Robust H∞ Control for Autonomous Underwater Vehicle’s Time-Varying Delay Systems under Unknown Random Parameter Uncertainties and Cyber-Attacks
Abstract
:1. Introduction
2. Problem Formulation and Preliminaries
2.1. AUV System I with Time-Varying Delay
2.2. AUV System II with Time-Varying Delays
2.3. AUV Auxiliary State Dynamics System
- (1)
- The closed-loop system from with is asymptotically stable for admissible uncertainties satisfying .
- (2)
- Under the zero initial condition, one satisfies:where is a given constant.
- (1)
- ;
- (2)
- , .
3. Main Results
3.1. Stability of AUV System with Time-Varying Delays
3.2. Stability of Auxiliary State Dynamics System
4. Computer Simulation Examples
- Case 1.
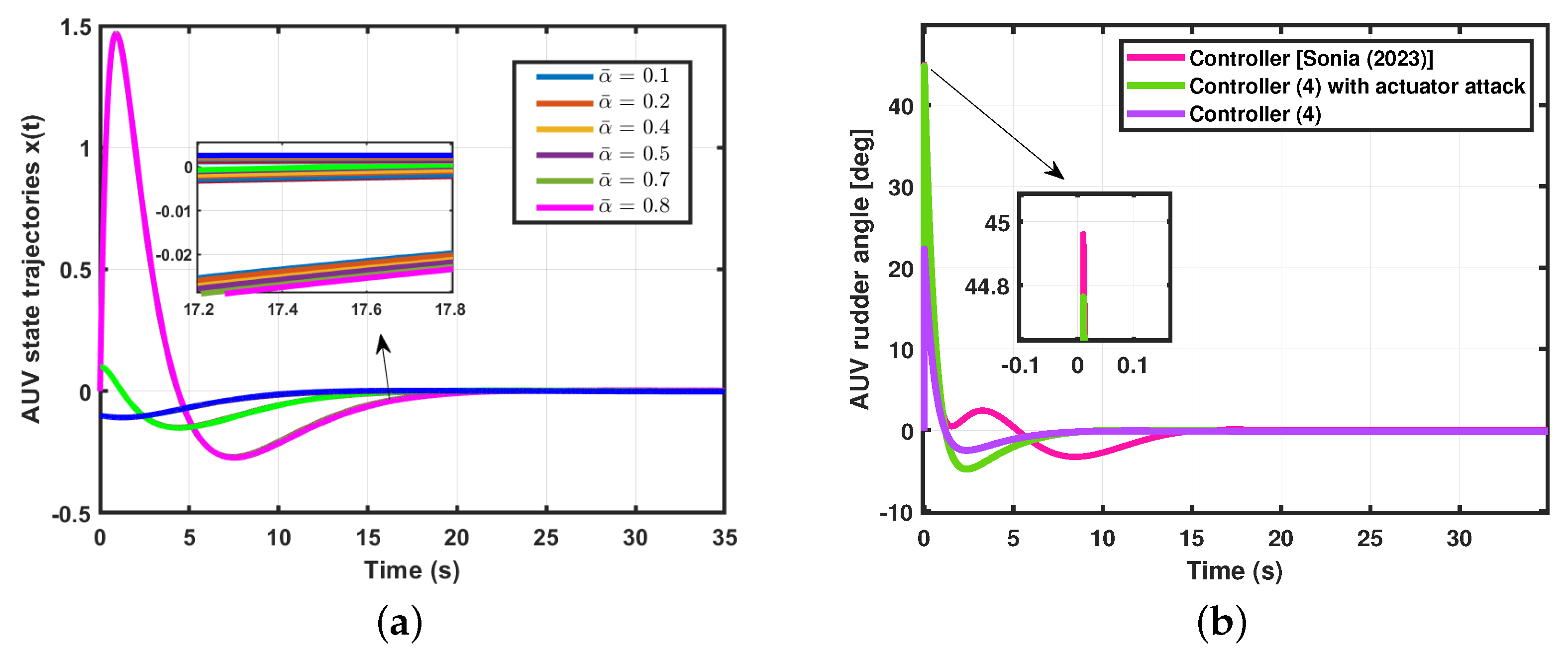
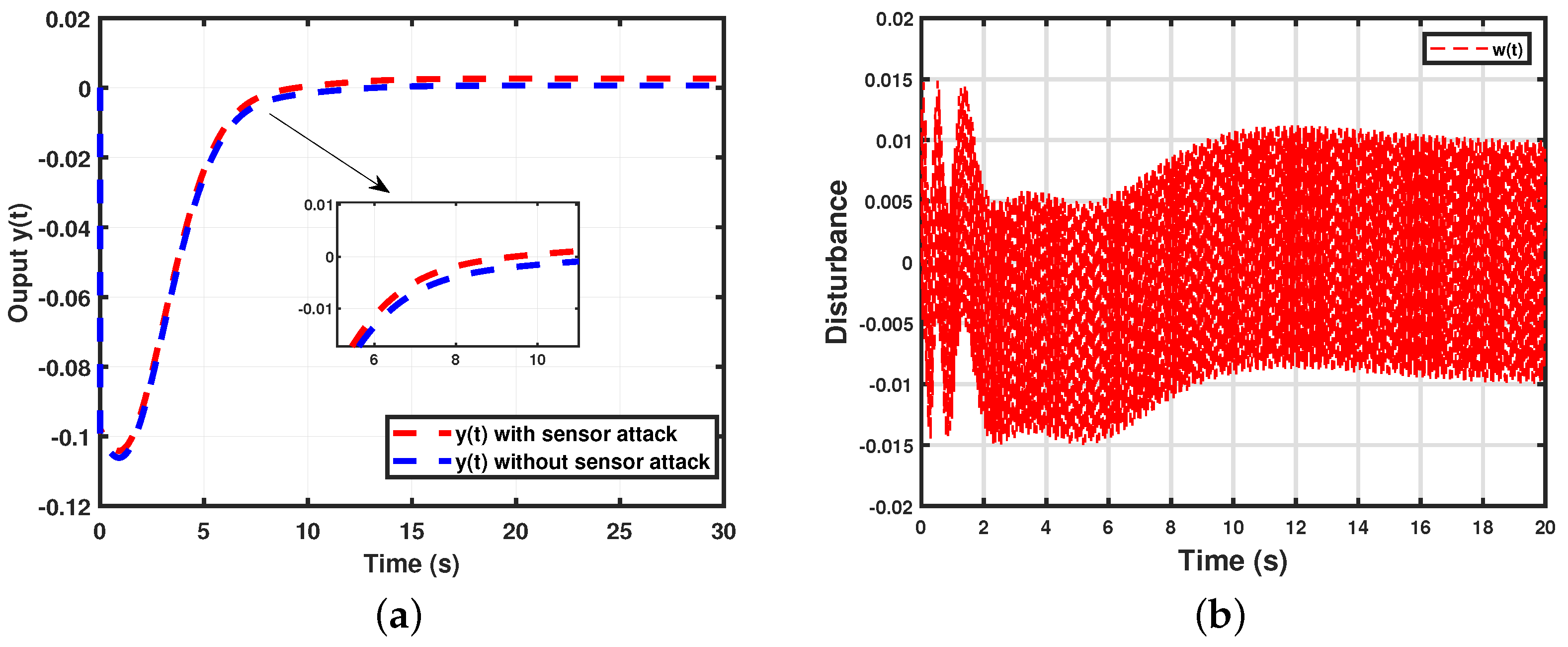
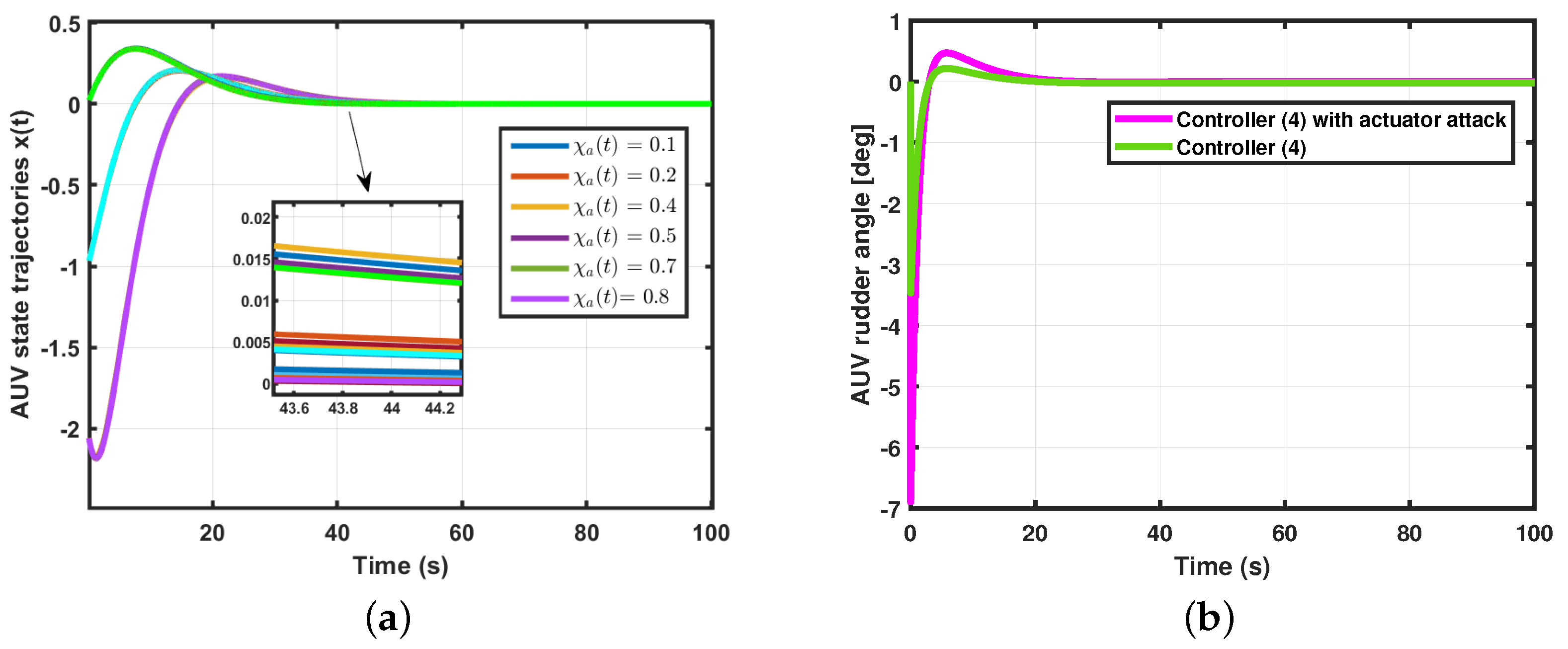
- (AUV system I with time-varying delay) For the simulation of Theorem 1, using the following parameter values: time , performance