HyperIO: A Hypervisor-Based Framework for Secure IO
Abstract
:Featured Application
Abstract
1. Introduction
- secure item communication with the IO devices;
- isolated computation environment.
- We present a novel thin hypervisor with a minimal TCB, which implements a secure IO path.
- We demonstrate our approach’s applicability by describing the implementation of two security systems built using our hypervisor.
- We discuss the usability and security of HyperIO and compare it with previous works.
- We evaluate the performance of HyperIO and verify its effectiveness against popular keyloggers and screen-capturing software.
2. Background
2.1. Virtualization
2.2. TPM
2.3. Certificates
2.4. PS/2
2.5. Display Adapter
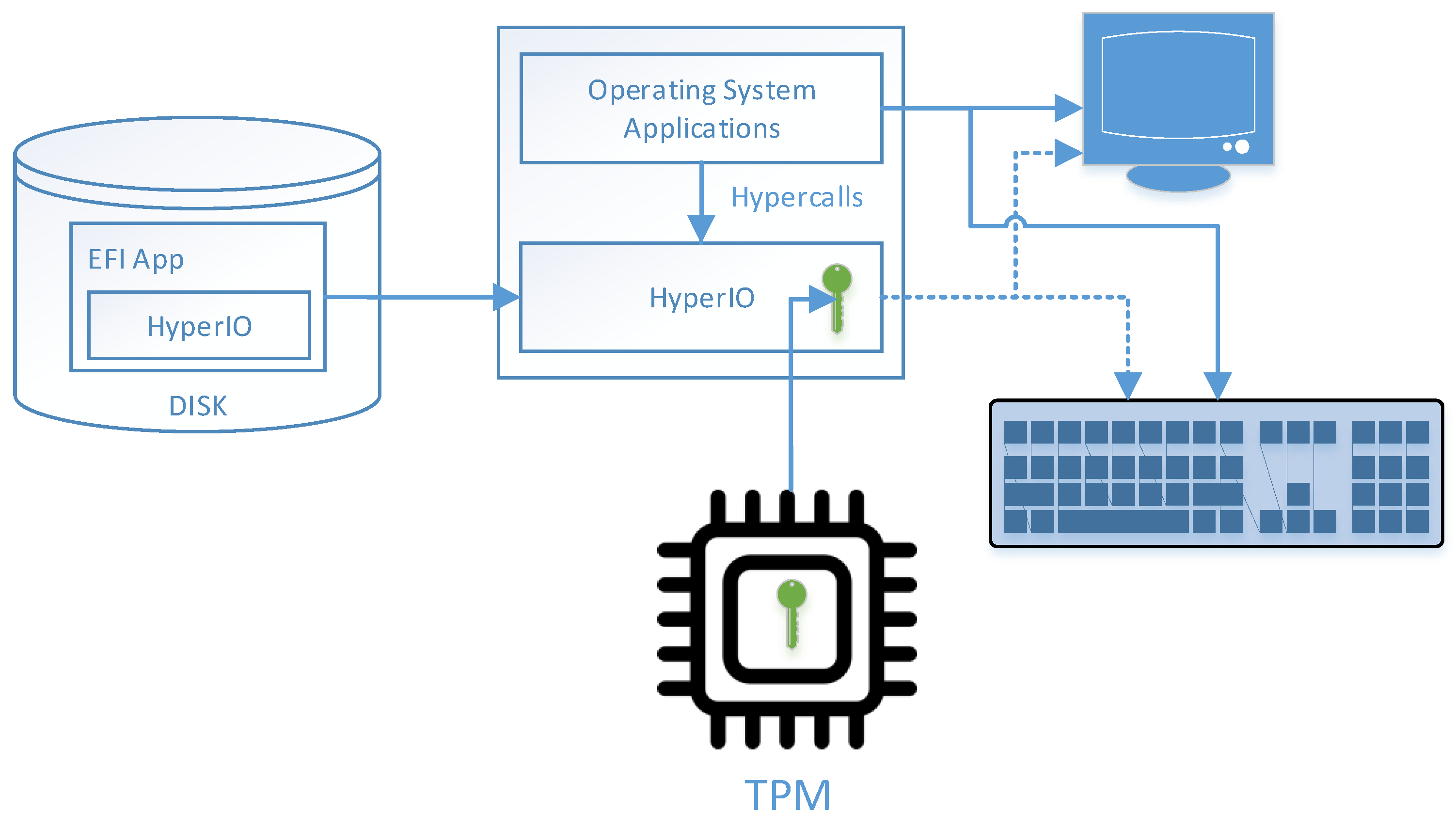
3. System Design
3.1. Threat Model
3.2. System Architecture
- HyperIO intercepts all the keystrokes and records them in a secure memory region;
- HyperIO switches the display adapter to the text mode; and
- HyperIO intercepts all attempts to change the video mode or access the display adapter’s text mode buffer.
