An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities
Abstract
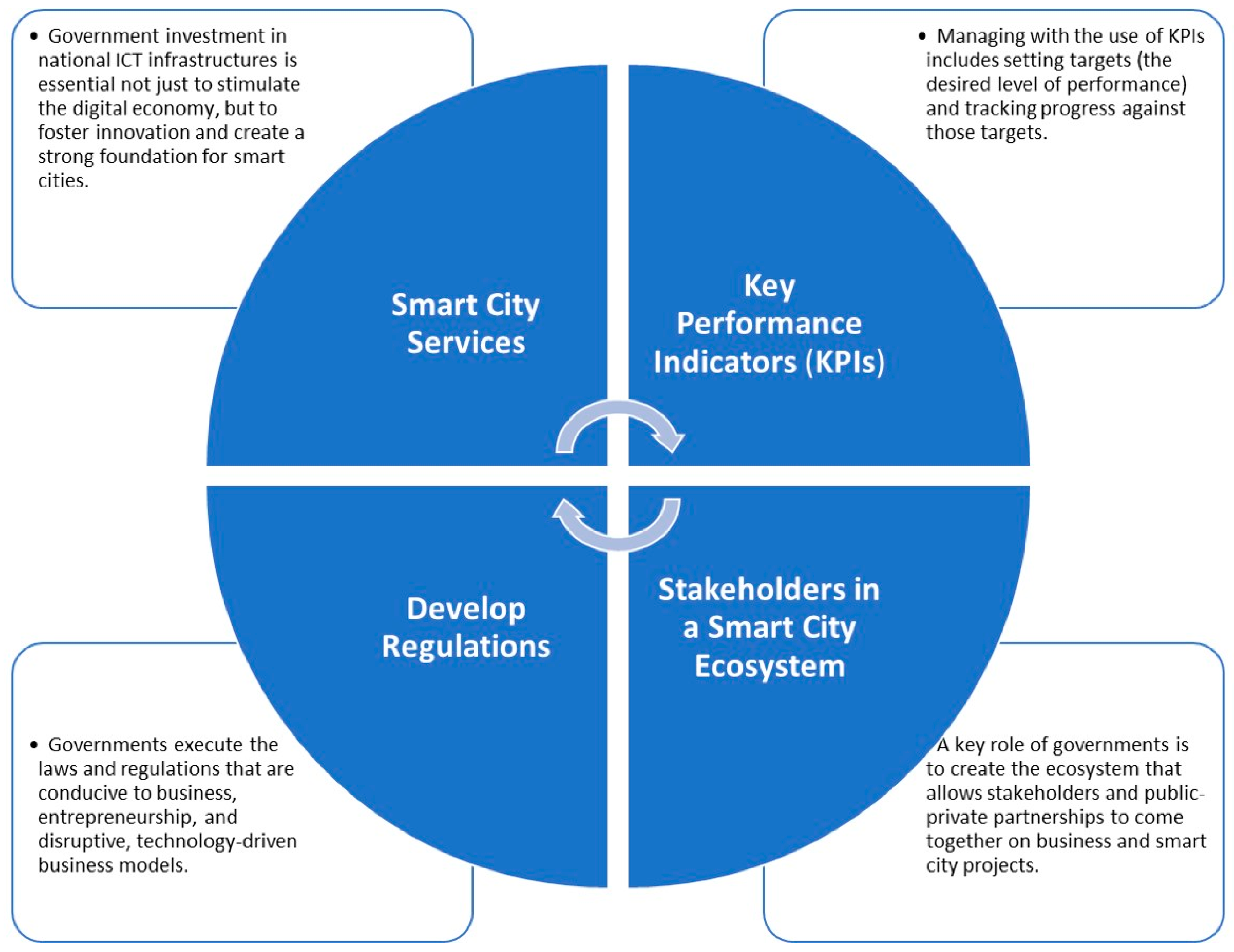
1. Introduction
- A large and complex attack surface: As cities become more intelligent, they will incorporate more systems and “systems of systems,” increasing the risk and impact of an attack and necessitating better control and visibility. Furthermore, the integration of vendor solutions increases the complexity of intelligent city systems, particularly during rapid technological transformations.
- Inadequate oversight and organization: Complex systems will necessitate more robust management and governance capabilities. Keeping leadership fully informed of complex occurrences will require additional resources and capabilities.
2. Literature Review
2.1. Smart Government
2.1.1. Cyber Threats or Attacks
- Permission hierarchy model. Upper-tier authorities need a multilevel governance solution to distribute and transfer authority and duties across various levels of government (top-down governance) [19].
- Keeping track of duties. Because of the variety of IoT systems and functions supplied in a smart city, the various authorities must administer a role-based access control system to allocate and monitor duties.
- Inclusion. An integrated strategy to accommodate heterogeneity within the same ICT-based solution is required to facilitate data interchange—third-party API (application programming interface) deployment, sharing credentials and permissions, and so forth.
- Support for new systems. A suitable solution that allows the integration of new IoT systems over time, independent of the technology on which they are based, is necessary for a dynamic smart municipal, integrating the latest IoT system into the ICT-based solution offered by the city authorities.
- Safety and privacy. It is critical to include security methods in the elements outlined above. For example, only authorized and authenticated users may manage permissions using well-tested and robust processes.
- COBIT—The Board of Standards Audit and Information Systems Control (ISACA) publishes the Control of Information and Related Technologies (COBIT), which offers a control framework for corporate governance and IT governance.
- ISO/IEC 15408—These assessment criteria were established and are aligned with the national security standards.
- ITIL (or ISO/IEC 20000 series)—This publication presents a collection of best practices in IT services management (ITSM), focusing on the IT service process and emphasizing the user’s important role.
- The ISO/IEC 27001—This certificate is often the most basic information technology standard and determines which other security standards must also comply by a government organization. For example, if a governance domain offers payment services, it must meet, if not exceed, the Payment Card Industry Data Security Standard (PCI DSS).
2.1.2. Countermeasures
2.2. Smart Mobility
2.2.1. Cyber Threats or Attacks
- All congestion, interference, and distributed denial-of-service (DDOS) assaults are eliminated.
- The size of the buffers in D-switches is cut in half.
- Delays in end-to-end IoT communications are brought down significantly.
- The D-switches do not require gigabytes of memory to store large IP routing tables.
- Hardware support is provided in layer 3 for the US NIST Zero Trust Architecture.
- Packets within a DVPN can be entirely encrypted using quantum-safe encryption, which is resistant to attacks by quantum computers using existing quantum algorithms.
- The likelihood of an undiscovered cyberattack against a DVPN may be arbitrarily tiny using lengthy quantum-safe encryption keys.
- Savings can approach thousands of dollars annually via decreased capital, energy, and operating expenses.