level minimum , lower bound , upper bound , , the probability of an random event occurs , the possibility of an actuator attack , the possibility of a sensor attack , the probability of an actuator attack , the probability of a sensor attack , , , and . We obtained the control gain matrix for the AUV system (4). Thus, the state trajectories simulation result is shown in Figure 2.
- Case 2.
- Case 3.
- Case 4.
- Case 5.
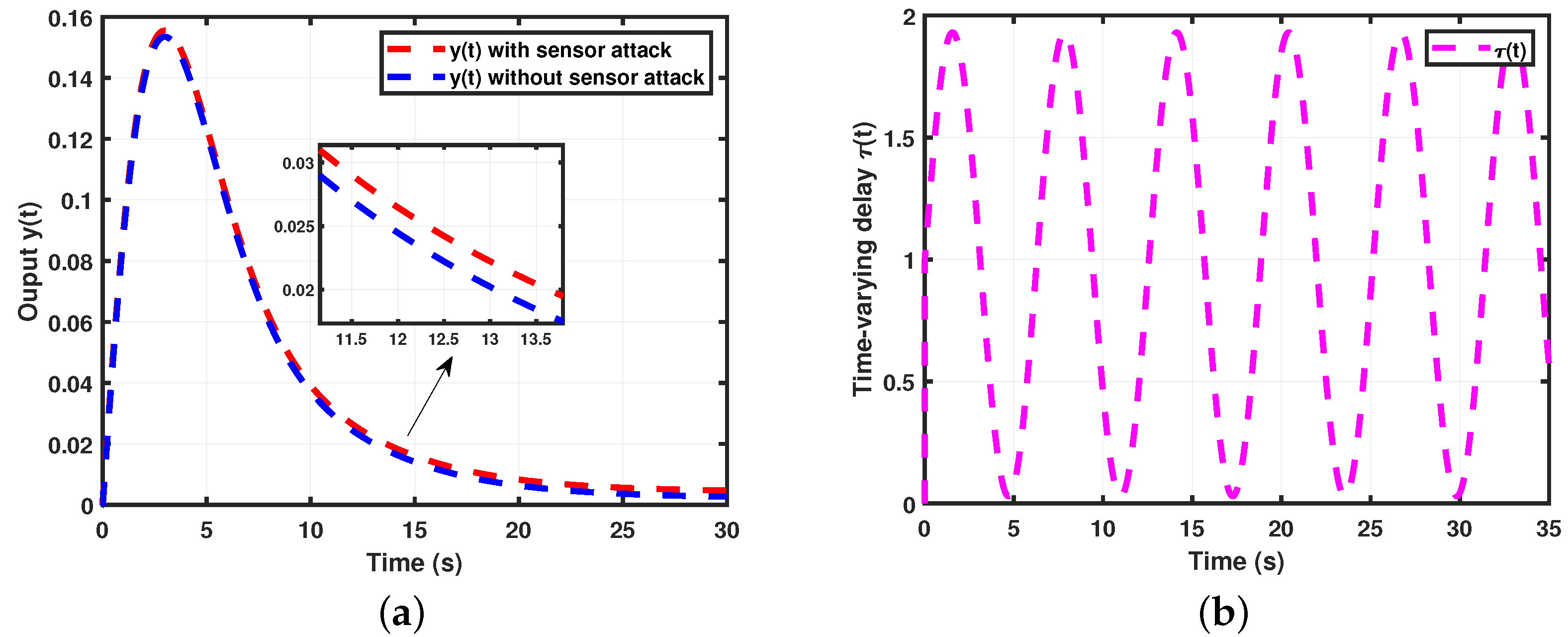
- Case 1.
