Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions
Abstract
1. Introduction
| Ref | Concentrate on | Limitations |
|---|---|---|
| [14,17,19,20] | Focused on discussing risks and security issues related to BYOD. | Not comprehensive for all security and privacy requirements and access control based on three layers. |
| [15] | Focused on techniques connected to the authenticity criteria. | Other * security and privacy criteria received less attention. |
| [16] | Overview of the BYOD compliance theories. | Not analysing technologies based on privacy criteria. |
| [21] | Classification scheme for proposed solutions based on identified security issues. | Not analysing technologies based on privacy criteria. |
| [18] | Mapping review of attack detection strategy based on machine learning. | Other * security and privacy requirements were ignored. |
- Identifies privacy and security criteria needed in the BYOD policy setting.
- Analyses existing policy techniques based on privacy and security requirements in three security policy layers.
- Introduces a novel taxonomy that categorizes policy techniques into three layers according to their alignment with privacy and security requirements. This taxonomy provides a structured framework for understanding and organizing policy techniques, contributing to the existing knowledge in the field.
- Identifies and discusses the current trends in technology related to policy techniques by examining the technological advancements within each layer.
- Addresses the measures used to evaluate the effectiveness of policy techniques, mainly through performance analysis, by discussing these evaluation measures.
- Presents a comprehensive evaluation of policy techniques’ technical advantages and limitations by highlighting the strengths and weaknesses of each technique.
- Identifies potential areas for future research and improvement in policy techniques. By pointing out the gaps and limitations in the existing techniques, the paper stimulates further exploration and encourages researchers to develop innovative approaches to address the identified challenges.
2. Background and Related Concepts
2.1. BYOD Risks
2.2. Security Challenges
2.3. Privacy Challenges
2.4. Security Policies
2.5. Security Technologies
2.6. Privacy and Security Requirements
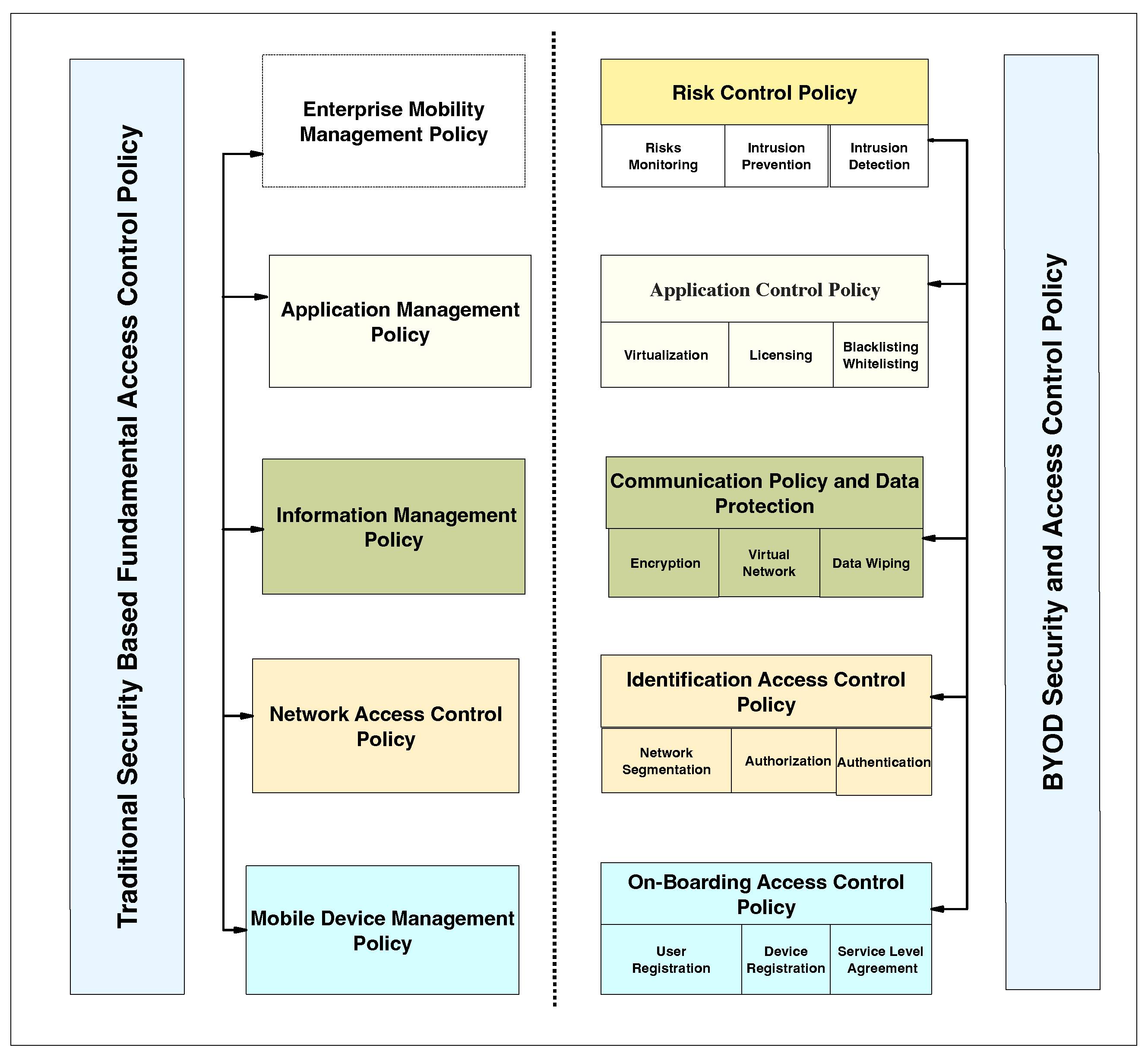
3. Comparison Traditional Access Control vs. Security Access Control Based on Three Layers
- Traditional security approaches are often deemed insufficient and potentially vulnerable in providing the required level of protection [1,31]. For example, network access control policies in traditional security heavily rely on mobile device management (MDM) technology for authenticating and managing BYOD devices within the organization. In contrast, ideal BYOD security emphasizes identification access control methods, such as biometrics and two-factor authentication. Additionally, ideal security policies for information protection encompass advanced measures like communication access control, encryption, virtual private networks (VPNs), and data wiping. On the other hand, traditional security approaches utilize mobile information management (MIM) to enforce information management policies.
- Traditional security policies lack the inclusion of risk access control policies, despite their importance in BYOD security, as recommended by Bello et al. [1].
- Traditional security policies fall short in adequately addressing all privacy requirements due to limitations in policy techniques and defense mechanisms [31]. These limitations serve as a motivation to address the challenges surrounding privacy and security and enhance security policies through the implementation of three layers of security policies, thus meeting the privacy requirements of BYOD security.
| Security Policy Approaches | Traditional Security | BYOD Security That Should Be Implemented |
|---|---|---|
| Mobile Device Management Policy. | ✓ | ✓ |
| Application Management Policy. | ✓ | ✓ |
| Information Management Policy. | ✓ | ✓ |
| Network Access Control Policy. | ✓ | ✓ |
| Enterprise Mobility Management Policy. | ✓ | ✓ |
| Security Communication Policy and Data Protection. | ✗ | ✓ |
| Private Network (VPN), Data Wiping and Data Backup. | ✗ | ✓ |
| Identification Access Control Policy. | ✗ | ✓ |
| Risk Access control policy. | ✗ | ✓ |
| Information Security Policy Compliance. | ✗ | ✓ |
| Comprehensive for the privacy requirements that the BYOD needs. | ✗ | ✓ |
3.1. Traditional Security-Based Fundamental Access Control Policy Approaches
3.1.1. Network Access Control Policy (NAC)
- Managing and accessing rich media material can contribute to network congestion.
- Malicious devices linked to the network can contaminate it.
- Malicious or infected devices can infect others on the same virtual local area network (VLAN).
3.1.2. Mobile Device Management Policy (MDM)
- There is a limit on the number of devices and operating systems.
- Personal and corporate data might be combined.
- Third-party apps are required to utilise MDM functionalities fully.
3.1.3. Mobile Application Management Policy (MAM)
3.1.4. Enterprise Mobility Management Policy (EMM)
- It combines all of the limitations and challenges of the strategies previously discussed.
- The user experience and satisfaction with BYOD may be compromised by this solution.
- By employing data separation techniques such as containers, corporate data can be vulnerable to security threats.
