Evaluating a Proposed E-Government Stage Model in Terms of Personal Data Protection
Abstract
:1. Introduction
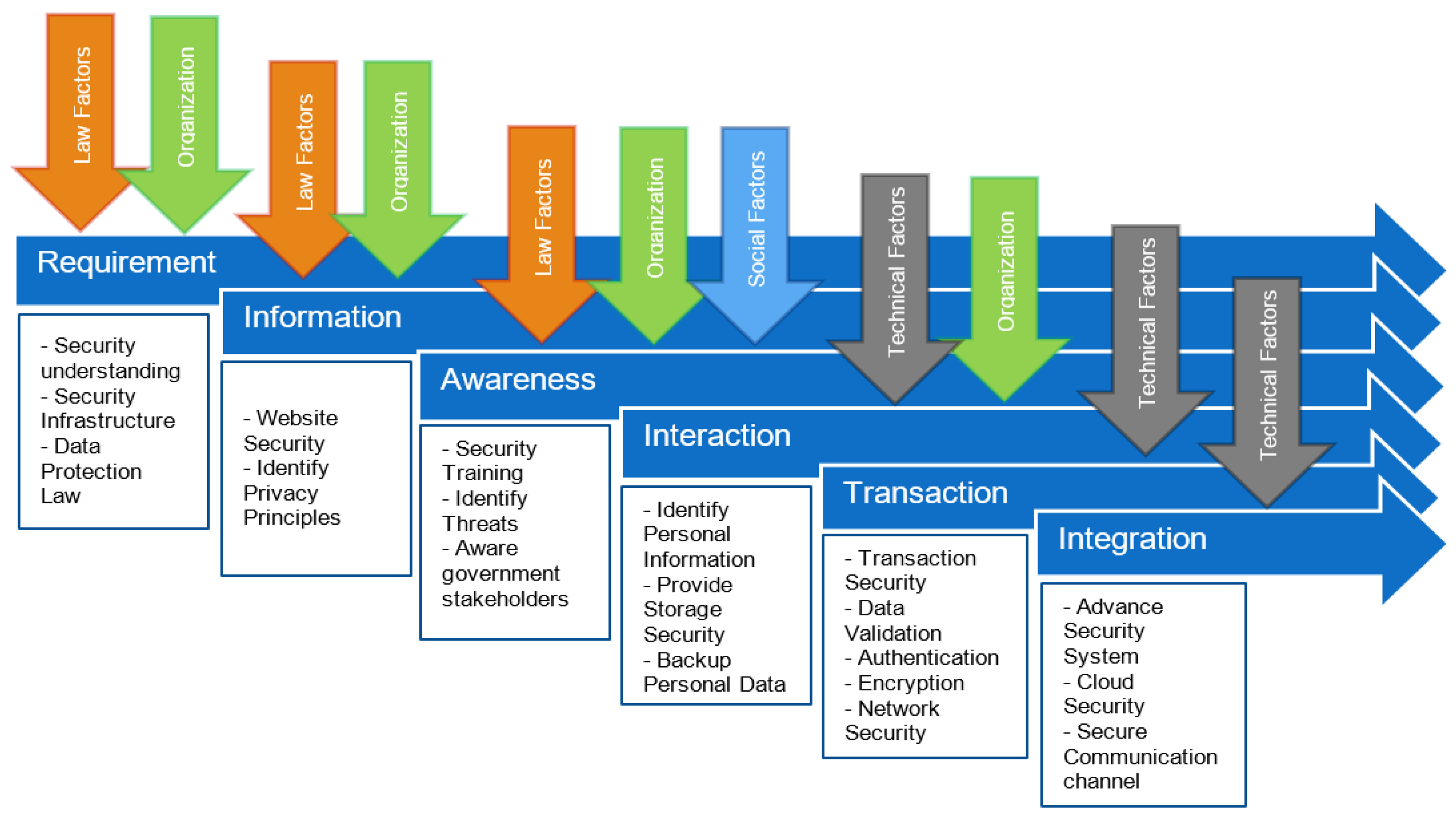
2. The Proposed Stage Model
3. Assessment Methodology
3.1. SOAR
- S1: Protecting personal information in one-way communication.
- S2: Protecting personal information in two-way communication.
- S3: Personal information protection awareness among e-government stakeholders.
- S4: Personal information security protocol.
- O1: Providing a proper personal data protection law context.
- O2: Developing security information infrastructure.
- O3: Identify personal information.
- O4: Enhance security of communication and storage.
- A1: Reduce cost.
- A2: Obtain law framework for protecting personal information.
- A3: Provide transparency.
- A4: Improve e-service.
