Maintaining Secure Level on Symmetric Encryption under Quantum Attack
Abstract
:1. Introduction
- To follow the framework of the original AES algorithm, and extend the key length to 384 bits and 512 bits in order to resist the threat introduced by quantum computers, and do an avalanche test on C++ software to prove the security of the AES 384 bits and 512 bits key.
- Improve the speed of AES encryption and decryption, write the AES algorithm into FPGA by using hardware description language, make use of its instruction parallelization characteristics, make parallel calculations, accelerate the encryption and decryption calculation, and achieve a hardware acceleration effect.
- Use different calculation structures and increase the amount of calculation per unit of time by adding registers, and use the space-for-time method for optimization.
2. Literature Review
2.1. Quantum Computer
2.2. Advanced Encryption Standard
2.3. Finite Field
2.4. Avalanche Effect
2.5. Parallel Computing
2.6. Field Programmable Gate Array (FPGA)
2.7. Abidalrahman Moh’d Proposed AES-512 Bits Method
3. System Architecture
3.1. AES Algorithm Parameters
- The number of encrypted blocks (Nb): The input plaintext, in 32 bits, is 1 word, because the AES plaintext block is fixed at 128 bits, which is the state matrix composed of four words.
- Number of key segments (Nk): The length of the key is 32 bits for one word, and is divided into four words, six words, and eight words according to the key length of 128 bits, 192 bits, and 256 bits.
- Number of encryption rounds (Nr): This is the number of iterations required for encryption and decryption, which is related to the key length. The number of rounds from short to long key length is 10, 12 and 14 rounds, respectively. The relationship between the number of encryption rounds and the number of key segments can be calculated as follows:
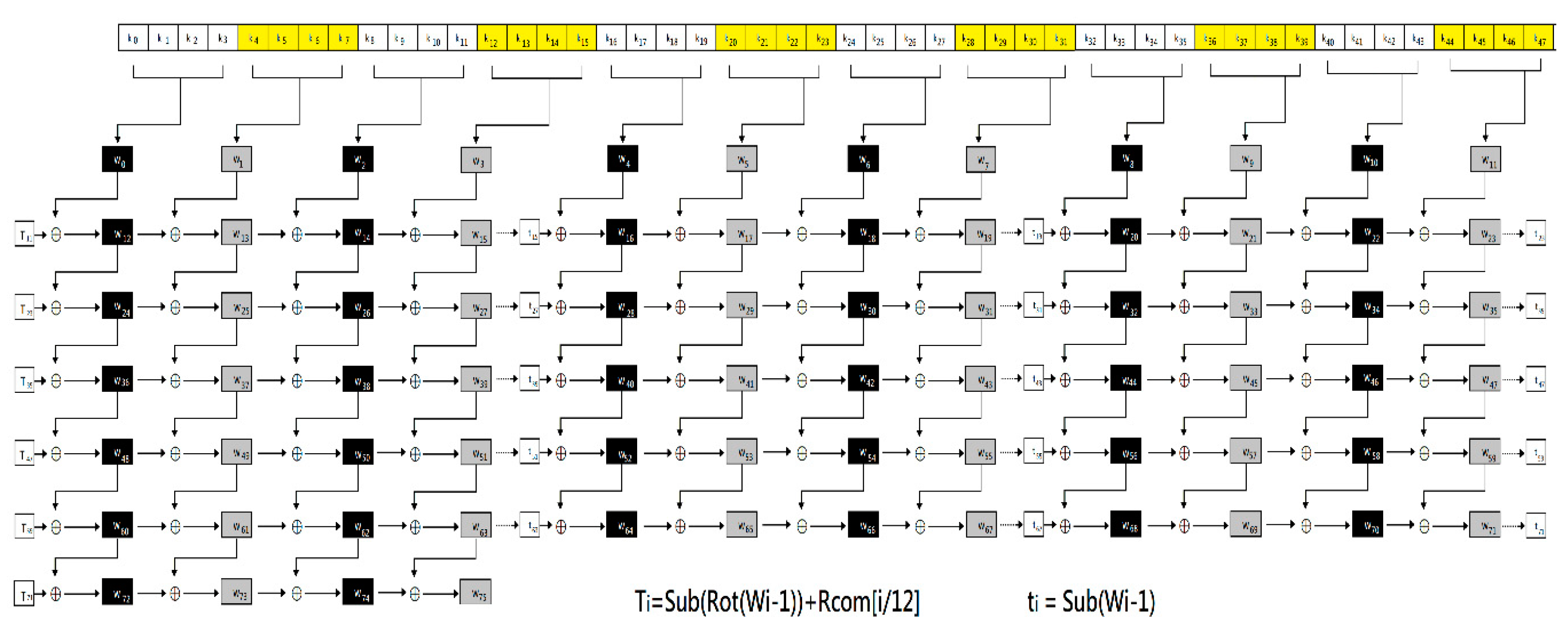
3.2. AES-384, AES-512 Concept and Software Implementation
4. Programming and Testing
4.1. Experimental Environment
4.2. Software Testing
4.3. Software Avalanche Test
4.4. Hardware Description Language Simulation
4.5. Compatibility of Rijndael
4.6. Parallel Computing Performance
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Amin, M.; Al-Obeidat, F.; Tubaishat, A.; Shah, B.; Anwar, S.; Tanveer, T.A. Cyber security and beyond: Detecting malware and concept drift in AI-based sensor data streams using statistical techniques. Comput. Electr. Eng. 2023, 108, 108702. [Google Scholar] [CrossRef]
- Tariq, N.; Asim, M.; Al-Obeidat, F.; Zubair Farooqi, M.; Baker, T.; Hammoudeh, M.; Ghafir, I. The Security of Big Data in Fog-Enabled IoT Applications Including Blockchain: A Survey. Sensors 2019, 14, 1788. [Google Scholar] [CrossRef] [PubMed]
- Al-Obeidat, F.; Hani, A.B.; Adedugbe, O.; Majdalawieh, M.; Benkhelifa, E. The Socio-economic Impacts of Social Media Privacy and Security Challenges. In Proceedings of the Frontiers in Cyber Security, Tianjin, China, 4 November 2020; pp. 553–563. [Google Scholar]
