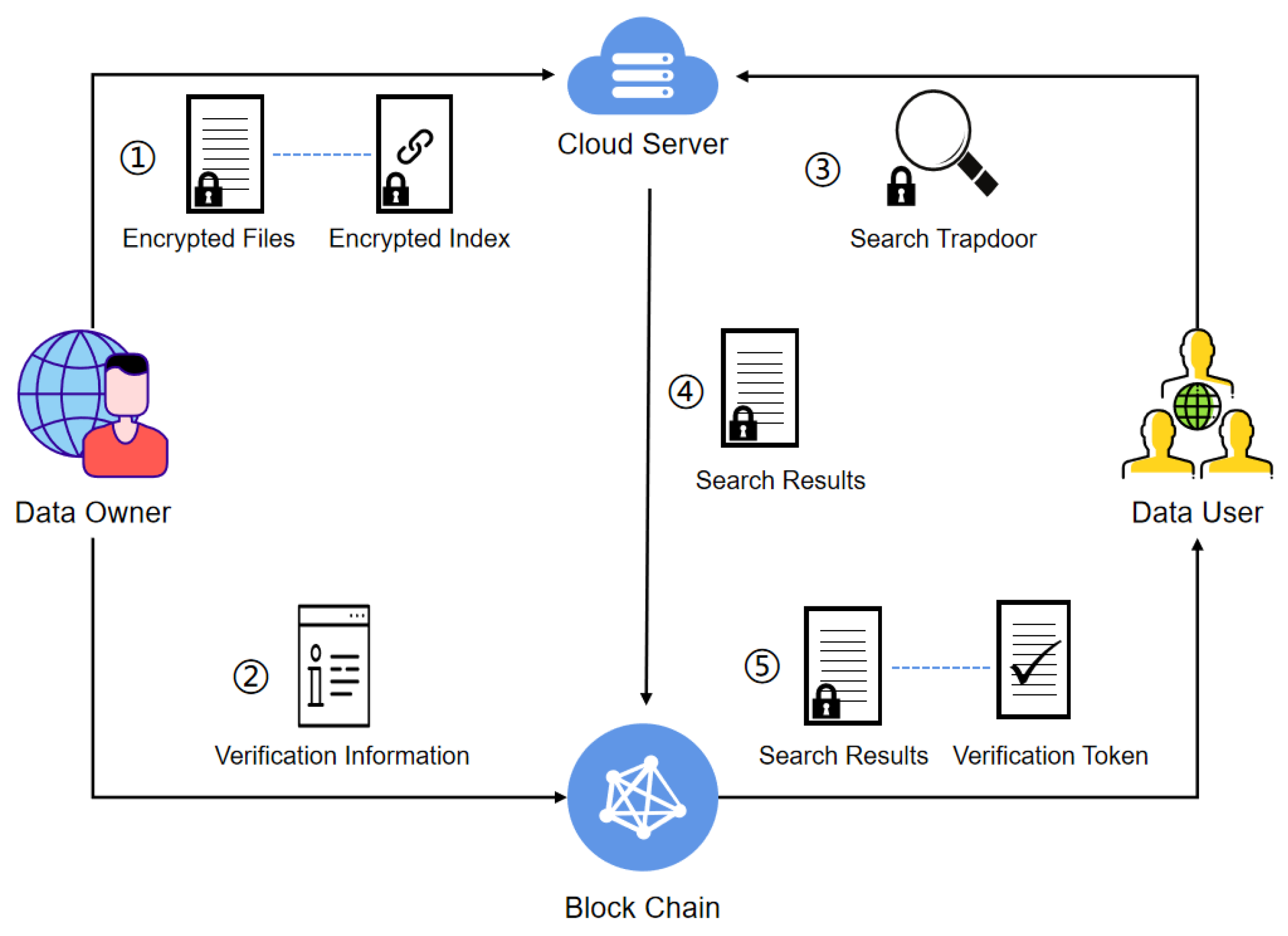
In this section, we present VSSE in detail, a verifiable dynamic searchable symmetric encryption scheme based on blockchain.
