Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack
Abstract
:1. Introduction
- This paper presents attack scenarios according to malicious codes based on APT attack cases. Moreover, according to the results of the scenarios, methods to detect malicious codes were classified and analyzed into security management systems, pattern-based detection methods, heuristic-based detection methods, reputation-based detection methods, behavior-based detection methods, virtualization-based detection methods, abnormal detection methods, big data-based detection methods, and other methods.
- Moreover, this article is distinct from survey articles comparing existing malicious code detection methods as follows: 1. We focus on the latest malware detection technologies. 2. We classify and analyze overall malicious code detection technologies, without being limited to a specific method. 3. Scenarios were presented based on actual attack cases, and malware detection methods were classified based on the presented scenarios.
- Finally, through the classification and analysis results of malicious code detection methods, we expect this article to be helpful in developing effective malicious code detection technologies against various attacks in the future.
2. Attack Cases by Malicious Codes
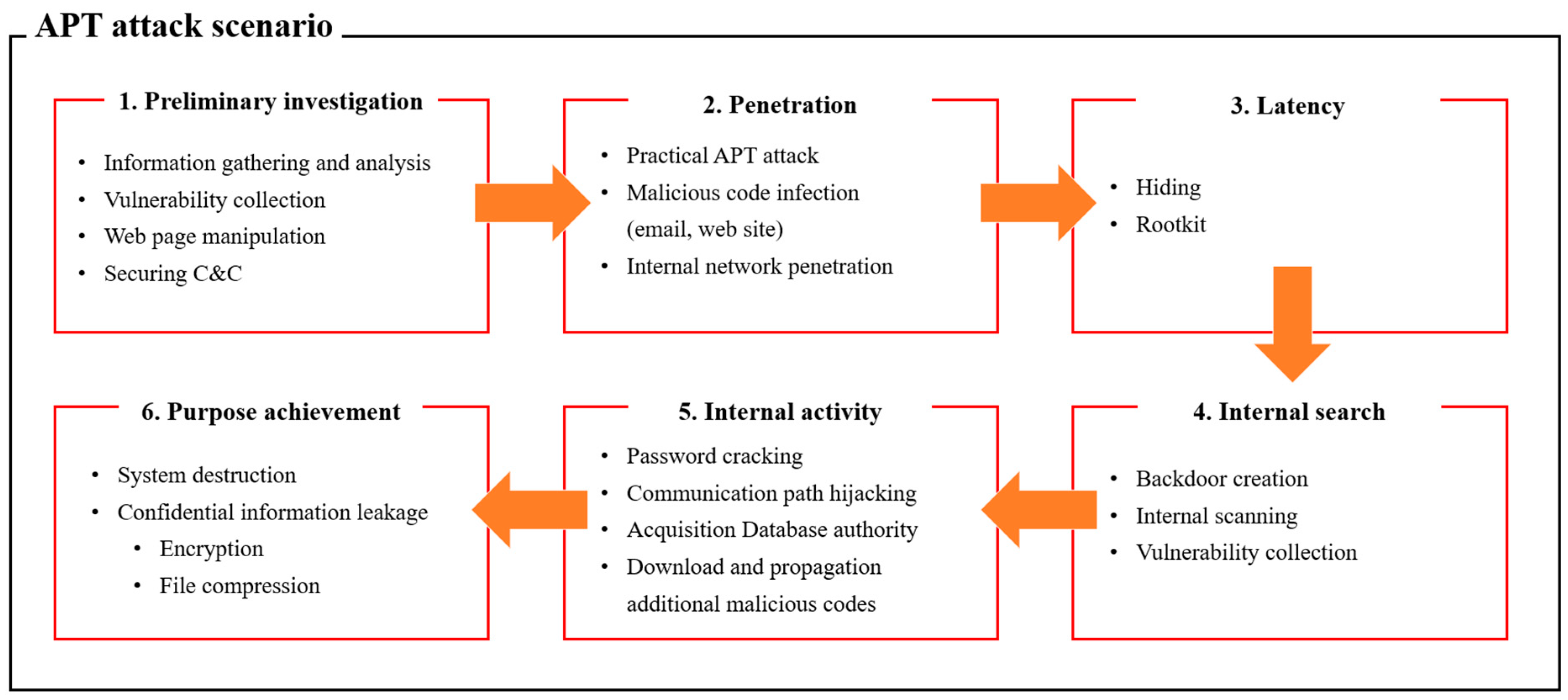
3. Malicious Code Attack Scenario
4. Attack Techniques Used by Malicious Code
5. Classification and Analysis of Malicious Code Detection Methods
5.1. Detection Techniques in Security Control Systems
5.2. Pattern-Based Detection Method
5.3. Heuristic-Based Detection Method
5.4. Reputation-Based Detection Method
5.5. Behavior-Based Detection Method
5.6. Virtualization-Based Detection Method
5.7. Anomalous Symptom Detection Method
5.8. Data Analysis-Based Detection
5.9. Other Detection Methods
5.10. Analysis of Advantages and Disadvantages of Malicious Code Detection Methods
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Khalid, A.; Zainal, A.; Maarof, M.A.; Ghaleb, F.A. Advanced Persistent Threat Detection: A Survey. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 5 April 2021; pp. 1–6. [Google Scholar]
- Saurabh, S.; Sharma, P.; Yeon Moon, S.; Daesung, M.; Hyuk Park, J. A comprehensive study on APT attacks and countermeasures for future networks and communications: Challenges and solutions. J. Supercomput. 2016, 75, 4543–4574. [Google Scholar]
- Joint Task Force Transformation Initiative. In Managing Information Security Risk: Organization, Mission, and Information System View; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011; p. NIST SP 800-39.
