Blockchain-based Multifactor Authentication for Future 6G Cellular Networks: A Systematic Review
Abstract
:1. Introduction
2. Methodology
3. 6G Cellular Network
3.1. Concept and Development
3.2. Security Needs
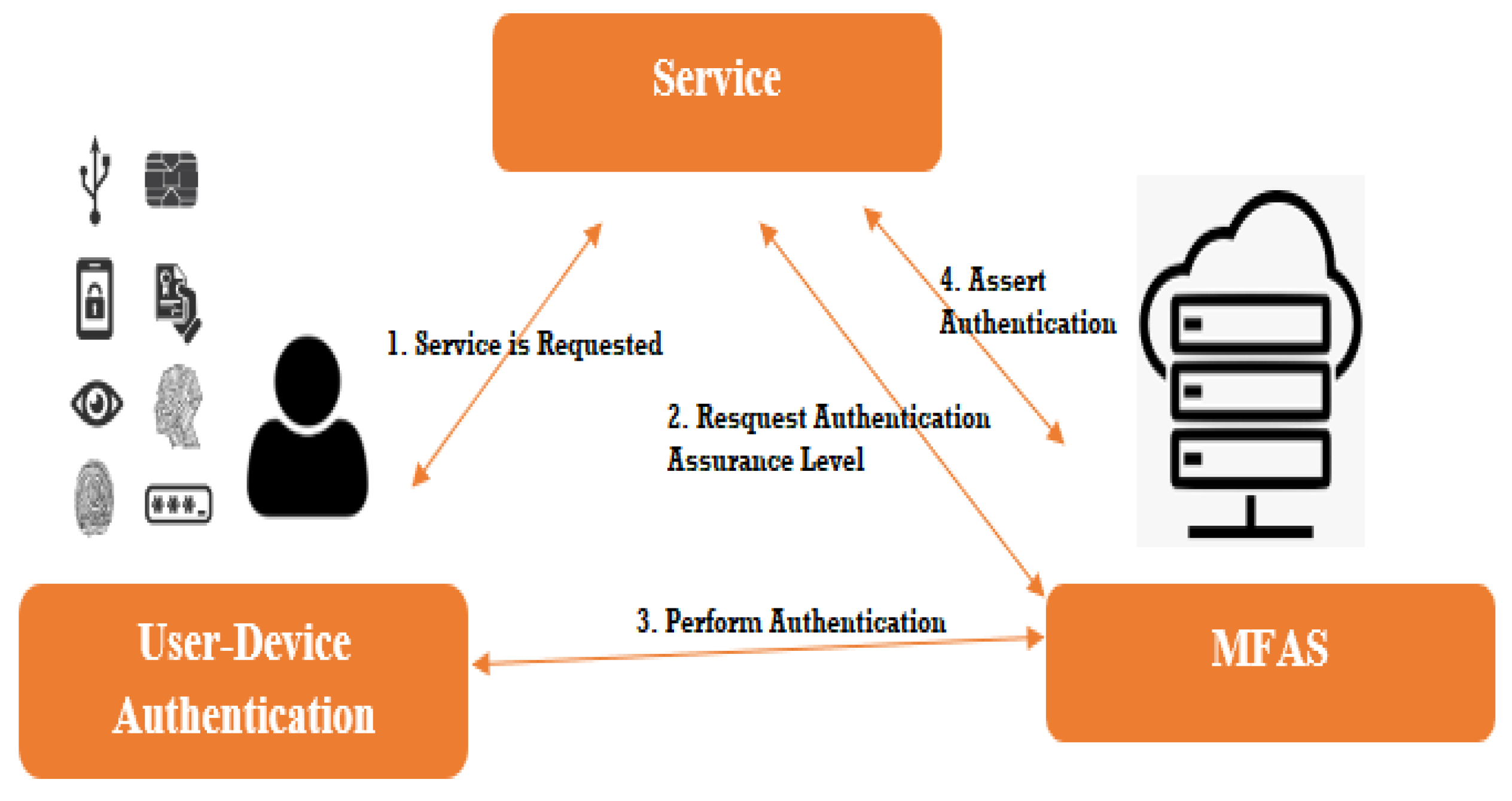
4. Multifactor Authentication
4.1. Concept and the Main Goal
4.2. Use of MFA
4.3. Advantages of MFA Implementation
5. Blockchain Technology
5.1. What Is Blockchain Technology?
5.2. How does Blockchain Work?
5.3. Benefits of Blockchain
6. Recent Exploration of MFA Applications and Blockchain Authentication
7. Observations
7.1. Recent Trends and Observations
7.2. Future Research Trends and Challenges
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, L.; Xu, B. Research on information security technology based on blockchain. In Proceedings of the 2018 IEEE 3rd International Conference on Cloud Computing and Big Data Analysis, Chengdu, China, 20–22 April 2018; pp. 380–384. [Google Scholar] [CrossRef]
- Ehrenberg, A.J.; King, J.L. Blockchain in Context. Inf. Syst. Front. 2020, 22, 29–35. [Google Scholar] [CrossRef]
- Abayomi-Zannu, T.P.; Odun-Ayo, I.A.; Barka, T.F. A Proposed Mobile Voting Framework Utilizing Blockchain Technology and Multi-Factor Authentication. J. Phys. Conf. Ser. 2019, 1378, 32104. [Google Scholar] [CrossRef]
- Zhu, Q.; Loke, S.W.; Trujillo-Rasua, R.; Jiang, F.; Xiang, Y. Applications of Distributed Ledger Technologies to the Internet of Things. ACM Comput. Surv. 2019, 52, 1–34. [Google Scholar] [CrossRef] [Green Version]
- Zheng, X.; Sun, S.; Mukkamala, R.R.; Vatrapu, R.; Ordieres-Meré, J. Accelerating Health Data Sharing: A Solution Based on the Internet of Things and Distributed Ledger Technologies. J. Med. Internet Res. 2019, 21, e13583. [Google Scholar] [CrossRef] [Green Version]
- Hathaliya, J.; Sharma, P.; Tanwar, S.; Gupta, R. Blockchain-Based Remote Patient Monitoring in Healthcare 4.0. In Proceedings of the IEEE 9th International Conference on Advanced Computing, IACC 2019, Tiruchirappalli, India, 13–14 December 2019; pp. 87–91. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Alqudaihi, K.S. A Lightweight Three-Factor Authentication Scheme for WHSN Architecture. Sensors 2020, 20, 6860. [Google Scholar] [CrossRef]
- Alharbi, E.T.; Alghazzawi, D. Two Factor Authentication Framework Using OTP-SMS Based on Blockchain ScaleUp View project Workflow Execution Time Predictions in Distributed Systems View project. Trans. Mach. Learn. Artif. Intell. 2019, 7, 17–27. [Google Scholar] [CrossRef]