3.1. Detailed Construction
VSSE defines four protocols:
Setup,
Update,
Search, and
Verify. We first describe the symbols and functions that may be involved in each protocol.
is a security parameter to generate secret keys. The value of
m represents the maximum capacity of the database and also indicates the maximum length of the bitmap index, and
,
are both hash function used to generate keyword state locations and encrypted entries, respectively. Algorithms 1–4 summarize
Setup,
Update,
Search, and
Verify protocols of VSSE, respectively. Specifically, the structure of state chains is shown in
Figure 3, while Setup, Update, and Search protocols are detailed below.
| Algorithm 1 VSSE.Setup. |
| : The security parameter . |
| : The security key and empty maps , Σ and . |
|
| 1: |
| 2: |
|
| 3: |
| : |
| 4: Σ, Tag |
Setup. In the this protocol, generates the secret key , and an empty maps, . The key and are secreted by a -bits random string that are used to encrypt keywords and users. The map is employed to maintain the most recent state of each keyword, organized as a dynamic list with two columns. Keywords and their latest states are sequentially arranged in the two columns of . maintains two empty map and . is a dynamic list with two columns to construct secure index, where the first column is used to store the location of update and the second column corresponds to the updated file identifiers. is used to map the information about the user. It consist of two columns: the user’s identifier and user’s file access authority are located in the two columns of in order. also maintains two empty maps, Σ and . Σ is employed to store the user’s identifier and the corresponding file identifier for a specific keyword. is a dynamic list to store verification tag in the form of two columns. The user’s identifiers and keywords are located in the first column of , and the MAC values corresponding to search results are in the second column.
Update. When updating (adds or deletes) a file with identifier
that contains keyword
w,
initiates the process by initially retrieving the previous state
associated with the keyword
w from
. Subsequently, a new state
is generated at random.
is also updated accordingly. Next,
computes
and
separately.
represents the location of encrypted index entry
e on the server, and
is used to compute the encrypted index entry
e. As the state is generated randomly, each observed state by the server during an update appears as if it has been drawn randomly. Consequently, the server remains incapable of deducing the subsequent state based on the current search token. This imparts a guarantee of forward privacy.
also needs to encrypt the authorized user’s identifiers
to facilitate the storage of corresponding information on the server and the blockchain. Finally,
sends
to the server, which then stores the encrypted entries and associated file identifiers. Meanwhile,
sends
to the blockchain to complete the result verification process, and the blockchain updates and stores the accessible files for the user along with their corresponding message authentication codes.
| Algorithm 2 VSSE.Update. |
| : The security key , the file identifier , the keyword w and user . |
| : The latest state , the index location , the index information . |
| : |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
|
| 15: |
| 16: |
| 17: |
| 18: |
| : |
| 19: |
| 20: |
| 21: |
| 22: |
Search. When searching for the files containing keyword
w,
encrypts keyword
w by using
and a pseudorandom function
F, and retrieves the current state from
. Then,
sends
to
.
uses the
to obtain the location of current state
and retrieves the corresponding encrypted entry
from
. By decrypting the encrypted entry,
obtains the file identifier
associated with the current state
and the previous state
. Finally, after
c iterations,
XORs each bitmap
to obtain the final result
, which includes all the results involving the keyword
w. For different
, the server retrieves the files that the current
is authorized to access from
by the user’s identifier. After completing the search for files containing
w,
must determine whether the user has permission to access these files, i.e., it performs an AND operation between
and
. The final result
is not directly returned to the
but is sent by the server to the blockchain for further verification.
| Algorithm 3 VSSE.Search. |
| : The security key , the keyword w and user . |
| : The search result . |
| : |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| Algorithm 4 VSSE.Verify. |
| : The encrypted keyword , the encrypted user and search result . |
| : The search result and the verify information . |
| : |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| 8: |
Verify. In this protocol, the blockchain utilizes a verification contract to validate the correctness of search results. The verification contract constructs a key-value pair list in the form of (addr, val), where the first column contains user and keyword information used to locate a specific entry, and the second column stores the MAC for the corresponding result. Upon receiving encrypted keywords , encrypted user identifiers , and search results from the server, the verification contract retrieves the MAC value for the corresponding result by using and as indices in the . Then, the verification contract computes the corresponding MAC value based on the search result and compares with . If they match, the verification token is set to 1, indicating that the search result is correct; otherwise, the verification token is set to 0. Finally, the blockchain sends the verification token along with the search result to , which employs to ascertain the correctness of the search outcome.
To illustrate the verification process of the scheme on the blockchain more intuitively, we provide an explanation using a simple example.