2.2.2. Countermeasures
2.3. Smart Environment
2.3.1. Cyber Threats or Attacks
2.3.2. Countermeasures
2.4. Smart Lining
- Detectors of fire: It is feasible to monitor, detect, and prevent fires in the urban environment with this 24/7 program. Furthermore, the detection may approach the various sources of fire efficiently to manage the fire more effectively.
- Intelligent video surveillance: to improve public safety and to use predictive analytics to optimize traffic flow and citizen safety.
- Sports facility management: Smart living solutions include controlling capacity and performing centralized administration of sports facilities. It is also beneficial for making judgments based on historical data, identifying deficiencies or requirements, and implementing management and infrastructure upgrades.
- Smart home automation: It monitors and regulates home smart applications such as temperature, humidity, electric equipment, security, and so on in real-time.
2.4.1. Cyber Threats or Attacks
2.4.2. Countermeasures
2.5. Smart Healthcare
2.5.1. Cyber Threats or Attacks
2.5.2. Countermeasures
2.6. Smart Economy
- JakPreneur: Jakarta’s MSME development initiative encourages the creation and collaboration of an entrepreneurial ecosystem. MSME actors will receive training, coaching, marketing, and even instruction on obtaining funding via JakPreneur.
- JakPangan: provides information on the cost of Jakarta’s primary commodities.
- JakNaker Platform: a portal designed to make it simpler for citizens to find jobs.
- JakOne Pay: a non-cash payment option developed in partnership with banks [9].
- JakLingko Card: The JakLingko card may pay for many kinds of transportation (buses, microbuses, railways, etc.).
- Managing system complexity: With so many moving parts and components, the decentralized marketplace system may become fragmented or difficult to scale; how can this be avoided? Maintaining a tight foundation may hinder scalability.
- Economic incentives and centralization: Without sufficient financial incentives for all parties involved, the decentralized marketplace may fail to operate successfully. It may be required to carefully construct the incentives so that additional decision-making power and data do not get concentrated in the hands of specific parties, thereby distorting rankings and recommendations in unjust ways.
- User-friendly interfaces and decentralized applications (apps) that make it simple to publish, browse, search, review, suggest, curate, verify, and data items, vendors, and customers will be required for a successful marketplace. People and organizations should be sufficiently incentivized to build and supply functional and user-friendly apps while keeping them decentralized.
2.6.1. Cyber Threats or Attacks
2.6.2. Countermeasures
2.7. Smart People
2.7.1. Cyber Threats or Attacks
2.7.2. Countermeasures
- Principles might contradict one another, deflecting the issue into a purely speculative sphere.
- If a higher-level principle is presented and contradicts another, a higher-higher-level regulation is required to enter an endless regress.
3. Recommendations
- Syncing smart city and cyber strategy. Cities should develop a detailed cybersecurity strategy consistent with their overall smart city strategy and can mitigate issues coming from the continuous convergence, interoperability, and interconnection of city technologies. Additionally, they should consider undertaking a thorough impact assessment of their data, procedures, and cyber assets to identify, assess, and reduce the risks associated with technical processes, policies, and solutions. Cities may build a comprehensive cybersecurity strategy with an integrated perspective of the risks and awareness of the interdependencies of important assets.
- Formalizing cyber and data governance. Cities must codify their approach to data governance, assets, infrastructure, and other technological components. Each important part of the smart city ecosystem should have its responsibilities and tasks, which should be defined in a comprehensive governance model. Multiple entities must collaborate to apply an ecosystem approach to cyber challenges, with a robust governance model serving as the foundation. Cities can collaborate with other cities, state agencies, academics, and enterprises to exchange threat information, capabilities, and contracts to bolster cyber defenses. Furthermore, data management, which includes rigorous data sharing and privacy policies, data analytics skills, and monetization models that allow the sourcing and use of “city data,” is an important part of this governance. Policies, regulations, and technology must be constantly coordinated to strike the proper balance of protection, privacy, transparency, and utility. The city’s comprehensive cyber strategy requires the maturation of the government, rules, and processes.
- Build strategic partnerships to grow cyber capabilities [147]. Because the cyber skills gap is not going away anytime soon, cities must be inventive and proactive in filling it in their communities. Smart cities necessitate the development of new skills and competencies across all ecosystem tiers. Strategic collaborations and contracts with service providers can help cities supplement their existing skills. His strategy may necessitate the local administration exploring unorthodox methods of attracting cyber expertise, such as crowdsourcing, rewards, and challenges to address cyber-related concerns.
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sánchez-Corcuera, R.; Nuñez-Marcos, A.; Sesma-Solance, J.; Bilbao-Jayo, A.; Mulero, R.; Zulaika, U.; Azkune, G.; Almeida, A. Smart cities survey: Technologies, application domains and challenges for the cities of the future. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719853984. [Google Scholar] [CrossRef]
- Win, L.L.; Tonyali, S. Security and privacy challenges, solutions, and open issues in smart metering: A review. In Proceedings of the 2021 6th International Conference on Computer Science and Engineering (UBMK), Ankara, Turkey, 15–17 September 2021; pp. 800–805. [Google Scholar] [CrossRef]
- Hamid, B.; Jhanjhi, N.; Humayun, M.; Khan, A.; Alsayat, A. Cyber security issues and challenges for smart cities: A survey. In Proceedings of the 2019 13th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics, Karachi, Pakistan, 14–15 December 2019. [Google Scholar] [CrossRef]
- Sedinić, I.; Lovrić, Z. Influence of established information security governance and infrastructure on future security certifications. In Proceedings of the 2013 36th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 20–24 May 2013; pp. 1111–1115. [Google Scholar]