3.1.5. Mobile Information Management Policy (MIM)
3.2. Security Access Control Based on Three Layers (Ideal Security Policy)
3.2.1. Operational Layer
3.2.2. Tactical Layer
3.2.3. Strategic Layer
4. Overview of the Privacy and Security Requirements in a BYOD Environment
4.1. CIA Triad Criteria Security and Privacy Requirements
4.2. IAS-Octave Security Criteria and Privacy Requirements
4.3. Addition of Attack Detection Requirements
5. SLR Methodology
- Step 1:
- Define research questions and objectives to give the study a broad scope.
- Step 2:
- Determine a search strategy for published research in available digital libraries.
- Step 3:
- Employ a screening process that uses inclusion and exclusion criteria to decide which studies to include.
- Step 4:
- Perform classification and data extraction, aided by keywording.
- Step 5:
- Extract and map data.
5.1. Research Questions and Objectives
5.2. Data Search Strategy
- “Bring your own device” OR “BYOD” AND “Security Policy” OR “Policy” AND “Security and Privacy”
- “Secure*” AND “Policy Techniques ” AND “Bring your own device” OR “BYOD”
- “Access control” AND “BYOD” OR “Bring your own device” AND “BYOD” OR “Bring your own device”
5.3. Criteria for Study Selection
5.4. Data Extraction
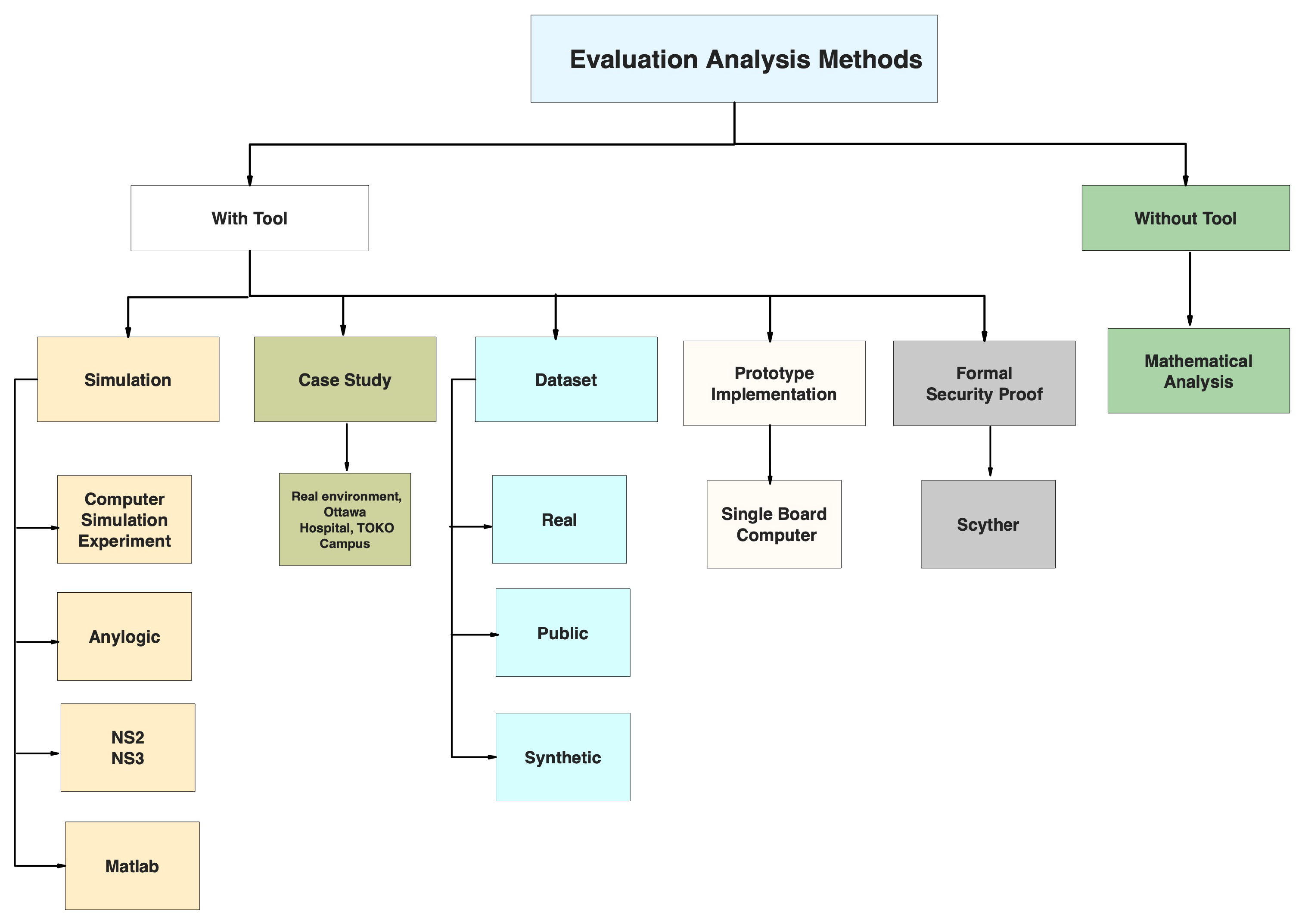
6. Data Analysis
6.1. Analysis of General Data
6.2. Analysis of BYOD Security Policy Techniques Based on Privacy and Security Requirements
6.2.1. Techniques That Satisfy Only One of the Privacy and Security Requirements
- A.
- Techniques Based on Authenticity Requirements:
- B.
- Cryptographic Techniques Based on Confidentiality Requirements:
- C.
- Isolation Techniques Based on Confidentiality Requirements:
- D.
- Technique-Based Attack Detection Requirement:
6.2.2. Techniques Based on More Than One Security and Privacy Requirement
6.2.3. Techniques That Did Not Fulfil Any of the Classified Security and Privacy Requirements
6.2.4. Performance Evaluation and Metrics Employed by the Techniques
7. Discussion
8. Open Issues
8.1. Blockchain-Based Authentication Techniques
8.2. Secure Two-Way Communication
8.3. Real-Time Authorization
8.4. Context-Aware Role-Based Access Control
8.5. Risk-Adaptive Policy Adjustments
8.6. Evaluation Metrics Employed by the Techniques
8.7. More Effort Is Required to Fulfill Specific Privacy and Security Criteria
9. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Bello, A.G.; Murray, D.; Armarego, J. A systematic approach to investigating how information security and privacy can be achieved in BYOD environments. Inf. Comput. Secur. 2017, 25, 475–492. [Google Scholar] [CrossRef]
- Agrawal, A.; Pandey, A.K.; Baz, A.; Alhakami, H.; Alhakami, W.; Kumar, R.; Khan, R.A. Evaluating the security impact of healthcare Web applications through fuzzy based hybrid approach of multi-criteria decision-making analysis. IEEE Access 2020, 8, 135770–135783. [Google Scholar] [CrossRef]
- Beckett, P. BYOD–popular and problematic. Netw. Secur. 2014, 2014, 7–9. [Google Scholar] [CrossRef]
- Njuguna, D.; Kanyi, W. An evaluation of BYOD integration cybersecurity concerns: A case study. Int. J. Recent Res. Math. Comput. Sci. Inf. Technol. 2023, 9, 80–91. [Google Scholar]
- Conteh, N.Y.; Schmick, P.J. Cybersecurity: Risks, vulnerabilities and countermeasures to prevent social engineering attacks. Int. J. Adv. Comput. Res. 2016, 6, 31. [Google Scholar] [CrossRef]
- Clarke, J.; Hidalgo, M.G.; Lioy, A.; Petkovic, M.; Vishik, C.; Ward, J. Consumerization of IT: Top risks and opportunities. In ENISA Deliverables; European Network and Information Security Agency (ENISA) Report; European Network and Information Security Agency (ENISA): Athens, Greece, 2012. [Google Scholar]
- Utter, C.J.; Rea, A. The“ Bring your own device” conundrum for organizations and investigators: An examination of the policy and legal concerns in light of investigatory challenges. J. Digit. Forensics Secur. Law 2015, 10, 4. [Google Scholar] [CrossRef]
- Rhee, K.; Won, D.; Jang, S.W.; Chae, S.; Park, S. Threat modeling of a mobile device management system for secure smart work. Electron. Commer. Res. 2013, 13, 243–256. [Google Scholar] [CrossRef]
- Morrow, B. BYOD security challenges: Control and protect your most sensitive data. Netw. Secur. 2012, 2012, 5–8. [Google Scholar] [CrossRef]
- La Polla, M.; Martinelli, F.; Sgandurra, D. A survey on security for mobile devices. IEEE Commun. Surv. Tutor. 2012, 15, 446–471. [Google Scholar] [CrossRef]
- Kok, J.; Kurz, B. Analysis of the botnet ecosystem. In Proceedings of the 10th Conference of Telecommunication, Media and Internet Techno-Economics (CTTE), Berlin, Germany, 16–18 May 2011; VDE: Frankfurt am Main, Germany, 2011; pp. 1–10. [Google Scholar]
- Niehaves, B.; Köffer, S.; Ortbach, K. IT consumerization—A theory and practice review. In Proceedings of the 18th Americas Conference on Information Systems (AMCIS 2012), Seattle, WA, USA, 9–11 August 2012. [Google Scholar]
- Garba, A.B.; Armarego, J.; Murray, D.; Kenworthy, W. Review of the information security and privacy challenges in Bring Your Own Device (BYOD) environments. J. Inf. Priv. Secur. 2015, 11, 38–54. [Google Scholar] [CrossRef]
- Oktavia, T.; Yanti; Prabowo, H.; Meyliana. Security and privacy challenge in Bring Your Own Device environment: A systematic literature review. In Proceedings of the 2016 International Conference on Information Management and Technology (ICIMTech), Bandung, Indonesia, 16–18 November 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 194–199. [Google Scholar]
- Jamal, F.; Taufik, M.; Abdullah, A.A.; Hanapi, Z.M. A Systematic Review Of Bring Your Own Device (BYOD) Authentication Technique. J. Phys. Conf. Ser. 2020, 1529, 042071. [Google Scholar] [CrossRef]
- Palanisamy, R.; Norman, A.A.; Kiah, M.L.M. Compliance with bring your own device security policies in organizations: A systematic literature review. Comput. Secur. 2020, 98, 101998. [Google Scholar] [CrossRef]
- Wani, T.A.; Mendoza, A.; Gray, K. Hospital bring-your-own-device security challenges and solutions: Systematic review of gray literature. JMIR mHealth uHealth 2020, 8, e18175. [Google Scholar] [CrossRef] [PubMed]
- Eke, C.I.; Norman, A.A.; Mulenga, M. Machine learning approach for detecting and combating bring your own device (BYOD) security threats and attacks: A systematic mapping review. Artif. Intell. Rev. 2023, 56, 8815–8858. [Google Scholar] [CrossRef]
- AL-Azazi, O.A.A.S.; Norman, A.A.; Ghani, N.B.A. BrA Systematic Literature Review and Bibliometric Analysis (2017–2022) Your Own Device Information Security Policy Compliance Framework. In Proceedings of the 2022 International Conference on Cyber Resilience (ICCR), Dubai, United Arab Emirates, 6–7 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–8. [Google Scholar]
- Soubhagyalakshmi, P.; Reddy, K.S. An efficient security analysis of bring your own device. IAES Int. J. Artif. Intell. 2023, 12, 696. [Google Scholar] [CrossRef]
- Ratchford, M.; El-Gayar, O.; Noteboom, C.; Wang, Y. BYOD security issues: A systematic literature review. Inf. Secur. J. Glob. Perspect. 2022, 31, 253–273. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.B.; Wahab, A.W.B.A.; Ho, A.T.; Khan, S.; Musa, S.N.B.; Taha, A.Z.B. Systematic review on security and privacy requirements in edge computing: State of the art and future research opportunities. IEEE Access 2020, 8, 76541–76567. [Google Scholar] [CrossRef]
- Kaspersky. Available online: https://www.kaspersky.com (accessed on 9 May 2023).
- Batool, H.; Masood, A. Enterprise mobile device management requirements and features. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 109–114. [Google Scholar]
