Abstract
To solve the limitations of reversible data hiding in encrypted domains (RDH-ED) that cannot be applied to a distributed variable security environment, a novel RDH-ED scheme based on variable threshold image secret sharing (VTSIS) is proposed. Initially, a security vulnerability analysis of existing changing thresholds in a bivariate polynomial-based secret image sharing (TCSIS) method is conducted and validated through experiments. Subsequently, enhancements are made to the VTSIS scheme to rectify the identified security loopholes. During the image encryption process, additional data can be embedded into the redundancy of VTSIS, which results in a large embedding rate and high security. Finally, theoretical analysis and experimental proofs are carried out for the proposed scheme, and the results show that our scheme broadens the application scenarios of RDH-ED. Notably, the scheme eliminates the need for preprocessing and has the advantages of high security, a large embedding rate, and complete reversibility.
1. Introduction
Image data hiding involves concealing information within a publicly shared image in a manner that remains imperceptible to casual observers. The concealed data can be extracted by the intended recipient and serves various purposes, such as covert communication and copyright protection. Many techniques have been used to design data-hiding schemes, such as least significant bit substitution [1] and matrix coding [2]. However, traditional data-hiding methods often result in significant distortions to the cover image. To tackle this challenge, reversible data hiding (RDH) [3] has been introduced. RDH not only enables the extraction of hidden data but also ensures the recovery of the original image. This technology finds applications across various fields, including social media, medical data, and financial information. Moreover, RDH facilitates covert data transmission and storage, enhancing data transmission security and making it a preferred option in cloud computing and the Internet of Things (IoT). Additionally, RDH plays a vital role in safeguarding digital copyrights by embedding copyright information to enable data traceability and content protection.
There are many RDH schemes, such as difference expansion [4], histogram shifting [5], prediction error expansion [6], and lossless compression-based schemes [7]. These schemes can be effectively used in scenarios that require high reversibility. Recently, numerous studies have significantly enhanced the performance and efficiency of RDH by integrating deep learning [8,9], blockchain technology [10,11], and IoT technology [12] into algorithm optimization. However, in certain situations, such as in cloud computing services, safeguarding the privacy of carrier images is paramount. Consequently, reversible data hiding in encrypted domain (RDH-ED) [13] has been proposed to address this need.
RDH-ED refers to the embedding of additional information in an encrypted carrier, which is characterized by the fact that the carrier used for embedding is encrypted. This requires that the embedded information can be accurately extracted and that the original image can be recovered without any loss. The key to RDH-ED is to find and utilize redundant space in the carrier. Based on the method of generating redundancy, embedding algorithms can be classified into three categories: vacating room after encryption (VRAE) [14,15], vacating room before encryption (VRBE) [16], and vacating redundancy in encryption (VRIE) [17,18]. The VRIE scheme seamlessly integrates data hiding with cryptography, leading to enhancements in security, reversibility, and embedding rate (ER). However, the current cryptographic algorithms applicable to the VRIE schemes are difficult, so the research is limited.
While these schemes offer complete reversibility, it is crucial to acknowledge that if the tagged encrypted image is lost due to a single point of failure, the embedded secret data and images become irretrievable. Therefore, distributed storage is needed. Moreover, with the rapid development and application of cloud computing, distributed environments represented by distributed cloud services [19], edge computing [20], and federated learning [21] continue to emerge. However, traditional RDH-ED schemes introduce only a single participant and cannot meet the security requirements of distributed systems [22,23]. In recent years, several RDH-ED schemes based on secret sharing (SS-RDHED) [24] have been proposed. The threshold effect of secret sharing makes it more disaster-tolerant and suitable for distributed scenarios.
In 2018, Wu et al. [25] first proposed a VRAE SS-RDHED scheme, which embeds additional data into the shared image after secret sharing using difference expansion and prediction error histogram panning, with low computational complexity and high embedding capacity. Chen et al. [26] exploited the additive homomorphism property of secret sharing and combined it with difference expansion to embed secret data into a pair of pixels, which reduces the time complexity; however, this scheme has only one data hider. Chen et al. [27] proposed a scheme with multiple data hiders, but its ER is limited by the number of hiders. Ke et al. [28] used the Chinese remainder theorem to design an SS-RDHED, which achieves separation and better reversibility. Qin et al. [29] proposed SS-RDHED on the Galois field (GF)(p) and GF(28), which has a low distortion rate and solves the pixel overflow problem. To solve the disadvantage of traditional secret sharing without diffusion, Hua et al. [30] constructed a polynomial encryption method in Cipher Feedback mode that can effectively resist a variety of attacks. Subsequently, Hua et al. [31] proposed a scheme using matrix secret sharing, which can extract data without loss, and its embedding capacity is much larger than that of the existing scheme. To adapt to distributed systems with multiple participants, Xiong et al. [32] utilized the comprehensive decoding of Hamming codes and additive homomorphism of polynomials; multiple data hiders can embed the shared data into the shared image. Recently, Hua et al. [33] designed an embedding scheme based on secret sharing without preprocessing, and a reliable key management system was not required to securely manage the secret image. Yu et al. [34] proposed a new SS-RDHED based on the Chinese residual theorem and hybrid coding, which utilizes iterative encryption to preserve the correlation between encrypted blocks and has better embedding performance. Xiong et al. [35] used secret sharing to divide secret data and then used the proposed modification–recomputation strategy to generate labeled shared images, obtaining fault tolerance and full separability. Yu et al. [36] used pixel value order technology and secret sharing, allowing multiple data hiders, which can address the limitations of single data hider scenarios, enhancing the scheme’s flexibility and security, particularly in applications requiring robust copyright protection.
