Abstract
This study aimed to strengthen the security of autonomous vehicles by analyzing the current status of autonomous vehicle security, such as autonomous vehicle features, security threats, and compliance, and deriving security-level check items. Based on this, the relative importance could be obtained by applying it to the AHP (Analytic Hierarchy Process) model. The results of the empirical analysis showed that the order of priority was the establishment/implementation of a cybersecurity management system, encryption, and risk assessment. The significance of this study is that by deriving security-level check items related to autonomous vehicles and verifying the research model, we can reduce cyber security accidents that can cause loss of life and improve the level of autonomous vehicle security management of related companies. Additionally, by applying AHP evaluated by security experts to the autonomous vehicle field for the first time, it will contribute to the market expansion of the autonomous vehicle industry, which is concerned with security. Furthermore, major automobile companies have to manage the security levels of numerous tier companies due to the nature of the industry. Therefore, if they perform a Quick Check (QC) considering the relative importance of the autonomous vehicle security-level check items presented in this paper, they will be able to effectively identify the security levels of tier companies early.
1. Introduction
Artificial intelligence, which is revolutionizing the entire industry, is rapidly driving autonomous vehicle technology, and the size of the autonomous vehicle market is also growing rapidly. In particular, according to a Research and Markets report, the global autonomous vehicle market size is expected to grow at a CAGR of 21.9% and expand to USD 214.32 billion by 2030 [1]. With AI technology innovation and market size expansion, autonomous vehicles will quickly replace existing cars, just as smartphones instantly replaced cell phones. Autonomous vehicles use new technologies such as AI, cloud, and big data to allow drivers to work in the car like an office space or relax with infotainment. Moreover, autonomous vehicles will provide various conveniences such as increased mobility for the vulnerable, like the elderly. In addition, to ensure better safety, external connectivity between vehicles and transportation infrastructure are being expanded.
However, as autonomous vehicles become more intelligent and more connected, their convenience improves. On the other hand, the points of contact for cyberattacks are expanding. As a result, the security threats to autonomous vehicles are also increasing [2]. The following are the most well-known examples of autonomous vehicle security threats. In July 2015, at Black Hat USA 2015, Charlie Miller and Chris Valasek demonstrated a hack targeting a Jeep Cherokee vehicle about 18 km away. They were able to remotely control the vehicle’s speed and direction. This led to Fiat Chrysler Automobiles issuing a software security update recall for about 1.4 million vehicles [3]. Furthermore, at Pwn2Own 2023 in Vancouver, Canada, in 2023, a Tesla Model 3 vehicle was remotely hacked, opening its trunk and doors [4]. Also, in the case of hacking in the existing IT environment, the damage is in the cyber realm, which is far from human casualties. However, hacking attacks on autonomous vehicles can directly affect the physical environment, such as paralyzing roads and causing human casualties, so a systematic security response system is necessary [5,6,7]. When comparing the loss of life in conventional vehicles with a small digital sector and human control in the event of a cyberattack with the loss of life in autonomous vehicles that are completely computer-controlled and unmanned, the loss of life is likely to be greater in the autonomous vehicles. That is why autonomous vehicle security is very important for the future. The international standard for automotive cybersecurity, UNR No. 155, was adopted in the EU in June 2020 and has been implemented since July 2022 [8,9]. The relevant regulations require automobile manufacturers to establish and implement a vehicle cybersecurity management system and conduct security risk assessments and management for vehicles. In this way, it is also true that requirements for cybersecurity are increasing in terms of compliance. However, existing studies are fragmentary studies centered on technical security trends, and there are difficulties in responding to various autonomous vehicle security attacks that can threaten human life. Therefore, an integrated study that combines compliance with administrative, technical, and physical security checks is absolutely necessary. Since organizations have limited resources in terms of time and money, if they consider the relative importance of each item and check some of them first, they will be able to save time and money, as well as identify the security level early. In particular, the automobile we are dealing with in this paper consists of more than 20,000 parts. As a result, there are many tier companies producing parts, and major OEMs (Original Equipment Manufacturers) producing complete vehicles must simultaneously pay attention to the products and security of many tier companies [10]. Therefore, a Quick Check (QC) considering relative importance will help OEMs quickly check the security level of tier companies. In addition, this paper will solve the security concerns of those in the autonomous vehicle industry by applying AHP, evaluated by experienced security experts, for the first time to the autonomous vehicle field. This will ultimately contribute to the expansion of the autonomous vehicle market.
Therefore, this study analyzed autonomous vehicle security threats, compliance, and previous studies to derive integrated security-level check items related to autonomous vehicles. In addition, the relative importance of each check item was empirically analyzed. Based on the results of this study, if companies with limited time and resources selectively use high-ranking items, they will be able to quickly identify the security level.
The rest of this article is organized as follows. Section 2 describes autonomous vehicle security threats, compliance, and previous studies. Section 3 presents a research model and method for deriving autonomous vehicle security-level inspection items and comparing relative importance. Section 4 empirically analyzes relative importance using the AHP (Analytic Hierarchy Process) analysis technique. Finally, Section 5 presents the conclusion and future research work.
2. Related Works
This section describes the theories related to this paper, such as autonomous vehicle characteristics, security threats, compliance, and previous studies. In addition, security threats include vulnerabilities and threats that may occur in the autonomous vehicle ecosystem, and compliance covers standards and laws related to autonomous vehicles in major countries.
2.1. Autonomous Vehicles
Looking at the definitions of autonomous vehicles, the Oxford Dictionary defines it as “a vehicle that has the technology to drive itself without a person in control” [11]. The UK’s Automated Vehicles Bill also states: A vehicle “satisfies the self-driving test” if it is designed or adapted with the intention that a feature of the vehicle will allow it to travel autonomously, and it is capable of doing so, by means of that feature, safely and legally [12].
In other words, it can be said to be a car that moves safely on its own by utilizing various technologies without human intervention. The operation mechanism of an autonomous vehicle can be explained by dividing it into perception, judgment, and control. The perception is the stage of recognizing the surrounding environment such as fixed objects such as lanes, traffic lights, tunnels, and crosswalks on the road, and moving objects such as pedestrians and vehicles. It accurately and quickly collects and recognizes related data through Advanced Driver Assistance System (ADAS) sensors such as cameras, lasers, and lidars [13]. In other words, the surrounding situation is recognized with ADAS sensors corresponding to human eyes, but for safety reasons, it also tries to recognize the surrounding situation through external communication called Vehicle to Everything (V2X). V2X technology is a connection communication between a vehicle and the outside world, and it is classified into Vehicle to Vehicle (V2V), Vehicle to Infra (V2I), Vehicle to Pedestrian (V2P), and Vehicle to Nomadic Devices (V2N), and includes all forms of communication technologies that can be operated in cars on the road [14,15,16]. This technology is necessary to implement an Intelligent Transport System (ITS) that makes roads and vehicles intelligent and considers safety [17]. However, V2X communication technology is a channel through which autonomous vehicles connect to the outside world and may be vulnerable to attacks by external hackers [18,19]. Therefore, security measures for V2X communication technology are necessary to consider the safety of autonomous vehicles.
2.2. Autonomous Vehicle Security Threats
In autonomous vehicles, the Electronic Control Unit (ECU) is an electronic control module that controls and manages sensors, actuators, etc. In the case of autonomous vehicles, external contact points are becoming more diverse, but authentication is weak, so attackers use this environment to falsify ECU firmware [20]. In addition, hackers can use ECU SW defects to perform malicious attacks and cause vehicle malfunctions [21,22,23].
Threats can be identified by dividing the network into internal and external. There is the threat of a man-in-the-middle attack (MITM) that intercepts sessions on the Controller Area Network (CAN), which is an internal network of the vehicle; steals information; and falsifies data being transmitted or received. Therefore, it is possible to cause service failures such as control seizure and system malfunction through session hijacking, sniffing attack, and replay attack [24,25]. Additionally, CAN processes packets according to priority with a Broadcast Bus structure that does not have information about the transmitting device. If a hacker launches a DoS attack that generates a large number of high-priority packets in a short period of time, the ECU devices may be paralyzed [26]. Autonomous vehicles connect to external networks via wireless networks such as GPS, Dedicated Short-Range Communications (DSRCs) in V2V, and Wireless Access in Vehicular Environments (WAVEs) in V2X. At this time, sessions can be intercepted and key information stolen through man-in-the-middle attacks [27]. Therefore, transmitted and received messages can be falsified. In addition, DDoS attacks that can cause serious threats such as vehicle system overload and service failure are also possible via external networks [28], and since there is always a threat of important data leakage, it is necessary to consider encryption when storing, transmitting, and receiving data. In addition, hackers can illegally access component controllers through weak authentication and encryption-key theft and attempt various attacks, such as malicious reversing and code modification [29,30]. In other words, there is a threat of theft of confidential data such as encryption keys, passwords, and important information.