- Bhatia, V.; Ramkumar, K.R. An Efficient Quantum Computing technique for cracking RSA using Shor’s Algorithm. In Proceedings of the IEEE 5th International Conference on Computing Communication and Automation (ICCCA), Greater Noida, India, 30–31 October 2020. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 22–24 May 1996. [Google Scholar]
- Grassl, M.; Langenberg, B.; Roetteler, M.; Steinwandt, R. Applying Grover’s algorithm to AES: Quantum resource estimates. In Proceedings of the International Conference on Post-Quantum Cryptography, Fukuoka, Japan, 24–26 February 2016. [Google Scholar]
- NIST. Announcing the Advanced Encryption Standard (AES); Federal Information Processing Standards Publication: Gaithersburg, MD, USA, 2001; pp. 5–26. [Google Scholar]
- Jose, L.H.; Guido, P.; Christof, E.; Mario, P. Quantum Computing. IEEE Softw. 2021, 38, 7–15. [Google Scholar]
- Mattsson, J.P.; Smeets, B.; Thormarker, E. Quantum-Resistant Cryptography. arXiv 2021, arXiv:2112.00399. [Google Scholar]
- Al-Ghamdi, A.B.; Al-Sulami, A.; Aljahdali, A.O. On the security and confidentiality of quantum key distribution. Secur. Priv. 2020, 3, e111. [Google Scholar] [CrossRef]
- Balupala, H.K.; Rahul, K.; Yachareni, S. Galois Field Arithmetic Operations using Xilinx FPGAs in Cryptography. In Proceedings of the IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, Canada, 14 May 2021. [Google Scholar]
- Feistel, H. Cryptography and Computer Privacy. Sci. Am. 1973, 228, 15–23. [Google Scholar] [CrossRef]
- Webster, A.F.; Tavares, S.E. On the Design of S-Boxes. In Advances in Cryptology—CRYPTO ‘85 Proceedings; Springer: Berlin/Heidelberg, Germany, 1985; pp. 523–534. [Google Scholar]
- Khose, P.N.; Raut, V.G. Implementation of AES algorithm on FPGA for low area consumption. In Proceedings of the International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015. [Google Scholar]
- Moh’d, A.; Jararweh, Y.; Tawalbeh, L.A. AES 512: 512-bit Advanced Encryption Standard algorithm design and evaluation. In Proceedings of the International Conference on Information Assurance and Security (IAS), Melacca, Malaysia, 5–8 December 2011. [Google Scholar]
- D’souza, F.J.; Panchal, D. Advanced encryption standard (AES) security enhancement using hybrid approach. In Proceedings of the International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017. [Google Scholar]
- Hu, F.; Ni, F. Software Implementation of AES-128: Side Channel Attacks Based on Power Traces Decomposition. In Proceedings of the 2022 International Conference on Cyber Warfare and Security (ICCWS), Islamabad, Pakistan, 7–8 December 2022. [Google Scholar]
- Sanap, S.D.; More, V. Performance Analysis of Encryption Techniques Based on Avalanche effect and Strict Avalanche Criterion. In Proceedings of the International Conference on Signal Processing and Communication, Coimbatore, India, 13–14 May 2021. [Google Scholar]
