ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles
Abstract
:1. Introduction
2. Related Work
3. Black-Box Penetration Testing Framework for ICVs
3.1. Penetration Testing
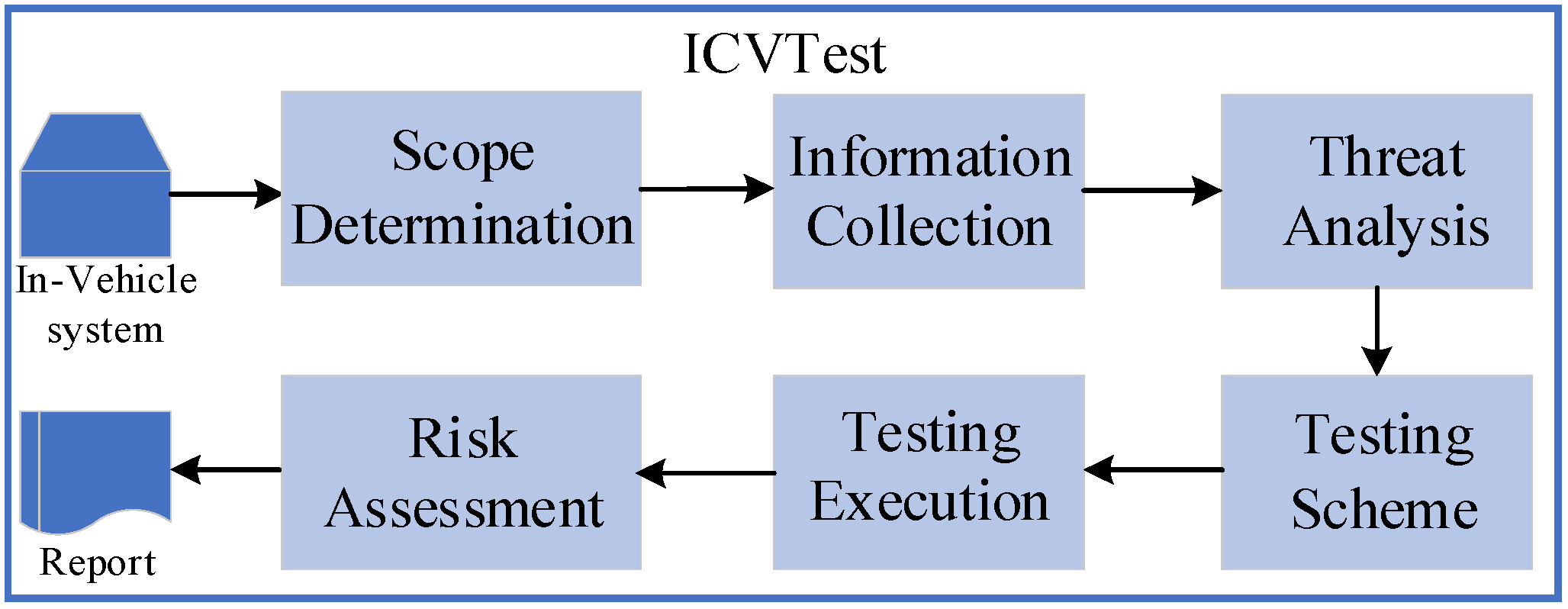
3.2. Penetration Testing Process in ICVTest
- 1.
- Scope Determination
- 2.
- Information Collection
- 3.
- Threat Analysis
- 4.
- Testing Scheme Development
- 5.
- Testing Execution
- 6.
- Risk Assessment
3.3. Penetration Testing Case Set in ICVTest
- OBD-II
- 2.
- Sensors
- 3.
- Infotainment system
- 4.
- Wireless Communication
- 1.
- Hardware Security Test Case Set
- 2.
- Firmware Security Test Case Set
- 3.
- In-Vehicle Bus Security Test Case Set
- 4.
- System Security Test Case Set
- 5.
- Radio Security Test Case Set
- 6.
- Network Security Test Case Set
- 7.
- Web Security Test Case Set
- 8.
- APP Security Test Case Set
- 9.
- Sensor Security Test Case Set
- 10.
- Privacy Security Test Case Set
3.4. Cybersecurity Testing Platform for ICVTest
- 1.
- ICVTest Infrastructure
- 2.
- ICVTest Tool and Guide Manuals
- 3.
- ICVTest Agent
- 4.