Most of the existing SS-RDHEDs have been developed assuming a static security environment where the threshold remains constant. However, in reality, security landscapes are dynamic, necessitating adjustments to the threshold based on varying situations and risks. For instance, within the financial sector, the information security standards of banks may require modifications to address diverse risks and threats. During normal circumstances, banks might maintain a relatively lower information security level to offer more convenient services and enhance operational efficiency. Yet, in times of financial crises or other significant events, banks may swiftly elevate their information confidentiality protocols and bolster security measures to preempt potential threats and attacks.
To adapt to the variable security environment, Sun et al. [37] proposed changing the threshold in a bivariate polynomial-based secret image-sharing scheme (TCSIS), which can provide multiple possible thresholds. When the secret level is low, fewer participants can recover the secret information, and when the secret level is high, more participants are required to recover it. Using this scheme to design RDH-ED has extensive application potential, and there is a large amount of coefficient redundancy available for embedding additional data during the construction of binary polynomial coefficients. However, this scheme uses all the image pixels as the coefficient matrix of the binary polynomial, which is susceptible to exhaustive attacks due to the strong correlation between the pixels in each row and column. Therefore, the resistance to attacks needs to be improved by eliminating the correlations between pixels. The traditional method is to encrypt the carrier image, but the complex encryption process affects its practicality. Therefore, we propose preprocessing-free RDH-ED based on the improved TCSIS (VTSIS), which uses a random substitution matrix as the hiding key to implement embedding in the polynomial coefficients, which leads to the existence of only a single pixel value or an extra secret in each row and column of the polynomial coefficient matrix. The experiments demonstrate that the scheme in this paper achieves better security and ER without preprocessing. The main contributions of this paper are as follows:
- A VRIE RDHED scheme applicable to a distributed variable security environment is proposed, which extends the application scenarios.
- Improving the security of existing TCSIS and using the redundancy space to embed extra data in the encryption process results in better security and embedding performance.
- Using the random substitution matrix as the hidden key, only the seed key needs to be transmitted without transmitting the hidden key to the extractor, which effectively reduces communication overhead and improves security.
- Theoretical analyses and experimental results show that the proposed scheme has high security, a large embedding rate, complete reversibility, and low computational complexity. In addition, it does not require preprocessing and solves the problem of pixel overflow.
The remainder of this paper is as follows: In Section 1, the relevant work is introduced, which mainly focuses on the security analysis and experimental effect demonstration of the TCSIS scheme. Section 2 describes the algorithm in detail and provides a specific example for elucidation. In Section 3, the superior performance of the scheme is proven by many theoretical analyses and experiments. Finally, this paper concludes with a summary.
2. Related Work
2.1. Shamir’s (k, n) Secret Sharing
Theorem 1.
For any k distinct points , the k − 1th polynomial can be uniquely determined by the Lagrange interpolation formula:
Shamir first proposed a secret sharing scheme based on Theorem 1. First, the k − 1th polynomial can be constructed using the secret s and the random numbers a1, a2, …, ak−1. Then, the secret shares (i = 1, 2, …, n) are computed and distributed to n different users . According to Theorem 1, can be reconstructed via any k different , so the coefficients s, a1, a2, …, ak−1 can be recovered.
2.2. Security Analysis of the TCSIS Scheme
The scheme on GF (28) in [37] uses binary polynomials to construct a TCSIS that can provide multiple thresholds. The participants update the initial shares autonomously according to the changing thresholds without the involvement of the secret owner, which effectively improves security. The TCSIS scheme is described as follows:
- Secret share generation
First, the image owner divides the image into blocks equally, and each block contains pixels. Then, the owner selects a block to construct a binary polynomial. Assuming its pixel value is , i = 0, 1, …, k − 1, j = 0, 1, …, h − 1, the polynomial can be expressed as follows:
The owner computes and ; then, can be an initial share distributed to the participants , t = 0, 1, …, n.
- 2.
- Secret image reconstruction
The secret owner selects the threshold T from according to the current security environment, and the participants update the shares according to different thresholds using the corresponding methods:
- When , updates the secret share to ;
- When , updates the secret share to ;
- When , first choose h-T integers randomly different from 1, 2, …, n and then update the secret share to .
The scheme is susceptible to exhaustive attacks using all pixel values as all polynomial coefficients. Assuming that there are T − 1 different ( = 0, 1, …, k − 1) attempts to recover the secret image, the T − 1 attacker can provide T − 1 different shares: , , …, . From Equation (2), F(x, y) can be expressed as follows:
where , , …, are monic polynomials of order k − 1. In addition, can be expressed as:
Therefore, can be regarded as the interpolation of , and [37]. Then, the k − 1 attacker can provide k − 1 different to obtain k − 1 different equations:
Although Equation (5) contains k unknowns and the attacker can only provide k − 1 equations, since , an exhaustive attack on one of the unknowns 255 times can yield 255 different solutions. Since there is a strong correlation between the image pixels, the attacker can determine the correct solution from the 255 different solutions. Similarly, attacking each column of the coefficient matrix up to 255 times yields the correct solution, so up to 255 exhaustive attacks can recover the secret image block. We have experimentally proven this security problem, and the results are shown in Figure 1. The test images are gray images selected from BOWS2 (https://dde.binghamton.edu/download/ (Accessed on 20 June 2017)) named Peppers, Woman, Baboon, Airplane, and Camera. Figure 1a–e are the original images, and Figure 1f–j are the reconstructed images when k − 1 attackers are involved. It can be seen that when k − 1 attackers are involved in reconstructing the images, the general outline characteristics of the test images can be obtained, which proves that there is a large security vulnerability in the TCSIS.
