Comparative Study of AI-Enabled DDoS Detection Technologies in SDN
Abstract
:1. Introduction
2. Research Background and Motivations
2.1. Background
2.2. Related Works and Research Motivations
3. Model Overview and Methodology
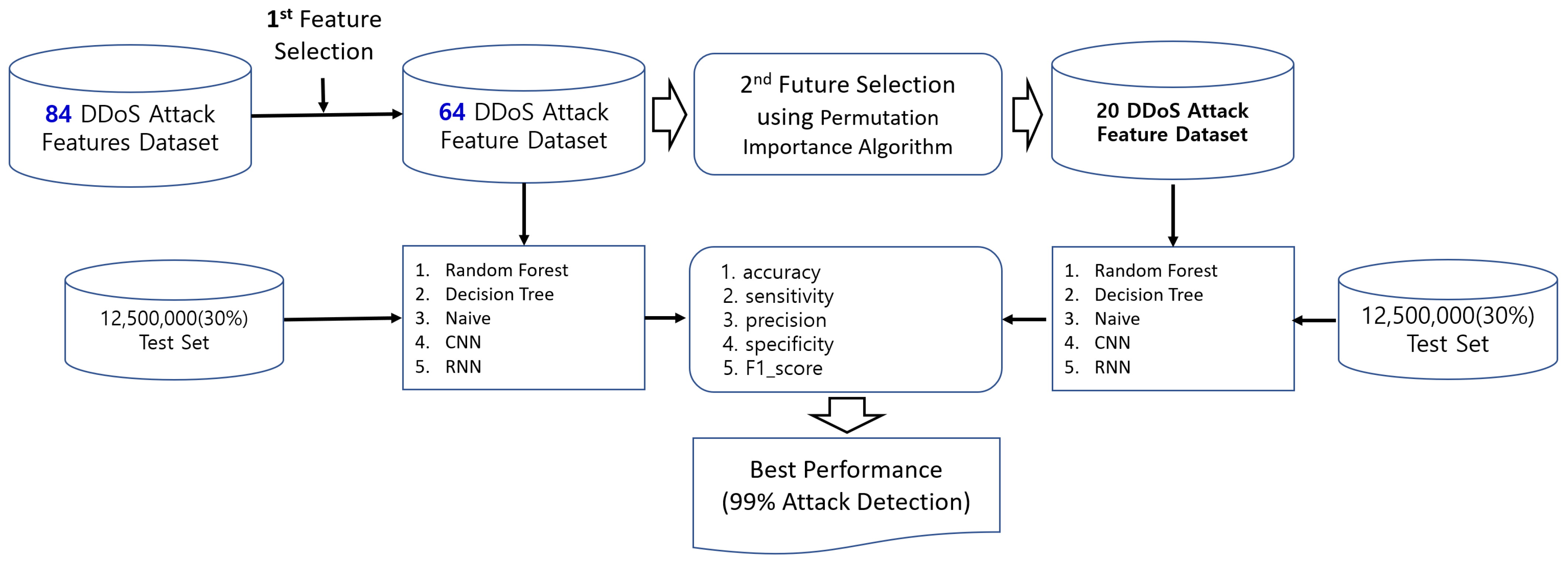
3.1. Model Overview
3.2. Experimental Dataset
3.3. Experimental Environment
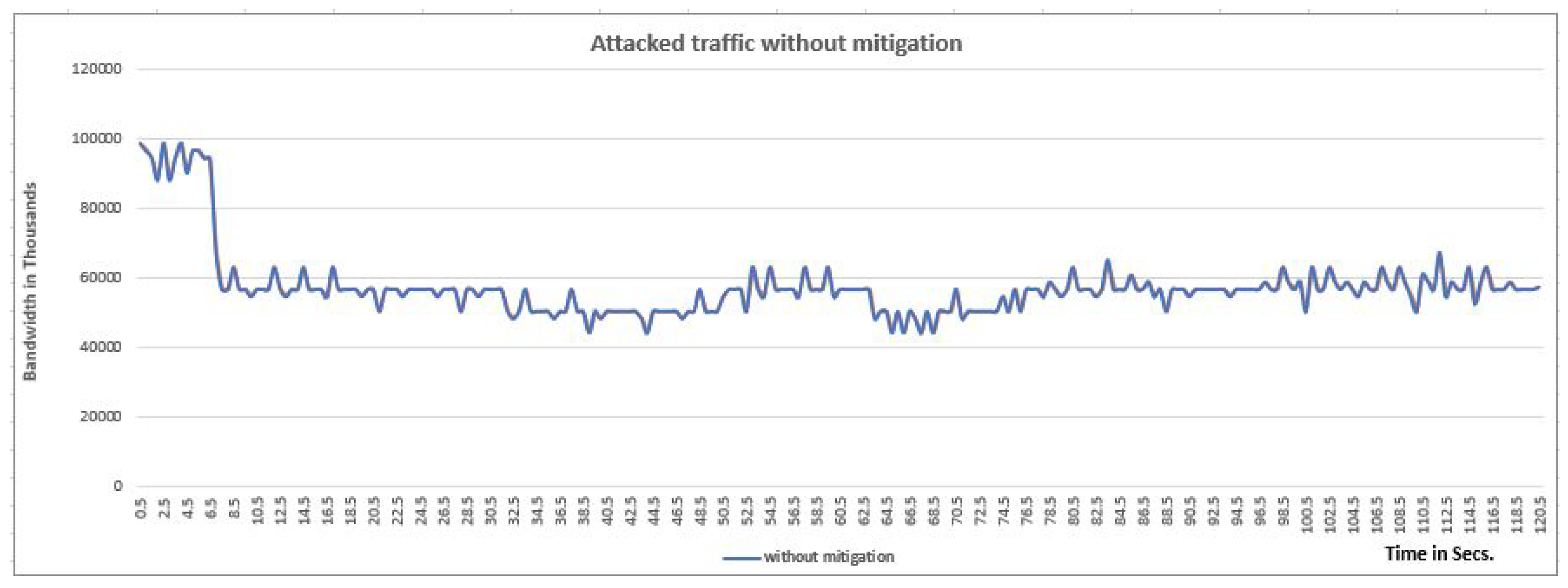
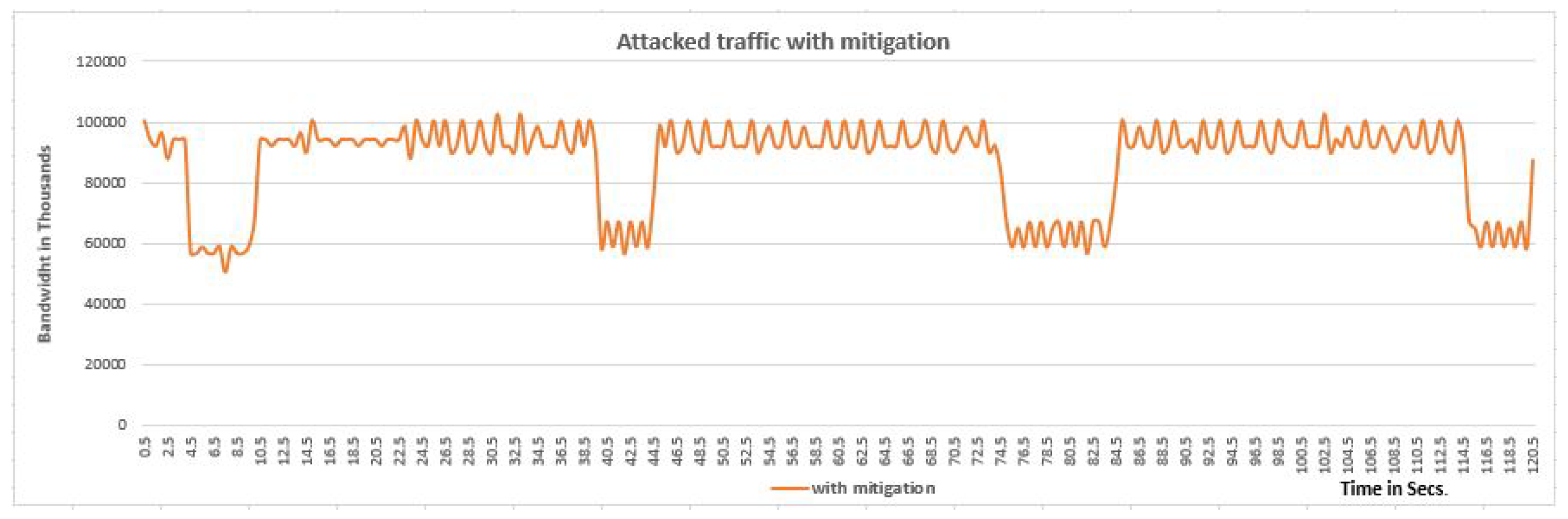
4. Experiment Analysis and Verification
Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ko, K.M. A DDoS Attack Detection Technique through CNN Model in Software Define Network. J. Korea Inst. Inf. Electron. Commun. Technol. 2020, 13, 605–610. [Google Scholar]
- Imran, M.; Durad, M.H.; Khan, F.A.; Derhab, A. Toward an optimal solution against denial of service attacks in software defined networks. Future Gener. Comput. Syst. 2019, 92, 444–453. [Google Scholar] [CrossRef]
- Rahman, O.; Quraishi, M.A.G.; Lung, C.H. DDoS attacks detection and mitigation in SDN using machine learning. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; Volume 2642, pp. 184–189. [Google Scholar]
- Tselios, C.; Politis, I.; Kotsopoulos, S. Enhancing SDN security for IoT-related deployments through blockchain. In Proceedings of the 2017 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Berlin, Germany, 6–8 November 2017; pp. 303–308. [Google Scholar]
- Tahaei, H.; Salleh, R.B.; Razak, M.F.A.; Ko, K.; Anuar, N.B. Cost Effective Network Flow Measurement for Software Defined Networks: A Distributed Controller Scenario. IEEE Access 2018, 6, 5182–5198. [Google Scholar] [CrossRef]
- Smith-Perrone, J.; Sims, J. Securing cloud, SDN and large data network environments from emerging DDoS attacks. In Proceedings of the 2017 7th International Conference on Cloud Computing, Data Science & Engineering-Confluence, Noida, India, 12–13 January 2017; pp. 466–469. [Google Scholar]
- Douligeris, C.; Mitrokotsa, A. DDoS attacks and defense mechanisms: A classification. In Proceedings of the 3rd IEEE International Symposium on Signal Processing and Information Technology (IEEE Cat. No. 03EX795), Darmstadt, Germany, 17 December 2003; pp. 190–193. [Google Scholar]
- Fonseca, P.; Bennesby, R.; Mota, E.; Passito, A. A replication component for resilient OpenFlow-based networking. In Proceedings of the 2012 IEEE Network Operations and Management Symposium, Maui, HI, USA, 16–20 April 2012; pp. 933–939. [Google Scholar]
- Wang, J.; Wang, L. SDN-Defend: A Lightweight Online Attack Detection and Mitigation System for DDoS Attacks in SDN. Sensors 2022, 22, 8287. [Google Scholar] [CrossRef] [PubMed]
- Manso, P.; Moura, J.; Serrão, C. SDN-Based Intrusion Detection System for Early Detection and Mitigation of DDoS Attacks. IEEE Access 2019, 10, 106. [Google Scholar] [CrossRef]