- ICVTest Web Application
4. Experiments
4.1. Scope Determination and Information Collection
- Testers can access and interact with the vehicle, but they are not permitted to dismantle it in order to obtain the ECU. Due to this limitation, hardware security testing in ICVTest cannot be fully implemented.
- Testers are not allowed to perform penetration tests on the cloud platform so as not to disrupt regular business operations.
- Testers possess physical keys and legal user accounts that enable them to log into the cloud platform. However, since they cannot physically damage or alter the vehicle, all its functions remain black-boxes for testers. With limited information available, testers can only control input parameters of vehicle functions and observe their responses.
- Despite these constraints, testers need to carry out a comprehensive penetration testing for the entire vehicle.
- Infotainment: the infotainment system features a large touch screen and operates on the Android operating system, offering numerous applications and supporting an extensive range of infotainment experiences. It provides network functionalities such as Bluetooth, 4G, Wi-Fi, and hotspot connectivity. Additionally, it enables communication with cloud platforms and mobile devices.
- Mobile device remote vehicle control: users have the ability to remotely control certain vehicular functions through a dedicated app installed on their mobile devices. Following user identity verification, operations like door unlocking, lighting control, and air conditioning adjustment can be performed remotely.
- Bluetooth digital key: users have the option to activate the Bluetooth digital key functionality which allows their mobile devices to function as virtual keys. However, it should be noted that this feature has not been activated in our experimental vehicle.
- OTA: the target vehicle can remotely upgrade certain functions through OTA.
- When the user approaches the vehicle with the physical key, passive keyless entry allows for automatic unlocking. The engine will only start when the physical key is detected inside the vehicle.
- TPMS: TPMS equipped in the vehicle sends a warning message to the driver when there is a significant deviation from normal tire pressure.
- An ultrasonic sensor installed in the vehicle alerts the driver of obstacles during reversing maneuvers.
- With traffic sign recognition enabled by a high-definition camera, road traffic signs are recognized to assist drivers in making informed decisions while driving.
- Vehicle diagnosis is facilitated through an OBD-II diagnostic interface, allowing for fault detection and localization when connected to diagnostic equipment.
4.2. Threat Analysis
4.3. Penetration Testing Scheme
4.4. Penetration Testing Execution
4.4.1. Infotainment Test
- 1.
- Bluetooth Test
- 2.
- Wi-Fi Test
- 3.
- 4G Test
- 4.
- “Vehicle-Cloud” Network Test
- 5.
- In-vehicle Operating System Test
- 6.
- USB Test
4.4.2. CAN Bus Test
- 1.
- CAN Frame Reverse Test
- 2.
- Replay Attack Test
- 3.
- Drop-Off Attack Test
- 4.
- Fuzzing Test
- 5.
- ECU Access Test
4.4.3. Remote Vehicle Control Test
- 1.
- APP Test
- 2.
- Authentication Test
- 3.
- Encryption Test
- 4.
- Integrity Test
- 5.
- Replay Test
- 6.
- PIN code Test
4.4.4. Sensor Test
- 1.
- PKES Test
- 2.
- GPS Test
- 3.
- Camera Test
- 4.
- Ultrasonic Radar Test
4.5. Cybersecurity Risk Assessment
- 1.
- Remote diagnosis service information leakage and ECU control vulnerability
- 2.
- In-vehicle USB unauthorized access vulnerability
- 3.
- ADB information leakage vulnerability
- 4.
- Unauthorized APP installation vulnerability
- 5.
- PIN brute-force cracking vulnerability
- 6.
- Insecure in-vehicle CAN bus communication vulnerability
- 7.
- GPS spoofing vulnerability
- 8.
- Ultrasonic Radar jamming vulnerability
- 9.
- Traffic sign recognition system spoofing vulnerability
- 10.
- PKE relay vulnerability
5. Discussions
5.1. Scalability
5.2. Applicability
5.3. Evolution
5.4. Privacy
5.5. Performance
5.6. Comparison
- Testing Process. The majority of frameworks do not prioritize the testing flow. Instead, most existing frameworks focus on theoretical threat analysis and risk assessment. However, our proposed ICVTest offers a standardized penetration testing procedure, which mitigates variances in test conclusions, enabling even novice testers to swiftly initiate penetration testing.
- Comprehensive Test Case Set. ICVTest abstract automotive security test scenarios into 10 sets that correspond to different fields of software and hardware architecture in vehicles, which allows for the reuse of test cases. The ability of 10 fields of vehicle cybersecurity threat modeling is not available in other frameworks.