- Alromaihi, S.; Elmedany, W.; Balakrishna, C. Cyber security challenges of deploying IoT in smart cities for healthcare applications. In Proceedings of the 2018 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Barcelona, Spain, 6–8 August 2018; pp. 140–145. [Google Scholar] [CrossRef]
- Bekkanti, A.; Aishwarya, R.; Suganya, Y.; Valarmathi, P.; Ganesan, S.; Basha, C.Z. Novel approach of internet of things (IoT) based smart ambulance system for patient’s health monitoring. In Proceedings of the 2021 2nd International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 7–9 October 2021; pp. 29–34. [Google Scholar] [CrossRef]
- Ganguly, P.; Nasipuri, M.; Dutta, S. Challenges of the existing security measures deployed in the smart grid framework. In Proceedings of the 2019 IEEE 7th International Conference on Smart Energy Grid Engineering (SEGE), Oshawa, ON, Canada, 12–14 August 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Giffinger, R.; Gudrun, H. Smart cities ranking: An effective instrument for the positioning of the cities? ACE Archit. City Environ. 2010, 4, 7–26. [Google Scholar] [CrossRef]
- Kartika, H.; Fatimah, Y.A.; Supangkat, S.H. Secure cashless payment governance in indonesia: A systematic literature review. In Proceedings of the 2018 International Conference on ICT for Smart Society (ICISS), Semarang, Indonesia, 10–11 August 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Lopes, N.V. Tutorial: Smart governance for Smart cities. In Proceedings of the 2018 International Conference on ICT for Smart Society (ICISS), Semerang, Indonesia, 10–11 October 2018; pp. 1–2. [Google Scholar] [CrossRef]
- Lopes, N.V. Smart governance: A key factor for smart cities implementation. In Proceedings of the 2017 IEEE International Conference on Smart Grid and Smart Cities (ICSGSC), Singapore, 23–26 July 2017; pp. 277–282. [Google Scholar] [CrossRef]
- Bai, Y.; Hu, Q.; Seo, S.-H.; Kang, K.; Lee, J.J. Public Participation Consortium Blockchain for Smart City Governance. IEEE Internet Things J. 2021, 9, 2094–2108. [Google Scholar] [CrossRef]
- Alotaibi, S.S. Registration Center Based User Authentication Scheme for Smart E-Governance Applications in Smart Cities. IEEE Access 2018, 7, 5819–5833. [Google Scholar] [CrossRef]
- Roy, A. Smart delivery of multifaceted services through connected governance. In Proceedings of the 2019 3rd International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 27–29 March 2019; pp. 476–482. [Google Scholar] [CrossRef]
- Ruiz-Zafra, A.; Pigueiras, J.; Millan-Alcaide, A.; Larios, V.M.; Maciel, R. A digital object-based infrastructure for smart governance of heterogeneous internet of things systems. In Proceedings of the 2020 IEEE International Smart Cities Conference (ISC2), Piscataway, NJ, USA, 28 September–1 October 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Cho, Y.; Oh, J.; Kwon, D.; Son, S.; Yu, S.; Park, Y.; Park, Y. A Secure Three-Factor Authentication Protocol for E-Governance System Based on Multiserver Environments. IEEE Access 2022, 10, 74351–74365. [Google Scholar] [CrossRef]
- Guo, Y.; Tang, Z.; Li, P.; Peng, H. The research on the connotation characteristics and policy analysis of smart urban agglomeration under holistic governance. In Proceedings of the 2021 International Conference on Big Data and Intelligent Decision Making (BDIDM), Guilin, China, 23–25 July 2021; pp. 96–99. [Google Scholar] [CrossRef]
- Javed, A.; Kubler, S.; Malhi, A.; Nurminen, A.; Robert, J.; Framling, K. bIoTope: Building an IoT Open Innovation Ecosystem for Smart Cities. IEEE Access 2020, 8, 224318–224342. [Google Scholar] [CrossRef]
- Cirillo, F.; Gomez, D.; Diez, L.; Maestro, I.E.; Gilbert, T.B.J.; Akhavan, R. Smart City IoT Services Creation Through Large-Scale Collaboration. IEEE Internet Things J. 2020, 7, 5267–5275. [Google Scholar] [CrossRef]
- Bartolucci, S.; Fiorentino, S. Blockchain and smart contracts as new governance tools for the sharing economy. In Proceedings of the 2021 IEEE 18th International Conference on Software Architecture Companion (ICSA-C), Stattgart, Germany, 22–26 March 2021; pp. 118–119. [Google Scholar] [CrossRef]
- Razaghi, M.; Finger, M. Smart Governance for Smart Cities. Proc. IEEE 2018, 106, 680–689. [Google Scholar] [CrossRef]
- Gowthami, J.; Shanthi, N.; Krishnamoorthy, N. Secure three-factor remote user authentication for e-governance of smart cities. In Proceedings of the 2018 International Conference on Current Trends towards Converging Technologies (ICCTCT), Coimbatore, India, 1–3 March 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Sifah, E.B.; Xia, H.; Cobblah, C.N.A.; Xia, Q.; Gao, J.; Du, X. BEMPAS: A Decentralized Employee Performance Assessment System Based on Blockchain for Smart City Governance. IEEE Access 2020, 8, 99528–99539. [Google Scholar] [CrossRef]
- Tang, Z. Analysis of information security problems and countermeasures in big data management of colleges and universities under smart campus environment. In Proceedings of the 2021 2nd International Conference on Information Science and Education (ICISE-IE), Chongqing, China, 22–26 November 2021; pp. 912–915. [Google Scholar] [CrossRef]
- EL Majdoubi, D.; EL Bakkali, H.; Sadki, S. Towards smart blockchain-based system for privacy and security in a smart city environment. In Proceedings of the 2020 5th International Conference on Cloud Computing and Artificial Intelligence: Technologies and Applications (CloudTech), Marrakesh, Morocco, 24–26 November 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Guo, G.; Zhu, Y.; Yu, R.; Chu, W.C.-C.; Ma, D. A Privacy-Preserving Framework With Self-Governance and Permission Delegation in Online Social Networks. IEEE Access 2020, 8, 157116–157129. [Google Scholar] [CrossRef]
- Alamleh, H.; AlQahtani, A.A.S. Analysis of the design requirements for remote Internet-based E-voting systems. In Proceedings of the 2021 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 10–13 March 2021; pp. 386–390. [Google Scholar] [CrossRef]
- Khlaponin, Y.; Vyshniakov, V.; Prygara, M.; Poltorak, V. The new concept of guaranteeing confidence in the E-voting system. In Proceedings of the 2020 IEEE International Conference on Problems of Infocommunications. Science and Technology (PIC S&T), Kharkhiv, Ukraine, 6–9 October 2020; pp. 747–752. [Google Scholar] [CrossRef]
- Mahrez, Z.; Sabir, E.; Badidi, E.; Saad, W.; Sadik, M. Smart Urban Mobility: When Mobility Systems Meet Smart Data. IEEE Trans. Intell. Transp. Syst. 2021, 23, 6222–6239. [Google Scholar] [CrossRef]
- Al-Rahamneh, A.; Astrain, J.J.; Villadangos, J.; Klaina, H.; Guembe, I.P.; Lopez-Iturri, P.; Falcone, F. Bi2Bi Communication: Toward Encouragement of Sustainable Smart Mobility. IEEE Access 2022, 10, 9380–9394. [Google Scholar] [CrossRef]