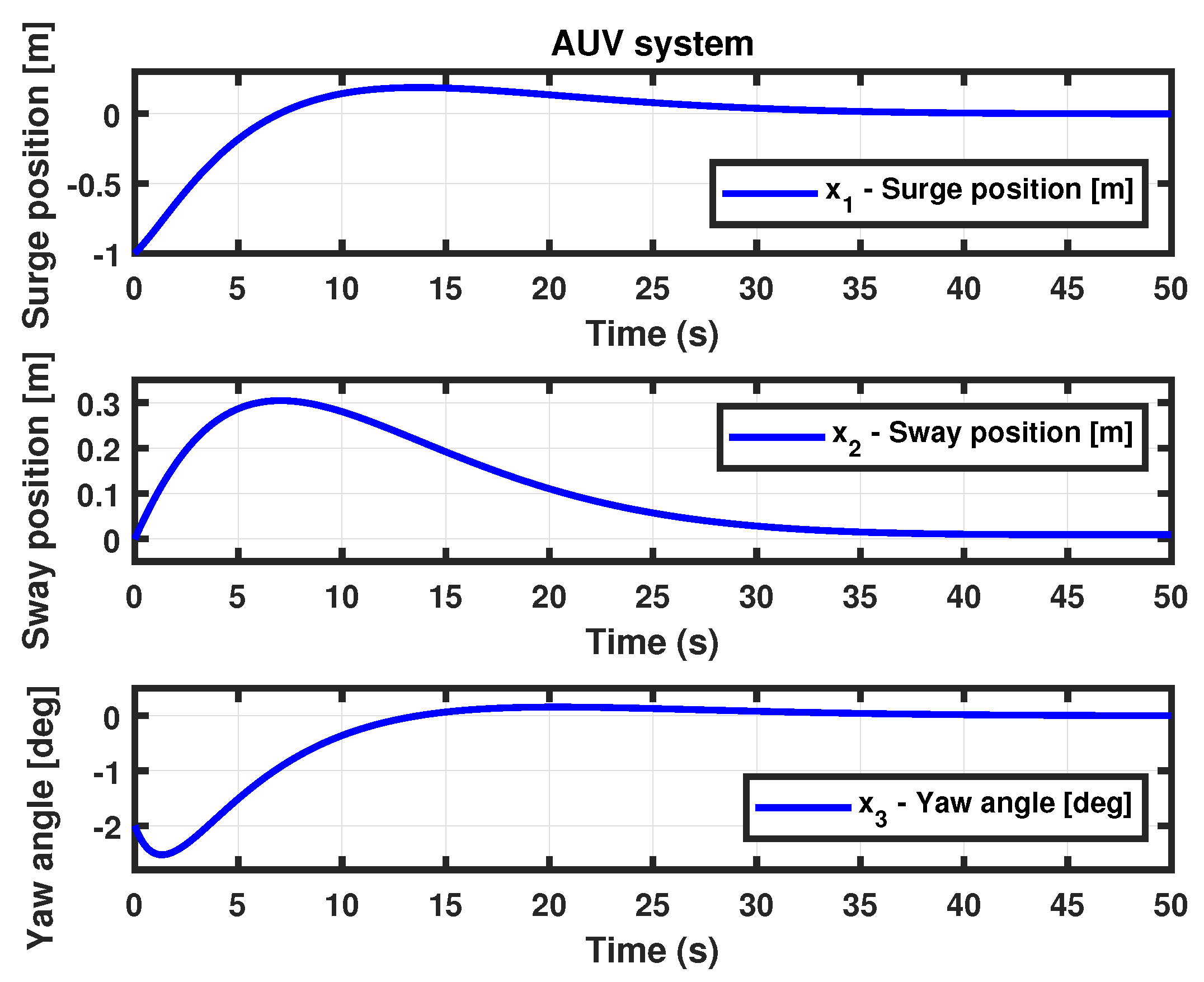
- (AUV system II with time-varying delays) For the simulation of Theorem 2, we used the following parameter values: time , performance level minimum , lower bound , upper bound , , the probability of an random event occurs , the possibility of an actuator attack , the possibility of a sensor attack , the probability of an actuator attack , the probability of a sensor attack , , , and . We obtained the controller gain matrix for the AUV system (6). Thus, the state trajectories simulation result is presented in Figure 6.
