Secure PBFT Consensus-Based Lightweight Blockchain for Healthcare Application
Abstract
:1. Introduction
1.1. Motivation
1.2. Major Contributions and Paper Organization
- We propose using the Eigen trust-based reputation model to verify the reliability of each and every node using a global trust value. The reputation model is related to the node behavior in the system, it also helps in reducing the number of untrusted nodes participating in the consensus process.
- We propose a VRF-based election process to ensure fairness and randomness in electing the primary node from a group of trusted consensus nodes. This process will reduce the communication complexity among nodes and also strengthen the security of the healthcare system.
- The proposed model is tested in a simulated environment and analyzed with the existing PBFT consensus algorithm intents of throughput, latency, and communication overhead. The proposed algorithm results in better performance.
2. Literature Review
3. Proposed Model
3.1. Practical Byzantine Fault Tolerance
3.2. Computation of Node Trust Value Using Eigen Trust Model
- Direct trust value: If there is a direct transaction between Nodep and Nodeq, for example in Figure 3 Node1 to Node2, the direct trust value for Nodep is calculated by considering the satisfactory and unsatisfactory transaction history between p and q as Spq = Satisfactory(p,q) − Unsatisfactory(p,q). After certain transactions, we can normalize it as
- Indirect trust value: When there is no direct transaction between Nodep and Nodeq, we need to compute indirect trust based on transitive trust, considering direct trust and the transaction history represented in Equation (3)
- Global trust value: Each Nodep in the blockchain network has unique global trust value GTi based on the current transaction history. The global trust value of Nodep is computed using the local trust value of all nodes in the network to Nodep, global trust of the current node, and trust value of current Nodev created during the last cycle s−1. The initial global trust value of nodes in the network is GT = 1/n where n is the total number of nodes.
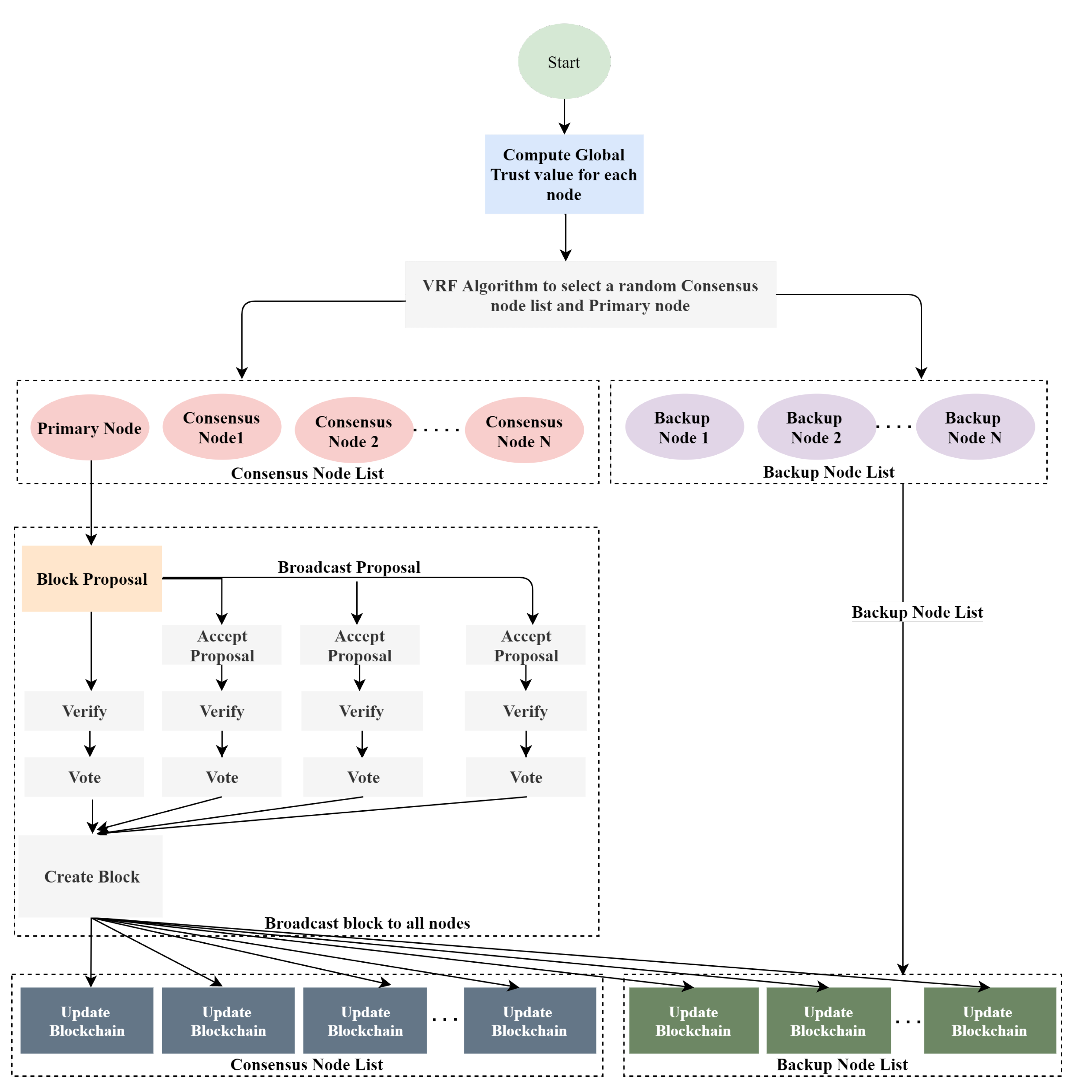
3.3. Node Grouping and Primary Node Selection Using Verifiable Random Function (VRF)
- Step 1:
- Identify the Global Trust value of each node present in the network using the Algorithm 1.
- Step 2:
- Choose a Primary Node using the VRF algorithm and divide the nodes into consensus node list and backup node list using global trust value as parameter.
- Step 3:
- Primary node will execute the PBFT Consensus algorithm using set of consensus nodes.
- Step 4:
