1. Introduction
In recent years, the Internet of Things (IoT) [
1] based on Wireless Sensor Networks (WSNs) has become more and more developed. The purpose of the IoT is to access data from each other through the remote connection of machine to machine (M2M) without human operation. The architecture of the IoT can be divided into three layers, named the sensing layer, network layer, and application layer. To meet the heterogeneous network architecture in the IoT system, most people choose to add a network layer gateway for heterogeneous network processing and upload the processed information to the cloud. Most gateways only process the heterogeneous network information and configure sufficient minimum storage capacity. The limitation of storage capacity makes it impossible for users to install anti-virus software on IoT devices, resulting in many potential loopholes.
With the rapid development of network technology, the speed of data exchange between devices is getting faster and faster. In the case of vulnerabilities in the system software or firmware, attackers can not only steal the data collected from the device for selling personal data, phishing, spreading spam, etc., but can even launch distributed denial of service (DDoS) attacks against other targets by controlling the device [
2]. It is difficult for common users to detect the device being attacked or controlled for the first time until network resources or system resources are affected and network services are temporarily delayed or interrupted. Therefore, we hope to make future IoT devices more secure by analyzing network packets to prevent blocking attacks.
There is already much literature proposing a variety of methods to lessen the effect of DDoS on IoT [
3,
4,
5,
6]. In addition, with the development of artificial intelligence, various algorithms have been applied in different fields. Deep Learning is a framework belonging to artificial intelligence, which is derived from the Neural Network (NN) framework improved by Hinton et al. in 2006 [
7]. It can analyze sequential data and has been applied to many fields, such as speech recognition, image recognition, natural language processing, etc. Through [
8,
9,
10,
11,
12], it can be demonstrated that deep learning can be applied to intrusion detection systems and can effectively improve the efficiency of network information security detection.
However, the identification results on the edge computer when measured under different conditions, in which Feature is the identification result of the feature model, and Flow means the identification result of the traffic model. Therefore, we conducted our research using the related neural network approach. The proposed architecture of edge computing with a trained CNN model will make correct identifications under the normal transmission, SYN flood attack, UDP flood attack, ICMP flood attack, and MIX flood attack, respectively. In this proposal, we would like to maximize the use of information about changes in related characteristics when packets are transmitted in the system, which can effectively improve the accuracy of recognition and make up for the shortcomings of using a single model for judgment.
Some relevant pieces of literature about machine learning (ML) based methods to mitigate DDoS attacks in IoT systems in recent years will be reviewed below. An evaluation of using a Random Neural Network (RNN) trained by normal traffic data compared to the Long-Short Term Memory (LSTM) to detect SYN flood DDoS attacks was provided in [
13]. It shows better results in RNN than LSTM, but its accuracy was almost 81% and not considered better enough to rely on. In [
14], a new deep neural network to identify the network flows being normal or abnormal was presented. The authors adopted a feedforward back-propagation design with seven secret layers and tested the method for DDoS detection using the most up-to-date Canadian dataset (CIC IDS 2017). The test provided a value of 0.99 scores which means that the experimental results were accurate in terms of Recall and Precision. A resource-friendly ML algorithm called Edge2Guard (E2G) was introduced in [
15]. It was trained and tested over the N-BaIoT dataset of normal and attack network traffic logs recorded by using Mirai and Bashlitte Botnets. The algorithm has resource-friendly detection depending on creating an E2G model for each MCU-based IoT device separately in the system. The disadvantage of this algorithm is that the model should be upgraded frequently after being trained with data from the developed type of malware action resulting in rising difficulties in the deployment process. An effective method employing two essential attributes named Volumetric and Asymmetric to detect two forms of flooding-based DDoS attacks was presented in [
16]. The proposed DDoS attack detection method based on SDN can cause minimal disruption to effective user activity and reduce both training and testing time.
In addition, it proposed the Advanced Support Vector Machine (ASVM) technique to enhance the current Support Vector Machine (SVM) algorithm to detect DDoS flooding attacks effectively. In [
17], a new detection classification system based on SVM and CNN ML algorithms was proposed. It converts the binary files into visualized images in grayscale. Then the CNN and SVM process these images to detect if a file contains maliciously injected code. The accuracy of this method is up to 94% in the binary classification case but only 81% in the multi-classification case. A new ML method based on clustering and graph structure features to predict the occurrence of DDoS attacks was provided in [
18]. The method creates the edge and vertex structures in graph theory and extracts eight features of traffic data as input variables. Then uses the principal component analysis (PCA) model to extract the features of DDoS and normal communication. Finally, the fuzzy C-means (FCM) clustering method is used to detect DDoS. The availability of this method is verified by taking 2000 traffic data in CICIDS-2017 as an example. The results of recall, false positive, true positive, true negative, and false negative were 100.00%, 1.05%, 68.95%, 0.00%, and 30.00%, respectively, indicating that it improves the reliability of detection and has a good detection effect on DDoS attacks compared to other methods.
