Secure Image Signal Transmission Scheme Using Poly-Polarization Filtering and Orthogonal Matrix
Abstract
1. Introduction
- Both the image information security and PDL elimination were considered in the PPF-OM scheme. The PDL was eliminated, and the information security was enhanced, which was evaluated by both the BER and secrecy-rate performances.
- The information was conveyed by two signals, which were mixed twice by PSs and the OM, step by step. After two mixing procedures, signals became difficult to decipher.
- The parameters of u, l, PSs, orthogonal matrix, and modulation mode should be determined in order, and if there is an error in a parameter, the latter parameters would produce greater errors. In addition, if eavesdroppers attempted to breach one parameter through the method of exhaustion, the recovered signals would be random plurals. Therefore, the PPF-OM scheme offered good protection for parameters, thus improving information security.
- In the PPF-OM scheme, all power was used to transmit the signal, and no power was wasted. In this manner, there would still be self-interference in the eavesdropper’s received signals, with an effect similar to the artificial noise that deteriorates the channel quality. Therefore, a positive secrecy capacity could be guaranteed to ensure information security.
- In [25], the weight-weighted fractional Fourier transform (WFRFT) was used to process the transmit signal vectors to enhance information security. As described in the reference, the WFRFT operation consisted of a K-point discrete Fourier transform operation (O()) and two reverse modulo-K operations (O(K)). Thus, the larger the signal vector length K was, the larger the amount of computation became. However, in the PPF-OM scheme, a similar security performance could be achieved with less computation, which is described detailed in following sections.
2. System Model
3. Signal Model and Problem Description
- Based on the k-th received image signal, the PS was obtained, as follows:
- With , the polarization matching was carried out according to the k-th received signal, such as in Equation (3), as follows:
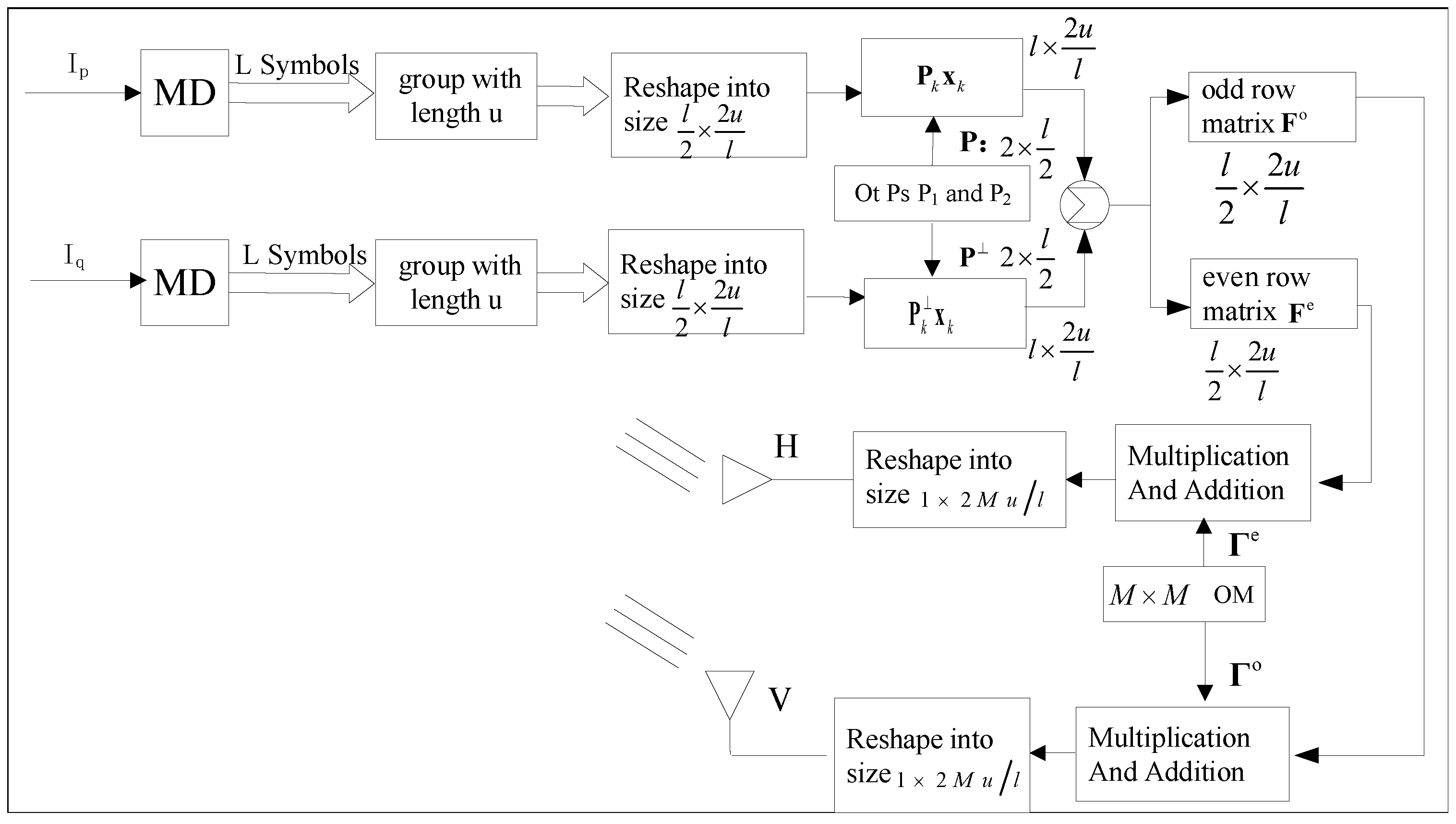
4. The Principle of the PPF-OM Scheme
4.1. Signal Processing on the Transmitter Side
4.2. Signal Processing on the Receiver Side
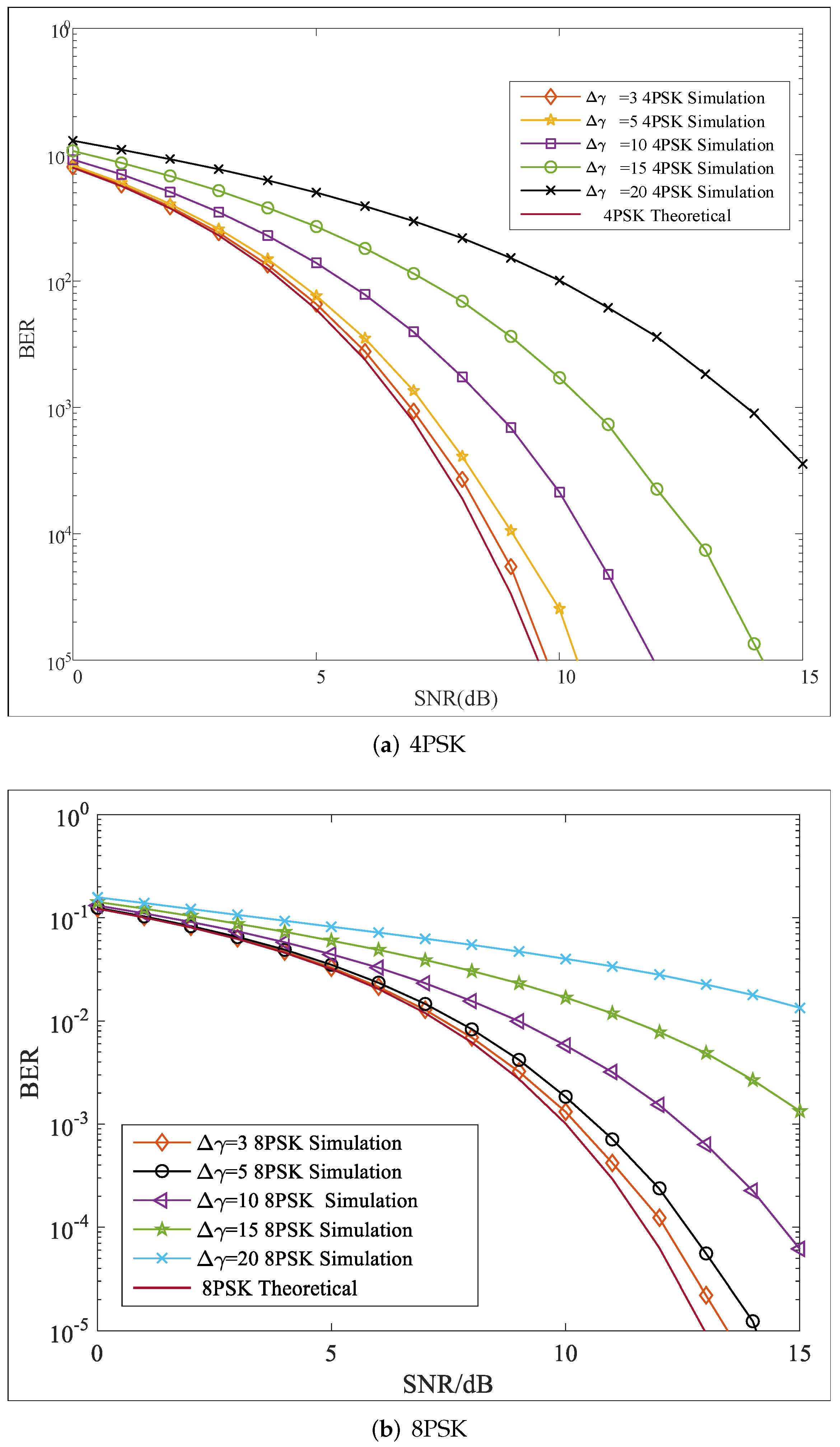
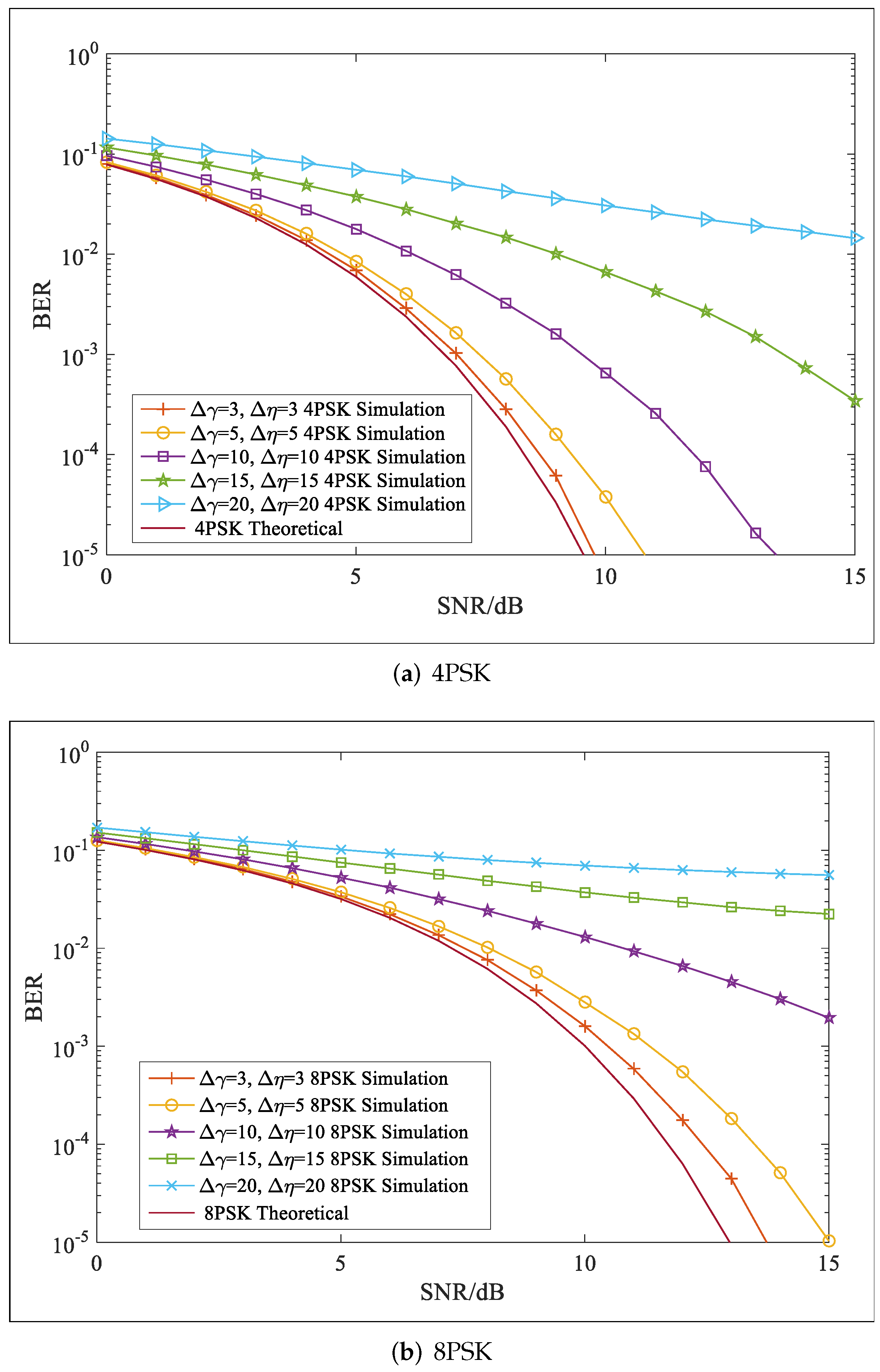
5. Security Performance Evaluation
- It was known that the length of the received image signal vector was , and if the number of the divisor of was , there were at least matrix reconstruction methods. In addition, was adjustable and would increase as increased. Moreover, the reshaped matrices and were composite matrices, and the orthogonal matrix was also unknown, which made it difficult to determine the correct matrix size. When the size of the reshaped matrices and were incorrect, it was not possible to correctly recover the horizontal and vertical signal component matrices.
- If Eve could correctly reshape the received image signal vector into a matrix, Eve would know and were composite matrices that should be processed by in the correct order. As Eve did not have the information about , it needed to search for the correct and order, as follows:According to Equation (26), only obtained . In other cases, H and V components could not be correctly recovered, nor could the two signals be separated through polarization filtering. In addition, a larger M led to a larger amount of calculation for Eve. Therefore, in this case, the parameters were difficult to determine.