- Kim, G.; Choi, C.; Choi, J. Ontology Modeling for APT Attack Detection in an IoT-Based Power System. In Proceedings of the 2018 Conference on Research in Adaptive and Convergent Systems, Honolulu, Hawaii, 9 October 2018; pp. 160–164. [Google Scholar]
- Fei, Y.; Ning, J.; Jiang, W. A Quantifiable Attack-Defense Trees Model for APT Attack. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 October 2018; pp. 2303–2306. [Google Scholar]
- Gao, P.; Xiao, X.; Li, Z.; Xu, F.; Kulkarni, S.R.; Mittal, P. AIQL: Enabling Efficient Attack Investigation from System Monitoring Data. In Proceedings of the 2018 USENIX Conference on Usenix Annual Technical Conference, Boston, MA, USA, July 2018; pp. 113–125. [Google Scholar]
- Chuan, B.L.J.; Singh, M.M.; Shariff, A.R.M. APTGuard: Advanced Persistent Threat (APT) Detections and Predictions Using Android Smartphone. In Computational Science and Technology; Alfred, R., Lim, Y., Ibrahim, A.A.A., Anthony, P., Eds.; Springer: Singapore, 2019; Volume 481, pp. 545–555. [Google Scholar]
- Nicho, M.; Oluwasegun, A.; Kamoun, F. Identifying Vulnerabilities in APT Attacks: A Simulated Approach. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–4. [Google Scholar]
- FireEye, M-Trends. 2022. Available online: https://content.fireeye.com/m-trends/rpt-m-trends-2022. (accessed on 5 January 2023).
- Esfahani, A.; Mantas, G.; Barcelos, M.; Saghezchi, F.B.; Sucasas, V.; Bastos, J.; Rodriguez, J. Security Framework for the Semiconductor Supply Chain Environment. In Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Victory, S., Georggios, M., Eds.; Springer: Cham, Switzerland, 2019; Volume 263, pp. 159–168. [Google Scholar]
- Kim, N.; Lee, S.; Cho, H.; Kim, B.-I.; Jun, M. Design of a Cyber Threat Information Collection System for Cyber Attack Correlation. In Proceedings of the 2018 International Conference on Platform Technology and Service (PlatCon), Jeju, Republic of Korea, 29–31 January 2018; pp. 1–6. [Google Scholar]
- Moon, D.; Pan, S.B.; Kim, I. Host-Based Intrusion Detection System for Secure Human-Centric Computing. J Supercomput 2016, 72, 2520–2536. [Google Scholar] [CrossRef]
- Kim, Y.; Kim, I. Involvers Behavior-based Modeling in Cyber Targeted Attack. In Proceedings of the Eighth International Conference on Emerging Security Information, Systems and Technologies (SECURWARE), Lisbon, Portugal, 16–20 November 2014. [Google Scholar]
- Jonathan, A.P.; Kim, K.H.; Park, J.-H.; Kim, C.-H.; Lee, H.-J. Analysis of the 2013.3.20 South Korea APT Attack. In Proceedings of the Korean Institute of Information and Commutation Sciences Conference, Mokpo, Republic of Korea, 24–25 May 2013; pp. 249–252. [Google Scholar]
- Park, D.-W. Preemptive Response Strategy for Attacker Origin for National Cybersecurity. Int. Inf. Inst. Inf. 2018, 21, 277–285. [Google Scholar]
- Kim, Y.S.; Kim, I.; Park, N. Analysis of cyber attacks and security intelligence. In Mobile, Ubiquitous, and Intelligent Computing; Springer: Berlin/Heidelberg, Germany, 2014; pp. 489–494. [Google Scholar]
- Agham, V. Unified threat management. Int. Res. J. Eng. Technol. 2016, 3, 32–36. [Google Scholar]
- McAfee, Gold Dragon Widens Olympics Malware Attacks, Gains Permanent Presence on Victims’ Systems. 2018. Available online: https://vxug.fakedoma.in/archive/APTs/2018/2018.02.02/Gold%20Dragon.pdf. (accessed on 25 January 2023).
- Sharma, R.; Arya, R. Secure transmission technique for data in IoT edge computing infrastructure. Complex Intell. Syst. Nov. 2021, 8, pp. 3817–3832. [Google Scholar] [CrossRef]
- Swain, S.C. Cybersecurity Threats and Technology Adoption in the Indian Banking Sector: A Study of Retail Banking Customers of Bhubaneswar. In Strategies for e-Service, e-Governance, and Cybersecurity: Challenges and Solutions for Efficiency and Sustainability; CRC Press: Boca Raton, FL, USA, 2021. [Google Scholar]
- Vardalaki, A.; Vlachos, V. Emerging Malware Threats: The Case of Ransomware. In Cybersecurity Issues in Emerging Technologies; CRC Press: Boca Raton, FL, USA, 2021; pp. 153–170. [Google Scholar]
- Ghafir, I.; Prenosil, V.; Hammoudeh, M.; Aparicio-Navarro, F.J.; Rabie, K.; Jabban, A. Disguised executable files in spear-phishing emails: Detecting the point of entry in advanced persistent threat. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems (ICFNDS), New York, NY, USA, 26–27 June 2018. [Google Scholar]
- Heartfield, R.; Loukas, G. Protection against semantic social engineering attacks. In Versatile Cybersecurity; Maruro, C., Gaurav, S., Eds.; Springer: Cham, Switzerland, 2018; Volume 72, pp. 99–140. [Google Scholar]
- Kim, J. North Korea’s cyber attack threat analysis research(Based on the type of attack technology). In Proceedings of the Korean Society of Computer Information Conference, Jeju, South Korea, 16–18 July 2020; pp. 107–110. [Google Scholar]
- Rath, S.; Zografopoulos, I.; Konstantinou, C. Stealthy Rootkit Attacks on Cyber-Physical Microgrids: Poster. In Proceedings of the Twelfth ACM International Conference on Future Energy Systems, Virtual Event, Italy, 22 June 2021; pp. 294–295. [Google Scholar]
- Li, M.; Huang, W.; Wang, Y.; Fan, W.; Li, J. The Study of APT Attack Stage Model. In Proceedings of the 2016 IEEE/ACIS 15th International Conference on Computer and Information Science (ICIS), Okayama, Japan, 26–29 June 2016; pp. 1–5. [Google Scholar]
- Bermejo Higuera, J.; Abad Aramburu, C.; Bermejo Higuera, J.-R.; Sicilia Urban, M.A.; Sicilia Montalvo, J.A. Systematic Approach to Malware Analysis (SAMA). Appl. Sci. 2020, 10, 1360. [Google Scholar] [CrossRef] [Green Version]
