Machine Learning-Based DoS Amplification Attack Detection against Constrained Application Protocol
Abstract
1. Introduction
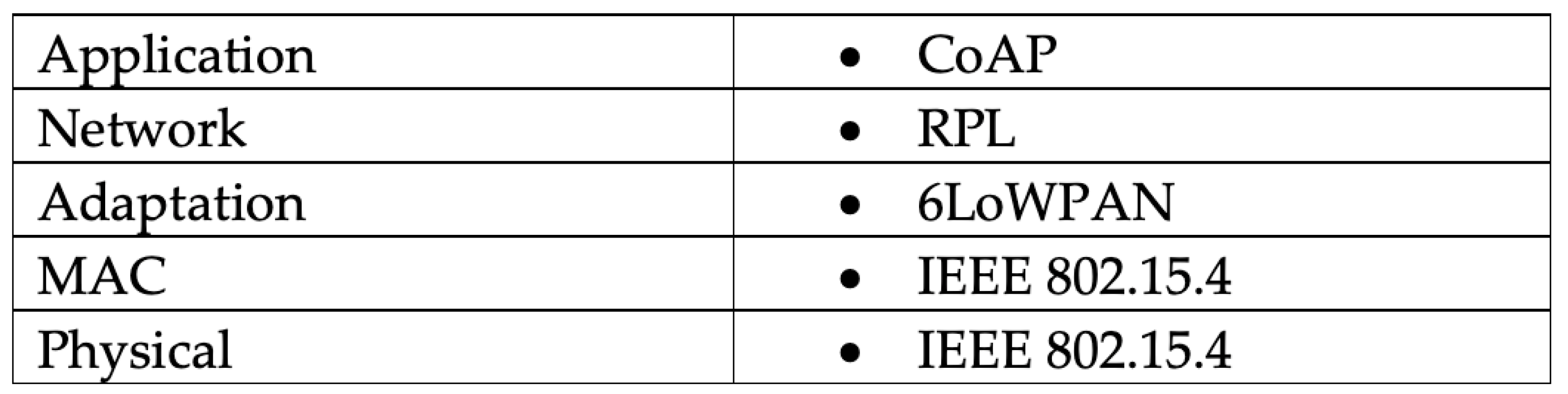
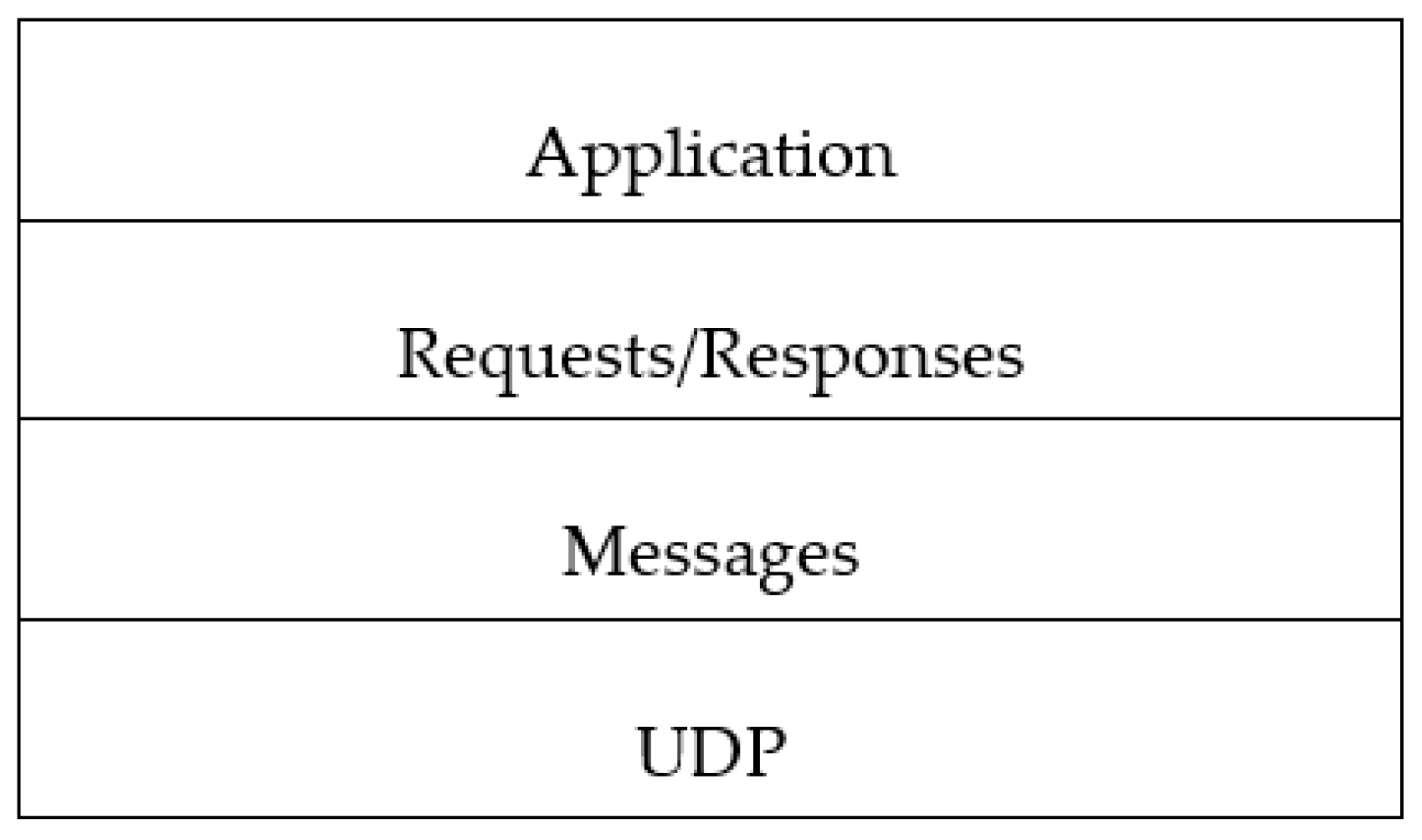
1.1. IoT-CoAP Overview
1.2. CoAP Architecture
1.3. CoAP Security Overview
- A.
- NoSec Mode: The DTLS is not deployed in this mode assuming that the lower layers will take the role of securing the messages. This paper assumes that the CoAP is in the NoSec mode while trying to find an alternative way to secure the CoAP clients against the CoAP amplification attacks instead of using the DTLS protocol. This paper’s target is to secure the CoAP in its vicinity, and the NoSec mode is the default mode for this work.
- B.