- Da Veiga, A.; Astakhova, L.V.; Botha, A.; Herselman, M. Defining organisational information security culture—Perspectives from academia and industry. Comput. Secur. 2020, 92, 101713. [Google Scholar] [CrossRef]
- Whitman, M.E.; Mattord, H.J. Principles of Information Security; Cengage Learning: Boston, MA, USA, 2021. [Google Scholar]
- Mohsin, M.K.A.; Ab Hamid, Z. Bring Your Own Device (BYOD): Legal Protection of The Employee in Malaysia. Malays. J. Soc. Sci. Humanit. (MJSSH) 2022, 7, e001609. [Google Scholar]
- Johnston, Z.A. Exploring Privacy Concern Effect on Organizational BYOD Policies and Security Measures Compliancy. Ph.D. Thesis, Capella University, Minneapolis, MN, USA, 2022. [Google Scholar]
- Véliz, C. Privacy and digital ethics after the pandemic. Nat. Electron. 2021, 4, 10–11. [Google Scholar] [CrossRef]
- White, B. The Influence of BYOD Security Risk on SME Information Security Effectiveness. Ph.D. Thesis, Capella University, Minneapolis, MN, USA, 2022. [Google Scholar]
- Macaraeg, T.A., Jr. Bring-Your-Own-Device (BYOD): Issues and Implementation in Local Colleges and Universities in the Philippines; ResearchGate: Berlin, Germany, 2013. [Google Scholar]
- Herrera, A.V.; Ron, M.; Rabadão, C. National cyber-security policies oriented to BYOD (bring your own device): Systematic review. In Proceedings of the 2017 12th Iberian Conference on Information Systems and Technologies (CISTI), Lisbon, Portugal, 21–24 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–4. [Google Scholar]
- Scarfo, A. New security perspectives around BYOD. In Proceedings of the 2012 Seventh International Conference on Broadband, Wireless Computing, Communication and Applications, Victoria, BC, Canada, 12–14 November 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 446–451. [Google Scholar]
- Alotaibi, B.; Almagwashi, H. A review of BYOD security challenges, solutions and policy best practices. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Mosenia, A.; Jha, N.K. A comprehensive study of security of internet-of-things. IEEE Trans. Emerg. Top. Comput. 2016, 5, 586–602. [Google Scholar] [CrossRef]
- Karimi, K.; Krit, S. Smart home-smartphone systems: Threats, security requirements and open research challenges. In Proceedings of the 2019 International Conference of Computer Science and Renewable Energies (ICCSRE), Agadir, Morocco, 22–24 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Rodríguez, N.R.; Murazzo, M.A.; Chávez, S.B.; Valenzuela, F.A.; Martín, A.E.; Villafane, D.A. Key aspects for the development of applications for Mobile Cloud Computing. J. Comput. Sci. Technol. 2013, 13, 143–148. [Google Scholar]
- Downer, K.; Bhattacharya, M. BYOD security: A new business challenge. In Proceedings of the 2015 IEEE International Conference on Smart City/SocialCom/SustainCom (SmartCity), Chengdu, China, 19–21 December 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1128–1133. [Google Scholar]
- Doh, I.; Lim, J.; Chae, K. Secure authentication for structured smart grid system. In Proceedings of the 2015 9th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Santa Catarina, Brazil, 8–10 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 200–204. [Google Scholar]
- Almarhabi, K.; Jambi, K.; Eassa, F.; Batarfi, O. Survey on access control and management issues in cloud and BYOD environment. Int. J. Comput. Sci. Mob. Comput. 2017, 6, 44–54. [Google Scholar]
- Ali, M.I.; Kaur, S. Next-generation digital forensic readiness BYOD framework. Secur. Commun. Netw. 2021, 2021, 6664426. [Google Scholar] [CrossRef]
- Sushil, G.S.; Deshmuk, R.K.; Junnarkar, A.A. Security Challenges and Cyber Forensics For IoT Driven BYOD Systems. In Proceedings of the 2022 IEEE 7th International conference for Convergence in Technology (I2CT), Mumbai, India, 7–9 April 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–7. [Google Scholar]
- Kitchenham, B.; Brereton, P. A systematic review of systematic review process research in software engineering. Inf. Softw. Technol. 2013, 55, 2049–2075. [Google Scholar] [CrossRef]
- Lee, J.E.; Park, S.H.; Yoon, H. Security policy based device management for supporting various mobile os. In Proceedings of the 2015 Second International Conference on Computing Technology and Information Management (ICCTIM), Johor, Malaysia, 21–23 April 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 156–161. [Google Scholar]
- Guerar, M.; Verderame, L.; Merlo, A.; Palmieri, F.; Migliardi, M.; Vallerini, L. CirclePIN: A novel authentication mechanism for smartwatches to prevent unauthorized access to IoT devices. ACM Trans.-Cyber-Phys. Syst. 2020, 4, 1–19. [Google Scholar] [CrossRef]
- Yanson, K. Results of implementing WPA2-enterprise in educational institution. In Proceedings of the 2016 IEEE 10th International Conference on Application of Information and Communication Technologies (AICT), Baku, Azerbaijan, 12–14 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–4. [Google Scholar]
- Gkamas, V.; Paraskevas, M.; Varvarigos, E. Design of a secure BYOD policy for the Greek School Network: A Case Study. In Proceedings of the 2016 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC) and 15th International Symposium on Distributed Computing and Applications for Business Engineering (DCABES), Paris, France, 24–26 August 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 557–560. [Google Scholar]
- Oluwatimi, O.; Damiani, M.L.; Bertino, E. A context-aware system to secure enterprise content: Incorporating reliability specifiers. Comput. Secur. 2018, 77, 162–178. [Google Scholar] [CrossRef]
- Kao, Y.C.; Chang, Y.C.; Chang, R.S. EZ-Net BYOD service management in campus wireless networks. J. Internet Technol. 2017, 18, 907–917. [Google Scholar]
- Heo, H.; Ryou, J. Design and implementation of lightweight network access control technique on wireless router. Int. J. Serv. Technol. Manag. 2017, 23, 101–116. [Google Scholar] [CrossRef]
- Jaha, F.; Kartit, A. Pseudo code of two-factor authentication for BYOD. In Proceedings of the 2017 International Conference on Electrical and Information Technologies (ICEIT), Rabat, Morocco, 15–18 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–7. [Google Scholar]
- Cai, C.; Weng, J.; Liu, J. Mobile authentication system based on national regulation and NFC technology. In Proceedings of the 2016 IEEE First International Conference on Data Science in Cyberspace (DSC), Changsha, China, 13–16 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 590–595. [Google Scholar]
- Deng, R.; Weng, J.; Ren, K.; Yegneswaran, V. Security and privacy in communication networks. In Proceedings of the Security and Privacy in Communication Networks: 12th International Conference (SecureComm 2016), Guangzhou, China, 10–12 October 2016; Springer: Berlin/Heidelberg, Germany, 2017; Volume 198. [Google Scholar]
- Seneviratne, B.; Senaratne, S. Integrated Corporate Network Service Architecture for Bring Your Own Device (BYOD) Policy. In Proceedings of the 2018 3rd International Conference on Information Technology Research (ICITR), Moratuwa, Sri Lanka, 5–7 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Rahardjo, M.R.D.; Shidik, G.F. Design and implementation of self encryption method on file security. In Proceedings of the 2017 International Seminar on Application for Technology of Information and Communication (iSemantic), Semarang, Indonesia, 7–8 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 181–186. [Google Scholar]
- Vinh, T.L.; Cagnon, H.; Bouzefrane, S.; Banerjee, S. Property-based token attestation in mobile computing. Concurr. Comput. Pract. Exp. 2020, 32, e4350. [Google Scholar] [CrossRef]