- Dharma, N.G.; Muthohar, M.F.; Prayuda, J.A.; Priagung, K.; Choi, D. Time-based DDoS detection and mitigation for SDN controller. In Proceedings of the 2015 17th Asia-Pacific Network Operations and Management Symposium (APNOMS), Busan, Republic of Korea, 19–21 August 2015; pp. 550–553. [Google Scholar]
- Oshima, S.; Nakashima, T.; Sueyoshi, T. Early DDoS detection method using short-term statistics. In Proceedings of the 2010 International Conference on Complex, Intelligent and Software Intensive Systems, Krakow, Poland, 15–18 February 2010; pp. 168–173. [Google Scholar]
- Zubaydi, H.D.; Anbar, M.; Wey, C.Y. Review on Detection Techniques against DDoS Attacks on a Software-Defined Networking Controller. In Proceedings of the IEEE 2017 Palestinian International Conference on Information and Communication Technology (PICICT), Gaza, Palestine, 8–9 May 2017; pp. 22–31. [Google Scholar]
- Wang, R.; Jia, Z.; Ju, L. An entropy-based distributed DDoS detection mechanism in software-defined networking. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 310–317. [Google Scholar]
- Ashraf, J.; Latif, S. Handling intrusion and DDoS attacks in Software Defined Networks using machine learning techniques. In Proceedings of the 2014 National Software Engineering Conference, Rawalpindi, Pakistan, 11–12 November 2014; pp. 55–60. [Google Scholar]
- Sultana, N.; Chilamkurti, N.; Peng, W.; Alhadad, R. Survey on SDN based network intrusion detection system using machine learning approaches. Peer-to-Peer Netw. Appl. 2019, 12, 493–501. [Google Scholar] [CrossRef]
- Braga, R.; Mota, E.; Passito, A. Lightweight DDoS flooding attack detection using NOX/OpenFlow. In Proceedings of the IEEE Local Computer Network Conference, Denver, CO, USA, 10–14 October 2010; pp. 408–415. [Google Scholar]
- Zhai, S.; Cheng, Y.; Lu, W.; Zhang, Z. Deep structured energy based models for anomaly detection. arXiv 2016, arXiv:1605.07717. [Google Scholar]
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M. Deep learning approach for network intrusion detection in software defined networking. In Proceedings of the 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 26–29 October 2016; pp. 258–263. [Google Scholar]
- Potluri, S.; Diedrich, C. Accelerated deep neural networks for enhanced intrusion detection system. In Proceedings of the 2016 IEEE 21st International Conference on Emerging Technologies and Factory Automation (ETFA), Berlin, Germany, 6–9 September 2016; pp. 1–8. [Google Scholar]
- Malaiya, R.K.; Kwon, D.; Kim, J.; Suh, S.C.; Kim, H.; Kim, I. An empirical evaluation of deep learning for network anomaly detection. In Proceedings of the 2018 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 893–898. [Google Scholar]
