An Introduction to Quantum Model Checking
Abstract
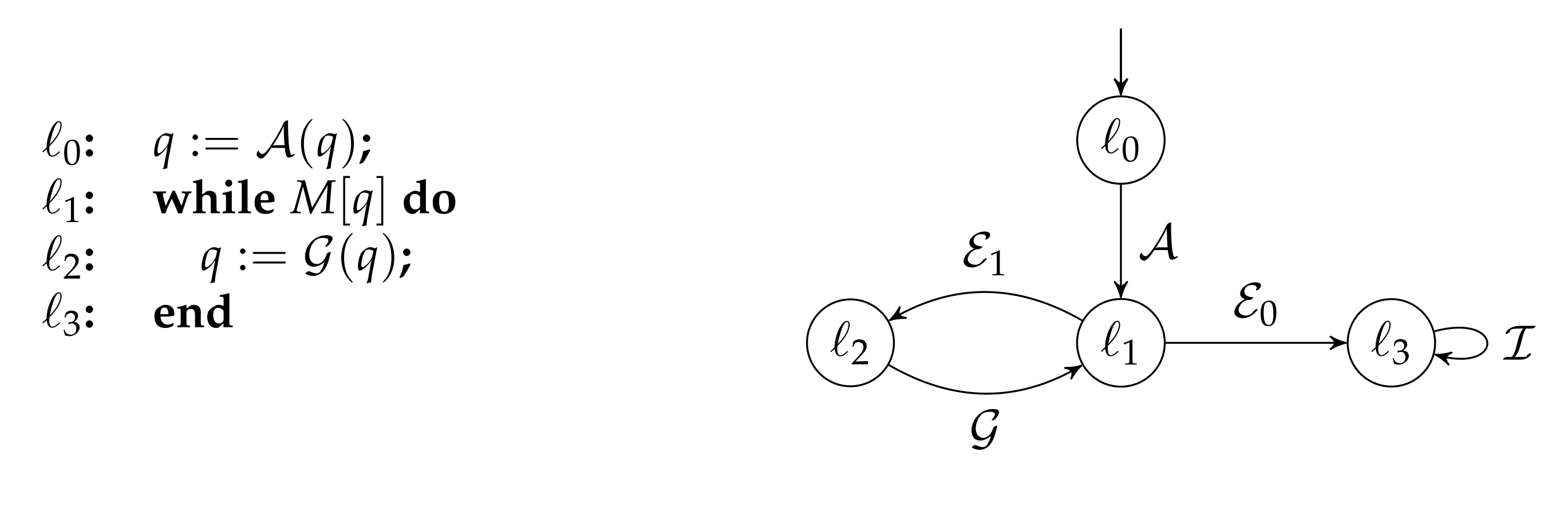
:1. Introduction
- One can test the system, by feeding it with several inputs and looking at the correctness of the generated output. However, as Dijkstra said in his Turing Award lecture [1],
- “program testing can be a very effective way to show the presence of bugs, but is hopelessly inadequate for showing their absence.”
- In fact, if the testing inputs do not trigger the bug, it remains undetected, ready to cause damages once the system is deployed to production.
- One can manually prove that the system is correct by applying the techniques learned in programming and cryptography courses, such as by using Hoare logic/triples to prove properties of programs or by showing that the cryptographic protocol is provably secure. This approach provides the desired guarantees, but it is tedious, error prone, and reasonably applicable only to very small systems.
- One can apply one of the several techniques developed by researches specifically for this purpose, such as model checking, abstract interpretation, and high-order theorem proving. These techniques can be usually applied automatically to the system and are able to scale to large systems.
1.1. The Successful Story of Model Checking
- The system can have a probabilistic behavior, as a result of internal random choices (such as the sampling of nonces in a security protocol) or of external uncertainty (the message is sent on a noisy channel that may alter it).
- The system can have a nondeterministic behavior, as the result of multiple components running in parallel and interacting with each other in no predefined order.
- The system needs to take care of the amount of time available for reacting to input or for completing its tasks: a collision avoidance system installed on an airplane needs to warn the pilot as soon as possible about the risk of the collision; it is certain that it needs to do so within the time limits imposed by the aviation authorities.
- 1.
- How can we model formally the given quantum protocol?
- 2.
- How can we specify the desired properties?
