MT-SOTA: A Merkle-Tree-Based Approach for Secure Software Updates over the Air in Automotive Systems
Abstract
:Featured Application
Abstract
1. Introduction
- An overview of the process for software updates over the air and the current solutions employed in the automotive industry.
- An overview of the new vehicle architectures and the challenges in dynamically updating selective software clusters.
- The design of a novel hash-based scheme that improves on the existing literature, efficiently stores integrity information for ECU software images, and addresses the various architectures of the software and vehicle markets. Our approach allows us to maintain one key security pair for signing and the same signature size to obtain the target security level. We define our scheme to accommodate interactions and compatibility between distinct software images, whether logically or physically interconnected within the vehicle.
- The development of the suggested approach prototype and demonstration that our strategy fulfills the specified requirements.
2. Related Work
3. System Model
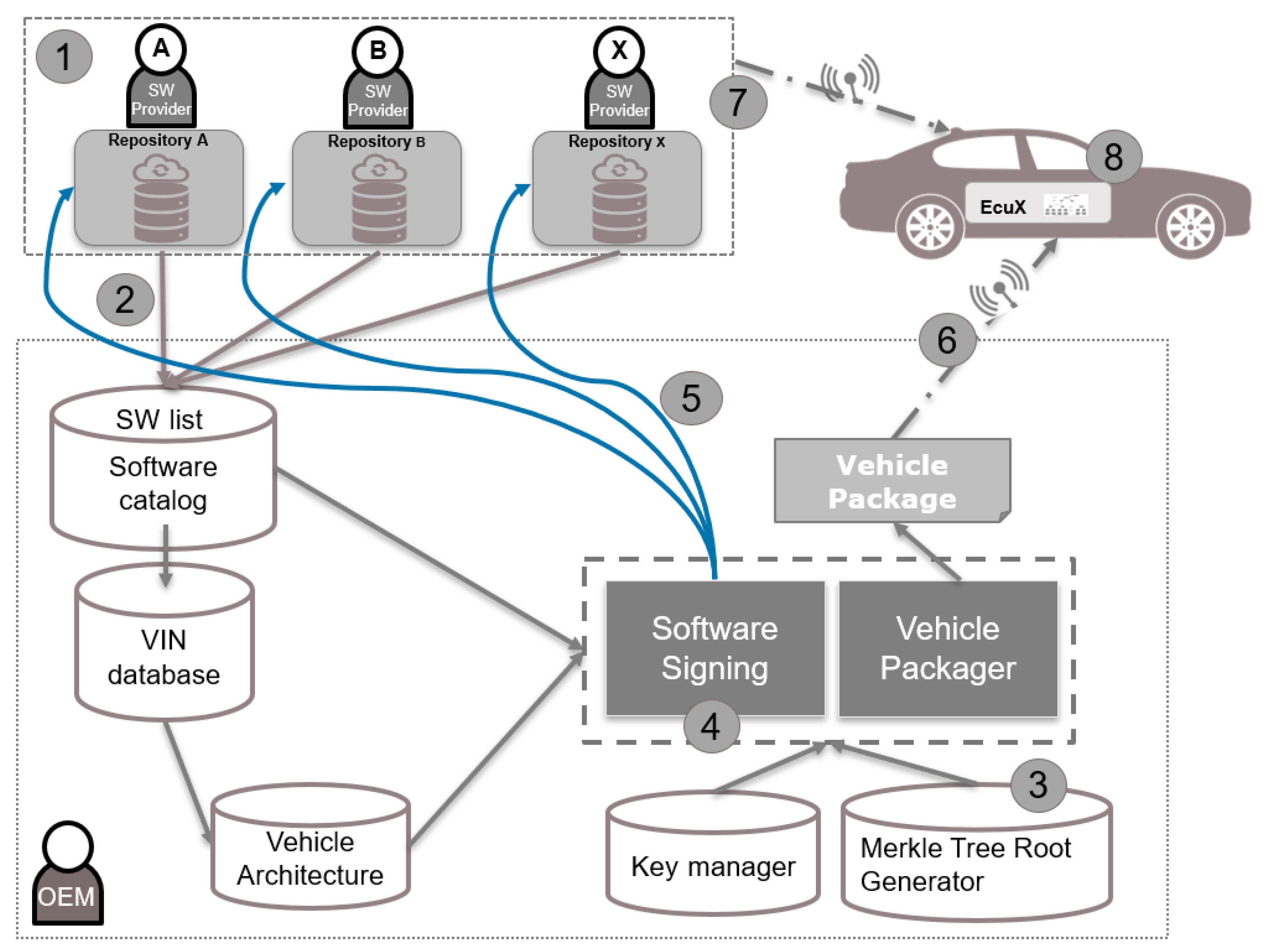
- OEM Repository “OemR”: This repository is responsible for signing software images. Given the role of OemR in common SOTA processes, OemR contains all of the information about images to be installed on ECUs, generally using an OEM inventory database containing information on vehicles, ECUs, software images, etc. Each software image must have a unique identifier linked to an ECU identifier that specifies the ECU installing the image. Our scheme extends the OemR with the capability of creating and maintaining the Merkle trees. In our study, we focus on a scenario in which software clusters reside in the same ECU. Thus, the OemR has to create a Merkle tree for each ECU in the vehicle. OemR has to store the hash value of each software cluster in addition to existing image metadata such as image name, version, size, hashing function used, and any additional proprietary OEM information, such as the download URL for the image file located in the image repository. OemR is trusted and responsible for protecting the harmonization among software clusters as well as the integrity of each software image to prevent any tampering.
- Image repository “ImgR”: This repository contains the software binary images to install as well as the signatures (authentication tags) for these images. These signatures are generated by OemR.
- OTA Master “OtaM”: This entity is responsible for receiving software images in the vehicle and distributing them to other ECUs in the vehicle. OtaM is capable of connecting to backend repositories through wireless channels, such as Wi-Fi or cellular communications.
- End-Target ECU “EcuX”: This is the ECU in the vehicle where software image is installed or updated. Upon reception of new image software, EcuX validates the integrity and authentication of the image as well as proves complete possession and compatibility of the software image in question. EcuX can be directly connected to OtaM through in-vehicle communication channels, e.g., CAN or Ethernet, or can be indirectly connected through a gateway or domain controller. In case the software image is intended for the OTA Master itself, OtaM will play the role of EcuX.
3.1. Adversary Model
3.2. Assumptions
- A1: ECUs are able to perform cryptographic digital signature operations and key management throughout the entire lifecycle, including key establishment, storage, and usage. By using existing methods such as public key infrastructure (PKI) [21], OemR owns a private and public key pair for each EcuX. OemR uses the private key for signature generation and EcuX uses the public key for signature verification. We assume that the public keys are distributed and installed in EcuX before any software updates can be performed. The public keys shared between the OemR and EcuX are not guessable and cannot be accessed by the adversary.
- A2: The communication between OemR and ImgR is secure. We assume that they are able to connect and communicate whenever the ImgR has a new software image version to be deployed to the vehicle or whenever OemR finds out that the vehicle does not have the latest software images.
- A3: The hash function used is not breakable, meeting the requirements of preimage-resistant, second-preimage-resistant, and collision-resistant for a hash function [22]. In other words, for a hash value H(SW) calculated for a given image software SW, it is infeasible to find the software image SW (preimage-resistant feature). It is also infeasible to find another image SW’ such that Hash(SW) = Hash(SW’) and SW ≠ SW’ (second-preimage-resistant feature), as it is also infeasible to find any two images SW and SW’ such that Hash(SW) = Hash(SW’) and SW ≠ SW’.
- A4: The chosen signature scheme is strongly unforgeable. Strong unforgeability assures the adversary cannot generate a new signature for a previously signed software image. In other words, assume an adversary obtains the software image and signature pair (SW, ); the signature is strongly unforgeable if the adversary cannot generate a new signature ’ for the same software image SW.
- A5: The OemR and EcuX share the same information about the Merkle tree (e.g., max number of software images, left-right bottom-up approach, static or dynamic). Otherwise, EcuX, as the verifier, cannot validate the correctness of the software image.
3.3. Requirements
- Requirement 1: The scheme shall allow detection of any tampering with the software image.
- Requirement 2: The scheme shall allow detection of any incompatibilities between the logically or physically dependent software images in the vehicle.
- Requirement 3: The scheme shall work with any frameworks or platforms supporting multiple binaries programming using digital signatures. The scheme shall support different types of hash algorithms as well as different signature mechanisms.
