3.1. Research Question
As described above, the CNG cannot obtain information on the actual key because it is not directly receiving the key information during the encryption and decryption processes due to the fact that the key is processed through the handle obtained from the import and export processes (Question 1). Thus, when given the handle address of a key, the goal of this paper is to analyze the location of the actual key from the key handle address, namely to analyze the key storage mechanism (Question 2).
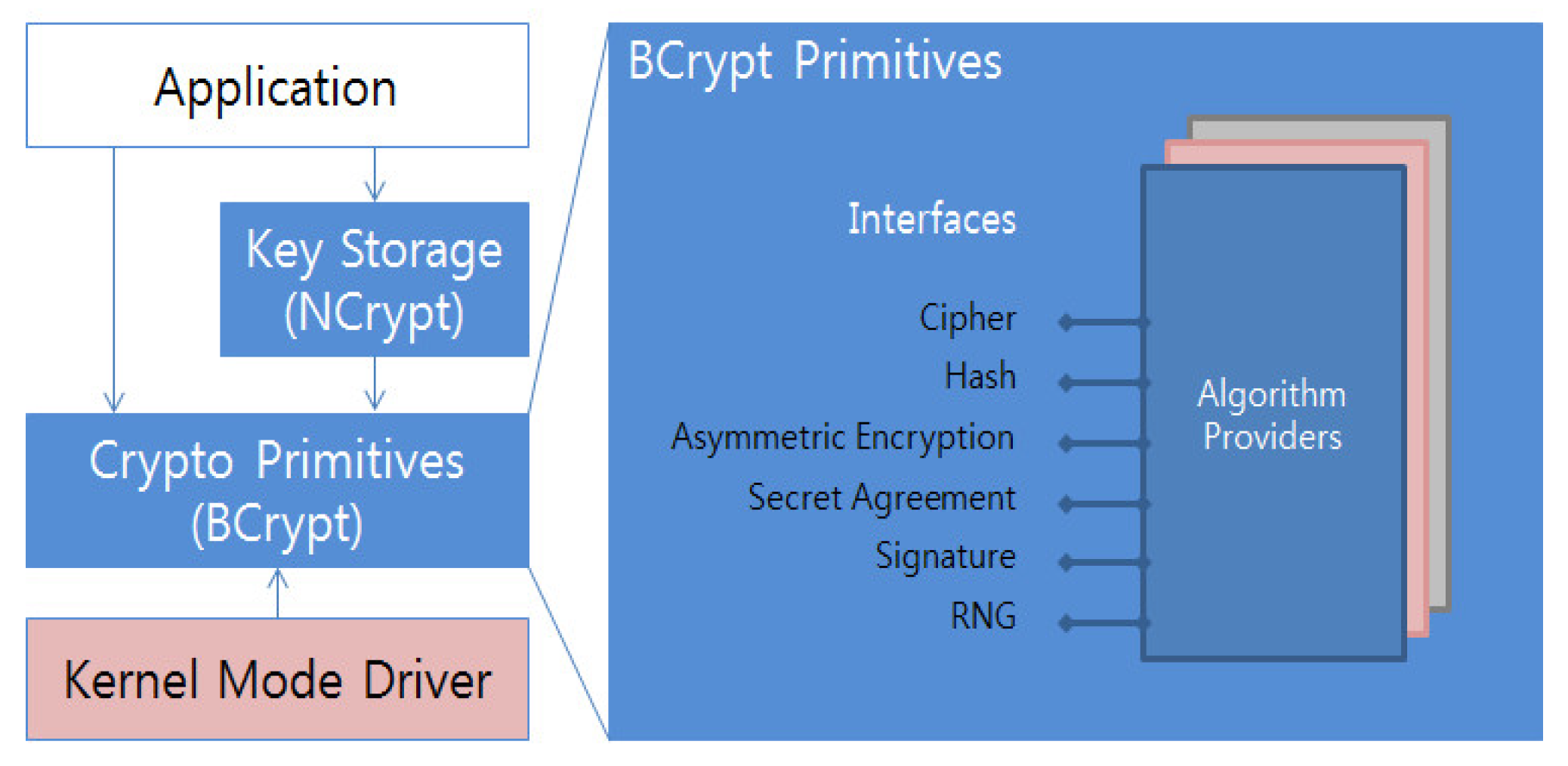
The functions related to encryption and decryption in CNG are classified into BCrypt, SSL, and NCrypt. The encryption and decryption functions of BCrypt are called BCryptEncrypt and BCryptDecrypt, respectively. The encryption and decryption functions of SSL are called SslEncryptPacket and SslDecryptPacket, respectively. The encryption and decryption functions of NCrypt are called NCryptEncrypt and NCryptDecrypt, respectively. In this paper, we analyze the key storage mechanism of NCrypt and the asymmetric-key-based RSA algorithm.
