Authentication and Authorization in Microservices Architecture: A Systematic Literature Review
Abstract
:1. Introduction
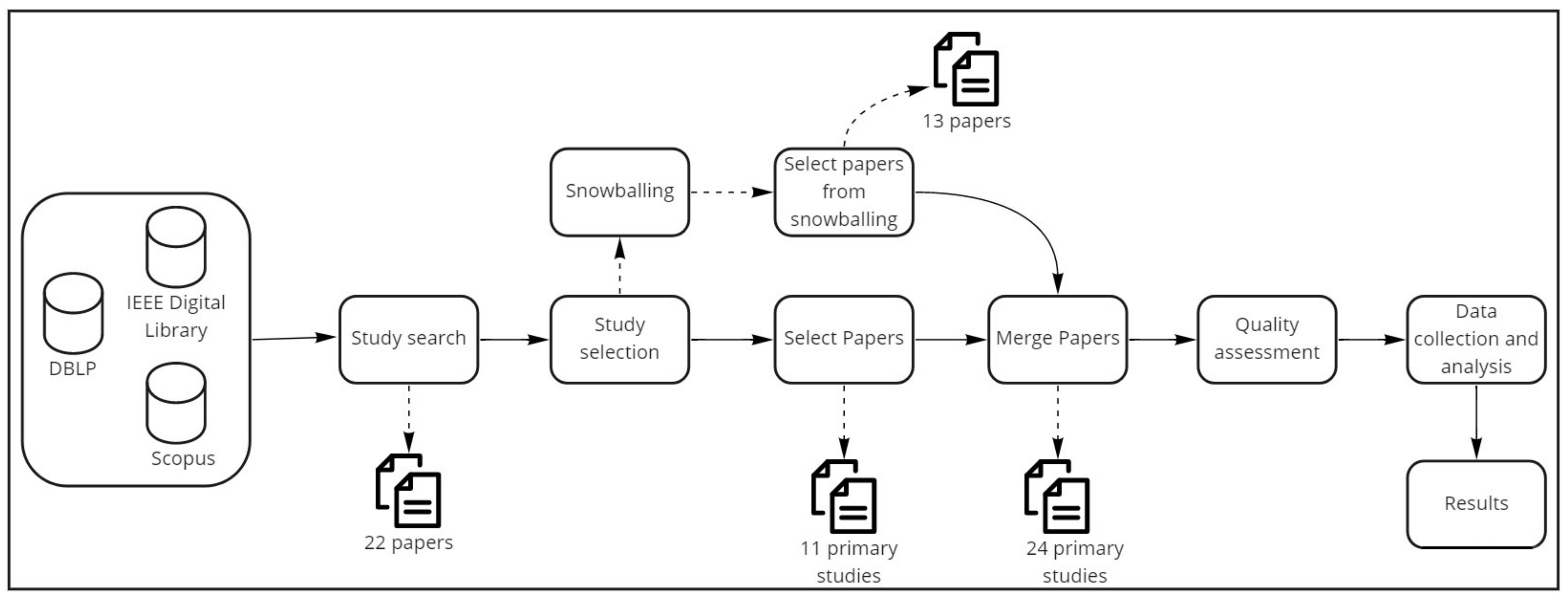
2. Systematic Literature Review
2.1. Research Questions
- RQ.1. What are the challenges mentioned in the literature to perform authentication and authorization in the context of microservice architecture systems?
- RQ.2. What mechanisms are used in the literature to deal with the challenges related to authentication and authorization in a microservices architecture?
- RQ.3. What are the main open-source technology solutions that implement the authentication and authorization mechanisms identified in the literature?
2.2. Search Process
(“MICROSERVICE” OR “MICROSERVICES”) AND (“SECURITY” AND “AUTHENTICATION” AND “AUTHORIZATION”) AND (“CHALLENGE*” OR “PROBLEM*” OR “ISSUE*” OR “SOLUTION*” OR “PROTOCOL*” OR “MECHANISM*” “STRATEG*” OR “IMPLEMENTATION*” OR “OPENSOURCE” OR “OPEN-SOURCE” OR “OPEN SOURCE”).
2.3. Inclusion and Exclusion Criteria
- IC.1 Studies dealing with challenges involving authentication and authorization in microservices;
- IC.2 Studies related to security mechanisms that deal with authentication and authorization challenges in microservices;
- IC.3 Studies related to open-source technologies that implement security mechanisms.
- EC.1 Studies that do not address the research object;
- EC.2 Studies prior to 2010;
- EC.3 Duplicate studies;
- EC.4 Studies published as short paper.
2.4. Quality Assessment
- Is the research objective clearly described?
- Do the authors describe the limitation of the study?
- Does the study identify problems and/or challenges involving authentication and authorization in microservices architecture?
- Does the study identify the mechanisms that mitigate the problems and/or challenges involving authentication and authorization in microservices architecture?
- Does the study present solutions that implement security mechanisms using open-source technology?
- Yes (1);
- Partially (0.5);
- No (0).
2.5. Data Collection and Analysis
3. SLR Results
3.1. Quality Assessment of Reviews Carried out
3.2. Quality Factors
3.3. RQ.1. What Are the Challenges Mentioned in the Literature to Perform Authentication and Authorization in the Context of Microservice Architecture Systems?