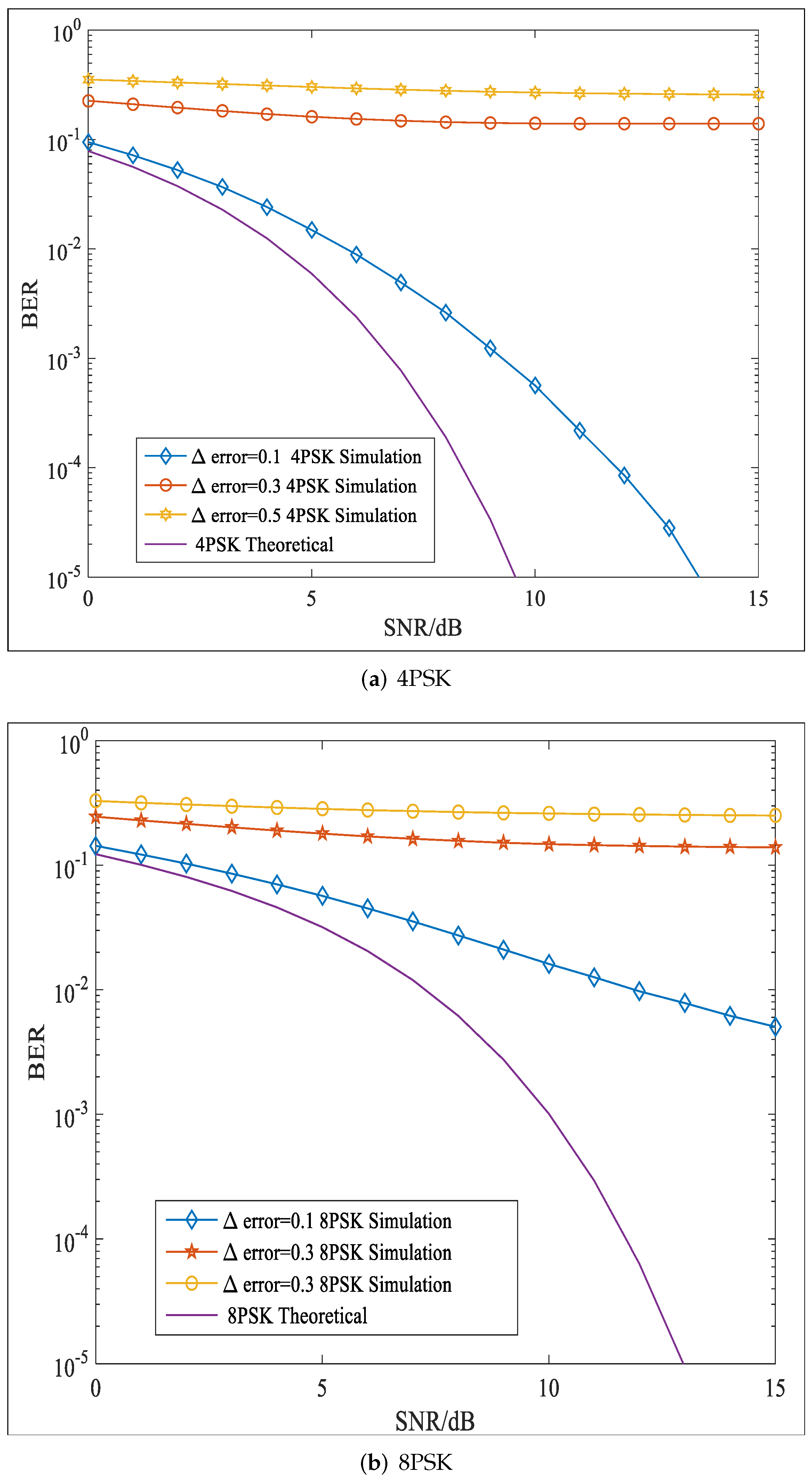
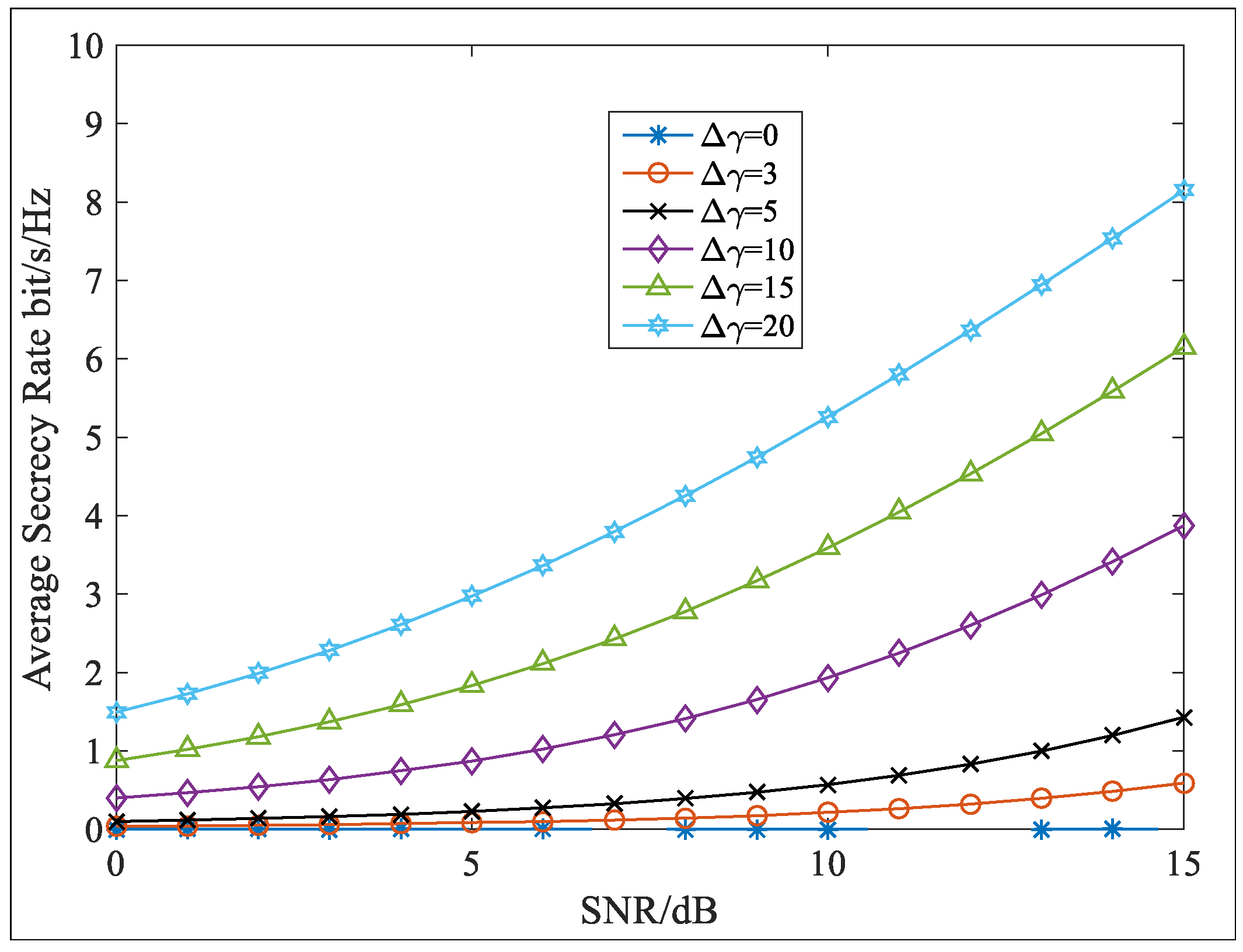
- If we assumed that Eve could correctly obtain the matrices and while the information regarding PSs was used for processing, the transmission signals were unknown. As and were mixed matrices of two polarized signals, the first step was to isolate them for demodulation. Thus, Eve must first search for the correct PSs to construct polarization filtering matrices for the signal separation. However, the PSs for each row signal vector were different, and the modulation mode of the two AM signals was unknown. Therefore, even with the right polarization filtering matrices, it would be difficult to determine the correct AM signals. Based on the above analysis, it was difficult to avoid errors in the PSs. In this condition, the PF matrices of Eve were written, as follows:where and denote the errors. Here, we assumed , and the signal separation of the k-th row signal vector was taken as an example:whereWe found , and after polarization matching, Equation (28) was written, as follows:In the same manner, we found the following:where .According to Equations (29) and (30), we found that there were interferences in recovered signals by Eve that would degrade BER performance. Thus, for Bob and Eve, the signal-to-noise ratio (SNR) was calculated as:Then, the average secrecy rate with the proposed scheme could be calculated, as follows:As analyzed in Equation (31), we found and ; thus, would always be positive when deviations existed in any of the parameters mention above, which ensured transmission security.