- PresharedKey Mode: In this mode, the DTLS is deployed, and for each key, there is a list of nodes that appear to engage in communication. So, every endpoint has its own key, and if it is within a group of nodes, it is authenticated within that group using pre-shared keys.
- C.
- RawPublicKey Mode: The DTLS is also deployed in this mode. If an endpoint requires authentication, a symmetric key is generated for all endpoints to avoid the need for a certificate.
- D.
- Certificate Mode: In this mode, the DTLS is deployed, and a symmetric key pair is generated for each endpoint. The certificate authority is responsible for ensuring the validity of each endpoint.
Denial-of-Service Attacks against CoAP
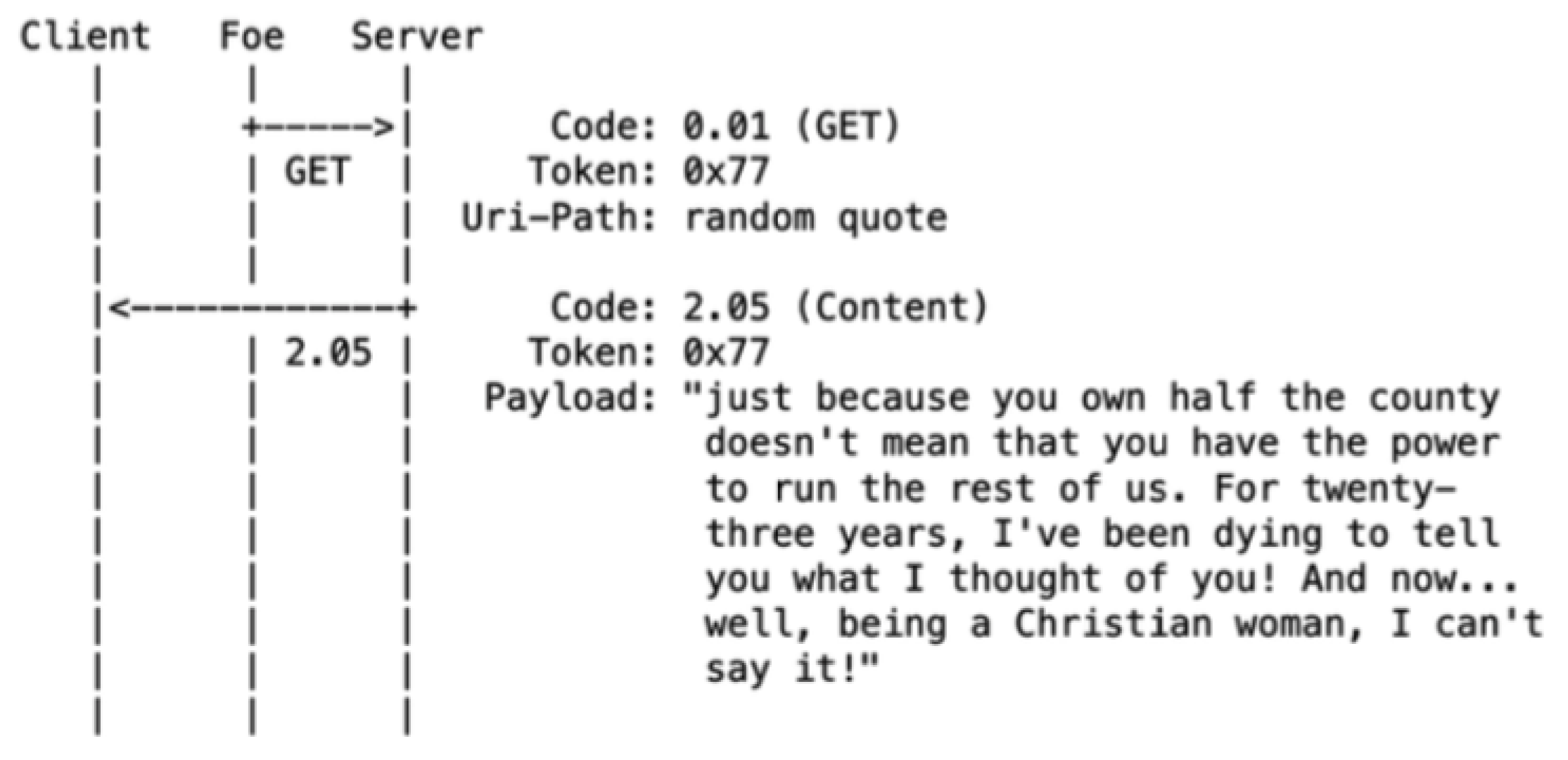
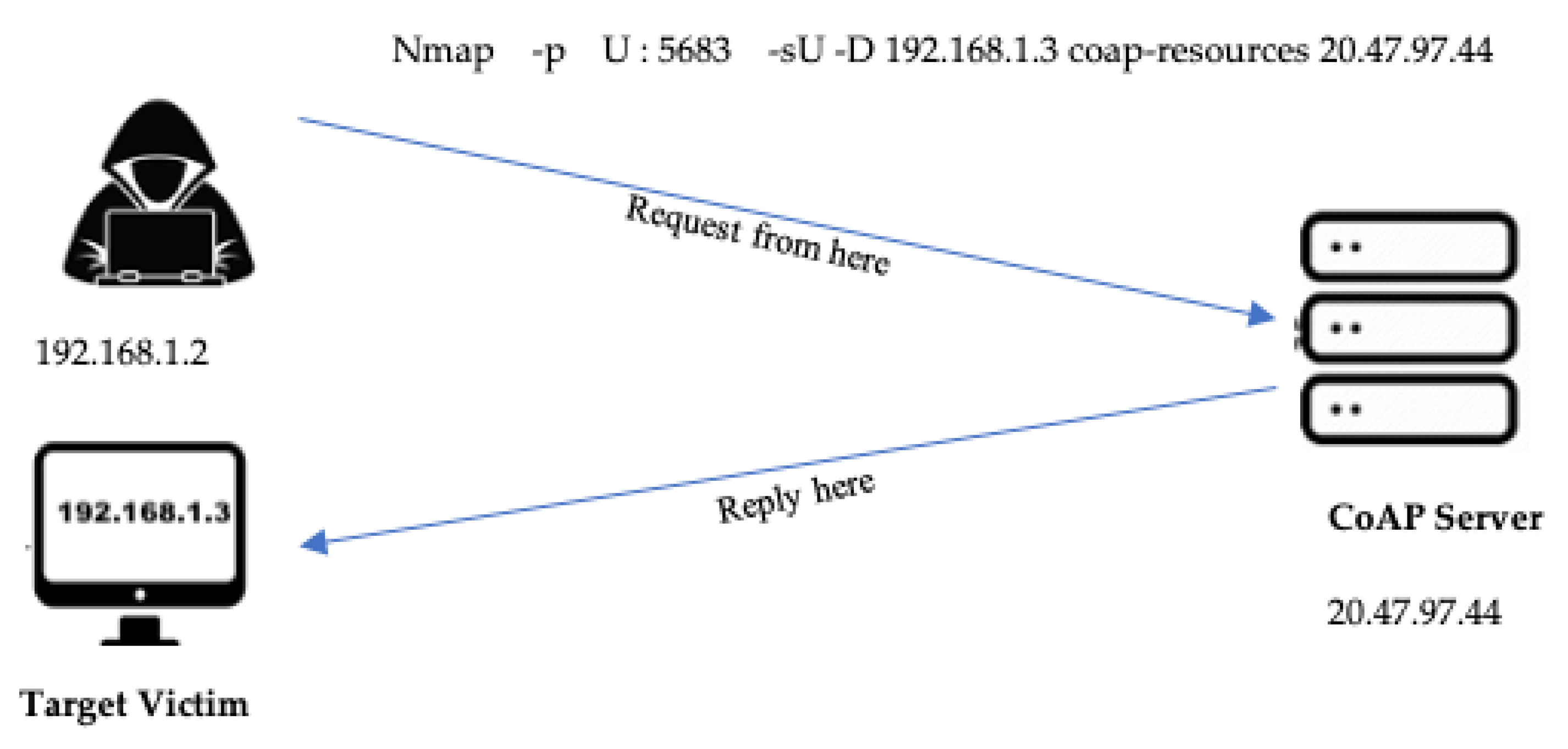
- 1. Simple Amplification Attack
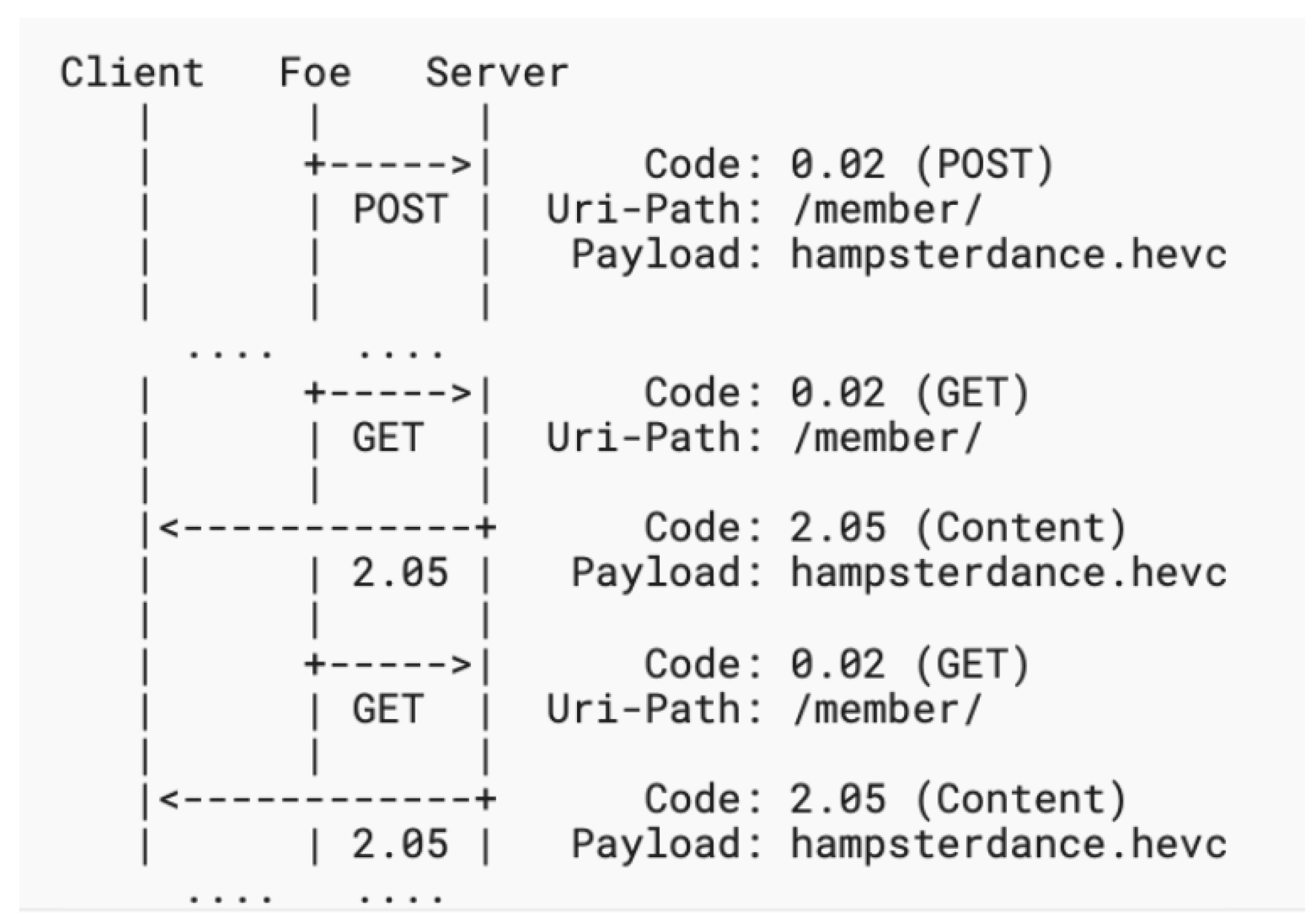
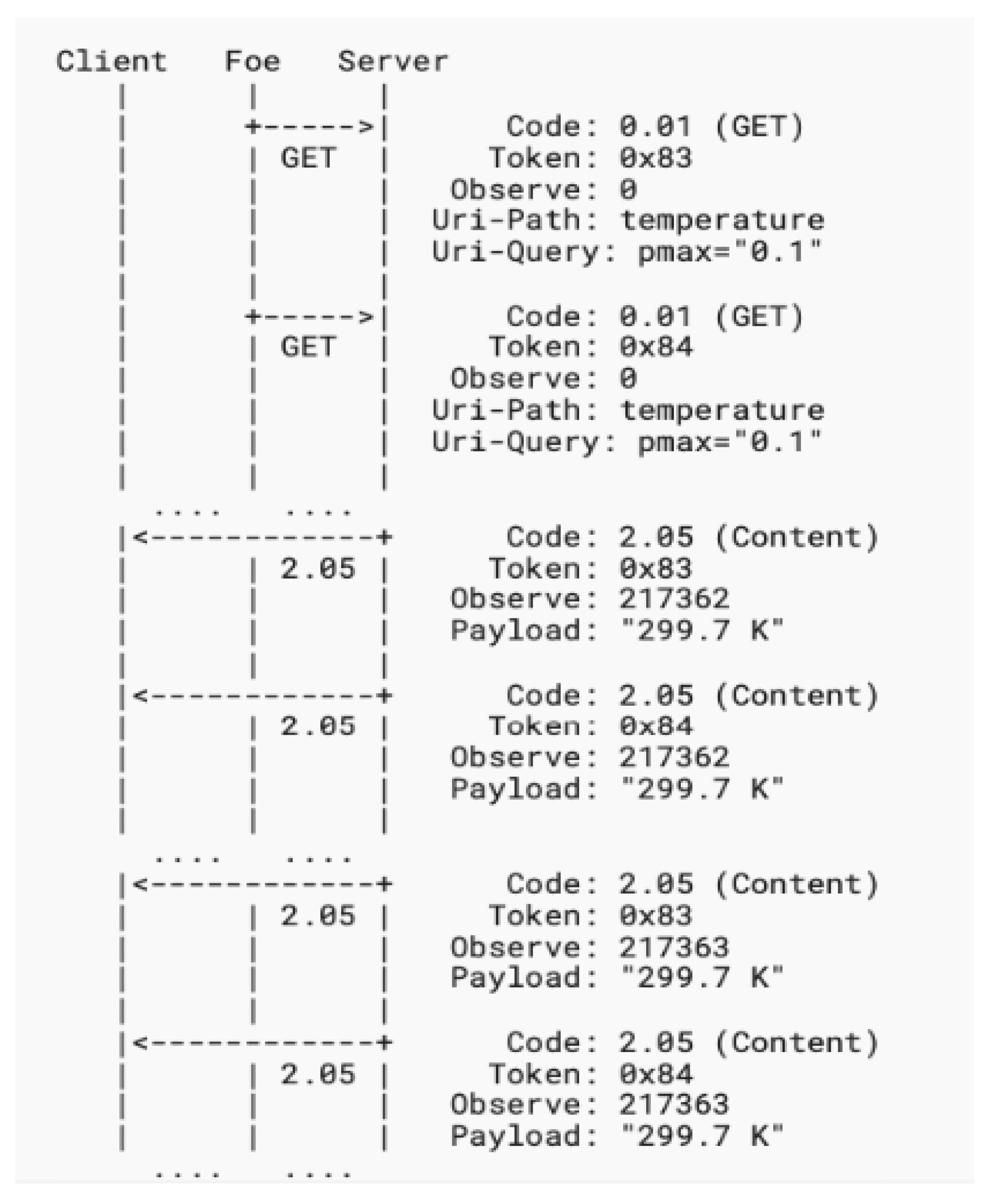