- Integrated platform. Most frameworks only theoretically point out the threats that should be considered during security assessment, and not actual tools or platforms provided for security testing. In ICVTest, we have developed a cybersecurity testing platform to facilitate the testing task for security testers.
- Industry Scenario. The ICVTest we propose differs from the one used in educational scenario, as it demonstrates superior performance in real-world automobile cybersecurity testing scenario. While some frameworks theoretically address threat analysis and risk assessment during the vehicle design phase, they fail to tackle the issue of cybersecurity testing during the verification phase effectively. Consequently, verifying whether the identified threats indeed manifest as exploitable vulnerabilities becomes unfeasible for these frameworks.
- Vehicle Penetration Testing. ICVTest is intended for comprehensive vehicle cybersecurity testing, which includes in-vehicle subsystem cybersecurity testing as well. Furthermore, the test cases used in ICVTest are compatible with those of the in-vehicle subsystem cybersecurity test framework.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Chattopadhyay, A.; Lam, K.Y.; Tavva, Y. Autonomous vehicle: Security by design. IEEE Trans. Intell. Transp. Syst. 2020, 22, 7015–7029. [Google Scholar] [CrossRef]
- Hataba, M.; Sherif, A.; Mahmoud, M.; Abdallah, M.; Alasmary, W. Security and Privacy Issues in Autonomous Vehicles: A Layer-Based Survey. IEEE Open J. Commun. Soc. 2022, 3, 811–829. [Google Scholar] [CrossRef]
- Li, J.; Zhang, M.; Lai, Y. A light-weighted machine learning based ECU identification for automative CAN security. In Proceedings of the 2023 International Conference on Networking and Network Applications (NaNA), Qingdao, China, 18–21 August 2023. [Google Scholar]
- Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-vehicle communication cyber security: Challenges and solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef] [PubMed]
- Ma, B.; Yang, S.; Zuo, Z.; Zou, B.; Cao, Y.; Yan, X.; Zhou, S.; Li, J. An authentication and secure communication scheme for in-vehicle networks based on SOME/IP. Sensors 2022, 22, 647. [Google Scholar] [CrossRef] [PubMed]
- Francia, G.A. Connected vehicle security. In Proceedings of the International Conference on Cyber Warfare and Security (ICCWS 2020), Norfolk, VA, USA, 12–13 March 2020. [Google Scholar]
- Anwar, A.; Anwar, A.; Moukahal, L.; Zulkernine, M. Security assessment of in-vehicle communication protocols. Veh. Commun. 2023, 44, 100639. [Google Scholar] [CrossRef]
- Hariharan, S.; Papadopoulos, A.V.; Nolte, T. On in-vehicle network security testing methodologies in construction machinery. In Proceedings of the 2022 IEEE 27th International Conference on Emerging Technologies and Factory Automation (ETFA), Stuttgart, Germany, 6–9 September 2022. [Google Scholar]
- Kang, L.; Shen, H. Detection and mitigation of sensor and CAN bus attacks in vehicle anti-lock braking systems. ACM Trans. Cyber-Phys. Syst. (TCPS) 2022, 6, 1–24. [Google Scholar] [CrossRef]
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Petrovski, A.; Madzudzo, G.; Cheah, M. Ai-based intrusion detection systems for in-vehicle networks: A survey. ACM Comput. Surv. 2023, 55, 1–40. [Google Scholar] [CrossRef]
- Saber, O.; Mazri, T. Security of Autonomous Vehicles: 5g Iov (internet of Vehicles) Environment. The International Archives of the Photogrammetry. Remote Sens. Spat. Inf. Sci. 2022, 48, 157–163. [Google Scholar]
- Mudhivarthi, B.R.; Thakur, P.; Singh, G. Aspects of cyber security in autonomous and connected vehicles. Appl. Sci. 2023, 13, 3014. [Google Scholar] [CrossRef]
- Hallyburton, R.S.; Liu, Y.; Cao, Y.; Mao, Z.M.; Pajic, M. Security Analysis of {Camera-LiDAR} Fusion Against {Black-Box} Attacks on Autonomous Vehicles. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), Boston, MA, USA, 10–12 August 2022. [Google Scholar]
- ISO/SAE 21434: 2021; Road Vehicles: Cybersecurity Engineering. International Organization for Standardization ISO: Geneva, Switzerland, 2021.