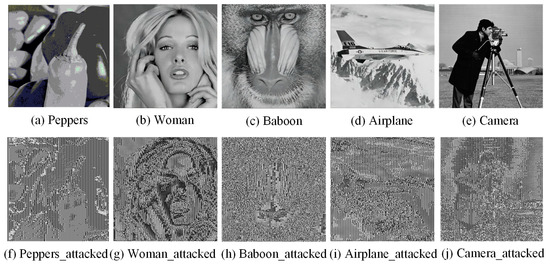
Figure 1.
Test image and attack effect when k − 1 attackers are involved in reconstructing the images.
3. Proposed RDH-ED Scheme Based on VTSIS
The security environment in the cloud environment is variable and may be affected by factors, such as the secret security level, secret urgency, and adversary attack capability. Hence, it becomes imperative to tailor strategies in response to this dynamic security environment. The framework of the proposed scheme is illustrated in Figure 2, delineated into three primary stages: image encryption and data embedding, secret share updating, image reconstruction and secret extraction. Initially, the original carrier image is encrypted with VTSIS. At the same time, the secret is embedded into the polynomial coefficient redundant generated in the encryption process. After embedding, n shares generated by VTSIS are distributed to n different participants, with the threshold value T = k. T can be adjusted according to the new security environment when the security environment is changed, and the values {k, k + 1, …, h} can be taken. The receiver can collect T shares randomly to extract the secret and recover the carrier image.
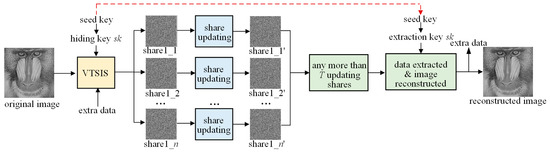
Figure 2.
The framework of the proposed scheme.
3.1. Secret Sharing and Data Embedding
The process of secret sharing and data embedding is shown in Algorithm 1. The secret owner chooses a prime number p to construct the Galois domain and selects . Every eight bits of the secret to be embedded are converted into decimal numbers. To improve security, different encryption algorithms can be selected according to the characteristics of the data to be embedded, e.g., stream encryption, AES, or some more efficient encryption algorithms [38]. The data hider uses a pseudorandom number generator to generate a coefficient matrix of size and then uses the seed key to generate a substitution matrix of size (each row and column has one and only one element that is 1, all others are 0.) as the hidden key sk. The embedding is performed by scanning the key matrix from top to bottom and from left to right. The position of one is the position of the embedding image pixel and extra secret, and the position of zero remains unchanged. The data hider can embed k − 1 secrets in each pixel. Assuming that the lth pixel of the original image is , l = 0, 1, …, , is the size of the image, and the k − 1 secrets to be embedded are , , …, , the generated coefficient matrix coefficients are , i = 0, 1, …, k − 1, j = 0, 1, …, h − 1. The data hider first constructs a polynomial using the as follows:
Then, the data hider can generate the hidden key based on the seed key. Pixel encryption and data embedding can be implemented by replacing pixels or extra secrets with random numbers. The secret owner computes , , t = 1, 2, …, n. can be the initial share distributed to n participants. At the same time, the seed key can be sent to the participants via a secure channel.
| Algorithm 1: Secret sharing and data embedding |
| Input: original image, prime number p, k, n |
| 1: Scan the original image to obtain the size M × N; |
| 2: l←1; |
| 3: while l < M × N do |
| 4: Scan pixel to obtain pl; |
| 5: Generate k × h coefficient matrix C using pseudorandom number; |
| 6: Generate k × k hiding key matrix H using the seed key; |
| 7: Encrypt extra secrets using AES; |
| 8: Construct the polynomial F(x, y); |
| 9: Scan di,j in C and di,j’ in H; |
| 10: if di,j’ = = 1 |
| 11: then replace di,j with extra secrets or pl; |
| 12: else |
| 13: not to change di,j |
| 14: return F(x, y); |
| 15: Calculate ft(y) = F(t, y), gt(x) = F(x, t) then distribute (ft(y), gt(x)) to participant Pt; |
| 16: end if |
| 17: l←l + 1; |
| 18: end while |
| Output: Share images with extra secrets embedded |
An instance flowchart is shown in Figure 3, when k = 2, h = 3, n = 4, and p = 251, the data hider first utilizes the 6 to construct a polynomial as follows:
The hidden key generated via the seed key is as follows:
Assuming that the pixel is 86, and the secret to be embedded is 79, the embedding process is shown in Equation (9).
The data hider first calculates the initial shares and . Four initial secret shares can be obtained, and distributed to four different participants. Each participant obtains the initial share as follows:
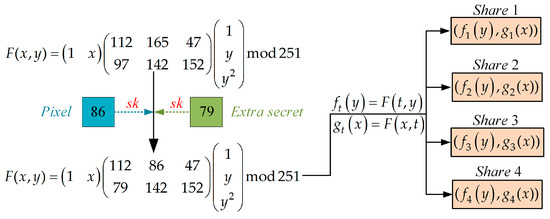
Figure 3.