- Sunil, J.; Suhas, H.S.; Sumanth, B.K.; Santhameena, S. Implementation of AES Algorithm on FPGA and on software. In Proceedings of the IEEE International Conference for Innovation in Technology (INOCON), Bangluru, India, 6–8 November 2020. [Google Scholar]
- Singh, K.; Dod, S. An Efficient Hardware design and Implementation of Advanced Encryption Standard (AES) Algorithm. Comput. Sci. 2016. [Google Scholar] [CrossRef]
- Kumar, K.; Singh, V.; Mishra, G.; Babu, B.R.; Tripathi, N.; Kumar, P. Power-Efficient Secured Hardware Design of AES Algorithm on High Performance FPGA. In Proceedings of the 2022 5th International Conference on Contemporary Computing and Informatics (IC3I), Uttar Pradesh, India, 14–16 December 2022. [Google Scholar]
- Rahim, U.; Siddiqui, M.F.; Javed, M.A.; Nafi, N. Architectural Implementation of AES based 5G Security Protocol on FPGA. In Proceedings of the 2022 32nd International Telecommunication Networks and Applications Conference (ITNAC), Wellington, New Zealand, 30 November–2 December 2022. [Google Scholar]
- Shet, G.G.; Jamuna, V.; Shravani, S.; Nayana, H.G.; Kumar, P. Implementation of AES Algorithm Using Verilog. JNNCE J. Eng. Manag. 2020, 4, 1. [Google Scholar] [CrossRef]
- Soumya, V.H.; Neelagar, M.B.; Kumaraswamy, K.V. Designing of AES Algorithm using Verilog. In Proceedings of the International Conference for Convergence in Technology (I2CT), Mangalore, India, 27–28 October 2018. [Google Scholar]
- Srinivas, N.S.; Akramuddin, M.D. FPGA based hardware implementation of AES Rijndael algorithm for Encryption and Decryption. In Proceedings of the International Conference on Electrical Electronics and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016. [Google Scholar]
- Shah, S.S.; Raja, G. FPGA implementation of chaotic based AES image encryption algorithm. In Proceedings of the IEEE International Conference on Signal and Image Processing Applications (ICSIPA), Kuala Lumpur, Malaysia, 19–21 October 2015. [Google Scholar]
- Joshi, A.; Dakhole, P.K.; Thatere, A. Implementation of S-Box for Advanced Encryption Standard. In Proceedings of the IEEE International Conference on Engineering and Technology (ICETECH), Coimbatore, India, 20 March 2015. [Google Scholar]
- Nadjia, A.; Mohamed, A. Efficient implementation of AES S-box in LUT-6 FPGAs. In Proceedings of the International Conference on Electrical Engineering (ICEE), Boumerdes, Algeria, 13–15 December 2015. [Google Scholar]
- Pammu, A.A.; Chong, K.S.; Ne, K.Z.; Gwee, B.H. High Secured Low Power Multiplexer-LUT Based AES S-Box Implementation. In Proceedings of the International Conference on Information Systems Engineering (ICISE), Los Angeles, CA, USA, 20–22 April 2016. [Google Scholar]








| Key Length (Bits) | Number of Encrypted Segments (Nb) | Number of Key Segments (Nk) | Number of Encrypted Rounds (Nr) |
|---|---|---|---|
| 128 | 4 | 4 | 10 |
| 192 | 4 | 6 | 12 |
| 256 | 4 | 8 | 14 |
| Version | Round |
|---|---|
| 384 | 18 |
| 512 | 22 |
| Version | Nr | Words |
|---|---|---|
| 384 | 18 | 76 |
| 512 | 22 | 92 |
| Block Number | Rule |
|---|---|
| Block Number | Rule |
|---|---|