- At the end of the consensus mechanism, the primary node will create a block with a valid transaction.
- Step 5:
- Primary node will broadcast the updated block to both consensus node list and backup node list.
| Algorithm 1 Pseudo-code for calculating global trust. |
| Input: , Output: Global trust of |
4. Experimental Results
4.1. Throughput Analysis
4.2. Transaction Latency
4.3. Faulty Nodes
4.4. Communication between Nodes
5. Conclusions and Future Scope
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Maddikunta, P.K.R.; Gadekallu, T.R.; Kaluri, R.; Srivastava, G.; Parizi, R.M.; Khan, M.S. Green communication in IoT networks using a hybrid optimization algorithm. Comput. Commun. 2020, 159, 97–107. [Google Scholar] [CrossRef]
- Ch, R.; Srivastava, G.; Gadekallu, T.R.; Maddikunta, P.K.R.; Bhattacharya, S. Security and privacy of UAV data using blockchain technology. J. Inf. Secur. Appl. 2020, 55, 102670. [Google Scholar] [CrossRef]
- Ratta, P.; Kaur, A.; Sharma, S.; Shabaz, M.; Dhiman, G. Application of blockchain and internet of things in healthcare and medical sector: Applications, challenges, and future perspectives. J. Food Qual. 2021, 2021, 1–20. [Google Scholar] [CrossRef]
- Rejeb, A.; Keogh, J.G.; Treiblmaier, H. Leveraging the internet of things and blockchain technology in supply chain management. Future Internet 2019, 11, 161. [Google Scholar] [CrossRef] [Green Version]
- Wang, Q.; Zhu, X.; Ni, Y.; Gu, L.; Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet Things 2020, 10, 100081. [Google Scholar] [CrossRef]
- Ray, P.P.; Dash, D.; Salah, K.; Kumar, N. Blockchain for IoT-based healthcare: Background, consensus, platforms, and use cases. IEEE Syst. J. 2020, 15, 85–94. [Google Scholar] [CrossRef]
- Reddy Maddikunta, P.K.; Srivastava, G.; Reddy Gadekallu, T.; Deepa, N.; Boopathy, P. Predictive model for battery life in IoT networks. IET Intell. Transp. Syst. 2020, 14, 1388–1395. [Google Scholar] [CrossRef]
- Khan, S.; Lee, W.K.; Hwang, S.O. AEchain: A lightweight blockchain for IoT applications. IEEE Consum. Electron. Mag. 2021, 11, 64–76. [Google Scholar] [CrossRef]
- Bandara, E.; Tosh, D.; Foytik, P.; Shetty, S.; Ranasinghe, N.; De Zoysa, K. Tikiri—Towards a lightweight blockchain for IoT. Future Gener. Comput. Syst. 2021, 119, 154–165. [Google Scholar] [CrossRef]
- Guo, R.; Zhuang, C.; Shi, H.; Zhang, Y.; Zheng, D. A lightweight verifiable outsourced decryption of attribute-based encryption scheme for blockchain-enabled wireless body area network in fog computing. Int. J. Distrib. Sens. Netw. 2020, 16, 1550147720906796. [Google Scholar] [CrossRef]
- Mouha, N. The design space of lightweight cryptography. Cryptol. ePrint Arch. 2015.