- Khan, A.H.; Hassan, N.U.; Yuen, C.; Zhao, J.; Niyato, D.; Zhang, Y.; Poor, H.V. Blockchain and 6G: The Future of Secure and Ubiquitous Communication. IEEE Wirel. Commun. 2021, 1–8. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Liang, K. BPAS: Blockchain-Assisted Privacy-Preserving Authentication System for Vehicular Ad Hoc Networks. IEEE Trans. Ind. Inform. 2020, 16, 4146–4155. [Google Scholar] [CrossRef]
- Wu, L.; Du, X.; Wang, W.; Lin, B. An Out-of-band Authentication Scheme for Internet of Things Using Blockchain Technology. In Proceedings of the International Conference on Computing, Networking and Communications, Maui, HI, USA, 5–8 March 2018; pp. 769–773. [Google Scholar] [CrossRef]
- Maksymyuk, T.; Volosin, M.; Gazda, J.; Liyanage, M. Blockchain-based Decentralized Service Provisioning in Local 6G Mobile Networks. In Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems, Coimbra, Portugal, 15–17 November 2021; pp. 516–519. [Google Scholar] [CrossRef]
- Velliangiri, S.; Manoharn, R.; Ramachandran, S.; Rajasekar, V.R. Blockchain Based Privacy Preserving Framework for Emerging 6G Wireless Communications. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Imran, M.; Han, Z.; Hong, C.S. 6G Wireless Systems: A Vision, Architectural Elements, and Future Directions. IEEE Access 2020, 8, 147029–147044. [Google Scholar] [CrossRef]
- Kebande, V.R.; Awaysheh, F.M.; Ikuesan, R.A.; Alawadi, S.A.; Alshehri, M.D. A Blockchain-Based Multi-Factor Authentication Model for a Cloud-Enabled Internet of Vehicles. Sensors 2021, 21, 6018. [Google Scholar] [CrossRef] [PubMed]
- Şahan, S.; Ekici, A.F.; Bahtiyar, Ş. A Multi-Factor Authentication Framework for Secure Access to Blockchain. In Proceedings of the 2019 5th International Conference on Computer and Technology Applications, Istanbul, Turkey, 16–17 April 2019. [Google Scholar] [CrossRef]
- Siddiqi, M.A.; Yu, H.; Joung, J. 5G Ultra-Reliable Low-Latency Communication Implementation Challenges and Operational Issues with IoT Devices. Electronics 2019, 8, 981. [Google Scholar] [CrossRef] [Green Version]
- Gupta, R.; Reebadiya, D.; Tanwar, S. 6G-enabled Edge Intelligence for Ultra -Reliable Low Latency Applications: Vision and Mission. Comput. Stand. Interfaces 2021, 77, 103521. [Google Scholar] [CrossRef]
- Taher, B.H.; Liu, H.; Abedi, F.; Lu, H.; Yassin, A.A.; Mohammed, A.J. A Secure and Lightweight Three-Factor Remote User Authentication Protocol for Future IoT Applications. J. Sens. 2021, 2021, 8871204. [Google Scholar] [CrossRef]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Yu, J.; Wang, G.; Mu, Y.; Gao, W. An Efficient Generic Framework for Three-Factor Authentication with Provably Secure Instantiation. IEEE Trans. Inf. Forensics Secur. 2014, 9, 2302–2313. [Google Scholar] [CrossRef] [Green Version]
