Detecting Phishing Domains Using Machine Learning
Abstract
:1. Introduction
2. Background
2.1. Decision Tree
2.2. Random Forest
2.3. Support Vector Machine
2.4. Ensemble Classification Techniques
2.4.1. Bagging

2.4.2. Boosting
2.4.3. Stacking
2.5. Ensemble Classification Techniques
3. Related Work
4. Methodology
4.1. Dataset Used: UCI Phishing Websites
4.2. Implemented Algorithm
5. Model’s Flowchart
- Read the URL’s UCI phishing websites dataset.
- Check the data features.
- Check the proposed data types.
- Clean missing values from the data.
- Split the data into training and testing sets.
- Train the model using four machine-learning techniques: RF, SVM, DT, and ANN.
- Evaluate the model’s performance to estimate the accuracy and calculate the accuracy results.
- Select the best model as the final model.
6. Findings and Analysis
7. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Cabaj, K.; Domingos, D.; Kotulski, Z.; Respício, A. Cybersecurity Education: Evolution of the Discipline and Analysis of Master Programs. Comput. Secur. 2018, 75, 24–35. [Google Scholar] [CrossRef]
- Iwendi, C.; Jalil, Z.; Javed, A.R.; Reddy, G.T.; Kaluri, R.; Srivastava, G.; Jo, O. KeySplitWatermark: Zero Watermarking Algorithm for Software Protection Against Cyber-Attacks. IEEE Access 2020, 8, 72650–72660. [Google Scholar] [CrossRef]
- Rehman Javed, A.; Jalil, Z.; Atif Moqurrab, S.; Abbas, S.; Liu, X. Ensemble Adaboost Classifier for Accurate and Fast Detection of Botnet Attacks in Connected Vehicles. Trans. Emerg. Telecommun. Technol. 2020, 33, e4088. [Google Scholar] [CrossRef]
- Conklin, W.A.; Cline, R.E.; Roosa, T. Re-Engineering Cybersecurity Education in the US: An Analysis of the Critical Factors. In Proceedings of the 2014 47th Hawaii International Conference on System Sciences, IEEE, Waikoloa, HI, USA, 6–9 January 2014; pp. 2006–2014. [Google Scholar]
- Javed, A.R.; Usman, M.; Rehman, S.U.; Khan, M.U.; Haghighi, M.S. Anomaly Detection in Automated Vehicles Using Multistage Attention-Based Convolutional Neural Network. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4291–4300. [Google Scholar] [CrossRef]
- Mittal, M.; Iwendi, C.; Khan, S.; Rehman Javed, A. Analysis of Security and Energy Efficiency for Shortest Route Discovery in Low-energy Adaptive Clustering Hierarchy Protocol Using Levenberg-Marquardt Neural Network and Gated Recurrent Unit for Intrusion Detection System. Trans. Emerg. Telecommun. Technol. 2020, 32, e3997. [Google Scholar] [CrossRef]
- Bleau, H.; Global Fraud and Cybercrime Forecast. Retrieved RSA 2017. Available online: https://www.rsa.com/en-us/resources/2017-global-fraud (accessed on 19 November 2021).
- Computer Fraud & Security. APWG: Phishing Activity Trends Report Q4 2018. Comput. Fraud Secur. 2019, 2019, 4. [Google Scholar] [CrossRef]
- Hulten, G.J.; Rehfuss, P.S.; Rounthwaite, R.; Goodman, J.T.; Seshadrinathan, G.; Penta, A.P.; Mishra, M.; Deyo, R.C.; Haber, E.J.; Snelling, D.A.W. Finding Phishing Sites; Google Patents: Microsoft Corporation, Redmond, WA, USA, 2014. [Google Scholar]
- What Is Phishing and How to Spot a Potential Phishing Attack. PsycEXTRA Dataset. Available online: https://www.imperva.com/learn/application-security/phishing-attack-scam/ (accessed on 20 November 2021).
- Gupta, B.B.; Tewari, A.; Jain, A.K.; Agrawal, D.P. Fighting against Phishing Attacks: State of the Art and Future Challenges. Neural Comput. Appl. 2016, 28, 3629–3654. [Google Scholar] [CrossRef]
- Zhu, E.; Ju, Y.; Chen, Z.; Liu, F.; Fang, X. DTOF-ANN: An Artificial Neural Network Phishing Detection Model Based on Decision Tree and Optimal Features. Appl. Soft Comput. 2020, 95, 106505. [Google Scholar] [CrossRef]
- Machine Learning Decision Tree Classification Algorithm—Javatpoint. Available online: https://www.javatpoint.com/machine-learning-decision-tree-classification-algorithm (accessed on 25 November 2021).