- Butler, L.; Yigitcanlar, T.; Paz, A. Smart Urban Mobility Innovations: A Comprehensive Review and Evaluation. IEEE Access 2020, 8, 196034–196049. [Google Scholar] [CrossRef]
- Derawi, M.; Dalveren, Y.; Cheikh, F.A. Internet-of-things-based smart transportation systems for safer roads. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Vishal, D.; Afaque, H.S.; Bhardawaj, H.; Ramesh, T.K. IoT-driven road safety system. In Proceedings of the 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques (ICEECCOT), Mysuru, India, 15–16 December 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Taha, A.-E.M. An IoT Architecture for Assessing Road Safety in Smart Cities. Wirel. Commun. Mob. Comput. 2018, 2018, 1–11. [Google Scholar] [CrossRef]
- Brincat, A.A.; Pacifici, F.; Martinaglia, S.; Mazzola, F. The Internet of things for intelligent transportation systems in real smart cities scenarios. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 128–132. [Google Scholar] [CrossRef]
- Yongjun, Z.; Xueli, Z.; Shuxian, Z.; Shenghui, G. Intelligent transportation system based on Internet of Things. In Proceedings of the World Automation Congress, Puerto Vallarta, Mexico, 24–28 June 2012; pp. 1–3. [Google Scholar]
- Bojan, T.M.; Kumar, U.R.; Bojan, V.M. An internet of things based intelligent transportation system. In Proceedings of the 2014 IEEE International Conference on Vehicular Electronics and Safety, Hyderabad, India, 16–17 December 2014; pp. 174–179. [Google Scholar] [CrossRef]
- Sherly, J.; Somasundareswari, D. Internet of things based smart transportation systems. Int. Res. J. Eng. Technol. 2015, 2, 1207–1210. [Google Scholar]
- Herrera-Quintero, L.F.; Banse, K.; Vega-Alfonso, J.C.; Jalil-Nasser, W.D.; Bedoya, O.E.H. IoT approach applied in the context of ITS: Monitoring highways through instant messaging. In Proceedings of the 14th International Conference on ITS Telecommunications (ITST), Copenhagen, Denmark, 2–4 December 2015; pp. 27–31. [Google Scholar] [CrossRef]
- Savithramma, R.M.; Ashwini, B.P.; Sumathi, R. Smart Mobility Implementation in Smart Cities: A Comprehensive Review on State-of-art Technologies. In Proceedings of the 2022 4th International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 20–22 January 2022; pp. 10–17. [Google Scholar] [CrossRef]
- Semanjski, I.; Mandzuka, S.; Gautama, S. Smart Mobility. In Proceedings of the 2018 International Symposium ELMAR, Zadar, Croatia, 16–19 September 2018. [Google Scholar] [CrossRef]
- Kumar, B.; AbuAlhaija, M.; Alqasmi, L.; Dhakhri, M. Smart cities: A new age of digital insecurity. In Proceedings of the 2020 9th International Conference System Modeling and Advancement in Research Trends (SMART), Moradabad, India, 4–5 December 2020; pp. 267–272. [Google Scholar] [CrossRef]
- Righini, S.; Calderoni, L.; Maio, D. A Privacy-Aware Zero Interaction Smart Mobility System. IEEE Access 2022, 10, 11924–11937. [Google Scholar] [CrossRef]
- Axelsson, J.; Nylander, S. An analysis of systems-of-systems opportunities and challenges related to mobility in smart cities. In Proceedings of the 2018 13th Annual Conference on System of Systems Engineering (SoSE), Paris, France, 19–22 June 2018; pp. 132–137. [Google Scholar] [CrossRef]
- Szymanski, T.H. The “Cyber Security via Determinism” Paradigm for a Quantum Safe Zero Trust Deterministic Internet of Things (IoT). IEEE Access 2022, 10, 45893–45930. [Google Scholar] [CrossRef]
- Pundir, A.; Singh, S.; Kumar, M.; Bafila, A.; Saxena, G.J. Cyber-Physical Systems Enabled Transport Networks in Smart Cities: Challenges and Enabling Technologies of the New Mobility Era. IEEE Access 2022, 10, 16350–16364. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Shi, Z.; Shen, X.S. A Lightweight Conditional Privacy-Preservation Protocol for Vehicular Traffic-Monitoring Systems. IEEE Intell. Syst. 2013, 28, 62–65. [Google Scholar] [CrossRef]
- Samara, G.; Alsalihy, W.A.A. A new security mechanism for vehicular communication networks. In Proceedings of the 2012 International Conference on Cyber Security, Cyber Warfare and Digital Forensic, Kuala Lumpur, Malaysia, 26–28 June 2012; pp. 18–22. [Google Scholar] [CrossRef]
- Skorput, P.; Vojvodic, H.; Mandzuka, S. Cyber security in cooperative intelligent transportation systems. In Proceedings of the 2017 International Symposium ELMAR, Zadar, Croatia, 18–20 September 2017; pp. 35–38. [Google Scholar] [CrossRef]
- Badra, M.; Ben Hamida, E. A novel cryptography based privacy preserving solution for urban mobility and traffic control. In Proceedings of the 2015 7th International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 27–29 July 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Vaidya, B.; Mouftah, H.T. Security for Shared Electric and Automated Mobility Services in Smart Cities. IEEE Secur. Priv. 2020, 19, 24–33. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Gagnon, F.; Ahmed, S.H.; Guizani, M. A secure, lightweight, and privacy-preserving authentication scheme for V2G connections in smart grid. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 541–546. [Google Scholar] [CrossRef]
- Sabaliauskaite, G.; Liew, L.S.; Zhou, F.; Cui, J. Designing safe and secure mixed traffic systems. In Proceedings of the 2019 IEEE 19th International Symposium on High Assurance Systems Engineering (HASE), Hangzhou, China, 3–5 January 2019; pp. 222–227. [Google Scholar] [CrossRef]
- Arabi, N.S.; Halabi, T.; Zulkernine, M. Reinforcement learning-driven attack on road traffic signal controllers. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; pp. 218–225. [Google Scholar] [CrossRef]
- Dong, C.; Wang, H.; Ni, D.; Liu, Y.; Chen, Q. Impact Evaluation of Cyber-Attacks on Traffic Flow of Connected and Automated Vehicles. IEEE Access 2020, 8, 86824–86835. [Google Scholar] [CrossRef]
- Ongel, A.; Cornet, H.; Kong, P.; Khoo, R.; Liu, T.; Kloeppel, M. Public transport service quality improvement using universal design standards and advanced vehicle technologies. In Proceedings of the 2018 International Conference on Intelligent Autonomous Systems (ICoIAS), Singapore, 1–3 March 2018; pp. 211–216. [Google Scholar] [CrossRef]
- Li, H.; Fu, Y. Research on the triggering factors of PPP in urban mass transit. In Proceedings of the 2017 4th International Conference on Industrial Economics System and Industrial Security Engineering (IEIS), Kyoto, Japan, 24–27 July 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Wazid, M.; Bera, B.; Das, A.K.; Mohanty, S.P.; Jo, M. Fortifying Smart Transportation Security Through Public Blockchain. IEEE Internet Things J. 2022, 9, 16532–16545. [Google Scholar] [CrossRef]
- Data Analysis and Information Security of an Internet of Things (IoT) Intelligent Transit System—IEEE Conference Publication. Available online: https://ieeexplore.ieee.org/document/8374744 (accessed on 6 February 2020).