In addition, if access control and authority management are insufficient, personnel who have access to internal vehicle components for vehicle maintenance may have malicious intentions and modify ECU-related firmware, which may have a significant impact on the safe operation of the vehicle or illegally leak important data [31,32]. Security threats also exist during vehicle diagnosis and updates. The OBD (On Board Diagnostics) port is used to diagnose defects and the performance of the vehicle’s main units. The port connects to a computer via a wired or wireless connection and communicates with the CAN bus to check ECU values [33]. At this time, an attacker may manipulate the accelerator value or stop the engine by forging the CAN packet. So, in the past, there have been cases where Chevrolet Corvette OBD-II vehicles were hacked, and remote illegal control was possible. In other words, USB and OBD ports for diagnosis and updates can be illegally used [34,35,36,37]. So, an attacker who has hacked OBD can paralyze the vehicle system through illegal manipulation, data deletion, and malicious programs.
2.3. Compliance of Autonomous Vehicles
2.3.1. UNR No.155
The WP.29, under the United Nations Economic Commission for Europe (UNECE) on automotive cybersecurity, adopted UNR No.155, an international standard for automotive cybersecurity, in June 2020, and the relevant regulation came into effect in the EU in July 2022. According to UNR No.155, automobile manufacturers must have a Cyber Security Management System (CSMS) and conduct risk assessments and management for each vehicle type. In particular, manufacturers need to demonstrate that their cybersecurity management system is appropriate for identifying, assessing, classifying, and managing security threats, as well as for the vehicle security testing process and for monitoring and responding to security threats. Here, manufacturers refer to the OEMs mentioned above, and they also have to manage the risks of the parts of the vehicle, the aftermarket software, and the parts of the tier companies [38]. UNR No.155 also categorizes the list of technical security threats and measures for vehicles. Further details, particularly on data sources, are recorded in UNR No.155 Annex 5. Looking at these, vehicle-related backend server threats include the infringement of data, networks, and applications of backend servers; vehicle threats using communication channels include data theft and network attacks on internal and external vehicle communication access paths; and vehicle update procedure-related threats include misuse and damage during vehicle module updates. Threats to vehicles regarding their external connectivity and connections are threats to attack vehicle systems through external-access media such as USB and OBD port interfaces and third-party software, and threats to vehicle data and codes are classified as threats that attack data, code, and environment-setting variables used in autonomous vehicles. Potential vulnerabilities include hacking threats toward potential security vulnerabilities that may arise in an environment that unintentionally facilitates cyberattacks by normal actors, or in situations where SW and networks are not sufficiently protected during design. Meanwhile, looking at matters related to vehicle approval, the US and Korea are adopting self-certification based on UNR No. 155, and the EU is introducing type approval.
2.3.2. ISO/SAE 21434
ISO/SAE 21434 is an international standard that establishes and implements a life cycle-centered cybersecurity management process to meet the security requirements of the automotive industry [39]. The standard consists of 15 parts, and parts 5 to 15 can be considered as the main parts. Looking at the main parts, part 5 specifies the overall cybersecurity management of the organization. Part 6 defines the cybersecurity process at the project level that organizations are conducting. First, a cybersecurity officer is designated within the project, and the designated cybersecurity officer establishes a cybersecurity plan, assigns cybersecurity responsibilities to each person in charge, and builds a security team, and the team performs cybersecurity activities for unnecessary components and off-the-shelf components of the developed product. OEMs, who have overall responsibility for automobiles, assign security activity roles and evaluate capabilities to tier companies that supply automobile sectors. Part 8 is an ongoing cybersecurity activity. Cybersecurity monitoring and periodic vulnerability analysis should be performed to maintain an appropriate level of security. Parts 9 through 14 establish and manage cybersecurity activities throughout the vehicle production life cycle, from vehicle concept design to end of warranty. Part 15 is about managing risks for vehicles by utilizing TARA (Threat Analysis and Risk Assessment). In this way, ISO/SAE 21434 requires cybersecurity management for vehicles throughout the entire life cycle, including the development, production, sales, use, service, and disposal stages of the vehicle.
2.3.3. Korea Automobile Cybersecurity Guide
The Smart Transportation Cybersecurity Guide [40], published in May 2018, was further revised in December 2019 due to the growth of the autonomous vehicle market and increased security vulnerabilities. This security guide is based on international standards in the smart transportation field and categorizes the threats to and vulnerabilities of availability damage, data loss, MITM, inappropriate password use, inappropriate access control, inappropriate physical control, malicious program execution, and insufficient user management. In addition, the security response items are classified into development/management protection, physical protection, authentication, password, and data protection. Additionally, the Automobile Cybersecurity Guide announced by the domestic government agency in December 2020 requires management security such as the establishment and implementation of CSMS based on the international standard UNR No. 155. In addition, it is determined that vehicle threats using communication channels, threats to backend servers related to real-road vehicles, threats to external connections and access to vehicles, threats to vehicle data and code, and potential vulnerabilities due to lack of protection are items that must be responded to in the technical area.
2.3.4. Laws Related to Autonomous Vehicles
The laws of each country regarding autonomous vehicles are as follows:
- The United States: Looking at the compliance of autonomous vehicles in the United States, the National Highway and Transportation Safety Administration (NHTSA) and the Department of Transportation (DOT) have been publishing guidelines related to autonomous driving since 2016, presenting the direction and major standards of autonomous driving-related policies. These guidelines have been continuously updated since then, and the fourth revised version, Automated Vehicles 4.0, was published in 2020 [41]. In the case of AV 4.0, compared to previous reports, it presents policy directions such as technology regulation, traffic safety, and technology innovation, as well as 10 technology principles. Among them, the most important principles are the protection of users and communities and the promotion of harmony between the roles of each entity. In other words, it protects users through safety being first, with an emphasis on security, cybersecurity, and reliable privacy and data security. It also emphasizes the roles and harmony of various stakeholders. Also, based on NHTSA’s guidelines, the Safely Ensuring Lives Future Deployment and Research in Vehicle Evolution Act and the American Vision for Safer Transportation through Advancement of Revolutionary Technologies Act were proposed in the federal Congress in 2017, but both were scrapped. No federal legislative action has been taken yet.
- Germany: In the case of Germany, the Road Traffic Act established a legal system in 2017 for the commercialization of level 3 and level 4 autonomous vehicles but did not allow unmanned autonomous vehicles that operate without a driver on board. However, with the approval of the German Federal Senate in 2021 of the amendments to the Road Traffic Act and the Compulsory Automobile Insurance Act, Germany became the first country in the world to establish a legal system for the commercialization of unmanned autonomous vehicles [42]. The law explicitly introduced the principle of prioritizing human life into the legal norms. In addition, the law introduced the obligation of manufacturers to guarantee the information sovereignty of owners, thereby establishing basic and core matters for the use and protection of data related to autonomous vehicles.
- UK: In the UK, the Automated Vehicles Bill was enacted in November 2023, allowing autonomous vehicles to be on UK roads by 2026 [43]. The Act is divided into seven sections, including regulatory regimes, criminal liability for vehicle use, policing and investigation, etc. It also requires that autonomous vehicles achieve at least the same level of safety as a careful and competent human driver and undergo rigorous safety checks before being allowed on the road.
- Korea: In Korea, the Act on the Promotion of and Support for Commercialization of Autonomous Vehicles was implemented on 1 May 2020 to supplement the existing Automobile Management Act and commercialize autonomous vehicles. The content on autonomous vehicles and fully autonomous vehicles has been further detailed, and it stipulates deregulation and exclusion for promoting commercialization, special provisions on automobile safety standards, and special provisions on intelligent transportation system standards. It also includes the designation and management of pilot operation areas, the designation of safety sections, the use of anonymous personal information, and the training of specialized personnel.