- 2. Amplification Attack Using Observe
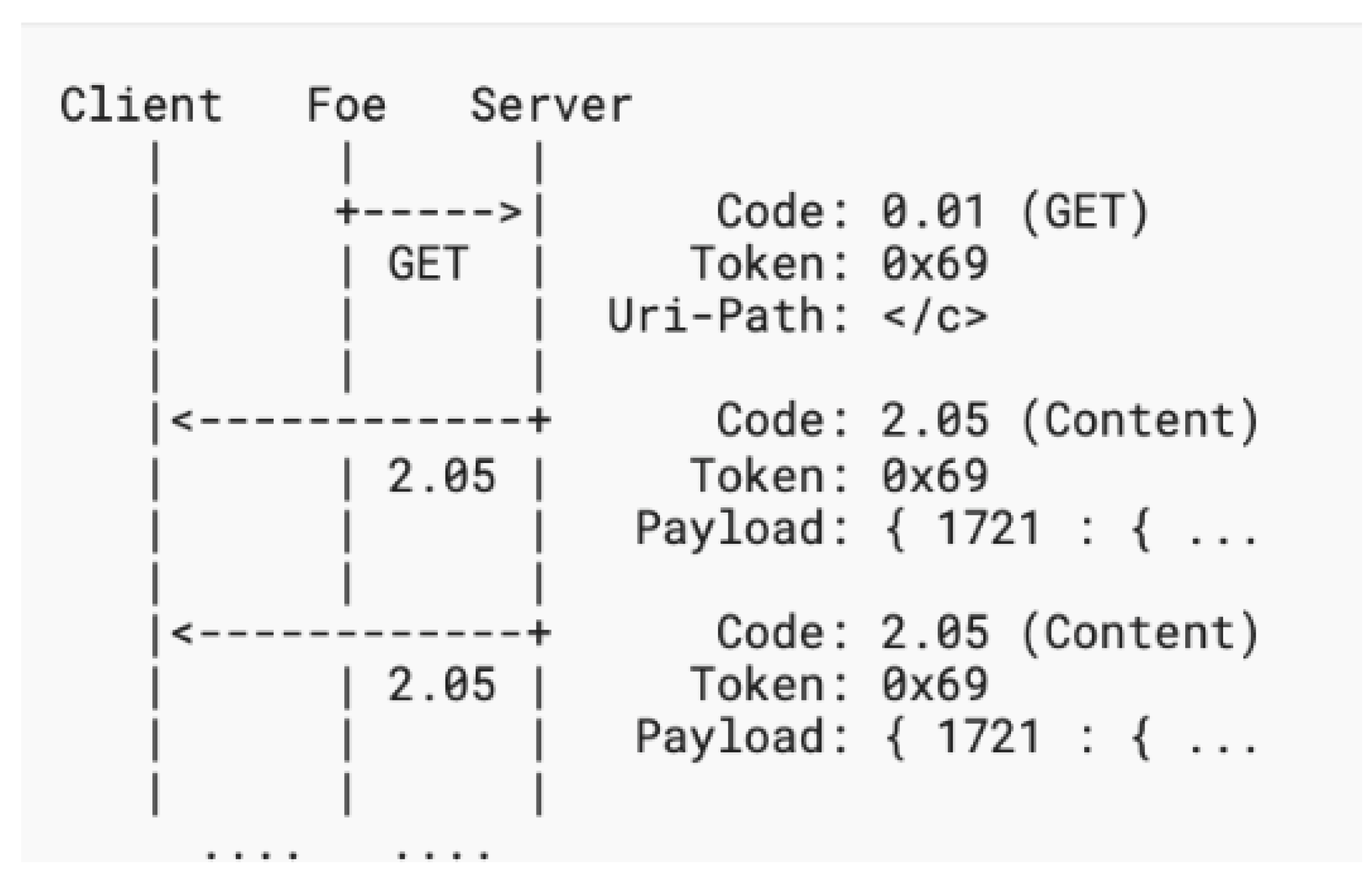
- 3. Amplification Attack Using Multicast
2. Related Work
2.1. Proposed Defense Mechanisms for IoT Network
2.1.1. SDN Platform for IoT Network Security
2.1.2. Machine Learning and Deep Learning for IoT Network Security
2.1.3. Cloud Platform for IoT Network Security
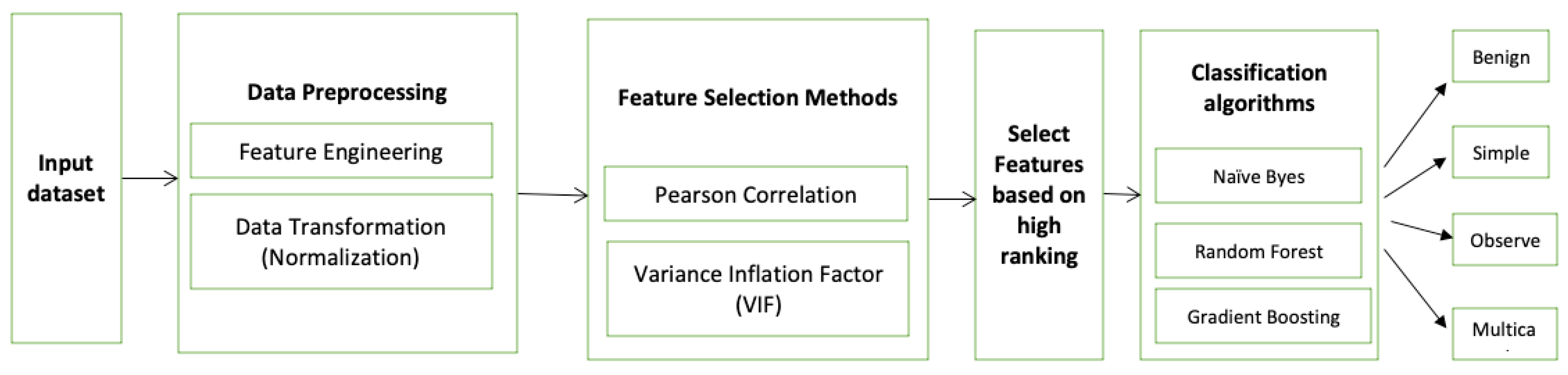
3. Materials and Methods
3.1. Dataset Creation
3.2. Data Preprocessing
3.3. Feature Selection
3.4. Model Training
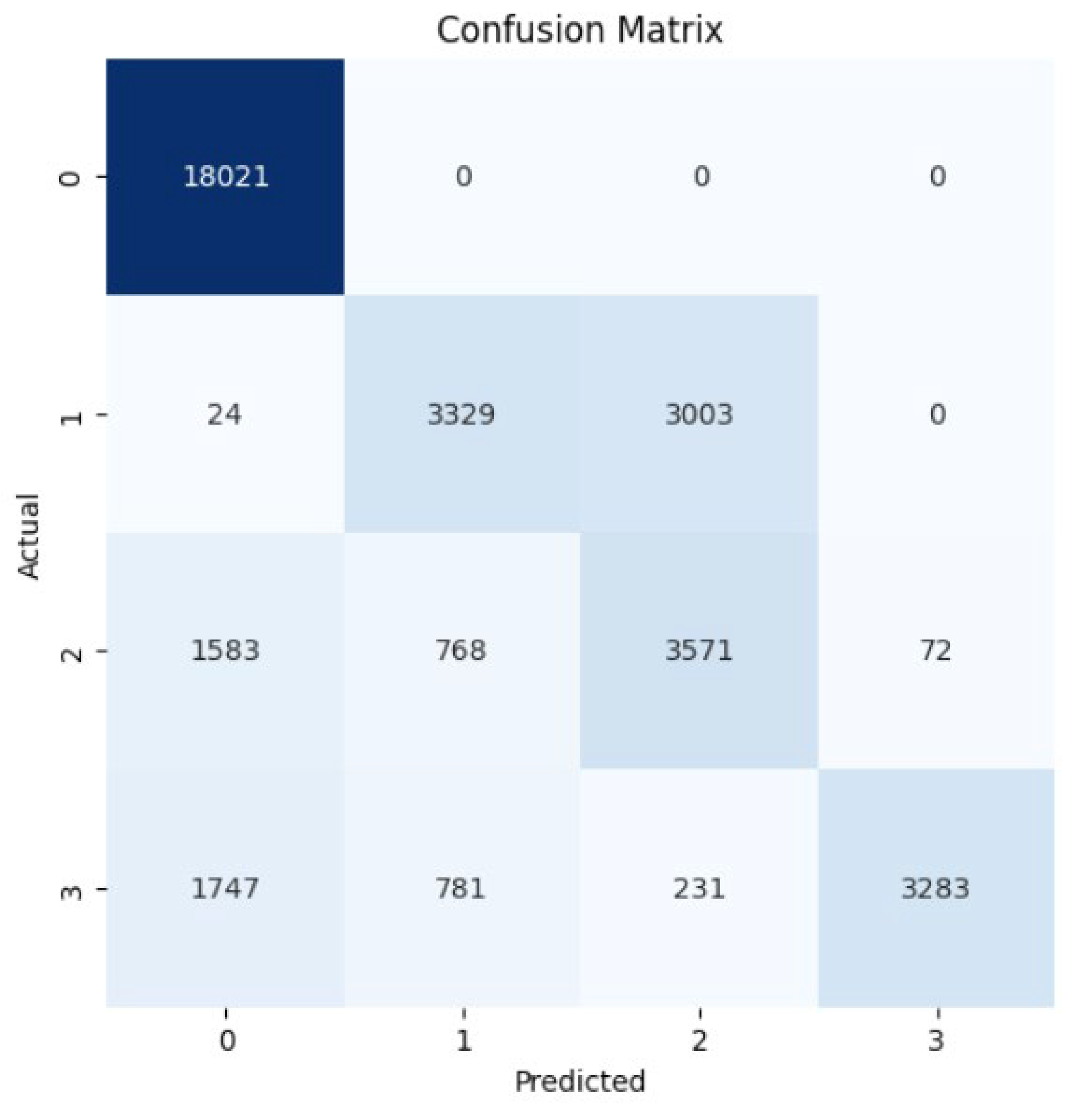
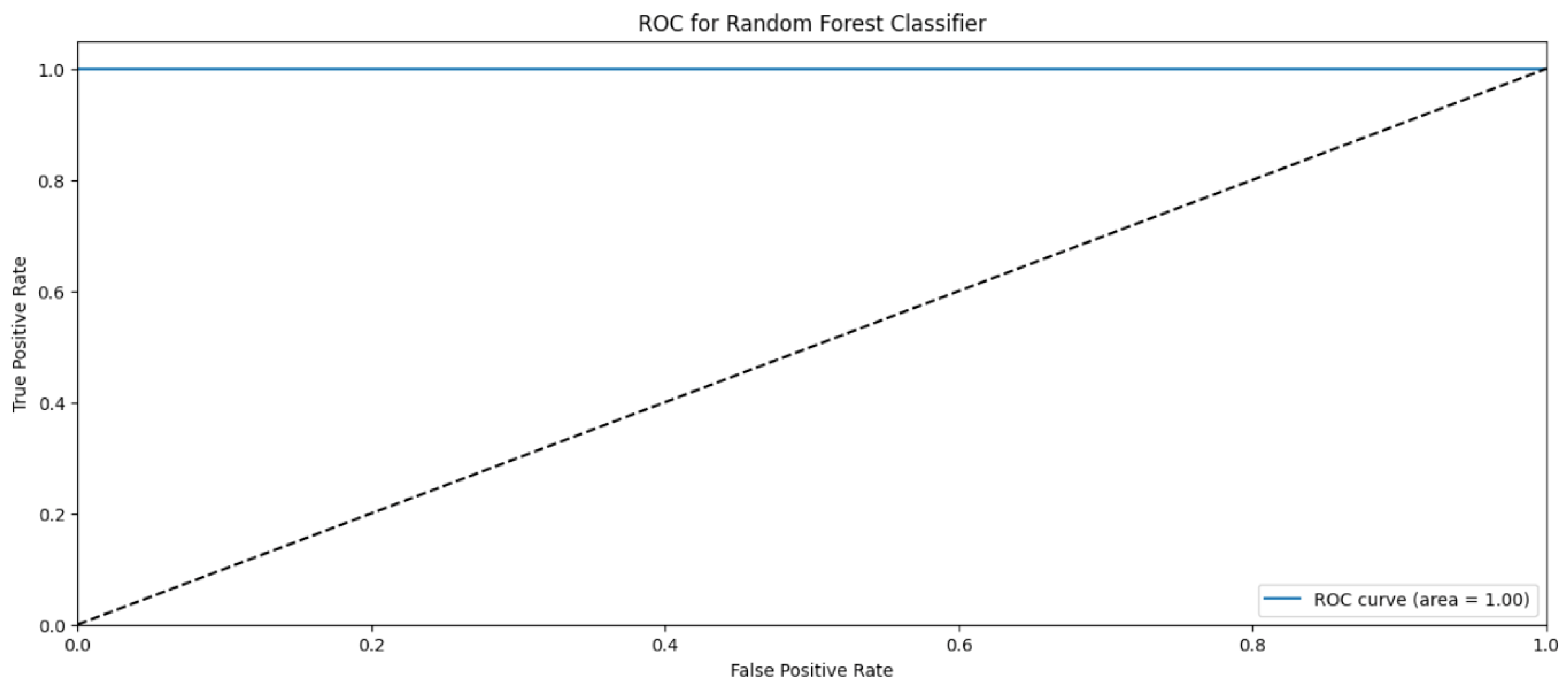
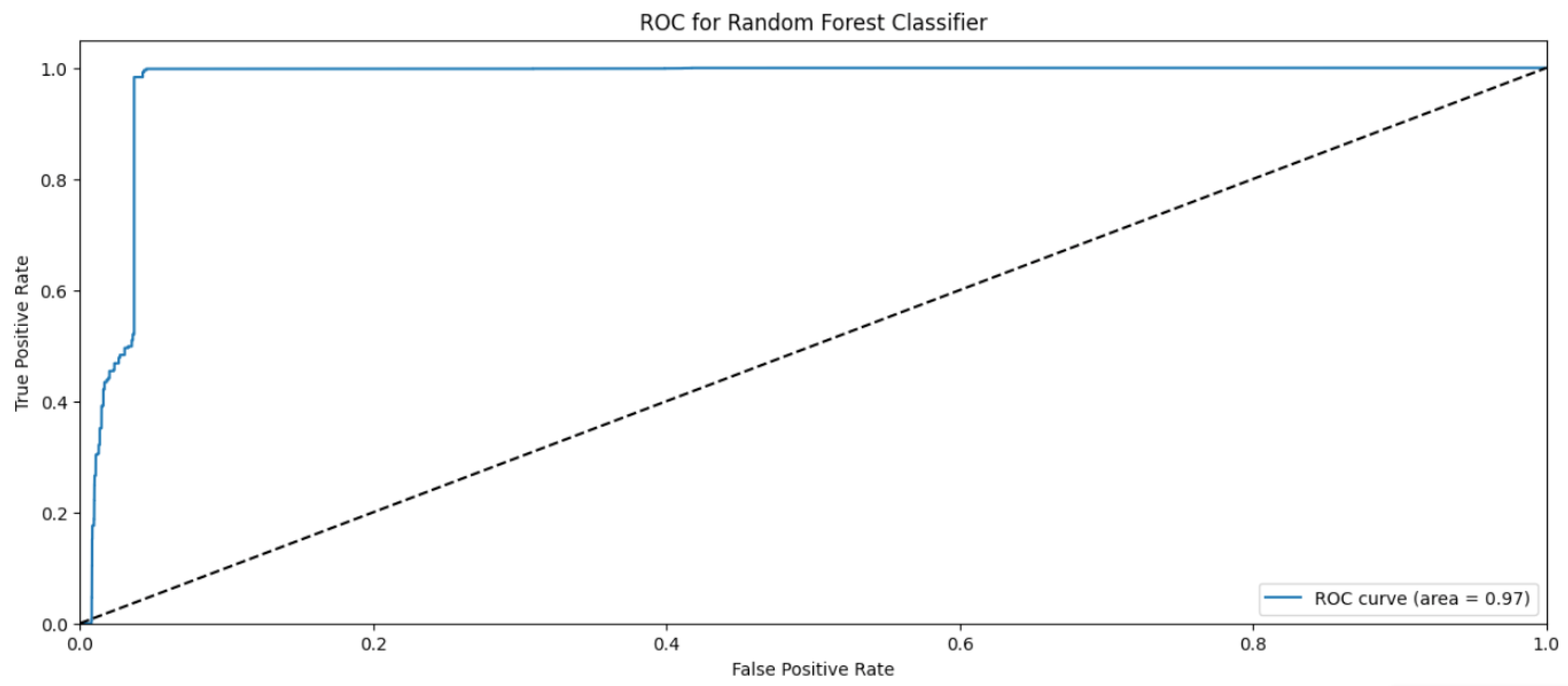
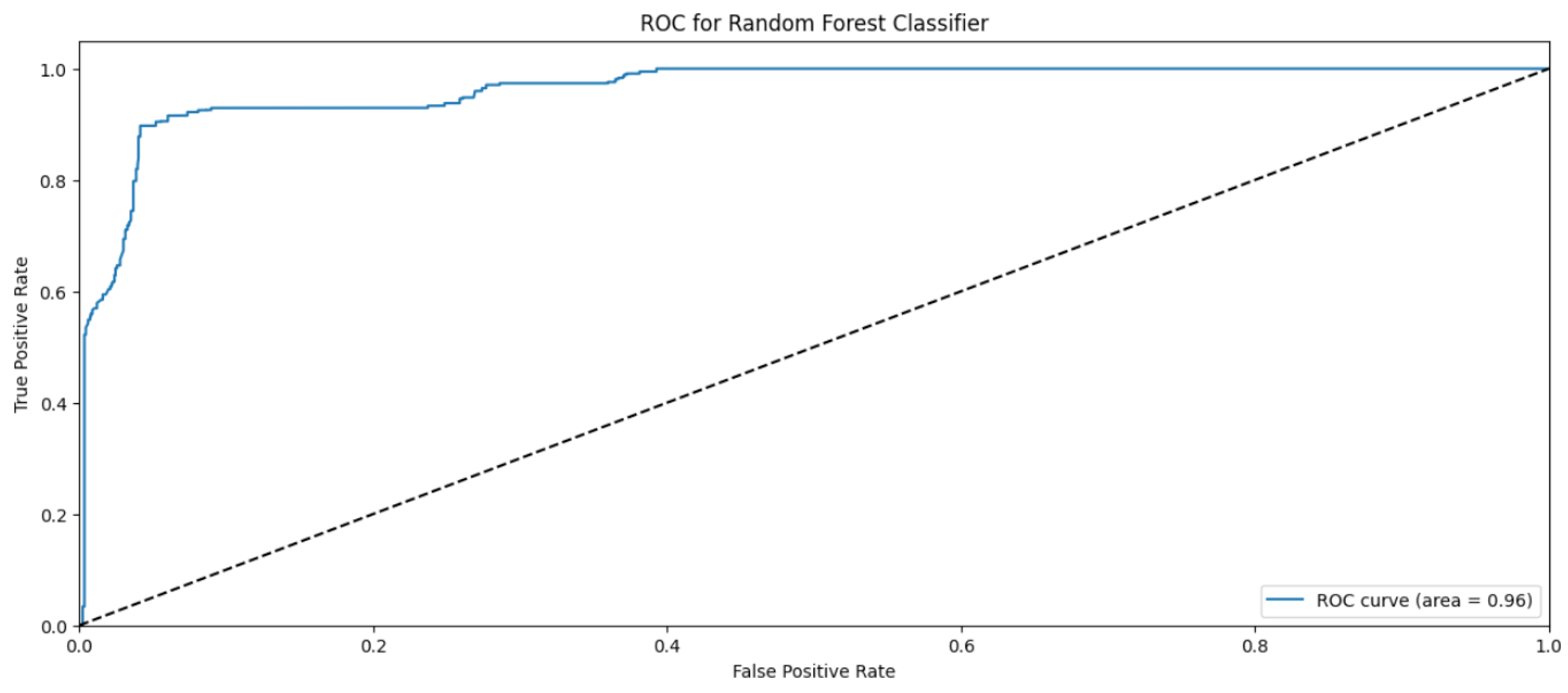
4. Results and Discussions
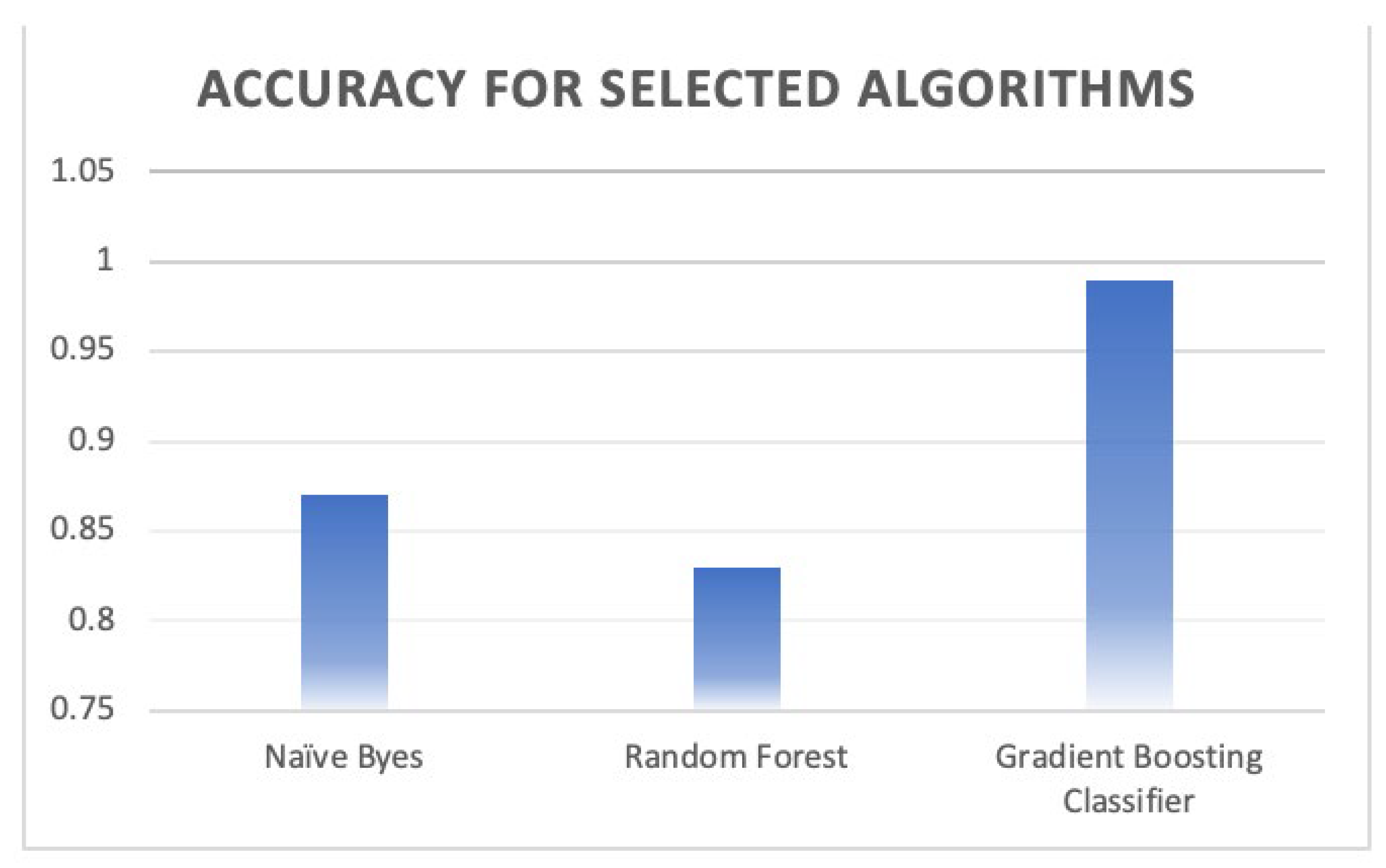
4.1. Naïve Byes
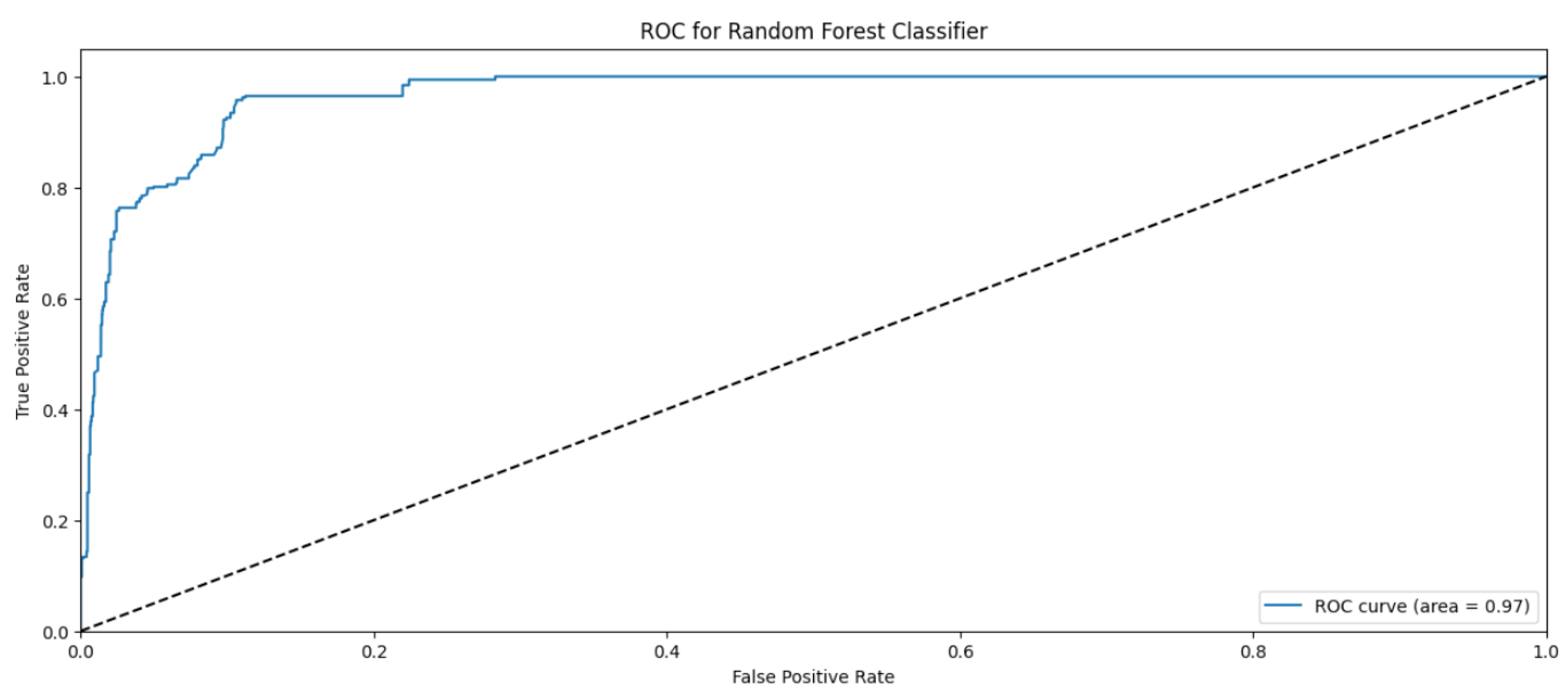
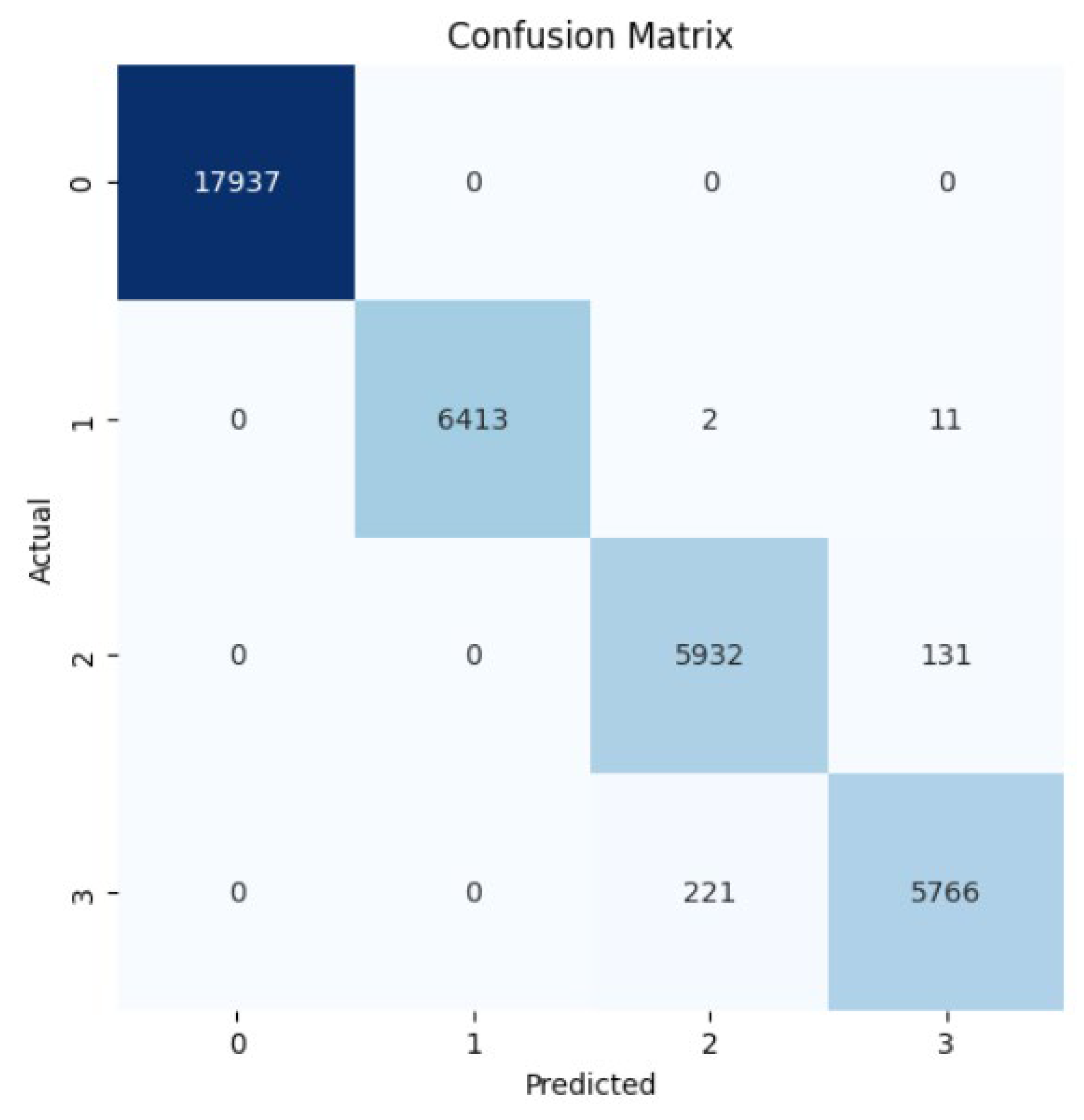
