Signature Split Method for a PQC-DSA Compliant with V2V Communication Standards
Abstract
:1. Introduction
1.1. Related Work
1.2. Contribution
2. Preliminaries
2.1. Post-Quantum Cryptography
2.2. Crystals-Dilithium
| Algorithm 1 Ditlihium.() |
| 1: := 2: := 3: := 0, := ⊥ 4: while := ⊥ do 5: := 6: 7: 8: := 9: := 10: := 11: if or or 12: then := ⊥ 13: else 14: := 15: if or the # of 1’s in is greater than w then := ⊥ 16: 17: return |
| Algorithm 2 Ditlihium. |
| 1: := 2: := 3: := 4: return and c := and # of 1’s in is |
2.3. Falcon
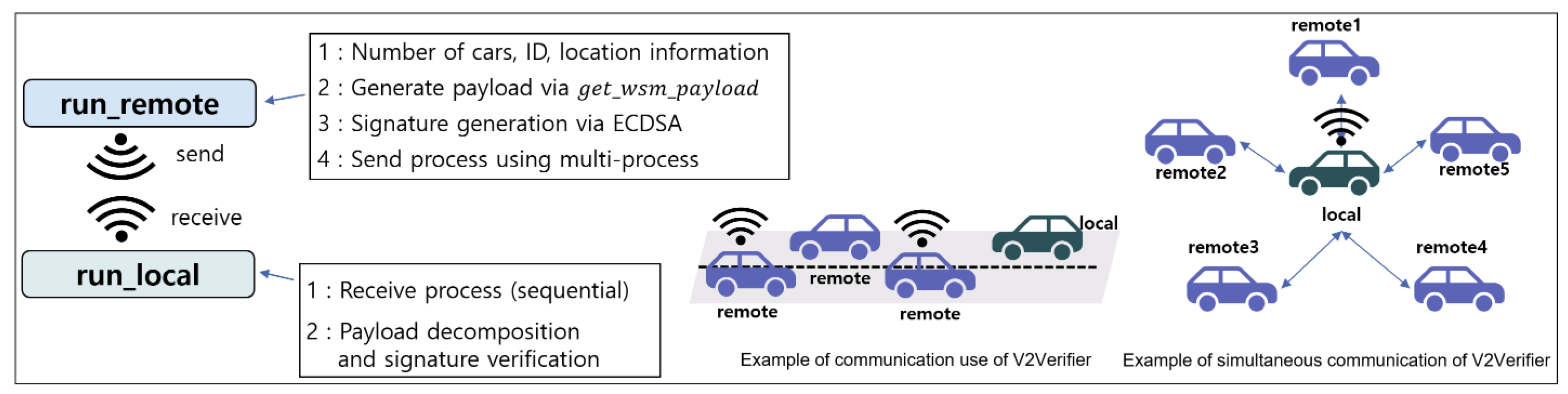
2.4. V2Verifier
- Security features from the IEEE 1609.2 standard for V2V security, including message signing and verification and V2V certificates.
- Dedicated short-range communication (DSRC)—adapted from the WiME Project’s IEEE 802.11p transceiver
- Cellular vehicle-to-everything (C-V2X)—based on the srsRAN project (formerly srsLTE) (temporarily not supported).
- run_remote“run_remote” API simultaneously generates as many payloads as the number of remote cars using a multiple processes and broadcasts the payloads to local car. Using “yml” module, 300 pieces of location information are sent in a text file unique to each remote car to the local car at 0.1 s intervals. Additionally, based on the time function of the “time” module, the payload generation time for 300 pieces of location information is measured. In this process, each specific payload of remote cars is generated by calling the internal “Get_wsm_payload” API. The payload has three components, Bytestring (communication flag), Wsm header (Wsm header), and IEEE 1609.data (IEEE standard protocol), and consists of a total of 16 pieces of information. It requires about 500 bytes, excluding signature length information and signature. Therefore, if the sum of the signature length information and the signature of PQC-DSA is less than 1500 bytes, then the WAVE protocol requirement of less than 2000 bytes is satisfied, and it is applicable to the WAVE protocol. This process maintains the IDs and locations of n cars in context. The payload generation process includes a signature to the current location. Moreover, when the payload is generated, it uses multiprocessing to send the payload to “run_local” API. The initial communication of between remote cars and local car involves the process of generating a key used for signing.