- Potter, B.; McGraw, G. Software security testing. IEEE Secur. Priv. 2004, 2, 81–85. [Google Scholar] [CrossRef]
- Prathap, V.; Rachumallu, A. Penetration Testing of Vehicle ECUs. Master’s Thesis, Chalmers University of Technology, Gothenburg, Sweden, 2013. [Google Scholar]
- Schönhärl, S.; Fuxen, P.; Graf, J.; Schmidt, J.; Hackenberg, R.; Mottok, J. An Automotive Penetration Testing Framework for IT-Security Education. Cloud Comput. 2022, 2022, 10. [Google Scholar]
- Ebert, C.; Ray, R. Penetration Testing for Automotive Cybersecurity. ATZelectron. Worldw. 2021, 16, 16–22. [Google Scholar] [CrossRef]
- Dürrwang, J.; Braun, M.; Kriesten, R. Pretschner. Enhancement of automotive penetration testing with threat analyses results. SAE Int. J. Transp. Cybersecur. Priv. 2018, 1, 91–112. [Google Scholar] [CrossRef]
- Bayer, S.; Enderle, T.; Oka, D.K.; Wolf, M. Security Crash Test-Practical Security Evaluations of Automotive Onboard It Components. In Proceedings of the Automotive—Safety & Security 2014, Stuttgart, Germany, 21–22 April 2015; pp. 125–139. [Google Scholar]
- Mahmood, S.; Nguyen, H.N.; Shaikh, S.A. Systematic threat assessment and security testing of automotive over-the-air (OTA) updates. Veh. Commun. 2022, 35, 100468. [Google Scholar] [CrossRef]
- Utting, M.; Pretschner, A.; Legeard, B. A taxonomy of model-based testing approaches. Softw. Test. Verif. Reliab. 2012, 22, 297–312. [Google Scholar] [CrossRef]
- Santos, E.D.; Simpson, A.; Schoop, D. A formal model to facilitate security testing in modern automotive systems. Electron. Proc. Theor. Comput. Sci. 2018, 271, 95–104. [Google Scholar] [CrossRef]
- Mahmood, S.; Fouillade, A.; Nguyen, H.N.; Shaikh, S.A. A Model-Based Security Testing Approach for Automotive Over-The-Air Updates. In Proceedings of the 2020 IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Porto, Portugal, 24–28 October 2020. [Google Scholar]
- Li, S.; Zhang, X.; Zhou, Y.; Zhang, M. SP-E: Security Evaluation Framework of In-vehicle Infotainment System based on Threat Analyses and Penetration Tests. J. Phys. Conf. Ser. 2023, 2517, 012012. [Google Scholar] [CrossRef]
- Luo, F.; Zhang, X.; Hou, S. Research on Cybersecurity Testing for In-vehicle Network. In Proceedings of the 2021 International Conference on Intelligent Technology and Embedded Systems (ICITES), Chengdu, China, 23 September 2022. [Google Scholar]
- He, K.; Wang, C.; Han, Y.; Fang, X. Research on cyber security Technology and Test Method of OTA for Intelligent Connected Vehicle. In Proceedings of the 2020 International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Virtual Conference, China, 16 July 2022. [Google Scholar]
- Li, Q.; Zuo, J.; Cao, R.; Chen, J.; Liu, Q.; Wang, J. A Security Evaluation Framework for Intelligent Connected Vehicles Based on Attack Chains. In IEEE Network; IEEE: New York, NY, USA, 2023; p. 1. [Google Scholar] [CrossRef]
- Shirvani, S.; Baseri, Y.; Ghorbani, A. Evaluation Framework for Electric Vehicle Security Risk Assessment. IEEE Trans. Intell. Transp. Syst. 2023, 1–24. [Google Scholar] [CrossRef]
- Arkin, B.; Stender, S.; McGraw, G. Software penetration testing. IEEE Secur. Priv. 2005, 3, 84–87. [Google Scholar] [CrossRef]
- Scarfone, K.; Souppaya, M.; Cody, A.; Orebaugh, A. Technical guide to information security testing and assessment. NIST Spec. Publ. 2008, 800, 2–25. [Google Scholar]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the 20th USENIX Security Symposium (USENIX Security 11), San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Persial, J.P.; Prabhu, M.; Shanmugalakshmi, R. Side channel attack-survey. Int. J. Adva. Sci. Res. Rev. 2011, 1, 54–57. [Google Scholar]