The instance flowchart of secret sharing and data embedding.
3.2. Secret Extraction and Image Reconstruction
The process of secret extraction and image reconstruction is shown in Algorithm 2. Assuming that there are m (m = T) participants to extra secrets, the participants first update their shares according to the following threshold:
- If , updates the secret share to ;
- If , updates the secret share to ;
- If , first choose h-T integers randomly different from 1, 2, …, n, and then update the secret share to ;
| Algorithm 2: Secret extraction and image reconstruction |
| Input: Share images with extra secrets embedded, T, k, n |
| 1: l←1; |
| 2: while l < M × N do |
| 3: if T = = k |
| 4: Update the original secret share to = ft(y); |
| 5: else if k < T < h |
| 6: Select h-T distinct integers e1, e2, …, eh-T excluding 1, 2, …, n; |
| 7: Update the original secret share to = {, ft(e1), ft(e2), …, ft(eh-T)}; |
| 8: else if T = = h |
| 9: Update the original secret share to = gt(x); |
| 10: Reconstruct F(x, y) from the updated shares using Equation (1); |
| 11: Extract pixel and extra secrets according to hiding key; |
| 12: end if |
| 13: l←l + 1; |
| 14: end while |
| Output: reconstructed Secret, reconstructed image |
The extractor can reconstruct the coefficient matrix according to the Lagrange interpolation. After generating the extractor key using the seed key, the image pixel and extra data can be obtained. For enhanced comprehension, an instance flowchart is shown in Figure 4, and two examples are given as follows:
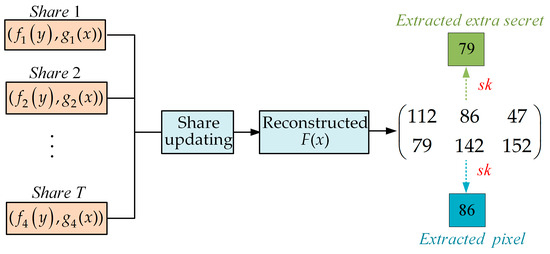
Figure 4.
The instance flowchart of secret extraction and image reconstruction.
- When T = 2, the secret owner updates the share to . If and need to extract the extra data, Equation (11) can be obtained by the Lagrange interpolation formula:where is the reconstructed polynomial, and its coefficients are 112 and 79. The reconstructed coefficient 79 is the embedded secret. In the same way, and can be reconstructed, so the original pixel and the embedded secret can be recovered.
- When T = 3, the secret owner updates shares to . If , and need to extract the extra data, Equation (12) can be obtained by the Lagrange interpolation formula:where is the reconstructed polynomial, and its coefficients are 112, 86 and 47. The reconstructed coefficient 86 is the pixel. In the same way, can be reconstructed, so the original pixel and the embedded secret can be recovered.
4. Theoretical and Experimental Analyses
The experiments were conducted on Windows 10, programmed with Python 3.6 and MATLAB R2021b. The experimental equipment configuration is an Intel(R) Core(TM) i7-11800H 2.30 GHz, 32 GB. The test images selected from BOWS2 (https://dde.binghamton.edu/download/ (Accessed on 20 June 2017)) named Jetplane, Peppers, Airplane, Goldhill, and Baboon are shown in Figure 5, all of which are 512 × 512 grayscale images but with different texture features. The parameter settings are as follows: k = 2, h = 4, and n = 4; thus, T can be 2, 3, or 4. Normally, the prime number p is taken to be 251, but this makes it impossible to handle pixels larger than 250, leading to pixel overflow problems, so we choose p = 28.

Figure 5.
The test images.
4.1. Correctness
- When , participant updates the original secret share to . can be expressed as . , , …, are monic polynomials of order k − 1. Because can be expressed as , , , …, can be regarded as the interpolation of , and . Since is a k − 1 order polynomial, the threshold of reconstructing with , , …, is k. Similarly, the thresholds of reconstructing , , …, are all k. In other words, k secret shares can reconstruct the binary polynomial.
- When , participant updates the original secret share to . can be expressed as . , , …, are monic polynomials of order k − 1. Because can be expressed as , , , …, can be regarded as the interpolation of , and . Since is an h − 1 order polynomial, the threshold for reconstructing with , , …, is h. Similarly, the thresholds for reconstructing , , …, are all h. In other words, h secret shares can reconstruct the binary polynomial.
- When , participant updates the original secret share to . Here , , …, are h-T integers randomly chosen and different from 1, 2, …, n. Since , can be regarded as an interpolant of . Since is a k − 1 order polynomial when , can be reconstructed from T updated shadows , where t = 1, 2, …, T. Therefore, , , …, can be reconstructed from . can be expressed as . Therefore, additional h-T additional interpolations can be obtained. Since T interpolations can be obtained from and , , …, are the h − 1st degrees, so can be reconstructed.
4.2. Visualization
The visual effect is the most intuitive way to evaluate the feasibility of the scheme. The test effect of Peppers is shown in Figure 6. Figure 6a is the original image, Figure 6b is the first share, and Figure 6c–e are the reconstructed images for T = 2, T = 3, and T = 4, respectively. The share is irregularly distributed, which indicates that the scheme has high security. The reconstructed images with different thresholds are consistent with the original image, which shows the feasibility of the proposed scheme.