- run_localLocal car receives a payload containing the current position of remote cars. “run_local” API is always active in receive standby mode. It then goes through a signature verification process and deconstructs the payload when the verification is successful. If the signature verification succeeds, API disassembles payload, and the local car obtains the location information. If the signature verification fails, one waits for the next payload reception.
3. Proposed Simulation
3.1. Selection of Crypto Codes
3.2. Proposed Split Signature Transmission
- Naive split wayThe first method involves a very simple means for dividing the signature, which is to keep the size of the signature less than 1400 bytes, excluding the header information or payload (approximately 500 bytes). Please note that maximum packet size of the WAVE protocol is 2000 bytes. For example, depending on the level of security of the Crystals-Dilithium, signatures can be split into 2, 3, and 4 blocks (the signature sizes of Crystals-Dilithium are 2420, 3293, and 4595 bytes for security level 2, 3, and 5, respectively). We add an an 8-bit order-bit to the MSB of the partitioned block. Signature verification of Crystals-Dilithium adds a block alignment process, but this is not expensive because in the sorting process, only 4 blocks are searched based on security level 5. “Simple split way” is very simple, but not very good in terms of efficiency. As the length of the signature increases, the number of order-bits required for sorting increases; therefore, if an algorithm with a very large signature size is proposed in the future, such as SPHINCS+, the amount of signature that can actually be transmitted will decrease, which is an inefficient method.
- Split way for Crystals-DilithiumWe aim to analyze the structure of signature of Crystals-Dilithium and observe the signature length for each security level. Algorithm 1 shows the pseudocode of the overall structure of “Split way for Crystals-Dilithium”. As analyzed in Section 2.1, the signature consists of , h, and c. Since the combined sizes of c and h are less than 120 bytes, they can be composed of one block. In addition, since 2 × 640 bytes can be additionally assigned to its block, the first block can be composed of c, h, and two packed polynomials of . From the second block, we continue to construct two packed polynomials of . Based on security level 5, if we assign 1 bit to determine the first block and 2 bits to determine the order of each block, the order-bit, which is in the MSB of the block, can be composed of a total of 3 bits. Compared to the above “Simple split way” method, the number of blocks is not changed. However, this method has advantages in the long run. In V2Verifier, the local car receives multiple signature blocks in random order. At this time, the local car checks for the existence of the first block through MSB 1-bit, and if the first block c and h are divided, hint information is collected using h data. After this, the unpacking process is performed on the two packed polynomials of in the first block. If the received signature block is not the first block, the unpacking process can be started immediately because there are only two polynomials in the second and lower block. In the “Simple split way” approach, one can wait for the receipt of all signature blocks and start the verification process of Crystals-Dilithium after sorting the blocks. However, our method can start the signature verification process before all the blocks arrive. Since the process of checking the order-bit is the same as that in “Simple split way”, additional costs are not incurred and performance can be expected to increase. Therefore, our method is effective when a parallel process is introduced in the local car API or when the length of the signature is increased in the future with the rise of the security level.
3.3. Application Plan for V2Verifier
- Generating the payloadV2Verifier generates the payload in V2Verifier using “Get_wsm_payload” API. The payload consists of three components (Bytestring, Wsm-header, and IEE 1609.data) and a total of 16 pieces of information. The payload requires approximately 500 bytes, excluding signature length information and the signature.
- Generating key pair and signing the payloadGenerating the key pair process for generating the public and private keys for PQC-DSA is completed in the first session for local and remote cars. It does not work on session reconnect. Signing payload process generates a signature for the current location of the remote car. For satisfying the correctness of the verification of Crystals-Dilithium on V2Verifier, we used the “Split way for Crystals-Dilithium” for this process.