- Kim, S.; Won, Y.; Park, I.-H.; Eun, Y.; Park, K.-J. Cyber-Physical Vulnerability Analysis of Communication-Based Train Control. IEEE Internet Things J. 2019, 6, 6353–6362. [Google Scholar] [CrossRef]
- Guo, H.; Wong, J.W. Cyber-physical authentication for metro systems. In Proceedings of the 23rd Asia-Pacific Conference on Communications (APCC), Perth, WA, Australia, 11–13 December 2017. [Google Scholar] [CrossRef]
- Aktouche, S.R.; Sallak, M.; Bouabdallah, A.; Schon, W. Towards reconciling safety and security risk analysis processes in railway remote driving. In Proceedings of the 2021 5th International Conference on System Reliability and Safety (ICSRS), Palermo, Italy, 24–26 November 2021; pp. 148–154. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L. Detecting invasive species with a bio-inspired semi-supervised neurocomputing approach: The case of Lagocephalus sceleratus. Neural Comput. Appl. 2016, 28, 1225–1234. [Google Scholar] [CrossRef]
- Ullo, S.L.; Sinha, G.R. Advances in Smart Environment Monitoring Systems Using IoT and Sensors. Sensors 2020, 20, 3113. [Google Scholar] [CrossRef]
- Anezakis, V.-D.; Iliadis, L.; Demertzis, K.; Mallinis, G. Hybrid soft computing analytics of cardiorespiratory morbidity and mortality risk due to air pollution. In Proceedings of the International Conference on Information Systems for Crisis Response and Management in Mediterranean Countries, Xanthi, Greece, 18–20 October 2017; pp. 87–105. [Google Scholar] [CrossRef]
- Anezakis, V.-D.; Demertzis, K.; Iliadis, L.; Spartalis, S. A hybrid soft computing approach producing robust forest fire risk indices. In Proceedings of the IFIP International Conference on Artificial Intelligence Applications and Innovations, Thessaloniki, Greece, 16–18 September 2016; pp. 191–203. [Google Scholar] [CrossRef]
- Elhabyan, R.; Shi, W.; St-Hilaire, M. Coverage protocols for wireless sensor networks: Review and future directions. J. Commun. Networks 2019, 21, 45–60. [Google Scholar] [CrossRef]
- Patel, S.T.; Mistry, N.H. A review: Sybil attack detection techniques in WSN. In Proceedings of the 2017 4th International Conference on Electronics and Communication Systems (ICECS), Coimbatore, India, 24–25 February 2017; pp. 184–188. [Google Scholar] [CrossRef]
- Sudheendran, S.; Bouachir, O.; Moussa, S.; Dahmane, A.O. Review—Challenges of mobility aware MAC protocols in WSN. In Proceedings of the 2018 Advances in Science and Engineering Technology International Conferences (ASET), Abu Dhabi, United Arab Emirates, 16 February–5 April 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, C.-H.; Teng, P.-C. The study for campus monitoring system of attacks analysis. In Proceedings of the 2010 International Symposium on Computer, Communication, Control and Automation (3CA), Tainan, Taiwan, 5–7 May 2010; Volume 1, pp. 407–410. [Google Scholar] [CrossRef]
- Teng, Z.; Pang, B.; Du, C.; Li, Z. Malicious Node Identification Strategy With Environmental Parameters. IEEE Access 2020, 8, 149522–149530. [Google Scholar] [CrossRef]
- Bajwa, S.S.; Khan, M.K. Grouped Black hole Attacks Security Model (GBHASM) for wireless Ad-hoc networks. In Proceedings of the 2010 The 2nd International Conference on Computer and Automation Engineering (ICCAE), Singapore, 26–28 February 2010; Volume 1, pp. 756–760. [Google Scholar] [CrossRef]
- Murino, G.; Armando, A.; Tacchella, A. Resilience of Cyber-Physical Systems: An Experimental Appraisal of Quantitative Measures. In Proceedings of the 2019 11th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 28–31 May 2019. [Google Scholar] [CrossRef]
- Hasan, M.K.; Khan, M.A.; Issa, G.F.; Atta, A.; Akram, A.S.; Hassan, M. Smart waste management and classification system for smart cities using deep learning. In Proceedings of the 2022 International Conference on Business Analytics for Technology and Security (ICBATS), Dubai, United Arab Emirates, 16–17 February 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Addeen, H.H.; Xiao, Y.; Li, J.; Guizani, M. A Survey of Cyber-Physical Attacks and Detection Methods in Smart Water Distribution Systems. IEEE Access 2021, 9, 99905–99921. [Google Scholar] [CrossRef]
- Binnar, P.; Dalvi, A.; Bhirud, S.; Kazi, F. Cyber forensic case study of waste water treatment plant. In Proceedings of the 2021 IEEE Bombay Section Signature Conference (IBSSC), Gwalior, India, 18–20 November 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. Distributed Attack Detection in a Water Treatment Plant: Method and Case Study. IEEE Trans. Dependable Secur. Comput. 2018, 18, 86–99. [Google Scholar] [CrossRef]
- Chenaru, O.; Popescu, D.; Enache, D.; Ichim, L.; Stoican, F. Improving operational security for web-based distributed control systems in wastewater management. In Proceedings of the 2017 25th Mediterranean Conference on Control and Automation (MED), Valletta, Malta, 3–6 July 2017; pp. 1089–1093. [Google Scholar] [CrossRef]
- Zhe, W.; Wei, C.; Chunlin, L. DoS attack detection model of smart grid based on machine learning method. In Proceedings of the 2020 IEEE International Conference on Power, Intelligent Computing and Systems (ICPICS), Shenyang, China, 28–30 July 2020; pp. 735–738. [Google Scholar] [CrossRef]
- Kumar, S.; Kumar, H.; Gunnam, G.R. Security integrity of data collection from smart electric meter under a cyber attack. In Proceedings of the 2019 2nd International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 28–30 June 2019; pp. 9–13. [Google Scholar] [CrossRef]
- Lu, X.; Jing, J.; Wu, Y. False data injection attack location detection based on classification method in smart grid. In Proceedings of the 2020 2nd International Conference on Artificial Intelligence and Advanced Manufacture (AIAM), Manchester, UK, 15–18 October 2020; pp. 133–136. [Google Scholar] [CrossRef]