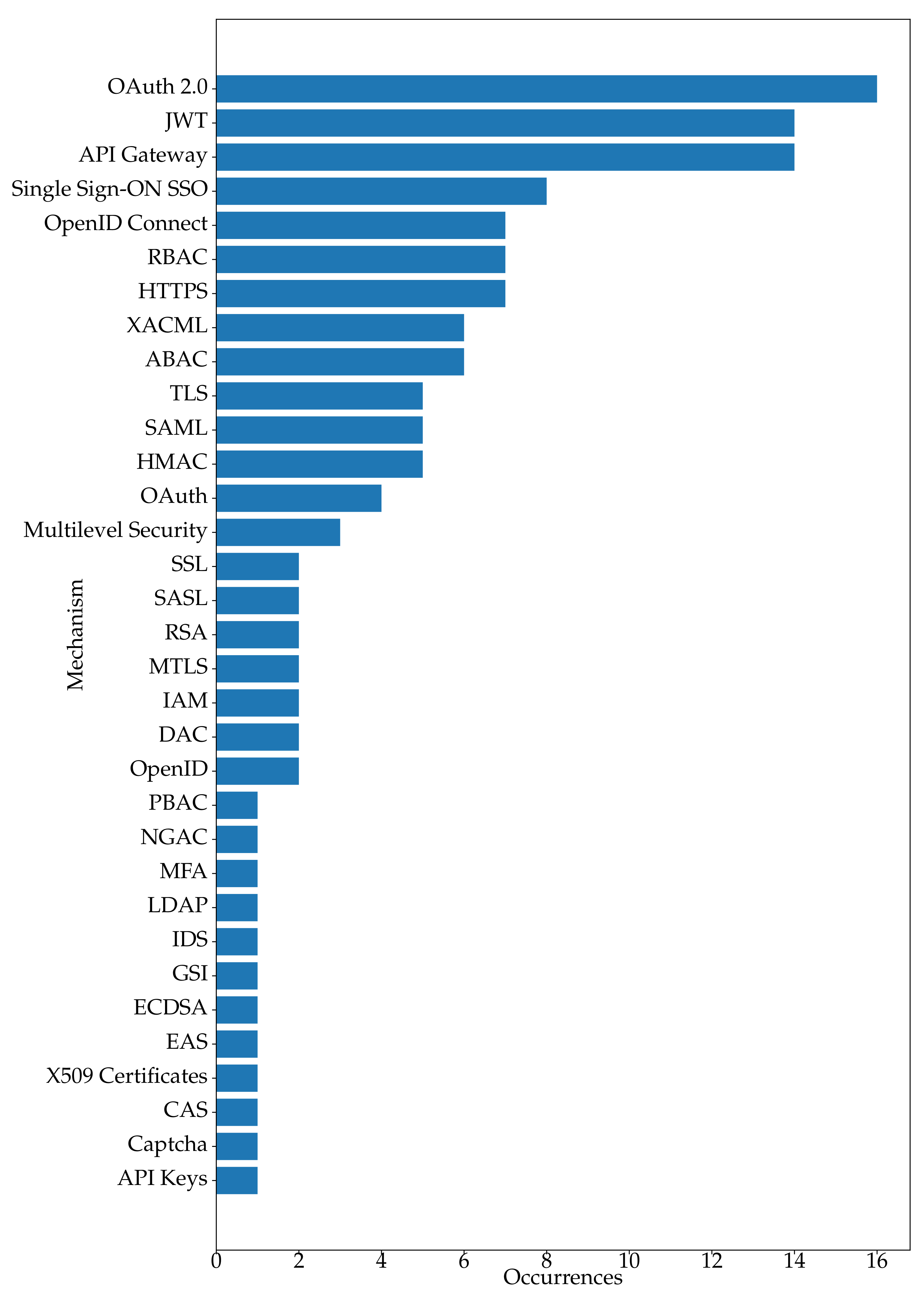
3.4. RQ.2. What Mechanisms Are Used in the Literature to Deal with the Challenges Related to Authentication and Authorization in a Microservices Architecture?
- OAuth 2.0 (Open Authorization): The OAuth 2.0 protocol is defined by RFC 6749 [39]. According to Banati et al. [29] OAuth 2.0 is an authorization framework that allows users to access different services without having to share their credentials. In a practical scenario, the user authenticates to an authorization server and receives an authorization code or an access token, which can be used to access resources, without the need to contact the authorization server again or have to inform the username and password [25]. Access tokens are validated on each request for some service [15,35]. This procedure poses a risk for affecting the performance of a distributed architecture because if there is a large number of requests, the authentication server may be affected [22]. OAuth 2.0 is one of the protocols most used by microservice architectures for access delegation [25,31] and can be applied both in web applications and in backend services, in addition to meeting both the authentication and authorization proposal [24,28]. It is important to mention that OAuth 2.0 is widely used as an authorization protocol to protect services that use the REST (Representational State Transfer) [23,25,27], in addition to adopting the HTTPS protocol in data communication [25].