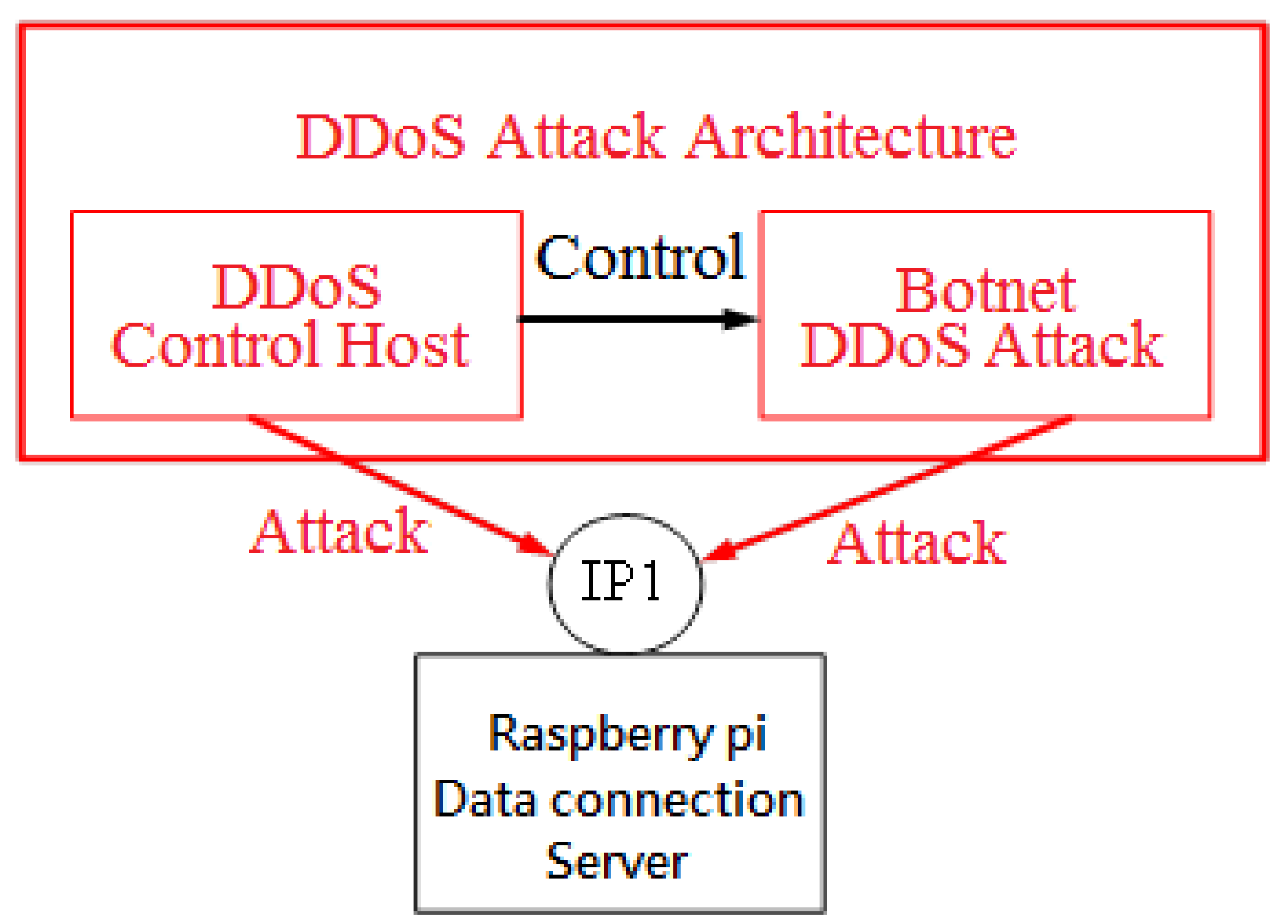
In the IoT system, due to the different wireless sensing networks used by the sensing layer, most of them need a gateway for cross-heterogeneous network processing. However, most gateways are used for heterogeneous network processing and do not have a lot of storage space. As a result, anti-virus software cannot be installed on the device, resulting in security vulnerabilities in the system. That makes the storage devices of the IoT the target of malicious attacks tested by novice hackers, among which the most common malicious attack mode includes DDoS attacks, which exhaust the target network or system resources through flood attacks, thereby slowing down or terminating their services. How to detect malicious attacks will be the focus of this paper.