Figure 6.
The visual presentation of the proposed scheme.
4.3. Security
4.3.1. Analysis of Attack Resistance
In the scenario where the attacker acquires any T − 1 secret shares, the reconstruction of the polynomial becomes infeasible. At most, only the T − 1 equations can be used to solve for T unknowns. An exhaustive enumeration of a given unknown p times yields p solutions, and since there is no correlation between individual pixels, the attacker strikes are unable to determine the correct solution to the equation from p different solutions. Assuming that the attacker collects any secret share greater than or equal to T shares, can be reconstructed by the Lagrange interpolation formula, which can recover the coefficients. Nevertheless, lacking an extraction key, the attacker remains incapable of determining the carrier pixel’s location or extracting the embedded secret.
4.3.2. Histogram
A histogram serves as a visual representation of the pixel distribution. The greater the uniformity in pixel distribution, the more robust and resistant the scheme becomes against statistical analysis attacks. The histograms of Peppers are shown in Figure 7. To show the pixel distribution more clearly, scatterplots and 3D histogram distributions were also tested. The results show that the pixel distribution of the share image is more uniform, which indicates that the scheme has high security. In addition, the pixel distributions of the reconstructed image and original image remain consistent, indicating that the carrier image is fully recoverable. In addition, we tested the scheme with the threshold value changed. As depicted in Figure 7, for T = 3 and T = 4, the reconstructed image maintains an identical pixel distribution to the original image, which shows that the proposed scheme has threshold variability.
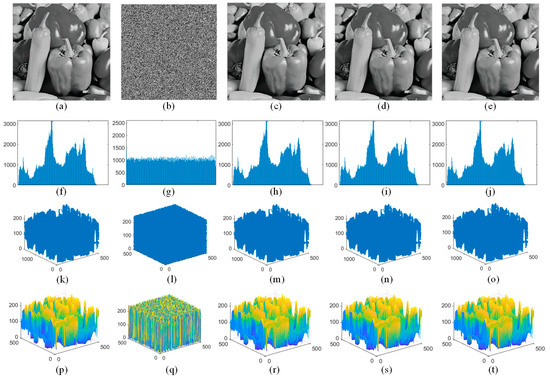
Figure 7.
Histogram of Peppers ((a) original image, (b) the first share, (c) the reconstructed image at T = 2, (d) the reconstructed image at T = 3, (e) the reconstructed image at T = 4; (f–j) the corresponding plane histogram; (k–o) the corresponding scatter histogram; (p–t) the corresponding 3D histogram).
4.3.3. Entropy
Information entropy is used to describe the uncertainty or randomness of data. The entropy can be calculated by Shannon’s information entropy formula, which is calculated as follows:
where H(X) denotes the entropy of random X and P(x) is the probability of x. For a grayscale image, Z = 256. When all pixels have the same probability, i.e., , H(X) achieves a theoretical maximum value, i.e., . Therefore, for a grayscale image, the closer H(X) is to, the more secure the image is. Table 1 shows the entropy of the shared images of the five test images, and the entropy of the image with only two shares is reconstructed when T = 3. An entropy close to eight indicates that this proposed scheme has a good encryption effect without preprocessing, and the shares with less than the threshold condition cannot recover the carrier image correctly. Table 1 shows that the entropy of the four generated shares is close to eight, indicating that our scheme can achieve an excellent encryption effect without preprocessing. In addition, when T = 2, the entropy of the reconstructed image is also close to eight, demonstrating that the image reconstructed by participants with less than the threshold condition is also irregular, i.e., the carrier image cannot be recovered at this time.

Table 1.
Entropy of the 5 test images.
4.3.4. Pixel Correlation
A small pixel correlation in the encrypted image means that the scheme is more secure. We tested the correlation coefficients from four angles, horizontal, vertical, 45°, and 135°, called RH, Rv, RD, and RID. First, Peppers’ first share was tested, and the results are shown in Figure 8, which shows that the pixels in the share are uniformly distributed and the pixel correlation coefficients of the four directions are close to zero, which indicates that the scheme has a terrific encryption effect. Then, we tested the reconstructed image with only two shares when T = 3, and the results are shown in Figure 9. The pixel correlation coefficients in all four directions are also close to zero, indicating that less than the threshold number of participants cannot reconstruct the carrier image.
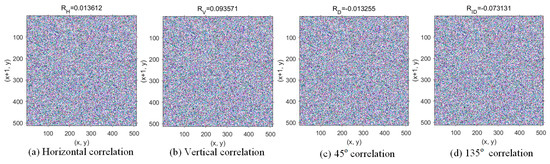
Figure 8.
Pixel correlation in the four directions of the first share.
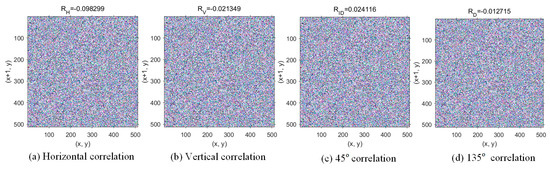
Figure 9.
Pixel correlation in the four directions of the reconstructed image with only two shares when T = 3.