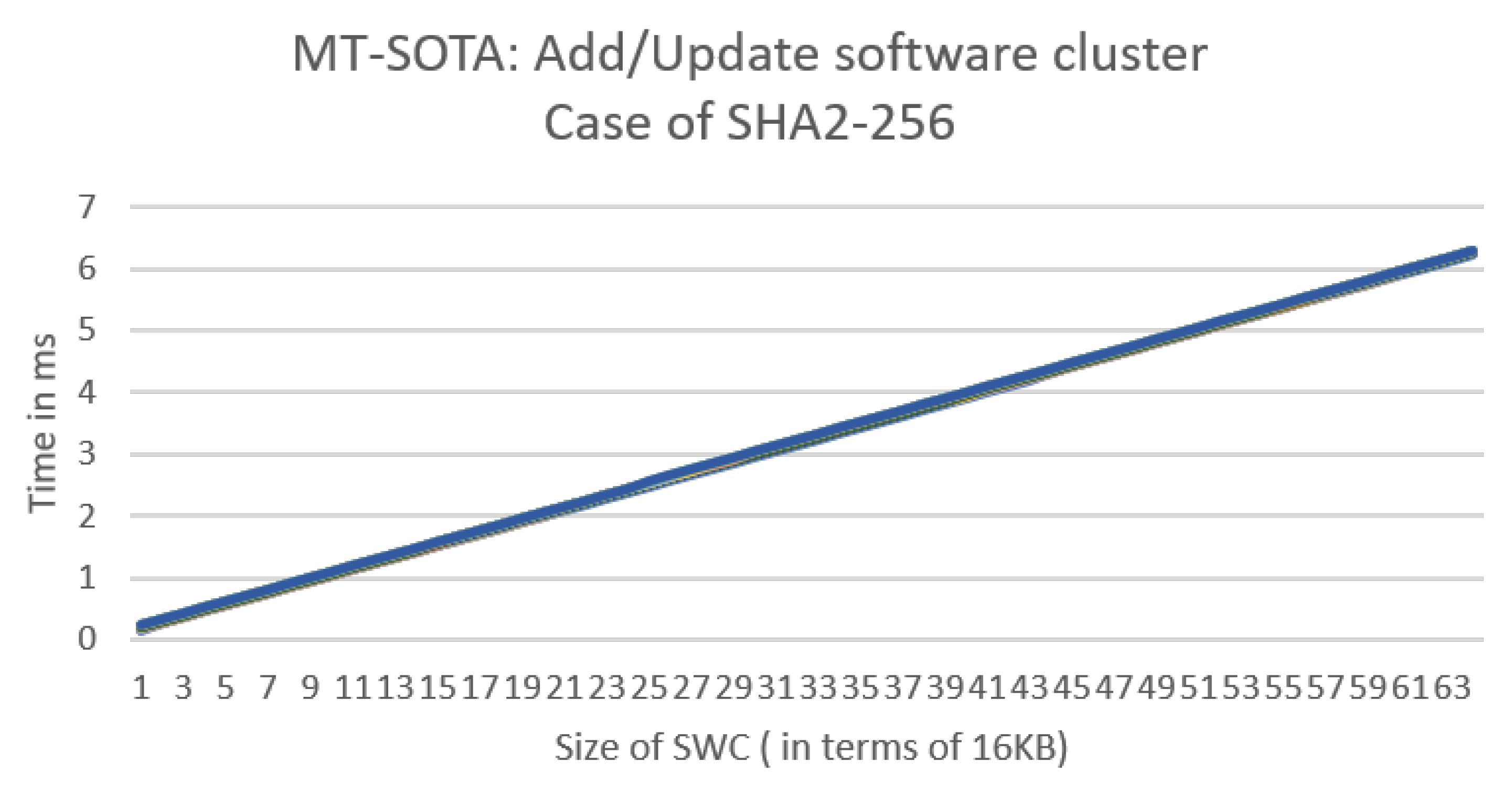
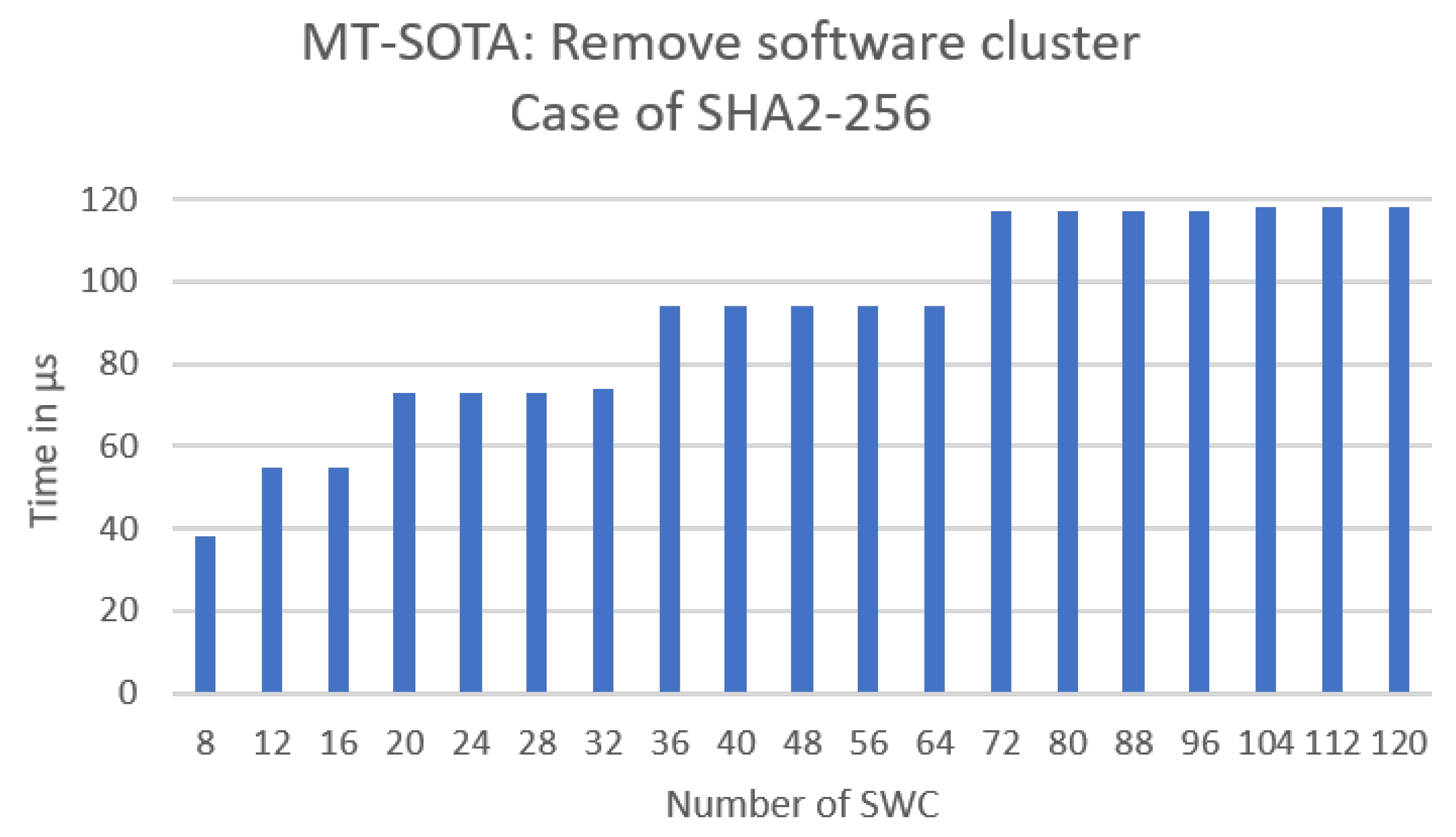
- Requirement 4: The scheme shall allow efficient addition or removal of software clusters. The vehicle should be able to receive requests to add a new software cluster or remove an existing one. Thus, the scheme shall enable efficient generation and secure storage of the signature.
- Requirement 5: As ECUs might be heterogeneous in terms of hardware, computation capabilities, and memory storage, the scheme shall make it possible to induce insignificant overheads in the lightweight ECUs with limited memory and computation resources on the installation of additional images.
- Requirement 6: The scheme may be used for intra-ECU and inter-ECU distribution of software clusters. Dependant software clusters can be located in the same physical ECU. However, it is possible they are physically running in different ECUs. In this case, it should be possible for the ECU to validate the signature even it doesn’t have access to complete software clusters. This enables flexibility to move a software cluster from one ECU to another ECU while keeping the dependency among the software clusters.
- Requirement 7: The scheme shall use one key pair per ECU to generate and verify the signature regardless of how many software clusters are used per ECU.
4. Scheme Design
- Case 1: A single software package in an ECU (e.g., traditional classic AUTOSAR platform, software is decomposed into software blocks).
- Case 2: Multiple software packages in an ECU (e.g., adaptive AUTOSAR, flexible classic AUTOSAR platform).
- Case 3: Multiple software packages in different ECUs (e.g., zone controllers and connected ECUs).
- Case 4: Multiple software packages on-board and off-board (e.g., AI-based cloud applications, backend user applications).
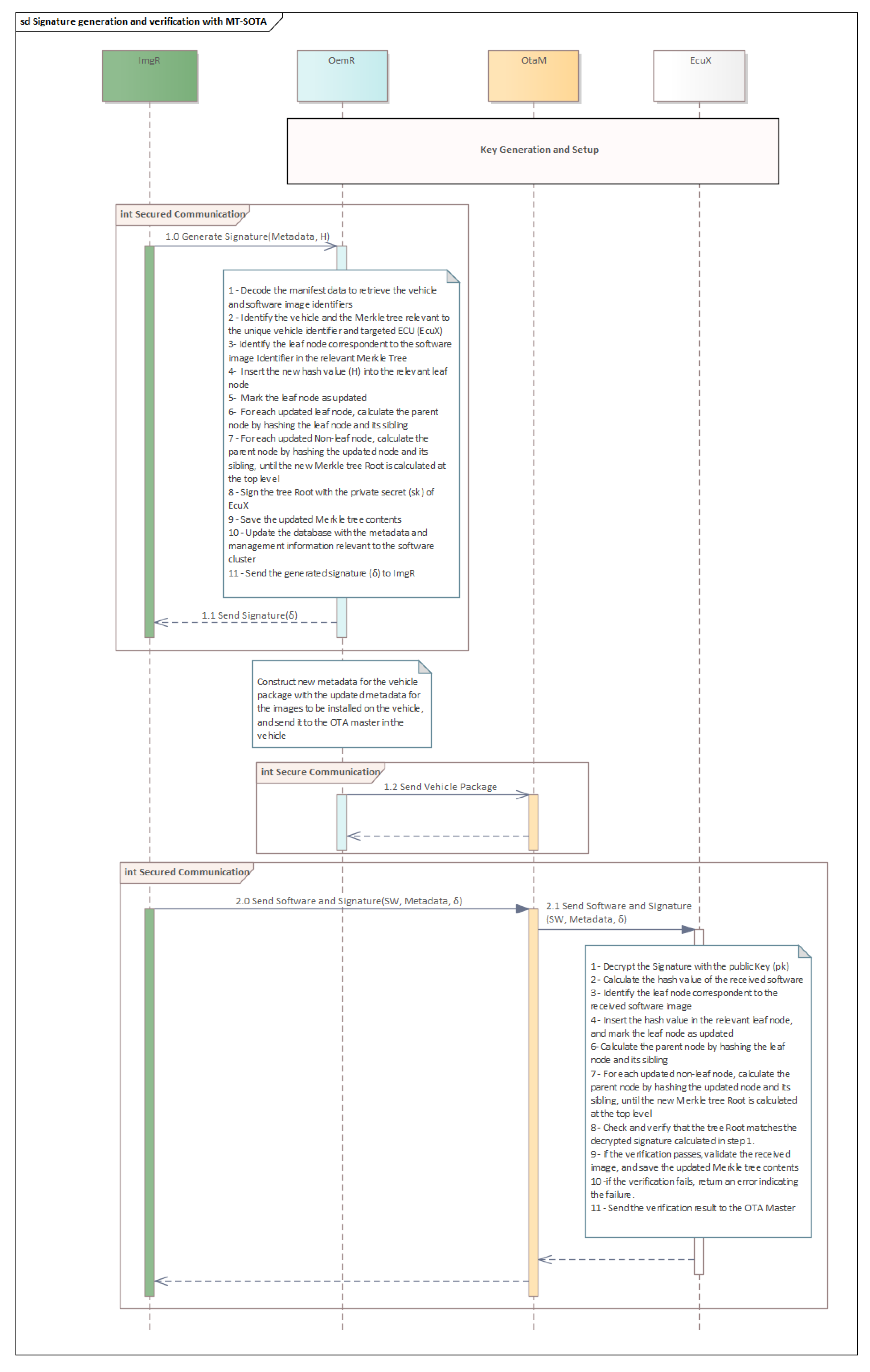
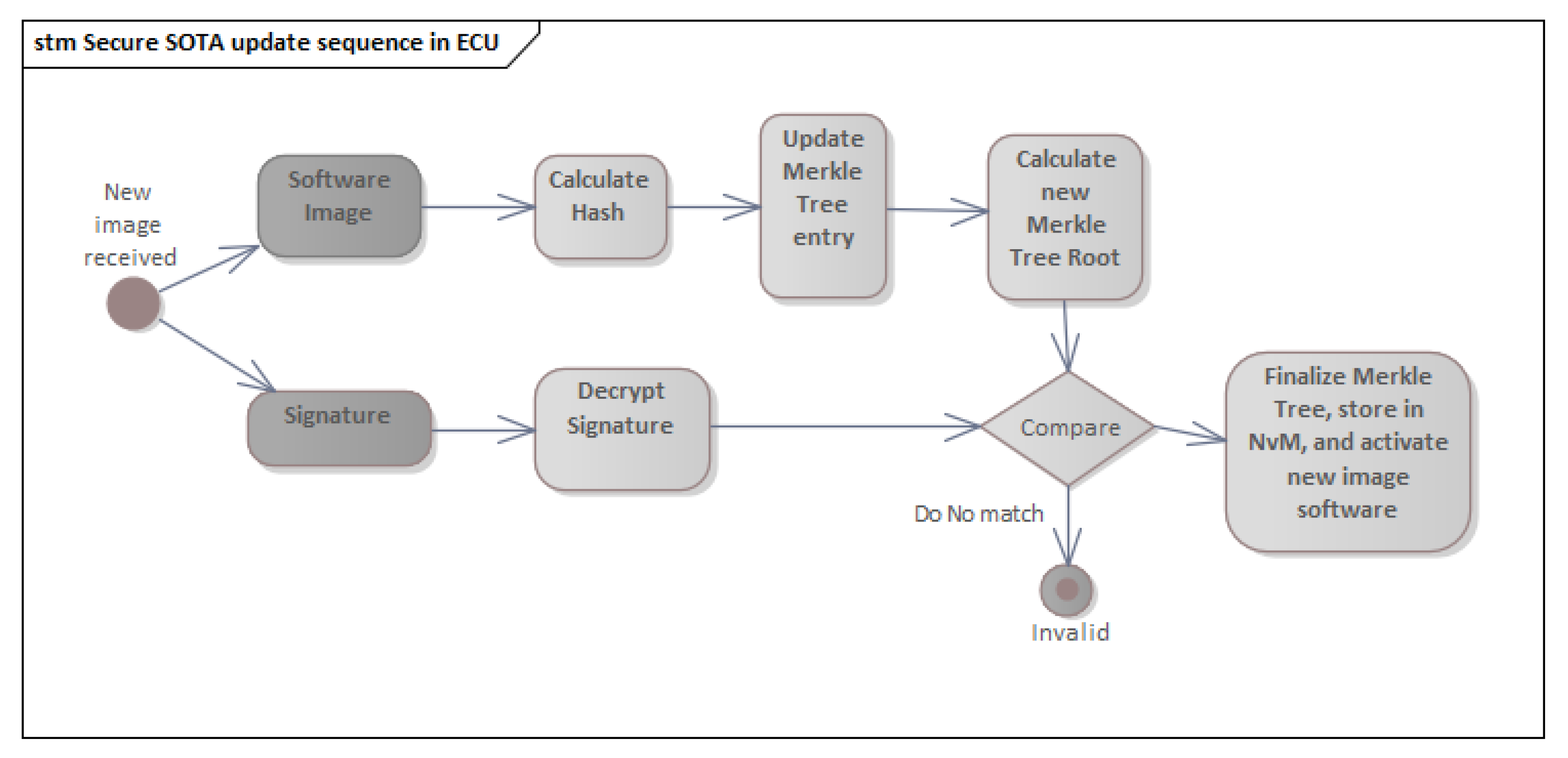
- The image software resides in the image repository (ImgR).