- Case 2.
- Case 3.
- Case 4.
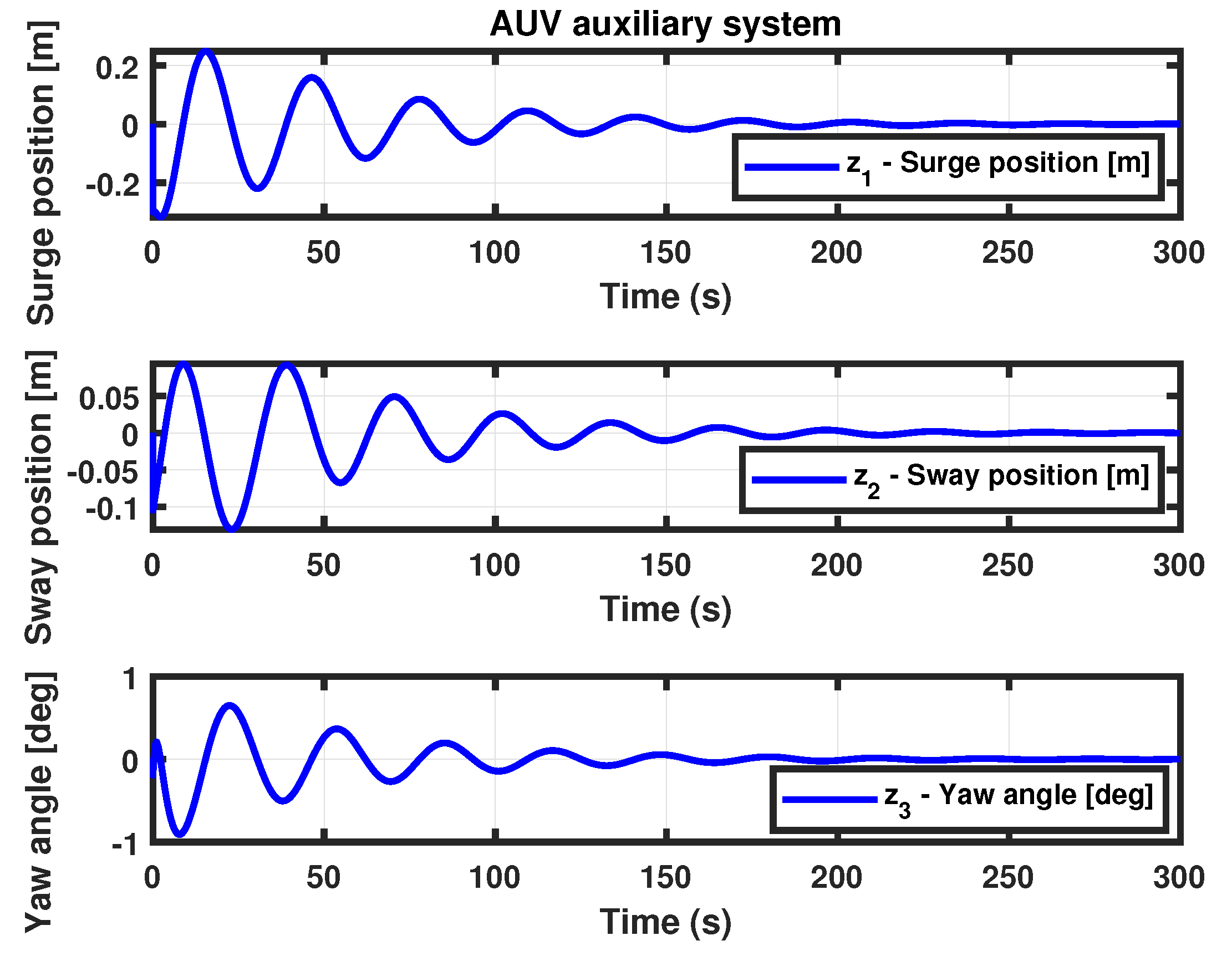
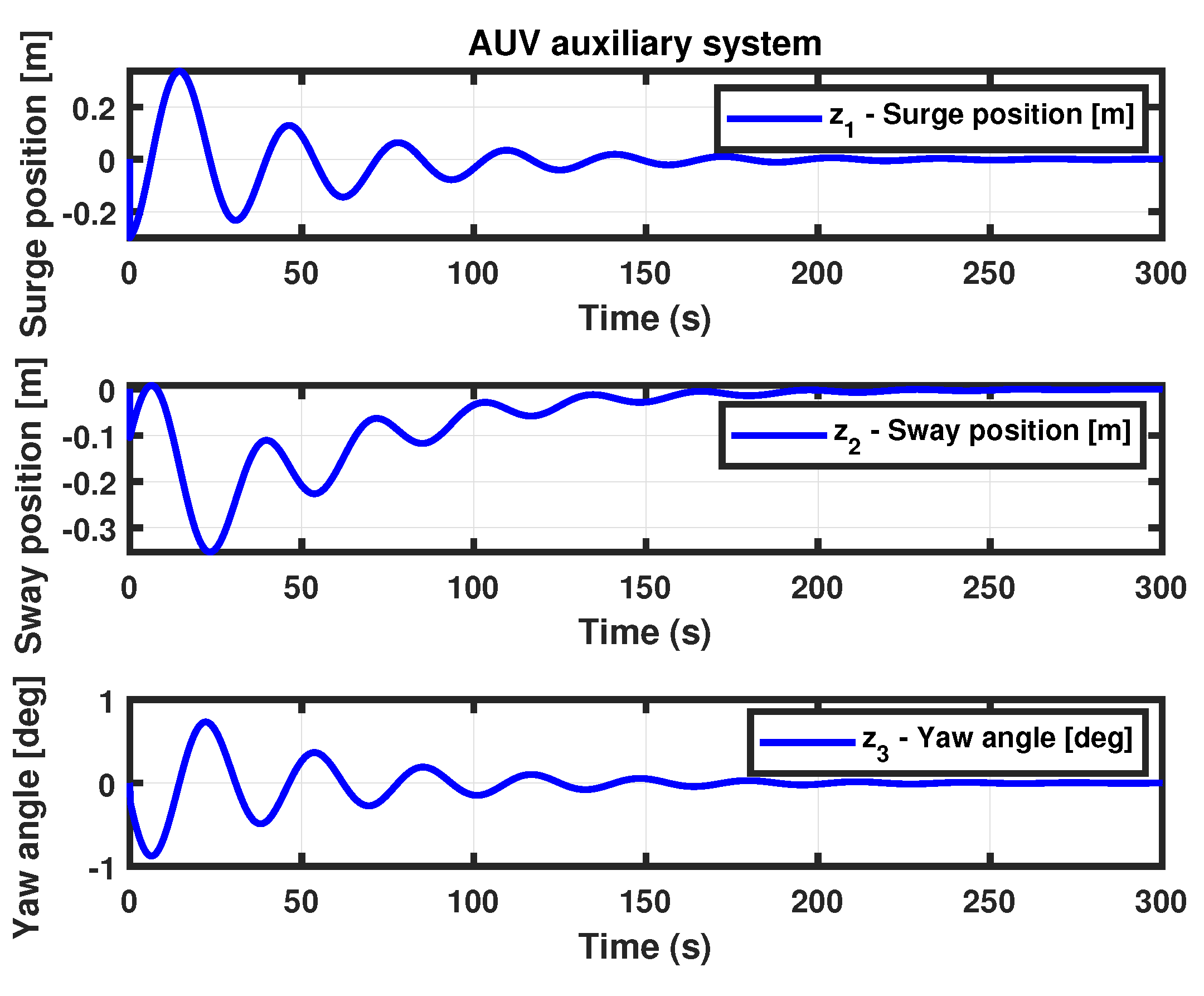
- (Auxiliary state dynamics system II) Theorem 4 for the AUV auxiliary system yields the controller gain matrix , using the same parameter values as in Theorem 2. The surge and sway positions, along with the yaw angle of the auxiliary system state trajectories, are shown in Figure 9.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Thuyen, N.A.; Thanh, P.N.N.; Anh, H.P.H. Adaptive finite-time leader-follower formation control for multiple AUVs regarding uncertain dynamics and disturbances. Ocean Eng. 2023, 269, 113503. [Google Scholar] [CrossRef]
- Li, Y.; He, J.; Shen, H.; Zhang, W.; Li, Y. Adaptive practical prescribed-time fault-tolerant control for autonomous underwater vehicles trajectory tracking. Ocean Eng. 2023, 277, 114263. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, Z.; Chen, M.; Kong, L. Predefined-time sliding mode formation control for multiple autonomous underwater vehicles with uncertainties. Chaos Solitons Fractals 2021, 144, 110680. [Google Scholar] [CrossRef]
- Li, J.; Du, J.; Chang, W.J. Robust time-varying formation control for underactuated autonomous underwater vehicles with disturbances under input saturation. Ocean Eng. 2019, 179, 180–188. [Google Scholar] [CrossRef]
- Li, J.; Du, J.; Hu, X. Robust for dynamic positioning of ships under unknown disturbances and input constraints. Ocean Eng. 2020, 206, 107254. [Google Scholar] [CrossRef]
- Li, X.G.; Wang, J.M. Fuzzy active disturbance rejection control design for autonomous underwater vehicle manipulators system. Adv. Control Appl. 2021, 3, e44. [Google Scholar] [CrossRef]
- Liu, H.; Lyu, Y.; Lewis, F.L.; Wan, Y. Robust time-varying formation control for multiple underwater vehicles subject to nonlinearities and uncertainties. Int. J. Robust Nonlinear Control 2019, 29, 2712–2724. [Google Scholar] [CrossRef]
- Xu, Y.; Wan, L.; Zhang, Z.; Chen, G. Robust adaptive path following control of autonomous underwater vehicle with uncertainties and communication bandwidth limitation. Ocean Eng. 2023, 287, 115895. [Google Scholar] [CrossRef]