- Breiman, L. Random Forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef] [Green Version]
- Friedman, J.H. The Elements of Statistical Learning: Data Mining, Inference, and Prediction; Springer Open: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Brownlee, J. Train-Test Split for Evaluating Machine Learning Algorithms. Mach. Learn. Mastery 2020, 23. Available online: https://machinelearningmastery.com/train-test-split-for-evaluating-machine-learning-algorithms/ (accessed on 25 December 2021).
- Subasi, A.; Molah, E.; Almkallawi, F.; Chaudhery, T.J. Intelligent Phishing Website Detection Using Random Forest Classifier. In Proceedings of the 2017 International Conference on Electrical and Computing Technologies and Applications (ICECTA), Ras Al Khaimah, United Arab Emirates, 21–23 November 2017; pp. 1–5. [Google Scholar]
- Jeremybeauchamp English: A Visual Comparison between the Complexity of Decision Trees and Random Forests. 2020. Available online: https://commons.wikimedia.org/wiki/File:Decision_Tree_vs._Random_Forest.png (accessed on 27 December 2021).
- Sönmez, Y.; Tuncer, T.; Gökal, H.; Avcı, E. Phishing Web Sites Features Classification Based on Extreme Learning Machine. In Proceedings of the 2018 6th International Symposium on Digital Forensic and Security (ISDFS), IEEE, Antalya, Turkey, 22–25 March 2018; pp. 1–5. [Google Scholar]
- ResearchGate. Figure 2. Classification of Data by Support Vector Machine (SVM). Available online: https://www.researchgate.net/figure/Classification-of-data-by-support-vector-machine-SVM_fig8_304611323 (accessed on 6 October 2021).
- Cristianini, N.; Shawe-Taylor, J. An Introduction to Support Vector Machines and Other Kernel-Based Learning Methods; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Gomes, H.M.; Barddal, J.P.; Enembreck, F.; Bifet, A. A Survey on Ensemble Learning for Data Stream Classification. ACM Comput. Surv. CSUR 2017, 50, 1–36. [Google Scholar] [CrossRef]
- Zhou, Z.-H. Ensemble Methods: Foundations and Algorithms; Chapman and Hall/CRC: London, UK, 2019; ISBN 1-4398-3005-3. [Google Scholar]
- Yaman, E.; Subasi, A. Comparison of Bagging and Boosting Ensemble Machine Learning Methods for Automated EMG Signal Classification. BioMed Res. Int. 2019, 2019, 9152506. [Google Scholar] [CrossRef]
- Bagging (Bootstrap Aggregation)—Overview, How It Works, Advantages—Ro.Outletshop2021.Ru. Available online: https://corporatefinanceinstitute.com/resources/data-science/bagging-bootstrap-aggregation/#:~:text=Bagging%20offers%20the%20advantage%20of,of%20interpretability%20of%20a%20model. (accessed on 6 October 2021).
- Junior, J.R.B.; do Carmo Nicoletti, M. An Iterative Boosting-Based Ensemble for Streaming Data Classification. Inf. Fusion 2019, 45, 66–78. [Google Scholar] [CrossRef]
- Zhou, Z.-H. Ensemble Learning. In Machine Learning; Springer: Berlin/Heidelberg, Germany, 2021; pp. 181–210. [Google Scholar]
- AdaBoost Classifier in Python—DataCamp. Available online: https://www.datacamp.com/tutorial/adaboost-classifier-python (accessed on 6 October 2021).