- The ImgR provides the correspondent hash value of the software image with additional manifest data to the OEM repository (OemR) to generate the signature.
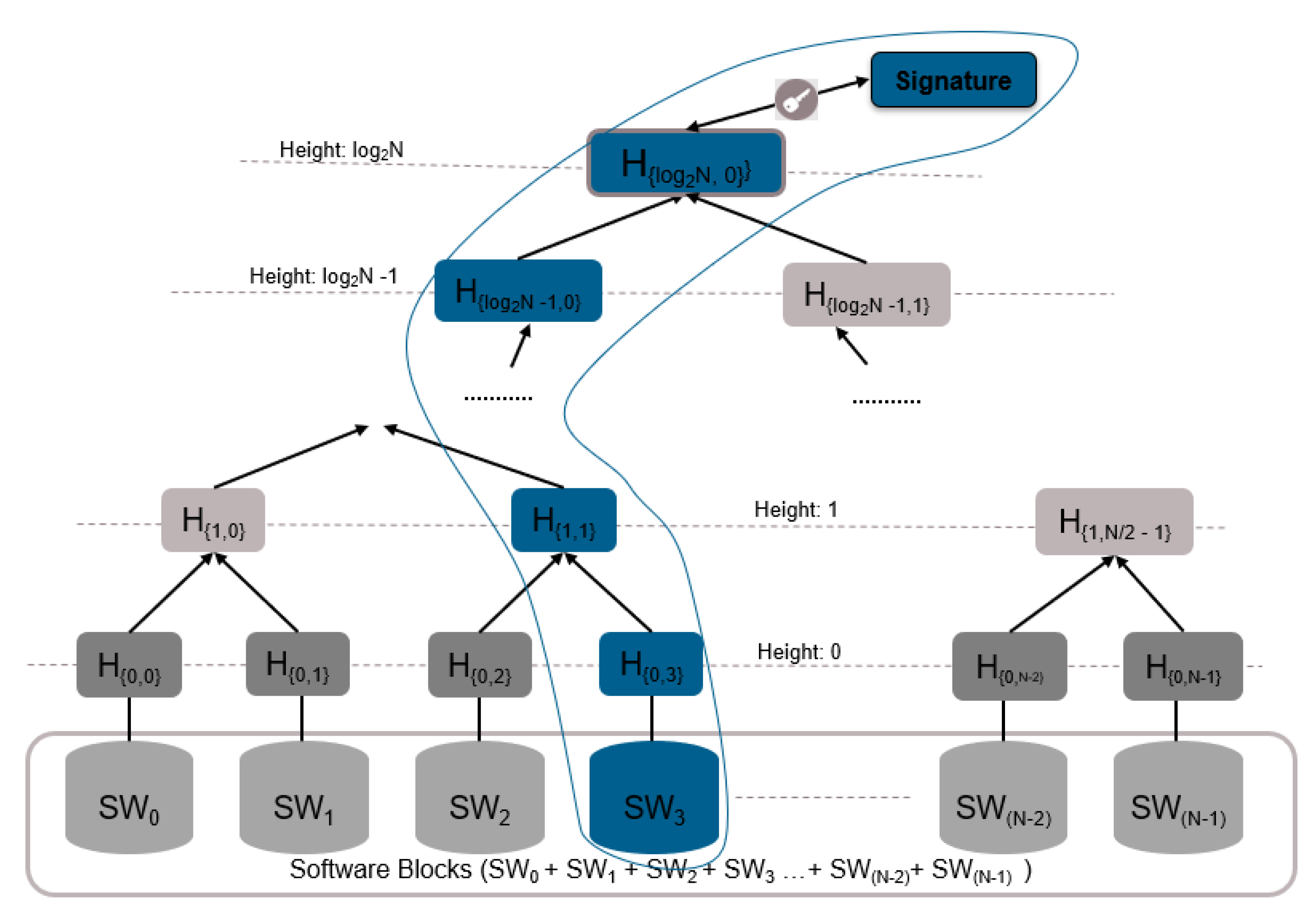
- The OemR has all information about the vehicle, ECUs, and software clusters. The OemR checks which ECU the software cluster belongs to and uses the corresponding Merkle tree to calculate the root.
- Using the private key assigned to EcuX, the Merkle tree root is signed to create the signature of the software image.
- The OemR provides the generated signature to ImgR.
- The OemR constructs the vehicle package containing the manifest data for the software images to be installed, and then sends it to the OtaM in the vehicle.
- The ImgR sends the software image appended with the signature.
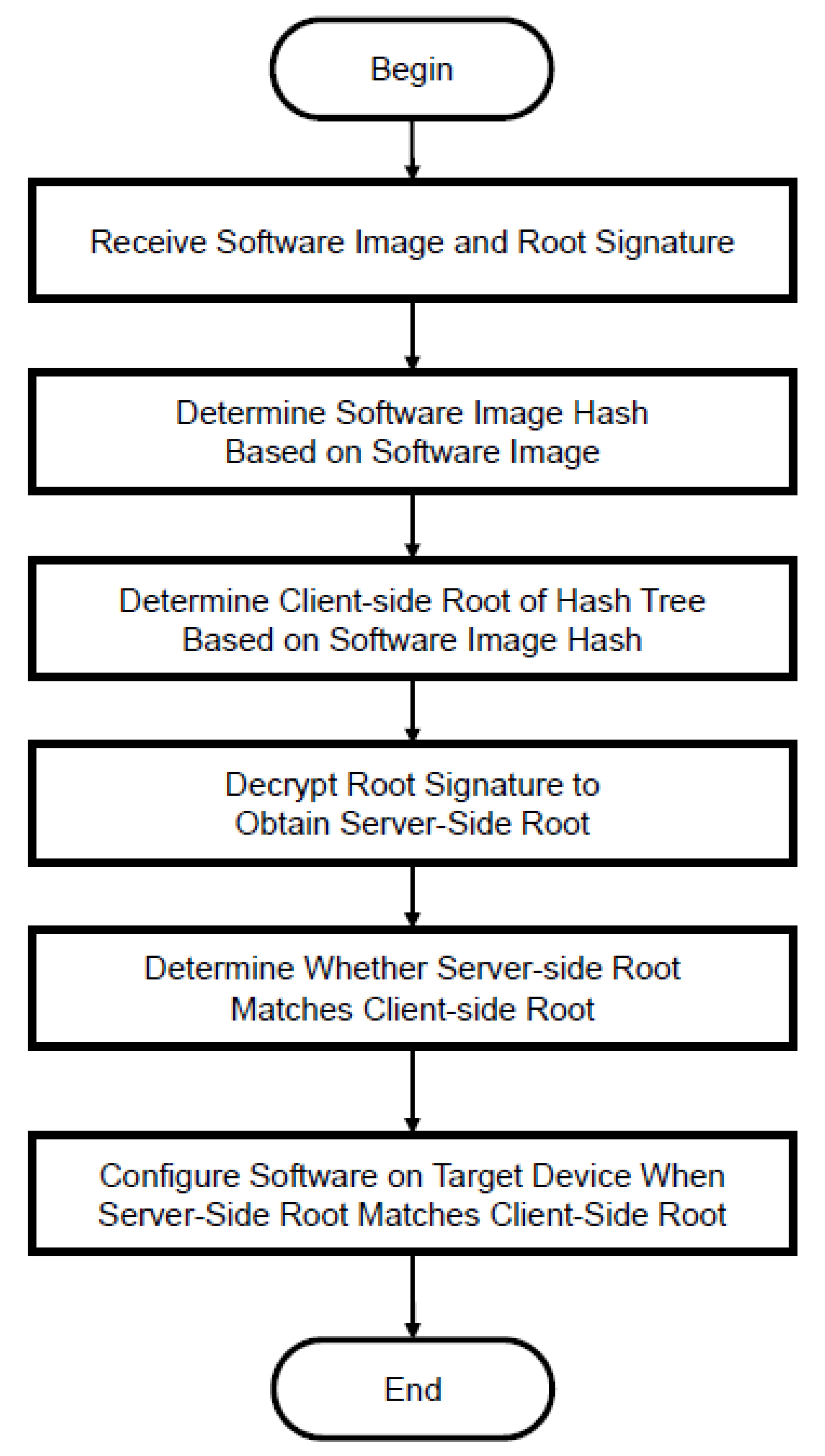
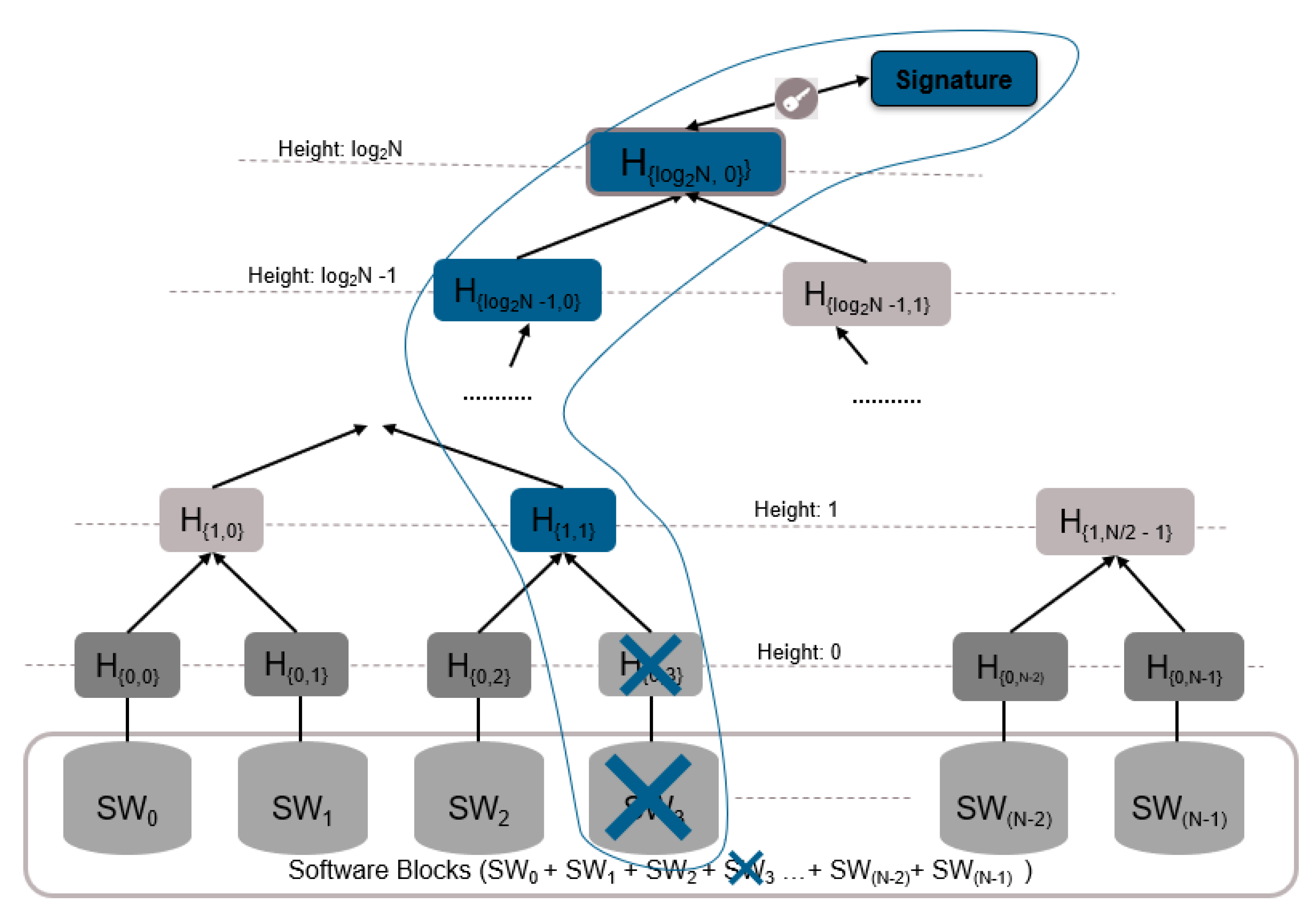
- Once EcuX receives the software image, it updates the Merkle tree with the hash of the received software image, and then it determines whether the root tree is the same as the one received from the ImgR (after decrypting the received value with the public key of EcuX). Once verified, EcuX stores the value of updated node and root node in the Merkle tree in a secure location.