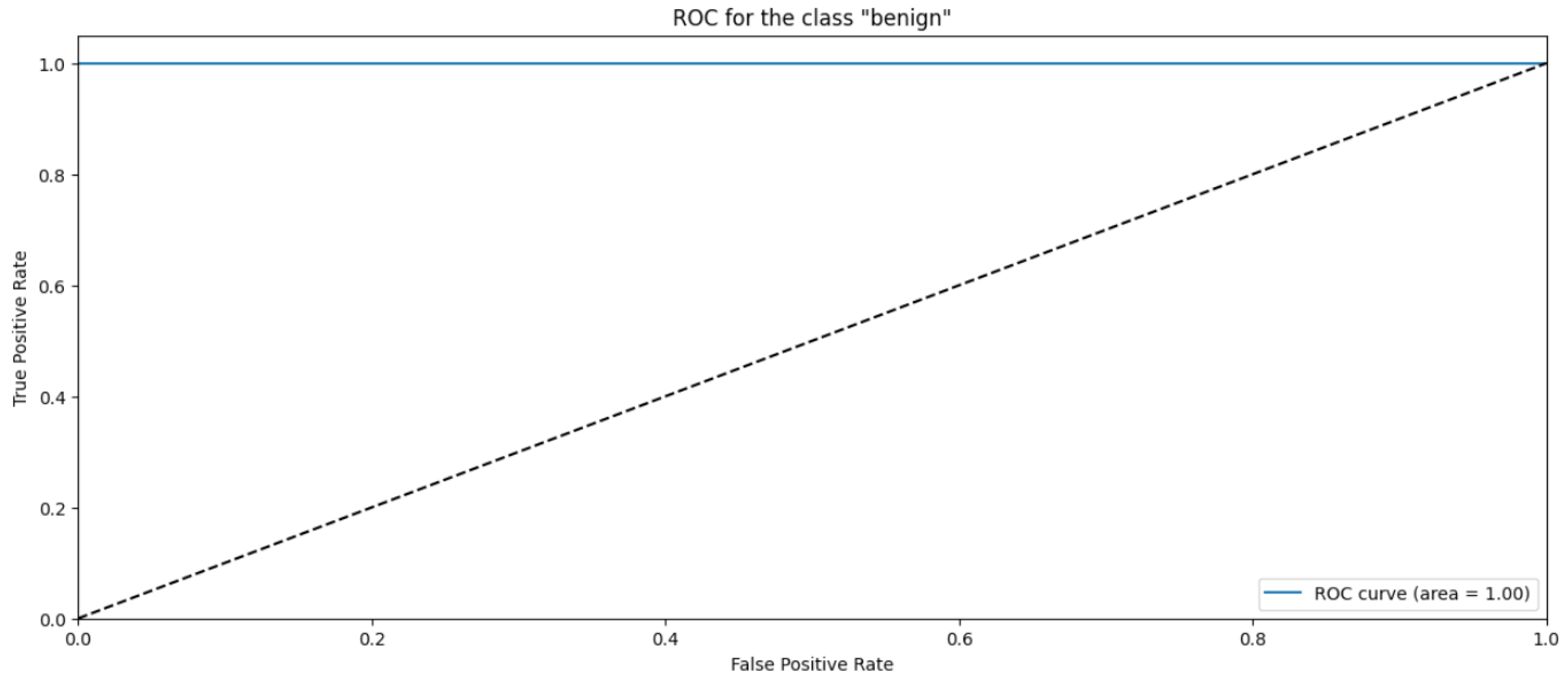
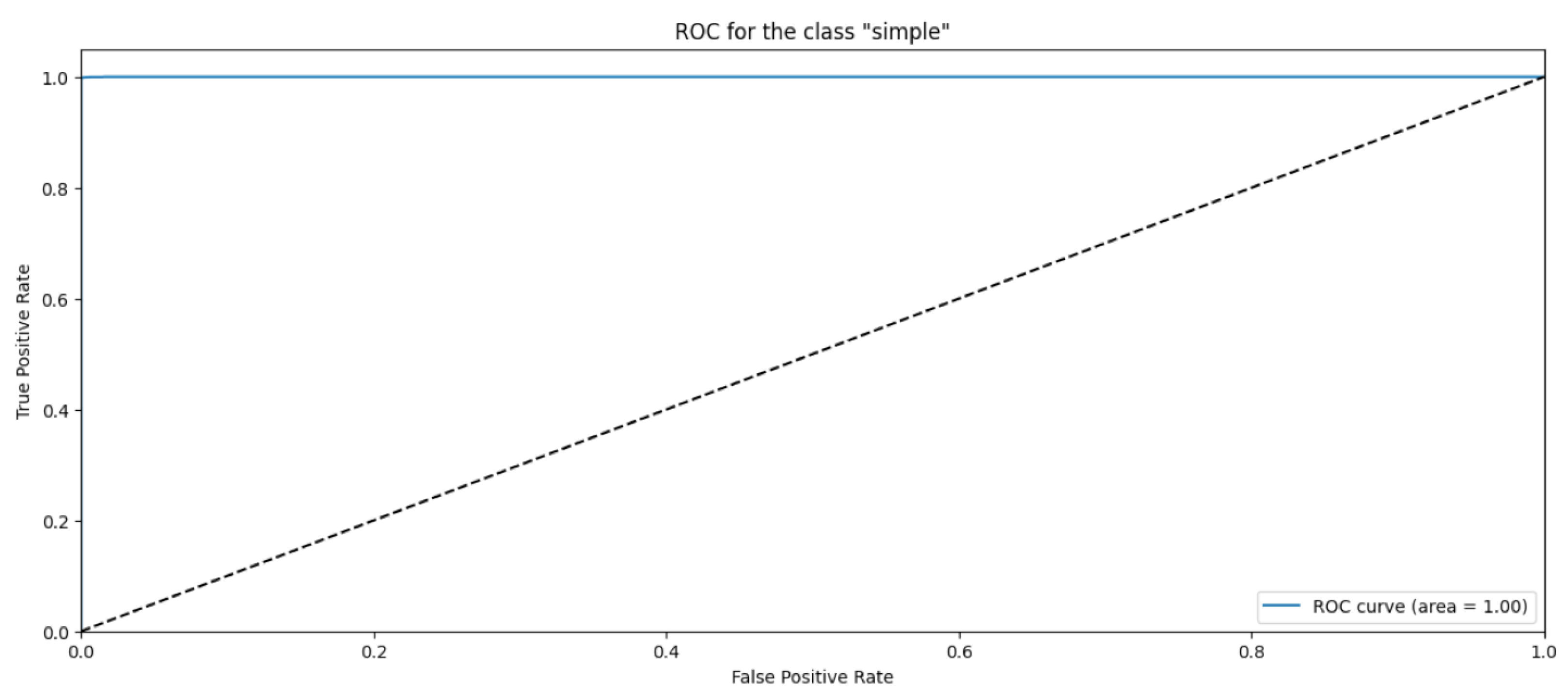
4.2. Random Forest
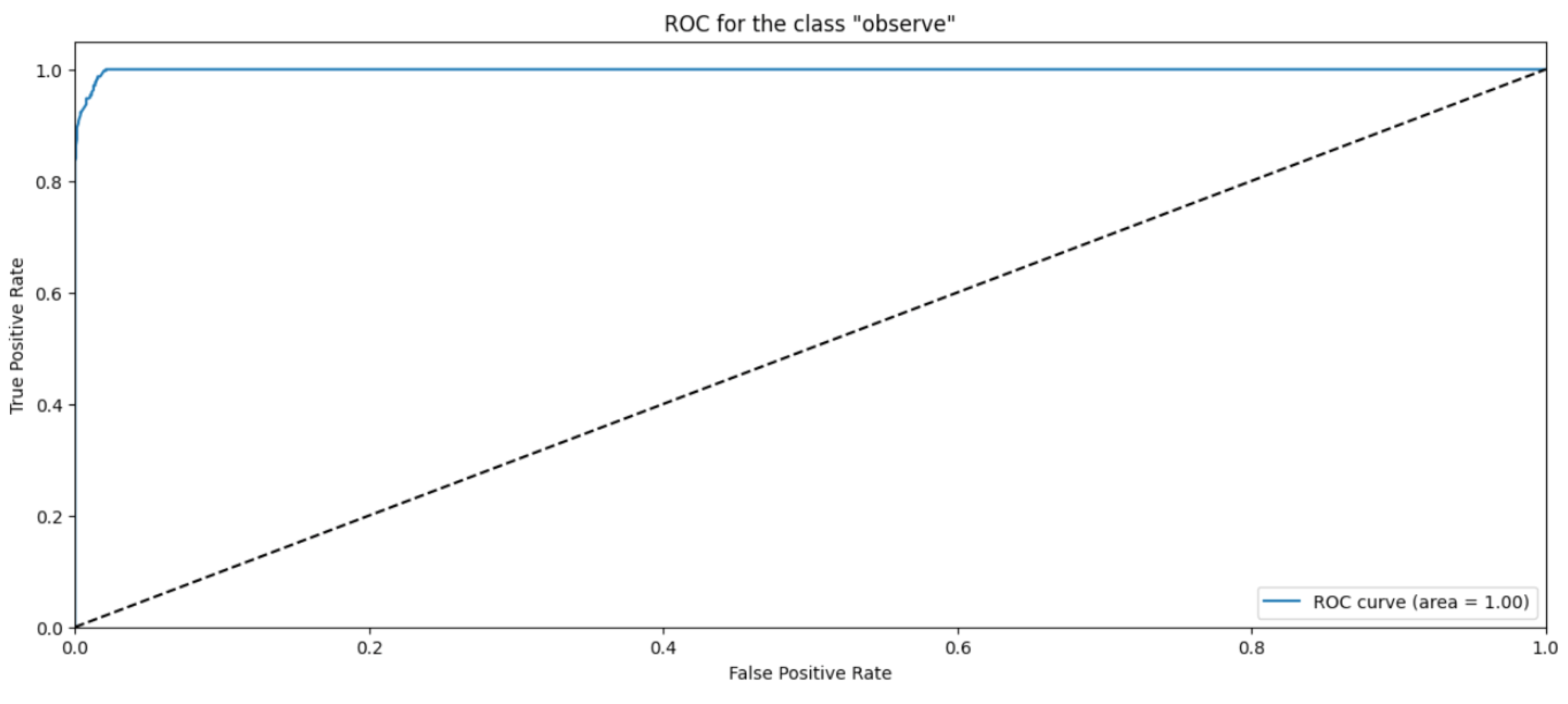
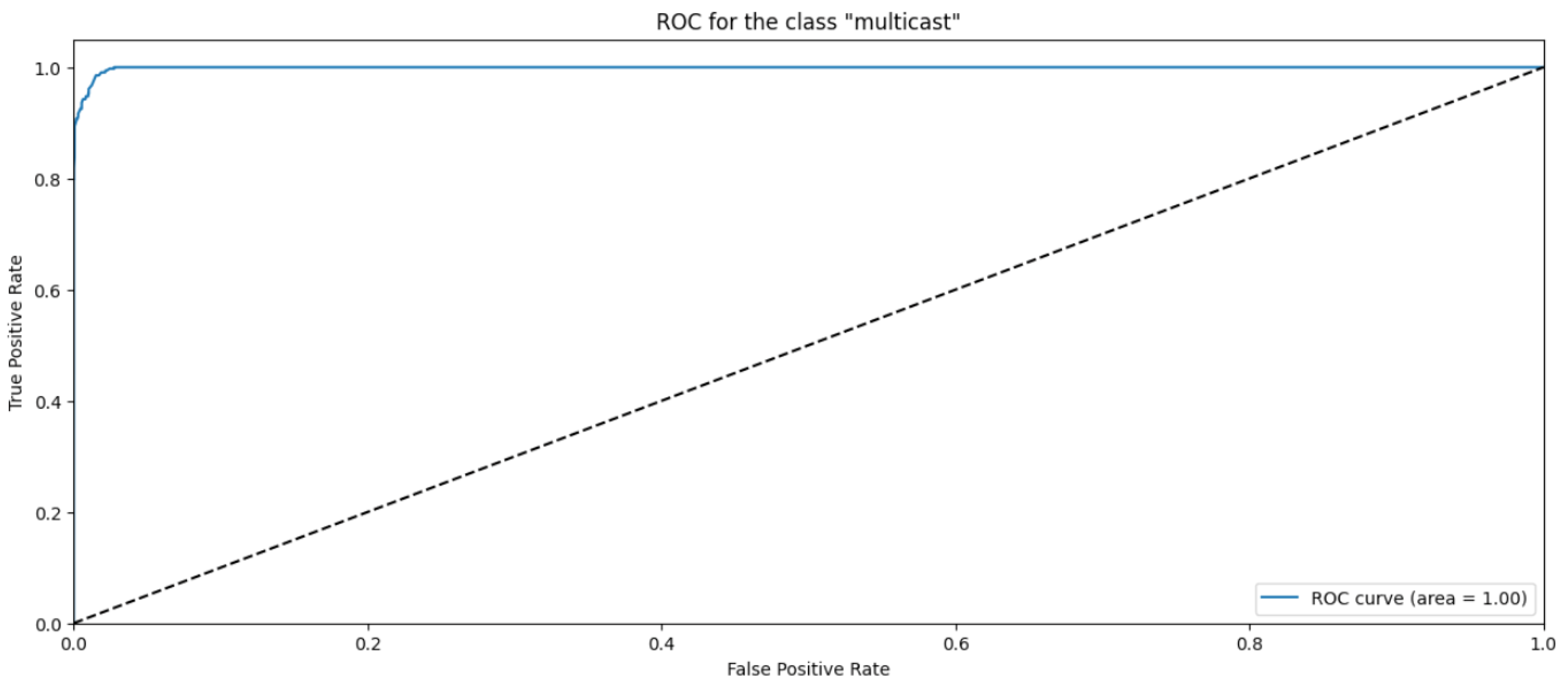
4.3. Gradient Boosting Classifier
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| CoAP | Constrained Application Protocol |
| UDP | User Datagram Protocol |
| TCP | Transmission Control Protocol |
| DTLS | Datagram Transport Layer Security |
| NoSec | No Security mode |
| RPL | Routing Protocol |
| 6LoWPAN | IPv6 over Low-power Wireless Personal Area Networks |
| LLN | Low-Power and Lossy Networks |
| LSPWSN | Lightweight and Secure Protocol for Wireless Sensor Networks |
| MQTT | Message Queuing Telemetry Transport |
| DoS | Denial-of-Service |
| DDoS | Distributed Denial-of-Service |