- JWT (JSON Web Token): The JWT is defined by RFC 7519 [40]. It is an open standard that provides a compact and independent way to securely transmit information between applications using a JSON (Javascript Object Notation) object. This information is verifiable and trustworthy as it is digitally signed using a secret [22]. It has a format divided into three parts: Header, Payload and Signature. The header is separated into two parts, token type and the algorithm, that may be a HMAC, SHA256 or RSA [29].The JWT has an advantage over traditional tokens, this verification can be done directly on the resource server, without connecting to the authentication server [22,36]. Using JWT it is possible to retrieve user information directly from the token [22,26]. In addition to user information, it is common to find in a JWT their permissions and expiration time of the token [36]. The JWT has adherence to “stateless” applications, that is, those that do not keep a session on the server side, but stay data with the client side, and must be used in each client request to the resource [26]. In a microservices environment, JWTs can be transferred during the communication between them [35]. Finally, it is important to know that JWT can be integrated with the OAuth 2.0 protocol [4,23].
- API Gateway: In the microservices environment, API Gateway acts as an intermediary between the client and the microservices, providing a private network environment that allows the exchange of private data [3,15], that is, clients do not communicate directly with services, but only with a Gateway, which is responsible for communicates with the requested service. It can be an input that performs the filtering of client requests, making the appropriate forwarding to the microservice [23], and it can check the user’s credentials, to find out if he owns the proper authorization [7,37]. We realized that API Gateway is a technique to decrease microservice exposure. Nevertheless, it is important in a future work compares the communication in different scenarios. These scenarios could be using or not using the API gateway between the client and microservices. Consequently, it will be possible to collect the strengths and weakness of both approaches and verify the possibility of hybrid scenarios.Lu et al. [34], stated that the API Gateway can aggregate multiple microservices in a single client interface, being an element that stands between the client and the requested service. Using the API Gateway helps to reduce the exposure of systems, then, the microservices are all protected behind the API Gateway [8]. Although several advantages for its implementation have been observed, its use may not prove advantageous when it becomes a single decision point, because, in case of failure in this element, the entire application may become inaccessible [8]. An API Gateway can use services such as JWT and OAuth 2.0 [7,8,15,23,25,34,36].
- OpenID Connect: OpenID Connect is an open authentication standard that ensures users have only one digital identity for multiple applications or services [29]. Dongjin et al. [25] stated that it is an authentication layer over the OAuth protocol, allowing services to read the user’s basic information. Nehme et al. [27,31] observed that OpenID Connect is built on top of the OAuth protocol. Yarygina and Bage [7] reinforced that OpenID Connect provisions the user’s identity. OpenID Connect can be used in conjunction with OAuth 2.0 [4,8,35]. There is a difference between OpenID and OpenID Connect (OIDC). According to the OpenID Foundation website, “OpenID Connect performs many of the same tasks as OpenID 2.0, but does so in a way that is API-friendly, and usable by native and mobile applications” [41]. They also explain that “OpenID Connect defines optional mechanisms for robust signing and encryption. Whereas integration of OAuth 1.0a and OpenID 2.0 required an extension, in OpenID Connect, OAuth 2.0 capabilities are integrated with the protocol itself” [41].
- SSO (Single Sign-On): SSO allows a user to be authenticated only once when logging into a particular system, therefore, users can access all authorized resources and services on a system without needing another authentication [29,36]. According to Banati et al. [29], the main purpose of this mechanism is the exchange of authorization credentials and not the authentication by itself. The authors also reinforced that the mechanism guarantees unified authentication in microservices and the implementation of this feature can improve the user experience [33]. In the same way as the API Gateway, the implementation of an SSO server may cause a “Single Point of Failure”, that is, if there are problems in this system, every application can be compromised, as it centralizes all authentication of a system [36]. It is possible to implement a Single Sign-On system based on OAuth 2.0 [16,29,35].
- HTTPS: The Hyper Text Transfer Protocol Secure is defined by RFC 2818 [42]. It describes the use of HTTP over TLS (Transport Layer Security). Using the HTTPS protocol will ensure that the communication be encrypted [16]. It provides a channel between two hosts identified by certificates [30]. The use of HTTPS not just limited to encrypt data, but ensures that a given client is communication with whom he wants to [3].
- RBAC: Role-Based Access Control is used in authorization process [4]. It is a very know identity-based access control model [35]. The use of a role-based access control will increase the flexibility of the system because the role will define what access the client is allowed [22]. RBAC is user-centric access control model, it does not account for relationship between the requesting entity and the resource [7]. RBAC authorization roles can be incorporated into JWT tokens as an additional attribute [7].
- ABAC: Attribute-Based Access Control, based in the words of Preuveneers and Joosen [35] “grants access rights to subjects through the use of policies or rules that combine various types of attributes to facilitate user access to the right resources under the right conditions”. They complemented that it offers more expressivity and flexibility compared to another access control models such as RBAC. The primary goal of ABAC in the words of Yu et al. [25] is “an access control model is to fulfill the requirements of highly heterogeneous environments such as multi-cloud environment”. They also pointed the benefit of centralized security management and orchestration that will protect the application according to consistent policies. ABAC is recommended to be used when there is fine-grained authorization of resources, such as access to a specific API call [7].
- XACML: eXtensible Access Control Markup Language is defined by RFC 7061 [43]. According to this document, XACML “defines an architecture and a language for access control (authorization). The language consists of requests, responses, and policies”. It is used to create access control policies and can be used with OAuth 2.0 protocol [31]. Nehme et al. [31] proposed a model using XACML along with OAuth 2.0. In this case, OAuth 2.0 acts as an authorization service and XACML with policy administration and decision points. Barabanov and Marushin [8] discourage the use of XAML because it use a complicated syntax, causing more work for developers, adding to the fact that there were not many open-source integrations.
