Aspects of Cyber Security in Autonomous and Connected Vehicles
Abstract
:1. Introduction
- We have illustrated the bibliometric survey and reviewed the collected data from the Scopus database.
- Further, we have classified the various attacks in autonomous and connected vehicles.
- Moreover, we have researched various defenses for the attacks on the classified regions as well as recommended a few future works.
2. Related Work
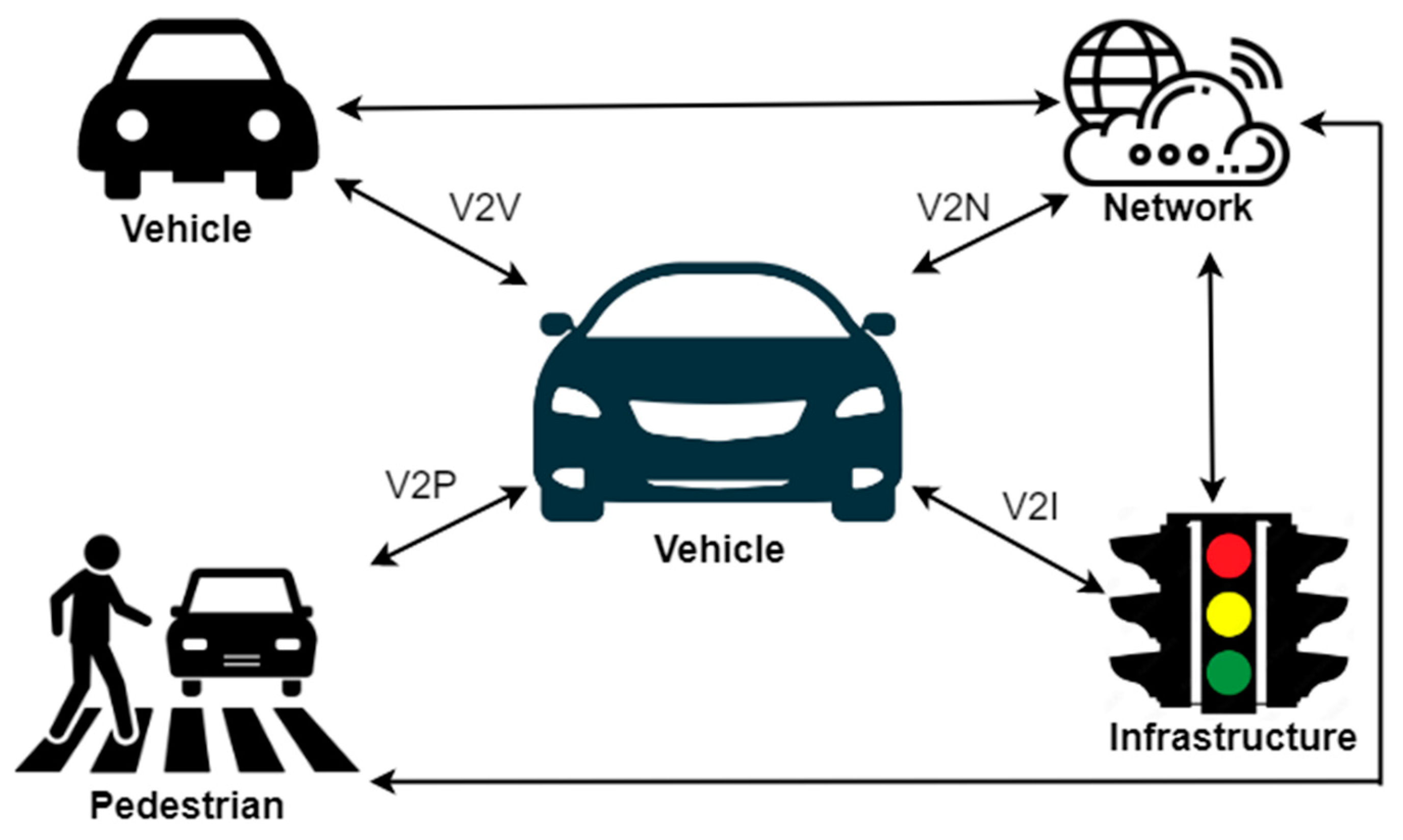
3. Domain Analysis
4. Autonomous and Connected Vehicle
4.1. Safety Systems
4.2. Connectivity
4.3. Diagnostics
5. Attacks on Autonomous and Connected Vehicle
5.1. Attacks on Safety Systems
5.2. Attacks on Connectivity
5.3. Attacks on Diagnostics
| Autonomous and Connected Vehicle Classification | Sub-Systems | Vulnerable Parts or Systems | Attacks |
|---|---|---|---|
| Safety systems | ASS | FMCW radar | Spoofing of radar [51] |
| Wheel speed sensor of ABS | Disruptive attack and spoofing attack [52] | ||
| TPMS | Eavesdropping attack [53] | ||
| GPS | Location spoofing [54] | ||
| Lidar | Replay attack [55], relay attack [18], blinding attack [56], DoS attack [50] | ||
| Ultrasonic sensor | Blind spot exploitation attacks [57], sensor interference attacks [57] | ||
| Camera | Blinding attack [18], phantom attack [75,76] | ||
| Connectivity | V2X | Communication channel | DoS attack [58,59], sybil attack [60], impersonation attack [60] |
| Network or transport layer | Replay attack [16], data falsification attack [64,65], eavesdropping attacks [66] | ||
| Routing protocols | Black hole attack [61], grey hole attack [62], wormhole attack [63] | ||
| Smart features | Key less entry system | Password attack [67], keyless entry attacks [16], key fob attacks [16] | |
| In-vehicle | CAN bus | Frame sniffing attack [68], frame falsifying attack [11] | |
| Ethernet | CAM attack [69] | ||
| LIN bus | False frame attack [70] | ||
| FlexRay | Full and target DoS attack [71] | ||
| Diagnostics | OBD port | In-vehicle buses | In-vehicle access attack [72,73] |
| CAN bus | frame sniffing [73] | ||
| frame injection [73] | |||
| FOTA | Firmware | Control override attacks [74] | |
| Spoofing attack [72] |
6. Defenses or Countermeasures for Autonomous and Connected Vehicles
6.1. Defenses for V2X
6.1.1. Symmetric and Asymmetric Encryption
6.1.2. Intrusion Detection Systems (IDS)
6.1.3. Smart Features Defenses
6.1.4. In-Vehicle Connectivity Defenses
6.2. Defenses for Safety Systems
6.2.1. Countermeasures on Radar and GPS
6.2.2. Countermeasures on TPMS and WSS
6.2.3. Countermeasures on Lidar
6.2.4. Countermeasures on Ultrasonic Sensors and Camera
6.3. Defenses for Diagnostics
| Autonomous and Connected Vehicle Classification | Sub-Systems | Defenses or Countermeasures |
|---|---|---|
| Safety systems | ASS | Filter method [96], STCR [97], PyCRA [101], anonymity encryption [100], signal encryption [98], side channel approach [102], increasing objects [18], camera integration [102], inferred light filters [18], photochromic lenses [18] |
| Connectivity | V2X | 2FLIP [77], SAKMP [80], GSIS [85], novel IDS [89], TACKs [83], AECFV [91], PACP [78], domain aware IDS [92], ECDSA [79], PPGCV [82], TARI [84], |
| Smart features | Multifactor authentication [93], cryptography [16] | |
| In-vehicle | AES encryption [68], domain aware IDS [92], CNN IDS [69], secure ECU [94], gateway firewall [95] | |
| Diagnostics | OBD port | RBAC [47], balanced approach [103] |
| FOTA | secure protocol [104], ECU self-verification [105] |
7. Result of Analysis
8. Recommendations and Scope