2.4. Related Previous Studies
Looking at related previous studies, Yu et al. [44] performed systematic mapping on vehicle security measures but only targeted the network within the vehicle, not the autonomous vehicles as a whole. Kwon et al. [45] described the technological stages of autonomous vehicles and the operating principles, consisting of perception, judgment, and control, and explained the security threats that may occur in autonomous vehicles and the standardization of security technologies such as IEEE 1609.2 and ISO 14229. Li et al. [46] proposed a risk assessment process based on ISO 21434 to respond to accidental vehicle failures and cyber security threats, but they focused only on risk assessment as part of administrative security. Ju et al. [47] described that denial of service, replay, and false data injection attacks could pose threats to intra-vehicle networks, inter-vehicle networks, and sensors. Dibaei et al. [48] presented Sybil attacks, DoS, vehicular malware, and timing attacks on vehicular networks. Aliwa et al. [49] described that the defense of the CAN bus, which plays a critical role in vehicles, is essential because the CAN protocol is vulnerable to security attacks such as frame injection and denial of service. Pham et al. [50] presented that sensors, cameras, and vehicle communication mechanisms on the roadside or from other vehicles are easy targets for hacker attacks and suggest that a defense strategy is needed. Sun et al. [51] categorized vulnerabilities and cybersecurity risks into attacks within vehicles, between vehicles, and vehicle infrastructure. They focus on network sectors such as lightweight security models, V2X security, and dynamic risks. Sommer et al. [52] presented a taxonomy useful for threat analysis and risk management from the perspective of autonomous vehicle security attacks. Gupta et al. [53] analyzed the security mechanism of the autonomous vehicle ecosystem and suggested security measures for the safe operation of the ecosystem. Grimm et al. [54] classified network monitoring techniques for security and compared general IT security measures with the ones in the vehicle security field. Seo et al. [55] identified trends in autonomous vehicle technology and security vulnerabilities such as V2X remote access and flooding within the CAN bus. They defined vehicle system-attack scenarios targeting some functions and described countermeasures. They also presented security requirements such as message authentication or encryption for CAN protection. Kim [56] described cyberattacks that may occur as autonomous vehicles become commercialized and mentioned 10 security threats and security requirements of the Smart Transportation Cyber Security Guide, including development and management protection, physical protection, authentication, passwords, and data protection. The author also presented safety improvement measures, such as building an integrated control system and security education. Aravind et al. [57] described vulnerabilities in the CAN bus, such as encryption and authentication. They also identified vulnerabilities in the CAN bus and the resulting vulnerabilities in Remote Control Execution and proposed solutions to counter them. Lee et al. [58] proposed a dataset for developing a machine learning model that can detect DoS attacks in a V2V communication environment. The dataset was generated by reflecting the properties of the V2V communication environment and attack characteristics using simulation tools such as OMNeT++, SUMO, Veins, and INET. In addition, they described that the dataset could detect DoS attacks in various machine learning models.
However, most related studies are fragmentary and focused on security technology trends, and there is a lack of research and efforts to analyze the items and check the levels of autonomous vehicle security and their relative priorities.
2.5. AHP
The AHP technique, developed by Professor Thomas L. Satty in the early 1970s, is a model that simplifies the entire decision-making process and leads to a final effective decision [59]. AHP quantifies relative importance through pairwise comparisons made by evaluators. The evaluation goal is placed at the highest level, with evaluation criteria that influence this goal set below it. These criteria can be divided into multiple levels and further hierarchized into sub-evaluation criteria. If we look more closely, attributes are arranged hierarchically, and the survey result data are entered here to perform pairwise comparisons for each hierarchy. After estimating the relative importance of decision-making factors for each hierarchy from the pairwise comparison matrix, the consistency ratio is calculated to check validity. The consistency ratio verifies whether the evaluator’s response is consistent, and if it is within 10%, the evaluator’s judgment is considered to be consistent.
3. Methods
3.1. Deriving Autonomous Vehicle Security-Level Check Items
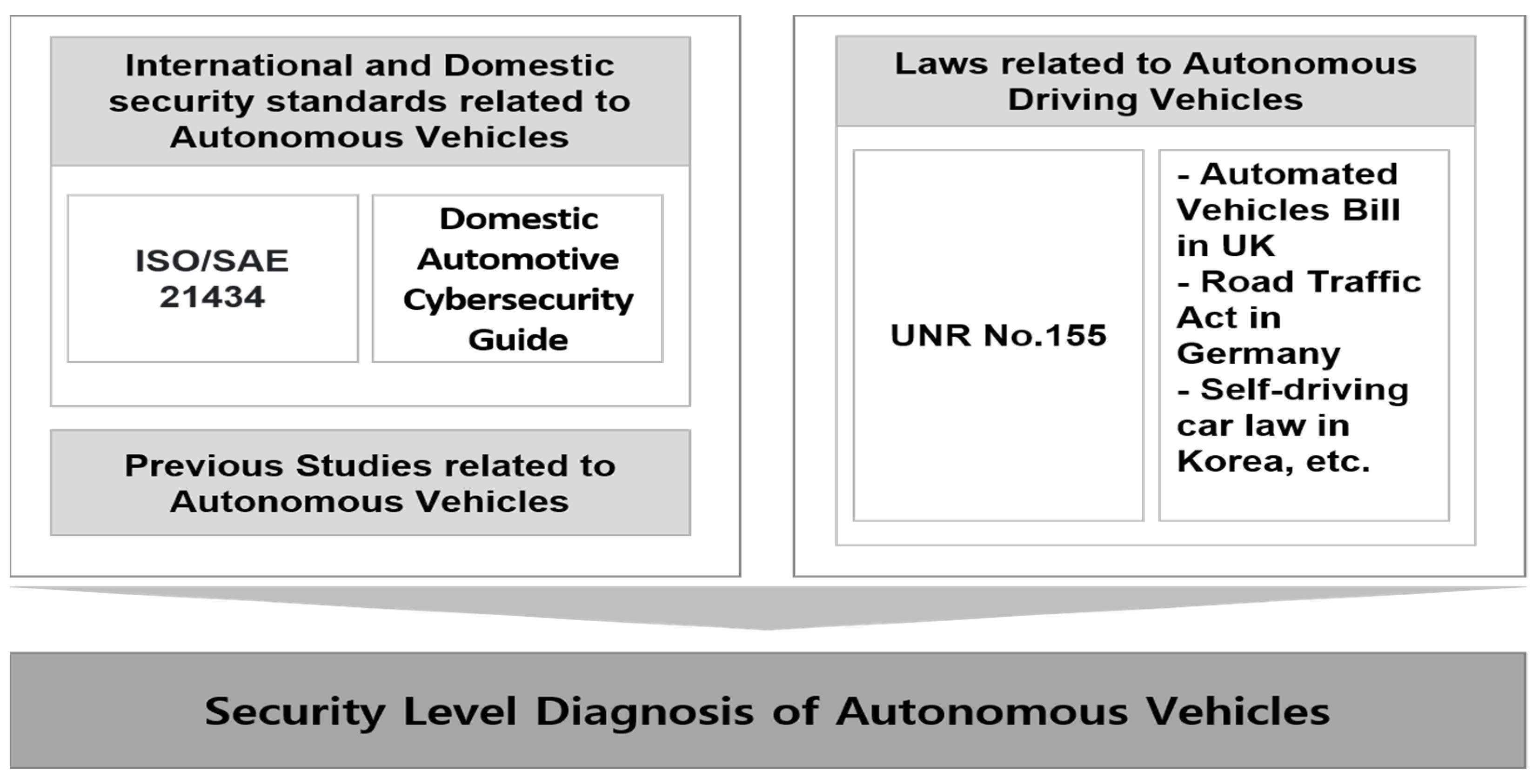
In addition to theoretical considerations from previous studies, security-check items related to autonomous vehicle security were derived from international standards such as UNR No. 155, ISO/SAE 21434, Korea’s vehicle cybersecurity guide, and overseas related laws. The contents are as shown in Figure 1.
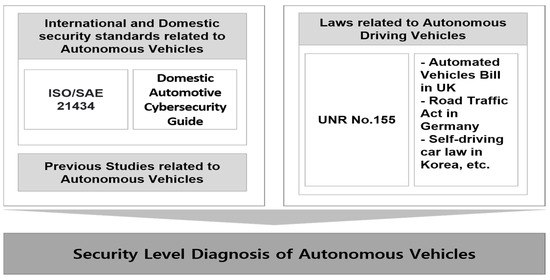
Figure 1.
Derivation of security-level checklist of autonomous vehicles.
The derived autonomous vehicle security-level check items are used as hierarchical components of the AHP model. Looking at it more closely, threats that install malware inside autonomous vehicles and flood the CAN bus, causing ECU failures, can affect driver safety. This requires vehicle-security operation management that can detect and respond to malicious software that threatens data and networks, as well as attacks that exhaust the CAN. Accordingly, in international regulation UNR No. 155, the items for checking malicious software activities in 22.1 to respond to threats to internal vehicle data and code, and the items for responding to threats to flood the CAN bus or interrupt internal network communication with high message transmission rates in 24.1, were derived as security operation management check items.
The derived items were mapped to the data protection malware response of the Smart Transportation Cybersecurity Guide and finalized as vehicle-security operation management check items in the technical sector. Table 1 shows the autonomous vehicle security-level check items derived from autonomous vehicle security threats, compliance, and previous studies.

Table 1.
Level checklists derived by this study for autonomous vehicle security.