- R1: Enhance security of communication channels.
- R2: Provide high level of security for personal information within government organizations.
- R3: Increase trust of people towards the e-government.
- R4: Increase e-participation.
3.2. Analytic Hierarchy Process (AHP)
- Developing a hierarchical structure with a goal at the top level. The attributes/criteria at the second level and the alternatives at the third level.
- Determine the relative importance of different attributes or criteria, with respect to the goal (using the fundamental scale values from Table 2). In this step, a pairwise comparison matrix is created with the help of scale of relative importance, as shown in Saaty’s table.
- 3.
- A normalized pairwise matrix is calculated by all of the elements of the column divided by the sum of the column (Equation (2)).
- 4.
- Calculate the criteria weights by averaging all the elements in the row (Equation (3)).
- 5.
- Multiply each value in the column by the criteria weight in order to determine whether the calculated value is correct or not for this or another pairwise comparison matrix that is not normalized.
- 6.
- Calculate the weighted sum value by taking the sum of each value in the row.
- 7.
- Calculate the ratio of the weighted sum value and the criteria weight (Equation (4)).
- 8.
- Calculate Lambda max (λmax) by taking the average of all values that come from step 7 (Equation (4)).
- 9.
- The consistency index CI, which is given by the formula lambda max minus n upon n minus 1 (Equation (6)).
- 10.
- The consistency ratio is given by dividing the consistency index with random index RI (Equation (7)). Random index is the consistency index of the randomly generated pairwise matrix. Table 3 shows the random index table for up to 10 criteria.
- 11.
3.3. AHP-SOAR Calculation
- T1: Improve security of personal information.
- T2: Achieve trust to e-government services.
- T3: Provide a reliable communication between the government and its stakeholders.
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Choi, J.P.; Jeon, D.-S.; Kim, B.-C. Privacy and Personal Data Collection with Information Externalities. J. Public Econ. 2019, 173, 113–124. [Google Scholar] [CrossRef] [Green Version]
- Hiller, J.S.; Bélanger, F. Privacy Strategies for Electronic Government. E-Gov. 2001, 200, 162–198. [Google Scholar]
- Wescott, C.G. E-Government in the Asia-Pacific Region: Progress and Challenges. Syst. Cybern. Inform. 2004, 3, 37–42. [Google Scholar]
- Hernández-Moreno, S.; de Hoyos-Martínez, J. Indicators of Urban Sustainability in Mexico. Theor. Empir. Res. Urban Manag. 2010, 5, 46–60. [Google Scholar]
- Kumar, P.; Kumar, R.; Kumar, A.; Franklin, A.; Jolfaei, A. Blockchain and Deep Learning Empowered Secure Data Sharing Framework for Softwarized UAVs. In Proceedings of the 2022 IEEE International Conference on Communications Workshops (ICC Workshops), Seoul, Republic of Korea, 16–20 May 2022; pp. 770–775. [Google Scholar]
- Cole, M.L.; Cox, J.D.; Stavros, J.M. Building Collaboration in Teams through Emotional Intelligence: Mediation by SOAR (strengths, Opportunities, Aspirations, and Results). J. Manag. Organ. 2019, 25, 263–283. [Google Scholar] [CrossRef]
- Shareef, S.M. Electronic Government Adoption Based on Citizen-Centric Approach in Regional Government in Developing Countries: The Case of Kurdistan Region of Iraq (KRI). Ph.D. Thesis, University of East London, London, UK, 2012. [Google Scholar]
- Muhammad, H.; Hromada, M. Proposing an E-Government Stage Model in Terms of Personal Information Security in Developing Countries. In Proceedings of the 2022 IEEE International Carnahan Conference on Security Technology (ICCST), Valeču Hrotovic, Czech Republic, 7–9 September 2022; pp. 1–5. [Google Scholar]
- Al-Dabbagh, M. Electronic Government in Iraq: Challenges of Development and Implementation; Swedish Business School at Örebro University: Örebro, Sweden, 2011. [Google Scholar]
- Wu, Y. Protecting Personal Data in E-Government: A Cross-Country Study. Gov. Inf. Q. 2014, 31, 150–159. [Google Scholar] [CrossRef]
- Houben, G.; Lenie, K.; Vanhoof, K. A Knowledge-Based SWOT-Analysis System as an Instrument for Strategic Planning in Small and Medium Sized Enterprises. Decis. Support Syst. 1999, 26, 125–135. [Google Scholar] [CrossRef]