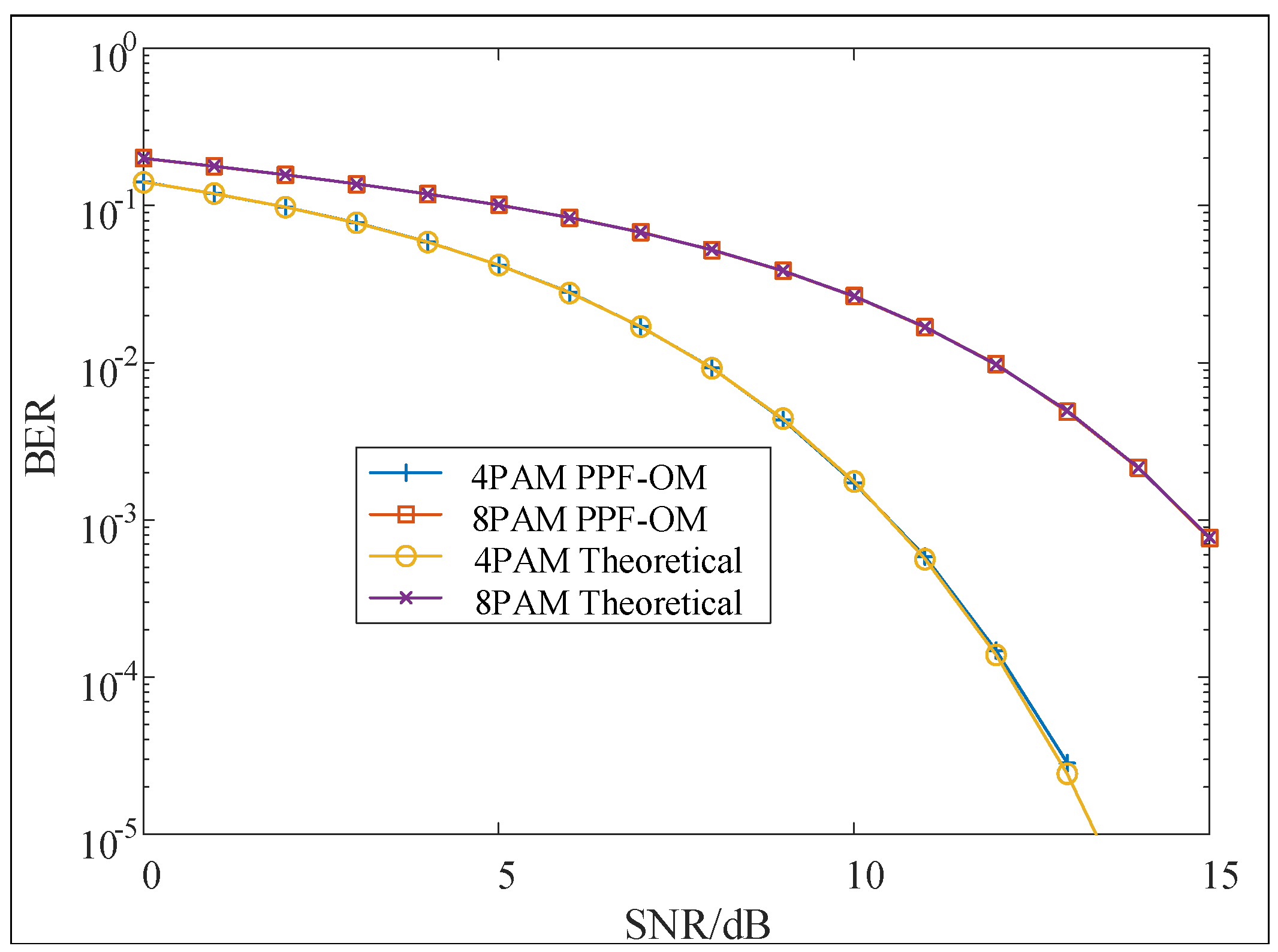
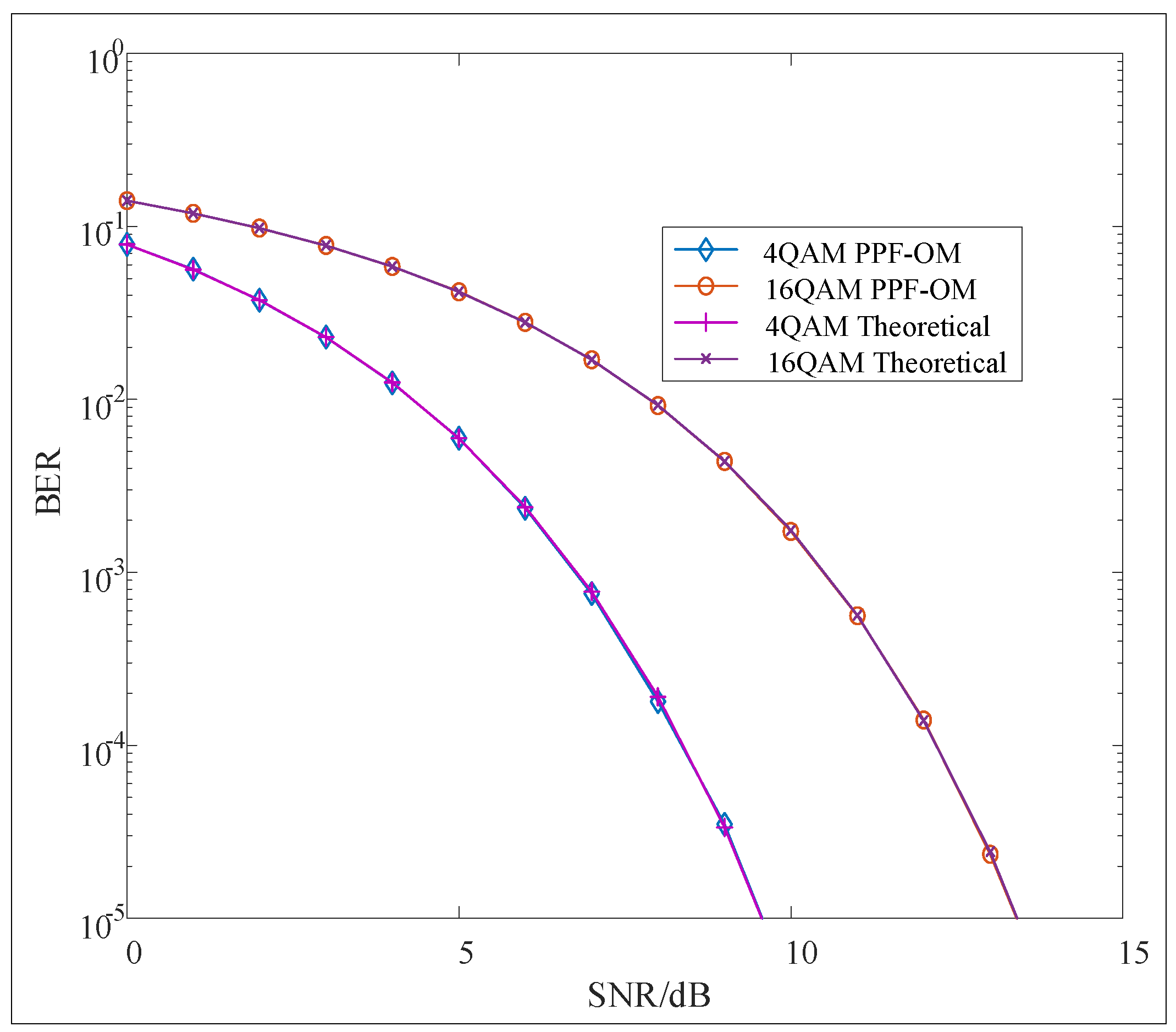
6. Numerical Result
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Hajiyat, Z.; Ismail, A.; Sali, A.; Hamidon, M.N. Antenna in 6G Wireless Communication System: Specifications, Challenges, and Research Directions. Optik 2021, 231, 166415. [Google Scholar] [CrossRef]
- Li, Q.; Xu, D. Secure Transmission in Multicarrier Power-Splitting Wireless Powered Communication Networks with Full-duplex Receivers. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 1355–1359. [Google Scholar] [CrossRef]
- Da, X.; Liang, Y.; Hu, H.; Xu, R.; Ni, L.; Zhai, D.; Pan, Y. Embedding WFRFT Signals Into TDCS for Secure Communications. IEEE Access 2018, 6, 54938–54951. [Google Scholar] [CrossRef]
- Luo, Z.; Wang, H.; Zhou, K.; Lv, W. Combined Constellation Rotation With Weighted FRFT for Secure Transmission in Polarization Modulation Based Dual-Polarized Satellite Communications. IEEE Access 2017, 5, 27061–27073. [Google Scholar] [CrossRef]
- Fang, X.; Sha, X.; Li, Y. MP-WFRFT and constellation scrambling based physical layer security system. China Commun. 2016, 13, 138–145. Available online: http://xueshu.baidu.com/s?wd=paperuri (accessed on 9 February 2023).
- Valliappan, N.; Lozano, A.; Heath, R.W. Antenna Subset Modulation for Secure Millimeter-Wave Wireless Communication. IEEE Trans. Commun. 2013, 61, 3231–3245. [Google Scholar] [CrossRef]
- Wang, S.; Wei, L.; Jing, L. Physical-Layer Encryption in Massive MIMO Systems with Spatial Modulation. China Commun. 2018, 15, 159–171. [Google Scholar] [CrossRef]
- Wang, Z.; Chen, F.; Qiu, W.; Chen, S.; Ren, D. A two layer chaotic encryption scheme of secure image transmission for DCT precoded OFDM-VLC transmission. Opt. Commun. 2018, 410, 94–101. [Google Scholar] [CrossRef]
- Xie, T.; Zhu, J.; Li, Y. Artificial-Noise-Aided Zero-Forcing Synthesis Approach for Secure Multi-Beam Directional Modulation. IEEE Commun. Lett. 2018, 22, 276–279. [Google Scholar] [CrossRef]
- Wang, Q. Defending wireless communication against eavesdropping attacks using secret spreading codes and artificial interference. Comput. Secur. 2021, 103, 102175. [Google Scholar] [CrossRef]