- HMAC: Hash-based Message Authentication Code is defined by RFC 2104. It provides a way to check the integrity of an information transmitted in a medium [44]. In the words of Mateus-Coelho et al., HMAC consists in “hash-based messaging code to sign the request”. According to the same authors, there are many examples that can be found in internet suggesting the use of HMAC over HTTP. HMAC algorithm can also be used to sign a JWT [22].
- SAML: The Security Assertion Markup Language (SAML) 2.0 is defined by RFC 7522 and is defined as an XML-based framework that allows identity and security information to be shared across security domains [45]. In a microservices environment, SAML is used to exchange user attributes stored at the identity provider [35]. Mateus-Coelho et al. [3] affirmed that “SAML and OpenID is perfect for Authentication and Authorization of someone’s on a system but it’s also great for service-to-service authentication as well”. Nevertheless, they admitted that SAML is complex when it is compared to other technologies such as Api Keys.
3.5. RQ.3.What Are the Main Open-Source Technology Solutions That Implement the Authentication and Authorization Mechanisms Identified in the Literature?
4. Discussions
Study Limitations
5. Final Remarks
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lewis, J.; Fowler, M. Microservices—A Definition of This New Archtectural Term; EA PAD: Redwood City, CA, USA, 2014. [Google Scholar]
- Merson, P. Microservices beyond the Hype: What You Gain and What You Lose; SEI Digital Library: San Diego, CA, USA, 2015. [Google Scholar]
- Mateus-Coelho, N.; Cruz-Cunha, M.; Ferreira, L.G. Security in microservices architectures. Procedia Comput. Sci. 2021, 181, 1225–1236. [Google Scholar] [CrossRef]
- Pereira-Vale, A.; Fernandez, E.B.; Monge, R.; Astudillo, H.; Márquez, G. Security in microservice-based systems: A Multivocal literature review. Comput. Secur. 2021, 103, 102200. [Google Scholar] [CrossRef]
- Pippal, S.K.; Kumari, A.; Kushwaha, D.S. CTES based Secure approach for Authentication and Authorization of Resource and Service in Clouds. In Proceedings of the 2011 2nd International Conference on Computer and Communication Technology (ICCCT-2011), Allahabad, India, 15–17 September 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 444–449. [Google Scholar]
- Halonen, T. Authentication and authorization in mobile environment. In Tik-110.501 Seminar on Network Security; Citeseer: Princeton, NJ, USA, 2000. [Google Scholar]
- Yarygina, T.; Bagge, A.H. Overcoming Security Challenges in Microservice Architectures. In Proceedings of the 12th IEEE International Symposium on Service-Oriented System Engineering, SOSE 2018 and 9th International Workshop on Joint Cloud Computing, JCC 2018, Bamberg, Germany, 26–29 March 2018; pp. 11–20. [Google Scholar] [CrossRef] [Green Version]
- Barabanov, A.; Makrushin, D. Authentication and authorization in microservice-based systems: Survey of architecture patterns. arXiv 2020, arXiv:2009.02114. [Google Scholar] [CrossRef]
- Sun, Y.; Nanda, S.; Jaeger, T. Security-as-a-service for microservices-based cloud applications. In Proceedings of the IEEE 7th International Conference on Cloud Computing Technology and Science, CloudCom 2015, Vancouver, BC, Canada, 30 November–3 December 2015; pp. 50–57. [Google Scholar] [CrossRef]
- Mehraj, S.; Banday, M.T. Establishing a Zero Trust Strategy in Cloud Computing Environment. In Proceedings of the 2020 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 22–24 January 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; Technical Report; National Institute of Standards and Technology: Gaithersburg, MA, USA, 2020. [Google Scholar]
- Rossi, B.; Russo, B.; Succi, G. Adoption of free/libre open source software in public organizations: Factors of impact. Inf. Technol. People 2012, 25, 156–187. [Google Scholar] [CrossRef] [Green Version]
- Hippel, E.V.; Krogh, G.V. Open source software and the “private-collective” innovation model: Issues for organization science. Organ. Sci. 2003, 14, 209–223. [Google Scholar] [CrossRef] [Green Version]
- Lavazza, L. Beyond Total Cost of Ownership: Applying Balanced Scorecards to Open-Source Software. In Proceedings of the International Conference on Software Engineering Advances (ICSEA 2007), Cap Esterel, France, 25–31 August 2007; p. 74. [Google Scholar] [CrossRef]
- Xu, R.; Jin, W.; Kim, D. Microservice security agent based on API gateway in edge computing. Sensors 2019, 19, 4905. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Krämer, M.; Frese, S.; Kuijper, A. Implementing secure applications in smart city clouds using microservices. Future Gener. Comput. Syst. 2019, 99, 308–320. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; EBSE: Goyang, Korea, 2007. [Google Scholar]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering—A systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Freitas, V. Parsifal, 2021. Available online: https://parsif.al (accessed on 17 October 2021).