3.3. Initialization and Handshake
- Generates a random number r.
- Computes .
- Computes , where is HyperIO’s public key.
- Computes , where is the requester’s private key.
- Computes the full payload where is the requester’s certificate signed by and so on, and is a certificate hard-coded in HyperIO.
- Performs
3.4. Implementation Details
- the display mode is selected to be text mode;
- the memory region that controls the displayed characters is configured to be inaccessible.
4. Related Work
4.1. External Device
4.2. SMM
4.3. Hypervisor
5. Discussion
5.1. Security
- entering the secure mode;
- typing a short message;
- exiting the secure mode.
5.2. Performance
- without a hypervisor;
- with HyperIO’s hypervisor;
- with HyperIO (which includes additional interceptions, e.g., key presses);
- with Oracle VirtualBox (6.1.14) as an example of a full hypervisor, running the same version of Windows with 4 GB of RAM.
6. Applications
- Trustworthy network paths;
- Trustworthy human interface devices;
- Trustworthy screen output.
6.1. FireSafe—Secure IO in Web Applications
6.2. ClipCrypt—Secure IO in Graphical Applications
- select the current content by pressing “CTRL + A”;
- copy this content to the clipboard by pressing “CTRL + C”;
- press the “scroll lock” key to enter the secure mode;
- perform the actual editing and presses the “scroll lock” key to return to the regular mode;
- paste the content of the clipboard by pressing “CTRL + V”.
6.3. Convenience
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| FHV | full hypervisor |
| FW | firmware |
| IO | Input/output |
| OS | operating system |
| SGX | Secure guard extentions |
| SLOC | Software lines of code |
| SMM | System management mode |
| THV | thin hypervisor |
| TPM | Trusted platform module |
| VMM | Virtual machine monitor |
References
- Rescorla, E. RFC2818: Http over TLS, 2000. Available online: https://dl.acm.org/doi/abs/10.17487/RFC2818 (accessed on 16 February 2023).
- Sharma, R.K.; Kalita, H.K.; Issac, B. Different firewall techniques: A survey. In Proceedings of the Fifth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Hefei, China, 11–13 July 2014; pp. 1–6. [Google Scholar]
- Gandotra, E.; Bansal, D.; Sofat, S. Malware analysis and classification: A survey. J. Inf. Secur. 2014, 2014. [Google Scholar] [CrossRef]
- Axelsson, S. Intrusion Detection Systems: A Survey and Taxonomy; Technical Report; 2000. Available online: https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=7a15948bdcb530e2c1deedd8d22dd9b54788a634 (accessed on 16 February 2023).
- Hussain, M.; Al-Haiqi, A.; Zaidan, A.; Zaidan, B.; Kiah, M.M.; Anuar, N.B.; Abdulnabi, M. The rise of keyloggers on smartphones: A survey and insight into motion-based tap inference attacks. Pervasive Mob. Comput. 2016, 25, 1–25. [Google Scholar] [CrossRef]
- Farinholt, B.; Rezaeirad, M.; McCoy, D.; Levchenko, K. Dark Matter: Uncovering the DarkComet RAT Ecosystem. In Proceedings of the Web Conference 2020, Online, 20 April 2020; pp. 2109–2120. [Google Scholar]
- Pinto, S.; Santos, N. Demystifying ARM TrustZone: A comprehensive survey. ACM Comput. Surv. (CSUR) 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Rosenbaum, A.; Biham, E.; Bitan, S. Trusted Execution Environments. Ph.D. Thesis, Computer Science Department, Technion, Haifa, Israel, 2019. [Google Scholar]
- Neiger, G.; Santoni, A.; Leung, F.; Rodgers, D.; Uhlig, R. Intel Virtualization Technology: Hardware Support for Efficient Processor Virtualization. Intel Technol. J. 2006, 10, 167. [Google Scholar] [CrossRef]
- Costan, V.; Devadas, S. Intel SGX Explained. IACR Cryptol. ePrint Arch. 2016, 2016, 1–118. [Google Scholar]
- Weiser, S.; Werner, M. Sgxio: Generic trusted i/o path for intel sgx. In Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; pp. 261–268. [Google Scholar]
- Vasudevan, A.; Chaki, S.; Jia, L.; McCune, J.; Newsome, J.; Datta, A. Design, implementation and verification of an extensible and modular hypervisor framework. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 430–444. [Google Scholar]
- Shinagawa, T.; Eiraku, H.; Tanimoto, K.; Omote, K.; Hasegawa, S.; Horie, T.; Hirano, M.; Kourai, K.; Oyama, Y.; Kawai, E.; et al. Bitvisor: A thin hypervisor for enforcing i/o device security. In Proceedings of the 2009 ACM SIGPLAN/SIGOPS International Conference on Virtual Execution Environments, Washington, DC, USA, 11–13 March 2009; pp. 121–130. [Google Scholar]
- Chapweske, A. The PS/2 Mouse/Keyboard Protocol. 2003. Available online: http://www.computer-engineering.org/ps2protocol (accessed on 16 February 2023).