1.2. How Can We Model Formally the Given Quantum Protocol?
1.3. How Can We Specify the Desired Properties?
1.4. Organization of the Paper
2. Quantum Markov Chains
- S is a finite set of classical states;
- is called the transition matrix where for each , the super-operator is trace-preserving, that is .
- is a finite set of atomic propositions and
- is a labelling function.
3. Model Checking CTL Properties
3.1. The Model Checking Problem
3.2. The Standard Bottom-Up Approach
3.3. Complexity of the QCTL Model Checking Problem
4. Model Checking Fidelity Properties
4.1. The Model Checking Problem
4.2. The Standard Bottom–Up Approach
4.3. Complexity of the FCTL Model Checking Problem
5. Model Checking LTL and -Regular Properties
5.1. The Model Checking Problem
5.2. The Standard Automata-Based Approach
5.3. The Standard Automata-Based Approach Does Not Work Directly for LQMCs
5.4. Parity Automata and Parity Quantum Markov Chains
- A is a finite set of automaton states;
- is the initial state;
- is a finite set of atomic propositions;
- is a transition function; and
- is a priority function.
- ;
- if , and otherwise; and
- .
5.5. Computing PQMC Values
- invariant for if ;
- a BSCC of if holds for each pure state , where is the reachable subspace of starting in ;
- transient if for each , where is the projection onto X.
- 1.
- A projective measurement is performed on the classical system to determine the current classical state.
- 2.
- If the measurement outcome of M is s, then the quantum measurement is performed on the quantum system .
- 3.
- If the observed outcome of is , then the classical state is set to be .
- if , then ;
- if , then ; and
- if , then ,
5.6. Complexity of the LTL and -Regular Model Checking Problem
6. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Dijkstra, E.W. The Humble Programmer. Commun. ACM 1972, 15, 859–866. [Google Scholar] [CrossRef] [Green Version]
- Clarke, E.M.; Emerson, E.A. Design and Synthesis of Synchronization Skeletons Using Branching-Time Temporal Logic. In Logic of Programs; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1981; Volume 131, pp. 52–71. [Google Scholar]
- Queille, J.; Sifakis, J. Specification and verification of concurrent systems in CESAR. In Symposium on Programming; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1982; Volume 137, pp. 337–351. [Google Scholar]
- Burch, J.R.; Clarke, E.M.; McMillan, K.L.; Dill, D.L. Sequential Circuit Verification Using Symbolic Model Checking. In Proceedings of the 27th ACM/IEEE Design Automation Conference, Orlando, FL, USA, 24–28 June 1990; pp. 46–51. [Google Scholar]
- Clarke, E.M.; Filkorn, T.; Jha, S. Exploiting Symmetry In Temporal Logic Model Checking. In CAV; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1993; Volume 697, pp. 450–462. [Google Scholar]
- Gupta, A. Formal Hardware Verification Methods: A Survey. Formal Methods Syst. Des. 1992, 1, 151–238. [Google Scholar] [CrossRef]
- Kropf, T. Introduction to Formal Hardware Verification; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
- Yoeli, M. Formal Verification of Hardware Design; IEEE Computer Society Press: Piscataway, NJ, USA, 1990. [Google Scholar]
- Liggesmeyer, P.; Rothfelder, M.; Rettelbach, M.; Ackermann, T. Qualitätssicherung Software-basierter technischer Systeme—Problembereiche und Lösungsansätze. Inform. Spektrum 1998, 21, 249–258. [Google Scholar] [CrossRef]
- Peled, D.A. Software Reliability Methods; Texts in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001. [Google Scholar]
- Rushby, J.M.; von Henke, F.W. Formal Verification of Algorithms for Critical Systems. IEEE Trans. Softw. Eng. 1993, 19, 13–23. [Google Scholar] [CrossRef]
- Tretmans, J.; Wijbrans, K.; Chaudron, M.R.V. Software Engineering with Formal Methods: The Development of a Storm Surge Barrier Control System Revisiting Seven Myths of Formal Methods. Formal Methods Syst. Des. 2001, 19, 195–215. [Google Scholar] [CrossRef]