- Wohlin, C. Guidelines for Snowballing in Systematic Literature Studies and a Replication in Software Engineering. In Proceedings of the 18th International Conference on Evaluation and Assessment in Software Engineering, EASE ’14. London, UK, 13–14 May 2014; Association for Computing Machinery: New York, NY, USA, 2014. [Google Scholar] [CrossRef]
- Safaryan, O.; Pinevich, E.; Roshchina, E.; Cherckesova, L.; Kolennikova, N. Information system development for restricting access to software tool built on microservice architecture. E3S Web Conf. 2020, 224, 01041. [Google Scholar] [CrossRef]
- Shulin, Y.; Jieping, H. Research on Unified Authentication and Authorization in Microservice Architecture. In Proceedings of the International Conference on Communication Technology Proceedings, ICCT, Nanning, China, 28–31 October 2020; pp. 1169–1173. [Google Scholar] [CrossRef]
- Jin, W.; Xu, R.; You, T.; Hong, Y.G.; Kim, D. Secure edge computing management based on independent microservices providers for gateway-centric IoT networks. IEEE Access 2020, 8, 187975–187990. [Google Scholar] [CrossRef]
- Nguyen, Q.; Baker, O. Applying Spring Security Framework and OAuth2 To Protect Microservice Architecture API. J. Softw. 2019, 14, 257–264. [Google Scholar] [CrossRef] [Green Version]
- Yu, D.; Jin, Y.; Zhang, Y.; Zheng, X. A survey on security issues in services communication of Microservices-enabled fog applications. Concurr. Comput. Pract. Exp. 2019, 31, e4436. [Google Scholar] [CrossRef]
- Bhutada, S.; Jyothi, K.K. Enhancing Security to the Microservice (MS) Architecture By Implementing Authentication and Authorization Service using Docker and Kubernetes. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 401–407. [Google Scholar]
- Nehme, A.; Jesus, V.; Mahbub, K.; Abdallah, A. Securing Microservices. IT Prof. 2019, 21, 42–49. [Google Scholar] [CrossRef]
- Pereira-Vale, A.; Marquez, G.; Astudillo, H.; Fernandez, E.B. Security mechanisms used in microservices-based systems: A systematic mapping. In Proceedings of the 2019 45th Latin American Computing Conference, CLEI 2019, Panama City, Panama, 30 September–4 October 2019. [Google Scholar] [CrossRef]
- Banati, A.; Kail, E.; Karoczkai, K.; Kozlovszky, M. Authentication and authorization orchestrator for microservice-based software architectures. In Proceedings of the 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 21–25 May 2018. [Google Scholar]
- Jander, K.; Braubach, L.; Pokahr, A. Defense-in-depth and Role Authentication for Microservice Systems. Procedia Comput. Sci. 2018, 130, 456–463. [Google Scholar] [CrossRef]
- Nehme, A.; Jesus, V.; Mahbub, K.; Abdallah, A. Fine-Grained Access Control for Microservices. Lect. Notes Comput. Sci. Incl. Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinform. 2019, 11358 LNCS, 285–300. [Google Scholar] [CrossRef]
- Richter, D.; Neumann, T.; Polze, A. Security considerations for microservice architectures. In Proceedings of the CLOSER 2018-Proceedings of the 8th International Conference on Cloud Computing and Services Science, Funchal, Portugal, 19–21 March 2018; pp. 608–615. [Google Scholar] [CrossRef] [Green Version]
- Cao, R.; Lu, S.; Wang, X.; Xiao, H.; Chi, X. Unified Account Management for High Performance Computing as a Service with Microservice Architecture. In Proceedings of the Unified Account Management for High Performance Computing as a Service with Microservice Architecture, Taipei, Taiwan, 16–23 March 2018. [Google Scholar]
- Lu, D.; Huang, D.; Walenstein, A.; Medhi, D. A Secure Microservice Framework for IoT. In Proceedings of the Proceedings-11th IEEE International Symposium on Service-Oriented System Engineering, SOSE 2017, San Francisco, CA, USA, 6–9 April 2017; pp. 9–18. [Google Scholar] [CrossRef]
- Preuveneers, D.; Joosen, W. Access Control with Delegated Authorization Policy Evaluation for Data-Driven Microservice Workflows. Future Internet 2017, 9, 58. [Google Scholar] [CrossRef] [Green Version]
- He, X.; Yang, X. Authentication and Authorization of End User in Microservice Architecture. J. Phys. Conf. Ser. 2017, 910, e012060. [Google Scholar] [CrossRef]
- Torkura, K.A.; Sukmana, M.I.; Meinel, C. Integrating continuous security assessments in microservices and cloud native applications. In Proceedings of the UCC 2017-Proceedings of the10th International Conference on Utility and Cloud Computing, Austin, TX, USA, 5–8 December 2017; pp. 171–180. [Google Scholar] [CrossRef]
- Dooley, K. Designing Large Scale Lans: Help for Network Designers; O’Reilly Media: Sebastopol, CA, USA, 2001. [Google Scholar]
- Hardt, D. Rfc 6749: The oauth 2.0 authorization framework. Internet Eng. Task Force IETF 2012, 10, 1–75. [Google Scholar]
- Jones, M.; Bradley, J.; Sakimura, N. Rfc 7519: Json Web Token (jwt); IETF: Fremont, CA, USA, 2015. [Google Scholar]
- Foundation, O. How Is OpenID Connect Different than OpenID 2.0? 2022. Available online: https://openid.net/connect/ (accessed on 4 February 2022).