- Devi, M.; Majumder, A. Side-Channel Attack in Internet of Things: A Survey; Springer: Singapore, 2021; pp. 213–222. [Google Scholar]
- Le, T.H.; Canovas, C.; Clédiere, J. An overview of side channel analysis attacks. In Proceedings of the 2008 ACM Symposium on Information, Computer and Communications Security, Tokyo, Japan, 18–20 March 2008. [Google Scholar]
- Agrawal, D.; Archambeault, B.; Rao, J.R.; Rohatgi, P. The EM side—channel(s). In Proceedings of the International workshop on Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, 13–15 August 2002. [Google Scholar]
- Asadi, G.; Miremadi, S.G.; Zarandi, H.R.; Ejlali, A. Fault injection into SRAM-based FPGAs for the analysis of SEU effects. In Proceedings of the 2003 IEEE International Conference on Field-Programmable Technology (FPT), Tokyo, Japan, 17 December 2003. [Google Scholar]
- Bozzato, C.; Focardi, R.; Palmarini, F. Shaping the glitch: Optimizing voltage fault injection attacks. IACR Transactions on Cryptographic. Hardw. Embed. Syst. 2019, 2019, 199–224. [Google Scholar]
- Moro, N.; Dehbaoui, A.; Heydemann, K.; Robisson, B.; Encrenaz, E. Electromagnetic fault injection: Towards a fault model on a 32-bit microcontroller. In Proceedings of the 2013 Workshop on Fault Diagnosis and Tolerance in Cryptography, Alamitos, CA, USA, 20 August 2013. [Google Scholar]
- Van Woudenberg, G.J.; Witteman, M.F.; Menarini, F. Practical optical fault injection on secure microcontrollers. In Proceedings of the 2011 Workshop on Fault Diagnosis and Tolerance in Cryptography, Nara, Japan, 28 September 2011. [Google Scholar]










| Threat | In-Vehicle System | Attack Entry | Threat Fields |
|---|---|---|---|
| ① | Infotainment | Bluetooth | Radio Threat/ System Threat |
| Wi-Fi | |||
| 4G | |||
| USB | Hardware Threat | ||
| ② | CAN Bus | OBD-II | In-vehicle Bus Threat |
| ③ | Mobile Device | APP | APP Threat |
| ④ | Sensors | PKES | Sensor Threat |
| GPS | |||
| Camera | |||
| Ultrasonic Radar | |||
| ⑤ | Network | Infotainment | Network Threat |
| APP | |||
| ⑥ | Cloud Platform | APP | Web Threat |
| Infotainment |
| In-Vehicle System | Test Case | Test Case Set |
|---|---|---|
| Infotainment | Bluetooth Test | Radio Test Case Set |
| Wi-Fi Test | ||
| 4G Test | ||
| “Vehicle-Cloud” Network Test | Network Test Case Set | |
| In-vehicle Operating System Test | System Test Case Set | |
| USB Test | Hardware Test Case Set | |
| CAN Bus | CAN Bus Test | In-vehicle Bus Test Case Set |
| Remote Vehicle Control | APP Test | APP Test Case Set |
| Network Test | Network Test Case Set | |
| Sensors | PKES Test | Sensor Test Case Set |
| GPS Test | ||
| Camera Test | ||
| Ultrasonic Radar Test |
| CAN ID | CAN Segment | Function |
|---|---|---|
| 0 × 375 | [28, 29] | left turn signal |
| 0 × 37d | [51, 51] | high beam |
| 0 × 3a5 | [20, 20] | air conditioner |
| 0 × 1a3 | [19, 21] | player volume |
| 0 × 379 | [21, 22] | right window |
| CAN ID | CAN Data | Function |
|---|---|---|
| 0 × 375 | [‘0 × 80’, ‘0 × 02’, ‘0 × 10’, ‘0 × 00’, ‘0 × 01’, ‘0 × 02’, ‘0 × 02’, ‘0 × 68’] | left turn signal |
| 0 × 37d | [‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 01’, ‘0 × a6’, ‘0 × 87’] | high beam |
| 0 × 3a5 | [‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’, ‘0 × 00’] | air conditioner |