3.2. The Proposed Model
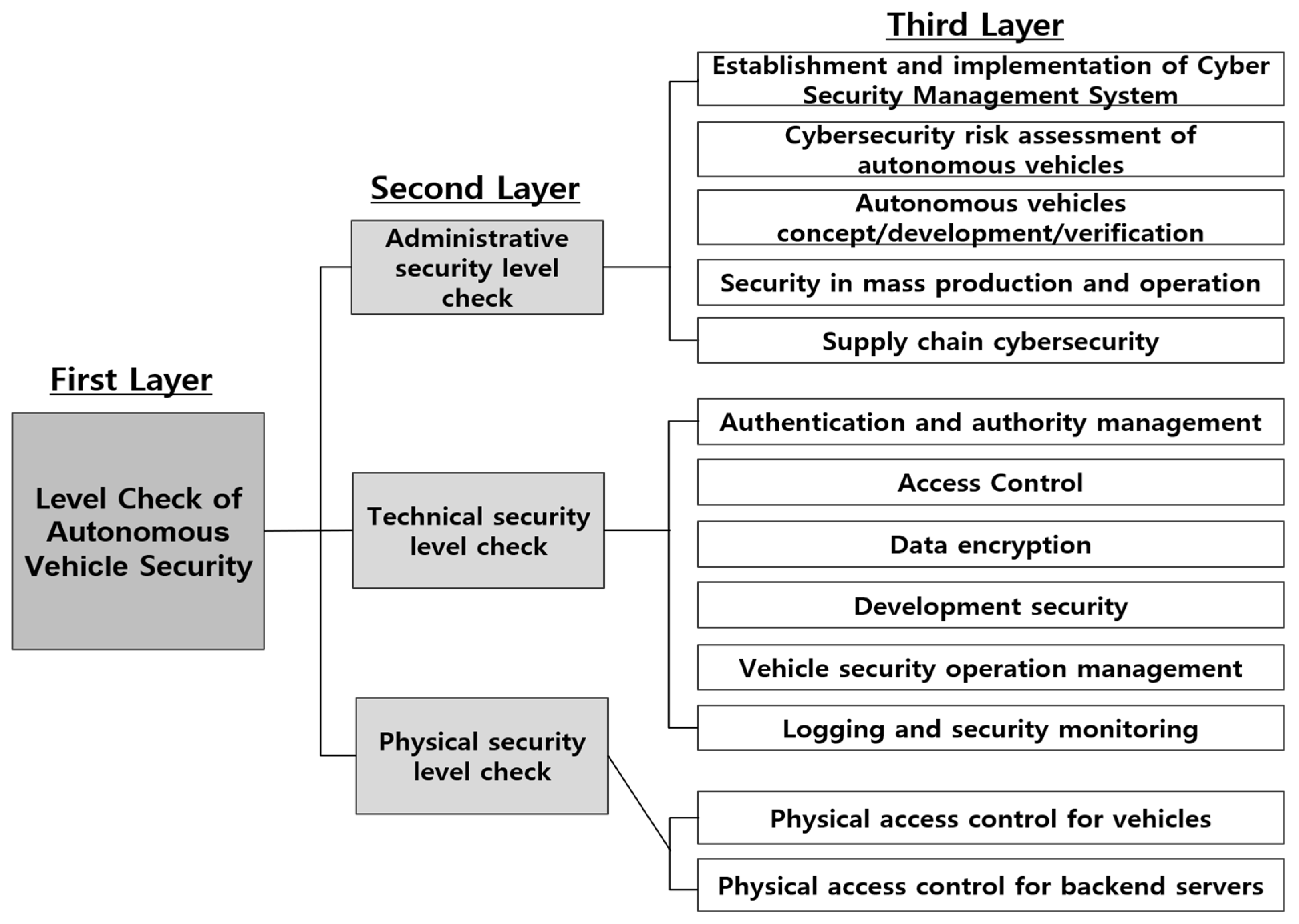
The research model for evaluating the relative importance of items based on the autonomous vehicle security-level check items is shown in Figure 2. The goal of the research model is the first layer, and the second layer is divided into three areas of autonomous vehicle security-level check items: management, technology, and physical areas. These areas are used to form the sub-criteria for evaluation. The third layer consists of 13 items. The sub-items for conducting the management security-level check are CSMS establishment and implementation, cybersecurity risk assessment, autonomous vehicle concept, development and verification, mass production and operation security, and supply chain cybersecurity. Sub-items of the technical security-level check include authentication and authorization management, access control, autonomous driving data encryption, development security, logging and security monitoring, and vehicle-security operation management. The sub-items of the physical security-level check are physical access control for vehicles and physical access control for backend servers.
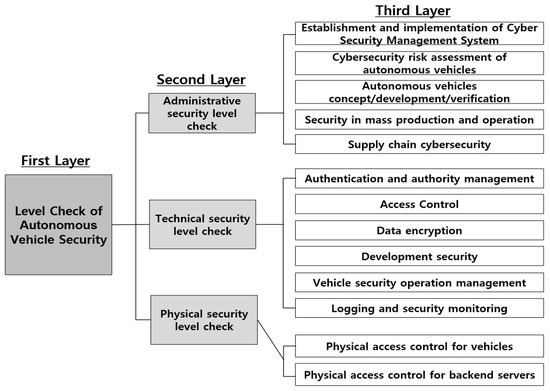
Figure 2.
Proposed hierarchy model.
3.3. Research Procedure
3.3.1. Research and Sample Characteristics
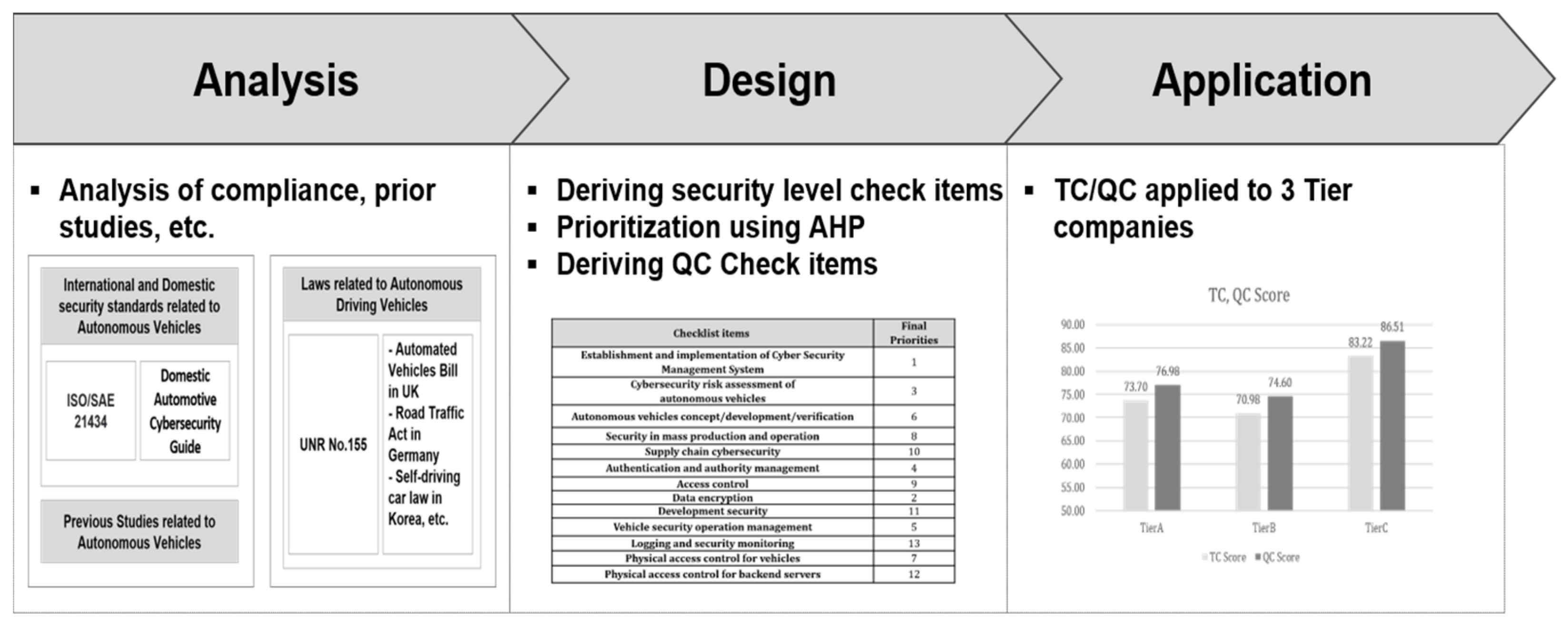
The AHP survey for this study was conducted for one month from 14 January to 14 February 2024. In order to ensure the objectivity and accuracy of the survey, the survey method was to first explain each item via phone and SNS, and then send an email to write them. The evaluation items in the questionnaire were composed of three upper-level check items in the second layer and thirteen lower-level check items in the third layer, to allow for pairwise comparisons between the same layers. The evaluation numerical scale used the nine-point scale, which is the most frequently used in the AHP questionnaire, and the weight distribution utilized the distributive mode in which the sum of all the weights of the comparison targets becomes one. In other words, it was configured to provide a score on a nine-point scale to indicate which item is relatively more important when comparing two check items. The subjects of the survey were domestic and foreign security experts with more than 5 years of security experience and certified security certifications such as CISA, CISSP, and ISMS-P. This clarified the criteria for selecting the experts in order to secure the minimum objectivity, reproducibility, and transparency of the AHP results. That is, we established safety measures by selecting experts with more than 5 years of security experience and those with overseas recognized global security certifications such as CISA and CISSP. Therefore, the relative importance was calculated for 22 security experts, and 21 valid copies were used for the analysis, excluding one copy with a consistency ratio of 0.1 or higher. The demographic characteristics of the survey sample are as follows. The respondents were 40–49 years old, accounting for the largest proportion at 57.1%, and their education level was 38.1% with a master’s degree and 14.3% with a doctorate, accounting for more than 52% of the total. In addition, the security experience was 11–19 years, accounting for the largest proportion at 52.4%, followed by 6–10 years at 23.8%, etc. Meanwhile, the research process is summarized in a schematic diagram. The contents are shown in Figure 3.