- Rescorla, E. Rfc 2818: HTTP over TLS; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2000. [Google Scholar]
- Sinnema, R.; Wilde, E. Rfc 7061: eXtensible Access Control Markup Language (XACML) XML Media Type; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2013. [Google Scholar]
- Krawczyk, H.; Bellare, M.; Canetti, R. MAC: Keyed-Hashing for Message Authenticatio; Internet Engineering Task Force (IETF): Fremont, CA, USA, 1997. [Google Scholar]
- Campbell, B.; Mortimore, C.; Jones, M. Security Assertion Markup Language (SAML) 2.0 Profile for OAuth 2.0 Client Authentication and Authorization Grants; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2015. [Google Scholar]
- Pivotal. Spring Cloud. 2021. Available online: https://spring.io/projects/spring-cloud (accessed on 14 October 2021).
- Kit, G. Go Kit—A Toolkit for Microservices. 2022. Available online: https://gokit.io/ (accessed on 4 February 2022).
- Pallets Projects. Flask Web Development. 2022. Available online: https://flask.palletsprojects.com/ (accessed on 4 February 2022).
- Microsoft. NET Core. 2022. Available online: https://dotnet.microsoft.com/ (accessed on 4 February 2022).
- Kong. Kong API Gateway. 2021. Available online: https://konghq.com/kong (accessed on 14 October 2021).
- Garousi, V.; Felderer, M.; Mäntylä, M.V. Guidelines for including grey literature and conducting multivocal literature reviews in software engineering. Inf. Softw. Technol. 2019, 106, 101–121. [Google Scholar] [CrossRef] [Green Version]

| ID | Year | Title | Ref |
|---|---|---|---|
| S1 | 2021 | Security in microservice-based systems: A Multivocal literature review | [4] |
| S2 | 2021 | Security in microservices architectures | [3] |
| S3 | 2020 | Authentication and authorization in microservice-based systems: survey of architecture patterns | [8] |
| S4 | 2020 | Information system development for restricting access to software tool built on microservice architecture | [21] |
| S5 | 2020 | Research on Unified Authentication and Authorization in Microservice Architecture | [22] |
| S6 | 2020 | Secure Edge Computing Management Based on Independent Microservices Providers for Gateway-Centric IoT Networks | [23] |
| S7 | 2019 | Applying Spring Security Framework and OAuth 2.0 To Protect Microservice Architecture API | [24] |
| S8 | 2019 | A survey on security issues in services communication of Microservices-enabled fog applications | [25] |
| S9 | 2019 | Enhancing security to the MicroService (MS) architecture by implementing Authentication and Authorization (AA) service using Docker and Kubernetes | [26] |
| S10 | 2019 | Implementing secure applications in smart city clouds using microservices | [16] |
| S11 | 2019 | Microservice Security Agent Based On API Gateway in Edge Computing | [15] |
| S12 | 2019 | Securing Microservices | [27] |
| S13 | 2019 | Security Mechanisms Used in Microservices-Based Systems: A Systematic Mapping | [28] |
| S14 | 2018 | Authentication and authorization orchestrator for microservice-based software architectures | [29] |
| S15 | 2018 | Defense-in-depth and Role Authentication for Microservice Systems | [30] |
| S16 | 2018 | Fine-Grained Access Control for Microservices | [31] |
| S17 | 2018 | Overcoming Security Challenges in Microservice Architectures | [7] |
| S18 | 2018 | Security considerations for microservice architectures | [32] |
| S19 | 2018 | Unified account management for high performance computing as a service with microservice architecture | [33] |
| S20 | 2017 | A Secure Microservice Framework for IoT | [34] |
| S21 | 2017 | Access control with delegated authorization policy evaluation for data-driven microserviceworkflows | [35] |
| S22 | 2017 | Authentication and Authorization of End User in Microservice Architecture | [36] |
| S23 | 2017 | Integrating Continuous Security Assessments in Microservices and Cloud Native Applications | [37] |
| S24 | 2015 | Security-as-a-Service for Microservices-Based Cloud Applications | [9] |