- Sambangi, S.; Gondi, L. A Machine Learning Approach for DDoS (Distributed Denial of Service) Attack Detection Using Multiple Linear Regression. Proceedings 2020, 63, 51. [Google Scholar]
- Awan, M.J.; Farooq, U.; Babar, H.M.A.; Yasin, A.; Nobanee, H.; Hussain, M.; Hakeem, O.; Zain, A.M. Real-Time DDoS Attack Detection System Using Big Data Approach. Sustainability 2021, 13, 10743. [Google Scholar] [CrossRef]
- Nakip, M.; Gelenbe, E. Mirai botnet attack detection with auto-associative dense random neural network. In Proceedings of the in IEEE Global Communications Conference, GLOBECOM, Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Nakip, M.; Gelenbe, E. Botnet attack detection with incremental online learning. In Proceedings of the 2018 IEEE International Conference on Current Trends in Advanced Computing (ICCTAC), Chennai, India, 10–11 September 2018; pp. 51–60. [Google Scholar]
- Onyema, E.M.; Kumar, M.A.; Balasubaramanian, S.; Bharany, S.; Rehman, A.U.; Eldin, E.T.; Shafiq, M. A Security Policy Protocol for Detection and Prevention of Internet Control Message Protocol Attacks in Software Defined Networks. Sustainability 2022, 14, 11950. [Google Scholar] [CrossRef]
- Polat, H.; Polat, O.; Cetin, A. Detecting DDoS Attacks in Software-Defined Networks Through Feature Selection Methods and Machine Learning Models. Sustainability 2020, 12, 1035. [Google Scholar] [CrossRef]
- Tuan, T.A.; Long, H.V.; Son, L.H.; Kumar, R.; Priyadarshini, I.; Son, N.T.K. Performance evaluation of botnet ddos attack detection using machine learning. In Proceedings of the 2018 IEEE International Conference on Current Trends in Advanced Computing (ICCTAC), Evolutionary Intelligence, Xiamen, China, 29 March 2018; pp. 1–12. [Google Scholar]
- Khashab, F.; Moubarak, J.; Feghali, A.; Bassil, C. DDoS attack detection and mitigation in SDN using machine learning. In Proceedings of the 2021 IEEE 7th International Conference on Network Softwarization (NetSoft), Tokyo, Japan, 28 June–2 July 2021. [Google Scholar]
- Sanjeetha, R.; Kanavalli, A.; Gupta, A.; Pattanaik, A.; Agarwal, S. Real-time DDoS Detection and Mitigation in Software Defined Networks using Machine Learning Techniques. Int. J. Comput. 2022, 21, 353–359. [Google Scholar]
- Alkahtani, H.; Aldhyani, T.H. Developing Cybersecurity Systems Based on Machine Learning and Deep Learning Algorithms for Protecting Food Security Systems: Industrial Control Systems. Electronics 2022, 11, 1717. [Google Scholar] [CrossRef]
- Theyazn, H.H.; Aldhyani, H.A. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22, 360. [Google Scholar]
- Devendra. DDoS Dataset- Kaggle. Available online: https://www.kaggle.com/devendra416/ddos-datasets (accessed on 20 July 2020).