- Shojaei, K.; Chatraei, A. Robust platoon control of underactuated autonomous underwater vehicles subjected to nonlinearities, uncertainties and range and angle constraints. Appl. Ocean Res. 2021, 110, 102594. [Google Scholar] [CrossRef]
- Li, T.; Wang, W.; Chen, W. Mixed H∞ and passive event-triggered control for Markovian jump systems with sensor saturation under cyber-attacks. Asian J. Control 2022, 24, 3588–3600. [Google Scholar] [CrossRef]
- Zhang, H.; Chen, Z.; Zhao, N.; Xing, B.; Mathiyalagan, K. Adaptive neural dissipative control for markovian jump cyber-Physical systems against sensor and actuator attacks. J. Frank. Inst. 2023, 360, 7676–7698. [Google Scholar] [CrossRef]
- Nateghi, S.; Shtessel, Y.; Edwards, C. Resilient control of cyber-physical systems under sensor and actuator attacks driven by adaptive sliding mode observer. Int. J. Robust Nonlinear Control 2021, 31, 7425–7443. [Google Scholar] [CrossRef]
- Syfert, M.; Ordys, A.; Kościelny, J.M.; Wnuk, P.; Możaryn, J.; Kukiełka, K. Integrated approach to diagnostics of failures and cyber-attacks in industrial control systems. Energies 2022, 15, 6212. [Google Scholar] [CrossRef]
- Huang, X.; Dong, J. Secure tracking control against sensor and actuator attacks: A robust model-reference adaptive control method. Inf. Sci. 2022, 604, 11–27. [Google Scholar] [CrossRef]
- Huang, X.; Xing, M.; Mo, H.; Hu, S.; Luo, H. Stabilization of uncertain networked control systems with actuator saturation and probabilistic cyberattacks. Asian J. Control 2023, 25, 1407–1419. [Google Scholar] [CrossRef]
- Saravanakumar, T.; Lee, T. Hybrid-driven-based resilient control for networked T-S fuzzy systems with time-delay and cyber-attacks. Int. J. Robust Nonlinear Control 2023, 33, 7869–7891. [Google Scholar] [CrossRef]
- Saravanakumar, T.; Nirmala, V.; Raja, R.; Cao, J.; Lu, G. Finite-time reliable dissipative control of neutral-type switched artificial neural networks with non-linear fault inputs and randomly occurring uncertainties. Asian J. Control 2020, 22, 2487–2499. [Google Scholar] [CrossRef]