| SDN | Software Defined Networking |
| Nmap | Network Mapping |
| VIF | Variance Inflation Factor |
References
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defense mechanisms in the IoT network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Syed, N.F. IoT-MQTT Based Denial of Service Attack Modelling and Detection. 2020. Available online: https://ro.ecu.edu.au/theses/2303 (accessed on 5 May 2023).
- Hussain, F.; Abbas, S.G.; Husnain, M.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT DoS and DDoS attack detection using ResNet. In Proceedings of the 2020 IEEE 23rd International Multitopic Conference (IN-MIC), Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–6. [Google Scholar]
- Ragab, M. Hybrid firefly particle swarm optimization algorithm for feature selection problems. Expert Syst. 2023. [CrossRef]
- Alhaidari, F.A.; Alqahtani, E.J. Securing communication between fog computing and IoT using constrained application protocol (coap): A survey. J. Commun. 2020, 15, 14–30. [Google Scholar] [CrossRef]
- Bhardwaj, K.; Miranda, J.C.; Gavrilovska, A. Towards IoT-DDoS prevention using edge computing. In Proceedings of the {USENIX} Workshop on Hot Topics in Edge Computing (HotEdge 18), Boston, MA, USA, 9 July 2018. [Google Scholar]
- Shelby, Z.; Hartke, K.; Bormann, C. RFC 7252: The Constrained Application Protocol (CoAP); ACM, Inc.: New York, NY, USA, 2014. [Google Scholar] [CrossRef]
- Amplification Attacks Using the Constrained Application Protocol (CoAP). (n.d.). IETF Datatracker. Available online: https://datatracker.ietf.org/doc/draft-irtf-t2trg-amplification-attacks/ (accessed on 5 May 2023).