- Yeo, M.; Koo, Y.; Yoon, Y.; Hwang, T.; Ryu, J.; Song, J.; Park, C. Flow-based malware detection using convolutional neural network. In Proceedings of the IEEE 2018 International Conference on Information Networking (ICOIN), Korean Society for Internet Information (KSII), Chiang Mai, Thailand, 10–12 January 2018; pp. 1–26. [Google Scholar]
- Team, M. Mininet Overview- Mininet. 2018. Available online: http://mininet.org/overview/ (accessed on 15 July 2020).
- Chen, Y.S.; Tsai, Y.T. A Mobility Management Using Follow-Me Cloud-Cloudlet in Fog-Computing-Based RANs for Smart Cities. Sensors 2018, 18, 489. [Google Scholar] [CrossRef] [PubMed]
- Ryu, A. Component-Based Software-Defined Networking Framework; Nippon Telegraph and Telephone Corporation: Tokyo, Japan, 2013. [Google Scholar]
- Asadollahi, S.; Goswami, B.; Sameer, M. Ryu controller’s scalability experiment on software defined networks. In Proceedings of the 2018 IEEE International Conference on Current Trends in Advanced Computing (ICCTAC), Bangalore, India, 1–2 February 2018; pp. 1–5. [Google Scholar]





| Method | Advantages | Issues |
|---|---|---|
| Time-Based DDoS Detection | Contains a mitigation process by creating time patterns to prevent future attacks. Reduces controller processing rate because the flow collector handles this task. | Causes time delay because the processor adds more processing for non-valid packets. Requires additional implementation. |
| Entropy-Based DDoS Detection | Lightweight method. Detects DDoS attack at early stages. Flexible; can modify any parameter. | Additional overhead from window size. Unable to detect DDoS attacks on multiple hosts. No prevention technique. |