- Catuogno, L.; Galdi, C. A Fine-grained General Purpose Secure Storage Facility for Trusted Execution Environment. In Proceedings of the International Conference on Information Systems Security and Privacy (ICISSP 2019), Prague, Czech Republic, 23–25 February 2019; pp. 588–595. [Google Scholar]
- Li, F.; Rahulamathavan, Y.; Conti, M.; Rajarajan, M. Robust access control framework for mobile cloud computing network. Comput. Commun. 2015, 68, 61–72. [Google Scholar] [CrossRef]
- Gupta, S. Single Sign-On beyond Corporate Boundaries. In Proceedings of the 2018 8th International Conference on Intelligent Systems, Modelling and Simulation (ISMS), Kuala Lumpur, Malaysia, 8–10 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 38–42. [Google Scholar]
- Abisheka, P.C.; Azra, M.F.; Poobalan, A.; Wijekoon, J.; Yapa, K.; Murthaja, M. An Automated Solution For Securing Confidential Documents in a BYOD Environment. In Proceedings of the 2021 3rd International Conference on Advancements in Computing (ICAC), Colombo, Sri Lanka, 9–11 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 61–66. [Google Scholar]
- Kim, J.; Kim, T.Y.; Kim, D. Network based vByod scheme in NFV platform. In Proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 18–20 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1143–1145. [Google Scholar]
- Ocano, S.G.; Ramamurthy, B.; Wang, Y. Remote mobile screen (RMS): An approach for secure BYOD environments. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, USA, 16–19 February 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 52–56. [Google Scholar]
- Dong, Y.; Mao, J.; Guan, H.; Li, J.; Chen, Y. A virtualization solution for BYOD with dynamic platform context switching. IEEE Micro 2015, 35, 34–43. [Google Scholar] [CrossRef]
- Averlant, G. Multi-level isolation for android applications. In Proceedings of the 2017 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), Toulouse, France, 23–26 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 128–131. [Google Scholar]
- Chiueh, T.C.; Lin, H.; Chao, A.; Wu, T.G.; Wang, C.M.; Wu, Y.S. Smartphone virtualization. In Proceedings of the 2016 IEEE 22nd International Conference on Parallel and Distributed Systems (ICPADS), Wuhan, China, 13–16 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 141–150. [Google Scholar]
- Ketel, M. Enhancing BYOD security through SDN. In Proceedings of the SoutheastCon 2018, St. Petersburg, FL, USA, 19–22 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–2. [Google Scholar]
- Kim, G.; Jeon, Y.; Kim, J. Secure mobile device management based on domain separation. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 19–21 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 918–920. [Google Scholar]
- Kim, G.; Kim, J. Secure voice communication service based on security platform for mobile devices. In Proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 18–20 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1190–1192. [Google Scholar]
- Mishima, K.; Sakurada, T.; Hagiwara, Y.; Tsujisawa, T. Secure Campus Network System with Automatic Isolation of High Security Risk Device. In Proceedings of the 2018 ACM SIGUCCS Annual Conference, Orlando, FL, USA, 7–10 October 2018; pp. 107–110. [Google Scholar]
- Kim, D.; Lee, S. Study of identifying and managing the potential evidence for effective Android forensics. Forensic Sci. Int. Digit. Investig. 2020, 33, 200897. [Google Scholar] [CrossRef]
- Ali, M.I.; Kaur, S.; Khamparia, A.; Gupta, D.; Kumar, S.; Khanna, A.; Al-Turjman, F. Security challenges and cyber forensic ecosystem in IOT driven BYOD environment. IEEE Access 2020, 8, 172770–172782. [Google Scholar] [CrossRef]
- Tan, X.; Li, H.; Wang, L.; Xu, Z. End-Edge Coordinated Inference for Real-Time BYOD Malware Detection using Deep Learning. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Republic of Korea, 25–28 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Watkins, L.; Kalathummarath, A.L.; Robinson, W.H. Network-based detection of mobile malware exhibiting obfuscated or silent network behavior. In Proceedings of the 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–4. [Google Scholar]
- Atlam, H.F.; Alenezi, A.; Walters, R.J.; Wills, G.B.; Daniel, J. Developing an adaptive Risk-based access control model for the Internet of Things. In Proceedings of the 2017 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Exeter, UK, 21–23 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 655–661. [Google Scholar]
- Tiwari, P.K.; Velayutham, T. Andrologger: Collecting and correlating events to identify suspicious activities in android. In Proceedings of the 2017 8th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Delhi, India, 3–5 July 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–7. [Google Scholar]
- Aldini, A.; Seigneur, J.M.; Lafuente, C.B.; Titi, X.; Guislain, J. Design and validation of a trust-based opportunity-enabled risk management system. Inf. Comput. Secur. 2017. [Google Scholar] [CrossRef]
- Eslahi, M.; Yousefi, M.; Naseri, M.V.; Yussof, Y.; Tahir, N.; Hashim, H. Mobile botnet detection model based on retrospective pattern recognition. Int. J. Secur. Appl. 2016, 10, 39–44. [Google Scholar] [CrossRef]
- Joshi, P.; Jindal, C.; Chowkwale, M.; Shethia, R.; Shaikh, S.A.; Ved, D. Protego: A passive intrusion detection system for android smartphones. In Proceedings of the 2016 International Conference on Computing, Analytics and Security Trends (CAST), Pune, India, 19–21 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 232–237. [Google Scholar]
- Kim, T. A Study on the Detection of Abnormal Behavior and Vulnerability Analysis in BYOD. In Proceedings of the International Internet of Things Summit; Springer: Berlin/Heidelberg, Germany, 2015; pp. 162–167. [Google Scholar]
- Ammar, M.; Rizk, M.; Abdel-Hamid, A.; Aboul-Seoud, A.K. A framework for security enhancement in SDN-based datacenters. In Proceedings of the 2016 8th IFIP international conference on new technologies, Mobility and security (NTMS), Larnaca, Cyprus, 21–23 November 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–4. [Google Scholar]
- Akhuseyinoglu, N.B.; Akhuseyinoglu, K. AntiWare: An automated Android malware detection tool based on machine learning approach and official market metadata. In Proceedings of the 2016 IEEE 7th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 20–22 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–7. [Google Scholar]
- De las Cuevas, P.; Mora, A.; Merelo, J.J.; Castillo, P.A.; Garcia-Sanchez, P.; Fernandez-Ares, A. Corporate security solutions for BYOD: A novel user-centric and self-adaptive system. Comput. Commun. 2015, 68, 83–95. [Google Scholar] [CrossRef]
- Petrov, D.; Znati, T. Context-aware deep learning-driven framework for mitigation of security risks in BYOD-enabled environments. In Proceedings of the 2018 IEEE 4th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 18–20 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 166–175. [Google Scholar]
- Zungur, O.; Suarez-Tangil, G.; Stringhini, G.; Egele, M. Borderpatrol: Securing byod using fine-grained contextual information. In Proceedings of the 2019 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Portland, OR, USA, 24–27 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 460–472. [Google Scholar]
- Lima, A.; Rosa, L.; Cruz, T.; Simões, P. A Security Monitoring Framework for Mobile Devices. Electronics 2020, 9, 1197. [Google Scholar] [CrossRef]
- Nikoloudakis, Y.; Pallis, E.; Mastorakis, G.; Mavromoustakis, C.X.; Skianis, C.; Markakis, E.K. Vulnerability assessment as a service for fog-centric ICT ecosystems: A healthcare use case. Peer-to-Peer Netw. Appl. 2019, 12, 1216–1224. [Google Scholar] [CrossRef]