In the past, the method of preventing DDoS attacks was to track the source of the attack and block the attack through functions such as Intrusion Detection Systems (IDS) and firewalls. However, with the increasing scale of DDoS attacks in recent years, such as the Mirai zombie virus in 2016, the Dyn.com domain name systems (DNS) services company, Domain Name Services suffered a DDoS attack, affecting websites such as Cable News Network and Twitter [
19]. This kind of attack may be a Botnet formed by a large number of IoT devices making massive DNS requests through a large number of IP addresses, resulting in service interruption [
20]. In addition, some attacks are carried out through disguised IP addresses, and these methods cannot effectively defend against DDoS attacks. It is easy to pass attack traffic or block normal traffic due to a single judgment. Therefore, how to reduce the error rate in DDoS attacks is very important.
To sum up, this research is mainly aimed at reducing the misjudgment probability of regular traffic packets and attack traffic packets in DDoS attacks. The convolutional neural network (CNN) is used to distinguish the captured packets to judge whether the current system is normal and use CNN to analyze the difference between a DDoS attack and normal transmission.
The remainder of the present work is structured as follows:
Section 2 briefly describes the scenario of a DDoS attack in the IoT network.
Section 3 introduces the experimental hardware and architecture, model training dataset, model training methods, IoT architecture, DDoS attack architecture, and system detection architecture. Next,
Section 4 is the implementation of the proposed method and experimental outcomes. Finally,
Section 5 summarizes the paper.
4. Results and Discussion
In this paper, TFN2K is used to collect packet traffic statistics, CPU and memory usage, average network speed, and other characteristics for five scenarios, including normal transmission, SYN flood attack, UDP flood attack, ICMP flood attack, and MIX flood attack. The collected data are preprocessed to build a packet traffic dataset and packet feature dataset, respectively, which can be used as the data for artificial intelligence model training. In this paper, the packet traffic is monitored for five minutes, and the relevant features of the packet traffic during this period are captured.
Figure 16a–e shows the total number of TCP, UDP, ICMP, and other packets under the normal transmission, SYN flood attack, UDP flood attack, ICMP flood attack, and MIX flood attack, respectively. The ordinate is the cumulative total number of packets, and the abscissa is the number of counts per 3 s.
Figure 16a–e shows the total number of TCP, UDP, ICMP, and other packets under the normal transmission, SYN flood attack, UDP flood attack, ICMP flood attack, and MIX flood attack, respectively. From
Figure 16a, it can be seen that under normal transmission conditions, there are all kinds of packets, and the cumulative number of packets increases moderately. However, no matter what kind of flood attack, the cumulative number of packets increases suddenly. Moreover, there are different cumulative numbers for different packet types when under attack. These characters can not only be used to judge whether an attack has been suffered but also can be used to identify the type of attack.
The experimental retrieval time is 5 min, so there are 100 records. Compared with
Figure 16a, it can be seen in
Figure 16b that suffered from an SYN flood attack, its TCP packets increased a lot, and the total number of TCP packets flowing through IP1 within 5 min was about 50,000, and other types of packets are almost equal to 0. In
Figure 16c of the UDP flood attack, it can be seen that UDP packets have increased a lot, while other types of packets are almost equal to 0. The collection time is 5 min. It can be seen that the sum of UDP packets during this period reached about 40000. In
Figure 16d of the ICMP flood attack, it can be seen that ICMP packets increased a lot, while other types of packets are almost equal to 0, and the collection time is 5 min. During this period of time, the sum of ICMP packets also reached about 40,000.
Figure 16e shows the situation of being attacked by other packets (MIX flood attack). At this time, the server flows through a large number of various types of packets, and the number of packets with UDP and TCP characteristics is almost the same. Therefore, in our experiment, it is obvious to observe that when attacked, the increase of various packets with this time and the change of the number of packets.