- Yrjola, S. How Could Blockchain Transform 6G towards Open Ecosystemic Business Models? In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, X.; Ng, D.W.K.; Yu, W.; Larsson, E.G.; Al-Dhahir, N.; Schober, R. Massive Access for 5G and Beyond. IEEE J. Sel. Areas Commun. 2021, 39, 615–637. [Google Scholar] [CrossRef]
- Prakasam, P.; Sayeed, S.; Ajayan, J. Guest editorials: P2P computing for 5G, beyond 5G (B5G) networks and internet-of-everything (IoE). Peer-to-Peer Netw. Appl. 2020, 14, 240–242. [Google Scholar] [CrossRef]
- Routray, S.K.; Mohanty, S. “Why 6G?”. arXiv 2019, arXiv:1903.04837v1. [Google Scholar]
- Dang, S.; Amin, O.; Shihada, B.; Alouini, M.-S. From a Human-Centric Perspective: What Might 6G Be? Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2020; Preprint November 2019. [Google Scholar] [CrossRef]
- Milovanovic, D.; Bojkovic, Z. 5G Mobile Networks: What is Next? Int. J. Commun. 2019, 4, 1–5. Available online: https://futurecomresearch.eu (accessed on 25 December 2021).
- Li, Y.; Yu, Y.; Susilo, W.; Hong, Z.; Guizani, M. Security and Privacy for Edge Intelligence in 5G and Beyond Networks: Challenges and Solutions. IEEE Wirel. Commun. 2021, 28, 63–69. [Google Scholar] [CrossRef]
- Dasgupta, D.; Roy, A.; Nag, A. Multi-Factor Authentication. Adv. User Authentication 2017, 185–233. [Google Scholar] [CrossRef]
- Dostalek, L. Multi-Factor Authentication Modeling. In Proceedings of the 2019 9th International Conference on Advanced Computer Information Technologies (ACIT), Ceske Budejovice, Czech Republic, 5–7 June 2019; pp. 443–446. [Google Scholar] [CrossRef]
- Shah, Y.; Choyi, V.; Subramanian, L. Multi-factor Authentication as a Service. In Proceedings of the 2015 3rd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering, MobileCloud 2015, San Francisco, CA, USA, 30 March–3 April 2015; pp. 144–150. [Google Scholar] [CrossRef]
- Cardoso, J.A.A.; Ishizu, F.T.; De Lima, J.T.; Pinto, J.D.S. Blockchain Based MFA Solution: The use of hydro raindrop MFA for information security on WordPress websites. Braz. J. Oper. Prod. Manag. 2019, 16, 281–293. [Google Scholar] [CrossRef]
- Gupta, R.; Kumari, A.; Tanwar, S. A taxonomy of blockchain envisioned edge-as-a-connected autonomous vehicles. Trans. Emerg. Telecommun. Technol. 2021, 32, e4009. [Google Scholar] [CrossRef]
- Yue, K.; Zhang, Y.; Chen, Y.; Li, Y.; Zhao, L.; Rong, C.; Chen, L. A Survey of Decentralizing Applications via Blockchain: The 5G and Beyond Perspective. IEEE Commun. Surv. Tutor. 2021, 23, 2191–2217. [Google Scholar] [CrossRef]
- Regulation, I. Commission Implementing Regulation (EU) 2015/2082 and 2015/2083 of 18 November 2015 Concerning the Non-Approval of Arctium. Regulation (EU). 2015. Available online: https://www.legislation.gov.uk/eur/2015/2082/adopted (accessed on 25 December 2021).