- E Silva, F.A.C.; Villibor, J.P.; Almeida, T.A.D.S.; Bonatto, B.D.; Ribeiro, P.F. Smart cities criteria: A discussion about relevant and contextualized indicators for sustainable smart living. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Conference—Latin America (ISGT Latin America), Lima, Peru, 15–17 September 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Kor, A.-L.; Yanovsky, M.; Pattinson, C.; Kharchenko, V. SMART-ITEM: IoT-enabled smart living. In Proceedings of the 2016 Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; pp. 739–749. [Google Scholar] [CrossRef]
- Das, S.K. Cyber-physical-social convergence in smart living: Challenges and opportunities. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, NSW, Australia, 14–18 March 2016; p. 1. [Google Scholar] [CrossRef]
- Hussain, A.J.; Marcinonyte, D.M.; Iqbal, F.I.; Tawfik, H.; Baker, T.; Al-Jumeily, D. Smart home systems security. In Proceedings of the 2018 IEEE 20th International Conference on High Performance Computing and Communications; IEEE 16th International Conference on Smart City; IEEE 4th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Exeter, UK, 28–30 June 2018; pp. 1422–1428. [Google Scholar] [CrossRef]
- Karimi, K.; Krit, S. Smart home-smartphone systems: Threats, security requirements and open research challenges. In Proceedings of the 2019 International Conference of Computer Science and Renewable Energies (ICCSRE), Agadir, Morocco, 22–24 July 2019; pp. 1–5. [Google Scholar] [CrossRef]
- James, F. A risk management framework and a generalized attack automata for IoT based smart home environment. In Proceedings of the 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, 23–25 October 2019. [Google Scholar] [CrossRef]
- Gamundani, A.M. An impact review on internet of things attacks. In Proceedings of the 2015 International Conference on Emerging Trends in Networks and Computer Communications (ETNCC), Windhoek, Namibia, 17–20 May 2015; pp. 114–118. [Google Scholar] [CrossRef]
- Ibrahim, M.; Nabulsi, I. Security analysis of smart home systems applying attack graph. In Proceedings of the 2021 5th World Conference on Smart Trends in Systems Security and Sustainability (WorldS4), London, UK, 29–30 July 2021; pp. 230–234. [Google Scholar] [CrossRef]
- She, W.; Gu, Z.-H.; Lyu, X.-K.; Liu, Q.; Tian, Z.; Liu, W. Homomorphic Consortium Blockchain for Smart Home System Sensitive Data Privacy Preserving. IEEE Access 2019, 7, 62058–62070. [Google Scholar] [CrossRef]
- Li, T.; Han, D.; Li, J.; Li, A.; Zhang, Y.; Zhang, R.; Zhang, Y. Your home is insecure: Practical attacks on wireless home alarm systems. In Proceedings of the IEEE INFOCOM 2021—IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10–13 May 2021; pp. 1–10. [Google Scholar] [CrossRef]
- He, W.; Zhao, V.; Morkved, O.; Siddiqui, S.; Fernandes, E.; Hester, J.; Ur, B. SoK: Context sensing for access control in the adversarial home IoT. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroS&P), Vienna, Austria, 6–10 September 2021; pp. 37–53. [Google Scholar] [CrossRef]
- Singh, A.; Sikdar, B. Adversarial attack for deep learning based IoT appliance classification techniques. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021; pp. 657–662. [Google Scholar] [CrossRef]
- Demertzis, K.; Tziritas, N.; Kikiras, P.; Sanchez, S.L.; Iliadis, L. The Next Generation Cognitive Security Operations Center: Adaptive Analytic Lambda Architecture for Efficient Defense against Adversarial Attacks. Big Data Cogn. Comput. 2019, 3, 6. [Google Scholar] [CrossRef]
- Muhammed, T.; Mehmood, R.; Albeshri, A.; Katib, I. UbeHealth: A Personalized Ubiquitous Cloud and Edge-Enabled Networked Healthcare System for Smart Cities. IEEE Access 2018, 6, 32258–32285. [Google Scholar] [CrossRef]
- Islam, M.; Razzaque, A.; Hassan, M.M.; Ismail, W.N.; Song, B. Mobile Cloud-Based Big Healthcare Data Processing in Smart Cities. IEEE Access 2017, 5, 11887–11899. [Google Scholar] [CrossRef]
- Amin, S.U.; Hossain, M.S.; Muhammad, G.; Alhussein, M.; Rahman, A. Cognitive Smart Healthcare for Pathology Detection and Monitoring. IEEE Access 2019, 7, 10745–10753. [Google Scholar] [CrossRef]
- Kumar, A.; Krishnamurthi, R.; Nayyar, A.; Sharma, K.; Grover, V.; Hossain, E. A Novel Smart Healthcare Design, Simulation, and Implementation Using Healthcare 4.0 Processes. IEEE Access 2020, 8, 118433–118471. [Google Scholar] [CrossRef]
- Khan, U.T.; Zia, M.F. Smart city technologies, key components, and its aspects. In Proceedings of the 2021 International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 9–10 November 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 100. Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 1 Introduction to smart healthcare and telemedicine systems. In Artificial Intelligence, Blockchain and IoT for Smart Healthcare; River Publishers: Gistrup, Denmark, 2022; pp. 1–12. Available online: https://ieeexplore.ieee.org/document/9782809 (accessed on 10 July 2022).
- Hussain, F.; Hammad, M. Smart healthcare facilities via IOT in the healthcare industry. In Proceedings of the 3rd Smart Cities Symposium (SCS 2020), Online, 21–23 September 2021; pp. 386–391. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 3 Role of Artificial Intelligence, IoT and Blockchain in Smart Healthcare. In Artificial Intelligence, Blockchain and IoT for Smart Healthcare; River Publishers: Gistrup, Denmark, 2022; pp. 25–36. Available online: https://ieeexplore.ieee.org/document/9782803 (accessed on 10 July 2022).
- Karunarathne, S.M.; Saxena, N.; Khan, M.K. Security and Privacy in IoT Smart Healthcare. IEEE Internet Comput. 2021, 25, 37–48. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 7 Security and Privacy challenge in Smart Healthcare and Telemedicine systems. In Artificial Intelligence, Blockchain and IoT for Smart Healthcare; River Publishers: Gistrup, Denmark, 2022; pp. 67–76. Available online: https://ieeexplore.ieee.org/document/9782812 (accessed on 10 July 2022).