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Patsakis, C.; Dellios, K.; Bouroche, M. Towards a distributed secure in-vehicle communication architecture for modern vehicles. Comput. Secur. 2014, 40, 60–74. [Google Scholar] [CrossRef]
- Alam, M.S. Securing vehicle Electronic Control Unit (ECU) communications and stored data. Ph.D. Dissertation, Queen’s University, Kingston, ON, Canada, 2018. [Google Scholar]
- Abbasi, R.; Bashir, A.K.; Alyamani, H.J.; Amin, F.; Doh, J.; Chen, J. Lidar point cloud compression, processing and learning for au-tonomous driving. IEEE Trans. Intell. Transp. Syst. 2022, 24, 962–979. [Google Scholar] [CrossRef]
- Abbasi, R.; Faseeh Qureshi, N.M.; Hassan, H.; Saba, T.; Rehman, A.; Luo, B.; Bashir, A.K. Generalized PVO-based dynamic block re-versible data hiding for secure transmission using firefly algorithm. Trans. Emerg. Telecommun. Technol. 2022, 33, e3680. [Google Scholar]
- Maphathe, B.F.; Thakur, P.; Singh, G.; Iddi, H.E. The Terahertz Channel Modeling in Internet of Multimedia Design In-Body Antenna. Int. J. E-Health Med. Commun. 2022, 13, 1–17. [Google Scholar] [CrossRef]
- Hao, J.; Han, G. On the Modeling of Automotive Security: A Survey of Methods and Perspectives. Future Internet 2020, 12, 198. [Google Scholar] [CrossRef]
- Thakur, P.; Singh, G. Security and interference management in the cognitive-inspired Internet of Medical Things. In Intelligent Data Security Solutions for e-Health Applications; Academic Press: Cambridge, MA, USA, 2020; pp. 131–149. [Google Scholar] [CrossRef]
- Juliussen, E. The future of automotive telematics. In Business Briefing: Global Automotive Manufacturing & Technology; Business Briefings Ltd.: London, UK, 2003; pp. 1–4. [Google Scholar]
- Mudhivarthi, B.R.; Thakur, P. Integration of artificial intelligence in robotic vehicles: A bibliometric analysis. Paladyn, J. Behav. Robot. 2022, 13, 110–120. [Google Scholar] [CrossRef]
- Rizvi, S.; Willet, J.; Perino, D.; Marasco, S.; Condo, C. A Threat to Vehicular Cyber Security and the Urgency for Correction. Procedia Comput. Sci. 2017, 114, 100–105. [Google Scholar] [CrossRef]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar]
- Miller, C.; Valasek, C. Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015, 91, 1–91. [Google Scholar]
- Nie, S.; Liu, L.; Du, Y. Free-fall: Hacking tesla from wireless to can bus. Brief. Black Hat USA 2017, 25, 1–6. [Google Scholar]
- Khatri, N.; Shrestha, R.; Nam, S. Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain. Electronics 2021, 10, 893. [Google Scholar] [CrossRef]
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and Countermeasures for In-Vehicle Networks. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A Survey on Cyber-Security of Connected and Autonomous Vehicles (CAVs). IEEE Trans. Intell. Transp. Syst. 2021, 23, 6240–6259. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, S.; Sun, W.; Shi, Y. In-Vehicle Network Attacks and Countermeasures: Challenges and Future Directions. IEEE Netw. 2017, 31, 50–58. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Sugunaraj, N.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity Attacks in Vehicular Sensors. IEEE Sens. J. 2020, 20, 13752–13767. [Google Scholar] [CrossRef]
- Kumar, A.D.; Chebrolu, K.N.; KP, S. A brief survey on autonomous vehicle possible attacks, exploits and vulnerabilities. arXiv 2018, arXiv:1810.04144. [Google Scholar]
- Dibaei, M.; Zheng, X.; Jiang, K.; Maric, S.; Abbas, R.; Liu, S.; Zhang, Y.; Deng, Y.; Wen, S.; Zhang, J.; et al. An overview of attacks and defences on intelligent connected vehicles. arXiv 2019, arXiv:1907.07455. [Google Scholar]