| & | |
| & |
| Items of Hardware Objects | AES-384 Bits | AES-512 Bits |
|---|---|---|
| Number of Slices | 4879 | 6371 |
| Number of Slices FF | 2791 | 3791 |
| Number of four-input LUTs | 8997 | 11,211 |
| Number of bonded IOBs | 471 | 594 |
| 00 | 01 | 02 | 03 | 04 | 05 | 06 | 07 | 08 | 09 | 0a | 0b | 0c | 0d | 0e | 0f | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 00 | 63 | 7c | 77 | 7b | f2 | 6b | 6f | c5 | 30 | 01 | 67 | 2b | fe | d7 | ab | 76 |
| 10 | ca | 82 | c9 | 7d | fa | 59 | 47 | f0 | ad | d4 | a2 | Af | 9c | a4 | 72 | c0 |
| 20 | b7 | fd | 93 | 26 | 36 | 3f | f7 | cc | 34 | a5 | e5 | f1 | 71 | d8 | 31 | 15 |
| 30 | 04 | c7 | 23 | c3 | 18 | 96 | 05 | 9a | 07 | 12 | 80 | e2 | eb | 27 | b2 | 75 |
| 40 | 09 | 83 | 2c | 1a | 1b | 6e | 5a | a0 | 52 | 3b | d6 | b3 | 29 | e3 | 2f | 84 |
| 50 | 53 | d1 | 00 | ed | 20 | fc | b1 | 5b | 6a | cb | be | 39 | 4a | 4c | 58 | cf |
| 60 | d0 | ef | aa | fb | 43 | 4d | 33 | 85 | 45 | f9 | 02 | 7f | 50 | 3c | 9f | a8 |
| 70 | 51 | a3 | 40 | 8f | 92 | 9d | 38 | f5 | bc | b6 | da | 21 | 10 | ff | f3 | d2 |
| 80 | cd | 0c | 13 | ec | 5f | 97 | 44 | 17 | c4 | a7 | 7e | 3d | 64 | 5d | 19 | 73 |
| 90 | 60 | 81 | 4f | dc | 22 | 2a | 90 | 88 | 46 | ee | b8 | 14 | de | 5e | 0b | db |
| a0 | e0 | 32 | 3a | 0a | 49 | 06 | 24 | 5c | c2 | d3 | ac | 62 | 91 | 95 | e4 | 79 |
| b0 | e7 | c8 | 37 | 6d | 8d | d5 | 4e | a9 | 6c | 56 | f4 | ea | 65 | 7a | ae | 08 |
| c0 | ba | 78 | 25 | 2e | 1c | a6 | b4 | c6 | e8 | dd | 74 | 1f | 4b | bd | 8b | 8a |
| d0 | 70 | 3e | b5 | 66 | 48 | 03 | f6 | 0e | 61 | 35 | 57 | b9 | 86 | c1 | 1d | 9e |
| e0 | e1 | f8 | 98 | 11 | 69 | d9 | 8e | 94 | 9b | 1e | 87 | e9 | ce | 55 | 28 | df |
| f0 | 8c | a1 | 89 | 0d | bf | e6 | 42 | 68 | 41 | 99 | 2d | 0f | b0 | 54 | bb | 16 |
| Original Key | 2b | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | 09 | cf | 4f | 3c |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Round 1 key | a0 | fa | fe | 17 | 88 | 54 | 2c | b1 | 23 | a3 | 39 | 39 | 2a | 6c | 76 | 05 |
| Round 2 key | f2 | c2 | 95 | f2 | 7a | 96 | b9 | 43 | 59 | 35 | 80 | 7a | 73 | 59 | f6 | 7f |
| Round 3 key | 3d | 80 | 47 | 7d | 47 | 16 | fe | 3e | 1e | 23 | 7e | 44 | 6d | 7a | 88 | 3b |
| Round 4 key | ef | 44 | a5 | 41 | a8 | 52 | 5b | 7f | b6 | 71 | 25 | 3b | db | 0b | ad | ee |
| Round 5 key | d4 | d1 | c6 | f8 | 7c | 83 | 9d | 87 | ca | f2 | b8 | bc | 11 | f9 | 15 | bc |
| Round 6 key | 6d | 88 | a3 | 7a | 11 | 0b | 3e | fd | db | f9 | 86 | 41 | ca | 00 | 93 | fd |
| Round 7 key | 4e | 54 | f7 | Be | 5f | 5f | c9 | f3 | 84 | a6 | 4f | b2 | 4e | a6 | dc | 4f |
| Round 8 key | ea | d2 | 73 | 21 | b5 | 8d | ba | d2 | 31 | 2b | f5 | 60 | 7f | 8d | 29 | 2f |
| Round 9 key | ac | 77 | 66 | f3 | 19 | fa | dc | 21 | 28 | d1 | 29 | 41 | 57 | 5c | 09 | 6e |
| Round 10 key | d0 | 14 | f9 | a8 | c9 | ee | 25 | 89 | e1 | 3f | 0c | c8 | b6 | 63 | 0c | a6 |
| Plaintext 1 | Plaintext 2 | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Text Characters | Helloworld123456 | Helloworld123450 | ||||||||||||||