The analysis environment is based on Intel® Core™ i5-2410M CPU 2.30 GHz, 4 GB RAM, a PC installed with Microsoft Windows 7 Home Premium K operating system, CNG SDK 2.0, Windows SDK 7.1, and .NET Framework 4 installation, Visual Studio 2005 to implement proof-of-concept tools, CNG Demo Sample Code installation for CNG sample source code reference, and OllyDbg v1.10 reverse engineering tool to analyze the key storage mechanism.
To analyze the key location in NCrypt-related functions, we first implemented a sample program based on the RSA algorithm where the plain text is “SignThis” and the key is “test2” by referring to the example of Windows CNG Demo Sample Code. As a result, the implemented program executes encryption and decryption operations, as shown in
Figure 3, and outputs the result, as shown in
Figure 4.
To analyze the key location, we confirmed the related parameters of the NCryptDecrypt function after setting a breakpoint on the NCryptDecrypt function. As a result, we found that the first parameter is the address associated with the key handle, as shown in
Figure 5. Nevertheless, there was no specific information related to the key, as shown in
Figure 6, after checking the key handle address 0x0051A288 in detail.
Since there is no way to obtain key-related information through the key handle address, we, therefore, derived clues about the key location by checking the key-related information when the key is loaded.
Figure 7 analyzes the key-related parameters after setting a breakpoint on the NCryptImportKey function and shows that the sixth parameter stores the key information, while the seventh parameter stores the key size. The sixth parameter for storing the key information is the address 0x004BE880, and it stores a value that starts with “RSA2”, as shown in
Figure 8. Nevertheless,
Figure 9 shows that as a result of inferring the location from the key handle based on the key information when the key is loaded, the exact location could not be analyzed (response to Question 1).
3.2. Key Storage Mechanism Analysis
We considered that it was difficult to analyze the location of the NCrypt key based on the above result. Hence, after analyzing the location of the keys in BCrypt, the NCrypt key location was analyzed by deriving clues to key locations.
First, the BCrypt sample program was implemented based on the decryption key information utilized by NCrypt to derive the key structure difference between NCrypt and BCrypt.
Figure 10 shows the program flow of the BCrypt sample, while
Figure 11 shows the execution result.
To derive the key structural differences between NCrypt and BCrypt based on the implemented sample code when importing the NCrypt key into BCrypt,
Figure 12 compares these structures and shows their structural differences.
The Magic of NCrypt starts with “RSA2”, while BCrypt starts with “RSAk”, and the size and information contained inside are also different.
Figure 13 analyzes the key location for the RSA algorithm in BCrypt, the result of setting a breakpoint on the BCryptDecrypt function. The breakpoint address is 0x00414DE8, and the key handle address is 0x0051BF70.
Inside the BCryptDecrypt function, the address that is a value (0x1E) of the address (0x051CB30) obtained by adding 0x90 to offset 0x08 from the key handle address is pushed, and the other function is then called. The function called here is a function to check the value (0x1E) obtained by adding 0x90 to offset 0x08 from the key handle address. The address of the breakpoint is 0x72AB6B29, and
Figure 14 shows the result of the breakpoint being set.
If the value 0x1E of the address obtained by adding 0x90 to the address 0x8 from the key handle address is successfully confirmed, another function is called after pushing the address (0x0051BF70), which is the address of offset 0xC from the key handle address. The address of the breakpoint is 0x72AB192B, and
Figure 15 shows the state where the breakpoint is set. Inside the function, another function is called after pushing the address (0x0051BF70), which is again the address of offset 0xC from the key handle address. The function called here is a function that checks Magic (“KRSM”). The address of the breakpoint is 0x72A9A4B5, and
Figure 16 shows the result of setting the breakpoint.
