Image Copy-Move Forgery Detection Based on Fused Features and Density Clustering
Abstract
1. Introduction
2. Related Works
3. SURF and A-KAZE Descriptors
3.1. SURF Descriptor
3.2. A-KAZE Descriptor
4. The Proposed Scheme
4.1. SURF and A-KAZE Feature Extraction
4.2. g2NN Feature Matching
4.3. Removing Mismatched Pairs
- Core point: If point has at least points in its neighborhood, then is a core point. We can define the sets of all core points as and the set of non-core points as .
- Boundary point: If satisfies and is in the neighborhood of a core point, then is a boundary point. Boundary points can be located within the neighborhood of one or more core points at the same time.
- Outlier: This is neither a core point nor a boundary point.
4.4. Tampered Region Localization
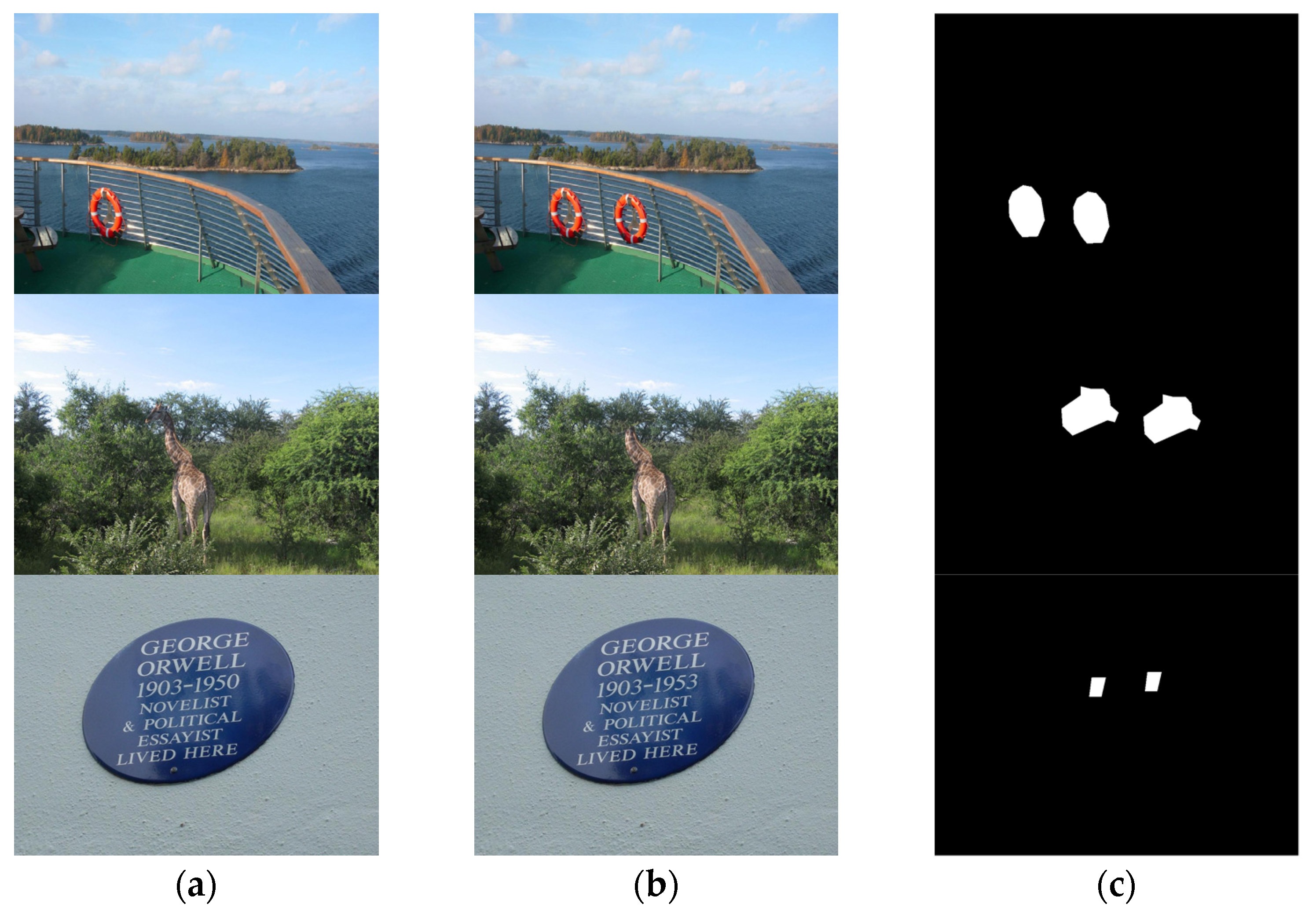
5. Experimental Results
5.1. Datasets
5.1.1. Ardizzone
5.1.2. CoMoFoD
5.2. Evaluation Metrics
5.3. Lab Environment
5.4. Copy-Move Forgery Detection
5.4.1. Geometric Transformation Forgery Detection
5.4.2. Post-Processing Forgery Detection
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bensaad, A.; Loukhaoukha, K.; Sadoudi, S. Keypoint-based copy-move forgery detection in digital images: A survey. In Proceedings of the 2022 7th International Conference on Image and Signal Processing and Their Applications (ISPA), Mostaganem, Algeria, 8–9 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Paul, S.; Pal, A.K. A fast copy-move image forgery detection approach on a reduced search space. Multimed. Tools Appl. 2023, 82, 25917–25944. [Google Scholar] [CrossRef]
- Anushree, R.; Vinay Kumar, S.B.; Sachin, B.M. A Survey on Copy Move Forgery Detection (CMFD) Technique. In Proceedings of the 2023 International Conference on Intelligent and Innovative Technologies in Computing, Electrical and Electronics (IITCEE), Bengaluru, India, 27–28 January 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 439–443. [Google Scholar]
- Venugopalan, A.K.; Gopakumar, G. Copy-Move Forgery Detection-A Study and the Survey. In Proceedings of the 2022 Third International Conference on Intelligent Computing Instrumentation and Control Technologies (ICICICT), Kannur, India, 11–12 August 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1327–1334. [Google Scholar]
- Zhang, Z.; Wang, C.; Zhou, X. A survey on passive image copy-move forgery detection. J. Inf. Process. Syst. 2018, 14, 6–31. [Google Scholar]
- Fridrich, J. Detection of copy-move forgery in digital images. In Proceedings of the Digital Forensic Research Workshop, Cleveland, OH, USA, 6–8 August 2003; pp. 19–23. [Google Scholar]
- Kumar, A.; Singh, K.U.; Swarup, C.; Singh, T.; Raja, L.; Kumar, A. Detection of Copy-Move Forgery Using Euclidean Distance and Texture Features. Traitement Signal 2022, 39, 781–788. [Google Scholar] [CrossRef]