- Tan, C.; Wang, Q.; Wang, L.; Zhao, L. Attack Provenance Tracing in Cyberspace: Solutions, Challenges and Future Directions. IEEE Netw. 2019, 33, 174–180. [Google Scholar] [CrossRef]
- Milajerdi, S.; Eshete, B.; Gjomemo, R.; Venkatakrishnan, V.N. ProPatrol: Attack Investigation via Extracted High-Level Tasks. In Information Systems Security; Ganapathy, V., Jaeger, T., Shyamasundar, R.K., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2018; Volume 11281, pp. 107–126. ISBN 978-3-030-05170-9. [Google Scholar]
- Saleem, J.; Hammoudeh, M. Defense Methods Against Social Engineering Attacks. In Computer and Network Security Essentials; Daimi, K., Ed.; Springer International Publishing: Cham, Switzerland, 2018; pp. 603–618. ISBN 978-3-319-58423-2. [Google Scholar]
- Faruki, P.; Laxmi, V.; Gaur, M.S.; Vinod, P. Behavioural Detection with API Call-Grams to Identify Malicious PE Files. In Proceedings of the First International Conference on Security of Internet of Things-SecurIT ’12, Kollam, India; 2012; pp. 85–91. [Google Scholar]
- Shahzad, F.; Shahzad, M.; Farooq, M. In-Execution Dynamic Malware Analysis and Detection by Mining Information in Process Control Blocks of Linux OS. Inf. Sci. 2013, 231, 45–63. [Google Scholar] [CrossRef]
- Sengan, S.; Khalaf, O.I.; Sharma, D.K.; Hamad, A.A. Secured and privacy-based IDS for healthcare systems on E-medical data using machine learning approach. Int. J. Reliab. Qual. Healthcare 2022, 11, 1–11. [Google Scholar] [CrossRef]
- Mehmood, M.; Javed, T.; Nebhen, J.; Abbas, S.; Abid, R.; Bojja, G.R.; Rizwan, M. A hybrid approach for network intrusion detection. Comput. Mater. Contin. 2021, 70, 91–107. [Google Scholar] [CrossRef]
- Otoum, Y.; Liu, D.; Nayak, A. DL-IDS: A deep learning–based intrusion detection framework for securing IoT. Trans. Emerg. Telecommun. Technol. 2019, 33, e3803. [Google Scholar] [CrossRef]
- Ahmed, W.; Shahzad, F.; Javed, A.R.; Iqbal, F.; Ali, L. WhatsApp Network Forensics: Discovering the IP Addresses of Suspects. In Proceedings of the 2021 11th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 19 April 2021; pp. 1–7. [Google Scholar]
- Qureshi, S.; Tunio, S.; Akhtar, F.; Wajahat, A.; Nazir, A.; Ullah, F. Network Forensics: A Comprehensive Review of Tools and Techniques. IJACSA 2021, 12. [Google Scholar] [CrossRef]
- Son, K.H.; Tajine, L.; Won, D. Design for Zombie PCs and APT Attack Detection based on traffic analysis. J. Korea Inst. Inf. Secur. Cryptol. 2014, 24, 491–498. [Google Scholar] [CrossRef]
- Zhao, G.; Xu, K.; Xu, L.; Wu, B. Detecting APT Malware Infections Based on Malicious DNS and Traffic Analysis. IEEE Access 2015, 3, 1132–1142. [Google Scholar] [CrossRef]
- Negi, P.S.; Garg, A.; Lal, R. Intrusion detection and prevention using honeypot network for cloud security. In Proceedings of the 2020 10th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 29–31 January 2020. [Google Scholar]
- Sun, X.; Wang, Y.; Ren, J.; Zhu, Y.; Liu, S. Collecting Internet Malware Based on Client-Side Honeypot. In Proceedings of the 2008 the 9th International Conference for Young Computer Scientists, 18–21 November 2008; pp. 1493–1498. [Google Scholar]
- Zhuge, J.; Holz, T.; Han, X.; Song, C.; Zou, W. Collecting Autonom s Spreading Malware Using High-Interaction Honeypots. In Information and Communications Security; Qing, S., Imai, H., Wang, G., Eds.; Lecture Notes in Computer Science; Springer Berlin Heidelberg: Berlin/Heidelberg, Germany, 2007; Volume 4861, pp. 438–451. [Google Scholar]
- Wang, Y.-M.; Beck, D.; Jiang, X.; Roussev, R.; Verbowski, C.; Chen, S.; King, S. Automated Web Patrol with Strider HoneyMonkeys. In Proceedings of the 2006 Network and Distributed System Security Symposium, San Diego, CA, USA, 3–5 December 2006; pp. 35–39. [Google Scholar]
- Radek, H. The Capture-HPC Client Architecture; Technical report; Victoria University of Wellington: Wellington, New Zealand, 2009. [Google Scholar]
- Ikinci, A.; Holz, T.; Freiling, F. Monkey-spider: Detecting malicious websites with low-interaction honeyclients. Sicherheit 2008, 8, 407–421. [Google Scholar]
- Mohr, G.; Stack, M.; Ranitovic, I.; Avery, D.; Kimpton, M. An Introduction to Heritrix. In Proceedings of the 4th International Web Archiving Workshop, Bath, UK, 16 September 2004; Volume 15, pp. 109–115. [Google Scholar]
- Xie, M.; Wu, Z.; Wang, H. HoneyIM: Fast Detection and Suppression of Instant Messaging Malware in Enterprise-Like Networks. In Proceedings of the Twenty-Third Annual Computer Security Applications Conference (ACSAC 2007), Miami Beach, FL, USA, 10–14 December 2007; pp. 64–73. [Google Scholar]
- Xie, M.; Wu, Z.; Wang, H. Secure Instant Messaging in Enterprise-like Networks. Comput. Netw. 2012, 56, 448–461. [Google Scholar] [CrossRef]
- El Kamel, N.; Eddabbah, M.; Lmoumen, Y.; Touahni, R. A Smart Agent Design for Cyber Security Based on Honeypot and Machine Learning. Secur. Commun. Netw. 2020, 2020, 1–9. [Google Scholar] [CrossRef]
- Devi, B.T.; Shitharth, S.; Jabbar, M.A. An Appraisal over Intrusion Detection Systems in Cloud Computing Security Attacks. In Proceedings of the 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 722–727. [Google Scholar]
- Ghafir, I.; Prenosil, V.; Hammoudeh, M.; Han, L.; Raza, U. Malicious SSL Certificate Detection: A Step Towards Advanced Persistent Threat Defence. In Proceedings of the Proceedings of the International Conference on Future Networks and Distributed Systems, Cambridge, UK, 19 July 2017. [Google Scholar]
- Lee, K.; Oh, I.; Lee, Y.; Lee, H.; Yim, K.; Seo, J. A Study on a Secure USB Mechanism That Prevents the Exposure of Authentication Information for Smart Human Care Services. J. Sens. 2018, 2018, 2089626. [Google Scholar] [CrossRef]