- Luo, F.; Jiang, Y.; Zhang, Z.; Ren, Y.; Hou, S. Threat Analysis and Risk Assessment for Connected Vehicles: A Survey. Secur. Commun. Netw. 2021, 2021, 1263820. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Jiang, K.; Abbas, R.; Liu, S.; Zhang, Y.; Xiang, Y.; Yu, S. Attacks and defences on intelligent connected vehicles: A survey. Digit. Commun. Netw. 2020, 6, 399–421. [Google Scholar] [CrossRef]
- Al-Sabaawi, A.; Al-Dulaimi, K.; Foo, E.; Alazab, M. Addressing Malware Attacks on Connected and Autonomous Vehicles: Recent Techniques and Challenges. In Malware Analysis Using Artificial Intelligence and Deep Learning; Springer: Berlin/Heidelberg, Germany, 2020; pp. 97–119. [Google Scholar] [CrossRef]
- Cui, J.; Liew, L.S.; Sabaliauskaite, G.; Zhou, F. A review on safety failures, security attacks, and available countermeasures for autonomous vehicles. Ad Hoc Netw. 2018, 90, 101823. [Google Scholar] [CrossRef]
- Hamdane, H.; Serre, T.; Masson, C.; Anderson, R. Issues and challenges for pedestrian active safety systems based on real world accidents. Accid. Anal. Prev. 2015, 82, 53–60. Available online: https://www.sciencedirect.com/science/article/pii/S0001457515001979 (accessed on 17 December 2021). [CrossRef] [Green Version]
- Rödel, C.; Stadler, S.; Meschtscherjakov, A.; Tscheligi, M. Towards autonomous cars: The effect of autonomy levels on acceptance and user experience. In Proceedings of the 6th International Conference on Automotive User Interfaces and Interactive Vehicular Applications, Seattle, WA, USA, 17–19 September 2014; pp. 1–8. [Google Scholar]
- Kaur, G.; Kumar, D. Lane detection techniques: A review. Int. J. Comput. Appl. 2015, 112, 4–8. [Google Scholar]
- Bhasin, K. A Review Paper on Anti-Lock Braking System (ABS) and its Future Scope. Int. J. Res. Appl. Sci. Eng. Technol. 2019, 7, 372–375. [Google Scholar] [CrossRef]
- Vahidi, A.; Eskandarian, A. Research advances in intelligent collision avoidance and adaptive cruise control. IEEE Trans. Intell. Transp. Syst. 2003, 4, 143–153. [Google Scholar] [CrossRef] [Green Version]
- Udugu, K.; Saddala, V.R.; Lingan, S. Active and Passive Safety: An Overview on Establishing Safety Assessment Standards in India. SAE Tech. Pap. 2016, 1. [Google Scholar] [CrossRef]
- Singh, G.; Thakur, P. Spectrum Sharing in Cognitive Radio Networks: Towards Highly Connected Environments; John Wiley & Sons:: Hoboken, NJ, USA, 2021. [Google Scholar]
- Perales, M.A.; Kebriaei, P.; Kean, L.S.; Sadelain, M. Building a safer and faster CAR: Seatbelts, airbags, and CRISPR. Biol. Blood Marrow Transplant. 2018, 24, 27–31. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wang, J.; Shao, Y.; Ge, Y.; Yu, R. A Survey of Vehicle to Everything (V2X) Testing. Sensors 2019, 19, 334. [Google Scholar] [CrossRef] [Green Version]
- Mishra, P.; Thakur, P.; Singh, G. Sustainable Smart City to Society 5.0: State-of-the-Art and Research Challenges. SAIEE Afr. Res. J. 2022, 113, 152–164. [Google Scholar] [CrossRef]
- Nguyen, T.; Lechner, B.; Wong, Y.D. Response-based methods to measure road surface irregularity: A state-of-the-art review. Eur. Transp. Res. Rev. 2019, 11, 1–18. [Google Scholar] [CrossRef] [Green Version]
- Ali, I.; Li, F. An efficient conditional privacy-preserving authentication scheme for Vehicle-To-Infrastructure communication in VANETs. Veh. Commun. 2019, 22, 100228. [Google Scholar] [CrossRef]