| 0 × 1a3 | [‘0 × 1a’, ‘0 × ed’, ‘0 × 40’, ‘0 × d9’, ‘0 × 7b’, ‘0 × 00’, ‘0 × 06’, ‘0 × 72’] | player volume |
| 0 × 379 | [‘0 × 59’, ‘0 × d0’, ‘0 × 00’, ‘0 × 11’, ‘0 × 45’, ‘0 × 68’, ‘0 × 95’, ‘0 × 14’] | right window |
| CAN ID | CAN Data | Function |
|---|---|---|
| 0 × 375 | [‘0 × 41’, ‘0 × 02’, ‘0 × 10’, ‘0 × 1d’, ‘0 × 00’, ‘0 × 02’, ‘0 × 12’, ‘0 × 3a’] | left turn signal |
| 0 × 375 | [‘0 × aa’, ‘0 × 41’, ‘0 × 00’, ‘0 × 24’, ‘0 × 0c’, ‘0 × 19’, ‘0 × a3’, ‘0 × b5’] | left turn signal |
| 0 × 42c | [‘0 × b1’, ‘0 × 0a’, ‘0 × ba’, ‘0 × c6’, ‘0 × de’, ‘0 × f4’, ‘0 × 03’, ‘0 × bc’] | wiper |
| 0 × 37b | [‘0 × 29’, ‘0 × ee’, ‘0 × a3’, ‘0 × 9b’, ‘0 × 04’, ‘0 × 1a’, ‘0 × 7e’, ‘0 × 72’] | high beams |
| 0 × 283 | [‘0 × 3a’, ‘0 × dc’, ‘0 × 54’, ‘0 × 9b’, ‘0 × ac’, ‘0 × c8’, ‘0 × 24’, ‘0 × 1a’] | seat belt warning light |
| 0 × 44c | [‘0 × b9’, ‘0 × 07’, ‘0 × ec’, ‘0 × 5a’, ‘0 × 30’, ‘0 × 80’, ‘0 × 7c’, ‘0 × 59’] | sunroof |
| Metric | Definition | Parameter |
|---|---|---|
| Response Time | The number of services that can be handled by the platform per unit time | <500 ms |
| Query to View Time | The total time consumed by the Query service | <50 ms |
| Query per Second | The number of queries the platform can process per unit time | >600 |
| Transaction per Second | The number of integrated services that can be handled by the platform per unit time | >400 |
| Concurrent Users | The number of users who simultaneously log in to the platform and perform business operations | ≥30 |
| Concurrent Agents | The number of agents that log in and register at the same time for business processing | ≥30 |
| Failure Ratio | Failure Ratio = (failed service)/(total service) * 100% | <0.1% |
| CPU Usage | Utilization rate of CPU resources (mean/peak) under platform service | 12%/80% |
| RAM Usage | Utilization rate of RAM resources (mean/peak) under platform service | 1 GB/8 GB |
| Disk Throughput | The amount of data read and write from a disk per unit time in the absence of disk failure | 400 MB/s |
| Network Throughput | The number of network data per unit time in the absence of network failures | 9 MB/s |
| Framework | Process | Test Case Set | Platform/Tool | Scenarios | Type |
|---|---|---|---|---|---|
| ICVTest | Yes | 10 | Yes | Penetration Testing | VPT |
| Q. Li et al. [28] | No | 3 | No | Risk Assessment | VPT |
| Shirvani et al. [29] | No | 10 | No | Risk Assessment | VPT |
| Schönhärl et al. [30] | No | 3 | Yes | Education | VPT |
| S. Li et al. [25] | No | 4 | No | Penetration Testing | IVSTP |
| F. Luo et al. [26] | Yes | 1 | Yes | Penetration Testing | IVSTP |
| K. He et al. [27] | No | 2 | Yes | Penetration Testing | IVSTP |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, H.; Wang, J.; Wang, Y.; Li, M.; Song, J.; Liu, Z. ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles. Appl. Sci. 2024, 14, 204. https://doi.org/10.3390/app14010204
Zhang H, Wang J, Wang Y, Li M, Song J, Liu Z. ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles. Applied Sciences. 2024; 14(1):204. https://doi.org/10.3390/app14010204
Chicago/Turabian StyleZhang, Haichun, Jie Wang, Yijie Wang, Minfeng Li, Jinghan Song, and Zhenglin Liu. 2024. "ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles" Applied Sciences 14, no. 1: 204. https://doi.org/10.3390/app14010204
APA StyleZhang, H., Wang, J., Wang, Y., Li, M., Song, J., & Liu, Z. (2024). ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles. Applied Sciences, 14(1), 204. https://doi.org/10.3390/app14010204