- Zimmer, V.; Rothman, M.; Hale, B. UEFI: From Reset Vector to Operating System. In Chapter 3 of Hardware-Dependent Software; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Gerck, E. Overview of Certification Systems: x. 509, CA, PGP and SKIP. Black Hat Briefings 1997, 99. Available online: https://www.researchgate.net/profile/Ed-Gerck/publication/318700731_original_web_site_Overview_of_Certification_Systems/data/597829520f7e9b277721d8ce/certhtm.pdf (accessed on 16 February 2023).
- Zhang, F.; Leach, K.; Wang, H.; Stavrou, A. Trustlogin: Securing password-login on commodity operating systems. In Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security, Singapore, 14–17 April 2015; pp. 333–344. [Google Scholar]
- Dowty, M.; Sugerman, J. GPU virtualization on VMware’s hosted I/O architecture. ACM SIGOPS Oper. Syst. Rev. 2009, 43, 73–82. [Google Scholar] [CrossRef]
- Milanov, E. The RSA algorithm; RSA Laboratories: Hebron, Connecticut, 2009; pp. 1–11. [Google Scholar]
- Daemen, J.; Rijmen, V. Reijndael: The Advanced Encryption Standard. Dr. Dobb’s J. Softw. Tools Prof. Program. 2001, 26, 137–139. [Google Scholar]
- Thomas, S. SSL and TLS Essentials; Wiley: New York, NY, USA, 2000; Volume 3. [Google Scholar]
- Zheng, S.; Zhou, Z.; Tang, H.; Yang, X. SwitchMan: An Easy-to-Use Approach to Secure User Input and Output. In Proceedings of the 2019 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 19–23 May 2019; pp. 105–113. [Google Scholar]
- Eskandarian, S.; Cogan, J.; Birnbaum, S.; Brandon, P.C.W.; Franke, D.; Fraser, F.; Garcia, G.; Gong, E.; Nguyen, H.T.; Sethi, T.K.; et al. Fidelius: Protecting user secrets from compromised browsers. IEEE Symp. Secur. Priv. 2019, 1, 264–280. [Google Scholar]
- Dhar, A.; Ulqinaku, E.; Kostiainen, K.; Capkun, S. ProtectIOn: Root-of-Trust for IO in Compromised Platforms. IACR Cryptol. ePrint Arch. 2019, 2019, 869. [Google Scholar]
- Perrig, J.M.M.A.; Reiter, M.K. Safe passage for passwords and other sensitive data. In Proceedings of the 16th Annual Network and Distributed System Security Symposium, San Diego, CA, USA, 8–11 February 2009. [Google Scholar]
- McCune, J.M.; Perrig, A.; Reiter, M.K. Bump in the Ether: A Framework for Securing Sensitive User Input. In Proceedings of the USENIX Annual Technical Conference, General Track, Boston, MA, USA, 30 May–3 June 2006; pp. 185–198. [Google Scholar]
- McCune, J.M.; Parno, B.J.; Perrig, A.; Reiter, M.K.; Isozaki, H. Flicker: An execution infrastructure for TCB minimization. In Proceedings of the 3rd ACM SIGOPS/EuroSys European Conference on Computer Systems, Glasgow, UK, 1–4 April 2008; pp. 315–328. [Google Scholar]
- Liang, H.; Li, M.; Chen, Y.; Jiang, L.; Xie, Z.; Yang, T. Establishing trusted i/o paths for sgx client systems with aurora. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1589–1600. [Google Scholar] [CrossRef]
- Hirano, M.; Umeda, T.; Okuda, T.; Kawai, E.; Yamaguchi, S. T-pim: Trusted password input method against data stealing malware. In Proceedings of the 2009 Sixth International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 27–29 April 2009; pp. 429–434. [Google Scholar]
- Rutkowska, J.; Wojtczuk, R. Qubes OS architecture. Invis. Things Lab Tech. Rep. 2010, 54, 65. [Google Scholar]
- Deshane, T.; Shepherd, Z.; Matthews, J.; Ben-Yehuda, M.; Shah, A.; Rao, B. Quantitative Comparison of Xen and KVM; Xen Summit: Boston, MA, USA, 2008; pp. 1–2. [Google Scholar]
- Zhou, Z.; Yu, M.; Gligor, V.D. Dancing with giants: Wimpy kernels for on-demand isolated I/O. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 308–323. [Google Scholar]
- Kiperberg, M.; Zaidenberg, N.J. HyperPass: Secure Password Input Platform. In Proceedings of the ICISSP, Online, 11–13 February 2021; pp. 580–587. [Google Scholar]
- Ellis, C. The Best Free Screen Recorders 2021: Free Software to Capture All the Action. 2020. Available online: https://www.techradar.com/news/the-best-free-screen-recorder (accessed on 16 February 2023).