| ID | AQ1 | AQ2 | AQ3 | AQ4 | AQ5 | Total |
|---|---|---|---|---|---|---|
| S1 | 1 | 1 | 1 | 1 | 1 | 5.0 |
| S8 | 1 | 0.5 | 1 | 1 | 1 | 4.5 |
| S16 | 1 | 1 | 1 | 1 | 0.5 | 4.5 |
| S23 | 1 | 1 | 1 | 0.5 | 1 | 4.5 |
| S17 | 1 | 1 | 1 | 1 | 0.5 | 4.5 |
| S21 | 1 | 0.5 | 0.5 | 1 | 1 | 4.0 |
| S5 | 1 | 0 | 1 | 1 | 1 | 4.0 |
| S6 | 1 | 0.5 | 0.5 | 1 | 1 | 4.0 |
| S13 | 1 | 1 | 1 | 1 | 0 | 4.0 |
| S7 | 1 | 0.5 | 0.5 | 0.5 | 1 | 3.5 |
| S3 | 1 | 0 | 1 | 1 | 0.5 | 3.5 |
| S15 | 0.5 | 0 | 1 | 1 | 1 | 3.5 |
| S10 | 1 | 0.5 | 1 | 1 | 0 | 3.5 |
| S11 | 1 | 0 | 0.5 | 1 | 1 | 3.5 |
| S20 | 1 | 1 | 0.5 | 0.5 | 0 | 3.0 |
| S14 | 1 | 0 | 1 | 1 | 0 | 3.0 |
| S12 | 1 | 0 | 1 | 1 | 0 | 3.0 |
| S2 | 1 | 0 | 1 | 1 | 0 | 3.0 |
| S19 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 3.0 |
| S4 | 0.5 | 0 | 1 | 0.5 | 0.5 | 2.5 |
| S24 | 0.5 | 0.5 | 1 | 0.5 | 0 | 2.5 |
| S22 | 0.5 | 0 | 0.5 | 0.5 | 0.5 | 2.0 |
| S18 | 0.5 | 0 | 0.5 | 0.5 | 0 | 1.5 |
| S9 | 0 | 0 | 0.5 | 0.5 | 0 | 1.0 |
| 2015 | 2017 | 2018 | 2019 | 2020 | 2021 | |
|---|---|---|---|---|---|---|
| Number of Studies | 1 | 4 | 6 | 7 | 4 | 2 |
| Rating Average | 2.5 | 3.38 | 3.33 | 3.29 | 3.50 | 4.00 |
| Standard deviation | 0 | 1.1087 | 1.1255 | 1.1127 | 0.7071 | 1.4142 |
| Coefficient of variation | 0 | 0.3285 | 0.3376 | 0.3386 | 0.2020 | 0.3536 |
| Pos | Challenge | ID | Number of Occurrences |
|---|---|---|---|
| 1st | Communication between microservices | S1, S2, S3, S4, S7, S9, S10, S15, S16, S17, S18, S23, S24 | 13 |
| 2nd | Trust between microservices compromised by unauthorized access | S1, S2, S4, S6, S8, S12, S15, S16, S19, S21, S23, S24 | 12 |
| 3rd | Individual concern for each microservice | S1, S2, S5, S10, S12, S13, S15, S16, S21, S22, S23, S24 | 12 |
| 4th | Increased attack surface (compared to monolithic) | S1, S2, S3, S7, S8, S13, S14, S16, S17, S23 | 10 |
| 5th | Microservice access control | S5, S8, S10, S11, S14, S15, S19, S20, S21 | 9 |
| 6th | Authorization between services | S1, S7, S8, S15, S16, S17, S18, S21 | 8 |
| 7th | Lack of studies about microservices | S1, S2, S4, S8, S10, S13, S17 | 7 |
| 8th | Lack of security patterns in microservices | S1, S13, S15, S17, S20, S21 | 6 |
| 9th | Different teams working on different microservices must have the same understanding of security | S3, S15, S17, S20, S23 | 5 |
| 10th | Bypass on Api Gateway | S3, S4, S6, S12 | 4 |
| 11th | Intrusion detection/monitoring | S1, S12, S24 | 3 |
| 12th | Escalation of privileges | S2, S16, S24 | 3 |
| 13th | Lack of study demonstrating practical implementation of security in microservices | S7, S13, S23 | 3 |
| 14th | Coordinate authentication server with new microservices | S1, S22 | 2 |
| 15th | Lack of attention in attack reaction/recovery | S1, S13 | 2 |
| 16th | Token validation at each microservice request | S5, S6 | 2 |
| 17th | Public Images may be compromised | S1 | 1 |
| 18th | Many applications in commercial microservices without possibility to evaluate code | S4 | 1 |
| 19th | Use of authentication/authorization server that handles all microservices | S3 | 1 |
| 20th | Possibility of development in various technologies | S23 | 1 |
| Pos | Mechanism | ID | Number of Occurrences |
|---|---|---|---|
| 1° | OAuth 2.0 | S1, S3, S5, S6,S7, S8, S10, S11, S12, S13, S14, S15, S16, S17, S20, S21 | 16 |
| 2° | JWT | S1, S3, S4, S5, S6, S9, S11, S12, S13, S14, S15, S17, S21, S22 | 14 |
| 3° | API Gateway | S2, S3, S4, S5, S6, S11, S12, S13, S14, S16, S17, S19, S20, S22 | 14 |
| 4° | Single Sign-ON SSO | S1, S2, S9, S10, S14, S19, S21, S22 | 8 |
| 5° | OpenID Connect | S1, S3, S8, S12, S16, S17, S21 | 7 |
| 6° | HTTPS | S2, S10, S14, S15, S17, S19, S20 | 7 |
| 7° | RBAC | S1, S3, S5, S13, S14, S17, S21 | 7 |
| 8° | ABAC | S1, S8, S14, S17, S20, S21 | 6 |
| 9° | XACML | S1, S3, S13, S15, S16, S21 | 6 |
| 10° | HMAC | S2, S3, S5, S14, S21 | 5 |
| 11° | SAML | S1, S2, S13, S14, S21 | 5 |
| 12° | TLS | S1, S10, S14, S15, S16 | 5 |