- Fattah, S.A.; Ullah, M.M.I.; Ahmed, M.; Ahmmed, I.; Shahnaz, C. A scheme for copy-move forgery detection in digital images based on 2D-DWT. In Proceedings of the 2014 IEEE 57th International Midwest Symposium on Circuits and Systems (MWSCAS), Station, TX, USA, 3–6 August 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 801–804. [Google Scholar]
- Sabeena, M.; Abraham, L.; Varghese, A. Digital Image Forgery Detection Using Local Binary Pattern (LBP) and Harlick Transform with classification. In Proceedings of the 2021 IEEE International Power and Renewable Energy Conference (IPRECON), Kollam, India, 24–26 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–6. [Google Scholar]
- Rahma, F.I.; Utami, E.; Al-Fatta, H. Gaussian Pyramid Decomposition in Copy-Move Image Forgery Detection with SIFT and Zernike Moment Algorithms. Telematika 2022, 15, 1–13. [Google Scholar] [CrossRef]
- Ye, W.; Zeng, Q.; Peng, Y.; Liu, Y.; Chang, C.C. A two-stage detection method of copy-move forgery based on parallel feature fusion. EURASIP J. Wirel. Commun. Netw. 2022, 2022, 30. [Google Scholar] [CrossRef]
- Lee, J.C.; Chang, C.P.; Chen, W.K. Detection of copy–move image forgery using histogram of orientated gradients. Inf. Sci. 2015, 321, 250–262. [Google Scholar] [CrossRef]
- Qin, C.; Chen, X.; Ye, D.; Wang, J.; Sun, X. A novel image hashing scheme with perceptual robustness using block truncation coding. Inf. Sci. 2016, 361, 84–99. [Google Scholar] [CrossRef]
- Wang, C.; Huang, Z.; Qi, S.; Yu, Y.; Shen, G.; Zhang, Y. Shrinking the Semantic Gap: Spatial Pooling of Local Moment Invariants for Copy-Move Forgery Detection. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1064–1079. [Google Scholar] [CrossRef]
- Kumar, S.; Mukherjee, S.; Pal, A.K. An improved reduced feature-based copy-move forgery detection technique. Multimed. Tools Appl. 2023, 82, 1431–1456. [Google Scholar] [CrossRef]
- Salman, M.; Uhl, A. Countering Anti-forensics of SIFT-based Copy-Move Detection. In Proceedings of the 2020 25th International Conference on Pattern Recognition (ICPR), Milan, Italy, 10–15 January 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 2701–2707. [Google Scholar]
- Badr, A.; Youssif, A.; Wafi, M. A robust copy-move forgery detection in digital image forensics using SURF. In Proceedings of the 2020 8th International Symposium on Digital Forensics and Security (ISDFS), Beirut, Lebanon, 1–2 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Kumar, N.; Meenpal, T. Salient keypoint-based copy–move image forgery detection. Aust. J. Forensic Sci. 2023, 55, 331–354. [Google Scholar] [CrossRef]
- Samel, M.; Reddy, A.M. An Empirical Study on Copy-Move Forgery Detection Techniques in Images. Math. Stat. Eng. Appl. 2022, 71, 183–193. [Google Scholar]