- Jung, W.; Yim, K.; Lee, K. Vulnerability Analysis of a Secure USB Memory: Based on a Commercial Product D. In Advances on Broad-Band Wireless Computing, Communication and Applications; Barolli, L., Ed.; Lecture Notes in Networks and Systems; Springer International Publishing: Cham, Switzerland, 2022; Volume 346, pp. 279–283. [Google Scholar]
- Lee, J.D.M. FingerTool v1.19 in the DM PD065 Secure USB is Susceptible to Improper Authentication by a Replay Attack. The MITRE Corporation. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-26824 (accessed on 23 December 2021).
- Firstbrook, P.; MacDonald, N. A buyers guide to endpoint protection platforms. Available online: https://www.gartner.com/doc/2973617/buyers-guide-endpoint-protection-platform (accessed on 23 December 2021).
- Jung, B.; Kim, T.; Im, E.G. Malware Classification Using Byte Sequence Information. In Proceedings of the 2018 Conference on Research in Adaptive and Convergent Systems, Honolulu, Hawaii, 9 October 2018; pp. 143–148. [Google Scholar]
- Tian, R.; Batten, L.; Islam, R.; Versteeg, S. An Automated Classification System Based on the Strings of Trojan and Virus Families. In Proceedings of the 2009 4th International Conference on Malicious and Unwanted Software (MALWARE), Montreal, QC, USA, 13–14 October 2009; pp. 23–30. [Google Scholar]
- Bilar, D. Opcodes as Predictor for Malware. IJESDF 2007, 1, 156. [Google Scholar] [CrossRef]
- Bonfante, G.; Kaczmarek, M.; Marion, J.-Y. Morphological Detection of Malware. In Proceedings of the 2008 3rd International Conference on Malicious and Unwanted Software (MALWARE), Fairfax, VI, USA, 13 October 2008; pp. 1–8. [Google Scholar]
- Pektaş, A.; Eriş, M.; Acarman, T. Proposal of N-Gram Based Algorithm for Malware Classification. In Proceedings of the the Fifth International Conference on Emerging Security Information, Systems and Technologies, Nice/Saint Laurent du Var, France, 21–27 August 2011; pp. 7–13. [Google Scholar]
- Santos, I.; Brezo, F.; Nieves, J.; Penya, Y.K.; Sanz, B.; Laorden, C.; Bringas, P.G. Idea: Opcode-Sequence-Based Malware Detection. In Engineering Secure Software and Systems; Massacci, F., Wallach, D., Zannone, N., Eds.; Lecture Notes in Computer Science; Springer Berlin Heidelberg: Berlin/Heidelberg, Germany, 2010; Volume 5965, pp. 35–43. ISBN 978-3-642-11746-6. [Google Scholar]
- Liu, Z.; Japkowicz, N.; Wang, R.; Cai, Y.; Tang, D.; Cai, X. A Statistical Pattern Based Feature Extraction Method on System Call Traces for Anomaly Detection. Inf. Softw. Technol. 2020, 126, 106348. [Google Scholar] [CrossRef]
- Zhou, L.; Liu, F. Research on Computer Network Security Based on Pattern Recognition. In Proceedings of the SMC’03 Conference Proceedings. 2003 IEEE International Conference on Systems, Man and Cybernetics. Conference Theme-System Security and Assurance (Cat. No.03CH37483), Washington, DC, USA, 8 October 2003; Volume 2, pp. 1278–1283. [Google Scholar]
- Li, P.; Teng, W.-D.; Zheng, W.; Zhang, K.-H. Formalized Answer Extraction Technology Based on Pattern Learning. In Proceedings of the International Forum on Strategic Technology 2010, Ulsan, Republic of Korea, 13–15 October 2010; pp. 236–240. [Google Scholar]
- Shreeranga, P.R.; Vig, A.; Narayana, V.S.A. An Efficient Classification Algorithm Based on Pattern Range Tree Prototypes. In Proceedings of the 10th International Conference on Information Technology (ICIT 2007), Rourkela, Orissa, India, 17–20 December 2007; pp. 50–55. [Google Scholar]
- Egele, M.; Kirda, E.; Kruegel, C. Mitigating Drive-By Download Attacks: Challenges and Open Problems. In iNetSec 2009–Open Research Problems in Network Security; Camenisch, J., Kesdogan, D., Eds.; IFIP Advances in Information and Communication Technology; Springer Berlin Heidelberg: Berlin/Heidelberg, Germany, 2009; Volume 309, pp. 52–62. ISBN 978-3-642-05436-5. [Google Scholar]
- Niki, A. Drive-by Download Attacks: Effects and Detection Methods. Ph.D. thesis, Master’s thesis, Royal Holloway University of London, London, UK, 2009. [Google Scholar]
- Zhou, R.; Pan, J.; Tan, X.; Xi, H. Application of CLIPS Expert System to Malware Detection System. In Proceedings of the 2008 International Conference on Computational Intelligence and Security, Suzhou, China, 13–17 December 2008; pp. 309–314. [Google Scholar]
- Al Daoud, E.; Jebril, I.H.; Zaqaibeh, B. Computer virus strategies and detection methods. J. Open Probl. Comput. Sci. Math. 2008, 1, 29–36. [Google Scholar]
- Dube, T.; Raines, R.; Peterson, G.; Bauer, K.; Grimaila, M.; Rogers, S. Malware Target Recognition via Static Heuristics. Comput. Secur. 2012, 31, 137–147. [Google Scholar] [CrossRef]
- Nissim, N.; Moskovitch, R.; Rokach, L.; Elovici, Y. Novel Active Learning Methods for Enhanced PC Malware Detection in Windows OS. Expert Syst. Appl. 2014, 41, 5843–5857. [Google Scholar] [CrossRef]
- Lu, H.; Wang, X.; Zhao, B.; Wang, F.; Su, J. ENDMal: An Anti-Obfuscation and Collaborative Malware Detection System Using Syscall Sequences. Math. Comput. Model. 2013, 58, 1140–1154. [Google Scholar] [CrossRef]
- Tabarzad, M.A.; Hamzeh, A. A Heuristic Local Community Detection Method (HLCD). Appl. Intell. 2017, 46, 62–78. [Google Scholar] [CrossRef]
- Akhtar, M.S.; Feng, T. Malware Analysis and Detection Using Machine Learning Algorithms. Symmetry 2022, 14, 2304. [Google Scholar] [CrossRef]
- Williams, C. Applications of Genetic Algorithms to Malware Detection and Creation. December 2009. Available online: https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=32fe925452da3a44ba92dc3df051d0ccc9061980 (accessed on 6 July 2021).