| 13° | OAuth | S1, S5, S8, S16 | 4 |
| 14° | Multilevel Security | S1, S3, S13 | 3 |
| 15° | DAC | S14, S21 | 2 |
| 16° | IAM | S14, S21 | 2 |
| 17° | RSA | S5, S11 | 2 |
| 18° | SASL | S1, S13 | 2 |
| 19° | SSL | S2, S13 | 2 |
| 20° | MTLS | S1, S17 | 2 |
| 21° | OpenID | S2, S14 | 2 |
| 22° | API Keys | S2 | 1 |
| 23° | Captcha | S19 | 1 |
| 24° | CAS | S8 | 1 |
| 25° | X509 Certificates | S1 | 1 |
| 26° | EAS | S3 | 1 |
| 27° | ECDSA | S5 | 1 |
| 28° | GSI | S8 | 1 |
| 29° | IDS | S12 | 1 |
| 30° | LDAP | S8 | 1 |
| 31° | MFA | S19 | 1 |
| 32° | NGAC | S3 | 1 |
| 33° | PBAC | S1 | 1 |
| Open-Source | ID |
|---|---|
| Spring Security | S1, S4, S5, S7, S8 |
| Kong | S6, S11 |
| Spring Boot | S6, S7 |
| Gateway Zuul | S4, S5 |
| Eureka Server | S5 |
| Jadex | S15 |
| Jarvis | S1 |
| Lagom | S15 |
| VertX | S15 |
| Challenge | Mechanism | Open-Source |
|---|---|---|
| Increased attack surface (compared to monolithic) | API Gateway (S2, S3, S4, S6, S12, S13, S16, S17, S20, S22), OAuth 2.0 (S7, S12, S13), SSO (S14) | Spring (S4, S7), Kong (S6, S11) |
| Authorization between services | OAuth 2.0 (S1, S5, S6, S7, S8, S10, S12, S13, S14, S15, S16, S17, S21), SAML(S2), OpenID(S2, S14, S16, S17), JWT (S9, S12, S13, S14, S15, S17, S21) | Spring (S1, S5) |
| Bypass in Api Gateway | XACML (S3), NGAC (S3), JWT (S3, S6, S12), OpenID (S3, S12, S16), OAuth 2.0 (S3, S6, S12, S16), TLS (S3), IDS (S12) | Spring (S4), Kong (S6) |
| Communication between microservices | TLS (S1, S10, S14, S15), MTLS (S17), SSL (S2), HTTPS (S2, S10, S14, S15, S17, S20), SAML(S2, S14, S21), XACML (S16, S21), OpenID(S2, S3, S8, S16, S17), JWT (S4, S5, S6, S12, S13, S14,15, S16, S17, S21), OAuth 2.0 (S5, S6, S7, S8, S10, S13, S15, S17, S21), GSI (S8) | Spring (s5), Kong (S6) |
| Trust between microservices compromised by unauthorized access | JWT (S1, S3, S4, S5, S6, S9, S11, S12, S13, S14, S15, S17, S21, S22), OAuth 2.0 (S1, S3, S5, S6, S7, S8, S10, S11, S12, S13, S14, S15, S16, S17, S20, S21), OpenID Connect S1, S2, S3, S8, S12, S14, S16, S17, S21) | Spring (S4, S5) |
| Microservice Access Control | OAuth 2.0 (S1, S5, S8, S10, S11, S12, S13, S14, S15, S16, S20, S21), OpenID (S1, S2, S3, S8, S12, S14, S16), TLS(S1), MTLS(S1), SASL (S1), SSO (S1, S2), JWT (S1, S5, S11, S12, S13, S14, S15, S21), HMAC(S2, S21), ABAC (S8, S17, S20, S21), RBAC (S17, S21), CAS (S8), RSA (S11), XACML (S16), Captcha (S20), Multiple FA (S20), DAC (S21), IAM (S21) | Spring (S1, S5, S11) |
| Coordinate authentication server with new microservices | LDAP (S8), SSO (S1, S2, 10, S13, s14, S20, S21, S22), OAuth 2.0 (S12, S14, S16), OpenID (S12, S14, S16), | |
| Individual concern for each microservice | JWT (S1, S3, S4, S5, S6, S9, S11, S12, S13, S14, S15, S17, S21, S22), OAuth 2.0 (S1, S3, S5, S6, S7, S8, S10, S11, S12, S13, S14, S15, S16, S17, S20, S21), OpenID Connect (S1, S2, S3, S8, S12, S14, S16, S17, S21) | Spring (S4, S5) |
| Use of authentication/authorization server that handles all microservices | SSO (S1, S2, 10, S13, s14, S20, S21, S22), OAuth 2.0 (S12, S14, S16) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
de Almeida, M.G.; Canedo, E.D. Authentication and Authorization in Microservices Architecture: A Systematic Literature Review. Appl. Sci. 2022, 12, 3023. https://doi.org/10.3390/app12063023
de Almeida MG, Canedo ED. Authentication and Authorization in Microservices Architecture: A Systematic Literature Review. Applied Sciences. 2022; 12(6):3023. https://doi.org/10.3390/app12063023
Chicago/Turabian Stylede Almeida, Murilo Góes, and Edna Dias Canedo. 2022. "Authentication and Authorization in Microservices Architecture: A Systematic Literature Review" Applied Sciences 12, no. 6: 3023. https://doi.org/10.3390/app12063023
APA Stylede Almeida, M. G., & Canedo, E. D. (2022). Authentication and Authorization in Microservices Architecture: A Systematic Literature Review. Applied Sciences, 12(6), 3023. https://doi.org/10.3390/app12063023