4.4. Reversibility
4.4.1. PSNR and SSIM
Reversibility refers to whether the original image can be completely recovered and the extra data can be extracted without loss. The peak signal-to-noise ratio (PSNR) and structural similarity (SSIM) can be used to evaluate the reversibility, which is calculated as follows:
where X is the original image, Y is the comparison image, P(i, j) is the original image pixel, P’(i, j) is the comparison image pixel, MX and MY are the mean values of X and Y, respectively, CX and CY are the standard deviations of X and Y, respectively, CXY represents the covariance of X and Y, and Cons1, Cons2 and Cons3 are constants. The larger the PSNR is, the closer the SSIM is to 1, which indicates greater reversibility. If and SSIM = 1, the scheme is fully reversible. Furthermore, when dB, there is no visual difference. The experiments were conducted on five test images, and the results are shown in Table 2. The PSNR values are all , and the SSIM values are all 1, which indicates that the proposed scheme is fully reversible. Since the proposed scheme uses Lagrange interpolation to reconstruct the image, its binary polynomial coefficients can be recovered, so the carrier image pixels and embedded extra data can be recovered correctly. To better highlight the advantages of the proposed scheme, we conducted a comparative analysis of the PSNR between our scheme and other high-performance schemes. The comparison results are illustrated in Figure 10. The PSNR of schemes [18,23,26,28] decreases with increasing ER, which indicates that the PSNR is greatly affected by the ER and that the carrier image is not completely reversible. In contrast, for schemes [29,34] and our scheme, which utilize polynomial secret sharing to encrypt the image, the PSNR is infinite and is not affected by the ER, which indicates that our scheme is fully reversible and has more stable reversibility.

Table 2.
PSNRs and SSIMs of the reconstructed images of the test images.
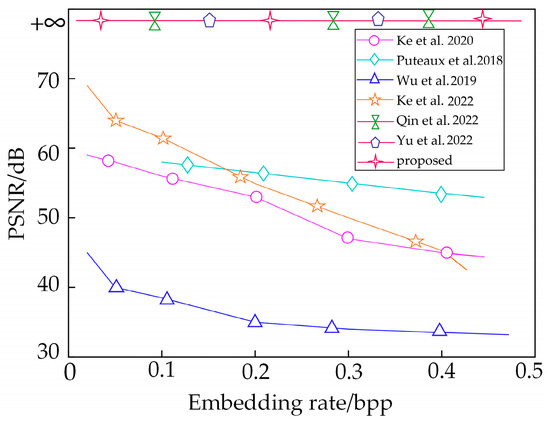
Figure 10.
Comparison of PSNR for different schemes [18,23,26,28,29,34].
4.4.2. Error Map
The error map serves as a detailed comparison between the processed data and the original data on a bit-by-bit basis. If the comparisons are equal, the error rate is zero. If the error maps of the reconstructed image and the original image are zero and the error maps of the extracted data and the embedded data are zero, the scheme is fully reversible. Figure 11 shows the error map of the extracted data and the error map of the reconstructed image after embedding the data in Peppers, from which it can be shown that the scheme is fully reversible.
Figure 11.
The error map of Peppers.
4.5. Embedding Rate
The ER represents the average amount of additional data embedded per pixel. The embedding method of this scheme is polynomial redundancy embedding, which is related only to the size of the carrier and the choice of parameters. It can be calculated as follows:
It can be seen that the proposed scheme has a more stable embedding performance because the ER is only related to the parameters k and n. Table 3 demonstrates the maximum ER of our scheme under the different common thresholds, from which it can be seen that the ER is independent of the value of h when k and n are certain, and the ER is better when n-k is smaller. To demonstrate the superior embedding performance of the proposed scheme, Figure 12 shows the comparison results of the ER between the proposed scheme and similar state-of-the-art schemes. The ER of the proposed scheme is the highest of all five test images in the scheme. Moreover, it has the greatest ER in the test image except for the Airplane under the common and schemes, because the Airplane is relatively homogeneous, a large number of redundant pixels can be compressed and extra data can be embedded. The comparison schemes are all based on secret sharing, when k = n, those schemes are not disaster-tolerant. Therefore, the scheme has a wider range of applications when k ≠ n. In this case, our scheme also has better embedding performance. Since this proposed scheme makes full use of the binary polynomial coefficient redundancy generated in the encryption process, the scheme has a larger ER and a more stable embedding performance.

Table 3.
ER of the proposed scheme at different thresholds.
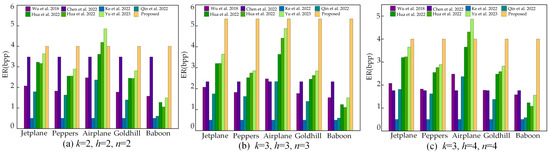
Figure 12.
Comparison of ER for different schemes [25,27,28,29,30,31,34].
4.6. Applicability
In this paper, we utilize the scheme to encrypt images and embed additional data in the encryption process, which is then stored on multiple participants. In this way, even if one or more participants are breached, the carrier images and secrets can still be recovered from other shares. Therefore, it has strong disaster tolerance. Moreover, the thresholds are dynamically changeable and can change with changes in the current security environment, which has stronger applicability and can be adapted to the application requirements of secure multiparty computing, federated learning, blockchain, multiparty copyright protection, and other scenarios in the cloud computing environment. In future applications, medical image transmission systems, distributed security authentication systems, identity authentication systems, and military information transmission systems can be designed based on the algorithm experiment of this paper, which has wide application value.