- Santos, I.; Brezo, F.; Ugarte-Pedrero, X.; Bringas, P.G. Opcode Sequences as Representation of Executables for Data-Mining-Based Unknown Malware Detection. Inf. Sci. 2013, 231, 64–82. [Google Scholar] [CrossRef]
- Yildiz, O.; Doğru, I.A. Permission-Based Android Malware Detection System Using Feature Selection with Genetic Algorithm. Int. J. Softw. Eng. Knowl. Eng. 2019, 29, 245–262. [Google Scholar] [CrossRef]
- Wang, L.; Gao, Y.; Gao, S.; Yong, X. A New Feature Selection Method Based on a Self-Variant Genetic Algorithm Applied to Android Malware Detection. Symmetry 2021, 13, 1290. [Google Scholar] [CrossRef]
- Sinha, S.; Bailey, M.; Jahanian, F. Shades of Grey: On the Effectiveness of Reputation-Based;Blacklists. In Proceedings of the 2008 3rd International Conference on Malicious and Unwanted Software (MALWARE), Alexandria, VA, USA, 7–8 October 2008; pp. 57–64. [Google Scholar]
- Choi, Y.H.; Han, B.J.; Bae, B.C.; Oh, H.G.; Sohn, K.W. Toward extracting malware features for classification using static and dynamic analysis. Comput. Netw. Technol. 2012, 126–129. [Google Scholar]
- Eskandari, M.; Khorshidpour, Z.; Hashemi, S. HDM-Analyser: A Hybrid Analysis Approach Based on Data Mining Techniques for Malware Detection. J. Comput. Virol. Hack Tech. 2013, 9, 77–93. [Google Scholar] [CrossRef]
- Damodaran, A.; Troia, F.D.; Visaggio, C.A.; Austin, T.H.; Stamp, M. A Comparison of Static, Dynamic, and Hybrid Analysis for Malware Detection. Comput. Virol. Hack Tech. 2017, 13, 1–12. [Google Scholar] [CrossRef]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, H.; Patel, A.; Rajarajan, M. A Survey of Intrusion Detection Techniques in Cloud. J. Netw. Comput. Appl. 2013, 36, 42–57. [Google Scholar] [CrossRef]
- Samsudin, K.; Al-baltah, I.A.; Al-Habshi, M.M. SCARECROW: Scalable Malware Reporting, Detection and Analysis. J. Converg. Inf. Technol. 2013, 8, 1–12. [Google Scholar]
- Qiao, Y.; Yang, Y.; Ji, L.; He, J. Analyzing Malware by Abstracting the Frequent Itemsets in API Call Sequences. In Proceedings of the 2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 265–270. [Google Scholar]
- Park, Y.; Reeves, D.S.; Stamp, M. Deriving Common Malware Behavior through Graph Clustering. Comput. Secur. 2013, 39, 419–430. [Google Scholar] [CrossRef]
- Islam, R.; Tian, R.; Batten, L.M.; Versteeg, S. Classification of Malware Based on Integrated Static and Dynamic Features. J. Netw. Comput. Appl. 2013, 36, 646–656. [Google Scholar] [CrossRef]
- Chen, Z.; Roussopoulos, M.; Liang, Z.; Zhang, Y.; Chen, Z.; Delis, A. Malware Characteristics and Threats on the Internet Ecosystem. J. Syst. Softw. 2012, 85, 1650–1672. [Google Scholar] [CrossRef]
- Salem, M.B.; Hershkop, S.; Stolfo, S.J. A Survey of Insider Attack Detection Research. In Insider Attack and Cyber Security; Stolfo, S.J., Bellovin, S.M., Keromytis, A.D., Hershkop, S., Smith, S.W., Sinclair, S., Eds.; Advances in Information Security; Springer: Boston, MA, USA, 2008; Volume 39, pp. 69–90. ISBN 978-0-387-77321-6. [Google Scholar]
- DeBarr, D.; Ramanathan, V.; Wechsler, H. Phishing Detection Using Traffic Behavior, Spectral Clustering, and Random Forests. In Proceedings of the 2013 IEEE International Conference on Intelligence and Security Informatics, Seattle, WA, USA, 4–7 June 2013; pp. 67–72. [Google Scholar]
- Scheutz, M.; Andronache, V. Architectural Mechanisms for Dynamic Changes of Behavior Selection Strategies in Behavior-Based Systems. IEEE Trans. Syst. Man, Cybern. B 2004, 34, 2377–2395. [Google Scholar] [CrossRef]
- Lauf, A.P.; Peters, R.A.; Robinson, W.H. Embedded Intelligent Intrusion Detection: A Behavior-Based Approach. In Proceedings of the 21st International Conference on Advanced Information Networking and Applications Workshops (AINAW’07), Niagara Falls, ON, Canada; 2007; pp. 816–821. [Google Scholar]
- Moon, D.; Im, H.; Kim, I.; Park, J.H. DTB-IDS: An Intrusion Detection System Based on Decision Tree Using Behavior Analysis for Preventing APT Attacks. J. Supercomput. 2017, 73, 2881–2895. [Google Scholar] [CrossRef]
- Zhao, Y.; Bo, B.; Feng, Y.; Xu, C.; Yu, B. A Feature Extraction Method of Hybrid Gram for Malicious Behavior Based on Machine Learning. Secur. Commun. Netw. 2019, 2019, 1–8. [Google Scholar] [CrossRef]
- Davies, S.R.; Macfarlane, R.; Buchanan, W.J. Differential Area Analysis for Ransomware Attack Detection within Mixed File Datasets. Comput. Secur. 2021, 108, 102377. [Google Scholar] [CrossRef]
- Jung, S.; Won, Y. Ransomware Detection Method Based on Context-Aware Entropy Analysis. Soft Comput. 2018, 22, 6731–6740. [Google Scholar] [CrossRef]
- McIntosh, T.; Jang-Jaccard, J.; Watters, P.; Susnjak, T. The inadequacy of entropy-based ransomware detection. In Proceedings of the International Conference on Neural Information Processing, Sydney, Australia, 12–15 December 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 181–189. [Google Scholar]