| Machine Learning-Based DDoS Detection | Introduces a high overhead reduction compared to other techniques.
| This technique is not implemented with normal switches. It requires additional implementation. |
| Deep Learning-Based DDoS Detection | It provides accurate information on anomalous behavior. It is able to evaluate big sets of data, with less time and CPU load. | Can be implemented on network system. Requires additional functionalities. |
| # | Feature | Importance | Description |
|---|---|---|---|
| 1 | fl_iat_avg | 0.5334 | Two flows average time |
| 2 | fw_iat_max | 0.3351 | Maximum time of two packets sent |
| 3 | fw_win_byt | 0.3248 | Number of bytes |
| 4 | fw_iat_tot | 0.3231 | Total time of two packets sent |
| 5 | fl_dur | 0.3162 | Time of duration |
| 6 | fl_iat_min | 0.2778 | Minimum time of two flows |
| 7 | bw_iat_min | 0.2655 | Minimum time of two packets sent |
| 8 | fl_iat_max | 0.2426 | Maximum time of two flows |
| 9 | fw_iat_avg | 0.2203 | Mean time of two packets sent |
| 10 | Bw_pkt_l_max | 0.2139 | Maximum size of packet |
| 11 | bw_iat_max | 0.2077 | Maximum time of two packets sent |
| 12 | bw_win_byt | 0.1944 | Number of bytes sent |
| 13 | bw_iat_tot | 0.1942 | Total time of two packets sent |
| 14 | fw_iat_min | 0.1520 | Minimum time of two packets sent |
| 15 | bw_iat_avg | 0.1513 | Mean time of two packets sent |
| 16 | idl_max | 0.1139 | Flow maximum time before becoming active |
| 17 | bw_seg_avg | 0.0926 | Average size observed |
| 18 | Bw_pkt_l_avg | 0.0922 | Packet average size |
| 19 | fw_pkt_l_avg | 0.0913 | Packet average size |
| 20 | pkt_size_avg | 0.0910 | Packet average size |
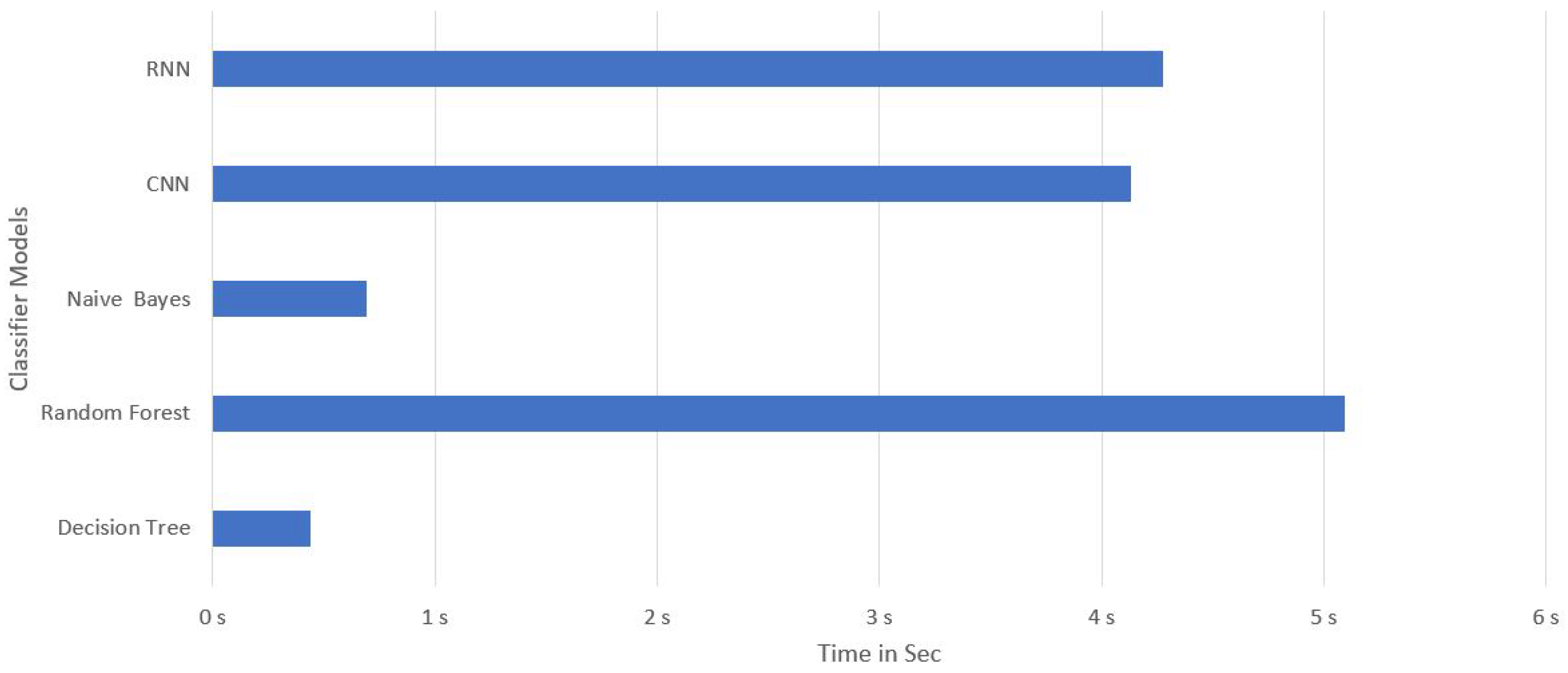