- Das, S.; Wang, B.; Tingle, Z.; Camp, L.J. Evaluating User Perception of Multi-Factor Authentication: A Systematic Review. arXiv 2019, arXiv:1908.05901v1. [Google Scholar]
- Javed, Y.; Khan, A.S.; Qahar, A.; Abdullah, J. Preventing DoS attacks in IoT using AES. J. Telecommun. Electron. Comput. Eng. 2017, 9, 55–60. [Google Scholar]
- Henricks, A.; Kettani, H. On Data Protection Using Multi-Factor Authentication. In Proceedings of the 2019 International Conference on Information System and System Management, Rabat, Morocco, 14–16 October 2019; PervasiveHealth: Pervasive Computing Technologies for Healthcare. pp. 1–4. [Google Scholar] [CrossRef]
- Copeland, M.; Jacobs, M. Reduce Cyber Security Vulnerabilities: Identity Layer. In Cyber Security on Azure; Apress: Berkeley, CA, USA, 2020; pp. 3–35. [Google Scholar] [CrossRef]
- Hess, E.M.; Tolbert, M.M.; Nascimento, M.C. Vulnerabilities of Multi-Factor Authentication in Modern Computer Networks. May 2021. Available online: https://digital.wpi.edu/concern/student_works/5d86p313s?locale=en (accessed on 25 December 2021).
- Alnahari, W.; Quasim, M.T. Authentication of IoT Device and IoT Server Using Security Key. In Proceedings of the 2021 International Congress of Advanced Technology and Engineering (ICOTEN), Taiz, Yemen, 4–5 July 2021; Research Square. pp. 1–9. [Google Scholar] [CrossRef]
- Khan, A.S.; Javed, Y.; Saqib, R.M.; Ahmad, Z.; Abdullah, J.; Zen, K.; Abbasi, I.A.; Khan, N.A. Lightweight Multifactor Authentication Scheme for NextGen Cellular Networks. IEEE Access 2022, 10, 31273–31288. [Google Scholar] [CrossRef]
- Dlamini, M.T.; Venter, H.S.; Eloff, J.; Blackledge, J.M.; Chetty, K. Securing Cloud Computing’ s Blind-Spots Using Strong and Risk-Based MFA. Association for Information Systems AIS Electronic Library (AISeL). 2016. Available online: http://aisel.aisnet.org/confirm2016/22 (accessed on 25 December 2021).
- Das, S.; Kim, A.; Camp, L.J. Short Paper: Organizational Security: Implementing a Risk-Reduction-Based Incentivization Model for MFA Adoption. In Proceedings of the International Conference on Financial Cryptography and Data Security, Virtual, 1–5 March 2021; pp. 406–413. [Google Scholar] [CrossRef]
- Abiew, N.A.K.; Jnr, M.D.; Banning, S.O. Design and Implementation of Cost Effective Multi-factor Authentication Framework for ATM Systems. Asian J. Res. Comput. Sci. 2020, 5, 7–20. [Google Scholar] [CrossRef]
- Khan, A.S.; Abdullah, J.; Zen, K.; Tarmizi, S. Secure and Scalable Group Rekeying for Mobile Multihop Relay Network. Adv. Sci. Lett. 2017, 23, 5242–5245. [Google Scholar] [CrossRef]
- Khan, A.S. Secure and efficient distributed relay-based rekeying algorithm for group communication in mobile multihop relay network. Int. J. Commun. Netw. Inf. Secur. 2014, 6, 189. [Google Scholar]
- Khan, N.; Johari, A.; Adnan, S. A Taxonomy Study of XSS Vulnerabilities. Asian J. Inf. Technol. 2017, 16, 169–177. [Google Scholar]
- Sanyal, S.; Tiwari, A.; Sanyal, S. A Multifactor Secure Authentication System for Wireless Payment. Adv. Inf. Knowl. Process. 2010, 53, 341–369. [Google Scholar] [CrossRef] [Green Version]
- Sinigaglia, F.; Carbone, R.; Costa, G.; Zannone, N. A survey on multi-factor authentication for online banking in the wild. Comput. Secur. 2020, 95, 101745. [Google Scholar] [CrossRef]
- Kennedy, E.; Millard, C. Data security and multi-factor authentication: Analysis of requirements under EU law and in selected EU Member States. Comput. Law Secur. Rev. 2016, 32, 91–110. [Google Scholar] [CrossRef]
- Bruun, A.; Jensen, K.; Kristensen, D. Usability of Single- and Multi-Factor Authentication Methods on Tabletops: A Comparative Study; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2014; pp. 299–306. [Google Scholar] [CrossRef] [Green Version]