- Capossele, A.; Cervo, V.; De Cicco, G.; Petrioli, C. Security as a CoAP resource: An op-timized DTLS implementation for the IoT. In Proceedings of the 2015 IEEE international conference on communications (ICC), London, UK, 8–12 June 2015; pp. 549–554. [Google Scholar]
- Maleh, Y.; Ezzati, A.; Belaissaoui, M. An enhanced DTLS protocol for Internet of Things applications. In Proceedings of the 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 26–29 October 2016; pp. 168–173. [Google Scholar]
- Kumar, P.M.; Gandhi, U.D. Enhanced DTLS with CoAP-based authentication scheme for the internet of things in healthcare application. J. Supercomput. 2020, 76, 3963–3983. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. CoAP—Application layer connection-less lightweight protocol for the Internet of Things (IoT) and CoAP-IPSEC Security with DTLS Supporting CoAP. In Digital Twin Technologies and Smart Cities; Springer: Berlin/Heidelberg, Germany, 2020; pp. 151–175. [Google Scholar]
- Mathews, J.; Chatterjee, P.; Banik, S. CoAP-DoS: An IoT Network Intrusion Data Set. In Proceedings of the 2022 6th International Conference on Cryptography Security and Privacy (CSP), Tianjin, China, 14–16 January 2022; pp. 91–95. [Google Scholar]
- Granjal, J.; Silva, J.M.; Lourenço, N. Intrusion detection and prevention in CoAP wireless sensor networks using anomaly detection. Sensors 2018, 18, 2445. [Google Scholar] [CrossRef] [PubMed]
- Conti, M.; Kaliyar, P.; Lal, C. Censor: Cloud-enabled secure IoT architecture over SDN paradigm. Concurr. Comput. Pract. Exp. 2019, 31, e4978. [Google Scholar] [CrossRef]
- Özçelik, M.; Chalabianloo, N.; Gür, G. Software-defined edge defense against IoT-based DDoS. In Proceedings of the 2017 IEEE International Conference on Computer and Information Technology (CIT), Helsinki, Finland, 21–23 August 2017; pp. 308–313. [Google Scholar]
- Yin, D.; Zhang, L.; Yang, K. A DDoS attack detection and mitigation with software-defined internet of things framework. IEEE Access 2018, 6, 24694–24705. [Google Scholar] [CrossRef]
- Galeano-Brajones, J.; Carmona-Murillo, J.; Valenzuela-Valdés, J.F.; Luna-Valero, F. Detection and mitigation of dos and DDoS attacks in IoT-based stateful Sdn: An experimental approach. Sensors 2020, 20, 816. [Google Scholar] [CrossRef] [PubMed]
- Yang, Y.; Wang, J.; Zhai, B.; Liu, J. IoT-based DDoS attack detection and mitigation using the edge of sdn. In Proceedings of the International Symposium on Cyberspace Safety and Security, Guangzhou, China, 1–3 December 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 3–17. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-baIoT—Network-based detection of IoT botnet attacks using deep autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Botica, M. Novel approach for detection of IoT generated DDoS traffic. Wirel. Netw. 2021, 27, 1573–1586. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A honeypot with machine learning-based detection framework for defending IoT based botnet DDoS attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 1019–1024. [Google Scholar]
- Soe, Y.N.; Santosa, P.I.; Hartanto, R. DDoS attack detection based on simple ann with smote for IoT environment. In Proceedings of the 2019 Fourth International Conference on Informatics and Computing (ICIC), Semarang, Indonesia, 16–17 October 2019; pp. 1–5. [Google Scholar]
- Dao, N.-N.; Phan, T.V.; Kim, J.; Bauschert, T.; Cho, S. Securing heterogeneous IoT with intelligent DDoS attack behavior learning. arXiv 2017, arXiv:1711.06041. [Google Scholar] [CrossRef]
- Jia, Y.; Zhong, F.; Alrawais, A.; Gong, B.; Cheng, X. Flowguard: An intelligent edge defense mechanism against IoT DDoS attacks. IEEE Internet Things J. 2020, 7, 9552–9562. [Google Scholar] [CrossRef]
- Dai, W.; Wan, P.; Qiang, W.; Yang, L.T.; Zou, D.; Jin, H.; Xu, S.; Huang, Z. Tnguard: Securing IoT oriented tenant networks based on sdn. IEEE Internet Things J. 2018, 5, 1411–1423. [Google Scholar] [CrossRef]
- Djouani, R.; Djouani, K.; Boutekkouk, F.; Sahbi, R. A security proposal for IoT integrated with sdn and cloud. In Proceedings of the 2018 6th International Conference on Wireless Networks and Mobile Communications (WINCOM), Marrakesh, Morocco, 16–19 October 2018; pp. 1–5. [Google Scholar]
- Muthanna, A.; A Ateya, A.; Khakimov, A.; Gudkova, I.; Abuarqoub, A.; Samouylov, K.; Koucheryavy, A. Secure and reliable IoT networks using fog computing with software-defined networking and blockchain. J. Sens. Actuator Netw. 2019, 8, 15. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-iot dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. Netflow datasets for machine learn-ing-based network intrusion detection systems. In Big Data Technologies and Applications: 10th EAI International Conference, BDTA 2020, and 13th EAI International Conference on Wireless Internet, WiCON 2020, Virtual Event, December 11, 2020, Proceedings 10; Springer International Publishing: Cham, Switzerland, 2020; pp. 117–135. [Google Scholar]
- Ghazanfar, S.; Hussain, F.; Rehman, A.U.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. March. Iot-flock: An open-source framework for iot traffic generation. In Proceedings of the 2020 International Conference on Emerging Trends in Smart Technologies (ICETST), Karachi, Pakistan, 26–27 March 2020; pp. 1–6. [Google Scholar]
- O. (n.d.). GitHub-Obgm/Libcoap: A CoAP (RFC 7252) Implementation in C. GitHub. Available online: https://github.com/obgm/libcoap (accessed on 5 May 2023).
- Coap-Resources NSE Script—Nmap Scripting Engine Documentation. (n.d.). Available online: https://nmap.org/nsedoc/scripts/coap-resources.html (accessed on 5 May 2023).
- Explore. (n.d.). Available online: https://www.shodan.io/explore (accessed on 5 May 2023).
- (n.d.-a). GitHub-Eclipse-Californium/Californium: CoAP/DTLS Java Implementation. GitHub. Available online: https://github.com/eclipse-californium/californium (accessed on 5 May 2023).
- Wireshark Display Filter Reference: Constrained Application Protocol. (n.d.). Available online: https://www.wireshark.org/docs/dfref/c/coap.html (accessed on 5 May 2023).
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Almeghlef, S.M.; AL-Ghamdi, A.A.-M.; Ramzan, M.S.; Ragab, M. Application Layer-Based Denial-of-Service Attacks Detection against IoT-CoAP. Electronics 2023, 12, 2563. [Google Scholar] [CrossRef]
- Katib, I.; Ragab, M. Blockchain-Assisted Hybrid Harris Hawks Optimization Based Deep DDoS Attack Detection in the IoT Environment. Mathematics 2023, 11, 1887. [Google Scholar] [CrossRef]
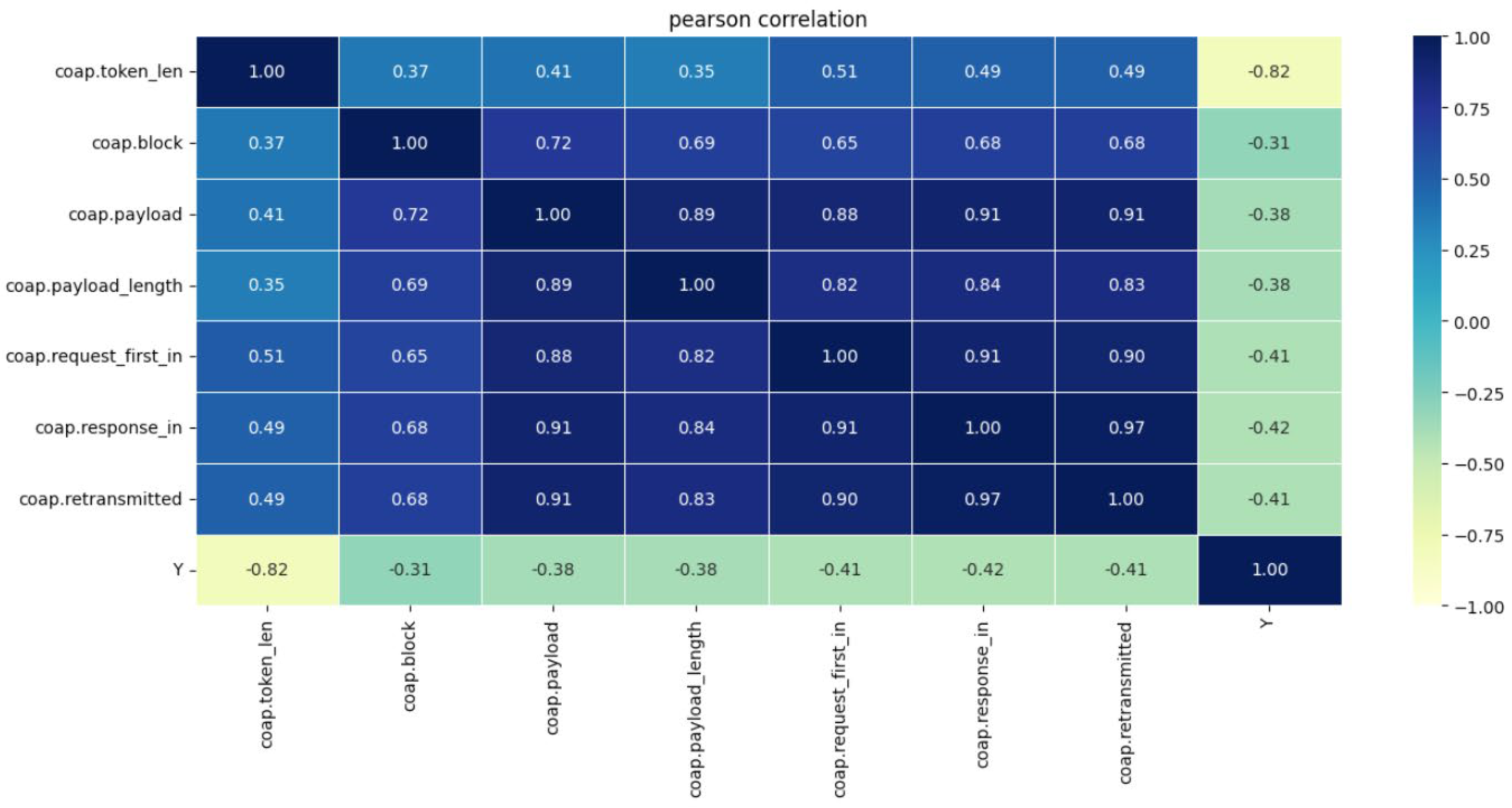
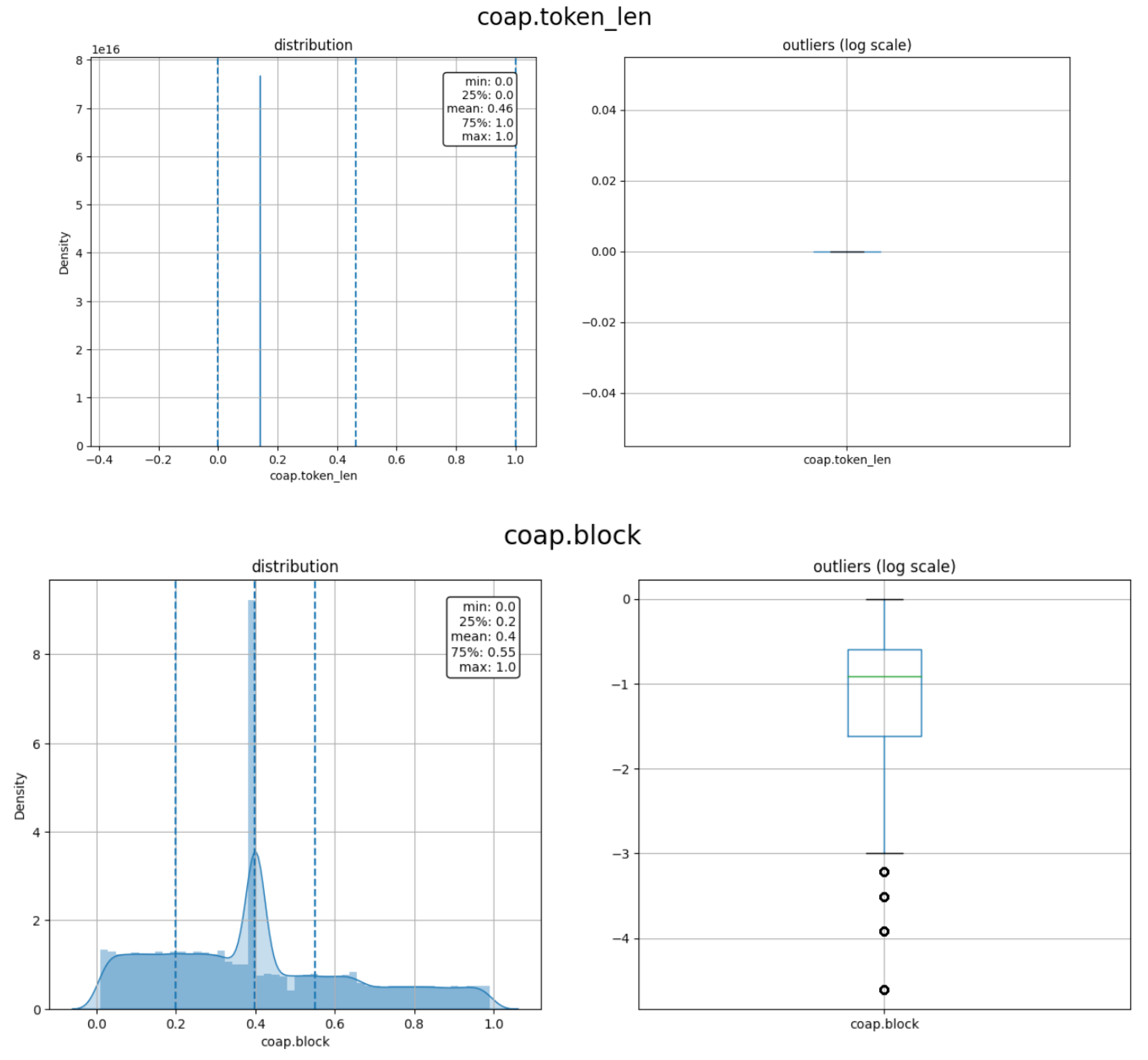

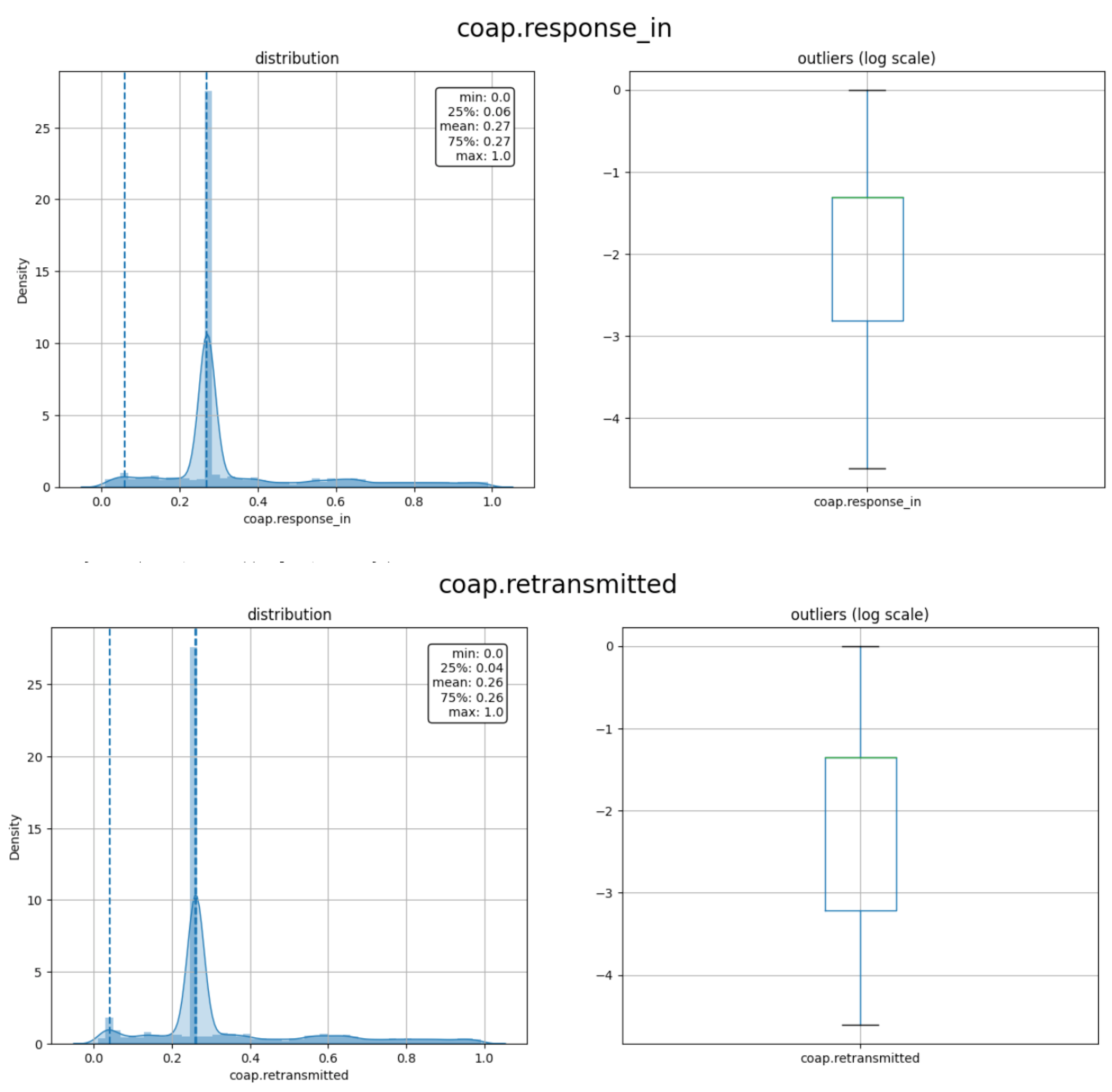

| Research Objective | Methodology Used | Results | Limitations |
|---|---|---|---|
| Employ Mobile Edge Computing (MEC) to safeguard IoT environment (2017) | MECshield is proposed that uses smart filter distributed over MEC to mitigate DDoS attack | Better detection accuracy and DDoS bottleneck is resolved | N/A |