- Abiodun, O.I.; Jantan, A.; Omolara, A.E.; Dada, K.V.; Mohamed, N.A.; Arshad, H. State-of-the-Art in Artificial Neural Network Applications: A Survey. Heliyon 2018, 4, e00938. [Google Scholar] [CrossRef] [Green Version]
- McCulloch, W.S.; Pitts, W. A Logical Calculus of the Ideas Immanent in Nervous Activity. Bull. Math. Biophys. 1943, 5, 115–133. [Google Scholar] [CrossRef]
- Jin, D.; Wang, P.; Bai, Z.; Wang, X.; Peng, H.; Qi, R.; Yu, Z.; Zhuang, G. Analysis of Bacterial Community in Bulking Sludge Using Culture-Dependent and-Independent Approaches. J. Environ. Sci. 2011, 23, 1880–1887. [Google Scholar] [CrossRef] [PubMed]
- Liu, Z.-W.; Liang, F.-N.; Liu, Y.-Z. Artificial Neural Network Modeling of Biosorption Process Using Agricultural Wastes in a Rotating Packed Bed. Appl. Therm. Eng. 2018, 140, 95–101. [Google Scholar] [CrossRef]
- Oliveira, V.; Sousa, V.; Dias-Ferreira, C. Artificial Neural Network Modelling of the Amount of Separately-Collected Household Packaging Waste. J. Clean. Prod. 2019, 210, 401–409. [Google Scholar] [CrossRef]
- Basit, A.; Zafar, M.; Liu, X.; Javed, A.R.; Jalil, Z.; Kifayat, K. A Comprehensive Survey of AI-Enabled Phishing attacks detection techniques. Telecommun. Syst. 2021, 76, 139–154. Available online: https://link.springer.com/article/10.1007/s11235-020-00733-2 (accessed on 27 September 2021). [CrossRef]
- A Comprehensive Guide to Understand and Implement Text Classification in Python. Anal. Vidhya 2018. Available online: http://www.shivambansal.com/blog/text-classification-guide/ (accessed on 25 October 2021).
- Sánchez-Paniagua, M.; Fernández, E.F.; Alegre, E.; Al-Nabki, W.; González-Castro, V. Phishing URL Detection: A Real-Case Scenario Through Login URLs. IEEE Access 2022, 10, 42949–42960. [Google Scholar] [CrossRef]
- James, J.; Sandhya, L.; Thomas, C. Detection of Phishing URLs Using Machine Learning Techniques. In Proceedings of the 2013 International Conference on Control Communication and Computing (ICCC), Thiruvananthapuram, India, 13–15 December 2013; Available online: https://ieeexplore.ieee.org/abstract/document/6731669 (accessed on 26 September 2021).
- Liew, S.W.; Sani NF, M.; Abdullah, M.T.; Yaakob, R.; Sharum, M.Y. An Effective Security Alert Mechanism for Real-Time Phishing Tweet Detection on Twitter—ScienceDirect. Comput. Secur. 2019, 83, 201–207. Available online: https://www.sciencedirect.com/science/article/pii/S0167404818309040 (accessed on 26 September 2021). [CrossRef]
- Hutchinson, S.; Zhang, Z.; Liu, Q. Detecting Phishing Websites with Random Forest. In Proceedings of the Machine Learning and Intelligent Communications, Hangzhou, China, 6–8 July 2018; Meng, L., Zhang, Y., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 470–479. [Google Scholar]
- Patil, V.; Thakkar, P.; Shah, C.; Bhat, T.; Godse, S.P. Detection and Prevention of Phishing Websites Using Machine Learning Approach. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 19–18 August 2018; pp. 1–5. [Google Scholar]
- Joshi, A.; Pattanshetti, P.T.R. Phishing Attack Detection Using Feature Selection Techniques; Social Science Research Network: Rochester, NY, USA, 2019. [Google Scholar]
- Ubing, A.; Kamilia, S.; Abdullah, A.; Zaman, N.; Supramaniam, M. Phishing Website Detection: An Improved Accuracy through Feature Selection and Ensemble Learning. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 252–257. [Google Scholar] [CrossRef] [Green Version]
- Li, Y.; Yang, Z.; Chen, X.; Yuan, H.; Liu, W. A Stacking Model Using URL and HTML Features for Phishing Webpage Detection. Future Gener. Comput. Syst. 2019, 94, 27–39. [Google Scholar] [CrossRef]
- Zamir, A.; Khan, H.U.; Iqbal, T.; Yousaf, N.; Aslam, F.; Anjum, A.; Hamdani, M. Phishing Web Site Detection Using Diverse Machine Learning Algorithms. Electron. Libr. 2020, 38, 65–80. [Google Scholar] [CrossRef]