- Maciej, B.; Imed, E.F.; Kurkowski, M. Multifactor Authentication Protocol in a Mobile Environment. IEEE Access 2019, 7, 157185–157199. [Google Scholar] [CrossRef]
- Ometov, A.; Petrov, V.; Bezzateev, S.; Andreev, S.; Koucheryavy, Y.; Gerla, M. Challenges of Multi-Factor Authentication for Securing Advanced IoT Applications. IEEE Netw. 2019, 33, 82–88. [Google Scholar] [CrossRef]
- Kinai, A.; Otieno, F.; Bore, N.; Weldemariam, K. Multi-factor authentication for users of non-internet based applications of blockchain-based platforms. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; pp. 525–531. [Google Scholar] [CrossRef]
- Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-Factor Authentication: A Survey. Cryptography 2018, 2, 1. [Google Scholar] [CrossRef] [Green Version]
- Khan, A.S.; Javed, Y.; Abdullah, J.; Zen, K. Trust-based lightweight security protocol for device to device multihop cellular communication (TLwS). J. Ambient Intell. Humaniz. Comput. 2021, 1–18. [Google Scholar] [CrossRef]
- Hewa, T.; Gur, G.; Kalla, A.; Ylianttila, M.; Bracken, A.; Liyanage, M. The Role of Blockchain in 6G: Challenges, Opportunities and Research Directions. In Proceedings of the 2020 2nd 6G Wireless Summit 2020: Gain Edge for the 6G Era, (6G SUMMIT), Levi, Finland, 17–20 March 2020. [Google Scholar] [CrossRef]
- Nguyen, T.; Tran, N.; Loven, L.; Partala, J.; Kechadi, M.-T.; Pirttikangas, S. Privacy-Aware Blockchain Innovation for 6G: Challenges and Opportunities. In Proceedings of the 2nd 6G Wireless Summit 2020: Gain Edge for the 6G Era, 6G SUMMIT 2020, Levi, Finland, 17–20 March 2020. [Google Scholar] [CrossRef]
- Gürkaynak, G.; Yılmaz, I.; Yeşilaltay, B.; Bengi, B. Intellectual property law and practice in the blockchain realm. Comput. Law Secur. Rev. 2018, 34, 847–862. [Google Scholar] [CrossRef]
- Teufel, B.; Sentic, A.; Barmet, M. Blockchain energy: Blockchain in future energy systems. J. Electron. Sci. Technol. 2019, 17, 100011. [Google Scholar] [CrossRef]
- Khan, N.; Abdullah, J.; Khan, A.S. Towards vulnerability prevention model for web browser using interceptor approach. In Proceedings of the 2015 9th International Conference on IT in Asia (CITA), Sarawak, Malaysia, 4–5 August 2015. [Google Scholar] [CrossRef]
- Peters, G.W.; Panayi, E. Understanding modern banking ledgers through blockchain technologies: Future of transaction processing and smart contracts on the internet of money. In Banking beyond Banks and Money; New Economic Windows; Springer: Cham, Switzerland, 2016; pp. 239–278. [Google Scholar] [CrossRef] [Green Version]
- Erdem, A.; Yildirim, S.; Angin, P. Blockchain for Ensuring Security, Privacy, and Trust in IoT Environments: The State of the Art. In Security, Privacy and Trust in the IoT Environment; Springer: Cham, Switzerland, 2019; pp. 97–122. [Google Scholar] [CrossRef]
- Khan, N.; Abdullah, J.; Khan, A.S. Defending Malicious Script Attacks Using Machine Learning Classifiers. Wirel. Commun. Mob. Comput. 2017, 2017, 5360472. [Google Scholar] [CrossRef]
- Gatteschi, V.; Lamberti, F.; Demartini, C.; Pranteda, C.; Santamaria, V. To Blockchain or Not to Blockchain: That Is the Question. IT Prof. 2018, 20, 62–74. [Google Scholar] [CrossRef]
- Andolfatto, D. Blockchain: What it is, what it does, and why you probably don’t need one. Fed. Reserv. Bank St. Louis Rev. 2018, 100, 87–95. [Google Scholar] [CrossRef] [Green Version]
- Khan, N.; Abdullah, J.; Khan, A.S. A Dynamic Method of Detecting Malicious Scripts Using Classifiers. Adv. Sci. Lett. 2017, 23, 5352–5355. [Google Scholar] [CrossRef]
- Vishwa, A.; Hussain, F.K. A Blockchain based approach for multimedia privacy protection and provenance. In Proceedings of the 2018 IEEE Symposium Series on Computational Intelligence (SSCI), Bangalore, India, 18–21 November 2018; pp. 1941–1945. [Google Scholar] [CrossRef]