- Muhammad, M.A.; Ayesh, A.; Zadeh, P.B. Developing an intelligent filtering technique for bring your own device network access control. In Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19–20 July 2017; pp. 1–8. [Google Scholar]
- Uddin, M.; Nadeem, T. TrafficVision: A case for pushing software defined networks to wireless edges. In Proceedings of the 2016 IEEE 13th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Brasilia, Brazil, 10–13 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 37–46. [Google Scholar]
- Ali, M.I.; Kaur, S. BYOD Cyber Threat Detection and Protection Model. In Proceedings of the 2021 International Conference on Computing, Communication, and Intelligent Systems (ICCCIS), Greater Noida, India, 19–20 February 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 211–218. [Google Scholar]
- Alghamdi, A.M.; Almarhabi, K. A Proposed Framework for the Automated Authorization Testing of Mobile Applications. Int. J. Comput. Sci. Netw. Secur. 2021, 21, 217–221. [Google Scholar]
- Kebande, V.R.; Karie, N.M.; Venter, H. A generic Digital Forensic Readiness model for BYOD using honeypot technology. In Proceedings of the 2016 IST-Africa Week Conference, Durban, South Africa, 11–13 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–12. [Google Scholar]
- Asante, A.; Amankona, V. Digital Forensic Readiness Framework Based on Honeypot Technology for BYOD. J. Digit. Forensics Secur. Law 2021, 16, 1–17. [Google Scholar]
- Eshmawi, A.; Nair, S. The Roving Proxy Framewrok for SMS Spam and Phishing Detection. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 1–3 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Awan, M.S.; AlGhamdi, M.; AlMotiri, S.; Burnap, P.; Rana, O. A classification framework for distinct cyber-attacks based on occurrence patterns. In Proceedings of the 8th International Conference on Security of Information and Networks, Sochi, Russia, 8–10 September 2015; pp. 165–168. [Google Scholar]
- Stoecklin, M.P.; Singh, K.; Koved, L.; Hu, X.; Chari, S.N.; Rao, J.R.; Cheng, P.C.; Christodorescu, M.; Sailer, R.; Schales, D.L. Passive security intelligence to analyze the security risks of mobile/BYOD activities. IBM J. Res. Dev. 2016, 60, 9:1–9:13. [Google Scholar] [CrossRef]
- Chen, Y.; Hu, H.c.; Cheng, G.z. Design and implementation of a novel enterprise network defense system bymaneuveringmulti-dimensional network properties. Front. Inf. Technol. Electron. Eng. 2019, 20, 238–252. [Google Scholar] [CrossRef]
- Yang, C.; Hong-Chao, H.; Guo-Zhen, C. A software-defined intranet dynamic defense system. In Proceedings of the 2018 IEEE 18th International Conference on Communication Technology (ICCT), Chongqing, China, 8–11 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 849–854. [Google Scholar]
- Gómez-Hernández, J.A.; Camacho, J.; Holgado-Terriza, J.A.; García-Teodoro, P.; Maciá-Fernández, G. ARANAC: A Bring-Your-Own-Permissions Network Access Control Methodology for Android Devices. IEEE Access 2021, 9, 101321–101334. [Google Scholar] [CrossRef]
- Pomak, W.; Limpiyakom, Y. Enterprise WiFi Hotspot Authentication with Hybrid Encryption on NFC-Enabled Smartphones. In Proceedings of the 2018 8th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 15–17 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 247–250. [Google Scholar]
- Qi, S.; Lu, Y.; Wei, W.; Chen, X. Efficient data access control with fine-grained data protection in cloud-assisted IIoT. IEEE Internet Things J. 2020, 8, 2886–2899. [Google Scholar] [CrossRef]
- Zheng, Y.; Cao, Y.; Chang, C.H. Facial biohashing based user-device physical unclonable function for bring your own device security. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 12–14 January 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Gebert, S.; Zinner, T.; Gray, N.; Durner, R.; Lorenz, C.; Lange, S. Demonstrating a personalized secure-by-default bring your own device solution based on software defined networking. In Proceedings of the 2016 28th International Teletraffic Congress (ITC 28), Würzburg, Germany, 12–16 September 2016; IEEE: Piscataway, NJ, USA, 2016; Volume 1, pp. 197–200. [Google Scholar]
- Zhu, Y.; Gan, G.; Guo, R.; Huang, D. PHE: An efficient traitor tracing and revocation for encrypted file syncing-and-sharing in cloud. IEEE Trans. Cloud Comput. 2016, 6, 1110–1124. [Google Scholar] [CrossRef]
- Selviandro, N.; Wisudiawan, G.; Puspitasari, S.; Adrian, M. Preliminary study for determining bring your own device implementation framework based on organizational culture analysis enhanced by cloud management control. In Proceedings of the 2015 3rd International Conference on Information and Communication Technology (ICoICT), Nusa Dua, Bali, Indonesia, 27–29 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 113–118. [Google Scholar]
- Flores, D.A.; Qazi, F.; Jhumka, A. Bring your own disclosure: Analysing BYOD threats to corporate information. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1008–1015. [Google Scholar]
- Zulkefli, Z.; Singh, M.M.; Malim, N.H.A.H. Advanced persistent threat mitigation using multi level security–access control framework. In Proceedings of the International Conference on Computational Science and Its Applications; Springer: Berlin/Heidelberg, Germany, 2015; pp. 90–105. [Google Scholar]
- Hajdarevic, K.; Allen, P.; Spremic, M. Proactive security metrics for bring your own device (byod) in iso 27001 supported environments. In Proceedings of the 2016 24th Telecommunications Forum (TELFOR), Belgrade, Serbia, 22–23 November 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–4. [Google Scholar]
- Aldini, A.; Seigneur, J.M.; Lafuente, C.B.; Titi, X.; Guislain, J. Formal modeling and verification of opportunity-enabled risk management. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; IEEE: Piscataway, NJ, USA, 2015; Volume 1, pp. 676–684. [Google Scholar]
- Morrison, A.; Xue, L.; Chen, A.; Luo, X. Enforcing Context-Aware BYOD Policies with In-Network Security. In Proceedings of the 10th USENIX Workshop on Hot Topics in Cloud Computing (HotCloud 18), Boston, MA, USA, 8–9 July 2018. [Google Scholar]
- Armando, A.; Costa, G.; Merlo, A.; Verderame, L.; Wrona, K. Developing a NATO BYOD security policy. In Proceedings of the 2016 International Conference on Military Communications and Information Systems (ICMCIS), Brussels, Belgium, 23–24 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Samaras, V.; Daskapan, S.; Ahmad, R.; Ray, S.K. An enterprise security architecture for accessing SaaS cloud services with BYOD. In Proceedings of the 2014 Australasian Telecommunication Networks and Applications Conference (ATNAC), Southbank, VIC, Australia, 26–28 November 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 129–134. [Google Scholar]
- Perini, V.L.; de Fátima Webber do Prado Lima, M. BYOD Manager Kit: Integration of Administration and Security Tools BYOD. In Proceedings of the XIV Brazilian Symposium on Information Systems, Caxias do Sul, Brazil, 4–8 June 2018; pp. 1–9. [Google Scholar]
- Zain, Z.M.; Othman, S.H.; Kadir, R. Security-Based BYOD Risk Assessment Metamodelling Approach. In Proceedings of the 21st Pacific Asia Conference on Information Systems (PACIS 2017), Langkawi, Malaysia, 16–20 July 2017. [Google Scholar]
- Liu, X.; Qian, F.; Qian, Z. Selective HTTPS traffic manipulation at middleboxes for BYOD devices. In Proceedings of the 2017 IEEE 25th International Conference on Network Protocols (ICNP), Toronto, ON, Canada, 10–13 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–10. [Google Scholar]