- Sultana, M.; Hossain, A.; Laila, F.; Taher, K.A.; Islam, M.N. Towards developing a secure medical image sharing system based on zero trust principles and blockchain technology. BMC Med. Inform. Decis. Mak. 2020, 20, 1–10. [Google Scholar] [CrossRef]
- Meshcheryakov, Y.; Melman, A.; Evsutin, O.; Morozov, V.; Koucheryavy, Y. On performance of PBFT blockchain consensus algorithm for IoT-applications with constrained devices. IEEE Access 2021, 9, 80559–80570. [Google Scholar] [CrossRef]
- Dodis, Y.; Yampolskiy, A. A verifiable random function with short proofs and keys. In Proceedings of the Public Key Cryptography-PKC 2005: 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; pp. 416–431. [Google Scholar]
- Chen, J.; Micali, S. Algorand: A secure and efficient distributed ledger. Theor. Comput. Sci. 2019, 777, 155–183. [Google Scholar] [CrossRef]
- Ismail, L.; Materwala, H.; Zeadally, S. Lightweight blockchain for healthcare. IEEE Access 2019, 7, 149935–149951. [Google Scholar] [CrossRef]
- Manoj, M.; Srivastava, G.; Somayaji, S.R.K.; Gadekallu, T.R.; Maddikunta, P.K.R.; Bhattacharya, S. An incentive based approach for COVID-19 planning using blockchain technology. In Proceedings of the 2020 IEEE Globecom Workshops, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Srivastava, G.; Crichigno, J.; Dhar, S. A light and secure healthcare blockchain for iot medical devices. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; pp. 1–5. [Google Scholar]
- Mohanty, S.N.; Ramya, K.; Rani, S.S.; Gupta, D.; Shankar, K.; Lakshmanaprabu, S.; Khanna, A. An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Future Gener. Comput. Syst. 2020, 102, 1027–1037. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Lei, K.; Zhang, Q.; Xu, L.; Qi, Z. Reputation-based byzantine fault-tolerance for consortium blockchain. In Proceedings of the 2018 IEEE 24th International Conference on Parallel and Distributed Systems (ICPADS), Singapore, 11–13 December 2018; pp. 604–611. [Google Scholar]
- Dwivedi, A.D.; Malina, L.; Dzurenda, P.; Srivastava, G. Optimized blockchain model for internet of things based healthcare applications. In Proceedings of the 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), Budapest, Hungary, 1–3 July 2019; pp. 135–139. [Google Scholar]
- Na, D.; Park, S. Fusion chain: A decentralized lightweight blockchain for IoT security and privacy. Electronics 2021, 10, 391. [Google Scholar] [CrossRef]
- Min, Y.A. The modification of pBFT algorithm to increase network operations efficiency in private blockchains. Appl. Sci. 2021, 11, 6313. [Google Scholar] [CrossRef]
- Li, C.; Zhang, J.; Yang, X.; Youlong, L. Lightweight blockchain consensus mechanism and storage optimization for resource-constrained IoT devices. Inf. Process. Manag. 2021, 58, 102602. [Google Scholar] [CrossRef]
- Xu, X.; Sun, G.; Yu, H. An efficient blockchain pbft consensus protocol in energy constrained iot applications. In Proceedings of the 2021 International Conference on UK-China Emerging Technologies (UCET), Chengdu, China, 4–6 November 2021; pp. 152–157. [Google Scholar]
- Cai, W.; Jiang, W.; Xie, K.; Zhu, Y.; Liu, Y.; Shen, T. Dynamic reputation–based consensus mechanism: Real-time transactions for energy blockchain. Int. J. Distrib. Sens. Netw. 2020, 16, 1550147720907335. [Google Scholar] [CrossRef] [Green Version]
- Kashyap, R.; Arora, K.; Sharma, M.; Aazam, A. Security-Aware ga based practical byzantine fault tolerance for permissioned blockchain. In Proceedings of the 2019 4th International Conference on Control, Robotics and Cybernetics (CRC), Tokyo, Japan, 27–30 September 2019; pp. 162–168. [Google Scholar]