- Kang, M.; Won, J.; Park, J.; Kim, J. A CNN-Based Encrypted Data Detection for Ransomware Defense. KIISE Trans. Comput. Pract. 2022, 25, 279–283. [Google Scholar] [CrossRef]
- Wojnowicz, M.; Chisholm, G.; Wolff, M.; Zhao, X. Wavelet Decomposition of Software Entropy Reveals Symptoms of Malicious Code. J. Innov. Digit. Ecosyst. 2016, 3, 130–140. [Google Scholar] [CrossRef]
- Ko, J.; Kwak, J. Accuracy Enhancement of Determining File Encryption Status through Divided Shannon Entropy. In Proceedings of the Korea Information Processing Society Conference, Jeju, Republic of korea, 11 October 2018; pp. 279–281. [Google Scholar]
- Lyda, R.; Hamrock, J. Using Entropy Analysis to Find Encrypted and Packed Malware. IEEE Secur. Privacy Mag. 2007, 5, 40–45. [Google Scholar] [CrossRef]
- Sorokin, I. Comparing Files Using Structural Entropy. J. Comput. Virol. 2011, 7, 259–265. [Google Scholar] [CrossRef]
- Baysa, D.; Low, R.M.; Stamp, M. Structural Entropy and Metamorphic Malware. J. Comput. Virol. Hack Tech. 2013, 9, 179–192. [Google Scholar] [CrossRef] [Green Version]
- Dewan, P.; Kashyap, A.; Kumaraguru, P. Analyzing Social and Stylometric Features to Identify Spear Phishing Emails. In Proceedings of the 2014 APWG Symposium on Electronic Crime Research (eCrime), Birmingham, AL, USA, 23–25 September 2014; pp. 1–13. [Google Scholar]
- Ndibanje, B.; Kim, K.; Kang, Y.; Kim, H.; Kim, T.; Lee, H. Cross-Method-Based Analysis and Classification of Malicious Behavior by API Calls Extraction. Appl. Sci. 2019, 9, 239. [Google Scholar] [CrossRef] [Green Version]
- Trinius, P.; Holz, T.; Gobel, J.; Freiling, F.C. Visual Analysis of Malware Behavior Using Treemaps and Thread Graphs. In Proceedings of the 2009 6th International Workshop on Visualization for Cyber Security, Atlantic City, NJ, USA, 11 October 2009; pp. 33–38. [Google Scholar]
- Nataraj, L.; Karthikeyan, S.; Jacob, G.; Manjunath, B.S. Malware Images: Visualization and Automatic Classification. In Proceedings of the Proceedings of the 8th International Symposium on Visualization for Cyber Security-VizSec’ 11, Pittsburgh, PA, USA, 20 July 2011; pp. 1–7. [Google Scholar]
- Ahmadi, M.; Ulyanov, D.; Semenov, S.; Trofimov, M.; Giacinto, G. Novel Feature Extraction, Selection and Fusion for Effective Malware Family Classification. In Proceedings of the Proceedings of the Sixth ACM Conference on Data and Application Security and Privacy, New Orleans, LA, USA, 9 March 2016; pp. 183–194. [Google Scholar]
- Kancherla, K.; Mukkamala, S. Image Visualization Based Malware Detection. In Proceedings of the 2013 IEEE Symposium on Computational Intelligence in Cyber Security (CICS), Singapore, 16 April 2013; pp. 40–44. [Google Scholar]
- Fredrikson, M.; Jha, S.; Christodorescu, M.; Sailer, R.; Yan, X. Synthesizing Near-Optimal Malware Specifications from Suspicious Behaviors. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA; 2010; pp. 45–60. [Google Scholar]
- Jiang, X.; Xu, D. Profiling Self-Propagating Worms via Behavioral Footprinting. In Proceedings of the 4th ACM workshop on Recurring, Alexandria, VA, USA; 2006; p. 17. [Google Scholar]
- Jiankun, H. Host-Based Anomaly Intrusion Detection. In Handbook of Information and Communication Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 235–255. [Google Scholar]
- Ashoor, A.S.; Gore, S. Intrusion Detection System: Case study. In Proceedings of the International Conference on Advanced Material Engineering, Cairo, Egypt, 9 October 2011; Volume 15, pp. 6–9. [Google Scholar]
- Murtaza, S.S.; Khreich, W.; Hamou-Lhadj, A.; Couture, M. A Host-Based Anomaly Detection Approach by Representing System Calls as States of Kernel Modules. In Proceedings of the 2013 IEEE 24th International Symposium on Software Reliability Engineering (ISSRE), Pasadena, CA, USA, 4–7 November 2013; pp. 431–440. [Google Scholar]
- Kaur, H.; Gill, N. Host Based Anomaly Detection Using Fuzzy Genetic Approach (FGA). IJCA 2013, 74, 5–9. [Google Scholar] [CrossRef]
- Cesare, S.; Xiang, Y. A Fast Flowgraph Based Classification System for Packed and Polymorphic Malware on the Endhost. In Proceedings of the 2010 24th IEEE International Conference on Advanced Information Networking and Applications, Perth, Australia; 2010; pp. 721–728. [Google Scholar]
- Song, D.; Brumley, D.; Yin, H.; Caballero, J.; Jager, I.; Kang, M.G.; Liang, Z.; Newsome, J.; Poosankam, P.; Saxena, P. BitBlaze: A New Approach to Computer Security via Binary Analysis. In Information Systems Security; Sekar, R., Pujari, A.K., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5352, pp. 1–25. [Google Scholar]
- Yoshioka, K.; Hosobuchi, Y.; Orii, T.; Matsumoto, T. Vulnerability in Public Malware Sandbox Analysis Systems. In Proceedings of the 2010 10th IEEE/IPSJ International Symposium on Applications and the Internet, Seoul, Republic of Korea, 19–23 July 2010; pp. 265–268. [Google Scholar]
- Willems, C.; Holz, T.; Freiling, F. Toward automated dynamic malware analysis using cwsandbox. IEEE Secur. Priv. 2007, 5, 32–39. [Google Scholar] [CrossRef]