Figure 4 depicts the verification process when the cloud server sends the keyword
, user identifier information
, and the corresponding search result
to the blockchain. Upon receiving the aforementioned information, the blockchain employs the verification contract to extract the correct MAC value stored in the
list for the combination of
, i.e.
. Subsequently, the verification contract computes the MAC value
for the result
sent by the cloud server and compares it with the extracted
from the
. Since
is equal to
, the verification token
is set to 1. Finally, the blockchain returns the verification token
along with the search result
to the user.
3.2. Security Analysis
Forward privacy is a crucial security attribute that a DSSE scheme should possess, as it involves the update and search operations common to all DSSE schemes. Therefore, our security analysis primarily focuses on threats associated with the update and search operations. VSSE satisfies definition of forward security. Specifically, in VSSE, each state of the keyword is randomly generated, the value of each state is indistinguishable from a random value in the server’s view, and the server is incapable of deducing the forthcoming state using the present state of the keyword. As a result, the forward privacy of VSSE remains ensured.
The theorem regarding the security of VSSE is as follows.
Theorem 1. Assume that F is a secure pseudorandom function, and and are hash functions in random oracle model. The leakage functions are denoted as and , where and are used to capture the leakage during the update and search, is the access pattern, and is the search pattern. Then VSSE is an -adaptively secure SSE scheme with forward privacy.
Proof of Theorem 1. The security of VSSE is proven through a sequence of games involving the real game and the ideal game . By demonstrating the indistinguishability between two adjacent games, we establish the equivalence between the real and ideal games.
Game :
is
game.
Game : In , instead of using a pseudo-random function F to generate , we randomly select and store it in the mapping . For the subsequent query on w, we can directly retrieve the corresponding from . Since we cannot distinguish between a F and a true random function, and are indistinguishable.
Game : no longer calls to generate location in the update protocol, but uses random numbers instead. Specifically, it involves using instead of and performing , where is a mapping held by . Then, is executed in the search protocol, where is the table of . It can be seen that is not updated in real time, so when the adversary accesses before the search query is issued, will randomly generate a value that is different from v. When the adversary accesses once more following the subsequent search, it will obtain the value v that has been updated into . By comparing the differences between the two access results, the adversary will know that it is in . However, the probability of such case occurring is negligible.
Based on the above, this case only happens when the adversary accesses
using
. Given that
is randomly generated, the likelihood of the adversary selecting
is
. Assuming a PPT adversary makes up to
guesses, the probability of this occurrence is
, which can be negligible. Therefore,
and
are indistinguishable.
Game : In the update protocol of
,
is processed in the same way as
in
. Since the likelihood of the adversary guessing
is
, and the probability after
polynomial queries by the adversary is
, it follows that
and
are indistinguishable.
Game : In , the value of is generated instantaneously during the search. Algorithm 5 shows the algorithmic changes on the . utilizes to record the update query that occurred after the last search, and extracts the number of updates and . randomly selects the query result of a random oracle without the information about . Subsequently, is generated and used to update the random oracle during the execution of the search operation. From the adversary’s perspective, since and output two random strings during the update phase and both output during the search, and are completely indistinguishable.
Simulator: In the ideal game
, the simulator
constructs a view by utilizing the leakage function. Algorithm 6 details
, which maintains two mappings and an update counter. The values of each mapping are also randomly generated during the update. Unlike
,
uses
to represent the first time to search keywords
w and uses the update history
as input to parse the number of keyword updates and update requests, rather than computing based on
. Afterwards,
randomly generates
and updates the random oracle with the information above. The simulator and
are entirely equivalent.
| Algorithm 5 Game |
| Setup(λ) |
|
| 1: |
| 2: |
| Update(ks,W,w, bs; T) |
| : |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| Search(ks,W,w; T) |
| : |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| 15: |
| 16: |
| 17: |
| 18: |
| 19: |
| 20: |
| 21: |
| 22: |
| 23: |
| Algorithm 6 Simulator |
| Setup() |
| : |
| 1: |
| 2: |
| Update() |
|
| 3: |
| 4: |
| 5: |
| 6: |
| Search(sp(w), uh(w)) |
| : |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| 15: |
| 16: , |
| 17: |
| 18: |
| 19: |
| 20: |
| 21: |
| 22: |
□