- Qiu, J.; Liang, X.; Shetty, S.; Bowden, D. Towards secure and smart healthcare in smart cities using blockchain. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Cook, D.J.; Duncan, G.; Sprint, G.; Fritz, R.L. Using Smart City Technology to Make Healthcare Smarter. Proc. IEEE 2018, 106, 708–722. [Google Scholar] [CrossRef] [PubMed]
- Butt, S.A.; Diaz-Martinez, J.L.; Jamal, T.; Ali, A.; De-La-Hoz-Franco, E.; Shoaib, M. IoT smart health security threats. In Proceedings of the 2019 19th International Conference on Computational Science and Its Applications (ICCSA), St. Petersburg, Russia, 1–4 July 2019; pp. 26–31. [Google Scholar] [CrossRef]
- Safavi, S.; Meer, A.M.; Melanie, E.K.J.; Shukur, Z. Cyber Vulnerabilities on smart healthcare, review and solutions. In Proceedings of the 2018 Cyber Resilience Conference (CRC), Putrajaya, Malaysia, 13–15 November 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Nidhya, R.; Kumar, M.; Maheswar, R.; Pavithra, D. Security and privacy issues in smart healthcare system using internet of things. In IoT-Enabled Smart Healthcare Systems, Services and Applications; Wiley: Hoboken, NJ, USA, 2022; pp. 63–85. [Google Scholar] [CrossRef]
- Chinnasamy, P.; Deepalakshmi, P. Design of Secure Storage for Health-care Cloud using hybrid cryptography. In Proceedings of the 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT), Coimbatore, India, 20–21 April 2018; pp. 1717–1720. [Google Scholar] [CrossRef]
- Yang, D.; Doh, I.; Chae, K. Secure medical image-sharing mechanism based on visual cryptography in EHR system. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018. [Google Scholar] [CrossRef]
- Quamara, M.; Gupta, B.B.; Yamaguchi, S. An end-to-end security framework for smart healthcare information sharing against botnet-based cyber-attacks. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 10–12 January 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Poonguzhali, N.; Gayathri, S.; Deebika, A.; Suriapriya, R. A framework for electronic health record using blockchain technology. In Proceedings of the 2020 International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 3–4 July 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Zhuang, Y.; Sheets, L.R.; Chen, Y.-W.; Shae, Z.-Y.; Tsai, J.J.P.; Shyu, C.-R. A Patient-Centric Health Information Exchange Framework Using Blockchain Technology. IEEE J. Biomed. Health Inform. 2020, 24, 2169–2176. [Google Scholar] [CrossRef] [PubMed]
- Reen, G.S.; Mohandas, M.; Venkatesan, S. Decentralized patient centric e-health record management system using blockchain and IPFS. In Proceedings of the 2019 IEEE Conference on Information and Communication Technology, Allahabad, India, 6–8 December 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Newaz, A.I.; Haque, N.I.; Sikder, A.K.; Rahman, M.A.; Uluagac, A.S. Adversarial attacks to machine learning-based smart healthcare systems. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwa, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Youssef, A.; Hajek, P. The role of smart economy in developing smart cities. In Proceedings of the 2021 International Symposium on Computer Science and Intelligent Controls (ISCSIC), Rome, Italy, 12–14 November 2021; pp. 276–279. [Google Scholar] [CrossRef]
- Purnomo, A.; Sano, A.V.D.; Nindito, H.; Madyatmadja, E.D.; Sianipar, C.P.M. Mapping of smart economy research themes: A nine-year review. In Proceedings of the 2021 International Conference on ICT for Smart Society (ICISS), Bandung, Indonesia, 2–4 August 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Riasat, S.; Shah, M.A. Securing smart cities: An analysis on using blockchain for digital economies. In Proceedings of the Competitive Advantage in the Digital Economy (CADE 2021), Online, 2–3 June 2021; pp. 143–148. [Google Scholar] [CrossRef]
- Bongestu, D.R.; Yappiter; Warnars, H.L.H.S. Jakarta smart city mobile application for problem reporting. In Proceedings of the 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS), Coimbatore, India, 25–27 March 2021; pp. 735–740. [Google Scholar] [CrossRef]
- Madyatmadja, E.D.; Abdurachman, E.; Gaol, F.L.; Pudjianto, B.W.; Hapsara, M. Potential impact of social media to support government services in jakarta smart city. In Proceedings of the 2018 International Conference on Information Management and Technology (ICIMTech), Jakarta, Indonesia, 3–5 September 2018; pp. 534–538. [Google Scholar] [CrossRef]
- Parlina, A.; Murfi, H.; Ramli, K. Smart city research in Indonesia: A bibliometric analysis. In Proceedings of the 2019 16th International Conference on Quality in Research (QIR): International Symposium on Electrical and Computer Engineering, Padang, Indonesia, 22–24 July 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Anindra, F.; Supangkat, S.H.; Kosala, R.R. Smart governance as smart city critical success factor (case in 15 cities in Indonesia). In Proceedings of the 2018 International Conference on ICT for Smart Society (ICISS), Semarang, Indonesia, 10–11 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Surbakti, E.; Tobing, F.; Prisalia, R.; Septa, R. AHP hierarchy structure for indicators of smart city implementation in Indonesia. In Proceedings of the 2021 2nd International Conference On Smart Cities, Automation & Intelligent Computing Systems (ICON-SONICS), Tangerang, Indonesia, 12–13 October 2021; pp. 25–30. [Google Scholar] [CrossRef]
- Wei, C.; Dong, Z. Promote Internet economic development and smart city construction with data sharing. In Proceedings of the 2021 2nd International Conference on Big Data Economy and Information Management (BDEIM), Sanya, China, 3–5 December 2021; pp. 483–486. [Google Scholar] [CrossRef]
- Guo, W.; Jiang, P. Framework for designing a smart connected product service system. In Proceedings of the 2021 IEEE 1st International Conference on Digital Twins and Parallel Intelligence (DTPI), Beijing, China, 15 July–15 August 2021; pp. 448–451. [Google Scholar] [CrossRef]
- Ramachandran, G.S.; Radhakrishnan, R.; Krishnamachari, B. Towards a decentralized data marketplace for smart cities. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Said, S.M.; Abderrahim, M.; Mohamed, O.; Mohamed, T. Dynamic approach to secure smart city applications (DCESA). In Proceedings of the 2018 Renewable Energies, Power Systems & Green Inclusive Economy (REPS-GIE), Casablanca, Morocco, 23–24 April 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Zainudin, Z.S.; Molok, N.N.A. Advanced persistent threats awareness and readiness: A case study in malaysian financial institutions. In Proceedings of the 2018 Cyber Resilience Conference (CRC), Putrajaya, Malaysia, 13–15 November 2018; pp. 1–3. [Google Scholar] [CrossRef]