- Cho, S.; Chen, G.; Coon, J.P. Zero-Forcing Beamforming for Active and Passive Eavesdropper Mitigation in Visible Light Communication Systems. IEEE Trans. Inf. Forensics Secur. 2021, 16, 1495–1505. [Google Scholar] [CrossRef]
- Shu, F.; Wu, X.; Li, J.; Chen, R.; Vucetic, B. Robust Synthesis Scheme for Secure Multi-Beam Directional Modulation in Broadcasting Systems. IEEE Access 2016, 4, 6614–6623. [Google Scholar] [CrossRef]
- Yaacoub, E.; Al-Husseini, M. Achieving physical layer security with massive MIMO beamforming. In Proceedings of the 2017 11th European Conference on Antennas and Propagation (EUCAP), Paris, France, 19–24 March 2017; pp. 1753–1757. [Google Scholar]
- Moualeu, J.M.; Ngatched, T.M.N. Physical-Layer Security Enhancement via Relay-Aided D2D Communications Underlaying Cellular Networks. IEEE Open J. Commun. Soc. 2020, 1, 413–427. [Google Scholar] [CrossRef]
- Ray, P.P. A perspective on 6G: Requirement, technology, enablers, challenges and future road map. J. Syst. Archit. 2021, 118, 102180. [Google Scholar] [CrossRef]
- Zhu, J.; Yang, P.; Xiao, Y.; Di Renzo, M.; Li, S. Dual Polarized Spatial Modulation for Land Mobile Satellite Communications. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, F.; Wang, X.; Li, R.; Wang, B. Multilevel Continuous Polarization Modulation With High Spectral Efficiency in the Depolarization Channels. IEEE Access 2018, 6, 33002–33014. [Google Scholar] [CrossRef]
- Sun, D.; Zhang, Q.; Wei, D.; Zhang, M. A Secure Constellation Design for Polarized Modulation in Wireless Communications. IEEE Access 2020, 8, 130588–130597. [Google Scholar] [CrossRef]
- Wei, D.; Feng, C.; Guo, C.; Liu, F. A Power Amplifier Energy Efficient Polarization Modulation Scheme Based on the Optimal Pre-Compensation. IEEE Commun. Lett. 2013, 17, 513–516. [Google Scholar] [CrossRef]
- Luo, Z.; Wang, H.; Zhou, K. Physical Layer Security Scheme Based on Polarization Modulation and WFRFT Processing for Dual-polarized Satellite Systems. KSII Trans. Internet Inf. Syst. 2017, 11, 5610–5624. [Google Scholar] [CrossRef]