| ASCII | 48 | 65 | 6c | 6c | 6f | 77 | 6f | 72 | 48 | 65 | 6c | 6c | 6f | 77 | 6f | 72 |
| 6c | 64 | 31 | 32 | 33 | 34 | 35 | 36 | 6c | 64 | 31 | 32 | 33 | 34 | 35 | 30 | |
| Original key (384 bits) | 2b | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | ||||
| 09 | cf | 4f | 3c | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | |||||
| f7 | 15 | 88 | 09 | cf | 4f | 3c | 2b | 2b | 7e | 15 | 16 | |||||
| 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | 09 | cf | 4f | 3c | |||||
| Plaintext 1 | Plaintext 2 | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Output ASCII | 8c | 09 | 93 | 51 | a6 | 3e | 92 | 8e | f2 | 99 | 04 | 96 | 69 | 31 | 36 | b1 |
| d6 | 99 | ba | 2f | ae | 53 | 6f | b6 | 55 | 98 | 13 | b1 | 4a | 77 | 33 | 9b | |
| Plaintext 1 | Plaintext 2 | |||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Text Characters | Thatisagoodidea8 | Thatisagoodidea5 | ||||||||||||||||||||||
| ASCII | 54 | 68 | 61 | 74 | 69 | 73 | 61 | 67 | 54 | 68 | 61 | 74 | 69 | 73 | 61 | 67 | ||||||||
| 6f | 6f | 64 | 69 | 64 | 65 | 61 | 38 | 6f | 6f | 64 | 69 | 64 | 65 | 61 | 35 | |||||||||
| Original key (384 bits) | 2b | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | ||||||||||||
| 09 | cf | 4f | 3c | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | |||||||||||||
| f7 | 15 | 88 | 09 | cf | 4f | 3c | 2b | 2b | 7e | 15 | 16 | |||||||||||||
| 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | 09 | cf | 4f | 3c | |||||||||||||
| 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | 09 | |||||||||||||
| 2b | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | f7 | 15 | 88 | |||||||||||||
| 09 | cf | 4f | 3c | 7e | 15 | 16 | 28 | ae | d2 | a6 | ab | |||||||||||||
| cf | 4f | 3c | 2b | |||||||||||||||||||||
| Plaintext 1 | Plaintext 2 | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Output ASCII | 2f | c4 | ae | d4 | f6 | 94 | 24 | 8f | c3 | 1a | 83 | 13 | c3 | 01 | f1 | fb |
| a4 | 93 | 64 | fb | f1 | 28 | 80 | 02 | aa | 7f | 1c | 46 | 9f | 98 | 23 | 20 | |
| Proposed | Rijndael | Abidalrahman Moh’d [15] | |
|---|---|---|---|
| Security level | I, III, V | I, III, V | X |
| Security Level under quantum calculation | I, III, V | I | V |
| AES-128 | O | O | X |
| AES-192 | O | O | X |
| AES-256 | O | O | X |
| AES-384 | O | X | X |
| AES-512 | O | X | O |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shiu, H.-J.; Yang, C.-T.; Tsai, Y.-R.; Lin, W.-C.; Lai, C.-M. Maintaining Secure Level on Symmetric Encryption under Quantum Attack. Appl. Sci. 2023, 13, 6734. https://doi.org/10.3390/app13116734
Shiu H-J, Yang C-T, Tsai Y-R, Lin W-C, Lai C-M. Maintaining Secure Level on Symmetric Encryption under Quantum Attack. Applied Sciences. 2023; 13(11):6734. https://doi.org/10.3390/app13116734
Chicago/Turabian StyleShiu, Hung-Jr, Chao-Tung Yang, Yun-Ru Tsai, Wei-Chung Lin, and Chun-Ming Lai. 2023. "Maintaining Secure Level on Symmetric Encryption under Quantum Attack" Applied Sciences 13, no. 11: 6734. https://doi.org/10.3390/app13116734