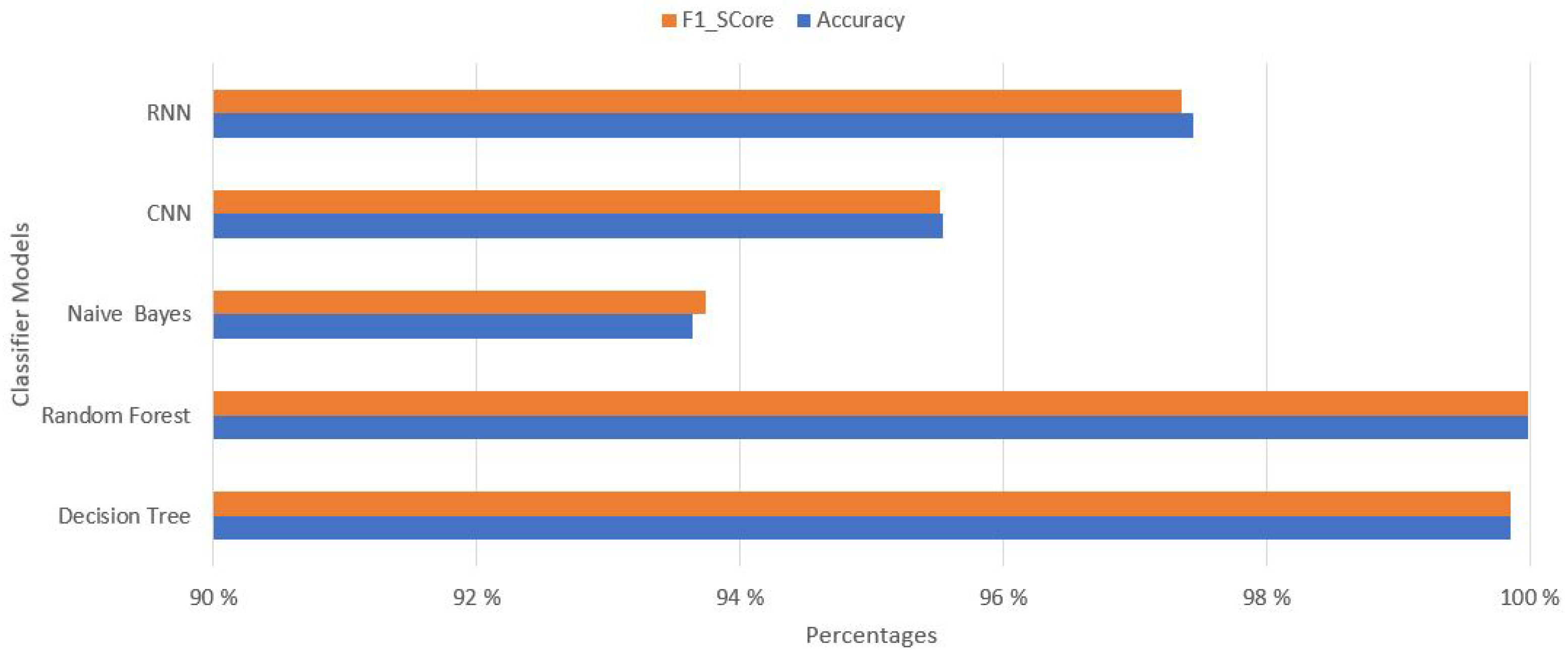
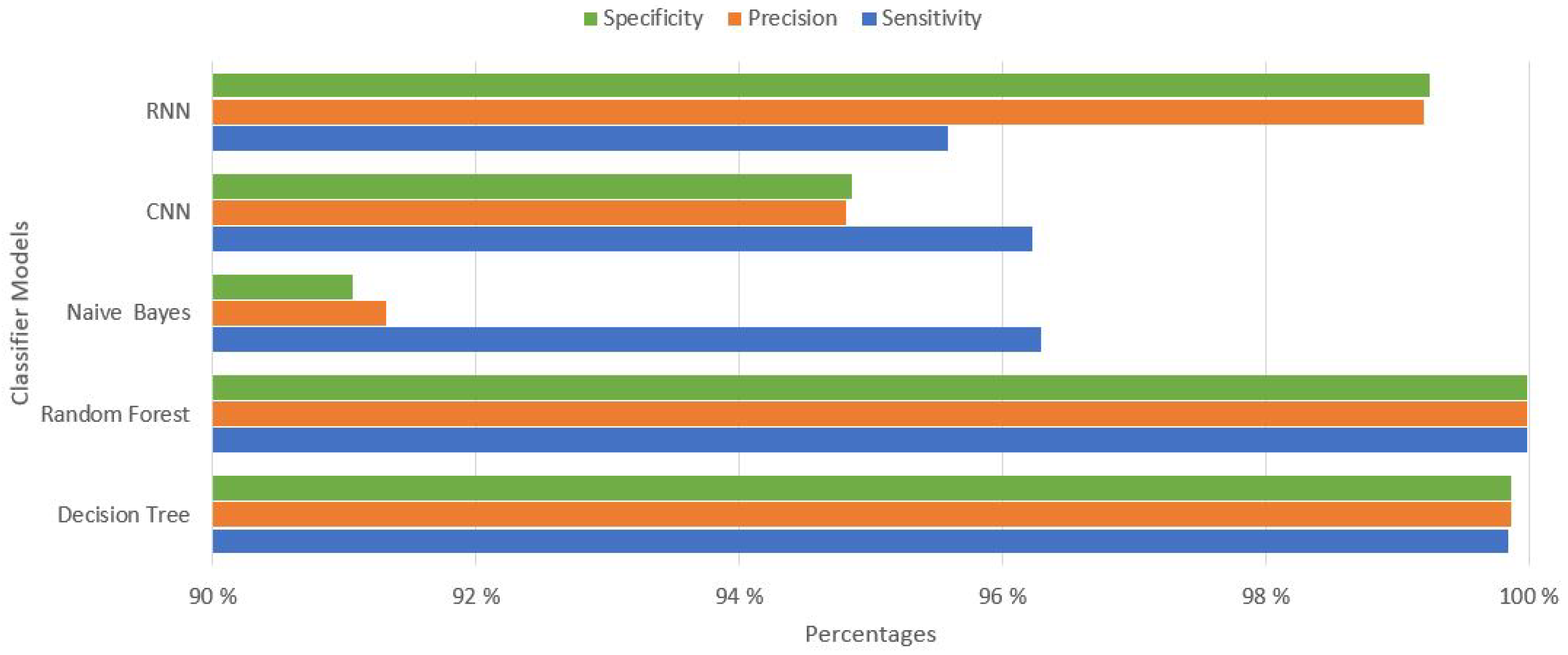
| Model | Features | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|---|
| Random Forest | 5 | 5.09 s | 99.976% | 99.974% | 99.978% | 99.978% | 99.976% |
| Decision Tree | 7 | 0.44 s | 99.842% | 99.829% | 99.852% | 99.856% | 99.840% |
| Naive Bayes | 8 | 0.69 s | 93.645% | 96.293% | 91.317% | 91.059% | 93.739% |
| CNN | 13 | 4.13 s | 96.654% | 94.412% | 98.760% | 98.843% | 96.537% |
| RNN | 15 | 4.28 s | 98.723% | 98.200% | 99.207% | 99.234% | 98.701% |
| Feature Set | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|
| 64 | 7.85 s | 99.979% | 99.978% | 99.980% | 99.980% | 99.979% |
| 12 | 5.66 s | 99.986% | 99.985% | 99.986% | 99.987% | 99.986% |
| 11 | 5.57 s | 99.986% | 99.985% | 91.986% | 99.987% | 99.986% |
| 10 | 5.07 s | 99.985% | 99.984% | 98.986% | 98.986% | 99.985% |
| 9 | 5.07 s | 99.978% | 99.977% | 99.978% | 99.979% | 99.978% |
| 8 | 4.88 s | 99.976% | 99.975% | 99.977% | 99.978% | 99.976% |
| 7 | 4.94 s | 99.976% | 99.975% | 99.977% | 99.978% | 99.976% |
| 6 | 5.09 s | 99.977% | 99.975% | 99.978% | 99.978% | 99.976% |
| 5 | 5.09 s | 99.976% | 99.974% | 99.978% | 99.978% | 99.976% |
| 4 | 4.59 s | 99.908% | 99.862% | 99.952% | 99.953% | 99.907% |
| Feature Set | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|
| 64 | 1.61 s | 99.984% | 99.982% | 99.985% | 99.985% | 99.984% |
| 12 | 0.49 s | 99.983% | 99.981% | 99.985% | 99.985% | 99.983% |
| 11 | 0.50 s | 99.853% | 99.841% | 99.862% | 99.865% | 99.852% |
| 10 | 0.49 s | 99.853% | 99.839% | 99.863% | 98.866% | 99.851% |
| 9 | 0.48 s | 99.842% | 99.829% | 99.852% | 99.855% | 99.841% |