- Wei, D.; Liang, L.; Zhang, M.; Qiao, R.; Huang, W. A Polarization state Modulation based Physical Layer Security scheme for Wireless Communications. In Proceedings of the MILCOM 2016—2016 IEEE Military Communications Conference, Baltimore, MD, USA, 1–3 November 2016; pp. 1195–1201. [Google Scholar] [CrossRef]
- Luo, Z.K.; Pei, Z.M.; Zou, B. Polarization Filtering Based Transmission Scheme for Wireless Communications. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2019, E102-A, 1387–1392. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, B.; Guo, D. Physical Layer Secure Transmission Based on Fast Dual Polarization Hopping in Fixed Satellite Communication. IEEE Access 2017, 5, 11782–11790. [Google Scholar] [CrossRef]
- Luo, Z.; Wang, H.; Zhou, K. Polarization Filtering Based Physical-Layer Secure Transmission Scheme for Dual-Polarized Satellite Communication. IEEE Access 2017, 5, 24706–24715. [Google Scholar] [CrossRef]
- Luo, Z.; Pei, Z. Orthogonal vector based transmission method for security enhancement and PDL elimination in dual-polarized wireless communications. Signal Process. 2022, 196, 108477. [Google Scholar] [CrossRef]
- Wen, Z.; Chunyan, F.; Fangfang, L.; Caili, G. Polarization oblique projection based self-interference cancellation against PA nonlinear distortion in MIMO full duplex system. China Commun. 2016, 13, 49–59. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Luo, Z.; Pei, Z.; Yang, C.; Liu, Z.; Chen, H. Secure Image Signal Transmission Scheme Using Poly-Polarization Filtering and Orthogonal Matrix. Appl. Sci. 2023, 13, 2513. https://doi.org/10.3390/app13042513
Luo Z, Pei Z, Yang C, Liu Z, Chen H. Secure Image Signal Transmission Scheme Using Poly-Polarization Filtering and Orthogonal Matrix. Applied Sciences. 2023; 13(4):2513. https://doi.org/10.3390/app13042513
Chicago/Turabian StyleLuo, Zhangkai, Zhongmin Pei, Chengwei Yang, Zhengjun Liu, and Hang Chen. 2023. "Secure Image Signal Transmission Scheme Using Poly-Polarization Filtering and Orthogonal Matrix" Applied Sciences 13, no. 4: 2513. https://doi.org/10.3390/app13042513
APA StyleLuo, Z., Pei, Z., Yang, C., Liu, Z., & Chen, H. (2023). Secure Image Signal Transmission Scheme Using Poly-Polarization Filtering and Orthogonal Matrix. Applied Sciences, 13(4), 2513. https://doi.org/10.3390/app13042513