Figure 3.
Research process schematic diagram.
3.3.2. AHP Procedure
This study analyzes the relative importance step by step. In the first step, the autonomous vehicle security-level check was hierarchized. In the second step, a survey related to AHP was conducted with 22 security experts. The survey compares two items and evaluates which check item is relatively more important. In the third step, the consistency ratio was checked, and the relative importance of each security-check item hierarchy was calculated using a pairwise comparison matrix. Finally, the priority was derived by multiplying the relative importance of each hierarchy and using the importance value.
In particular, if we look at step 3 in more detail, a pairwise comparison matrix is generated to compare the relative importance of sub-factors. When the horizontal axis is m criteria and the vertical axis is n criteria, the element format of the pairwise comparison matrix is as shown in Equation (1).
The expression implies reciprocal property as an AHP axiom. Therefore, in the H matrix below, the element at the position is expressed as . At this time, the relative importance between the mutually compared items is indicated. If m is more important than n, it is 9 to 1 on the left. If m has the same relative importance as n, it is 0, and if m is not more important than n, an appropriate score is given in the 9 to 1 section on the right. In AHP, −5 to 5, −7 to 7, or −9 to 9 are usually used to enable quantitative numerical comparisons with certain rules related to the priority weight-calculation interval scale, but in this paper, the interval scale is set to 9 rather than 5 or 7 for the detailed importance-priority calculation. Therefore, the pairwise comparison matrix that is constructed can be expressed as follows.
To obtain the weight vector, the pairwise comparison matrix product is calculated.
It is defined as a B matrix. First, the sums of each row are as follows.
The sum of the entire matrix is expressed as follows.
Therefore, the weight vector value of the j-th row is as shown in Equation (2).
The weight vector of each row is calculated through the product value of the pairwise comparison matrix and Equation (2). Therefore, when calculating the weight vector values for each row of the administrative security-level check, they can be determined as 0.5530, 0.2040, 0.1000, etc. Based on the weight vector values, the priority of importance for the detailed areas can be judged to be high in the order of “Establishment and implementation of Cyber Security Management System”, “Cybersecurity risk assessment of autonomous vehicles”, and so on.
4. Empirical Results
The results of the relative importance analysis of autonomous vehicle security-level check areas and detailed sub-check items using AHP are shown in Table 2.

Table 2.
Relative importance analysis results for security-level check items.
Through this, we can check the weighted results of the security-check items of the second layer, named the upper area, and the third layer, named the lower area. In addition, we can identify the relative priority of the overall weight of each sub-check item by synthesizing the upper area and the lower area. Looking at the detailed results of the empirical study, the results of the pairwise comparison between the upper areas showed that the importance results of the administrative, technical, and physical checks were 47.7%, 45.2%, and 7.1%, respectively. Therefore, it was confirmed that the administrative security-level check was the most important in the pairwise comparison between the upper areas. Therefore, in the pairwise comparison between the upper areas, it was confirmed that the administrative security-level check was the most important. This result is because the overall cybersecurity management system, including the security organization structure that can implement the strengthening of autonomous vehicle security, CSMS implementation, management system supervision, etc., and the security risk management that performs asset identification, risk assessment, and protection-measure establishment, should be structured as the baseline in the organization. In addition, the technical security-check area cannot be effective in the cybersecurity management system with a weak foundation.
In the lower area, the results of the administrative security-level check showed that the establishment and implementation of a cybersecurity management system had the highest weight at 55.3%, followed by risk assessment at 20.4%, autonomous vehicle concept/development/verification at 10%, and security in mass production and operation at 8.9%. In particular, the reason why the establishment and implementation of a cybersecurity management system had the highest weight is because it establishes a security management system structure such as CSMS implementation and management system supervision throughout the autonomous vehicle’s life cycle. As a result of the priority analysis of detailed areas in terms of technical security-level checks, encryption showed the highest figure at 51.5%, followed by authentication and authority management at 17%, vehicle-security operation management at 13.2%, access control at 9.3%, and development security at 5.4%. In particular, the reason why encryption is considered relatively important is that it can respond to illegal theft and authentication bypass by encrypting transmitted and received packets, and it also makes it impossible for unauthorized persons to identify information by encrypting important data. In addition, encryption keys, passwords, etc., are used to block illegal access to vehicle controllers. Therefore, secure encryption-key management is important because hackers can target related keys. As a result of the priority analysis of the detailed areas in terms of the physical security-level check, physical access control for autonomous vehicles was 66.7%, followed by physical access control for backend servers at 33.3%. In other words, the reason why the physical access control sector for vehicles was relatively important is because physical access control for the vehicle itself, which moves with the driver, was judged to be more important than the backend server infrastructure that assists in driving the vehicle.
Lastly, when looking at the final priorities through the relative weights of the upper and lower areas, the establishment and implementation of a cybersecurity management system in the administrative security-level check sector was ranked first with 26.3%, encryption in the technical security-level check sector was ranked second with 23.2%, and risk assessment in the administrative security-level check sector was ranked third with 9.7%.
Table 3 shows the superiority of this study through comparison with previous studies.

Table 3.
Comparison with previous studies and the proposed model.
Previous studies have focused on technical security trends and have been fragmentary, making it difficult to comprehensively examine the level of autonomous vehicle security. In this study, we comprehensively analyzed compliance with UNR no. 155, ISO/SAE 21434, etc., and combined them into administrative security/technical security/physical security items. Through this, we can effectively respond to autonomous vehicle security threats, and especially, by utilizing relative priorities, we can identify the level of autonomous vehicle security of an organization early. In other words, there are many cases where there is a lack of time and resources for checking the security level of autonomous vehicles. Therefore, if the items with the highest relative importance derived by applying AHP are checked first, the security level can be identified more quickly compared to checking all items, and the check time and cost can be reduced.
In the area of autonomous vehicle security, there are difficulties due to the many tier companies to be inspected and the limited resources, such as time and manpower, for inspection. Therefore, we applied the top major items of relative importance priority, which are the results of this study, by utilizing them more. In other words, due to the characteristics of the automobile industry, which has more than 20,000 parts, there are countless tier companies to be inspected, and inspections absolutely require a lot of time and money. In addition, many tier companies must be inspected every year for automobile security, but due to the limitations of inspection personnel, usually only about half of them are inspected on-site. Therefore, we proposed and demonstrated QCs that can be used to inspect effectively. QC utilizes the relative importance priority of AHP for the overall inspection—that is, it inspects the first and second items in each administrative/technical/physical security sector. Through this, even if the Total Check (TC) is not performed, the security management level status of tier companies can be quickly identified, and the invested resources can be reduced. Therefore, if TC and QC are used effectively, efficiency and security can be secured.
Looking at the QC calculation formula, the QC sum abbreviated by applying AHP among the autonomous vehicle security-check items was calculated by multiplying the obtained score of each QC item by the value of the importance weight considering the selection of security experts, relevance of hacking cases, etc., and then adding them. The weight values were three, two, and one. Then, the score was divided by the total QC score to finally obtain the percentage score of QC (PQC), as shown in Equation (3).
In the case of the TC calculation formula, the TC sum was calculated by multiplying the score of each TC item by the importance weighting factor that considered the selection of security experts, relevance of hacking cases, etc., and then adding them. Then, the score was divided by the total TC score to calculate the percentage score of TC (PTC), as shown in Equation (4).