- Koesyairy, A.A.; Kurniawan, A.; Hidayanto, A.N.; Budi, N.F.A.; Samik-Ibrahim, R.M. Mapping Internal Control of Data Security Issues of BYOD Program in Indonesian Banking Sector. In Proceedings of the 2019 5th International Conference on Computing Engineering and Design (ICCED), Singapore, 11–13 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Chu, P.Y.; Lu, W.H.; Lin, J.W.; Wu, Y.S. Enforcing enterprise mobile application security policy with plugin framework. In Proceedings of the 2018 IEEE 23rd Pacific Rim International Symposium on Dependable Computing (PRDC), Taipei, Taiwan, 4–7 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 263–268. [Google Scholar]
- Downer, K.; Bhattacharya, M. BYOD security: A study of human dimensions. Informatics 2022, 9, 16. [Google Scholar] [CrossRef]
- Ali, S.; Qureshi, M.N.; Abbasi, A.G. Analysis of BYOD security frameworks. In Proceedings of the 2015 Conference on Information Assurance and Cyber Security (CIACS), Rawalpindi, Pakistan, 18 December 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 56–61. [Google Scholar]

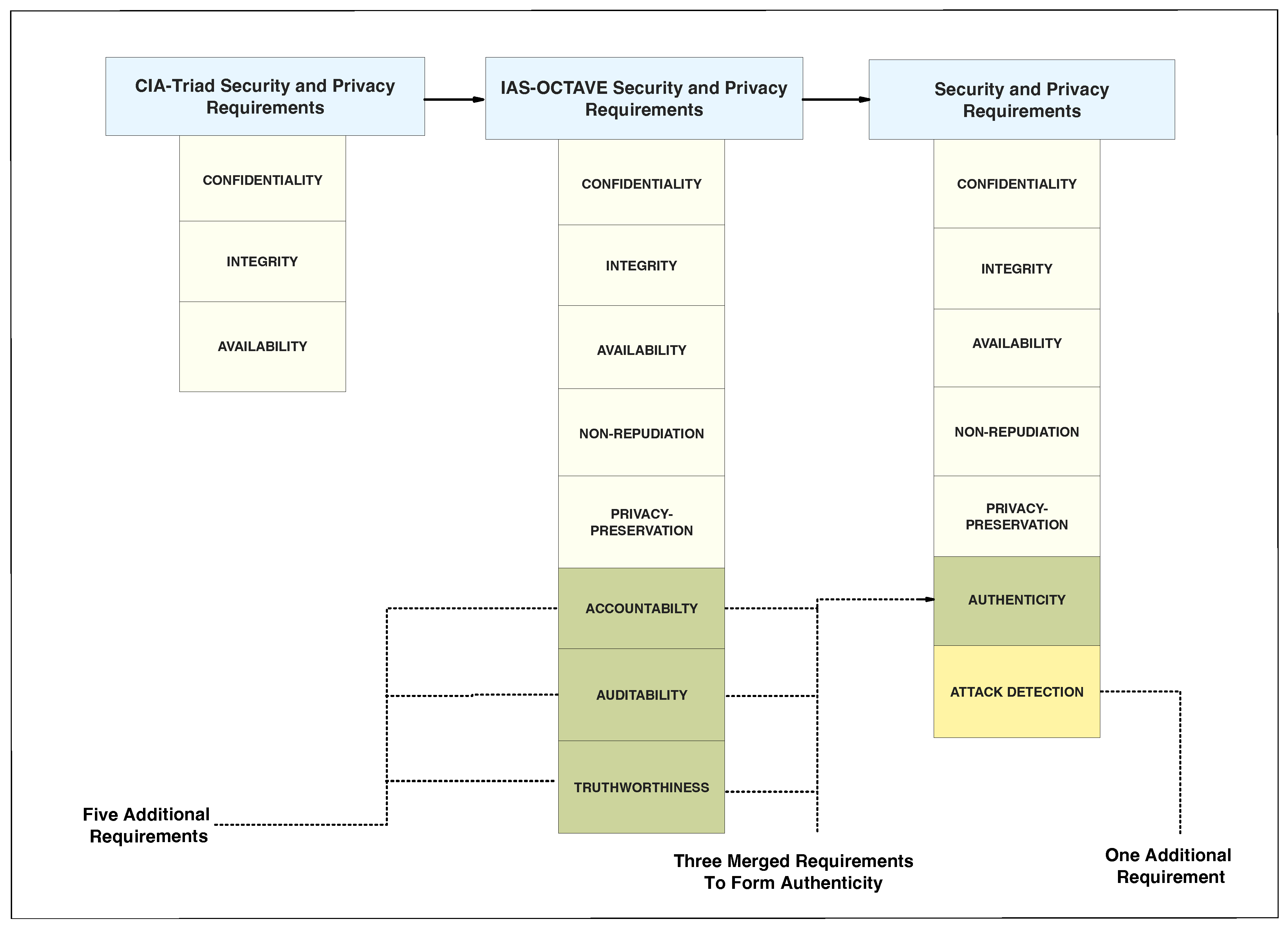







| Requirement | Description |
|---|---|
| Confidentiality | Ensures that unauthorized individuals are prevented from accessing shared data within BYOD-enabled organizations. |
| Integrity | Ensures that data is delivered exclusively to authorized BYOD devices without any unauthorized modifications. |
| Authenticity | Ensures accurate monitoring and verification of BYOD users’ identities, fostering trust between the BYOD devices, organizations, and their resources. |
| Nonrepudiation | Ensures accurate monitoring and verification of BYOD users’ identities, fostering trust between the BYOD devices, organizations, and their resources. |
| Privacy-Preservation | Ensures the secure and monitored storage of all confidential information related to BYOD devices, including end users. |
| Attack Detection | ensures the timely identification and effective mitigation of any security breaches or threats targeting BYOD devices. |
| Research Question | Research Objective |
|---|---|
| RQ1: For BYOD environments, what is the classification of privacy and security criteria? | To define the security and privacy requirements to ensure the highest level of security for the data of enterprises and BYOD users. |
| RQ2: What policy techniques are employed to ensure security and privacy requirements have been identified? | To analyse existing solutions to security policy techniques in terms of the three layers of BYOD security policy that are used to achieve specific security and privacy requirements. |
| RQ3: What are the trends in technological methods used by the identified techniques? | To identify trends in technological approaches used by the indicated methodology. |
| RQ4: What evaluation procedures should use to evaluate the performance measurement of technologies? | To determine the appropriate evaluation metrics used in evaluating the performance of technologies. |
| RQ5: What future research opportunities and gaps exist in the security policy and privacy field in BYOD for researchers? | To identify the currently open issues for privacy and policy issues in BYOD. |
| Inclusion | Exclusion |
|---|---|
| IC1: Papers related to research questions. | EC1: The papers do not address security policies based on BYOD. |
| IC2: Papers from journals or conferences. | EC2: Techniques and models used in the security policy are not addressed. |
| IC3: Papers are written in English only. | EC3: Duplicate papers. |
| IC4: Papers published between 2015 and 2022. | EC4: Full text is unavailable. |
| IC5: The full text is available. | EC5: Non-English. |
| IC6: Articles that present techniques and models of security policy in a BYOD environment. | EC6: White papers, chapters in books and magazines. |
| Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|
| [44] | MDM-based model. | Prototype implementation. | It can identify whether the BYOD device is disabled or enabled. | Only a limited number of devices and operating systems. |
| [45] | Pattern lock method and four-digit PIN(CirclePIN). | Experiment analysis and real dataset. | Protect against side-channel, shoulder-surfing and single-recording threats. | Less secure technologies. |
| [46] | Based on WPA2-Enterprise. | Experimental analyses, case study. | It eliminates shared password risks. | Increase processing power. |
| [47] | Set policies based on IEEE 802.1X/Certificated. | Case study of a Greek school. | Introduces security issues and their resolution. | Secure but vulnerable if authentication policies are simple. |
| [48] | Co-proximity authentication protocol(fingerprint sensors and biometric). | Prototype implementation and behavioural, biometric dataset. | Context-aware authentication. | Complex and time-intensive. |
| [49] | EZ-Net system. | Experimental analysis, Case study on campus. | Low-cost, high-performance. | Each user’s monthly authentication time is limited. |
| [50] | Lightweight network access control (NAC) module. | Prototype implementation, OpenWrt, NAC module. | Improves administrator management and OpenWrt is a free wireless router. | Unsuitable for all systems. |
| [51] | Pseudo-code-based two-factor authentication. | Mathematical analysis. | Simple to implement and inexpensive. | It is difficult to do while utilising a mobile phone rather than a laptop because the keyboard is different. |
| [52] | NFC technology. | Simulation (computer simulation experimental). | More secure, fast and convenient authentication. | Limited number of nodes. |
| [53] | AppShield scheme, certificate-based authentication. | Prototype implementation, synthetic dataset (1000 data access operations). | Most secure BYOD infrastructure control. | Complicated and time-consuming. |
| [54] | Fine-grained security policies (set policy as an individual, group for user and device). | Prototype implementation. | Very low cost. | Network address interpretation is weak. |
| Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|
| [55] | Cryptography-based algorithm (self-encryption). | Prototype implementation, (Encryption and decryption for Several files). | Effective in data storage units in enterprises that use BYOD. | Limitation in the execution time, compression. |
| [56] | RSA-based algorithm, property-based token attestation (PTA). | Mathematical analyses, a scyther tool for verification. | Secure enterprise network access. | Cloudlet-based BYOD models require modification of this PTA protocol. |
| [57] | MAC-based algorithm (symmetric key cryptographic), file-grained data. | Prototype implementation. | Sets policy rules in the endpoint and achieves confidentiality. | Makes use of the shared key. |
| [58] | ABE scheme-based algorithm. | Algorithmic proof. | Confidentiality. | Time increase due to sensor data collection and processing to determine attributes. |
| [59] | Based on the algorithm (RSA-Tokens). | Prototype implementation and Private cloud. | It reduces authentication time and information exchange from 3000 ms to 2000 ms using TLS. | It transfers data slowly. |
| [60] | Based on symmetric algorithm. | Prototype implementation. | BYODENCE is low-cost and delivers high accuracy and speed. | More complex. |
| Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|
| [61] | VNF scheme-based virtualization technique. | Prototype implementation and testing in real word network. | Improved security, mobility, and response time with virtual and dynamic networks. | Synchronization of physical and virtual security. |
| [62] | Remote mobile screen (RMS) system based virtualization method. | Experimental analysis. | RMS ensures data confidentiality, policy compliance and space isolation. | It poses numerous security risks. |