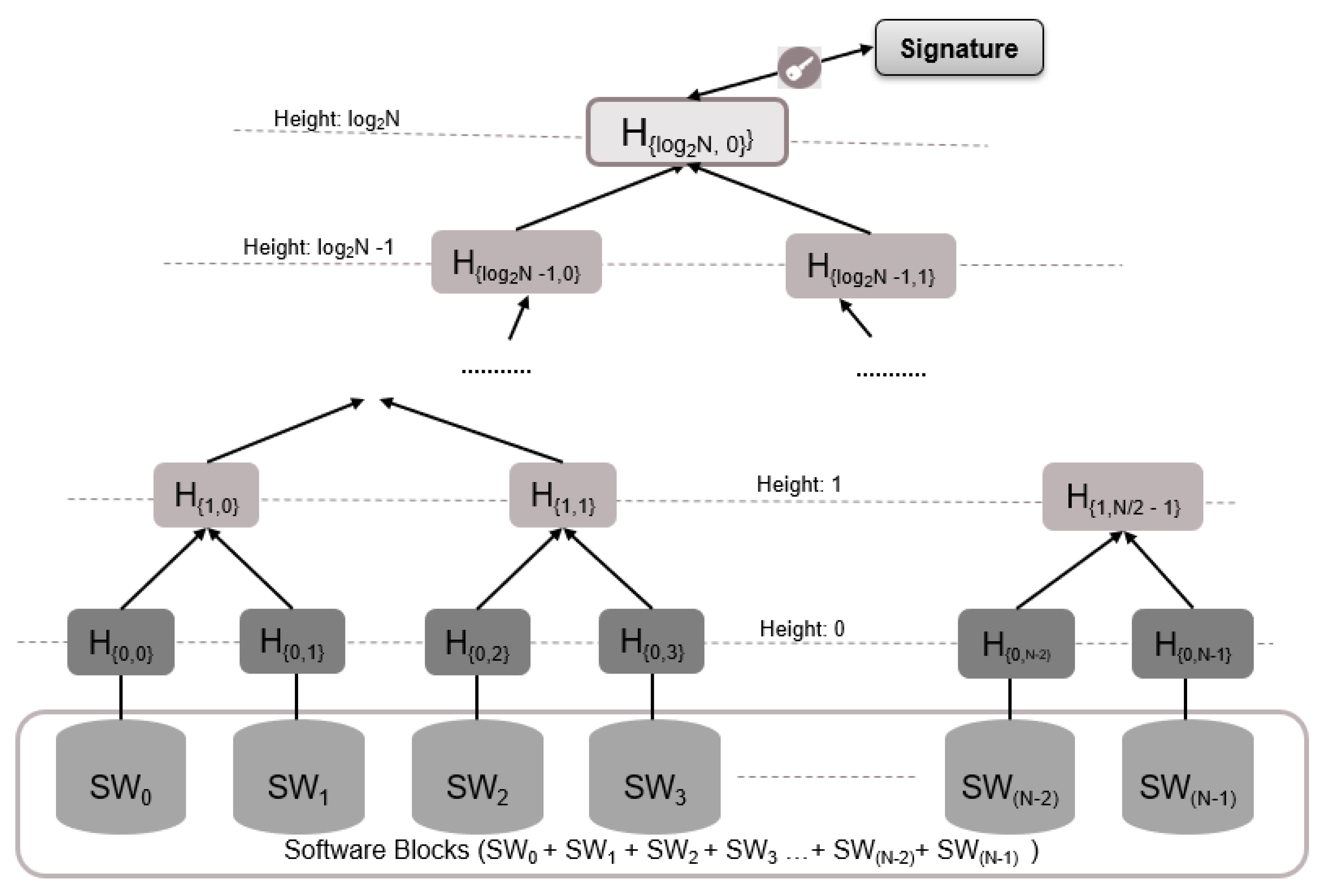
- SW = SW, …, SW: SW is one of the software cluster images to be updated in an ECU.
- N is the number of software clusters in an ECU.
- N is the max number of software clusters that can reside in an ECU throughout the lifetime of the ECU.
- S = ‖SW‖ is the size of the software cluster SW in bytes.
- H is the hash value of the software cluster SW image. ‖Hi‖ is the size of H in bytes.
- HT: is the Merkle tree height. The height at the root node is equal to log(N).
- SW is the modified SW cluster, SW∈ SW.
- MT: is the Merkle tree structure, MT[i][j] is the node at height i and index j.
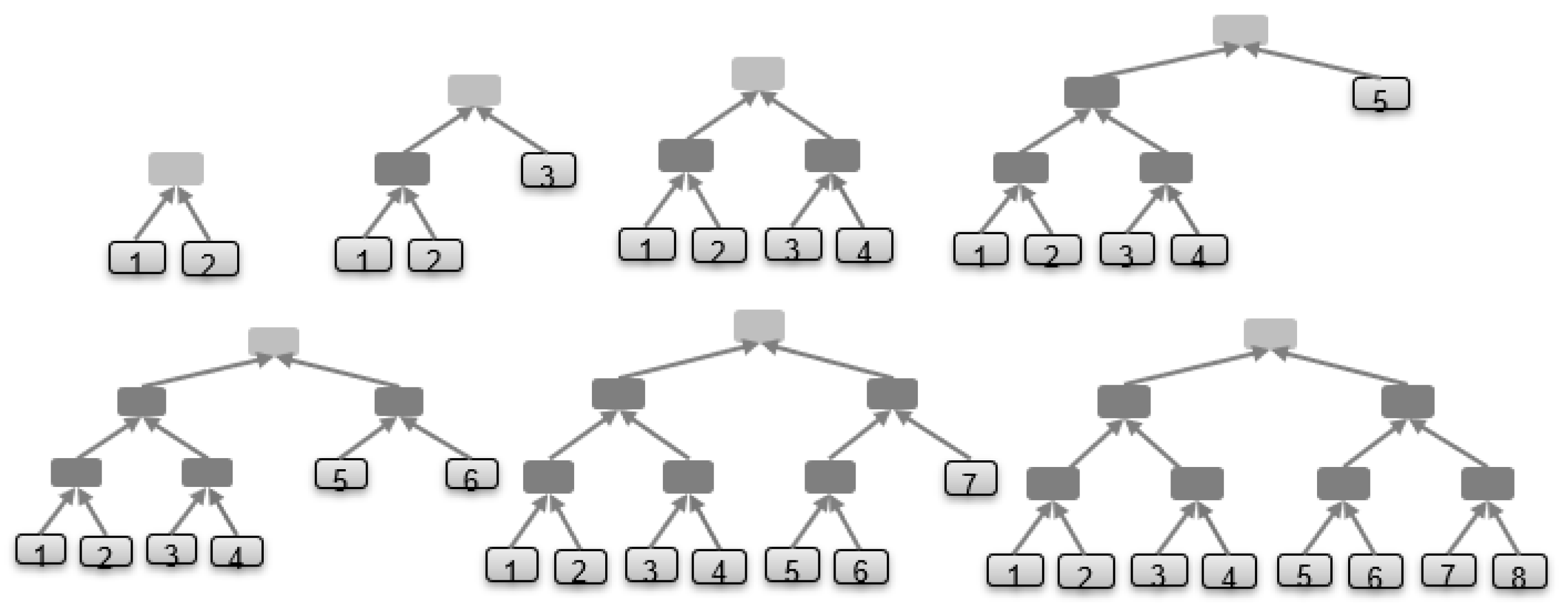
- The first set of hash results of the software images SW to SW, which are the H to H, represents leaf nodes in the hash tree at height 0.
- These nodes are combined in pairs to provide the first combined hash nodes. The value of the parent node is the hash of the concatenation of two child node hashes (left ‖ right), where concatenation is represented by ‖.
- The hash results are further combined in pairs to an intermediate level hash results. These intermediate level hash results are repeatedly paired and combined until only a single combined hash result remains. This is the Merkle tree root.