- Ameen, H.A.; Mahamad, A.K.; Saon, S.; Nor, D.M.; Ghazi, K. A review on vehicle to vehicle communication system applications. Indones. J. Electr. Eng. Comput. Sci. 2020, 18, 188–198. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. Security and Privacy in Vehicular Ad Hoc Network and Vehicle Cloud Computing: A Survey. Wirel. Commun. Mob. Comput. 2020, 2020, 1–25. [Google Scholar] [CrossRef] [Green Version]
- Tong, W.; Hussain, A.; Bo, W.X.; Maharjan, S. Artificial Intelligence for Vehicle-to-Everything: A Survey. IEEE Access 2019, 7, 10823–10843. [Google Scholar] [CrossRef]
- Kassabalidis, I.; El-Sharkawi, M.; Marks, R.; Arabshahi, P.; Gray, A. Swarm intelligence for routing in communication networks. IEEE Glob. Telecommun. Conf. 2002, 6, 3613–3617. [Google Scholar] [CrossRef]
- Swarnkar, R.; Harikrishnan, R.; Thakur, P.; Singh, G. Electric Vehicle Lithium-ion Battery Ageing Analysis Under Dynamic Con-dition: A Machine Learning Approach. SAIEE Afr. Res. J. 2022, 114, 4–13. [Google Scholar] [CrossRef]
- Wang, S.-S. A BLE-Based Pedestrian Navigation System for Car Searching in Indoor Parking Garages. Sensors 2018, 18, 1442. [Google Scholar] [CrossRef]
- Jadhav, S.; Kshirsagar, D. A survey on security in automotive networks. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–6. [Google Scholar]
- Ngene, C.E.; Thakur, P.; Singh, G. Free-space optical link optimization in visible light communication system. J. Opt. Commun. 2021. [Google Scholar] [CrossRef]
- Inambao, F.; Cunden, K. Offshore wind resource assessment off the South African coastline. Int. J. Me-Chanical Eng. Technol. 2019, 10, 95–119. [Google Scholar]
- Rimpas, D.; Papadakis, A.; Samarakou, M. OBD-II sensor diagnostics for monitoring vehicle operation and consumption. Energy Rep. 2019, 6, 55–63. [Google Scholar] [CrossRef]
- Ammar, M.; Janjua, H.; Thangarajan, A.S.; Crispo, B.; Hughes, D. Securing the on-board diagnostics port (obd-ii) in vehicles. SAE Int. J. Transp. Cybersecur. Priv. 2020, 2, 83–106. [Google Scholar] [CrossRef]
- John, A.A.; Thakur, P.; Singh, G. Potential, concepts, and key advances for a ubiquitous adaptive indigenous microengineering and nanoengineering in 6G network. Int. J. Commun. Syst. 2022. [Google Scholar] [CrossRef]
- La Manna, M.; Treccozzi, L.; Perazzo, P.; Saponara, S.; Dini, G. Performance evaluation of attribute-based encryption in automotive embedded platform for secure software over-the-air update. Sensors 2021, 21, 515. [Google Scholar] [CrossRef] [PubMed]
- Salfer, M.; Eckert, C. Attack surface and vulnerability assessment of automotive electronic control units. In Proceedings of the 2015 12th International Joint Conference on e-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015; Volume 4, pp. 317–326. [Google Scholar]
- Komissarov, R.; Wool, A. Spoofing attacks against vehicular FMCW radar. In Proceedings of the 5th Workshop on Attacks and Solutions in Hardware Security, Seoul, Republic of Korea, 19 November 2021; pp. 91–97. [Google Scholar]
- Shoukry, Y.; Martin, P.; Tabuada, P.; Srivastava, M. Non-invasive spoofing attacks for anti-lock braking systems. In Proceedings of the Cryptographic Hardware and Embedded Systems-CHES 2013: 15th International Workshop, Santa Barbara, CA, USA, 20–23 August 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 55–72. [Google Scholar]
- Rouf, I.; Miller, R.D.; Mustafa, H.A.; Taylor, T.; Oh, S.; Xu, W.; Gruteser, M.; Trappe, W.; Seskar, I. Security and Privacy Vulnerabilities of In-Car Wireless Networks: A Tire Pressure Monitoring System Case Study. In Proceedings of the USENIX Security Symposium, San Jose, CA, USA, 11–13 August 2010; Volume 10. [Google Scholar]