When Magic is confirmed, a specific function is called after pushing 0x100, and the function called here is a function that allocates memory. The address of the breakpoint is 0x72A9A512, and
Figure 17 shows the result of setting the breakpoint. When the memory is allocated successfully, the function is called after pushing a value of the address of offset 0x18 of the address of offset 0xC of the key handle address and the cipher text. The address of the breakpoint is 0x72A9A542, and
Figure 18 shows the result of setting the breakpoint.
Inside the function, the code compares the “RSAK” of Magic for the key handle. The address of the breakpoint that compares the Magic to the key handle is 0x72AA0E89, and
Figure 19 shows the result of setting the breakpoint. If the Magic of the key handle is confirmed, the memory allocation function is called after pushing eax. The address of the breakpoint is 0x732A0EE2, and
Figure 20 shows the result of setting the breakpoint.
If the memory is successfully allocated, the internal function is called after pushing the edi, 0x0B, and address of the cipher text, and the internal function copies the cipher text in reverse to the allocated memory. The breakpoint address is 0x72AA0F13, and
Figure 21 shows the result of setting the breakpoint. When the cipher text is copied successfully, the internal function is called after pushing the address to which the cipher text is copied to the allocated memory, 0x20, the address assigned to the memory address by adding 0x100, and the address of offset 0x50 of the address of offset 0xC of the key handle address (0x005BBFF0). The address of the breakpoint is 0x72AA0F58, and
Figure 22 shows the result of setting the breakpoint.
Inside the function, the internal function is called after pushing the address to which the cipher text is copied to the allocated memory, 0x20, the value of edi by adding 20, the address of offset 0x80 of the address of offset 0x0C of the key handle address (0x005BCDB0), and 0x10. The internal function is a function that compares constant values. The breakpoint address is 0x72A7E57C, and
Figure 23 shows the result of setting the breakpoint. After that, the memory allocation function is called after pushing 0 and 0x10. The breakpoint address is 0x72A88F48, and
Figure 24 shows the result of setting the breakpoint.
When the memory is allocated, the internal function is called after pushing the allocated memory, 0, the address of offset 0x64 of the address of offset 0xC of the key handle address (0x005BC004), 0x10, the address of offset 0x70 of the address of offset 0xC of the key handle address (0x005BCDB0), 0x20, and the address to which the cipher text is copied to the allocated memory. The breakpoint address is 0x72A88F67, and
Figure 25 shows the result of setting the breakpoint. Inside the function, the code copies the address of the cipher text to the allocated memory backward by 4 bytes. The breakpoint address is 0x72A9075A, and
Figure 26 shows the results of setting the breakpoint.
After copying the cipher text backward by 4 bytes, the internal function is called with the copied address of the cipher text from offset 0x40 of the allocated memory, the address of offset 0x70 of the address of offset 0x0C of the key handle address (0x005BCDB0), and 0x10. The address of the breakpoint is 0x72A9076D, and
Figure 27 shows the result of setting the breakpoint. Inside the function, the code loops around and performs the operation using the value of the cipher text from offset 0x40 of the allocated memory and the address of offset 0x70 of the address of offset 0x0C of the key handle address (0x005BCDB0). A total of 20 loop operations are performed. The breakpoint address is 0x72A7D71F, and
Figure 28 shows the result of setting the breakpoint. These operations are performed eight times in total, and the cipher text is decrypted based on the operation result. A total of eight operations are performed by those four operations being called twice, and
Figure 29 shows the first calling process, which is the calculation process. The information used in the operation is the copied value of the cipher text backward and the address of offset 0x70 of the address of offset 0xC of the key handle address, and the address of the breakpoint is 0x72AA0F58.