- Wijbrans, K.; Buve, F.; Rijkers, R.; Geurts, W. Software Engineering with Formal Methods: Experiences with the Development of a Storm Surge Barrier Control System. In FM; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5014, pp. 419–424. [Google Scholar]
- Holzmann, G.J. Design and Validation of Computer Protocols; Prentice-Hall, Inc.: Hoboken, NJ, USA, 1990. [Google Scholar]
- Holzmann, G.J. Design and Validation of Protocols: A Tutorial. Comput. Netw. ISDN Syst. 1993, 25, 981–1017. [Google Scholar] [CrossRef]
- Holzmann, G.J. The Theory and Practice of A Formal Method: NewCoRe. In IFIP Congress (1); IFIP Transactions; North-Holland: Amsterdam, The Netherlands, 1994; Volume A-51, pp. 35–44. [Google Scholar]
- Clarke, E.M.; Grumberg, O.; Hiraishi, H.; Jha, S.; Long, D.E.; McMillan, K.L.; Ness, L.A. Verification of the Futurebus+ Cache Coherence Protocol. Formal Methods Syst. Des. 1995, 6, 217–232. [Google Scholar] [CrossRef]
- Lowe, G. Breaking and Fixing the Needham-Schroeder Public-Key Protocol Using FDR. Softw. Concepts Tools 1996, 17, 93–102. [Google Scholar]
- Chen, T.; Diciolla, M.; Kwiatkowska, M.Z.; Mereacre, A. Quantitative verification of implantable cardiac pacemakers over hybrid heart models. Inf. Comput. 2014, 236, 87–101. [Google Scholar] [CrossRef]
- Chan, W.; Anderson, R.J.; Beame, P.; Burns, S.; Modugno, F.; Notkin, D.; Reese, J.D. Model Checking Large Software Specifications. IEEE Trans. Softw. Eng. 1998, 24, 498–520. [Google Scholar] [CrossRef]
- Staunstrup, J.; Andersen, H.R.; Hulgaard, H.; Lind-Nielsen, J.; Larsen, K.G.; Behrmann, G.; Kristoffersen, K.J.; Skou, A.; Leerberg, H.; Theilgaard, N.B. Practical Verification of Embedded Software. Computer 2000, 33, 68–75. [Google Scholar] [CrossRef]
- Havelund, K.; Lowry, M.R.; Penix, J. Formal Analysis of a Space-Craft Controller Using SPIN. IEEE Trans. Softw. Eng. 2001, 27, 749–765. [Google Scholar] [CrossRef] [Green Version]
- Holzmann, G.J.; Najm, E.; Serhrouchni, A. SPIN Model Checking: An Introduction. Int. J. Softw. Tools Technol. Transf. 2000, 2, 321–327. [Google Scholar] [CrossRef]
- Bozzano, M.; Cimatti, A.; Katoen, J.; Katsaros, P.; Mokos, K.; Nguyen, V.Y.; Noll, T.; Postma, B.; Roveri, M. Spacecraft early design validation using formal methods. Reliab. Eng. Syst. Saf. 2014, 132, 20–35. [Google Scholar] [CrossRef] [Green Version]
- Hoque, K.A.; Mohamed, O.A.; Savaria, Y. Towards an accurate reliability, availability and maintainability analysis approach for satellite systems based on probabilistic model checking. In Proceedings of the 2015 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2015; pp. 1635–1640. [Google Scholar]
- Clarke, E.M.; Henzinger, T.A.; Veith, H.; Bloem, R. (Eds.) Handbook of Model Checking; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Baier, C.; Katoen, J. Principles of Model Checking; MIT Press: Cambridge, MA, USA, 2008. [Google Scholar]
- Bérard, B.; Bidoit, M.; Finkel, A.; Laroussinie, F.; Petit, A.; Petrucci, L.; Schnoebelen, P.; McKenzie, P. Systems and Software Verification, Model-Checking Techniques and Tools; Springer: Berlin/Heidelberg, Germany, 2001. [Google Scholar]
- Clarke, E.M.; Grumberg, O.; Peled, D.A. Model Checking; MIT Press: Cambridge, MA, USA, 2001. [Google Scholar]
- Huth, M.; Ryan, M.D. Logic in Computer Science—Modelling and Reasoning about Systems; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Schneider, K. Verification of Reactive Systems—Formal Methods and Algorithms; Texts in Theoretical Computer Science; An EATCS Series; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Ben-Ari, M. Principles of the SPIN Model Checker; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- McMillan, K.L. Symbolic Model Checking; Kluwer: Alphen aan den Rijn, The Netherlands, 1993. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public-key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computer, Systems and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Bennett, C.H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 1992, 68, 3121. [Google Scholar] [CrossRef]