| 8 | 0.47 s | 99.842% | 99.829% | 99.851% | 99.855% | 99.840% |
| 7 | 0.44 s | 99.842% | 99.829% | 99.852% | 99.856% | 99.840% |
| 6 | 0.38 s | 97.740% | 99.960% | 99.660% | 95.572% | 97.763% |
| Feature Set | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|
| 64 | 7.85 s | 99.979% | 99.978% | 99.980% | 99.980% | 99.979% |
| 12 | 0.89 s | 93.637% | 96.300% | 91.297% | 91.036% | 93.732% |
| 11 | 0.88 s | 93.645% | 96.293% | 91.317% | 91.059% | 93.739% |
| 10 | 0.82 s | 93.645% | 96.293% | 91.317% | 91.059% | 93.739% |
| 9 | 0.71 s | 93.645% | 96.293% | 91.317% | 91.059% | 93.739% |
| 8 | 0.69 s | 93.645% | 96.293% | 91.317% | 91.059% | 93.739% |
| 7 | 0.59 s | 92.108% | 93.124% | 91.100% | 91.117% | 92.101% |
| Feature Set | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|
| 64 | 5.67 s | 96.244% | 95.161% | 97.178% | 97.301% | 96.159% |
| 15 | 4.38 s | 95.450% | 95.266% | 95.513% | 95.630% | 95.389% |
| 14 | 4.26 s | 96.471% | 94.103% | 98.694% | 98.784% | 96.344% |
| 13 | 4.13 s | 96.654% | 94.412% | 98.760% | 98.843% | 96.537% |
| 12 | 4.10 s | 95.349% | 91.718% | 98.780% | 98.894% | 95.118% |
| 11 | 4.12 s | 96.184% | 93.226% | 98.841% | 98.971% | 95.951% |
| 10 | 4.17 s | 95.537% | 96.233% | 94.812% | 94.858% | 95.517% |
| 9 | 4.23 s | 89.137% | 86.972% | 90.661% | 91.251% | 88.778% |
| Feature Set | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|
| 64 | 2.09 s | 95.874% | 97.830% | 94.056% | 93.963% | 95.906% |
| 15 | 4.28 s | 98.723% | 98.200% | 99.207% | 99.234% | 98.701% |
| 14 | 3.78 s | 97.407% | 95.579% | 99.141% | 99.192% | 97.328% |
| 13 | 3.63 s | 97.449% | 95.611% | 99.197% | 99.244% | 97.371% |
| 12 | 3.38 s | 97.366% | 95.477% | 99.161% | 99.211% | 97.284% |