- Inoue, D.; Yoshioka, K.; Eto, M.; Hoshizawa, Y.; Nakao, K. Automated malware analysis system and its sandbox for revealing malware’s internal and external activities. IEICE Trans. Inf. Syst. 2009, 92, 945–954. [Google Scholar] [CrossRef] [Green Version]
- Miwa, S.; MIYACHI, T.; ETO, M.; YOSHIZUMI, M.; SHINODA, Y. Design and Implementation of an Isolated Sandbox with Mimetic Internet Used to Analyze Malwares. In Proceeding of the 2007 USENIX Conference on Community Workshop on Cyber Security Experimentation and Test, Boston, MA, USA, 6–7 August 2007. [Google Scholar]
- Lee, D. Analysis of Malware Detection Techniques Based on Machine Learning. Master’s Thesis, Department of Convergence Service Security Engineering Graduate School of Soonchunhyang University, Asan, Republic of Korea, 2018. [Google Scholar]
- Rathore, H.; Agarwal, S.; Sahay, S.K.; Sewak, M. Malware Detection Using Machine Learning and Deep Learning. In Big Data Analytics; Mondal, A., Gupta, H., Srivastava, J., Reddy, P., Somayajulu, D., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2018; Volume 11297. [Google Scholar]
- Liu, L.; Wang, B.; Yu, B.; Zhong, Q. Automatic Malware Classification and New Malware Detection Using Machine Learning. Front. Inf. Technol. Electron. Eng. 2017, 18, 1336–1347. [Google Scholar] [CrossRef]
- Bae, S.I.; Lee, G.B.; Im, E.G. Ransomware Detection Using Machine Learning Algorithms. Concurr. Comput. Pr. Exper. 2020, 32, e5422. [Google Scholar] [CrossRef]
- Xu, Z.; Ray, S.; Subramanyan, P.; Malik, S. Malware Detection Using Machine Learning Based Analysis of Virtual Memory Access Patterns. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Lausanne, Switzerland, 27–31 March 2017; pp. 169–174. [Google Scholar]
- Singh, J.; Singh, J. Detection of Malicious Software by Analyzing the Behavioral Artifacts Using Machine Learning Algorithms. Inf. Softw. Technol. 2020, 121, 106273. [Google Scholar] [CrossRef]
- Arslan, R.S.; Doğru, İ.A.; Barişçi, N. Permission-Based Malware Detection System for Android Using Machine Learning Techniques. Int. J. Softw. Eng. Knowl. Eng. 2019, 29, 43–61. [Google Scholar] [CrossRef]
- Win, T.Y.; Tianfield, H.; Mair, Q. Big Data Based Security Analytics for Protecting Virtualized Infrastructures in Cloud Computing. IEEE Trans. Big Data 2018, 4, 11–25. [Google Scholar] [CrossRef]
- Xingyuan, C.H.E.N.; Yuanzhao, G.A.O.; Huilin, T.A.N.G.; Xuehui, D.U. Research progress on big data security technology. Sci. Sin. Inf. 2020, 50, 25–66. [Google Scholar]
- Choi, M.-J.; Bang, J.; Kim, J.; Kim, H.; Moon, Y.-S. All-in-One Framework for Detection, Unpacking, and Verification for Malware Analysis. Secur. Commun. Netw. 2019, 1–16. [Google Scholar] [CrossRef] [Green Version]
| Infection Notice | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 | 2021 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Outside | 94% | 63% | 67% | 69% | 53% | 47% | 38% | 41% | 53% | 41% | 47% |
| Inside | 6% | 37% | 33% | 31% | 47% | 53% | 62% | 59% | 47% | 59% | 53% |
| Attack Step | Attack Techniques |
|---|---|
| Preliminary investigation | Preparation of manipulated websites |
| SQL injection | |
| Web vulnerability | |
| Malware and Spyware | |
| Malware and Spyware | |
| Zero-day vulnerability | |
| Penetration | Mail (phishing, spam, spear phishing) |
| DBD (Drive-By-Download) | |
| Watering hole | |
| Manual attack | |
| Latency | Mail (phishing, spam, spear phishing) |
| DBD (Drive-By-Download) | |
| Watering hole | |
| Internal search | Backdoor |
| Network monitoring and analysis | |
| System monitoring | |
| Internal activity | Keylogger |
| IRC | |
| Interception of password hash values of victim accounts | |
| Eavesdropping on conversations recorded by microphone | |
| Information exposure and leakage |
| Detection Methods | Detection Techniques | ||
|---|---|---|---|
| Security control system | Firewall and web firewall | ||
| Anti-virus | |||
| Intrusion detection system | |||
| Intrusion prevention system | |||
| Network forensic | |||
| APT dedicated solution | Network-based | ||
| Host-based | |||
| Log analysis system | EMS | ||
| SIEM | |||
| Honeypot (client honeypot) | Low interaction client honeypot | ||
| High interaction client honeypot | |||
| Prevention of internal information leakage | |||
| Secure USB | |||
| Spam mail protection system | |||
| Pattern-based detection | Signature-based | String signature | |
| Instruction frequency signature | |||
| CFG signature | |||
| Byte sequence signature | |||
| Misuse detection | Signature analysis | ||
| Expert system | |||
| State transition analysis | |||
| Petri Net | |||
| Malicious URL/IP detection | |||
| Heuristic-based detection | Static heuristic | ||
| Dynamic heuristic | |||
| Negative heuristic | |||
| Genetic algorithm | Wildcard comparison | ||
| Mismatching | |||
| Reputation-based detection | Reputation-based detection | ||