- Lim, K.; Tuladhar, K.M.; Kim, H. Detecting location spoofing using ADAS sensors in VANETs. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11 January 2019; pp. 1–4. [Google Scholar]
- Stottelaar, B.G. Practical Cyber-Attacks on Autonomous Vehicles. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2015. [Google Scholar]
- Shin, H.; Kim, D.; Kwon, Y.; Kim, Y. Illusion and dazzle: Adversarial optical channel exploits against lidars for automotive ap-plications. In Proceedings of the Cryptographic Hardware and Embedded Systems–CHES 2017: 19th International Conference, Taipei, Taiwan, 25–28 September 2017; pp. 445–467. [Google Scholar]
- Lim, B.S.; Keoh, S.L.; Thing, V.L. Autonomous vehicle ultrasonic sensor vulnerability and impact assessment. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 231–236. [Google Scholar]
- Kumar, S.; Mann, K.S. Prevention of DoS Attacks by Detection of Multiple Malicious Nodes in VANETs. In Proceedings of the 2019 International Conference on Automation, Computational and Technology Management, London, UK, 24–26 April 2019; pp. 89–94. [Google Scholar] [CrossRef]
- He, Q.; Meng, X.; Qu, R. Survey on cyber security of CAV. In Proceedings of the 2017 Forum on Cooperative Positioning and Service (CPGPS), Harbin, China, 19–21 May 2017; pp. 351–354. [Google Scholar]
- Appathurai, A.; Manogaran, G.; Chilamkurti, N. Trusted FPGA-based transport traffic inject, impersonate (I2) attacks beaconing in the Internet of Vehicles. IET Netw. 2019, 8, 169–178. [Google Scholar] [CrossRef]
- Albouq, S.S.; Fredericks, E.M. Lightweight detection and isolation of black hole attacks in connected vehicles. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), Atlanta, GA, USA, 5–8 June 2017; pp. 97–104. [Google Scholar]
- Purohit, K.C.; Dimri, S.C.; Jasola, S. Mitigation and Performance Analysis of Routing Protocols Under Black-Hole Attack in Vehicular Ad-hoc Network (VANET). Wirel. Pers. Commun. 2017, 97, 5099–5114. [Google Scholar] [CrossRef]
- Kumar, P.; Verma, S. Detection of wormhole attack in VANET. Natl. J. Syst. Inf. Technol. 2017, 10, 71. [Google Scholar]
- Shukla, R.M.; Sengupta, S. Analysis and detection of outliers due to data falsification attacks in vehicular traffic prediction ap-plication. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York City, NY, USA, 8–10 November 2018; pp. 688–694. [Google Scholar]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Ge, L. Data Integrity Attacks Against Dynamic Route Guidance in Transportation-Based Cyber-Physical Systems: Modeling, Analysis, and Defense. IEEE Trans. Veh. Technol. 2018, 67, 8738–8753. [Google Scholar] [CrossRef]
- Balakrishnan, S.; Wang, P.; Bhuyan, A.; Sun, Z. Modeling and Analysis of Eavesdropping Attack in 802.11ad mmWave Wireless Networks. IEEE Access 2019, 7, 70355–70370. [Google Scholar] [CrossRef]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber Threats Facing Autonomous and Connected Vehicles: Future Challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2014, 16, 1–14. [Google Scholar] [CrossRef]
- Jeong, S.; Jeon, B.; Chung, B.; Kim, H.K. Convolutional neural network-based intrusion detection system for AVTP streams in au-tomotive Ethernet-based networks. Veh. Commun. 2021, 29, 100338. [Google Scholar]
- Takahashi, J.; Aragane, Y.; Miyazawa, T.; Fuji, H.; Yamashita, H.; Hayakawa, K.; Ukai, S.; Hayakawa, H. Automotive Attacks and Countermeasures on LIN-Bus. J. Inf. Process. 2017, 25, 220–228. [Google Scholar] [CrossRef] [Green Version]