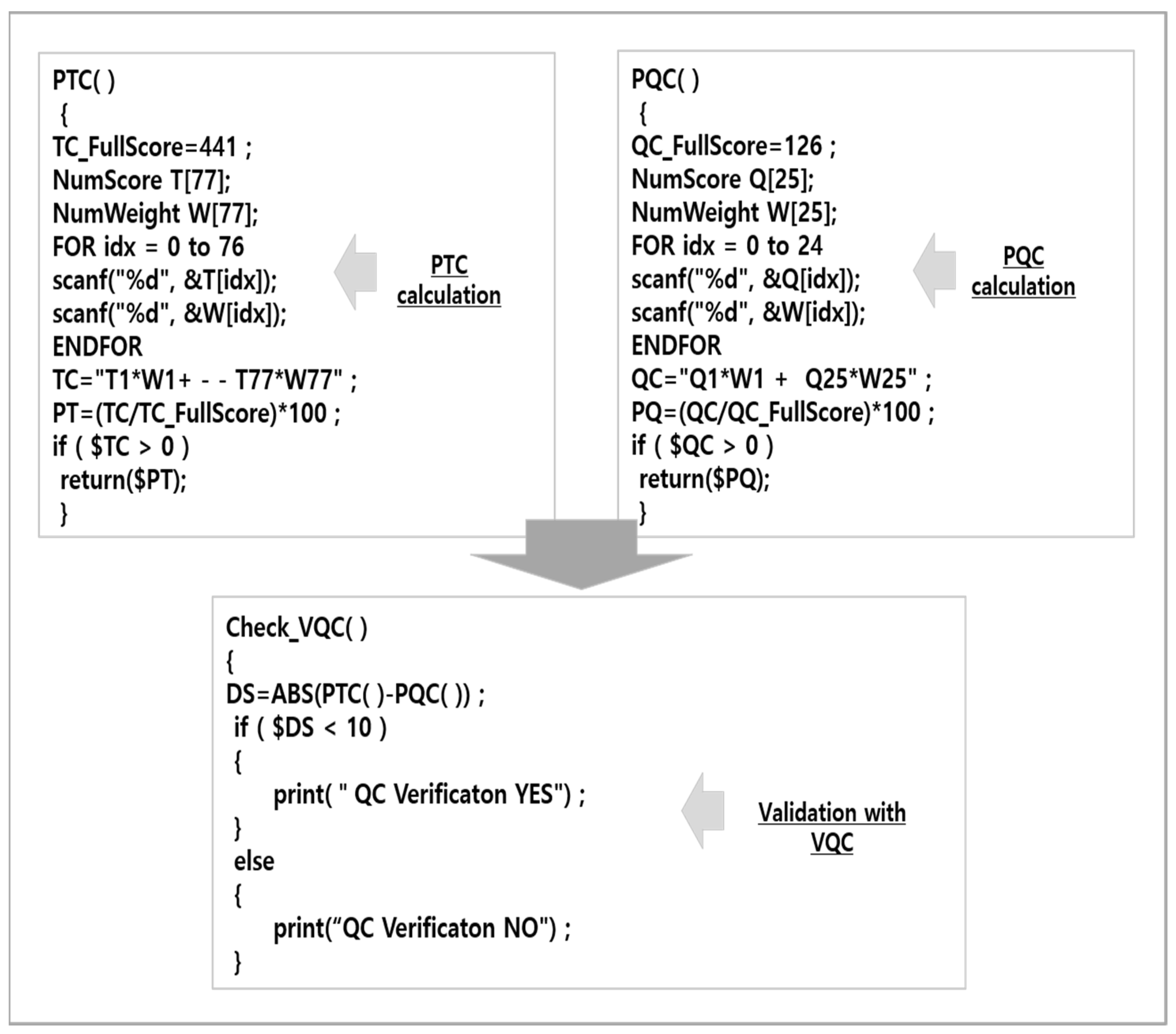
In order to verify the validity of QC, the PQC value of QC and the PTC values of TC were derived, and the validity was verified by comparing the difference between the two values. If we look into it in more detail, the pseudocode expression that checks |PTC − PQC| < 10, which is set as the validity value, is as follows in Figure 4. The function that calculates the PQC value, which is the final obtained score of QC, is defined as PQC( ), and the function that calculates the PTC value, which is the final obtained score of TC, is defined as PTC( ) to calculate the values. After that, the validity is verified by checking the difference between the two values through the Check_VQC( ) function. The number of evaluation data to be collected, which are the check items of TC and QC, are 77 and 25, respectively.
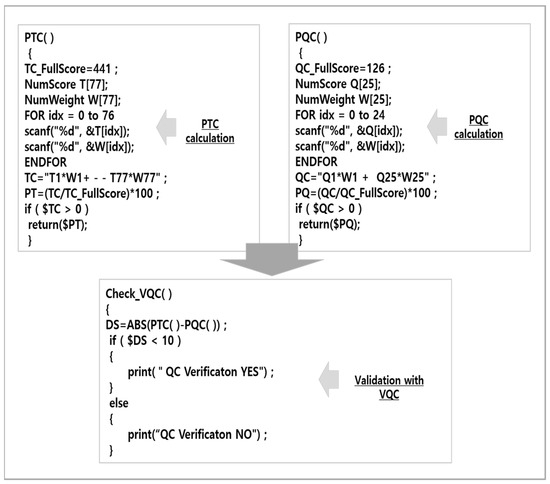
Figure 4.
QC validation expressions.
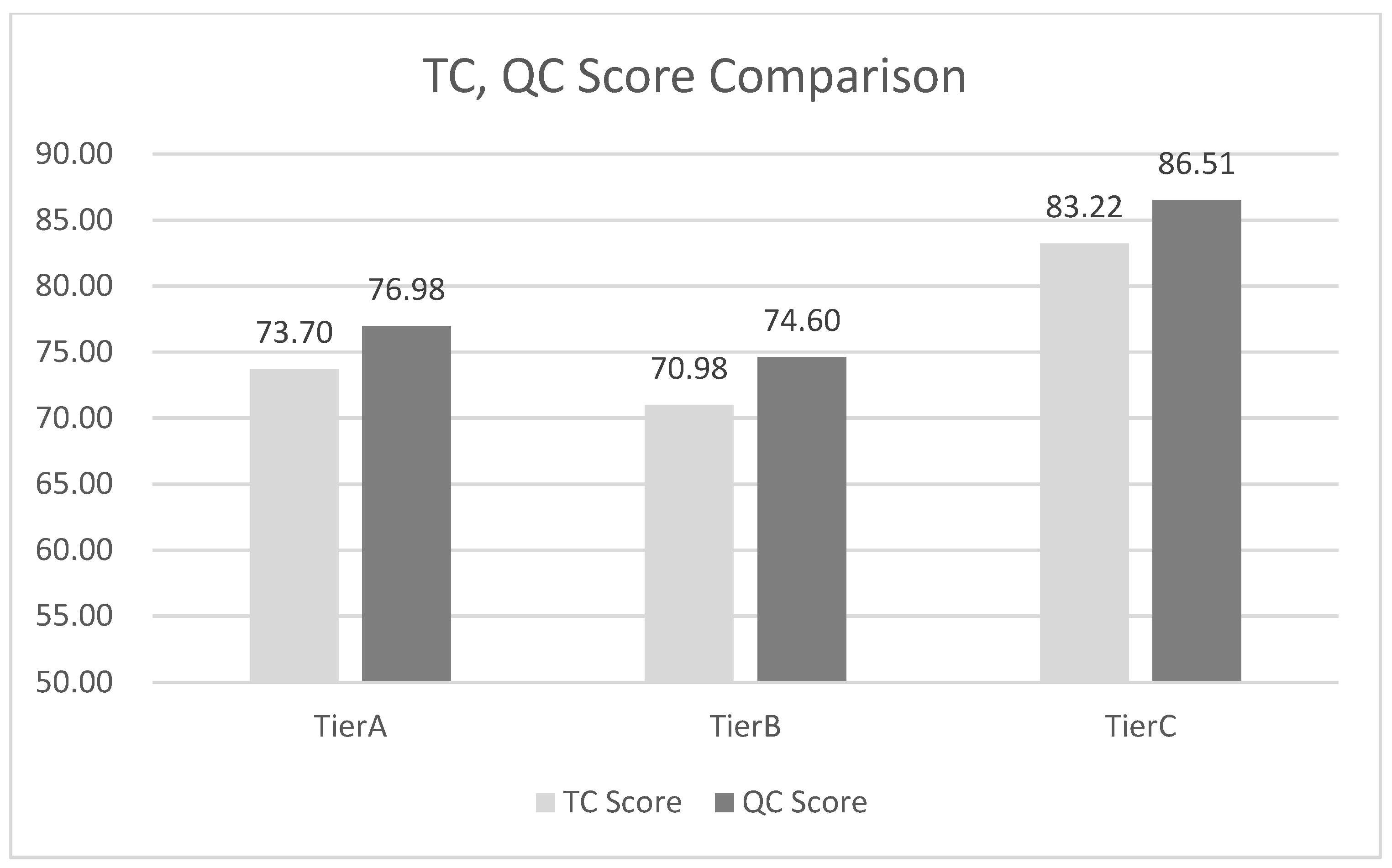
Looking at the tier companies that performed TC and QC, in the case of tier company A, the final QC score is 76.98 points when calculated with Equation (1), and the final TC score is 73.70 points when calculated with Equation (4). As |PTC-PQC| < 10 was set as the validity value above, the score difference between these two inspections is 3.6 points, so QC can be said to be valid. For tier companies B and C, the values were calculated using the above formulas and the validity values were checked, and they were within the threshold values. These values are shown in Figure 4.