| [63] | vNative-based virtualization method. | Prototype implementation, evaluation testbed configuration. | Data confidentiality and isolation. | Limited availability of BYOD/mobile devices. |
| [64] | Multi-level architecture for isolation. | Experimental analyses. | Provided privacy for android end-user. | The solution is only for android. |
| [65] | Brahma-based virtualization method. | Prototype implementation (KVM Module, Zenfone). | Privacy. | Less security. |
| [66] | EMM, SDN and NFV. | Prototype implementation. | SDN can enhance NFV performance with virtualization. | SSDN and NFV are independent. |
| [67] | MSS system-based virtualisation method. | Experimental analysis. | MSS secures sensitive data and security activities in a separate domain. | The MSS is only for one environment. |
| [68] | MSS system. | Experimental analyses. | Confidentiality. | Low cost. |
| Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|
| [69] | Risk access scheme, NGFW technique based deep-packet inspection firewall. | Experiment analyses and Case study (Tokyo University). | Reduces costs while increasing security. | It is weaker because package content should be verified instead of only filtered network traffic. |
| [70] | Forensics investigation method. | Experiment analyses, real dataset (Android log). | Works well to detect and analyse BYOD malware. | Only deal with log files without applications. |
| [71] | Forensic investigation model. | Simulation performed in three stages (computer, simulation, and experimental) | tracked BYOD user’s traffic. | Forensic investigation requires an end-to-end ecosystem. |
| [72] | Clustering algorithms | Simulation, public malware dataset, branchy model. | High precision and lower traffic. | long training time. |
| [73] | Risk-detection-based ML random forest algorithm. | Experimental analysis, tested by comparing infected, unaffected android, public malware App dataset. | The method examines the whole issue to see if BYOD is legal. | Less efficient. |
| [74] | Risk access control model based on a risk estimation algorithm (fuzzy model) | Prototype implementation and Smart contracts dataset. | Making access decisions based on anomalies. | The method requires further development. |
| [75] | Andrologger tool. | Experimental analyses, Real dataset. | Automatically sending BYOD data and user actions to the company’s server for analysis. | The method only works on android phones. |
| [76] | OPPRIM-based risk policy model | simulations (AnyLogic), Mathematical Analysis. | Adaptability, cost reduction. | Simulating risk will result in conservative behaviours from attackers. |
| [77] | Neural network-based algorithm to detect HTTP botnets. | Simulations (Anylogic), Drebin dataset, PRISM model checker and Mathematical analysis (Correlation) | High accuracy. | Complexity. |
| [78] | IDS model-based ML algorithm. | Prototype implementation, NSL KDD dataset. | Able to detect DoS, probing and torrent traffic. | The dataset quantity is large. |
| [79] | Behaviour-based abnormality detection model, Pattern Analysis (data mining). | Mathematical analysis. | Analyzing user behaviour to detect abnormal behaviour. | High false alarm rate. |
| [80] | System based SDN. | Simulation (NS2), attacks dataset (SYN attack, ICMP flood, Dos attack). | Self-adaptive network can defend against internal threats and reduce attack reaction time. | Should be extended and improved to detect sophisticated APTs. |
| [81] | Malware identification scheme based supervised classification algorithms/ML. | Prototype implemented-android applications dataset. | High accuracy. | The decision limit may be overtrained. |
| [82] | MUSES framework based fuzzy Logic, ML. | Prototype implementation. | Enhanced security and provided intrusion detection systems. | Difficult interpretation. |
| Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|
| [83] | ANN algorithm (deep learning). | Experimental analysis, Real data from the Media Lab of MIT dataset (incoming, outgoing, type of call). | Precision and accuracy of over 99%. | ANN has difficulty converting data into numerical values. |
| [84] | Border patrol system. | Prototype implementation, 2000 apps of Google Play an android emulator. | Introduced new policies for corporate networks to manage organised activities. | Limited ability to block malicious apps. |
| [85] | Anomaly detection method based ML algorithms. | Prototype implementation, a proof-of-concept and Spark dataset. | Detecting intrusions and anomalies. | Need more verification. |
| [86] | CVSS system-based decision engine logic algorithm. | Simulation (Computer simulation and experimental). | Privacy for the infrastructure layer. | The assessment time is still a major concern. |
| [87] | IFT technique based on a clustering algorithm/ML. | Experimental analyses, Public data set containing packet IAT features. | Employed the packet inter-arrival time feature to detect abnormal behaviour. | Need to improve the algorithm within large datasets. |
| [88] | Real-time traffic classification system based on ML. | Experimental analyses, proof of concept and real dataset. | Employed a fine-grained, real-time traffic classification. | Required a change in the entire network infrastructure to implement SDN protocol. |
| [89] | Detection technique-based novel algorithm. | Prototype implementation. | Reduced network risk and increased BYOD infrastructure security. | The analysis should include traffic instead of just the login log. |
| [90] | Other methods (white box method). | Prototype implementation. | Benefits both end-users and organisational use. | Exploiting apps makes security testing difficult. |
| [41,91] | DFRM model based honeypot technology (digital forensic readiness). | Prototype implementation. | Efficient method. | limited in digital evidence. |
| [92] | DFR framework-based honeypot technology. | Prototype implementation. | DFR improves BYOD security and reduces issues. | Honeypots only gather data when attacked. |
| [93] | Roving proxy server framework. | Prototype implementation and SMS spam dataset. | Efficient with a small dataset. | Need more work on a massive dataset. |
| [94] | Classification framework. | Correlation analysis, Real malicious traffic logs. | Useful for the network administrator. | Only classifies cyber-attack patterns and not types. |
| [95] | Based on dynamic decision tree algorithm (ML). | Experimentation and IBM’s internal network dataset. | Reducing enterprise risk. | Limited application installation. |
| [96] | Network scanning technique-based algorithm. | Proof-of-concept, Experimental analysis and Public dataset(Attack) | Preventing network eavesdropping and spoofing. | It should be implemented on the switch for better security. |
| [97] | SIDD system. | Prototype implementation, network attacks dataset (e.g., zero-day, worms, DoS). | Validate up to 99% and help to detect zero-day malware. | Should be applied to various attacks to ensure effectiveness. |
| [98] | ARANAC, a Novel access control | Experimental analysis, Case study using more than 80 Android devices at a university campus | ARANAC has monitoring, risk estimation, and attack detection modules. | Need to extend the model to estimate risk values for the remaining features. |
| Privacy Requirements | Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|---|
| Confidentiality and Authentication. | [99] | AES, HMAC algorithm | Prototype implementation. | Authentication-based cryptography secures networks and users. | Certificate management challenges. |
| Confidentiality and Authentication. | [100] | Optimizing and encrypting Schema-Based Access Control. | Prototype implementation. | Protects data from key leakage. | Secure but complicated. |