- Benhamza, H.; Djeffal, A.; Cheddad, A. Image forgery detection review. In Proceedings of the 2021 International Conference on Information Systems and Advanced Technologies (ICISAT), Tebessa, Algeria, 27–28 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–7. [Google Scholar]
- Pan, X.; Lyu, S. Region duplication detection using image feature matching. IEEE Trans. Inf. Forensics Secur. 2010, 5, 857–867. [Google Scholar] [CrossRef]
- Lowe, D.G. Distinctive image features from scale-invariant key points. Int. J. Comput. Vis. 2004, 60, 91–110. [Google Scholar] [CrossRef]
- Zheng, J.; Zhang, K. Copy-Move Forgery Detection Algorithm based on Feature Point Clustering. In Proceedings of the 2022 IEEE 6th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 4–6 March 2022; IEEE: Piscataway, NJ, USA, 2022; Volume 6, pp. 775–780. [Google Scholar]
- Fischler, M.A.; Bolles, R.C. Random sample consensus: A paradigm for model fitting with applications to image analysis and automated cartography. Commun. ACM 1981, 24, 381–395. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, H.; Chen, Y.; Wu, H.; Wang, H. A passive forensic scheme for copy-move forgery based on superpixel segmentation and K-means clustering. Multimed. Tools Appl. 2020, 79, 477–500. [Google Scholar] [CrossRef]
- Wang, X.Y.; Wang, C.; Wang, L.; Jiao, L.X.; Yang, H.Y.; Niu, P.P. A fast and high accurate image copy-move forgery detection approach. Multidimens. Syst. Signal Process. 2020, 31, 857–883. [Google Scholar] [CrossRef]
- Wang, X.; Chen, W.; Niu, P.; Yang, H. Image copy-move forgery detection based on dynamic threshold with dense points. J. Vis. Commun. Image Represent. 2022, 89, 103658. [Google Scholar] [CrossRef]
- Fatima, B.; Ghafoor, A.; Ali, S.S.; Riaz, M.M. FAST, BRIEF and SIFT based image copy-move forgery detection technique. Multimed. Tools Appl. 2022, 81, 43805–43819. [Google Scholar] [CrossRef]
- Orhei, C.; Radu, L.; Mocofan, M.; Vert, S.; Vasiu, R. Urban landmark detection using A-KAZE features and vector of aggregated local descriptors. In Proceedings of the 2022 International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 10–11 November 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–4. [Google Scholar]
- Ouyang, T.; Shen, X. Online structural clustering based on DBSCAN extension with granular descriptors. Inf. Sci. 2022, 607, 688–704. [Google Scholar] [CrossRef]
- Sujin, J.S.; Sophia, S. Copy-Move Geometric Tampering Estimation Through Enhanced SIFT Detector Method. Comput. Syst. Sci. Eng. 2023, 44, 157–171. [Google Scholar] [CrossRef]
- Bay, H.; Ess, A.; Tuytelaars, T.; Van Gool, L. Speeded-up robust features (SURF). Comput. Vis. Image Underst. 2008, 110, 346–359. [Google Scholar] [CrossRef]