- Bennett, C.H.; Wiesner, S.J. Communication Via One- and Two-particle Operators on Einstein-Podolsky-Rosen States. Phys. Rev. Lett. 1992, 69, 2881–2884. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Shor, P.W. Algorithms for Quantum Computation: Discrete Logarithms and Factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Gay, S.J.; Nagarajan, R.; Papanikolaou, N. Probabilistic model-checking of quantum protocols. In Proceedings of the 2nd International Workshop on Developments in Computational Models, Venice, Italy, 16 July 2006. [Google Scholar]
- Papanikolaou, N. Model Checking Quantum Protocols. Ph.D. Thesis, University of Warwick, Coventry, UK, 2009. [Google Scholar]
- Gay, S.J.; Nagarajan, R.; Papanikolaou, N. QMC: A Model Checker for Quantum Systems. In CAV; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5123, pp. 543–547. [Google Scholar]
- Hung, W.N.N.; Song, X.; Yang, G.; Yang, J.; Perkowski, M.A. Quantum logic synthesis by symbolic reachability analysis. In Proceedings of the 41st Annual Design Automation Conference, San Diego, CA, USA, 7–11 June 2004; pp. 838–841. [Google Scholar]
- Hung, W.N.N.; Song, X.; Yang, G.; Yang, J.; Perkowski, M.A. Optimal synthesis of multiple output Boolean functions using a set of quantum gates by symbolic reachability analysis. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2006, 25, 1652–1663. [Google Scholar] [CrossRef] [Green Version]
- Feng, Y.; Yu, N.; Ying, M. Model checking quantum Markov chains. J. Comput. Syst. Sci. 2013, 79, 1181–1198. [Google Scholar] [CrossRef]
- Pnueli, A. The Temporal Logic of Programs. In Proceedings of the 18th Annual Symposium on Foundations of Computer Science, Providence, RI, USA, 31 October–2 November 1977; pp. 46–57. [Google Scholar]
- Emerson, E.A.; Halpern, J.Y. “Sometimes” and “Not Never” revisited: On branching versus linear time temporal logic. J. ACM 1986, 33, 151–178. [Google Scholar] [CrossRef]
- Hansson, H.; Jonsson, B. A Logic for Reasoning about Time and Reliability. Formal Aspects Comput. 1994, 6, 512–535. [Google Scholar] [CrossRef] [Green Version]
- Bianco, A.; de Alfaro, L. Model Checking of Probabalistic and Nondeterministic Systems. In FSTTCS; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1995; Volume 1026, pp. 499–513. [Google Scholar]
- Feng, Y.; Hahn, E.M.; Turrini, A.; Ying, S. Model Checking Omega-regular Properties for Quantum Markov Chains. In CONCUR; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2017; Volume 85, pp. 35:1–35:16. [Google Scholar]
- Xu, M.; Fu, J.; Mei, J.; Deng, Y. An Algebraic Method to Fidelity-based Model Checking over Quantum Markov Chains. arXiv 2021, arXiv:2101.04971. [Google Scholar]
- Duan, Z.; Niu, L. Some properties of quantum fidelity in infinite-dimensional quantum systems. Int. J. Quantum Inf. 2018, 16, 1850028. [Google Scholar] [CrossRef]
- Uhlmann, A. On “Partial” Fidelities. Rep. Math. Phys. 2000, 45, 407–418. [Google Scholar] [CrossRef] [Green Version]
- Burrell, A.H.; Szwer, D.J.; Webster, S.C.; Lucas, D.M. Scalable simultaneous multiqubit readout with 99.99% single-shot fidelity. Phys. Rev. A 2010, 81, 040302. [Google Scholar] [CrossRef] [Green Version]
- Myerson, A.H.; Szwer, D.J.; Webster, S.C.; Allcock, D.T.C.; Curtis, M.J.; Imreh, G.; Sherman, J.A.; Stacey, D.N.; Steane, A.M.; Lucas, D.M. High-Fidelity Readout of Trapped-Ion Qubits. Phys. Rev. Lett. 2008, 100, 200502. [Google Scholar] [CrossRef] [Green Version]