- Alsariera, Y.A.; Adeyemo, V.E.; Balogun, A.O.; Alazzawi, A.K. AI Meta-Learners and Extra-Trees Algorithm for the Detection of Phishing Websites. IEEE Access 2020, 8, 142532–142542. [Google Scholar] [CrossRef]
- Ali, W.; Malebary, S. Particle Swarm Optimization-Based Feature Weighting for Improving Intelligent Phishing Website Detection. IEEE Access 2020, 8, 116766–116780. [Google Scholar] [CrossRef]
- Adebowale, M.A.; Lwin, K.T.; Sanchez, E.; Hossain, M.A. Intelligent Web-Phishing Detection and Protection Scheme Using Integrated Features of Images, Frames and Text—ScienceDirect. Expert Syst. Appl. 2019, 115, 300–313. Available online: https://www.sciencedirect.com/science/article/abs/pii/S0957417418304925 (accessed on 26 September 2021). [CrossRef] [Green Version]
- El Aassal, A.; Baki, S.; Das, A.; Verma, R.M. An In-Depth Benchmarking and Evaluation of Phishing Detection Research for Security Needs. IEEE Access 2020, 8, 22170–22192. Available online: https://ieeexplore.ieee.org/abstract/document/8970564 (accessed on 27 September 2021). [CrossRef]
- Subasi, A.; Kremic, E. Comparison of Adaboost with MultiBoosting for Phishing Website Detection—ScienceDirect. Procedia Comput. Sci. 2020, 168, 272–278. Available online: https://www.sciencedirect.com/science/article/pii/S1877050920303902 (accessed on 27 September 2021). [CrossRef]
- Mao, J.; Bian, J.; Tian, W.; Zhu, S.; Wei, T.; Li, A.; Liang, Z. Phishing Page Detection via Learning Classifiers from Page Layout Feature. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 43. Available online: https://jwcn-eurasipjournals.springeropen.com/articles/10.1186/s13638-019-1361-0 (accessed on 27 September 2021). [CrossRef] [Green Version]
- A Novel Machine Learning Approach to Detect Phishing Websites. Available online: https://ieeexplore.ieee.org/abstract/document/8474040/ (accessed on 27 September 2021).
- Chen, Y.H.; Chen, J.L. AI@ntiPhish—Machine Learning Mechanisms for Cyber-Phishing Attack. IEICE Trans. Inf. Syst. 2019, 102, 878–887. Available online: https://www.jstage.jst.go.jp/article/transinf/E102.D/5/E102.D_2018NTI0001/_article/-char/ja/ (accessed on 27 September 2021). [CrossRef] [Green Version]
- Abdelhamid, N.; Thabtah, F.; Abdel-Jaber, H. Phishing Detection: A Recent Intelligent Machine Learning Comparison Based on Models Content and Features. In Proceedings of the 2017 IEEE International Conference on Intelligence and Security Informatics, Beijing, China, 22–24 July 2017; Available online: https://ieeexplore.ieee.org/abstract/document/8004877 (accessed on 27 September 2021).
- Jain, A.K.; Gupta, B.B. Towards Detection of Phishing Websites on Client-Side Using Machine Learning Based Approach. Telecommun. Syst. 2018, 68, 687–700. Available online: https://link.springer.com/article/10.1007/s11235-017-0414-0 (accessed on 27 September 2021). [CrossRef]
- Lakshmi, L.; Reddy, M.P.; Santhaiah, C.; Reddy, U.J. Smart Phishing Detection in Web Pages Using Supervised Deep Learning Classification and Optimization Technique ADAM. Wirel. Pers. Commun. 2021, 118, 3549–3564. [Google Scholar] [CrossRef]
- Sahingoz, O.K.; Buber, E.; Demir, O.; Diri, B. Machine Learning Based Phishing Detection from URLs—ScienceDirect. Expert Syst. Appl. 2019, 117, 345–357. Available online: https://www.sciencedirect.com/science/article/abs/pii/S0957417418306067 (accessed on 27 September 2021). [CrossRef]
- Jagadeesan, S. URL Phishing Analysis Using Random Forest. Int. J. Pure Appl. Math. 2018, 118, 4159–4163. [Google Scholar]
- Niranjan, A.; Haripriya, D.K.; Pooja, R.; Sarah, S.; Deepa Shenoy, P.; Venugopal, K.R. EKRV: Ensemble of KNN and Random Committee Using Voting for Efficient Classification of Phishing; Springer: Singapore, 2019; Available online: https://link.springer.com/chapter/10.1007/978-981-13-1708-8_37 (accessed on 27 September 2021).