- Verifying the signature and decomposing the payloadIn the verifying signature process, only the signature block is extracted from the received payloads to verify the signature. In the case of Crystals-Dilithium, the process of checking or sorting the order of blocks is added. The decomposing payload process splits the payload, where the signature is validated in the verifying signature process. In “Split way for Crystals-Dilithium”, only the first received payload is split.
| Algorithm 3 Split Way for Crystals-Dilithium |
| Input: Param: - Basic-Safety Message: bsm, - public key: pk, - secret key: sk, - signature: , h, and c (k has a value of 4, 6, or 8 depending on the security level, respectively.), - payload: payload[k/2], - verification flag: flag, Func: - unpack API of Dilithium: Dilithium.Verify.unpack_sig, - align split signature: Align_sig 1: [run_remote] API 2: … (Generate bsm) 3: , h, and Dilithium.Sign(, ) 4: for to do 5: if i = 0 then 6: 7: else 8: 9: end if 10: Sending to "local car" 11: end for 12: … 13: [run_local] API 14: for to do 15: if there is no received payload then 16: return // waiting payload of next remote car 17: end if 18: Receiving payload[j] from "remote car" // random order 19: 20: if order < 4 then 21: Dilithium.Verify.unpack_sig_for_z(sig[j]) 22: else 23: Dilithium.Verify.unpack_sig_for_zch(sig[j]) 24: end if 25: end for 26: 27: Dilithium.Verify() // Verify API without unpack process 28: if == SUCCESS then 29: Decomposing 30: else 31: return // waiting payload of next remote car 32: end if 33: … |
4. Experiments
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Alagic, G.; Apon, D.; Cooper, D.; Dang, Q.; Dang, T.; Kelsey, J.; Lichtinger, J.; Miller, C.; Moody, D.; Peralta, R. Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process; NIST: Gaithersburg, MD, USA, 2022. [CrossRef]
- Schöffel, M.; Lauer, F.; Rheinländer, C.C.; Wehn, N. On the energy costs of post-quantum kems in tls-based low-power secure iot. In Proceedings of the International Conference on Internet-of-Things Design and Implementation, Charlottesvle, VA, USA, 18–21 May 2021; pp. 158–168. [Google Scholar]
- 1609.2.1-2020; IEEE Standard for Wireless Access in Vehicular Environments (WAVE)–Certificate Management Interfaces for End Entities (2020). IEEE: Piscataway, NJ, USA, 2020.
- Schwabe, P.; Stebila, D.; Wiggers, T. Post-quantum tls without handshake signatures. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual, 9–13 November 2020; pp. 1461–1480. [Google Scholar]
- Li, Y. An overview of the DSRC/WAVE technology. In Proceedings of the Quality, Reliability, Security and Robustness in Heterogeneous Networks: 7th International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness, QShine 2010, and Dedicated Short Range Communications Workshop, DSRC 2010, Houston, TX, USA, 17–19 November 2010; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Bindel, N. Suitability of 3rd Round Signature Candidates for Vehicle-to-Vehicle Communication. Available online: https://csrc.nist.gov/Presentations/2021/suitability-of-3rd-round-signaturecandidates-for (accessed on 18 April 2023).
- Lyubashevsky, V.; Ducas, L.; Kiltz, E.; Lepoint, T.; Schwabe, P.; Seiler, G.; Stehlé, D.; Bai, S. Crystals-Dillithium. 2022. Available online: https://pq-crystals.org/dilithium/index.shtml (accessed on 18 April 2023).
- Prest, T.; Fouque, P.-A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. Falcon. 2022. Available online: https://falcon-sign.info (accessed on 18 April 2023).
- Twardokus, G. Github Code of v2verifier. Available online: https://github.com/twardokus/v2verifier (accessed on 18 April 2023).