- Update an existing software cluster;
- Add a new software cluster;
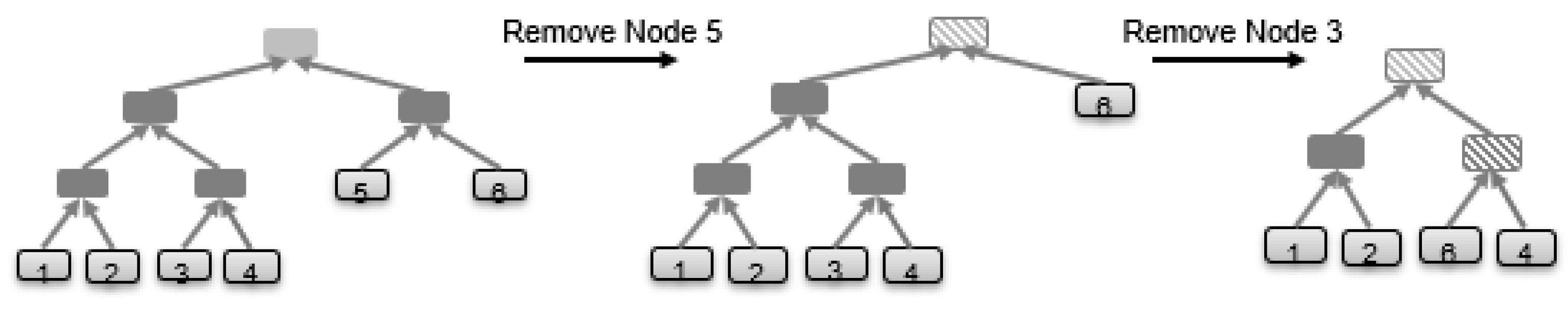
- Remove an existing software cluster.
| Algorithm 1 Merkle Tree Creation |
INPUT: List of software ID(SW), Address (Memory location), and Size(S) of each software cluster OUTPUT: Merkle Tree Root FUNCTION: BuildMerkleTree for i = 1 to N if (SW exist) Calculate H and save as a leaf node in tree end Calculate Merkle tree contents (MT[i][j]): (j is index of node in i level of the Merkle tree. i goes from 1 to HT, and j goes from 0 to (2HT−i−1) which is the number of nodes at the i level) for i = 1 to Height of the tree (HT) for j = 0 to number of nodes at the current level Calculate Hash of the child nodes (e.g., MT[i][j] = hash(MT[i−1][2j], MT[i−1][2j+1])) end end |
5. Security Analysis
- Fact1: Security of Merkle-Tree-Based Signature
- Fact2: Authentication of the individual software image
- Fact3: Resilience to the leakage of information
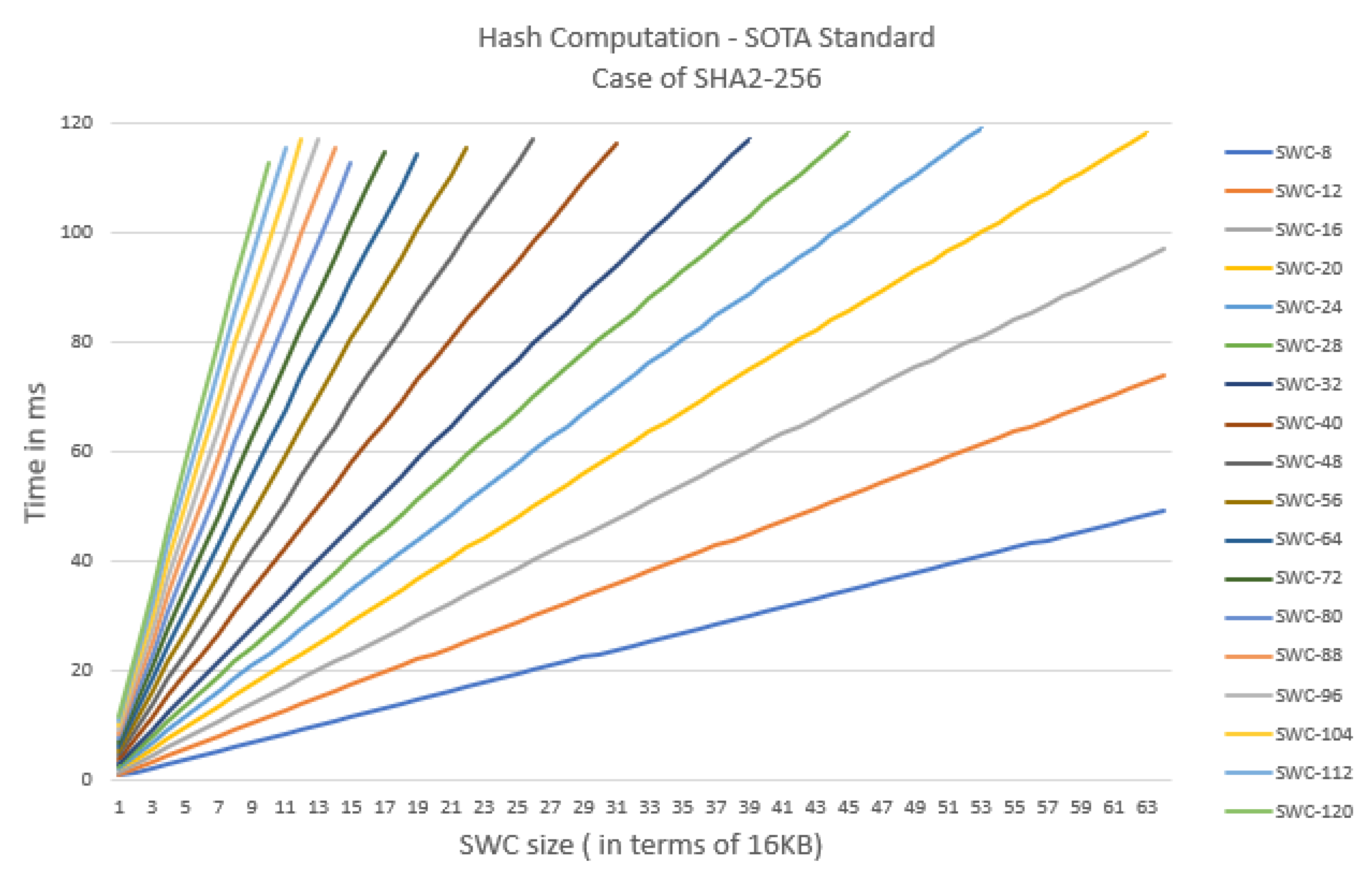
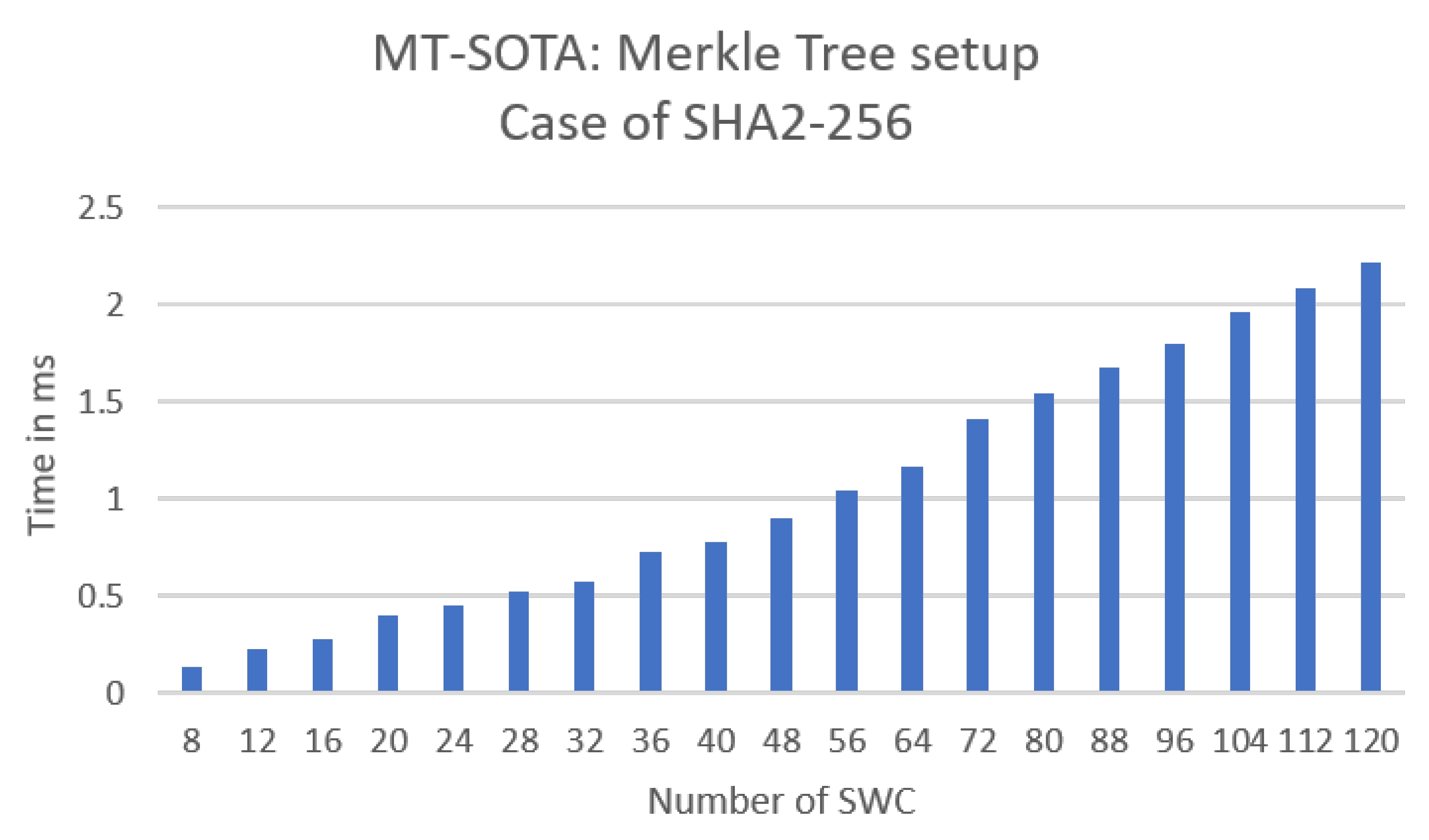
6. Evaluation and Analysis
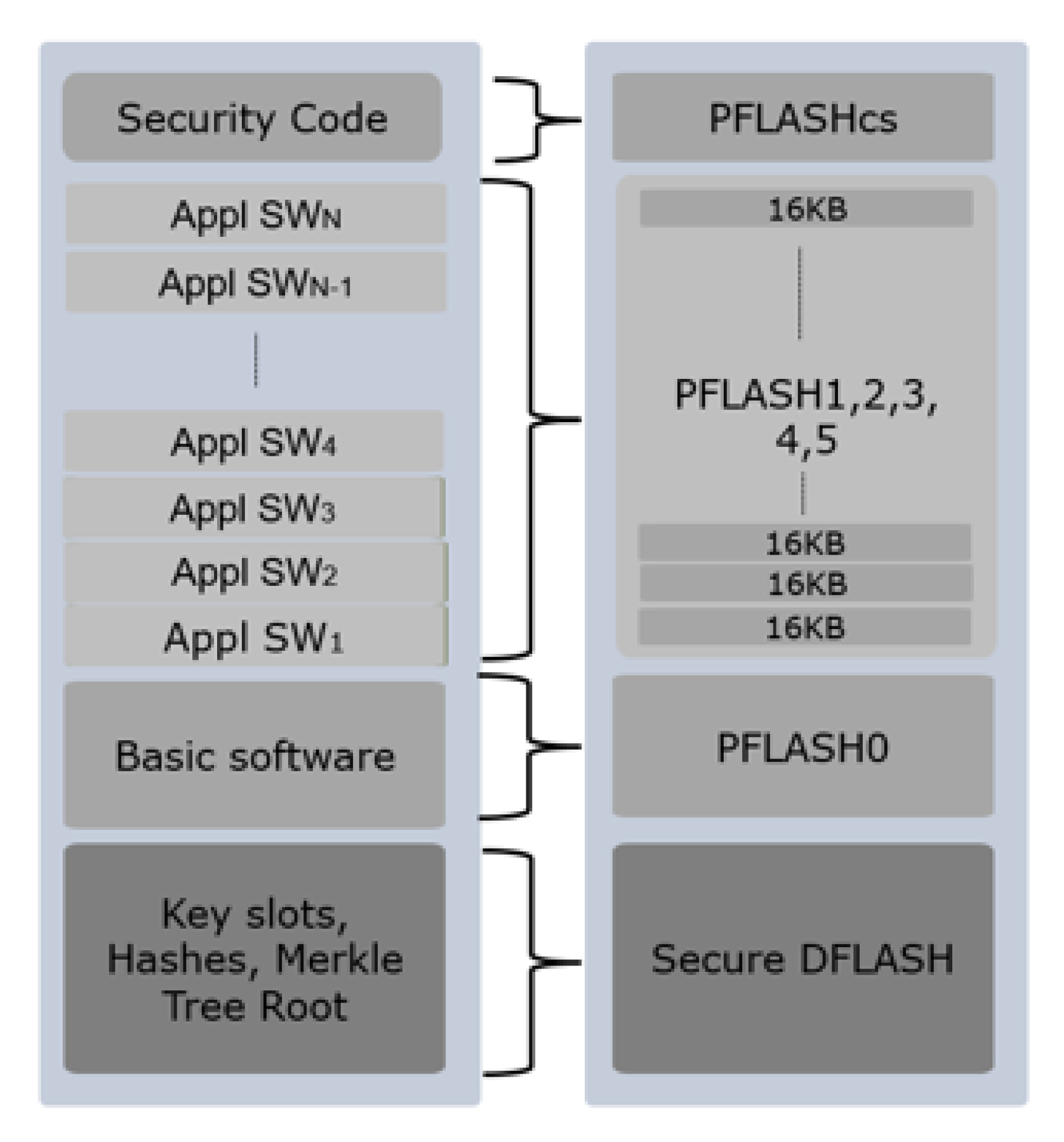
6.1. OemR
6.2. EcuX
6.3. Experimental Evaluation
- SHA-2: Length: 224, 256, 384, 512
- SHA-3: Length: 224, 256, 384, 512
- BLAKE: Length: 224, 256, 384, 512
- BLAKE: Length: 224, 256, 384, 512
- RIPEMD-160: Length: 128, 160, 256, 320
- SM3: Length: 256
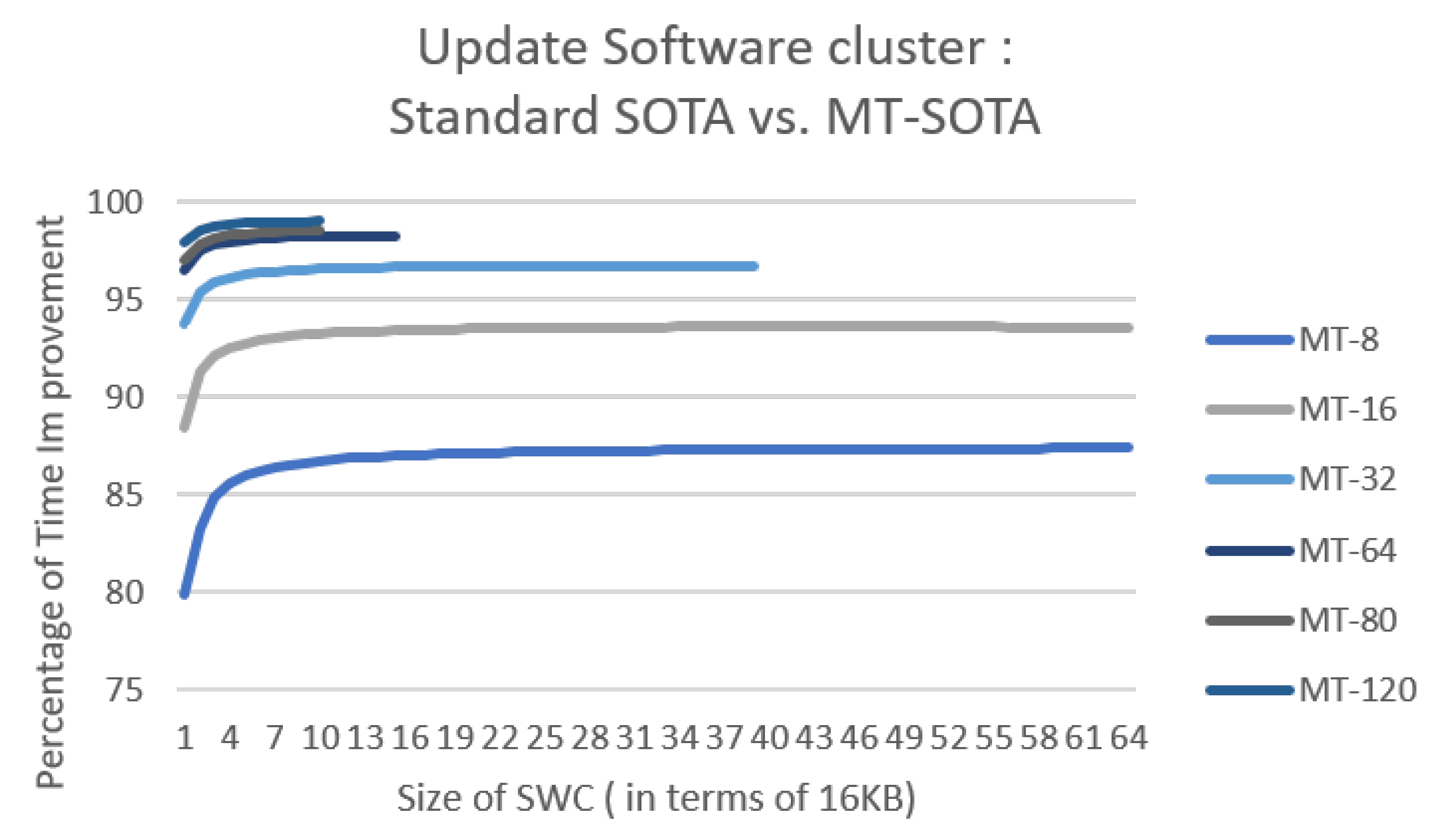
7. MT-SOTA Optimization Techniques
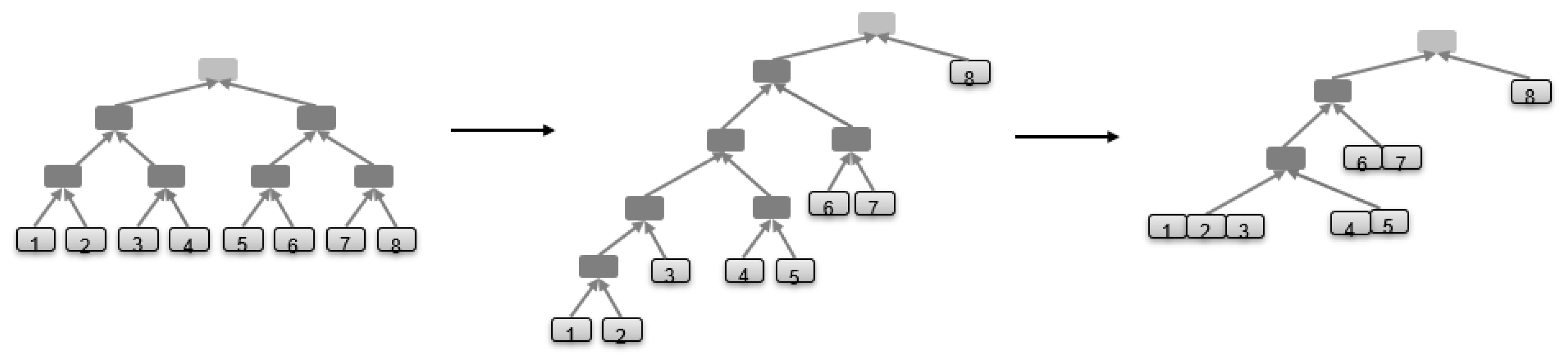
7.1. Dynamic Merkle Tree Algorithm
7.2. Skewed (Unbalanced) Merkle-Tree-Based SOTA
7.3. Memory Reduction—Usage of Different Hash Algorithm for Non-Leaf Nodes
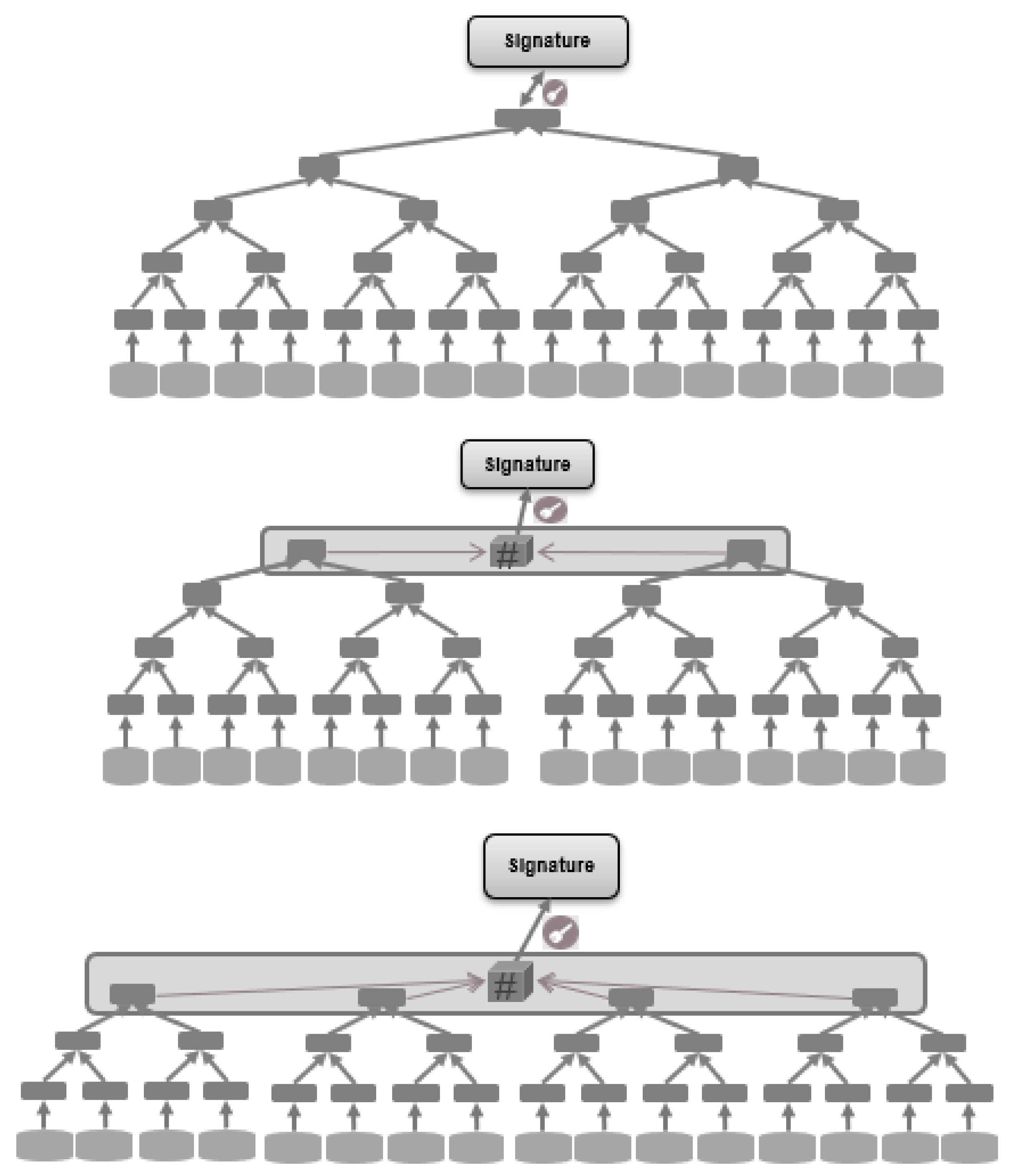
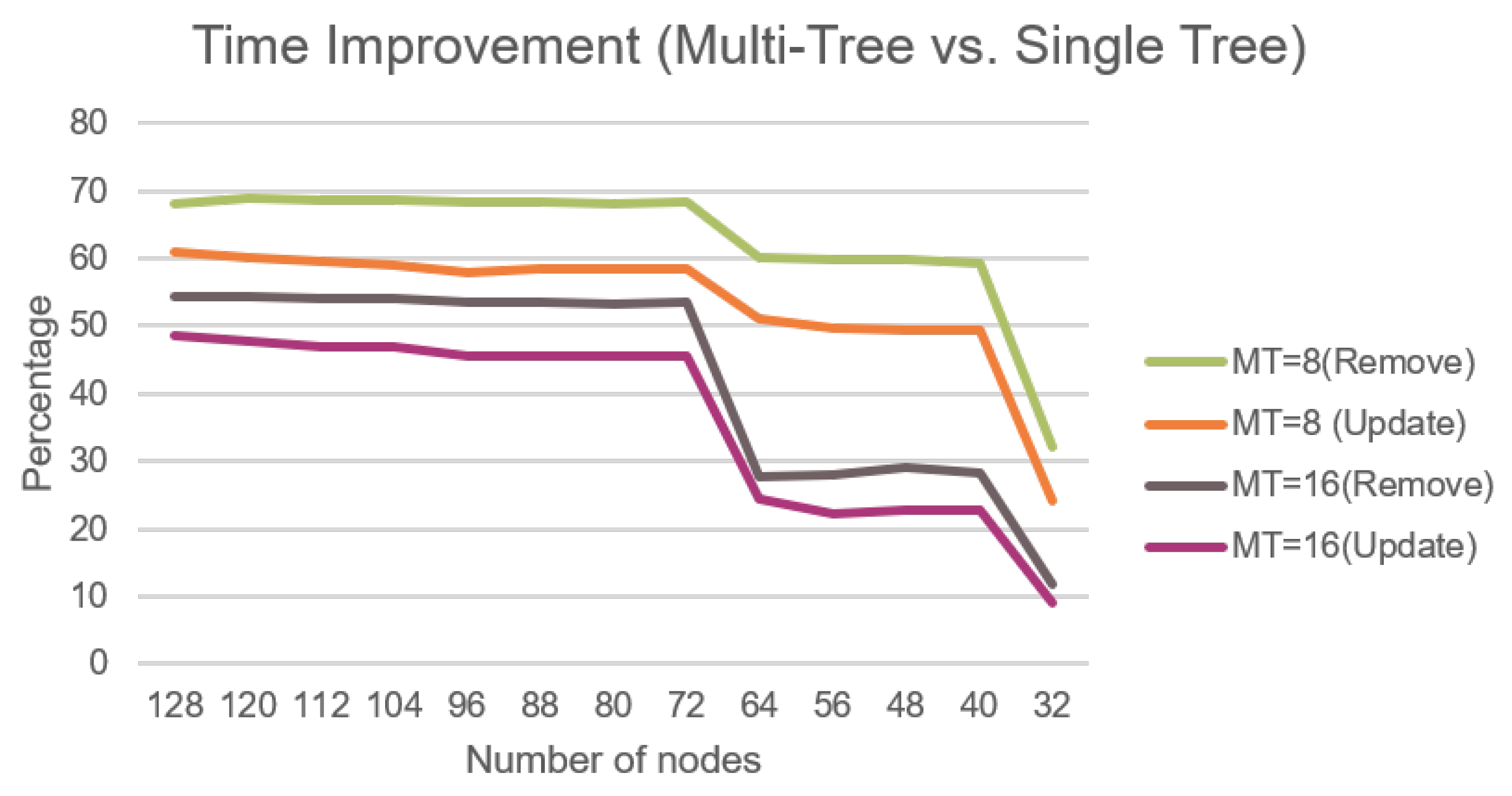
7.4. Time Execution Improvement—Multi Root Merkle Trees
7.5. Pre-Flash of Merkle Tree Leaf Nodes
8. Conclusions and Future Research
9. Patents
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AUTOSAR | AUTomotive Open System ARchitecture |
| ECU | Electronic Control Unit |
| ImgR | Image Repository |
| MT-SOTA | Merkle Tree-Based Software Updates over the Air |
| OEM | Original Equipment Manufacturer |
| OemR | OEM Repository |
| OtaM | OTA Master |
| SOTA | Software Updates over the Air |
Appendix A
| Algorithm A1 Dynamic Merkle Tree Node Insertion |