- Murvay, P.-S.; Groza, B. Practical Security Exploits of the FlexRay In-Vehicle Communication Protocol. In Risks and Security of Internet and Systems: 13th International Conference, CRiSIS 2018, Arcachon, France, 16–18 October 2018; Revised Selected Papers 13; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 172–187. [Google Scholar] [CrossRef]
- Carsten, P.; Andel, T.R.; Yampolskiy, M.; McDonald, J.T. In-vehicle networks: Attacks, vulnerabilities, and proposed solutions. In Proceedings of the 10th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 7–9 April 2015; pp. 1–8. [Google Scholar]
- Miller, C.; Valasek, C. Adventures in automotive networks and control units. Def Con. 2013, 21, 15–31. [Google Scholar]
- Philipsen, S.G.; Andersen, B.; Singh, B. Threats and attacks to modern vehicles. In Proceedings of the 2021 IEEE International Conference on Internet of Things and Intelligence Systems (IoTaIS), Bandung, Indonesia, 23–24 November 2021; pp. 22–27. [Google Scholar]
- Hodge, C.; Hauck, K.; Gupta, S.; Bennett, J.C. Vehicle Cybersecurity Threats and Mitigation Approaches; National Renewable Energy Lab.(NREL): Golden, CO, USA, 2019. [Google Scholar] [CrossRef]
- Schaffer, T.; Glaser, A.; Rao, S.; Franzon, P. A flip-chip implementation of the Data Encryption Standard (DES). In Proceedings of the 1997 IEEE Multi-Chip Module Conference, Santa Cruz, CA, USA, 4-5 February 1997; pp. 13–17. [Google Scholar]
- Wang, F.; Xu, Y.; Zhang, H.; Zhang, Y.; Zhu, L. 2FLIP: A Two-Factor Lightweight Privacy-Preserving Authentication Scheme for VANET. IEEE Trans. Veh. Technol. 2015, 65, 896–911. [Google Scholar] [CrossRef]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An Efficient Pseudonymous Authentication-Based Conditional Privacy Protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Knezevic, M.; Nikov, V.; Rombouts, P. Low-Latency ECDSA Signature Verification—A Road Toward Safer Traffic. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2016, 24, 3257–3267. [Google Scholar] [CrossRef]
- Tan, H.; Ma, M.; Labiod, H.; Boudguiga, A.; Zhang, J.; Chong, P.H.J. A Secure and Authenticated Key Management Protocol (SA-KMP) for Vehicular Networks. IEEE Trans. Veh. Technol. 2016, 65, 9570–9584. [Google Scholar] [CrossRef] [Green Version]
- Calandriello, G.; Papadimitratos, P.; Hubaux, J.P.; Lioy, A. Efficient and robust pseudonymous authentication in VANET. In Proceedings of the Fourth ACM International Workshop on Vehicular ad Hoc Networks, Montréal, QC, Canada, 10 September 2007; pp. 19–28. [Google Scholar]
- Wasef, A.; Shen, X. PPGCV: Privacy Preserving Group Communications Protocol for Vehicular Ad Hoc Networks. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 1458–1463. [Google Scholar] [CrossRef]
- Studer, A.; Shi, E.; Bai, F.; Perrig, A. TACKing together efficient authentication, revocation, and privacy in VANETs. In Proceedings of the 2009 6th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, Rome, Italy, 22–26 June 2009; pp. 1–9. [Google Scholar]
- Chen, R.; Ma, D.; Regan, A. TARI: Meeting delay requirements in VANETs with efficient authentication and revocation. In Proceedings of the 2nd International Conference on Wireless Access in Vehicular Environments (WAVE), Shanghai, China, 21–22 December 2009. [Google Scholar]
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Zaidi, K.; Milojevic, M.B.; Rakocevic, V.; Nallanathan, A.; Rajarajan, M. Host-Based Intrusion Detection for VANETs: A Statistical Approach to Rogue Node Detection. IEEE Trans. Veh. Technol. 2015, 65, 6703–6714. [Google Scholar] [CrossRef] [Green Version]
- Dhaliwal, S.S.; Nahid, A.-A.; Abbas, R. Effective Intrusion Detection System Using XGBoost. Information 2018, 9, 149. [Google Scholar] [CrossRef] [Green Version]