| Design framework for Software-Defined Internet of Things (SD-IoT) (2018) | SD-IoT uses cosine similarity of the vectors of the incoming packet and based on that it decides if a DDoS attack is triggered or not. | Detect and block the attack at the source | Susceptible to large amounts of traffic |
| Edge computing-based cloud platform (2018) | Cloud ShadowNet web service will receive the packets from edge nodes to vet them | It performs 10× faster in detecting UDP flood attack than existing models | Focus on speed but ignore accuracy since no method to differentiate between attack and Flash crowd |
| Anomaly-based detection to detect IoT traffic attacks (2018) | Deep Autoencoders is used to learn the behavior of normal IoT traffic and then detect the anomalies if re-construction has failed | N-BaIoT succeeded in detecting every single attack with 100% TPR | Deployment in a real-world scenario is costly |
| Securing tenant IoT network (2018) | TNGuard degrades the tenant network administrator to ensure the security | Several metrics used show sufficient work with most of the applications | Lack of dynamic integrity verification |
| Deploy SDN and cloud to secure IoT network (2018) | Delegate security mechanism to the cloud and management to the controllers and data plane to gateways | Security architecture containing trusted SDN controller& | Not tested in real environment |
| Detect DDoS based on the traffic behavior (2019) | Anomaly-based detection that measures the deviation of any traffic compared to legitimate traffic from the same class | Adaboost can effectively detect anomalies in the traffic behavior | No significant criterion to classify IoT devices |
| Honeypot-based detection framework (2019) | Luring the attacker to invade the IoT protection wall and then log all the activities and gain useful information about the new attacks | New variants of attacks are detected | Not tested in real environment |
| Fog Computing and SDN is deployed to secure IoT network (2019) | IoT-Fog system integrated with SDN and blockchain for securing IoT network | Resource utilization is efficient and the latency of end-to-end is reduced | N/A |
| Apply ANN to classify benign packets and DDoS packets (2019) | Constructing a simple ANN network with a single layer to classify DDoS attacks and benign packets | The detection results reached up to 100% | N/A |
| Use state-of-the-art deep learning techniques to classify DDoS attacks (2020) | Transform IoT traffic to image form and train ResNet over the new image format | ResNet gains 99.99% accuracy for binary classification | N/A |
| Detect IoT-DDoS at the edge servers (2020) | FlowGuard is employed at the edge server to vet the traffics passing through the server | Identification of long-short-term memory gains accuracy of 98.8% | N/A |
| Stateful SDN architecture is used to develop an entropy-based detection for IoT-attack (2020) | calculating the correlation of the entropy values for different extracted features to identify the attacks | Entropy-based on SDN can mitigate the attack by adding entries to the flow table of switches | Considers only limited types of DDoS attacks |
| Edge computing-based SDN (2020) | Intelligence is employed in the edge devices (OF switches) instead of the controller | 99% precision rate for detecting the attack at the OF switches | Susceptible to sophisticated DDoS attack like Crossfire attack |
| Feature | Description | Type |
|---|---|---|
| Coap.block_length | Block length | Unsigned Integer (4 bytes) |
| Coap.blocks | Block | Label |
| Coap.code | Code | Unsigned Integer |
| Coap.token_len | Token length | Unsigned Integer (1 byte) |
| Coap.type | Type | Unsigned Integer (1 byte) |
| Coap.block | Block | Frame number |
| Coap.block.count | Block count | Unsigned Integer (4 bytes) |
| Coap.block.error | Block defragmentation error | Frame number |
| Coap.block.multiple_tails | Block has multiple tails | Boolean |
| Coap.block.overlap | Block overlap | Boolean |
| Coap.block.overlap.conflicts | Block overlapping with conflicting data | Boolean |
| Coap.block.reassembled.in | Reassembled in | Frame number |
| coap.block.reassembled.length | Reassembled block length | Unsigned integer (4 byte) |
| coap.block.too_long | Block too long | Boolean |
| coap.length | Length | Unsigned integer (4 byte) |
| coap.oscore_kid | OSCORE Key ID | Byte sequence |
| coap.oscore_kid_context | OSCORE Key ID context | Byte sequence |
| coap.oscore_piv | OSCORE Partial IV | Byte sequence |
| coap.payload | Payload | Character string |
| coap.payload_desc | Payload Desc | Character string |
| coap.payload_length | Payload Length | Unsigned integer (4 byte) |
| coap.request_first_in | Retransmission of request in | Frame number |
| coap.response_in | Response in | Frame number |
| coap.retransmitted | Retransmitted | Label |
| Class | Precision | Recall | F1-Score | Support |
|---|---|---|---|---|
| Benign | 1.00 | 1.00 | 1.00 | 18,145 |
| Simple | 0.66 | 1.00 | 0.79 | 6303 |
| Observe | 0.82 | 0.38 | 0.51 | 5880 |
| Multicast | 0.86 | 0.85 | 0.85 | 6085 |
| Accuracy | 0.87 | 36,413 | ||
| Macro Average | 0.83 | 0.81 | 0.79 | 36,413 |
| Weighted Average | 0.89 | 0.87 | 0.86 | 36,413 |
| Class | Precision | Recall | F1-Score | Support |
|---|---|---|---|---|
| Benign | 0.79 | 1.00 | 0.88 | 18,068 |
| Simple | 0.99 | 0.48 | 0.65 | 6453 |
| Observe | 0.89 | 0.82 | 0.85 | 5914 |
| Multicast | 0.83 | 0.68 | 0.74 | 5978 |
| Accuracy | 0.83 | 36,413 | ||
| Macro Average | 0.87 | 0.74 | 0.78 | 36,413 |
| Weighted Average | 0.85 | 0.83 | 0.81 | 36,413 |
| Class | Precision | Recall | F1-Score | Support |
|---|---|---|---|---|
| Benign | 1.00 | 1.00 | 1.00 | 18,036 |
| Simple | 1.00 | 1.00 | 1.00 | 6363 |
| Observe | 0.96 | 0.98 | 0.97 | 6053 |
| Multicast | 0.98 | 0.96 | 0.97 | 5961 |
| Accuracy | 0.99 | 36,413 | ||
| Macro Average | 0.98 | 0.98 | 0.98 | 36,413 |
| Weighted Average | 0.99 | 0.99 | 0.99 | 36,413 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almeghlef, S.M.; AL-Ghamdi, A.A.-M.; Ramzan, M.S.; Ragab, M. Machine Learning-Based DoS Amplification Attack Detection against Constrained Application Protocol. Appl. Sci. 2023, 13, 7391. https://doi.org/10.3390/app13137391
Almeghlef SM, AL-Ghamdi AA-M, Ramzan MS, Ragab M. Machine Learning-Based DoS Amplification Attack Detection against Constrained Application Protocol. Applied Sciences. 2023; 13(13):7391. https://doi.org/10.3390/app13137391
Chicago/Turabian StyleAlmeghlef, Sultan M., Abdullah AL-Malaise AL-Ghamdi, Muhammad Sher Ramzan, and Mahmoud Ragab. 2023. "Machine Learning-Based DoS Amplification Attack Detection against Constrained Application Protocol" Applied Sciences 13, no. 13: 7391. https://doi.org/10.3390/app13137391
APA StyleAlmeghlef, S. M., AL-Ghamdi, A. A.-M., Ramzan, M. S., & Ragab, M. (2023). Machine Learning-Based DoS Amplification Attack Detection against Constrained Application Protocol. Applied Sciences, 13(13), 7391. https://doi.org/10.3390/app13137391