- Vimal Kumar, S.; Marshal Anthoni, S.; Raja, R. Dissipative analysis for aircraft flight control systems with randomly occurring uncertainties via non-fragile sampled-data control. Math. Comput. Simul. 2019, 155, 217–226. [Google Scholar] [CrossRef]
- Ghrab, S.; Ahmed Ali, S.; Benamor, A.; Langlois, N.; Messaoud, H. A novel robust discrete-time integral sliding mode tracking control design for time-varying delay MIMO systems with unknown uncertainties. ISA Trans. 2024, 145, 1–18. [Google Scholar] [CrossRef]
- Ghrab, S.; Benamor, A.; Messaoud, H. A new robust discrete-time sliding mode control design for systems with time-varying delays on state and input and unknown unmatched parameter uncertainties. Math. Comput. Simul. 2021, 190, 921–945. [Google Scholar] [CrossRef]
- Hernández-González, O.; Ramírez-Rasgado, F.; Farza, M.; Guerrero-Sánchez, M.-E.; Astorga-Zaragoza, C.-M.; M’Saad, M.; Valencia-Palomo, G. Observer for Nonlinear Systems with Time-Varying Delays: Application to a Two-Degrees-of-Freedom Helicopter. Aerospace 2024, 11, 206. [Google Scholar] [CrossRef]
- Campos-Martínez, S.-N.; Hernández-González, O.; Guerrero-Sánchez, M.-E.; Valencia-Palomo, G.; Targui, B.; López-Estrada, F.-R. Consensus Tracking Control of Multiple Unmanned Aerial Vehicles Subject to Distinct Unknown Delays. Machines 2024, 12, 337. [Google Scholar] [CrossRef]
- Hernández-González, O.; Targui, B.; Valencia-Palomo, G.; Guerrero-Sánchez, M.-E. Robust cascade observer for a disturbance unmanned aerial vehicle carrying a load under multiple time-varying delays and uncertainties. Int. J. Syst. Sci. 2024, 55, 1056–1072. [Google Scholar] [CrossRef]
- Li, Y.; Voos, H. An application of linear algebra theory in networked control systems: Stochastic cyber-attacks detection approach. IMA J. Math. Control Inf. 2015, 1–22. [Google Scholar] [CrossRef]
- Li, Y.; Voos, H.; Rosich, A.; Darouach, M. A Stochastic Cyber-Attack Detection Scheme for Stochastic Control Systems Based on Frequency-Domain Transformation Technique. In Network and System Security. In Proceedings of the 8th International Conference, NSS 2014, Xi’an, China, 15–17 October 2014; Au, M.H., Carminati, B., Kuo, C.-C.J., Eds.; Springer: Cham, Switzerland, 2014; Volume 8792, pp. 209–222. [Google Scholar]