- Perona, P.; Malik, J. Scale-space and edge detection using anisotropic diffusion. IEEE Trans. Pattern Anal. Mach. Intell. 1990, 12, 629–639. [Google Scholar] [CrossRef]
- Alcantarilla, P.F.; Solutions, T. Fast explicit diffusion for accelerated features in nonlinear scale spaces. IEEE Trans. Patt. Anal. Mach. Intell. 2011, 34, 1281–1298. [Google Scholar]
- Amerini, I.; Ballan, L.; Caldelli, R.; Del Bimbo, A.; Serra, G. A sift-based forensic method for copy–move attack detection and transformation recovery. IEEE Trans. Inf. Forensics Secur. 2011, 6, 1099–1110. [Google Scholar] [CrossRef]
- Borah, B.; Bhattacharyya, D.K. An improved sampling-based DBSCAN for large spatial databases. In Proceedings of the International Conference on Intelligent Sensing and Information Processing, Chennai, India, 4–7 January 2004; IEEE: Piscataway, NJ, USA, 2004; pp. 92–96. [Google Scholar]
- Ardizzone, E.; Bruno, A.; Mazzola, G. Copy–move forgery detection by matching triangles of key points. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2084–2094. [Google Scholar] [CrossRef]
- Aydin, Y.Ι. Comparison of color features on copy-move forgery detection problem using HSV color space. Aust. J. Forensic Sci. 2022, 1–17. [Google Scholar] [CrossRef]











| Row | First Row | Second Row | Third Row | Fourth Row | |
|---|---|---|---|---|---|
| Feature | |||||
| SIFT | 0 | 16 | 215 | 16 | |
| SURF | 0 | 2 | 124 | 5 | |
| A-KAZE | 0 | 23 | 175 | 5 | |
| BRISK | 0 | 17 | 96 | 4 | |
| SURF + A-KAZE | 98 | 145 | 325 | 18 | |
| Method | (%) | (%) | (%) |
|---|---|---|---|
| Badr et al. [17] | 89.52 | 91.23 | 90.37 |
| Aydin et al. [38] | 90.23 | 90.56 | 90.39 |
| Proposed method | 92.75 | 92.43 | 92.89 |
| Method | (%) | (%) | (%) |
|---|---|---|---|
| Badr et al. [17] | 88.56 | 90.54 | 89.58 |
| Aydin et al. [38] | 89.46 | 91.56 | 90.50 |
| Proposed method | 95.23 | 93.78 | 95.12 |
| Image Dataset | Precision | Recall | |
|---|---|---|---|
| Ardizzone | ±0.14 | ±0.20 | ±0.21 |
| CoMoFoD | ±0.15 | ±0.24 | ±0.28 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fu, G.; Zhang, Y.; Wang, Y. Image Copy-Move Forgery Detection Based on Fused Features and Density Clustering. Appl. Sci. 2023, 13, 7528. https://doi.org/10.3390/app13137528
Fu G, Zhang Y, Wang Y. Image Copy-Move Forgery Detection Based on Fused Features and Density Clustering. Applied Sciences. 2023; 13(13):7528. https://doi.org/10.3390/app13137528
Chicago/Turabian StyleFu, Guiwei, Yujin Zhang, and Yongqi Wang. 2023. "Image Copy-Move Forgery Detection Based on Fused Features and Density Clustering" Applied Sciences 13, no. 13: 7528. https://doi.org/10.3390/app13137528
APA StyleFu, G., Zhang, Y., & Wang, Y. (2023). Image Copy-Move Forgery Detection Based on Fused Features and Density Clustering. Applied Sciences, 13(13), 7528. https://doi.org/10.3390/app13137528