INPUT: SW ID, H OUTPUT: Merkle Tree Root, Position of SW FUNCTION: AddToMerkleTree if ( 2 = N) //Tree is full, Need to add another level { MT[HT][1] = H; MT[HT+1][0] = Hash(MT[HT][0], MT[HT][1]); Pos(SW) = [Height = HT, Index = 1]; HT++; N++; Return; //Exit } HT = HT-1;//starting at the top level( below the Root) i = 0; NodeNotlocated = 1; do //start of the (do- while)loop if(MT[HT][i] AND MT[HT][i+1] are leaf nodes) { MT[HT- 1][2i] = MT[HT][i]; MT[HT - 1][2i+1] = MT[HT][i+1]; MT[HT][i] = MT[HT+1][i/2]; MT[HT][i+1] = H; j = i; HT = HT; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j = 1 then j = 0; HT++; } Pos(SW) = [Height = HT,Index = i+1]; N++; NodeNotlocated = 0; //Exit while loop } else if ( MT[HT][i] is leaf node) { MT[HT- 1][i] = MT[HT][i]; MT[HT - 1][i+1] = H; MT[HT][i] = Hash(MT[HT-1][i], MT[HT-1][i+1]); j =i; HT = HT; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j =1 then j = 0; HT++; } Pos(SW) = [Height = HT - 1,Index = i+1]; N++; NodeNotlocated = 0; //Exit while loop } else if (MT[HT][i+1] is leaf node) { MT[HT-1][2i+2] = MT[HT][i+1]; MT[HT-1][2i+3] = H; MT[HT][i+1] = Hash(MT[HT - 1][2i+2], MT[HT -1][2i+3]); j =i; HT = HT; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j =1 then j=0; HT++; } Pos(SW) = [Height = HT - 1,Index = 2i+3]; N++; NodeNotlocated = 0; //Exit while loop } else { if (MT[HT][i] is set as complete) { //add node on the right side at this level i = 2*(i+1); HT = HT-1; } else { //add node on the left side at this level i = 2*i; HT = HT-1; } } while (NodeNotlocated) //end of the (do- while)loop |
| Algorithm A2 Dynamic Merkle Tree-Node Deletion |
INPUT: SW OUTPUT: Merkle Tree Root FUNCTION: DeleteFromMerkleTree Pos = Position (SW); if ( N % 2 == 0) // Node number is Even { DeleteNode(Pos); //Just delete node, no re-balancing } else // Node number is Odd—Rebalancing might be needed { HTt = HT; //starting at the top Root level i = 0; LineB: if ( MT[HTt][i] has 2 non-leaf nodes) if ( Pos at left side) i = 2i; else i = 2i + 1; HTt = HTt -1; goto LineB; else if ( MT[HTt][i] has 2 leaf nodes) [ SW, Ht2, Index2] = CheckSingleleafNode(HTt, Pos); if exist if deleted node is the left one: MT[HTt-1][2i] = MT[HT2][Index2]; MT[HTt][i] = Hash(MT[HTt-1][2i], MT[HTt-1][2i+1]); if deleted node is the right one: MT[HTt][2i+1] = MT[HT2][Index2] MT[HTt][i] = Hash(MT[HTt-1][2i], MT[HTt-1][2i+1]); j = i;if j =1 then j = 0; HT = HTt; while (HT < Ht2) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j =1 then j=0; HT++; } DeleteNode(Pos); Return; if Do not exist if deleted node is the left one: MT[HTt][i] = MT[HTt - 1][2i+1] else if deleted node is the right one: MT[HTt][i] = MT[HTt - 1][2i] j = i;if j =1 