- Dewa, M.; Zlotnikova, I. Citizens’ Readiness for E-Government Services in Tanzania. Adv. Comput. Sci. Int. J. 2014, 3, 37–45. [Google Scholar]
- Sutherland, J.; Stavros, J. The Heart of Appreciative Strategy. AI Pract. 2003, 5, 5–9. [Google Scholar]
- Stavros, J. The Generative Nature of SOAR: Applications, Results, and the New SOAR Profile. AI Pract. Int. J. Appreciative Inq. 2013, 15, 6–26. [Google Scholar] [CrossRef]
- Stavros, J.; Cooperrider, D.; Kelley, D.L. Strategic Inquiry Appreciative Intent: Inspiration to SOAR, a New Framework for Strategic Planning. AI Pract. 2003, 11, 1–21. [Google Scholar]
- Saaty, R.W. The Analytic Hierarchy Process—What It Is and How It Is Used. Math. Model. 1987, 9, 161–176. [Google Scholar] [CrossRef] [Green Version]
- Pickton, D.W.; Wright, S. What’s Swot in Strategic Analysis? Strateg. Chang. 1998, 7, 101–109. [Google Scholar] [CrossRef]
- Stavros, J.M.; Cole, M.L. SOARing towards Positive Transformation and Change. Abac Odi J. Vis. Action Outcome 2013, 1, 10–34. [Google Scholar]
- Karimi, A.; Mehrdadi, N.; Hashemian, S.; Bidhendi, G.; Moghaddam, R.T. Selection of Wastewater Treatment Process Based on the Analytical Hierarchy Process and Fuzzy Analytical Hierarchy Process Methods. Int. J. Environ. Sci. Technol. 2011, 8, 267–280. [Google Scholar] [CrossRef] [Green Version]
- Mu, E.; Pereyra-Rojas, M. Practical Decision Making: An Introduction to the Analytic Hierarchy Process (AHP) Using Super Decisions V2; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Brunelli, M. Introduction to the Analytic Hierarchy Process; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar]










| SOAR | SWOT |
|---|---|
| Focus on strength and opportunities | Equal focus on weaknesses and threats |
| Potential focus—“Be the best possible” | Competition focus—“Just be better” |
| Innovation and value generation | Incremental improvement |
| Stakeholder engagement | Top down |
| Focus on planning and implementation | Focus on analysis and planning |
| Energy creating | Energy depleting |
| Attention to results | Attention to gaps |
| Intensity of Interest | Information | Description |
|---|---|---|
| 1 | Both elements are just as important | Two elements have the same effect on a goal |
| 3 | One element is slightly more important than the other | Experience and judgment support a little more than other elements |
| 5 | One element is more important than any other element | Experience and judgment are very strong in favor of one element over the other |
| 7 | One element is clearly more important than any other elements | One of the strongest elements is preserved and dominate in practice |
| 9 | One of the most important elements of the other | Evidence favors a task in relation to another with the highest degree of reliability |
| 2, 4, 6, 8 | Values between two adjacent consideration values | This value is given when there are two compromises between two options |
| Inverse | If activity “i” acquires one number of activity “j”, then “j” has an opposite value to “i” from Equation (2) | |
| IR | 0 | 0 | 0.58 | 0.90 | 1.12 | 1.24 | 1.32 | 1.41 | 1.45 | 1.49 | 1.51 | 1.48 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Matrix | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| Factor1 | Factor2 | Factor3 | Factor4 | CR | |
|---|---|---|---|---|---|
| Strength | 0.616 | 0.474 | 0.129 | 0.105 | 0.071 |
| Opportunities | 0.207 | 0.429 | 0.170 | 0.097 | 0.081 |
| Aspirations | 0.110 | 0.106 | 0.185 | 0.055 | 0.066 |
| Results | 0.068 | 0.125 | 0.204 | 0.063 | 0.059 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Muhammad, H.; Hromada, M. Evaluating a Proposed E-Government Stage Model in Terms of Personal Data Protection. Appl. Sci. 2023, 13, 3913. https://doi.org/10.3390/app13063913
Muhammad H, Hromada M. Evaluating a Proposed E-Government Stage Model in Terms of Personal Data Protection. Applied Sciences. 2023; 13(6):3913. https://doi.org/10.3390/app13063913
Chicago/Turabian StyleMuhammad, Hemin, and Martin Hromada. 2023. "Evaluating a Proposed E-Government Stage Model in Terms of Personal Data Protection" Applied Sciences 13, no. 6: 3913. https://doi.org/10.3390/app13063913
APA StyleMuhammad, H., & Hromada, M. (2023). Evaluating a Proposed E-Government Stage Model in Terms of Personal Data Protection. Applied Sciences, 13(6), 3913. https://doi.org/10.3390/app13063913