| Behavior-based detection | |||
| Behavior-based detection | Static analysis | ||
| Dynamic analysis | |||
| Hybrid analysis | |||
| System-based | |||
| Network-based | |||
| Integrity check technique | |||
| Behavior monitoring and blocking | Spear phishing email surveillance | ||
| Frequency of occurrence of opcode sequence | |||
| Common behavior graph exhibiting malicious code execution behavior | |||
| Framework based on machine learning methods | |||
| Association with registry and process information | |||
| API call behavior detection | |||
| Entropy-based detection | |||
| Visualization | Tree map-based | ||
| Grayscale binary content | |||
| Function call graph | |||
| Control flow graph | |||
| Behavior dependent graph | |||
| Traffic characteristic | |||
| Anormal behavior detection | |||
| System call sequence state-based detection | |||
| Fuzzy logic and genetic algorithm | |||
| Emulator | |||
| Virtualization-based detection | Sandbox | ||
| Profiling | |||
| Anomalous symptom detection | Data mining | ||
| Statistical method | |||
| Real-time monitoring | |||
| Data analysis-based detection | Big data-based detection | Intelligence on threats | |
| Behavior profiling | |||
| Data and user monitoring | |||
| Application monitoring | |||
| Analysis and interpretation | |||
| Machine learning-based detection | Supervised learning | Artificial neural network (ANN) | |
| Deep neural network (DNN) | |||
| Convolutional neural network (CNN) | |||
| Support vector machine (SVM) | |||
| Unsupervised learning | K-means clustering algorithm | ||
| Reinforcement learning | Q-learning | ||
| Deep Q-Network | |||
| Generative adversarial network (GAN) | |||
| Other detection methods | Packer detection and unpacking | ||
| Malware-clustering technique | |||
| Methods | Information for Detection | Malicious Code Types | Detection Characteristics | Problems | |||||
|---|---|---|---|---|---|---|---|---|---|
| Analyzed Malicious Code | New Malicious Code | Variant Malicious Code | Packing or Encryption | Detection Speed | Detection Rate | False Negative and False Positive | |||
| Pattern | Signature (string, command, sequence, graph) | O | X | X | X | Fast | Analyzed malicious code: High New malicious code: Low Variant malicious code: Low | Low | Update rules and policies required pre-analysis |
| Heuristic | Behavior (file, registry, network communication, resource usage) | O | X | O | X | Fast | Analyzed malicious code: High New malicious code: Low Variant malicious code: High | High | Need for definition of similarity comparison Require pre-analysis |
| Reputation | Reputation (date of first discovery, number of users, number of suspicious actions) | O | Δ | Δ | X | Fast | Analyzed malicious code: High New malicious code: Low Variant malicious code: Medium | High | Need for agent installation of reputation collection Not applicable to network traffic |
| Behavior | Behavior (system, network, call flow and correlation) | O | O | O | Δ | Late | Analyzed malicious code: High New malicious code: High Variant malicious code: High | High | Difficult to detect applied anti-debugging and anti-virtual machine techniques Difficult to detect APT attack; high cost and time spent transforming data |
| Visual information (tree map, binary contents, FCG, CFG, BDG) | O | O | O | Δ | Late | Analyzed malicious code: High New malicious code: High Variant malicious code: High | Medium | ||
| Anomalous symptom | Log (correlation) | O | O | O | X | Late | Analyzed malicious code: High New malicious code: High Variant malicious code: High | Medium | Exposed to threats when real-time processing is disabled Difficult to analyze and detect in high-speed traffic |
| Big data | Traffic and Log (probability, statistics) | Δ | Δ | Δ | Δ | Late | Analyzed malicious code: Medium New malicious code: Medium Variant malicious code: Medium | Medium | Requires a lot of time for learning data Performance difference according to the quantity and quality of training data |
| Machine learning | All information (signature, behavior, visual data, reputation, log, traffic) | O | O | O | O | Fast | Analyzed malicious code: High New malicious code: High Variant malicious code: High | Low | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, K.; Lee, J.; Yim, K. Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack. Appl. Sci. 2023, 13, 2894. https://doi.org/10.3390/app13052894
Lee K, Lee J, Yim K. Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack. Applied Sciences. 2023; 13(5):2894. https://doi.org/10.3390/app13052894
Chicago/Turabian StyleLee, Kyungroul, Jaehyuk Lee, and Kangbin Yim. 2023. "Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack" Applied Sciences 13, no. 5: 2894. https://doi.org/10.3390/app13052894
APA StyleLee, K., Lee, J., & Yim, K. (2023). Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack. Applied Sciences, 13(5), 2894. https://doi.org/10.3390/app13052894