- Lao, L.; Dai, X.; Xiao, B.; Guo, S. G-PBFT: A location-based and scalable consensus protocol for IOT-Blockchain applications. In Proceedings of the 2020 IEEE International Parallel and Distributed Processing Symposium (IPDPS), New Orleans, LA, USA, 18–22 May 2020; pp. 664–673. [Google Scholar]
- Li, Y.; Wang, Z.; Fan, J.; Zheng, Y.; Luo, Y.; Deng, C.; Ding, J. An extensible consensus algorithm based on PBFT. In Proceedings of the 2019 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Guilin, China, 17–19 October 2019; pp. 17–23. [Google Scholar]
- Zhong, W.; Zheng, X.; Feng, W.; Huang, M.; Feng, S. Improve PBFT Based on Hash Ring. Wirel. Commun. Mob. Comput. 2021, 2021, 7327372. [Google Scholar] [CrossRef]
- Du, M.; Chen, Q.; Ma, X. MBFT: A new consensus algorithm for consortium blockchain. IEEE Access 2020, 8, 87665–87675. [Google Scholar] [CrossRef]
- Gao, S.; Yu, T.; Zhu, J.; Cai, W. T-PBFT: An EigenTrust-based practical Byzantine fault tolerance consensus algorithm. China Commun. 2019, 16, 111–123. [Google Scholar] [CrossRef]
- Micali, S.; Rabin, M.; Vadhan, S. Verifiable random functions. In Proceedings of the 40th Annual Symposium on Foundations of Computer Science (Cat. No. 99CB37039), New York, NY, USA, 17–19 October 1999; pp. 120–130. [Google Scholar]









| Consensus Algorithm | Type | Fault Tolerance | Power Consumption | Scalability |
|---|---|---|---|---|
| PoW (Proof of Work) | Proof based | 50% | High | High |
| PoS (Proof of Stake) | Proof based | 50% | Less | High |
| PBFT (Practical Byzantine Fault Tolerance) | Voting based | 33% | Negligible | Less |
| Ref | Consensus Algorithm | Parameters | Remarks | ||
| Security | Privacy | Communication Overhead | |||
| [29] | Geographic-PBFT | MID | MID | HIGH | Proposed model selects geographically distributed, powerful, and authenticated IoT devices for consensus operation. |
| [30] | EPBFT | MID | LOW | HIGH | Proposed model does not perform a detailed assessment of the reliability of the nodes. |
| [21] | Reputation-based PBFT | MID | LOW | MID | Proposed model selects nodes with high reputation values which are given more priority in voting process. |
| [31] | HRPBFT | MID | MID | LOW | Proposed model uses Hash ring to group the nodes. Primary node is elected based on the group. |
| [32] | MBFT | HIGH | MID | LOW | Proposed uses two-layered consensus algorithm. |
| [33] | Trust PBFT | HIGH | MID | LOW | Proposed model selects nodes based on the node trust value for the consensus operation |
| Consensus Algorithm | Nodes Participating in the Consensus Process | Node Reliability Assessment | Network Type | Node Election Fairness | Communication Overhead |
| PoW | All Nodes | No | Permission less | No | High |
| PoS | All Nodes | No | Permission less | No | High |
| DPoS | All Nodes | No | Permission less | No | High |
| PBFT | All Nodes | No | Permissioned | No | High |
| Proposed Algorithm | All Nodes | Yes | Permissioned | Yes | Low |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hegde, P.; Maddikunta, P.K.R. Secure PBFT Consensus-Based Lightweight Blockchain for Healthcare Application. Appl. Sci. 2023, 13, 3757. https://doi.org/10.3390/app13063757
Hegde P, Maddikunta PKR. Secure PBFT Consensus-Based Lightweight Blockchain for Healthcare Application. Applied Sciences. 2023; 13(6):3757. https://doi.org/10.3390/app13063757
Chicago/Turabian StyleHegde, Pawan, and Praveen Kumar Reddy Maddikunta. 2023. "Secure PBFT Consensus-Based Lightweight Blockchain for Healthcare Application" Applied Sciences 13, no. 6: 3757. https://doi.org/10.3390/app13063757