- Zhang, X.; Xu, X.; Li, J.; Luo, Y.; Wang, G.; Brunauer, G.; Dustdar, S. Observer-based H∞ fuzzy fault-tolerant switching control for ship course tracking with steering machine fault detection. ISA Trans. 2023, 140, 32–45. [Google Scholar] [CrossRef] [PubMed]
- Lien, C.H.; Yu, K.W.; Wu, L.C.; Chung, L.Y.; Chen, J.D. Robust H1 switching control and switching signal design for uncertain discrete switched systems with interval time-varying delay. J. Frank. Inst. 2014, 351, 565–578. [Google Scholar] [CrossRef]
- Wu, W.; Wang, X.; Rao, H.; Zhou, B. Delay-dependent Wide-area Damping Controller Synthesis Approach Using Jensen’s Inequality and Evolution Algorithm. CSEE J. Power Energy Syst. 2023, 9, 1774–17785. [Google Scholar]
- Park, P.; Ko, J.W.; Jeong, C. Reciprocally convex approach to stability of systems with time-varying delays. Automatica 2011, 47, 235–238. [Google Scholar] [CrossRef]


| Matrix | Continuous-Time [Proposed Method] | Discrete-Time [19] |
|---|---|---|
| A | ||
| B | ||
| C | ||
| Settling Time(s) | ||||
|---|---|---|---|---|
| Method | Surge | Sway | Yaw | Figure |
| Theorem 1 | 14.23 | 9.84 | 19.68 | Figure 2 |
| Sonia’s Method | 20 | 19 | 22 | Figure 8 in [19] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vimal Kumar, S.; Kim, J. Robust H∞ Control for Autonomous Underwater Vehicle’s Time-Varying Delay Systems under Unknown Random Parameter Uncertainties and Cyber-Attacks. Appl. Sci. 2024, 14, 8827. https://doi.org/10.3390/app14198827
Vimal Kumar S, Kim J. Robust H∞ Control for Autonomous Underwater Vehicle’s Time-Varying Delay Systems under Unknown Random Parameter Uncertainties and Cyber-Attacks. Applied Sciences. 2024; 14(19):8827. https://doi.org/10.3390/app14198827
Chicago/Turabian StyleVimal Kumar, Soundararajan, and Jonghoek Kim. 2024. "Robust H∞ Control for Autonomous Underwater Vehicle’s Time-Varying Delay Systems under Unknown Random Parameter Uncertainties and Cyber-Attacks" Applied Sciences 14, no. 19: 8827. https://doi.org/10.3390/app14198827