- Ando, B. A Smart Multisensor Approach to Assist Blind People in Specific Urban Navigation Tasks. IEEE Trans. Neural Syst. Rehabilitation Eng. 2008, 16, 592–594. [Google Scholar] [CrossRef]
- Wang, L.; Xu, L.; Zheng, Z.; Liu, S.; Li, X.; Cao, L.; Li, J.; Sun, C. Smart Contract-Based Agricultural Food Supply Chain Traceability. IEEE Access 2021, 9, 9296–9307. [Google Scholar] [CrossRef]
- Krejcar, O.; Maresova, P.; Selamat, A.; Melero, F.J.; Barakovic, S.; Husic, J.B.; Herrera-Viedma, E.; Frischer, R.; Kuča, K. Smart Furniture as a Component of a Smart City—Definition Based on Key Technologies Specification. IEEE Access 2019, 7, 94822–94839. [Google Scholar] [CrossRef]
- Kirimtat, A.; Krejcar, O.; Kertesz, A.; Tasgetiren, M.F. Future Trends and Current State of Smart City Concepts: A Survey. IEEE Access 2020, 8, 86448–86467. [Google Scholar] [CrossRef]
- Chye, C.M.; Fahmy-Abdullah, M.; Sufahani, S.F.; Bin Ali, M.K. A study of smart people toward smart cities development. In Proceedings of the Third International Conference on Trends in Computational and Cognitive Engineering; Springer: Singapore, 2022; pp. 257–271. [Google Scholar] [CrossRef]
- Wolff, A.; Kortuem, G.; Cavero, J. Towards smart city education. In Proceedings of the 2015 Sustainable Internet and ICT for Sustainability (SustainIT), Madrid, Spain, 14–15 April 2015; pp. 1–3. [Google Scholar] [CrossRef]
- Bululukova, D.; Tabakovic, M.; Wahl, H. Smart cities education as mobility, energy & ICT hub. In Proceedings of the 2016 5th International Conference on Smart Cities and Green ICT Systems (SMARTGREENS), Rome, Italy, 23–25 April 2016; pp. 1–8. [Google Scholar]
- Kwon, M.J.; Kwak, G.; Jun, S.; Kim, H.-J.; Lee, H.Y. Enriching security education hands-on labs with practical exercises. In Proceedings of the 2017 International Conference on Software Security and Assurance (ICSSA), Altoona, PA, USA, 24–25 July 2017; pp. 100–103. [Google Scholar] [CrossRef]
- Tseng, S.-S.; Chen, K.-Y.; Lee, T.-J.; Weng, J.-F. Automatic content generation for anti-phishing education game. In Proceedings of the 2011 International Conference on Electrical and Control Engineering, Yichang, China, 16–18 September 2011; pp. 6390–6394. [Google Scholar] [CrossRef]
- Ropke, R.; Schroeder, U.; Drury, V.; Meyer, U. Towards personalized game-based learning in anti-phishing education. In Proceedings of the 2020 IEEE 20th International Conference on Advanced Learning Technologies (ICALT), Tartu, Estonia, 6–9 July 2020; pp. 65–66. [Google Scholar] [CrossRef]
- Chiou, Y.-M.; Shen, C.-C.; Mouza, C.; Rutherford, T. Augmented reality-based cybersecurity education on phishing. In Proceedings of the 2021 IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), Taichung, Taiwan, 15–17 November 2021; pp. 228–231. [Google Scholar] [CrossRef]
- Yahya, F.; Mahibol, R.I.W.; Ying, C.K.; Bin Anai, M.; Frankie, S.A.; Nin Wei, E.L.; Utomo, R.G. Detection of phising websites using machine learning approaches. In Proceedings of the 2021 International Conference on Data Science and Its Applications (ICoDSA), Bandung, Indonesia, 6–7 October 2021; pp. 40–47. [Google Scholar] [CrossRef]
- Takata, T.; Ogura, K. Confront Phishing Attacks—From a Perspective of Security Education. In Proceedings of the 2019 IEEE 10th International Conference on Awareness Science and Technology (iCAST), Morioka, Japan, 23–25 October 2019. [Google Scholar] [CrossRef]
- Mtshali, P.; Khubisa, F. A smart home appliance control system for physically disabled people. In Proceedings of the 2019 Conference on Information Communications Technology and Society (ICTAS), Durban, South Africa, 6–8 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Kasthuri, R.; Nivetha, B.; Shabana, S.; Veluchamy, M.; Sivakumar, S. Smart device for visually impaired people. In Proceedings of the 2017 Third International Conference on Science Technology Engineering & Management (ICONSTEM), Chennai, India, 23–24 March 2017; pp. 54–59. [Google Scholar] [CrossRef]
- Richter, F. Ethics of AI as practical ethics. In Proceedings of the 2021 IEEE International Symposium on Technology and Society (ISTAS), Waterloo, ON, Canada, 28–31 October 2021; p. 1. [Google Scholar] [CrossRef]
- Gamundani, A.M.; Phillips, A.; Muyingi, H.N. An overview of potential authentication threats and attacks on Internet of Things(IoT): A Focus on Smart Home Applications. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 50–57. [Google Scholar] [CrossRef]
- Demertzis, K.; Kikiras, P.; Tziritas, N.; Sanchez, S.L.; Iliadis, L. The Next Generation Cognitive Security Operations Center: Network Flow Forensics Using Cybersecurity Intelligence. Big Data Cogn. Comput. 2018, 2, 35. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L.; Pimenidis, E.; Tziritas, N.; Koziri, M.; Kikiras, P. Blockchained adaptive federated auto metalearning BigData and DevOps CyberSecurity Architecture in Industry 4.0. In Proceedings of the International Neural Networks Society; Springer: Berlin/Heidelberg, Germany, 2021; pp. 345–363. [Google Scholar] [CrossRef]
- R, M.; K, G.; Rao, V.V. Proactive measures to mitigate cyber security challenges in IoT based smart healthcare networks. In Proceedings of the 2021 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 21–24 April 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Alshalali, T.; Mbale, K.; Josyula, D. Security and privacy of electronic health records sharing using hyperledger fabric. In Proceedings of the 2018 International Conference on Computational Science and Computational Intelligence (CSCI), Las Ve-gas, NV, USA, 13–15 December 2018. [Google Scholar]
- Bringer, J.; Chabanne, H.; Patey, A. Privacy-Preserving Biometric Identification Using Secure Multiparty Computation: An Overview and Recent Trends. IEEE Signal Process. Mag. 2013, 30, 42–52. [Google Scholar] [CrossRef]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Demertzi, V.; Demertzis, S.; Demertzis, K. An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities. Appl. Sci. 2023, 13, 790. https://doi.org/10.3390/app13020790
Demertzi V, Demertzis S, Demertzis K. An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities. Applied Sciences. 2023; 13(2):790. https://doi.org/10.3390/app13020790
Chicago/Turabian StyleDemertzi, Vasiliki, Stavros Demertzis, and Konstantinos Demertzis. 2023. "An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities" Applied Sciences 13, no. 2: 790. https://doi.org/10.3390/app13020790
APA StyleDemertzi, V., Demertzis, S., & Demertzis, K. (2023). An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities. Applied Sciences, 13(2), 790. https://doi.org/10.3390/app13020790