- Ying, M.; Feng, Y. Model Checking Quantum Systems: Principles and Algorithms; Cambridge University Press: Cambridge, UK, 2021. [Google Scholar]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Selinger, P. A Brief Survey of Quantum Programming Languages. In FLOPS; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2998, pp. 1–6. [Google Scholar]
- Feng, Y.; Hahn, E.M.; Turrini, A.; Zhang, L. QPMC: A Model Checker for Quantum Programs and Protocols. In FM; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9109, pp. 265–272. [Google Scholar]
- de Alfaro, L. Formal Verification of Probabilistic Systems. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 1997. [Google Scholar]
- Courcoubetis, C.; Yannakakis, M. The Complexity of Probabilistic Verification. J. ACM 1995, 42, 857–907. [Google Scholar] [CrossRef]
- Bustan, D.; Rubin, S.; Vardi, M.Y. Verifying omega-Regular Properties of Markov Chains. In CAV; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3114, pp. 189–201. [Google Scholar]
- Vardi, M.Y.; Wolper, P. An Automata-Theoretic Approach to Automatic Program Verification (Preliminary Report). In Proceedings of the First Symposium on Logic in Computer Science, Cambridge, MA, USA, 16–18 June 1986; pp. 332–344. [Google Scholar]
- Grädel, E.; Thomas, W.; Wilke, T. (Eds.) Automata, Logics, and Infinite Games: A Guide to Current Research; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2500. [Google Scholar]
- Mostowski, A.W. Regular expressions for infinite trees and a standard form of automata. In Symposium on Computation Theory; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1984; Volume 208, pp. 157–168. [Google Scholar]
- Emerson, E.A.; Jutla, C.S. Tree Automata, Mu-Calculus and Determinacy (Extended Abstract). In Proceedings of the 32nd Annual Symposium of Foundations of Computer Science, San Juan, PR, USA, 1–4 October 1991; pp. 368–377. [Google Scholar]
- Safra, S. On the Complexity of omega-Automata. In Proceedings of the 29th Annual Symposium on Foundations of Computer Science, White Plains, NY, USA, 24–26 October 1988; pp. 319–327. [Google Scholar]
- Piterman, N. From Nondeterministic Büchi and Streett Automata to Deterministic Parity Automata. Log. Methods Comput. Sci. 2007, 3, 1–21. [Google Scholar] [CrossRef] [Green Version]
- Schewe, S. Tighter Bounds for the Determinisation of Büchi Automata. In FoSSaCS; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5504, pp. 167–181. [Google Scholar]
- Kähler, D.; Wilke, T. Complementation, Disambiguation, and Determinization of Büchi Automata Unified. In ICALP (1); Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5125, pp. 724–735. [Google Scholar]
- Fogarty, S.; Kupferman, O.; Vardi, M.Y.; Wilke, T. Profile trees for Büchi word automata, with application to determinization. Inf. Comput. 2015, 245, 136–151. [Google Scholar] [CrossRef]
- Löding, C.; Pirogov, A. Determinization of Büchi Automata: Unifying the Approaches of Safra and Muller-Schupp. In ICALP; LIPIcs; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2019; Volume 132, pp. 120:1–120:13. [Google Scholar]
- Li, L.; Feng, Y. Quantum Markov chains: Description of hybrid systems, decidability of equivalence, and model checking linear-time properties. Inf. Comput. 2015, 244, 229–244. [Google Scholar] [CrossRef]
- Ying, S.; Feng, Y.; Yu, N.; Ying, M. Reachability Probabilities of Quantum Markov Chains. In CONCUR; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8052, pp. 334–348. [Google Scholar]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Turrini, A. An Introduction to Quantum Model Checking. Appl. Sci. 2022, 12, 2016. https://doi.org/10.3390/app12042016
Turrini A. An Introduction to Quantum Model Checking. Applied Sciences. 2022; 12(4):2016. https://doi.org/10.3390/app12042016
Chicago/Turabian StyleTurrini, Andrea. 2022. "An Introduction to Quantum Model Checking" Applied Sciences 12, no. 4: 2016. https://doi.org/10.3390/app12042016