- Chiew, K.L.; Tan, C.L.; Wong, K.; Yong, K.S.; Tiong, W.K. A New Hybrid Ensemble Feature Selection Framework for Machine Learning-Based Phishing Detection System—ScienceDirect. Inf. Sci. 2019, 484, 153–166. Available online: https://www.sciencedirect.com/science/article/abs/pii/S0020025519300763 (accessed on 27 September 2021). [CrossRef]
- Pandey, A.; Gill, N.; Sai Prasad Nadendla, K.; Thaseen, I.S. Identification of Phishing Attack in Websites Using Random Forest-SVM Hybrid Model. In Proceedings of the Intelligent Systems Design and Applications: 18th International Conference on Intelligent Systems Design and Applications (ISDA 2018), Vellore, India, 6–8 December 2018; Springer International Publishing: Midtown Manhattan, NY, USA, 2020. Available online: https://link.springer.com/chapter/10.1007/978-3-030-16660-1_12 (accessed on 27 September 2021).
- Ali, W.; Ahmed, A.A. Hybrid Intelligent Phishing Website Prediction Using Deep Neural Networks with Genetic Algorithm-Based Feature Selection and Weighting. IET Inf. Secur. 2019, 13, 659–669. [Google Scholar] [CrossRef]
- Aljofey, A.; Jiang, Q.; Qu, Q.; Huang, M.; Niyigena, J.P. An Effective Phishing Detection Model Based on Character Level Convolutional Neural Network from URL. Electronics 2020, 9, 1514. Available online: https://www.mdpi.com/2079-9292/9/9/1514 (accessed on 27 September 2021). [CrossRef]
- Shie, E.W.S. Critical Analysis of Current Research Aimed at Improving Detection of Phishing Attacks. Sel. Comput. Res. Pap. 2020, 45, 45–53. [Google Scholar]
- Maurya, S.; Jain, A. Deep Learning to Combat Phishing. J. Stat. Manag. Syst. 2020, 23, 945–957. [Google Scholar] [CrossRef]
- Mao, J.; Bian, J.; Tian, W.; Zhu, S.; Wei, T.; Li, A.; Liang, Z. Detecting Phishing Websites via Aggregation Analysis of Page Layouts—ScienceDirect. Procedia Comput. 2018, 129, 224–230. Available online: https://www.sciencedirect.com/science/article/pii/S187705091830276X (accessed on 27 September 2021). [CrossRef]
- Yang, L.; Zhang, J.; Wang, X.; Li, Z.; Li, Z.; He, Y. An Improved ELM-Based and Data Preprocessing Integrated Approach for Phishing Detection Considering Comprehensive Features—ScienceDirect. Expert Syst. Appl. 2021, 165, 113863. Available online: https://www.sciencedirect.com/science/article/abs/pii/S0957417420306734 (accessed on 27 September 2021). [CrossRef]
- Anupam, S.; Kar, A.K. Phishing Website Detection Using Support Vector Machines and Nature-Inspired Optimization Algorithms. Telecommun. Syst. 2021, 76, 17–32. Available online: https://link.springer.com/article/10.1007/s11235-020-00739-w (accessed on 27 September 2021). [CrossRef]
- UCI Machine Learning Repository: Phishing Websites Data Set. Available online: https://archive.ics.uci.edu/ml/datasets/phishing+websites (accessed on 29 November 2021).