- Hacks, M. Top 11 Powerful Keyloggers for Windows. 2019. Available online: https://hackernoon.com/top-10-powerful-keyloggers-for-windows-a18d3y9h (accessed on 16 February 2023).
- Fonseca, J. VMware SVGA Device Developer Kit. 2007. Available online: https://github.com/prepare/vmware-svga (accessed on 16 February 2023).
- Toulas, B. New Intel Chips Wo not Play Blu-ray Disks Due to SGX Deprecation. 2022. Available online: https://www.bleepingcomputer.com/news/security/new-intel-chips-wont-play-blu-ray-disks-due-to-sgx-deprecation/ (accessed on 16 February 2023).
- Sibai, F.N. Evaluating the performance of single and multiple core processors with PCMARK® 05 and benchmark analysis. ACM SIGMETRICS Perform. Eval. Rev. 2008, 35, 62–71. [Google Scholar] [CrossRef]
- Lopes, F. Interception. 2015. Available online: https://github.com/oblitum/Interception/tree/v1.0.1 (accessed on 16 February 2023).



| Solution | Trusted Code Base | External Device |
|---|---|---|
| SwitchMan | OS + FW | – |
| Fidelius/ProtectIon | – | V |
| Bumpy/BitE | – | V |
| Aurora | FW | – |
| TrustLogin | FW | – |
| T-PIM | FHV + FW | – |
| Qubes OS | FHV + FW | – |
| SGXIO | Drivers + THV + FW | – |
| HyperIO | THV + FW | – |
| Screen Capturing | Key Logging |
|---|---|
| OBS Studio | Spyrix Free Keylogger |
| FlashBack Express | Actual Keylogger |
| Debut Video Capture and | All In One Keylogger |
| ShareX | HomeGuard Activity Monitor |
| Host CPU | Intel(R) Core(TM) i7-10610U |
| Host memory | 16 GB |
| Host OS | Ubuntu 20.04.1 LTS |
| VMM | VMware Workstation 15.5.6 |
| Guest CPU | Intel(R) Core(TM) i7-10610U |
| Guest memory | 8 GB |
| Guest OS | Windows 10 (19041) |
| Category | Thin Hypervisor | HyperIO | VirtualBox |
|---|---|---|---|
| App start-up | 2.29 | 6.01 | 44.92 |
| Video conferencing | −8.36 | −8.02 | 43.78 |
| Web browsing | 2.66 | 2.75 | 32.75 |
| Spreadsheet | 1.18 | 2.62 | 39.91 |
| Writing | 1.54 | 2.69 | 42.66 |
| Photo editing | −0.24 | 0.38 | 38.35 |
| Video editing | 1.77 | 5.7 | 28.02 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kiperberg, M.; Zaidenberg, N.J. HyperIO: A Hypervisor-Based Framework for Secure IO. Appl. Sci. 2023, 13, 5232. https://doi.org/10.3390/app13095232
Kiperberg M, Zaidenberg NJ. HyperIO: A Hypervisor-Based Framework for Secure IO. Applied Sciences. 2023; 13(9):5232. https://doi.org/10.3390/app13095232
Chicago/Turabian StyleKiperberg, Michael, and Nezer Jacob Zaidenberg. 2023. "HyperIO: A Hypervisor-Based Framework for Secure IO" Applied Sciences 13, no. 9: 5232. https://doi.org/10.3390/app13095232
APA StyleKiperberg, M., & Zaidenberg, N. J. (2023). HyperIO: A Hypervisor-Based Framework for Secure IO. Applied Sciences, 13(9), 5232. https://doi.org/10.3390/app13095232