That is, the results obtained using functions such as PQC( ) and PTC( ) are as shown in Figure 5, and the validity of QC was verified as the score difference between the checks was smaller than the set threshold of 10.
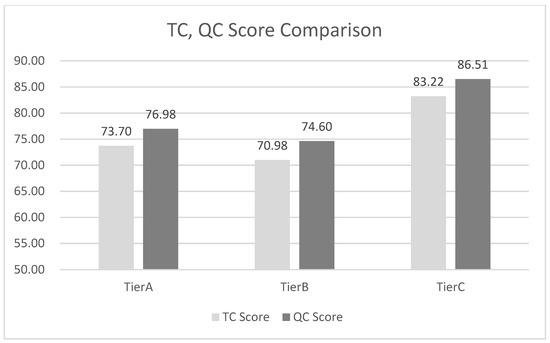
Figure 5.
TC and QC score comparison.
Therefore, if there are many tier companies and there is a lack of time and resources to conduct the security-level check of autonomous vehicles, the security level can be identified more quickly if QC, which is the top priority items in the relative importance derived from this study, is performed first. In addition, the security-level check time and costs of autonomous vehicles can be reduced.
5. Conclusions and Future Work
The global market for autonomous vehicles is expanding, and the external connection points of autonomous vehicles are becoming more diverse in order to secure safety and convenience. Consequently, the security threats to autonomous vehicles are bound to increase. Therefore, in order to protect driver safety by strengthening autonomous vehicle security, this study derived security-level check items through an analysis of the current status of autonomous vehicle security, such as autonomous vehicle characteristics, security threats, and compliance. Based on this, we were able to confirm the relative importance by applying the AHP. To summarize the empirical results, it was confirmed that the autonomous vehicle management security-level check was the most important among the upper areas in the importance evaluation of the check items. These results indicate that the administrative security-level check items, such as the establishment and implementation of the overall cybersecurity management system, including CSMS implementation, security organization structure, management system supervision, and risk assessment management, should be systematically established as a baseline. This is because technical security-level checks and physical security-level checks can be stably layered on top of them. In addition, encryption was ranked high in the lower area because the transmitted and received packets are encrypted, which can prevent authentication bypass, illegal access, and illegal theft. Additionally, the secure encryption management of encryption keys and important data makes it impossible to identify data information even if an unauthorized person steals the data. This is because encryption can be used to respond even if authentication and authority management and access control are weak.
This study derived administrative/technical/physical security-level check items based on compliance analysis and verified the proposed model in a situation where there is almost no existing research on autonomous vehicle security-level checks. Therefore, this paper enables an integrated response to hacking attacks on autonomous vehicles that could potentially cause human casualties. If global autonomous vehicle OEMs selectively conduct QCs based on the top-ranking items of relative importance from this study’s results, especially when identifying security levels quickly or when time and resources are limited, they will be able to identify security levels earlier compared to conducting a full TC and increase time and cost efficiency.
In order to increase the reliability of this study, it was conducted by security experts, but there are some limitations in generalizing the relative importance ranking. Therefore, in the future, we plan to expand the research target regionally and participate in research by involving various expert groups in the industrial sector. Through this, we will compare whether the relative importance rankings are different and also calculate the input resources, such as check time and cost. Additional security-check item exploration procedures are necessary as security threats, such as the latest security attacks and real-time threats, occur frequently. Therefore, in future work, we also plan to add a procedure that regularly reflects the latest vulnerability sites, such as CVE and CWE. This will help companies keep their security up to date by exploring check items that reflect the latest security attacks and threats.
Author Contributions
Conceptualization, D.-S.L. and S.-J.L.; formal analysis, D.-S.L.; methodology, D.-S.L.; investigation, D.-S.L.; supervision, S.-J.L.; visualization, D.-S.L.; writing—original draft, D.-S.L.; writing—review and editing, S.-J.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was partly supported by Innovative Human Resource Development for Local Intellectualization program through the Institute of Information & Communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (IITP-2024-RS-2022-00156287, 50%) and Regional strategic Industry convergence security core talent training business program through the IITP grant funded by MSIT (IITP-RS-2022-II221203, 50%).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AHP | Analytic Hierarchy Process |
| QC | Quick Check |
| TC | Total Check |
| OEM | Original Equipment Manufacturer |
| ECU | Electronic Control Unit |
| CAN | Controller Area Network |
| OBD | On Board Diagnostics |
| CSMS | Cyber Security Management System |
References
- Autonomous Vehicle Market. Available online: https://finance.yahoo.com/news/autonomous-vehicle-market-projected-reach-005800485.html?guccounter=1 (accessed on 10 January 2024).
- Upstream. Upstream Security Global Automotive Cybersecurity Report 2024; Upstream Security Ltd.: Herzliya, Israel, 2024. [Google Scholar]
- Miller, C.; Valasek, C. Remote exploitation of an unaltered passenger vehicle. In Proceedings of the Black Hat USA 2015, Las Vegas, NV, USA, 1–6 August 2015; p. 91. [Google Scholar]
- Hackers breach Tesla Model 3’s Infotainment System in Minutes in Competition. Available online: https://ca.news.yahoo.com/hackers-breach-tesla-model-3s-131300278.html (accessed on 10 January 2024).
- Carreras Guzman, N.H.; Wied, M.; Kozine, I.; Lundteigen, M.A. Conceptualizing the key features of cyber-physical systems in a multi-layered representation for safety and security analysis. Syst. Eng. 2020, 23, 189–210. [Google Scholar] [CrossRef]
- Pan, L.; Zheng, X.; Chen, H.; Luan, T.; Bootwala, H.; Batten, L. Cyber security attacks to modern vehicular systems. J. Inf. Secur. Appl. 2017, 36, 90–100. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150. [Google Scholar] [CrossRef]
- UN Regulations on Cybersecurity. Available online: https://unece.org/sustainable-development/press/un-regulations-cybersecurity-and-software-updates-pave-way-mass-roll (accessed on 10 January 2024).
- Three Landmark UN Vehicle Regulations Enter into Force. Available online: https://unece.org/sustainable-development/press/three-landmark-un-vehicle-regulations-enter-force (accessed on 10 January 2024).
- Increased Automotive Data Use Raises Privacy, Security Concerns. Available online: https://semiengineering.com/increased-automotive-data-use-raises-privacy-security-concerns/ (accessed on 10 January 2024).
- Self-Driving. Available online: https://www.oxfordlearnersdictionaries.com/definition/english/self-driving?q=self-driving (accessed on 10 January 2024).
- Automated Vehicles Act 2024. Available online: https://www.legislation.gov.uk/ukpga/2024/10/enacted (accessed on 22 May 2024).