| Confidentiality and Authentication. | [101] | Biohashing technique. | Mathematical analysis, Experimental. | Increases security and lowers error rates. | Data increases collision probability. |
| Attack Detection, Authentication, and Confidentiality. | [102] | SDN and 2FA (TOTP)-based virtualization method. | Prototype implementation, Proof of concept. | Security and assault reduction. | ARP spoofing is the only attack allowed with this method. |
| Confidentiality and attack detection. | [103] | PHE encryption, tracing, and revoking (tracing algorithm, public revocation algorithm). | Simulation, experimental analysis (an RBAC simulation system with ten classes and around ten users per class). | Tracking and key service interruptions provide safety. | It needs big master public keys. |
| Ref | Technology Employed | Performance Analysis | Advantage | Limitation |
|---|---|---|---|---|
| [104] | Enforce access control policy architecture. | NA | Simple policy. | It is only a preliminary proposal that needs implementation |
| [105] | STRIDE-based BYOD threat model. | NA | Help understand how BYOD concerns affect corporate data | Only provides an initial model. |
| [106] | An investigation framework. | Safe-Logic experts evaluated based on particular criteria. | Excellent awareness of BYOD threats and solutions. | Only provides an initial model. |
| [107] | Proactive approach based GQM (goal, question, metric). | NA | Creating benchmarks for BYOD security protocols. | Only identified security metric. |
| [108] | OPPRIM model. | Mathematical analysis and quantitative model. | Integrating trust and risk management mechanisms with threat analysis | Only provides an initial model. |
| [109] | Poise policy for device, app. | Prototype implementation. | It is network analysis. | It should build and test a complete prototype. |
| [110] | Fine-grained policies (BYODroid model). | Case Study. | Apply policy on the infrastructure layer. | Implementation is needed to verify rules. |
| [111,112] | Security architecture. | Case Study. | Flexible and adaptable to various business fields. | Only provides a starting point. |
| [113] | Metamodeling techniques. | Case study (Interview domain experts at the Ottawa Hospital to validate). | Identify key BYOD risk assessment metamodel concepts. | Initial and limited architecture. |
| [114,115] | Other methods (middleboxes and alert systems). | Prototype implementation. | Accurate transparency, usability, and performance with HTTPS security. | It is only a preliminary proposal that needs implementation. |
| [116] | Plugin Framework Based fine-grained security policy. | Prototype implementation. | Allows correct security policy execution on any device connection network organisation. | No other systems (only Android). |
| [117] | BYOD security framework | Case study (Australian, questionnaire instrument) | Building new framework to improve attack and threat defence. | Discusses only the theoretical aspect. |
| Ref | Requirement under Consideration | Purpose for the Evaluation | Evaluation Metrics |
|---|---|---|---|
| [44,46,47,50,51,54] | Authenticity. | To evaluate the functionalities of the authentication policy. | Access Response (Deny or Permit). |
| [45] | Authenticity. | To evaluate the possibility of an authentication policy for preventing unauthorized access. | Authentication Time, Access Response and Error Rate. |
| [48] | Authenticity. | To evaluate the performance of biometric authentication. | Accuracy and Frequency Detection Latency. |
| [49] | Authenticity. | To evaluate the functionalities of the authentication policy. | Response time and Cost. |
| [52,53] | Authenticity. | To evaluate the performance of the authentication system. | Performance, Memory Consumption, CPU consumption, Time overhead and Code Size |
| [55] | Confidentiality. | To reduce the time when switching the key. | Execution Time. |
| [67,68] | Confidentiality. | To evaluate the performance measurement of the MSS system. | Time and Performance Measurement. |
| [69] | Attack detection. | To evaluate the possibility of reducing management costs for Wireless Network Monitoring. | Cost. |
| [72] | Attack detection. | To evaluate the possibility of reducing costs and improving detection accuracy and efficiency. | Detection Accuracy and Cost. |
| [73,81] | Attack detection. | To evaluate the accuracy of detecting a specific malware and abnormal application class. | Accuracy. |
| [74] | Attack detection. | To evaluate the risk value associated with each access request. | Risk Value, Scalability and Context Awareness |
| [76] | Attack detection. | To determine the impact of threat and opportunity estimations on the risk. | threat probability. |
| [77] | Attack detection. | To evaluate the rate of detection and accuracy. | Accuracy and rate of detection |
| [78] | Attack detection. | To evaluate the model’s accuracy for detecting peer-to-peer traffic from torrent clients. | Accuracy and usability. |
| [79] | Attack detection. | To evaluate the ability to classify abnormal behavior. | Behaviour occurrence probability. |
| [80] | Attack detection. | To evaluate response time against internal threats. | Delay time. |
| [83] | Attack detection. | To evaluate the system’s ability to detect unauthorized access. | Precision (PPV), recall (TPR) and accuracy (ACC). |
| [84] | Attack detection. | To evaluate the ability to block unwanted application functions selectively. | Overhead and latency |
| [85] | Attack detection. | To evaluate RAM and CPU consumption over time. | RAM usage over time. CPU usage over time. |
| [86] | Attack detection. | To evaluate time duration and vulnerability assessment against the cyber threat. | Time and score assessment. |
| Ref | Requirement under Consideration | Purpose for the Evaluation | Evaluation Metrics |
|---|---|---|---|
| [56] | Confidentiality. | To evaluate the performance of PTA protocol. | Computation cost and performance consumption. |
| [57] | Confidentiality. | To evaluate the response time for each subsequent request. | Execution time, complexity of the access policy and block size. |
| [58] | Confidentiality. | Protecting BYOD users and network privacy with practical effect on communication performance. | Time complexity, communication costs and communications complexity. |
| [59] | Confidentiality. | To ensure the proper handshaking time between clients and serves. | Cost and exchange key time. |
| [61,64] | Confidentiality. | To reduce the delay in access time and run time. | Access time, power consumption and switching cost. |
| [62] | Confidentiality. | To evaluate the scalability of the approach. | CPU usage, memory usage and boot time. |
| [65] | Confidentiality. | To evaluate memory resource usage and power consumption due to virtualization. | Run-time memory usage and power consumption. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ayedh M, A.T.; Wahab, A.W.A.; Idris, M.Y.I. Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions. Appl. Sci. 2023, 13, 8048. https://doi.org/10.3390/app13148048
Ayedh M AT, Wahab AWA, Idris MYI. Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions. Applied Sciences. 2023; 13(14):8048. https://doi.org/10.3390/app13148048
Chicago/Turabian StyleAyedh M, Aljuaid Turkea, Ainuddin Wahid Abdul Wahab, and Mohd Yamani Idna Idris. 2023. "Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions" Applied Sciences 13, no. 14: 8048. https://doi.org/10.3390/app13148048
APA StyleAyedh M, A. T., Wahab, A. W. A., & Idris, M. Y. I. (2023). Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions. Applied Sciences, 13(14), 8048. https://doi.org/10.3390/app13148048








