of a Petri Net Supervisor. Symmetry 2021, 13, 2218. [Google Scholar] [CrossRef]
- Bause, F. Queueing Petri Nets-A formalism for the combined qualitative and quantitative analysis of systems. In Proceedings of the 5th International Workshop on Petri Nets and Performance Models, Toulouse, France, 19–22 October 1993; pp. 14–23. [Google Scholar] [CrossRef]
- Kounev, S.; Lange, K.D.; von Kistowski, J. Systems Benchmarking: For Scientists and Engineers; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar] [CrossRef]
- Patil, A.G.; Surve, A.R.; Gupta, A.K.; Sharma, A.; Anmulwar, S. Survey of synthetic traffic generators. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; Volume 1, pp. 1–3. [Google Scholar] [CrossRef]
- Rak, T. Performance Analysis of Distributed Internet System Models using QPN Simulation. In Proceedings of the Federated Conference on Computer Science and Information Systems (FedCSIS), Warsaw, Poland, 7–10 September 2014; Volume 2, pp. 769–774. [Google Scholar]
- Neter, J.; Wasserman, W.; Whitmore, G. Applied Statistics; Allyn & Bacon: Boston, MA, USA, 1992. [Google Scholar]















Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bożek, A.; Rak, T.; Rzonca, D. Timed Colored Petri Net-Based Event Generators for Web Systems Simulation. Appl. Sci. 2022, 12, 12385. https://doi.org/10.3390/app122312385
Bożek A, Rak T, Rzonca D. Timed Colored Petri Net-Based Event Generators for Web Systems Simulation. Applied Sciences. 2022; 12(23):12385. https://doi.org/10.3390/app122312385
Chicago/Turabian StyleBożek, Andrzej, Tomasz Rak, and Dariusz Rzonca. 2022. "Timed Colored Petri Net-Based Event Generators for Web Systems Simulation" Applied Sciences 12, no. 23: 12385. https://doi.org/10.3390/app122312385
APA StyleBożek, A., Rak, T., & Rzonca, D. (2022). Timed Colored Petri Net-Based Event Generators for Web Systems Simulation. Applied Sciences, 12(23), 12385. https://doi.org/10.3390/app122312385