- Seo, E.; Kim, H.K. Security of self-driving car from the point of view of in-vehicle system. Trans. Korean Soc. Automot. Eng. 2018, 26, 240–253. [Google Scholar] [CrossRef]
- Liu, L.; Chen, C.; Pei, Q.; Maharjan, S.; Zhang, Y. Vehicular Edge Computing and Networking: A Survey. Mob. Netw. Appl. 2021, 26, 1145–1168. [Google Scholar] [CrossRef]
- Maple, C.; Bradbury, M.; Le, A.; Ghirardello, K. A Connected and Autonomous Vehicle Reference Architecture for Attack Surface Analysis. Appl. Sci. 2019, 9, 5101. [Google Scholar] [CrossRef]
- Rask, E.; Auld, J.; Bush, B. SMART Mobility Connected and Automated Vehicles Capstone Report; U.S. Department of Energy Office of Scientific and Technical Information: Oak Ridge, TN, USA, 2020. [CrossRef]
- Jang, S. SW technology trends related to autonomous vehicles. Inf. Commun. Mag. 2016, 33, 29–30. [Google Scholar]
- Li, Y.; Luo, Q.; Liu, J.; Guo, H.; Kato, N. TSP Security in Intelligent and Connected Vehicles: Challenges and Solutions. IEEE Wirel. Commun. 2019, 26, 125–131. [Google Scholar] [CrossRef]
- Petit, J.; Stottelaar, B.; Feiri, M.; Kargl, F. Remote attacks on automated vehicles sensors: Experiments on camera and lidar. Black Hat Eur. 2015, 11, 995. [Google Scholar]
- Kwon, H.; Lee, S.; Choi, J.; Nah, J. Security Trends for Autonomous Driving Vehicle. Electron. Telecommun. Trends 2018, 33, 82–83. [Google Scholar]
- Lee, H.; Choi, K.; Chung, K.; Kim, J.; Yim, K. Fuzzing CAN Packets into Automobiles. In Proceedings of the IEEE 29th International Conference on Advanced Information Networking and Applications, Gwangju, Korea, 24–27 March 2015; pp. 817–821. [Google Scholar] [CrossRef]
- Milburn, A.; Timmers, N.; Wiersma, N.; Pareja, R.; Cordoba, S. There will be glitches: Extracting and analyzing automotive firmware efficiently. In Proceedings of the Black Hat USA, Las Vegas, NV, USA, 8–9 August 2018. [Google Scholar]
- Dürrwang, J.; Braun, J.; Rumez, M.; Kriesten, R.; Pretschner, A. Enhancement of Automotive Penetration Testing with Threat Analyses Results. SAE Int. J. Transp. Cybersecur. Priv. 2018, 1, 91–112. [Google Scholar] [CrossRef]
- Zachos, M.; Subke, P. Test Method for the SAE J3138 Automotive Cyber Security Standard. In Proceedings of the WCX SAE World Congress, Detroit, MI, USA, 21–23 April 2020. [Google Scholar] [CrossRef]
- Abbott-McCune, S.; Shay, L.A. Techniques in hacking and simulating a modem automotive controller area network. In Proceedings of the IEEE International Carnahan Conference on Security Technology (ICCST), Orlando, FL, USA, 24–27 October 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Lee, D.H. A Practical Wireless Attack on the Connected Car and Security Protocol for In-Vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- He, K.; Qin, K.; Wang, C.; Fang, X. Research on Cyber Security Test Method for GNSS of Intelligent Connected Vehicle. In Proceedings of the International Conference on Computer Information and Big Data Applications (CIBDA), Guiyang, China, 17–19 April 2020; pp. 200–203. [Google Scholar] [CrossRef]
- Ebert, C.; Ray, R. Penetration Testing for Automotive Cybersecurity. ATZelectronics Worldw. 2021, 16, 16–22. [Google Scholar] [CrossRef]
- Cheah, M.; Shaikh, S.A.; Haas, O.; Ruddle, A. Towards a systematic security evaluation of the automotive Bluetooth interface. Veh. Commun. 2017, 9, 8–18. [Google Scholar] [CrossRef]
- Mazloom, S.; Rezaeirad, M.; Hunter, A.; McCoy, D. A Security Analysis of an In-Vehicle Infotainment and App Platform. In Proceedings of the 10th USENIX Workshop on Offensive Technologies (WOOT 16), Austin, TX, USA, 8–9 August 2016. [Google Scholar]
- Nie, S.; Liu, L.; Du, Y. Free-fall: Hacking tesla from wireless to can bus. In Proceedings of the Black Hat USA, Las Vegas, NV, USA, 22–25 July 2017; pp. 1–16. [Google Scholar]
- Fowler, D.S.; Bryans, J.; Cheah, M.; Wooderson, P.; Shaikh, S.A. A Method for Constructing Automotive Cybersecurity Tests, a CAN Fuzz Testing Example. In Proceedings of the IEEE 19th International Conference on Software Quality, Reliability and Security Companion (QRS-C), Sofia, Bulgaria, 22–26 July 2019; pp. 1–8. [Google Scholar] [CrossRef]
- Kim, Y.; Lee, Y. A Study on the Vulnerability and Security Considerations of Autonomous Vehicles. Proc. Summer Conf. Korea Soc. Comput. Inf. 2017, 25, 165–166. [Google Scholar]
- Kexun, H.; Changyuan, W.; Yanyan, H.; Xiyu, F. Research on cyber security Technology and Test Method of OTA for Intelligent Connected Vehicle. In Proceedings of the International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Fuzhou, China, 12–14 June 2020; pp. 194–198. [Google Scholar] [CrossRef]
- Wen, H.; Chen, Q.A.; Lin, Z. Plug-N-Pwned: Comprehensive Vulnerability Analysis of OBD-II Dongles as A New Over-the-Air Attack Surface in Automotive IoT. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 949–965. [Google Scholar]
- Patki, P.; Gotkhindikar, A.; Mane, S. Intelligent Fuzz Testing Framework for Finding Hidden Vulnerabilities in Automotive Environment. In Proceedings of the Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Bayer, S.; Enderle, T.; Oka, D.K.; Wolf, M. Security crash test—Practical security evaluations of automotive onboard IT components. In Proceedings of the 6th Automotive “Safety and Security 2014”, Stuttgart, Germany, 20–22 August 2014; pp. 125–140. [Google Scholar]
- WP.29 R155; UN Regulation No. 155-Cyber Security and Cyber Security Management System. The United Nations Economic Commission for Europe (UNECE): Geneva, Switzerland, 2021.
- ISO/SAE 21434:2021; Road Vehicles—Cybersecurity Engineering. ISO/TC 22/SC 32 Electrical and Electronic Components and General System Aspects. ISO: Geneva, Switzerland, 2021.
- Smart Transportation Cybersecurity Guide. Available online: https://www.kisa.or.kr/2060205/form?postSeq=5&lang_type=KO&page=2 (accessed on 10 January 2024).
- Automated Vehicles 4.0. Available online: https://www.transportation.gov/policy-initiatives/automated-vehicles/av-40 (accessed on 10 January 2024).
- Kriebitz, A.; Max, R.; Lütge, C. The German Act on Autonomous Driving: Why Ethics Still Matters. Philos. Technol. 2022, 35, 29. [Google Scholar] [CrossRef]
- Self-Driving Vehicles Set to Be on Roads by 2026. Available online: https://www.gov.uk/government/news/self-driving-vehicles-set-to-be-on-roads-by-2026-as-automated-vehicles-act-becomes-law (accessed on 22 May 2024).
- Yu, J.; Wagner, S.; Wang, B.; Luo, F. A Systematic Mapping Study on Security Countermeasures of In-Vehicle Communication Systems. SAE Int. J. Transp. Cybersecur. Priv. 2021, 4, 97–116. [Google Scholar] [CrossRef]
- Kwon, S.; Lee, J. Autonomous Vehicle Security Threats and Technology Trends. Rev. KIISC 2020, 30, 31–39. [Google Scholar]
- Li, Y.; Liu, W.; Liu, Q.; Zheng, X.; Sun, K.; Huang, C. Complying with ISO 26262 and ISO/SAE 21434: A Safety and Security Co-Analysis Method for Intelligent Connected Vehicle. Sensors 2024, 24, 1848. [Google Scholar] [CrossRef] [PubMed]
- Ju, Z.; Zhang, H.; Li, X.; Chen, X.; Han, J.; Yang, M. A Survey on Attack Detection and Resilience for Connected and Automated Vehicles: From Vehicle Dynamics and Control Perspective. IEEE Trans. Intell. Veh. 2022, 7, 815–837. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Jiang, K.; Abbas, R.; Liu, S.; Zhang, Y.; Xiang, Y.; Yu, S. Attacks and defences on intelligent connected vehicles: A survey. Digit. Commun. Netw. 2020, 6, 399–421. [Google Scholar] [CrossRef]
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and countermeasures for in-vehicle networks. ACM Comput. Surv. (CSUR) 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Pham, M.T.T.; Xiong, K. A Survey on Security Attacks and Defense Techniques for Connected and Autonomous Vehicles. Comput. Secur. 2020, 109, 102269. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A Survey on Cyber-Security of Connected and Autonomous Vehicles (CAVs). IEEE Trans. Intell. Transp. Syst. 2021, 23, 6240–6259. [Google Scholar] [CrossRef]
- Sommer, F.; Dürrwang, J.; Kriesten, R. Survey and Classification of Automotive Security Attacks. Information 2019, 10, 148. [Google Scholar] [CrossRef]
- Gupta, S.; Maple, C.; Passerone, R. An Investigation of Cyber-Attacks and Security Mechanisms for Connected and Autonomous Vehicles. IEEE Access 2023, 11, 90641–90669. [Google Scholar] [CrossRef]
- Grimm, D.; Pistorius, F.; Sax, E. Network Security Monitoring in Automotive Domain. In Advances in Information and Communication; Arai, K., Kapoor, S., Bhatia, R., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 782–799. [Google Scholar] [CrossRef]
- Seo, H.; Lee, S.; Kwon, H.; Kwon, Y. Autonomous Vehicle Security Trends. J. Korea Inst. Inf. Secur. Cryptol. 2018, 28, 10–11. [Google Scholar]
- Kim, Y. A Proposal for Improvement of Safety by Commercialization of Autonomous Vehicles. Master’s Thesis, Sungkyunkwan University, Seoul, Republic of Korea, 2020. [Google Scholar]
- Aravind, G.; Nambiar, S.; Krishnan, M.B.M. Autonomous Vehicle Security Enhancement. In Proceedings of the 2023 International Conference on Networking and Communications (ICNWC), Chennai, India, 5–6 April 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Lee, H.; Lee, M.; Ha, J. Data Generation and Verification for Development of DoS Attack Detection Model in V2V Communication Environment. J. Korea Acad. -Ind. Coop. Soc. 2024, 25, 1–11. [Google Scholar] [CrossRef]
- Satty, T. Axiomatic foundation of the Analytic Hierarchy Process. Manag. Sci. 1986, 32, 841–850. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).