then j = 0; HT = HTt; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j = 1 then j = 0; HT++; } else if ( MT[HTt][i] has 1 leaf node) if it is a single node: { if deleted node is the leaf left node: MT[HTt+1][i/2] = MT[HTt][2i] else if deleted node is the leaf right node: MT[HTt+1][i/2] = MT[HTt][2i+1] } else { if deleted node is the leaf left node: MT[HTt][i] = MT[HTt - 1][2i+1] else if deleted node is the leaf right node: MT[HTt][i] = MT[HTt - 1][2i] else if deleted node is neither one: if ( Pos at left side) i = 2i; else i = 2i+1; HTt = HTt -1; goto LineB; } j = i;if j = 1 then j = 0; HT = HTt; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j =1 then j = 0; HT++; } N = N- 1; Height-Adjustment(); } INPUT: Pos //Position of SW OUTPUT: Merkle Tree Root FUNCTION: DeleteNode { HTt = HT; //starting at the top Root level i =0; LineA: if ( MT[HTt][i] has 2 non-leaf nodes) if ( Pos at left side) i = 2i; else i = 2i+1; HTt = HTt -1; goto LineA; else if ( MT[HTt][i] has 2 leaf nodes) if deleted node is the left one: MT[HTt][i] = MT[HTt - 1][2i+1] if deleted node is the right one: MT[HTt][i] = MT[HTt - 1][2i] j = i; if j =1 then j = 0; HT = HTt; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j = 1 then j = 0; HT++; } else if ( MT[HTt][i] has 1 leaf node) if deleted node is the leaf left node: MT[HTt][i] = MT[HTt - 1][2i+1] if deleted node is the leaf right node: MT[HTt][i] = MT[HTt - 1][2i] j = i; HT = HTt; while (HT < HT) { MT[HT+1][j/2] = Hash(MT[HT][j], MT[HT][j+1]); j = j/2; if j = 1 then j = 0; HT++; } N = N - 1; Height-Adjustment(); } |
References
- Dixon, R. Evolution of New EE Architecture. S&P Global. Available online: https://autotechinsight.ihsmarkit.com/shop/product/5003328/evolution-of-new-ee-architecture-october-2022 (accessed on 1 December 2022).
- AUTOSAR, Adaptive Release R22-11, 2022. Available online: https://www.autosar.org/search?tx_solr%5Bfilter%5D%5B0%5D=category%3AR22-11&tx_solr%5Bfilter%5D%5B1%5D=platform%3AAP&tx_solr%5Bq%5D= (accessed on 1 January 2023).
- Zeeb, A. AUTOSAR Classic Platform Flexibility Managing the complexity of distributed embedded software development: Invited Talk. In Proceedings of the IEEE 18th International Conference on Software Architecture Companion (ICSA-C), Stuttgart, Germany, 22–26 March 2021; p. 167. [Google Scholar]
- NIST FIPS 186-5, Digital Signature Standard (DSS), 3 February 2023. Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.186-5.pdf (accessed on 1 April 2023).