- Meunier, S. Blockchain 101: What is blockchain and how does this revolutionary technology work? In Transforming Climate Finance and Green Investment with Blockchains; Academic Press: Cambridge, MA, USA, 2018; pp. 23–34. [Google Scholar] [CrossRef]
- Pilkington, M. Blockchain Technology: Principles and Applications. In Research Handbook on Digital Transformations; Xavier, F., Zhegu, O.M., Eds.; Edward Elgar Publishing: London, UK, 2015; pp. 225–253. [Google Scholar] [CrossRef] [Green Version]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2018, 57, 2117–2135. [Google Scholar] [CrossRef] [Green Version]
- Xiaolong, H.; Huiqi, Z.; Lunchao, Z.; Nazir, S.; Jun, D.; Khan, A.S. Soft Computing and Decision Support System for Software Process Improvement: A Systematic Literature Review. Sci. Program. 2021, 2021, 7295627. [Google Scholar] [CrossRef]
- Kersten, W.; Blecker, T.; Ringle, C.M. Digitalization in Supply Chain Management and Logistics: Smart and Digital Solutions for an Industry 4.0 Environment. Proc. Hambg. Int. Conf. Logist. 2017, 23, 533. [Google Scholar] [CrossRef]
- Zubair, S.; Fisal, N.; Abazeed, M.B.; Salihu, B.A.; Khan, A.S. Lightweight distributed geographical: A lightweight distributed protocol for virtual clustering in geographical forwarding cognitive radio sensor networks. Int. J. Commun. Syst. 2015, 28, 1–18. [Google Scholar] [CrossRef]
- Niranjanamurthy, M.; Nithya, B.N.; Jagannatha, S. Analysis of Blockchain technology: Pros, cons and SWOT. Cluster Comput. 2019, 22, 14743–14757. [Google Scholar] [CrossRef]
- Faroukhi, A.Z.; El Alaoui, I.; Gahi, Y.; Amine, A. An Adaptable Big Data Value Chain Framework for End-to-End Big Data Monetization. Big Data Cogn. Comput. 2020, 4, 34. [Google Scholar] [CrossRef]
- Lin, W.; Yin, X.; Wang, S.; Khosravi, M.R. A Blockchain-enabled decentralized settlement model for IoT data exchange services. Wirel. Networks 2020, 1–15. [Google Scholar] [CrossRef]
- Xu, R.; Nikouei, S.Y.; Nagothu, D.; Fitwi, A.; Chen, Y. BlendSPS: A BLockchain-ENabled Decentralized Smart Public Safety System. Smart Cities 2020, 3, 928–951. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE 6th International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar] [CrossRef]
- Khan, A.S.; Lenando, H.; Abdullah, J.; Bin Jambli, M.N. Lightweight Message Authentication Protocol for Mobile Multihop Relay Networks. Int. Rev. Comput. Softw. (IRECOS) 2014, 9, 1720. [Google Scholar] [CrossRef]
- Hofmann, F.; Wurster, S.; Ron, E.; Bohmecke-Schwafert, M. The immutability concept of blockchains and benefits of early standardization. In Proceedings of the 2017 ITU Kaleidoscope Academic Conference: Challenges for a Data-Driven Society (ITU K), Nanjing, China, 27–29 November 2017. [Google Scholar] [CrossRef]
- Kim, S. Blockchain for a Trust Network Among Intelligent Vehicles. Adv. Comput. 2018, 111, 43–68. [Google Scholar] [CrossRef]
- Khan, A.S.; Javed, Y.; Abdullah, J.; Nazim, J.M.; Khan, N. Security issues in 5G device to device communication. IJCSNS 2017, 17, 366. [Google Scholar]
- Eskandari, S.; Barrera, D.; Stobert, E.; Clark, J. A First Look at the Usability of Bitcoin Key Management. arXiv 2018, arXiv:1802.04351. [Google Scholar] [CrossRef] [Green Version]
- Dildar, M.S.; Khan, N.; Bin Abdullah, J.; Khan, A.S. Effective way to defend the hypervisor attacks in cloud computing. In Proceedings of the 2017 2nd International Conference on Anti-Cyber Crimes, ICACC 2017, Abha, Saudi Arabia, 26–27 March 2017; pp. 154–159. [Google Scholar] [CrossRef]
- Chan, K.Y.; Abdullah, J.; Shahid, A. A Framework for Traceable and Transparent Supply Chain Management for Agri-food Sector in Malaysia using Blockchain Technology. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef] [Green Version]