- Bissmeyer, N.; Stresing, C.; Bayarou, K.M. Intrusion detection in VANETs through verification of vehicle movement data. In Proceedings of the 2010 IEEE Vehicular Networking Conference, Jersey City, NJ, USA, 13–15 December 2010; pp. 166–173. [Google Scholar] [CrossRef]
- Tomandl, A.; Fuchs, K.P.; Federrath, H. REST-Net: A dynamic rule-based IDS for VANETs. In Proceedings of the 2014 7th IFIP Wireless and Mobile Networking Conference (WMNC), Vilamoura, Portugal, 20–22 May 2014; pp. 1–8. [Google Scholar]
- Yu, B.; Xu, C.Z.; Xiao, B. Detecting sybil attacks in VANETs. J. Parallel Distrib. Comput. 2013, 73, 746–756. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M. An accurate and efficient collaborative intrusion detection framework to secure vehicular networks. Comput. Electr. Eng. 2015, 43, 33–47. [Google Scholar] [CrossRef]
- Markovitz, M.; Wool, A. Field classification, modeling and anomaly detection in unknown CAN bus networks. Veh. Commun. 2017, 9, 43–52. [Google Scholar] [CrossRef]
- Khankari, N.B.; Kale, G.V. One time password generation for multifactor authentication using graphical password. Int. J. Eng. Res. Gen. Sci. 2020, 3, 489–494. [Google Scholar]
- Larson, U.E.; Nilsson, D.K.; Jonsson, E. An approach to specification-based attack detection for in-vehicle networks. In Proceedings of the 2008 IEEE Intelligent Vehicles Symposium, Eindhoven, The Netherlands, 4–6 June 2008; pp. 220–225. [Google Scholar] [CrossRef]
- Wolf, M.; Weimerskirch, A.; Paar, C. Security in automotive bus systems. In Proceedings of the Workshop on Embedded Security in Cars, Bochum, Germany, 10–11 November 2004; pp. 1–13. [Google Scholar]
- Lu, G.; Zeng, D.; Tang, B. Anti-jamming filtering for DRFM repeat jammer based on stretch processing. In Proceedings of the 2010 2nd International Conference on Signal Processing Systems, Dalian, China, 5–7 July 2010; Volume 1, pp. V1–V78. [Google Scholar]
- Kapoor, P.; Vora, A.; Kang, K.D. Detecting and mitigating spoofing attack against an automotive radar. In Proceedings of the 2018 IEEE 88th Ve-hicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–6. [Google Scholar]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Kolodgie, A.; Berges, P.; Burrow, R.; Carman, M.; Collins, J.; Bair, S.; Moy, G.D.; Ernst, J.M.; Michaels, A.J. Enhanced TPMS security through acceleration timed transmissions. In Proceedings of the MILCOM 2017-2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 23–25 October 2017; pp. 35–39. [Google Scholar]
- Amoozadeh, M.; Raghuramu, A.; Chuah, C.-N.; Ghosal, D.; Zhang, H.M.; Rowe, J.; Levitt, K. Security vulnerabilities of connected vehicle streams and their impact on cooperative driving. IEEE Commun. Mag. 2015, 53, 126–132. [Google Scholar] [CrossRef] [Green Version]
- Shoukry, Y.; Martin, P.; Yona, Y.; Diggavi, S.; Srivastava, M. Pycra: Physical challenge-response authentication for active sensors under spoofing attacks. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1004–1015. [Google Scholar]
- Matsumura, R.; Sugawara, T.; Sakiyama, K. A secure LiDAR with AES-based side-channel fingerprinting. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018; pp. 479–482. [Google Scholar]
- Markham, T.R.; Chernoguzov, A. A balanced approach for securing the OBD-II port. SAE Int. J. Passeng. Cars-Electron. Electr. Syst. 2017, 10, 390–399. [Google Scholar] [CrossRef]
- Nilsson, D.K.; Larson, U.E. Secure firmware updates over the air in intelligent vehicles. In Proceedings of the ICC Workshops-2008 IEEE Interna-tional Conference on Communications Workshops, Beijing, China, 19–23 May 2008; pp. 380–384. [Google Scholar]