- Bazzi, A.; Shaout, A.; Ma, D. Secure Software Update in Automotive Modern Software Architecture. In Proceedings of the Women in Semiconductor Hardware (WISH) Conference, San Jose, CA, USA, 14–15 September 2022. [Google Scholar]
- Bielawski, R.; Gaynier, R.; Ma, D.; Lauzon, S.; Weimerskirch, A. Cybersecurity of Firmware Updates; Technical Report DOT HS 812 807; National Highway Traffic Safety Administration: Washington, DC, USA, 2020. [Google Scholar]
- Rehman, G.U.; Haq, M.I.U.; Zubair, M.M.; Mahmood, Z.; Singh, M.; Singh, D. Misbehavior of nodes in IoT based vehicular delay tolerant networks VDTNs. Multimedia Tools Appl. 2023, 82, 7841–7859. [Google Scholar] [CrossRef]
- Rehman, G.U.; Zubair, M.; Qasim, I.; Badshah, A.; Mahmood, Z.; Aslam, M.; Jilani, S.F. EMS: Efficient Monitoring System to Detect Non-Cooperative Nodes in IoT-Based Vehicular Delay Tolerant Networks (VDTNs). Sensors 2023, 23, 99. [Google Scholar] [CrossRef] [PubMed]
- TCG Guidance for Secure Update of Software and Firmware on Embedded Systems; Rep. Version 1, Revision 72; Trusted Computing Group: Beaverton, OR, USA, 2020.
- A Firmware Update Architecture for Internet of Things; IETF RFC 9019; 2022. Available online: https://datatracker.ietf.org/doc/html/rfc9019 (accessed on 15 August 2023).
- Kuppusamy, T.K.; DeLong, L.A.; Cappos, J. Uptane: Security and Customizability of Software Updates for Vehicles. IEEE Veh. Technol. Mag. 2018, 13, 66–73. [Google Scholar] [CrossRef]
- Steger, M.; Boano, C.A.; Niedermayr, T.; Karner, M.; Hillebrand, J.; Roemer, K.; Rom, W. An Efficient and Secure Automotive Wireless Software Update Framework. IEEE Trans. Ind. Inform. 2018, 14, 2181–2193. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Sun, L.; Nakajima, T. A Framework for Self-Verification of Firmware Updates over the Air in Vehicle ECUs. In Proceedings of the IEEE Globecom Workshops, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5. [Google Scholar]
- Ghosal, A.; Halder, S.; Conti, M. STRIDE: Scalable and Secure Over-The-Air Software Update Scheme for Autonomous Vehicles. In Proceedings of the IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Mansour, K.; Farag, W.; ElHelw, M. AiroDiag: A sophisticated tool that diagnoses and updates vehicles software over air. In Proceedings of the IEEE International Electric Vehicle Conference, Greenville, SC, USA, 4–8 March 2012; pp. 1–7. [Google Scholar]
- Mayilsamy, K.; Ramachandran, N.; Raj, V.S. An integrated approach for data security in vehicle diagnostics over internet protocol and software update over the air. Sci. Direct-Comput. Electr. Eng. 2018, 7, 578–593. [Google Scholar] [CrossRef]
- Suzuki, N.; Hayashi, T.; Kiyohara, R. Data Compression for Software Updating of ECUs. In Proceedings of the IEEE 23rd International Symposium on Consumer Technologies, Ancona, Italy, 19–21 June 2019; pp. 304–307. [Google Scholar]
- Bogdan, D.; Bogdan, R.; Popa, M. Delta flashing of an ECU in the automotive industry. In Proceedings of the IEEE 11th International Symposium on Applied Computational Intelligence and Informatics, Timisoara, Romania, 12–14 May 2016; pp. 503–508. [Google Scholar]
- Baza, M.; Nabil, M.; Lasla, N.; Fidan, K.; Mahmoud, M.; Abdallah, M. Blockchain-based Firmware Update Scheme Tailored for Autonomous Vehicles. In Proceedings of the IEEE Wireless Communications and Networking Conference, Marrakesh, Morocco, 15–18 April 2019; pp. 1–7. [Google Scholar]
- Steger, M.; Dorri, A.; Kanhere, S.S.; Römer, K.; Jurdak, R.; Karner, M. Secure Wireless Automotive Software Updates Using Blockchains: A Proof of Concept. In Proceedings of the Advanced Microsystems for Automotive Applications, Berlin, Germany, 11–12 September 2018; pp. 137–149. [Google Scholar]
- Menezes, A.J.; van Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Rogaway, P.; Shrimpton, T. Cryptographic Hash-Function Basics: Definitions, Implications, and Separations for Preimage Resistance, Second-Preimage Resistance, and Collision Resistance. In Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2004; pp. 371–388. [Google Scholar]
- Burkacky, O.; Deichmann, J.; Stein, J. Automotive Software and Electronics 2030. Available online: https://www.mckinsey.com/industries/automotive-and-assembly/our-insights/the-case-for-an-end-to-end-automotive-software-platform (accessed on 22 March 2023).
- ISO/IEC 10118-3:2018; IT Security Techniques—Hash-Functions —Part 3: Dedicated Hash-Functions. ISO: Geneva, Switzerland, 2018.
- Merkle, R.C. A Certified Digital Signature. In Advances in Cryptology—CRYPTO’ 89 Proceedings; Brassard, Gilles: New York, NY, USA, 1990; pp. 218–238. [Google Scholar]
- Merkle, C. Method of Providing Digital Signatures. U.S. Patent US4309569A, 5 January 1982. [Google Scholar]
- Infineon Technologies TC4xx Evaluation Board. Available online: https://www.infineon.com/cms/en/product/microcontroller/32-bit-tricore-microcontroller/32-bit-tricore-aurix-tc4x/ (accessed on 1 March 2023).
- Infineon Technologies TC3xx Evaluation Board. Available online: https://www.infineon.com/cms/en/product/microcontroller/32-bit-tricore-microcontroller/32-bit-tricore-aurix-tc3xx/ (accessed on 1 March 2023).
- Meguellati, F.M.; Zegour, D.E. A Survey on Balanced Binary Search Trees methods. In Proceedings of the International Conference on Information Systems and Advanced Technologies (ICISAT), Tebessa, Algeria, 27–28 December 2021; pp. 1–5. [Google Scholar]
- Comer, D. Ubiquitous b-tree. ACM Comput. Surv. 1979, 11, 121–137. [Google Scholar] [CrossRef]






| Approach | Description | Pros | Cons |
|---|---|---|---|
| Message-digest/Hash-based [13,14] | Software package is hashed, and result is compared with a trusted known-good value. Different types of hash chain have been proposed to increase security. | Simple to implement. One-way only. No security keys used. Can be software or hardware implemented. Memory efficient (typically 256 bits). | Inefficient when there are many collisions. Known-good value must be read/write protected. |
| Symmetric-based [15] | Software package is encrypted with a common key and then decrypted at the receiver side with the same key. Another approach is to generate a message authentication code (MAC) using the common key and verify the same MAC code at reception. | Fast cryptography. Easily implemented (AES accelerators are widely available in microcontrollers.) Small key lengths. Example of symmetric keys used: AES (128/192/256 bits), CHACHA20 (128+ bits). Modes of sharing: Diffie-Hellman and physically. | Key security (key must be read/write protected). Managing keys is a challenge. Complexity consistent regardless of number of users or frequency of use. |
| Asymmetric-based [16] | Software package is encrypted with a private key and then decrypted at the receiver side with the corresponding public key. Another approach is to generate a code signature by hashing the software package and then encrypt the hash value using a private key (e.g., RSA 2048, Ed25519). | Key flexibility. Relatively long key lengths. Example of asymmetric keys used: RSA-2048 (256 bytes), RSA-7096 (512 bytes), ECDSA (secp521r1:1042-bit for public key, 132 bytes for signature), EdDSA (32/57 bytes for keys, 64/114 bytes for signature). Modes of sharing: PKI. | Key security (key must be read/write protected). Slower cryptography than symmetric schemes. Complex to implement for some algorithms (e.g., ECDSA and EdDSA). Complexity grows with number of users and frequency of use. |
| Blockchain-based [19,20] | Distributed peer-to-peer database. Data are saved on each node, transactions are saved into blocks.Cryptography is based on hashing and digital signatures (using asymmetric cryptography e.g., ECDSA.) | Immutable (permanent and tamper-proof). Decentralized control. Redundant decentralized copy on every node of the network. Consensus-based, creates trust and integrity in an untrusted environment | New to Automotive. High memory consumption in the ECU. |
| Secure Software Repository Framework [11,12] | Framework introduced to allow repositories to build different security models that provide varying degrees of security and usability (e.g., Uptane framework). | Separation of trust. Explicit and implicit revocation of keys. Flexible implementation (full or partial verification, asymmetric or symmetric keys, encrypted or unencrypted update image, online or offline keys. | OEM has to setup and maintain the repositories. |
| Height | Max Number of Node | Tree Storage in Bytes |
|---|---|---|
| 1 | 2 | 96 |
| 2 | 4 | 224 |
| 3 | 8 | 480 |
| 4 | 16 | 992 |
| 5 | 32 | 2016 |
| 6 | 64 | 4064 |
| 7 | 128 | 8160 |
| Parameter | Supported Cases |
|---|---|
| Hash algorithm (Hash output size in bytes) | SHA3-512 (64), SHA3-256 (32), SHA2-256 (32), SHAKE-256 (32), SHAKE-128 (16), SHA1-160 (20), MD5-128 (16), SM3 (256) |
| Number of SWCs | 2 through 128 |
| Non-volatile program flash sizes | 1 MB through 20 MB |
| Size of software clusters | Multiple of 16 KB.Max size = Flash size/Number of software clusters |
| Type of Memory | Amount of Memory Used | Description |
|---|---|---|
| Non-volatile program flash | 7 KB | MT-SOTA handler code |
| Non-volatile data flash | Memory USED (Max Nodes/Hash Output Size):16.5 KB (128/64) 8.5 KB (128/32) 5.5 KB (128/20) 4.5 KB (128/16) 6.3 KB (64/64) 4.2 KB (64/32) 3.5 KB (64/20) 3.2 KB (64/16) | Merkle tree contents (64 or 128 as max number of stored nodes). The larger the hash output size is, the more memory is needed. |
| RAM (data) | 100 bytes + copy of Dflash Merkle tree contents | MT-SOTA handler-related variables. The Merkle tree contents have to be copied to RAM when a new software update has to be performed, and then the updated RAM copy will be copied to Dflash once the software update is validated and completed. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bazzi, A.; Shaout, A.; Ma, D. MT-SOTA: A Merkle-Tree-Based Approach for Secure Software Updates over the Air in Automotive Systems. Appl. Sci. 2023, 13, 9397. https://doi.org/10.3390/app13169397
Bazzi A, Shaout A, Ma D. MT-SOTA: A Merkle-Tree-Based Approach for Secure Software Updates over the Air in Automotive Systems. Applied Sciences. 2023; 13(16):9397. https://doi.org/10.3390/app13169397
Chicago/Turabian StyleBazzi, Abir, Adnan Shaout, and Di Ma. 2023. "MT-SOTA: A Merkle-Tree-Based Approach for Secure Software Updates over the Air in Automotive Systems" Applied Sciences 13, no. 16: 9397. https://doi.org/10.3390/app13169397
APA StyleBazzi, A., Shaout, A., & Ma, D. (2023). MT-SOTA: A Merkle-Tree-Based Approach for Secure Software Updates over the Air in Automotive Systems. Applied Sciences, 13(16), 9397. https://doi.org/10.3390/app13169397