- Balan, K.; Khan, A.S.; Julaihi, A.A.; Tarmizi, S.; Pillay, K.S.; Abdulrazak, L.F.; Sallehudin, H. RSSI and Public Key Infrastructure based Secure Communication in Autonomous Vehicular Networks. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 298–304. [Google Scholar] [CrossRef] [Green Version]
- Aqeel, S.; Khan, A.S.; Ahmad, Z.; Abdullah, J. A comprehensive study on DNA based Security scheme Using Deep Learning in Healthcare. EDP Audit. Control. Secur. Newsl. 2021, 1–17. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2020, 32, e4150. [Google Scholar] [CrossRef]
- Espitia, A.; Ortega, K.; Romero, E.; Jaramillo, I. Authentication and digital signature USB device for telemedicine applications. In Proceedings of the 7th International Caribbean Conference on Devices, Circuits and Systems, ICCDCS, Cancun, Mexico, 28–30 April 2008. [Google Scholar] [CrossRef]
- Shin, S.; Kwon, T. A Privacy-Preserving Authentication, Authorization, and Key Agreement Scheme for Wireless Sensor Networks in 5G-Integrated Internet of Things. IEEE Access 2020, 8, 67555–67571. [Google Scholar] [CrossRef]
- Ni, J.; Lin, X.; Shen, X.S. Efficient and Secure Service-Oriented Authentication Supporting Network Slicing for 5G-Enabled IoT. IEEE J. Sel. Areas Commun. 2018, 36, 644–657. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Nisar, K.; Haider, I.; Hassan, R.; Haque, M.; Tarmizi, S.; Rodrigues, J. Anomaly Detection Using Deep Neural Network for IoT Architecture. Appl. Sci. 2021, 11, 7050. [Google Scholar] [CrossRef]
- Huang, X.; Xiang, Y.; Bertino, E.; Zhou, J.; Xu, L. Robust Multi-Factor Authentication for Fragile Communications. IEEE Trans. Dependable Secur. Comput. 2014, 11, 568–581. [Google Scholar] [CrossRef]
- Luo, Y.; Cao, J.; Ma, M.; Li, H.; Niu, B.; Li, F. DIAM: Diversified Identity Authentication Mechanism for 5G Multi-Service System. In Proceedings of the 2019 International Conference on Computing, Networking and Communications, ICNC 2019, Honolulu, HI, USA, 18–21 February 2019; pp. 418–424. [Google Scholar] [CrossRef]
- Luo, Y.; Li, H.; Ma, R.; Guo, Z. A Composable Multifactor Identity Authentication and Authorization Scheme for 5G Services. Secur. Commun. Netw. 2021, 2021, 6697155. [Google Scholar] [CrossRef]
- Wong, A.M.-K.; Hsu, C.-L.; Le, T.-V.; Hsieh, M.-C.; Lin, T.-W. Three-Factor Fast Authentication Scheme with Time Bound and User Anonymity for Multi-Server E-Health Systems in 5G-Based Wireless Sensor Networks. Sensors 2020, 20, 2511. [Google Scholar] [CrossRef]
- Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET. Sensors 2019, 19, 4954. [Google Scholar] [CrossRef] [Green Version]
- Khan, A.S.; Ahmad, Z.; Abdullah, J.; Ahmad, F. A Spectrogram Image-Based Network Anomaly Detection System Using Deep Convolutional Neural Network. IEEE Access 2021, 9, 87079–87093. [Google Scholar] [CrossRef]
- Khan, A.S.; Iqbal, A.M. Mobile Multihop Relay WIMAX Networks: A Security Perspectives; Universiti Malaysia Sarawak: Sarawak, Malaysia, 2018. [Google Scholar]
- Saqib, R.M.; Khan, A.S.; Javed, Y.; Ahmad, S.; Nisar, K.; Abbasi, I.A.; Haque, M.R.; Julaihi, A.A. Analysis and Intellectual Structure of the Multi-Factor Authentication in Information Security. Intell. Autom. Soft Comput. 2022, 32, 1633–1647. [Google Scholar] [CrossRef]
- Javed, Y.; Khan, S.; Khan, A.S.; Qahar, A.; Abdullah, J. Preventing DoS Attacks in IoT Using AES Static Analysis of Web Applications View project Cloud Robotics View project Preventing DoS Attacks in IoT Using AES. J. Telecommu-Nication Electron. Comput. Eng. 2018, 9, 3–11. Available online: https://www.researchgate.net/publication/322243661 (accessed on 29 December 2021).
- Javed, Y.; Khan, S.; Khan, A.S.; Qahar, A.; Abdullah, J. EEoP: A Lightweight Security Scheme over PKI in D2D Cellular Networks. J. Telecommun. Electron. Comput. Eng. (JTEC) 2017, 9, 99–105. Available online: https://jtec.utem.edu.my/jtec/article/view/3191 (accessed on 29 December 2021).