5. Conclusions
Aiming at current distributed scenarios with variable security environments, this paper proposes an RDH-ED scheme based on VTSIS. First, this paper identifies and demonstrates security problems with existing TCSIS and proposes VTSIS by improving the TCSIS. Then, the redundancy of VTSIS is used for image encryption and data hiding, which achieves high-capacity embedding and high security. Finally, the effectiveness of the proposed scheme is proven through many theoretical analyses and experiments. The results show that the proposed scheme has a higher ER than current state-of-the-art schemes at commonly used thresholds, and it has high security and complete reversibility without any preprocessing. Most importantly, this study expands the application of RDH-ED. However, there are several shortcomings in our scheme. In the secret sharing scheme, when one pixel of the original image is changed, only a few pixels of the ciphertext pixels are also changed. Therefore, it does not have diffusion properties, which results in our scheme being unable to effectively resist differential attacks. In future research, it can be combined with cryptographic grouping linking, cryptographic feedback mechanism, etc., to improve security.
Author Contributions
The authors confirm contribution to the paper as follows: conceptualization, C.J., M.Z. and F.D.; methodology, C.J. and M.Z.; validation, C.J. and X.Z.; formal analysis, C.J., M.Z. and F.D.; investigation, C.J. and X.Z.; data curation, C.J.; writing—original draft preparation, C.J.; writing—review and editing, C.J., M.Z. and F.D.; visualization, M.Z.; supervision, M.Z.; project administration, M.Z. sand F.D.; funding acquisition, M.Z. and F.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, grant numbers 62272478, 62102450, 61872384, 62102451, 62202496 and Social Science Funds of China (No. 2022-SKJJ-C-091).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data that support the findings of this study are available from the first author, [Chao Jiang], upon reasonable request. The URL of the core code is as follows: https://github.com/Hackfreedom888/RDH-ED-based-on-RDH-ED (accessed on 3 June 2024).
Acknowledgments
The authors would like to thank the editor and anonymous reviewers for their valuable comments, which helped to improve this paper.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Solak, S. High embedding capacity data hiding technique Based on EMSD and LSB substitution algorithms. IEEE Access 2020, 8, 166513–166524. [Google Scholar] [CrossRef]
- Kim, C.; Shin, D.; Yang, C.; Chen, Y.; Wu, S. Data hiding using sequential hamming + k with m overlapped pixels. KSII Trans. Internet Inf. Syst. 2019, 13, 6159–6174. [Google Scholar] [CrossRef]
- Shi, Y.Q.; Li, X.; Zhang, X. Reversible data hiding: Advances in the past two decades. IEEE Access 2016, 4, 3210–3237. [Google Scholar] [CrossRef]
- Dragoi, I.C.; Coltuc, D. Local-prediction-based difference expansion reversible watermarking. IEEE Trans. Image Process. 2014, 23, 1779–1790. [Google Scholar] [CrossRef]
- Wang, J.; Ni, J.; Zhang, X. Rate and distortion optimization for reversible data hiding using multiple histogram shifting. IEEE Trans. Cybern. 2016, 47, 315–326. [Google Scholar] [CrossRef]
- Xiong, L.; Dong, D. Reversible data hiding in encrypted images with somewhat homomorphic encryption based on sorting block-level prediction-error expansion. J. Inf. Secur. Appl. 2019, 47, 78–85. [Google Scholar] [CrossRef]
- Wang, Y.; Cai, Z.; He, W. High capacity reversible data hiding in encrypted image based on intra-block lossless compression. IEEE Trans. Multimed. 2020, 23, 1466–1473. [Google Scholar] [CrossRef]
- Amrit, P.; Singh, K.N.; Baranwal, N. Deep learning-based segmentation for medical data hiding with Galois field. Neural Comput. Appl. 2023, 1–16. [Google Scholar] [CrossRef]
- Singh, H.K.; Singh, K.N.; Singh, A.K. Secure transmission of ocean images using deep learning-based data hiding. Expert Syst. 2023, e13469. [Google Scholar] [CrossRef]
- Tripathi, A.; Prakash, J. Blockchain enabled interpolation based reversible data hiding mechanism for protecting records. EAI Endorsed Trans. Scalable Inf. Syst. 2023, 10, e1. [Google Scholar]
- Rai, A.K.; Om, H.; Chand, S. High-capacity reversible data hiding based on two-layer embedding scheme for encrypted image using blockchain. Computers 2023, 12, 120. [Google Scholar] [CrossRef]
- Punia, R.; Malik, A.; Singh, S. An interpolation-based reversible data hiding scheme for internet of things applications. Discov. Internet Things 2023, 3, 18. [Google Scholar] [CrossRef]
- Qi, W.; Zhang, T.; Li, X.; Ma, B.; Guo, Z. Reversible data hiding based on prediction-error value ordering and multiple-embedding. Signal Process 2023, 207, 108956. [Google Scholar] [CrossRef]
- Dragoi, I.C.; Coltuc, D. Reversible data hiding in encrypted color images based on vacating room after encryption and pixel prediction. In Proceedings of the 25th IEEE International Conference on Image Processing (ICIP), Athens, Greece, 7–10 October 2018. [Google Scholar] [CrossRef]