Figure 17a–e are the usage rates of their CPU and memory, respectively. As can be seen from
Figure 17a, the CPU usage rate changes little during normal transmission, but it will fluctuate greatly under attacks. Similarly, the memory usage rate is much lower under normal transmission than under attacks. It helps to detect whether the system is under attack. In
Figure 17b, it can be seen that when an SYN flood attack is encountered, the usage rate of CPU is about 20% higher than that in
Figure 17a under normal conditions. As shown in
Figure 17c, when suffering from UDP flood attacks, the CPU usage rate fluctuates violently, and its highest usage rate reaches more than 50%. In
Figure 17d, we can see that when the ICMP flood attack is encountered, the CPU’s usage rate fluctuates violently. The situation of the oscillation is the same as that of the UDP flood attack, but it has different characteristics. In
Figure 17e, it can be seen that when the MIX flood is encountered During the attack, the CPU’s usage rate will suddenly rise and fluctuate violently, just like the previous attacks. As shown in
Figure 17b–e, the usage rate of the memory remains roughly the same as normal. Therefore, we can find out its characteristics from the fluctuation of CPU usage. From the results in
Table 4, it can be seen that various attacks will affect the network speed during transmission. In our experiment, the average network transmission speed will drop from an average of 14.2 Mbps to about 0.3 Mbps. Based on the above experimental results, we use a neural network for edge computing and model training.
In this paper, the model of a NN, one-dimensional CNN, and two-dimensional CNN are respectively trained and evaluated. The best-performing model will be applied to the practical validation of the proposed system. Accuracy is used to evaluate the proportion of correct predictions of true and false under all conditions, which can be expressed as
where the four conditions, True Positive (TP), True Negative (TN), False Positive (FP), and False Negative (FN), are described in
Table 5.
In this paper, we use the packet traffic dataset to train the three models mentioned above. One data is used as the labeled input, and the training parameters are 10, 50, 100, 150, and 200 times respectively. The batch size of each training is 2500, and the learning rate is 0.00001. The model uses three hidden layers, 128, 64, and 32 neurons, respectively, with an excitation function of “ReLU” and the output layer using the “softmax” as an excitation function for classification. When using the packet feature dataset for training, four pieces of data are used as label input and trained 10, 20, 30, 40, and 50 times respectively. The batch size is 2500, and the learning rate is 0.00001. The model has three hidden layers of 128, 64, and 32 neurons, respectively, and the excitation function is “ReLU.” The excitation function “softmax” is used for classification in the output layer. For one-dimensional and two-dimensional CNN, a dropout layer is added after the first layer to prevent overfitting.
The training accuracies of the two different pieces of training are shown in
Table 6 and
Table 7, respectively. It can be seen from
Table 6 and
Table 7 that with the increase in the number of training times and the ratio of input, the accuracy of training can reach more than 99% in the end. This shows that according to the characteristics of the environment, there must be more than a certain amount of data collected in order to have good training results. As shown in
Table 6 and
Table 7, the two-dimensional CNN model is more accurate after training, both in terms of packet traffic and feature training, named traffic model and feature model, respectively hereafter, so it will be used as the identification model for the practical validation.
Both the correct rate and loss rate of the two-dimensional CNN for the traffic model and feature model is shown in
Figure 18 and
Figure 19, respectively.
In this paper, we use a trained two-dimensional CNN model for real experiment verification. The data collection server IP1 is subjected to normal transmission, SYN flood attack, UDP flood attack, ICMP flood attack, and MIX flood attack, respectively, and the number and feature of packets flowing through IP1 are collected. It will be sent to the edge computing computer through IP2 to identify the current situation of the server by using a trained model. The edge computing computer will preprocess the received data and input them into the traffic model and feature model, respectively, for identification. The final identification result is obtained by combining the obtained identification rates and their weights. Considering that the data of the packet traffic dataset may be affected by the increasing number of users in the IoT, and the features captured will not be able to identify because the data captured is too small, this paper gives the traffic model and feature model the weights of 70% and 30% respectively, as the basis for judging the identification results.
Table 8 lists the identification results on the edge computer when measured under different conditions, in which Feature is the identification result of the feature model, Flow means the identification result of the traffic model, and Weighted is the identification result after individual weighting on the two models. According to the table, the proposed architecture of edge computing with a trained CNN model can make correct identifications under the normal transmission, SYN flood attack, UDP flood attack, ICMP flood attack, and MIX flood attack, respectively. Even in the lack of packets case during normal transmission, the feature model cannot recognize it normally, but the traffic model can still recognize it when the data is rare. Since the traffic model accounts for 70% of the weight, the weighted identification result is normal. The above experimental results are mainly because this system adopts two independent two-dimensional CNN models trained by the packet traffic dataset and packet features dataset, respectively, and recognizes the existing situation of the system at the same time and then adds appropriate weights to them as a basis for judgment. This design can maximize the use of information about changes in related characteristics when packets are transmitted in the system, which can effectively improve the accuracy of recognition and make up for the shortcomings of using a single model for judgment.
Table 9 shows the time interval, named identification time, between Raspberry pi transmitting the captured data to the edge computing computer and receiving the identification result returned by the edge computing computer. From this table, it can be concluded that the identification time does not cause the system identification delay due to the DDoS attack.