- Nilsson, D.K.; Sun, L.; Nakajima, T. A Framework for Self-Verification of Firmware Updates over the Air in Vehicle ECUs. In Proceedings of the 2008 IEEE Globecom Workshops, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5. [Google Scholar]






| Protocols | CAN [43] | LIN [45] | FlexRay [43] | Ethernet [43] |
|---|---|---|---|---|
| Data rate | 1 Mb/s | 20 Kb/s | 5 Mb/s | 40 Gb/s |
| Data field | 8 bytes | 8 bytes | 254 bytes | 1500 bytes |
| Key Element Classification | Type of Division | Attacks | Defenses |
|---|---|---|---|
| Safety | ASS | Spoofing of radar [51] | Filter method [96], STCR [97] |
| Disruptive attack and spoofing attack on WSS [52] | PyCRA [101] | ||
| Eavesdropping attack on TPMS [53] | Anonymity encryption [100] | ||
| GPS location spoofing [54] | Signal encryption [98] | ||
| Lidar replay attack [55] | Side channel approach [102] | ||
| Lidar relay attack [18] | |||
| Lidar blinding attack [56] | |||
| Lidar DoS attack [50] | Increasing objects [18] | ||
| Blind spot exploitation attacks on ultrasonic sensor [57] | Camera integration [102], Algorithms | ||
| Sensor interference attacks on ultrasonic sensor [57] | |||
| Blinding attack on camera [18] | Inferred light filters [18], photochromic lenses [18] | ||
| Phantom attack on camera [75,76] | Model to avoid phantoms [75] | ||
| Connectivity | V2X | DoS attack [58,59] | 2FLIP [77], SAKMP [80], GSIS [85] |
| Impersonation attack [60] | SAKMP [80], novel IDS [89] | ||
| Sybil attack [60] | TACKs [83], AECFV [91] | ||
| Replay attack [16] | PACP [78], SAKMP [80] | ||
| Black hole routing attack [61] | AECFV [91] | ||
| Grey hole routing attack [62] | |||
| Wormhole routing attack [63] | |||
| Data falsification attack [64,65] | Domain aware IDS [92], novel IDS [89] | ||
| Eavesdropping attacks [66] | PACP [78], Tacks [83] | ||
| Smart features | Password attack [67] | Multifactor authentication [93] | |
| Key less entry attacks [16] | cryptography [16] | ||
| Key fob attacks [16] | |||
| In-vehicle | CAN frame sniffing attack [68] | AES encryption [68] | |
| CAN frame falsifying attack [11] | AES encryption [68], Domain aware IDS [92] | ||
| Ethernet CAM attack [69] | CNN IDS [69] | ||
| LIN false frame attack [70] | Secure ECU [94] Domain aware IDS [92], Gateway firewall [95] | ||
| FlexRay full DoS attack [71] | |||
| FlexRay targeted DoS attack [71] | |||
| Diagnostics | OBD port | In-vehicle access attack [72,73] | RBAC [47], balanced approach [103] |
| CAN frame sniffing [73] | |||
| CAN frame injection [73] | |||
| FOTA | Control override attacks [74] | secure protocol [104] | |
| firmware spoofing attack [72] | ECU self-verification [105] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mudhivarthi, B.R.; Thakur, P.; Singh, G. Aspects of Cyber Security in Autonomous and Connected Vehicles. Appl. Sci. 2023, 13, 3014. https://doi.org/10.3390/app13053014
Mudhivarthi BR, Thakur P, Singh G. Aspects of Cyber Security in Autonomous and Connected Vehicles. Applied Sciences. 2023; 13(5):3014. https://doi.org/10.3390/app13053014
Chicago/Turabian StyleMudhivarthi, Bhavesh Raju, Prabhat Thakur, and Ghanshyam Singh. 2023. "Aspects of Cyber Security in Autonomous and Connected Vehicles" Applied Sciences 13, no. 5: 3014. https://doi.org/10.3390/app13053014
APA StyleMudhivarthi, B. R., Thakur, P., & Singh, G. (2023). Aspects of Cyber Security in Autonomous and Connected Vehicles. Applied Sciences, 13(5), 3014. https://doi.org/10.3390/app13053014