- Chen, K.; Guan, Q.; Zhang, W.; Yu, N. Reversible data hiding in encrypted images based on binary symmetric channel model and polar code. IEEE Trans. Dependable Secur. Comput. 2023, 20, 4519–4535. [Google Scholar] [CrossRef]
- Mohammadi, A. A general framework for reversible data hiding in encrypted images by reserving room before encryption. J. Vis. Commun. Image Represent. 2022, 85, 103478. [Google Scholar] [CrossRef]
- Huang, D.; Wang, J. High-capacity reversible data hiding in encrypted image based on specific encryption process. Signal Process. Image Commun. 2019, 80, 115632. [Google Scholar] [CrossRef]
- Ke, Y.; Zhang, M.Q.; Liu, J.; Su, T.T.; Yang, X.Y. Fully homomorphic encryption encapsulated difference expansion for reversible data hiding in encrypted domain. IEEE Trans. Circuits Syst. Video Technol. 2020, 30, 2353–2365. [Google Scholar] [CrossRef]
- Hogade, N.; Pasricha, S. A survey on machine learning for geo-distributed cloud data center managements. IEEE Trans. Sustain. Comput. 2023, 8, 15–31. [Google Scholar] [CrossRef]
- Yuan, L. Enabling Decentralized, Secure and cooperative multi-access edge computing based on blockchain. IEEE Trans. Parallel Distrib. Syst. 2023, 34, 894–908. [Google Scholar] [CrossRef]
- Ghimire, B.; Rawat, D.B. Recent advances on federated learning for cybersecurity and cybersecurity for federated learning for internet of things. IEEE Internet Things J. 2022, 9, 8229–8249. [Google Scholar] [CrossRef]
- Puech, W.; Chaumont, M.; Strauss, O. A reversible data hiding method for encrypted images. In Proceedings of the SPIE Electronic Imaging 2008—Security, Forensics, Steganography, and Watermarking of Multimedia Contents X, San Jose, CA, USA, 27 January 2008; SPIE: Bellingham, WA, USA, 2008; Volume 6819. [Google Scholar] [CrossRef]
- Puteaux, P.; Puech, W. An efficient msb prediction-based method for high-capacity reversible data hiding in encrypted images. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1670–1681. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Wu, X.T.; Weng, J.; Yan, W.Q. Adopting secret sharing for reversible data hiding in encrypted images. Signal Process. 2018, 143, 269–281. [Google Scholar] [CrossRef]
- Chen, Y.C.; Hung, T.H.; Hsieh, S.H.; Shiu, C.W. A new reversible data hiding in encrypted image based on multi-secret sharing and lightweight cryptographic algorithms. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3332–3343. [Google Scholar] [CrossRef]
- Chen, B.; Lu, W.; Huang, J.; Weng, J.; Zhou, Y. Secret sharing based reversible data hiding in encrypted images with multiple data-hiders. IEEE Trans. Dependable Secur. Comput. 2022, 19, 978–991. [Google Scholar] [CrossRef]
- Ke, Y.; Zhang, M.; Zhanga, X.; Liu, J.; Yang, X. A reversible data hiding scheme in encrypted domain for secret image sharing based on Chinese remainder theorem. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 2469–2481. [Google Scholar] [CrossRef]
- Qin, C.; Jiang, C.; Mo, Q.; Yao, H.; Chang, C.C. Reversible data hiding in encrypted image via secret sharing based on GF(p) and GF(28). IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 1928–1941. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Wang, Y.; Yi, S.; Zhou, Y.; Jia, X. Reversible data diding in encrypted images using cipher-feedback secret sharing. IEEE Trans. Circuits Syst. Video Technol. 2022, 32, 4968–4982. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Wang, Y.; Yi, S. Matrix-based secret sharing for reversible data hiding in encrypted images. IEEE Trans. Dependable Secur. Comput. 2022, 20, 3669–3686. [Google Scholar] [CrossRef]
- Xiong, L.Z.; Han, X.; Yang, C.N. Reversible data hiding in shared images based on syndrome decoding and homomorphism. IEEE Trans. Cloud Comput. 2023, 11, 3085–3098. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Liu, X.Y.; Zheng, Y.F. Reversible data hiding over encrypted images via preprocessing-free matrix secret sharing. IEEE Trans. Circuits Syst. Video Technol. 2023, 34, 1799–1814. [Google Scholar] [CrossRef]
- Yu, C.; Zhang, X.; Qin, C.; Tang, Z. Reversible data hiding in encrypted images with secret sharing and hybrid coding. IEEE Trans. Circuits Syst. Video Technol. 2023, 33, 6443–6458. [Google Scholar] [CrossRef]
- Xiong, L.; Han, X.; Yang, C.N. Reversible data hiding in shared images with separate cover image reconstruction and secret extraction. IEEE Trans. Cloud Comput. 2024, 12, 186–199. [Google Scholar] [CrossRef]
- Yu, H.Y.; Zhang, J.W.; Xiang, Z.X.; Liu, B.; Feng, H.M. Lossless reversible data hiding in encrypted image for multiple data hiders based on pixel value order and secret sharing. Sensors 2023, 23, 4865. [Google Scholar] [CrossRef] [PubMed]
- Sun, Q.; Cao, H.; Li, S.; Song, H.; Liu, Y. Changing the threshold in a bivariate polynomial based secret image sharing scheme. Mathematics 2022, 10, 710. [Google Scholar] [CrossRef]
- Jaradat, A.; Barhoush, M.; Kofahi, N. Performance enhancement of the advanced encryption standard via software pipelined implementation. J. Theor. Appl. Inf. Technol. 2019, 97, 4213–4226. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).