| 11 | 3.28 s | 97.454% | 95.601% | 99.218% | 99.264% | 97.376% |
| 10 | 3.07 s | 97.440% | 95.589% | 99.199% | 99.247% | 97.361% |
| 9 | 3.14 s | 97.061% | 94.672% | 99.348% | 99.394% | 96.954% |
| 8 | 3.27 s | 97.059% | 94.756% | 99.257% | 99.308% | 96.954% |
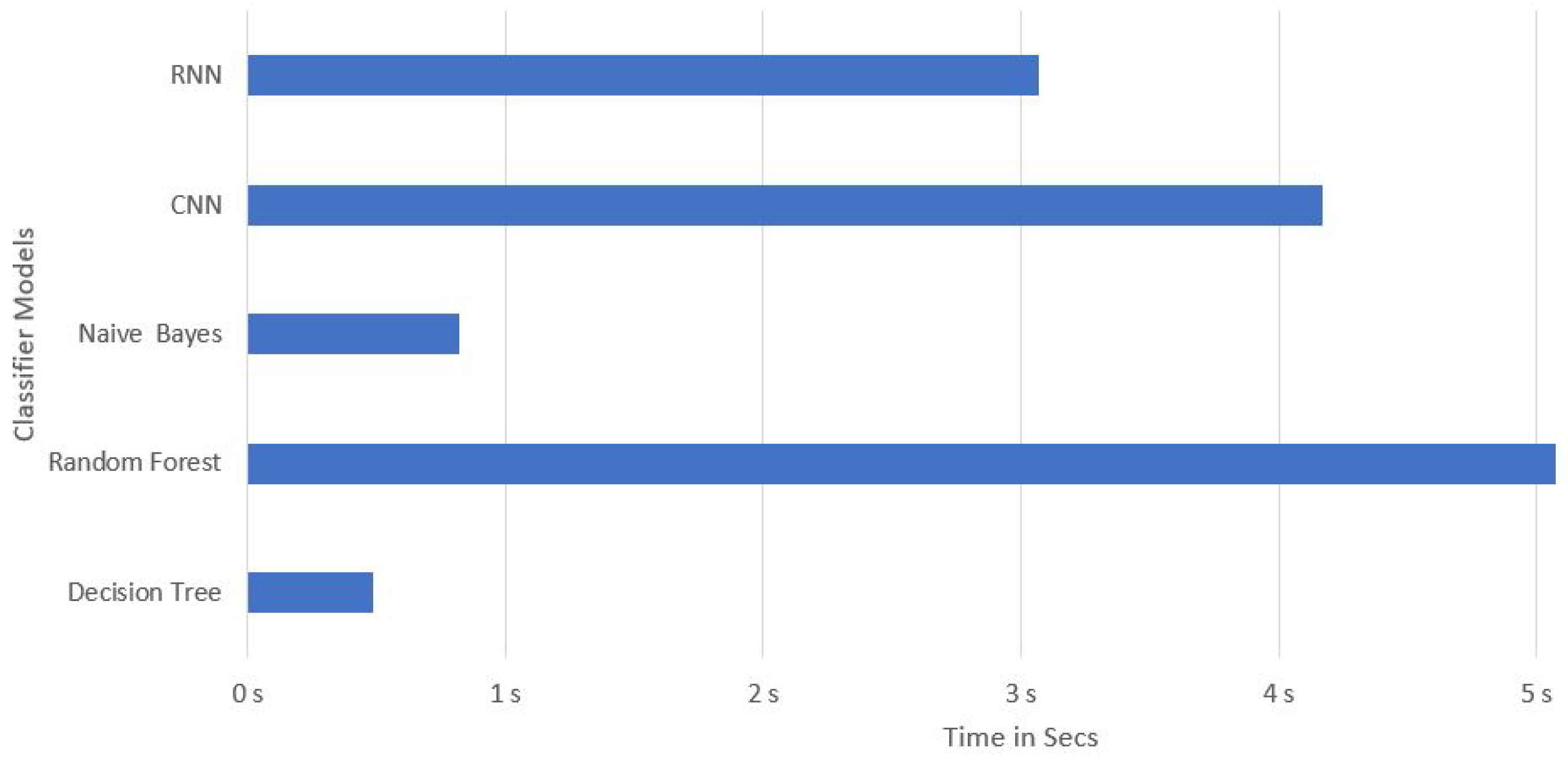
| Model | Features | Evaluation Time | Accuracy | Sensibility | Precision | Specificity | F1_Score |
|---|---|---|---|---|---|---|---|
| Random Forest | 10 | 0.49 s | 99.853% | 99.839% | 99.863% | 99.866% | 99.851% |
| Decision Tree | 10 | 5.07 s | 99.985% | 99.984% | 99.986% | 99.986% | 99.985% |
| Naive Bayes | 10 | 0.82 s | 93.645% | 96.293% | 91.317% | 91.059% | 93.739% |
| CNN | 10 | 4.17 s | 95.537% | 96.233% | 94.812% | 94.858% | 95.517% |
| RNN | 10 | 3.07 s | 97.440% | 95.589% | 99.199% | 99.247% | 97.361% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ko, K.-M.; Baek, J.-M.; Seo, B.-S.; Lee, W.-B. Comparative Study of AI-Enabled DDoS Detection Technologies in SDN. Appl. Sci. 2023, 13, 9488. https://doi.org/10.3390/app13179488
Ko K-M, Baek J-M, Seo B-S, Lee W-B. Comparative Study of AI-Enabled DDoS Detection Technologies in SDN. Applied Sciences. 2023; 13(17):9488. https://doi.org/10.3390/app13179488
Chicago/Turabian StyleKo, Kwang-Man, Jong-Min Baek, Byung-Suk Seo, and Wan-Bum Lee. 2023. "Comparative Study of AI-Enabled DDoS Detection Technologies in SDN" Applied Sciences 13, no. 17: 9488. https://doi.org/10.3390/app13179488
APA StyleKo, K.-M., Baek, J.-M., Seo, B.-S., & Lee, W.-B. (2023). Comparative Study of AI-Enabled DDoS Detection Technologies in SDN. Applied Sciences, 13(17), 9488. https://doi.org/10.3390/app13179488