- Bürstinghaus-Steinbach, K.; Krauß, C.; Niederhagen, R.; Schneider, M. Post-quantum tls on embedded systems: Integrating and evaluating kyber and sphincs+ with mbed tls. In Proceedings of the 15th ACM Asia Conference on Computer and Communications Security, Taipei, Taiwan, 5–9 October 2020; pp. 841–852. [Google Scholar]
- Kim, Y.; Song, J.; Seo, S.C. Accelerating falcon on armv8. IEEE Access 2022, 10, 44446–44460. [Google Scholar] [CrossRef]
- Kim, Y.; Song, J.; Youn, T.; Seo, S.C. Crystals-dilithium on armv8. Secur. Commun. Netw. 2022, 2022, 5226390. [Google Scholar] [CrossRef]


| Crystals-Dilithium | Falcon | |||||
|---|---|---|---|---|---|---|
| Problem | Module-LWE | NTRU | ||||
| NIST Security Level | Public Key [B] | Secret Key [B] | Signature [B] | Public Key [B] | Secret Key [B] | Signature [B] |
| 1 (AES-128) | - | - | - | 897 | 1281 | 690 |
| 2 (SHA256) | 1312 | 2528 | 2420 | - | - | - |
| 3 (AES-192) | 1952 | 4000 | 3293 | - | - | - |
| 5 (AES-256) | 2592 | 4864 | 4595 | 1793 | 2305 | 1330 |
| Type | WAVE (IEEE 802.11p) | C-V2X (3GPP Rel.14) | eC-V2X (3GPP Rel.15) | 5G-V2X |
|---|---|---|---|---|
| Processing rate (Mbps) | 3∼27 | 10∼100 (Maximum 1000) | Maximum 2000 | |
| BSM packet size | 2000 | 400 (advanced: 12,000 ) | Platooning: 6000 Advanced: 12,000 Autonomous: 41,700 | |
| Maximum communication radius | 1 km | 320 m | 1 km | Platooning : 350 m Advanced : 700 m Autonomous : 1 km |
| End-to-end latency (ms) | 100 | 100 | 100 (platooning: 10) | Platooning: 25 Advanced: 100 Autonomous: 5 |
| Vehicle maximum relative speed (km/h) | 200 | 280 | 500 | |
| Correctness | 80∼95% | 90∼100% | 90∼100% | |
| Algorithm | Security | Ref | Correctness | This Work | Correctness |
|---|---|---|---|---|---|
| ECDSA (P-256) | 1 | 3.9 | ✓ | - | - |
| Crystals-Dilithium | 2 | 2.2 | ✓ | 1.9 | ✓ |
| 3 | 4.1 | ✓ | 2.4 | ✓ | |
| 5 | 4.7 | ✓ | 3.0 | ✓ | |
| Falcon | 1 | 14.3 | ✓ | 12.7 | ✓ |
| 5 | 38.9 | ✓ | 33.3 | ✓ |
| Algorithm | Security | Ref | Correctness | This Work | Correctness |
|---|---|---|---|---|---|
| ECDSA (P-256) | 1 | 3.9 | ✓ | - | - |
| Crystals-Dilithium | 2 | 2.8 | ✗ | 2.4 | ✓ |
| 3 | 5.2 | ✗ | 3.6 | ✓ | |
| 5 | 6.1 | ✗ | 4.5 | ✓ | |
| Falcon | 1 | 14.3 | ✓ | 12.7 | ✓ |
| 5 | 38.9 | ✓ | 33.3 | ✓ |
| Algorithm | Security | Ref | This Work |
|---|---|---|---|
| ECDSA (P-256) | 1 | - | |
| Crystals-Dilithium | 2 | ||
| 3 | |||
| 5 | |||
| Falcon | 1 | ||
| 5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, Y.; Seo, S.C. Signature Split Method for a PQC-DSA Compliant with V2V Communication Standards. Appl. Sci. 2023, 13, 5874. https://doi.org/10.3390/app13105874
Kim Y, Seo SC. Signature Split Method for a PQC-DSA Compliant with V2V Communication Standards. Applied Sciences. 2023; 13(10):5874. https://doi.org/10.3390/app13105874
Chicago/Turabian StyleKim, Youngbeom, and Seog Chung Seo. 2023. "Signature Split Method for a PQC-DSA Compliant with V2V Communication Standards" Applied Sciences 13, no. 10: 5874. https://doi.org/10.3390/app13105874
APA StyleKim, Y., & Seo, S. C. (2023). Signature Split Method for a PQC-DSA Compliant with V2V Communication Standards. Applied Sciences, 13(10), 5874. https://doi.org/10.3390/app13105874