- Ramesh, G.; Krishnamurthi, I.; Kumar, K.S.S. An Efficacious Method for Detecting Phishing Webpages through Target Domain Identification. Decis. Support Syst. 2014, 61, 12–22. [Google Scholar] [CrossRef]
- Singh, C. Phishing Website Detection Based on Machine Learning: A Survey. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), IEEE, Coimbatore, India, 6–7 March 2020; pp. 398–404. [Google Scholar]
- Alsariera, Y.A.; Elijah, A.V.; Balogun, A.O. Phishing Website Detection: Forest by Penalizing Attributes Algorithm and Its Enhanced Variations. Arab. J. Sci. Eng. 2020, 45, 10459–10470. [Google Scholar] [CrossRef]






| Model | Dataset | Algorithm | Accuracy |
|---|---|---|---|
| James et al. [37] | URLs | IBK, SVM, NB | 89.75% |
| Subasi et al. [17] | website | ANN, KNN, RF, SVM, C4.5, RF | 97.36% |
| Mao et al. [50] | Websites | SVM, RF, DT, AB | 93% |
| Tyagi et al. [51] | URLs | DT, RF, GBM | 98.40% |
| Chen and Chen [52] | websites | ELM, SVM, LR, C4.5, LC-ELM, KNN, XGB | 99.2% |
| Joshi et al. [41] | Websites | RF | 97.63% |
| Ubing et al. [42] | UCI | Ensemble bagging, boosting, stacking | 95.4% |
| Sahingoz et al. [56] | Websites | SVM, DT, RF, KNN, KS, NB | 97.98% |
| Abdelhamid et al. [53] | URLs | eDRI | 93.5% |
| Patil et al. [40] | URLs | LR, DT, RF | 96.58% |
| Jain and Gupta [54] | Websites | RF | 99.57% |
| Jagadeesan et al. [57] | URLs | RF, SVM | 95.11% |
| Niranjan et al. [58] | Websites | RC, kNN, IBK, LR, PART | 97.3% |
| Chiew et al. [59] | URLs | RF, C4.5, PART, SVM, NB | 96.17% |
| Pandey et al. [60] | Websites | SVM, RF | 94% |
| Ali and Ahmed [61] | Websites | Genetic algorithm (GA) + DNN | 89.50% |
| Aljofey et al. [62] | Websites | CNN | 95.02% |
| Shie [63] | Websites | Convolutional auto encoder + DNN | 89.00% |
| Maurya and Jain [64] | Websites | PSL 1 + PART | 99.30% |
| Wang et al. [65] | Websites | RNN + CNN | 95.79% |
| Lakshmi et al. [55] | UCI | DNN +Adam | 96.00% |
| Li et al. [43] | URLs | GBDT, XGBoost and LightGBM | 98.60% |
| Yang et al. [66] | Websites | Auto encoder + NIOSELM | 94.60% |
| Anupam and Arpan [67] | Websites | Grey wolf optimizer + SVM | 90.38% |
| Classifier | Before Use Normalization | After Use Normalization |