- Khan, N.; Ahmad, F.; Khan, S.; Abdullah, J.; Khan, N.; Julahi, A.A.; Tarmizi, S. Quantum-Elliptic curve Cryptography for Multihop Communication in 5G Networks. IJCSNS Int. J. Comput. Sci. Netw. Secur. 2017, 17, 357. [Google Scholar]
- Khan, A.S.; Lenando, H.; Abdullah, J.; Fisal, N. Secure Authentication and Key Management Protocols for Mobile Multihop WiMAX Networks. J. Teknol. 2015, 73, 75–81. [Google Scholar] [CrossRef] [Green Version]






| Study | Year | Systematic Study | Blockchain Focused | MFA Focused | 6G Focused | Future Trends |
|---|---|---|---|---|---|---|
| [9] | 2021 | ✓ | ✓ | × | ✓ | ✓ |
| [14] | 2020 | ✓ | ✓ | ✓ | ✓ | × |
| [13] | 2021 | ✓ | ✓ | ✓ | × | ✓ |
| [20] | 2020 | ✓ | ✓ | ✓ | ✓ | × |
| [22] | 2020 | ✓ | ✓ | × | ✓ | ✓ |
| This study | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Domain | Number of Papers |
|---|---|
| Networks (2G, 3G, 4G, 5G, 6G) | 8 |
| Blockchain | 30 |
| Multifactor Authentication | 28 |
| Data, Security, Reliability, or other issues | 7 |
| MFA Type | Process | Pros | Cons |
|---|---|---|---|
| Hardware OTP [37,38] |
|
|
|
| Authenticator Applications [16,39] |
|
|
|
| Soft Token Software Development Kits (SDKS) [15,16,39,40] |
|
|
|
| OTPS Based On SMS [29,36,41,42] |
|
|
|
| Hardware Tokens [29,31,32,36,39] |
|
|
|
| Study | Technologies Mentioned | Advantage/Contribution | Disadvantage/Gap | ||
|---|---|---|---|---|---|
| MFA | BC | 3/4/5G | |||
| [95] | ✓ | ✓ | A robust and effective system for fragile communications between two nodes. | Vulnerable to access attacks. | |
| [93] | ✓ | The authentication mechanism for 5G enabled IoT networks in the form of a service. | Not an MFA-based technique. | ||
| [96] | ✓ | ✓ | The flexible 3-factor authentication mechanism for various kinds of applications that are based on 5G multiservice systems. | Costly in terms of time efficiency. | |
| [92] | ✓ | ✓ | Provides a multifactor authentication procedure for WSNs in recent network applications and may be extendible to future network advancements such as 6G. | Vulnerable to the collision of users and desynchronization attacks. | |
| [98] | ✓ | ✓ | Multiple server technologies are used to ensure that performance is quick and transparent. | Technique still poses a communication cost as it integrates biometrics, password, and smart card authentication. | |
| [97] | ✓ | ✓ | An adaptable and decomposable 3-factor authentication system that can be applied simultaneously to ensure efficiency and speed. | Further testing and real-time application are required. | |
| [32] | ✓ | ✓ | ✓ | Hydro Raindrop multifactor authentication technology to conduct 2FA for WordPress. | Not experimental in nature. |
| [10] | ✓ | ✓ | ✓ | BPAS for ensuring accuracy as well as trust in the systems. | A lack of support for batch verification for an optimized verification in form of blocks of data and hence reduce the load on the resource consumption. |
| [15] | ✓ | ✓ | ✓ | Embedded Digital Signature-based MFA suitable technique for countering the adversarial attacks. | Overheads are high. |
| [8] | ✓ | ✓ | ✓ | More security to the authentication process as compared to SMS-based authentication protocols. | This system was claimed to be safer than SMS-based authentication mechanisms, but it was less efficient in terms of time efficiency. |
| [11] | ✓ | ✓ | ✓ | Flexible, secure, and reliable authentication. | The overheads of blockchain use, however, were high. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Asim, J.; Khan, A.S.; Saqib, R.M.; Abdullah, J.; Ahmad, Z.; Honey, S.; Afzal, S.; Alqahtani, M.S.; Abbas, M. Blockchain-based Multifactor Authentication for Future 6G Cellular Networks: A Systematic Review. Appl. Sci. 2022, 12, 3551. https://doi.org/10.3390/app12073551
Asim J, Khan AS, Saqib RM, Abdullah J, Ahmad Z, Honey S, Afzal S, Alqahtani MS, Abbas M. Blockchain-based Multifactor Authentication for Future 6G Cellular Networks: A Systematic Review. Applied Sciences. 2022; 12(7):3551. https://doi.org/10.3390/app12073551
Chicago/Turabian StyleAsim, Jamil, Adnan Shahid Khan, Rashad Mahmood Saqib, Johari Abdullah, Zeeshan Ahmad, Shehla Honey, Shehroz Afzal, Malak S. Alqahtani, and Mohamed Abbas. 2022. "Blockchain-based Multifactor Authentication for Future 6G Cellular Networks: A Systematic Review" Applied Sciences 12, no. 7: 3551. https://doi.org/10.3390/app12073551
APA StyleAsim, J., Khan, A. S., Saqib, R. M., Abdullah, J., Ahmad, Z., Honey, S., Afzal, S., Alqahtani, M. S., & Abbas, M. (2022). Blockchain-based Multifactor Authentication for Future 6G Cellular Networks: A Systematic Review. Applied Sciences, 12(7), 3551. https://doi.org/10.3390/app12073551