When the first operation is completed, the second operation is performed using the result of the first operation, the address of offset 0x70 of the address of offset 0xC of the key handle address, and the address of offset 0x40 of the address of offset 0xC of the key handle address. The breakpoint address is 0x72AA0F6F, and
Figure 30 shows the result of setting the breakpoint. When the second operation is completed, the third operation is performed using the result of the second operation, the address of offset 0x70 of the address of offset 0xC of the key handle address, and the address of offset 0x48 of the address of offset 0xC of the key handle address. The breakpoint address is 0x72AA0F85, and
Figure 31 shows the result of setting the breakpoint.
When the third operation is completed, the fourth operation is performed using the result of the third operation and the address of offset 0xAC of the address of offset 0x0C of the key handle address. The breakpoint address is 0x72AA0FA3, and
Figure 32 shows the result of setting the breakpoint. When the fourth operation is completed, the fifth operation is performed so that the first operation is performed again using the result of the third operation and the address of offset 0xAC of the address of offset 0xC of the key handle address. The breakpoint address is 0x72AA0F58, and
Figure 33 shows the result of setting the breakpoint.
When the fifth operation is completed, the sixth operation is performed using the result of the fifth operation, the address of offset 0xAC of the address of offset 0xC of the key handle address, and the address of offset 0x44 of the address of offset 0xC of the key handle address. The breakpoint address is 0x72AA0F6F, and
Figure 34 shows the result of setting the breakpoint. When the sixth operation is completed, the seventh operation is performed using the result of the sixth operation, the address of offset 0xAC of the address of offset 0x0C of the key handle address, and the address of offset 0x4C of the address of offset 0xC of the key handle address. The breakpoint address is 0x72AA0F85, and
Figure 35 shows the result of setting the breakpoint.
When the seventh operation is completed, the eighth operation is performed using the result of the seventh operation and the address of offset 0x70 of the address of offset 0x0C of the key handle address. The breakpoint address is 0x72AA0FA3, and
Figure 36 shows the result of setting the breakpoint. When a total of eight operations are completed, the final decryption is performed using the result of the fourth operation, the result of the eighth operation, and the address of offset 0x70 of the address of offset 0x0C of the key handle address. The breakpoint address is 0x72AA0FDE, and
Figure 37 shows the result of setting the breakpoint.
3.3. Discussion
The derived information that is used for the decryption based on the result of the analysis is the copied value of the cipher text backward, the address of offset 0x70 of the address of offset 0xC of the key handle address, the address of offset 0x40 of the address of offset 0xC of the key handle address, the address of offset 0x48 of the address of offset 0xC of the key handle address, the address of offset 0xAC of the address of offset 0xC of the key handle address, the address of offset 0x44 of the address of offset 0xC of the key handle address, and the address of offset 0x4C of the address of offset 0xC of the key handle address.
Figure 38,
Figure 39,
Figure 40 and
Figure 41 show the decryption process (response to Question 2).
Finally, we tried to analyze the key storage location of NCrypt based on the analyzed BCrypt decryption process. The result of calling the internal function after setting the breakpoint on the NCryptDecrypt function, the NdrSendReceive function of the rpcrt4 library, is called from the inside, as shown in
Figure 42. Inside the NdrSendReceive function, the I_RpcSendReceive function is called, as shown in
Figure 43, and the ZwAlpcSendWaitReceivePort function of the ntdll library is called inside the I_RpcSendReceive function, as shown in
Figure 44. Inside the ZwAlpcSendWaitReceivePort function, the kernel code is executed in the kernel, and the decryption result is returned after the function is called, as shown in
Figure 45.
This article analyzed the key storage mechanism in the asymmetric-key-related functions of the CNG library and derived two research questions. The first question is whether it is possible to verify real key information from the obtained handle because CNG does not directly receive key information during the encryption and decryption processes. The second question is as follows: “If the handle address of an encryption or decryption key is given, can the location of the real key information be analyzed from the key handle address?” In answer to the first question, it was not possible to analyze the exact location using the key handle based on the key information obtained when the key was loaded in NCrypt. As shown in
Figure 41, the response to the second question accurately analyzed the key storage mechanism in asymmetric-key-related functions in BCrypt. Based on these questions and responses, the analyzed results can be used for the purpose of verifying key-related information, such as debugging and verification, when developing various cryptographic systems and application programs using CNG. Furthermore, if a tool for extracting key information is implemented, we believe that an automated key verification method can be developed.