|---|---|---|
| SVM | Accuracy: 94.46 Precision: 93.64 Recall: 96.62 F1-measure: 95.10 | Accuracy: 94.66 Precision: 93.9 Recall: 96.6 F1-measure: 95.3 |
| ANN | Accuracy: 95.5 Precision: 95.6 Recall: 96.3 F1-measure: 96 | Accuracy: 96.2 Precision: 96 Recall: 97.2 F1-measure: 96.6 |
| RF | Accuracy: 96.86 Precision: 96.56 Recall: 97.84 F1-measure: 97.20 | Accuracy: 97.3 Precision: 96.9 Recall: 98.62 F1-measure: 97.6 |
| DT | Accuracy: 95.4 Precision: 95.8 Recall: 95.9 F1-measure: 95.8 | Accuracy: 96.3 Precision: 96.5 Recall: 96.8 F1-measure: 96.7 |
| Classifier | Parameters | TPR | TNR |
|---|---|---|---|
| SVM | Kernel function = rbf | 0.92 | 0.96 |
| ANN | Iterations = 500, Activation = Relu, Optimizer = Adam | 0.94 | 0.96 |
| RF | Trees = 100, Creation = gini | 0.96 | 0.98 |
| DT | Criterion = gini, Splitter = best | 0.95 | 0.96 |
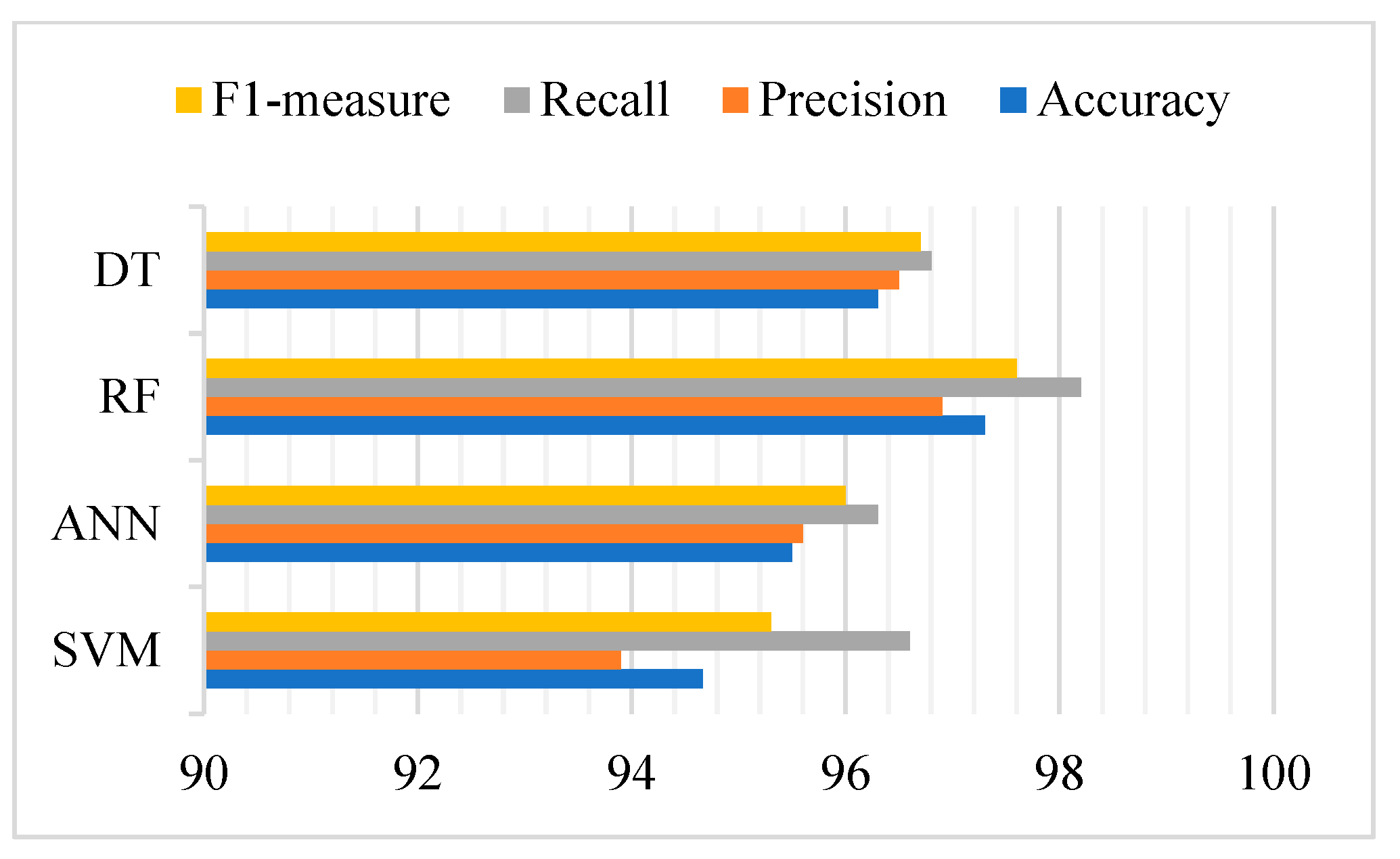
| Classifier | Accuracy | Precision | Recall | F1-Measure |
|---|---|---|---|---|
| SVM | 94.66 | 93.9 | 96.6 | 95.3 |
| ANN | 95.5 | 95.6 | 96.3 | 96 |
| RF | 97.3 | 96.9 | 98.2 | 97.6 |
| DT | 96.3 | 96.5 | 96.8 | 96.7 |
| Schemes | Dataset | Algorithm | Accuracy |
|---|---|---|---|
| Ubing et al. [42] | UCI | Ensemble bagging, boosting, stacking | 95.4% |
| Alsariera et al. [71] | UCI | ForestPA-PWDM, Bagged-ForestPA-PWDM, and Adab-ForestPA-PWDM | 96.26% 96.5% 97.4% |
| Lakshmi et al. [55] | UCI | DNN +Adam | 96.00% |
| Random Forest Model | UCI | Random Forest | 97.3% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alnemari, S.; Alshammari, M. Detecting Phishing Domains Using Machine Learning. Appl. Sci. 2023, 13, 4649. https://doi.org/10.3390/app13084649
Alnemari S, Alshammari M. Detecting Phishing Domains Using Machine Learning. Applied Sciences. 2023; 13(8):4649. https://doi.org/10.3390/app13084649
Chicago/Turabian StyleAlnemari, Shouq, and Majid Alshammari. 2023. "Detecting Phishing Domains Using Machine Learning" Applied Sciences 13, no. 8: 4649. https://doi.org/10.3390/app13084649
APA StyleAlnemari, S., & Alshammari, M. (2023). Detecting Phishing Domains Using Machine Learning. Applied Sciences, 13(8), 4649. https://doi.org/10.3390/app13084649






