1. Introduction
The advanced metering infrastructure (AMI) is a complete network processing system for collecting, storing and analyzing user electricity data, which is mainly composed of smart meters (SMs), data concentrators (DCs), the measurement data management system (MDMS), the local communication network, and the communication network connecting power company data center [
1]. Among them, the communication network in the AMI includes uplink and downlink networks. The smart meter collects electricity consumption information from the user side and uploads the message to the MDMS through the DC, which belongs to the uplink network, and the process of MDMS transmitting command information from DC to SM belongs to the downlink network [
2]. Eavesdropping, tampering and other attacks on the uplink network will lead to the exposure of electricity data and billing fraud, resulting in privacy leakage (such as whether the user is at home, whether the house is idle) and economic losses. Attacks on the downlink network will lead to errors in the command information, which will destroy the normal operation of the power system and can even lead to the paralysis of the whole power system [
3,
4]. For example, in 2014, Spanish hackers used meter vulnerabilities to conduct billing fraud and even shut down the entire circuit system, causing a large-scale power outage. In 2019, hackers used a firewall vulnerability to launch a denial-of-service attack against the American electrical company, resulting in equipment communication interruption.
In [
5], the security vulnerabilities in the AMI were analyzed, and authentication and encryption were pointed out to be effective means to ensure the secure communication of the AMI. The secure communication scheme based on asymmetric cryptography has problems such as high communication overheads and multiple interactions during asymmetric encryption and decryption, making it unsuitable for smart meters with limited computing and communication resources. The key agreement mechanism allows both parties to negotiate the same session key before communication and uses symmetric encryption to communicate, which has less computation power and a faster speed. The certificateless key agreement scheme can not only avoid the complex certificate management in public key infrastructure (PKI), but also avoid the key escrow in identity-based cryptography (IBC). It is very suitable for entities in AMI with limited computation and communication resources such as smart meters [
6].
In certificateless key agreement schemes, the scheme based on the hash algorithm [
7] uses ultra-lightweight hash functions to achieve key agreements, which is suitable for scenarios with very limited communication resources, but cannot meet the security requirements well. In order to enhance security, many key agreement schemes based on bilinear pairing and an elliptic curve have been proposed. Bilinear mapping is simply a mapping
e, which can map two elements in the cyclic group
and
of order
n to one element in
, and the mapping satisfies bilinearity. The elliptic curve cryptosystem is based on the generalized discrete logarithm problem, and the use of shorter operands can provide the same security level as RSA.
In [
8], anonymous communication between edge computing infrastructures in smart grid was realized, but the complexity of pairing operation increases the computational overhead. In addition, [
9] proved that the scheme struggles to resist impersonation and transient key exposure attacks. In [
10], a key exchange scheme named AAS-IoTaSG was proposed for the smart grid environment in the Internet of Things. This scheme is based on the anonymous signature, which allows the dynamic addition of nodes. However, it is proved by [
9] that the scheme struggles to resist man-in-the-middle attacks and impersonation attacks. In [
11], a key agreement scheme based on the elliptic curve was designed for the smart grid, but it was proved by [
12] that the scheme cannot complete the authentication process in practical application scenarios. In [
13], an authentication and key agreement scheme based on elliptic curves was proposed for smart grid environments that can satisfy forward confidentiality. In [
14], a DRMAS scheme for identity authentication in demand response management in smart grid environment was proposed, which is based on the elliptic curve and the certificate. The use of the certificate and elliptic curve cryptosystem results in higher overheads. In [
15], a lightweight authentication protocol was proposed for the smart metering infrastructure. The protocol is based on one-way hash and an elliptic curve, which can meet the security characteristics such as anonymity and mutual authentication. However, the scheme proved to be fragile in the face of impersonation attacks and key leakage attacks, and could not provide forward secrecy. In [
16], in order to protect the secure communication between users and substations, an authentication scheme was designed using the elliptic curve cryptosystem. It was proved in [
2] that the scheme could not provide anonymous and forward secrecy security features and could not resist ESL (Ephemeral Secret Leakage) attacks. In [
17], a privacy protection and lightweight authentication scheme based on elliptic curves was proposed to achieve secure communication between SMs and neighbor area network gateways. In [
18], Kumar et al.’s scheme [
19] was proven to fail to satisfy security characteristics such as anonymity, and a lightweight key agreement scheme based on elliptic curves was proposed to establish a secure channel for data transmission in the smart grid environment. In [
20], a blockchain-based privacy preserving authentication scheme was proposed for demand response management in the smart grid environment, establishing a secure channel between smart meters and service providers. However, the above schemes still have deficiencies in security, and still need more computational and communication overheads compared with other non-bilinear mapping and non-elliptic curve schemes.
In recent years, many scholars have proposed key agreement schemes based on chaotic maps. The chaotic map is a kind of random nonlinear process with high initial value sensitivity, high complexity and good confidentiality. The chaotic map based on the Chebyshev polynomial originates from the expansion of a multi-angle cosine function and sine function, which is very suitable for the design of cryptography and secure communication schemes. The definition and properties are shown in
Section 2. According to relevant research, the cost of chaotic mapping is only about one-third of the elliptic curve point multiplication operation, which can greatly reduce the operation cost. Compared with bilinear pairing and elliptic curves, chaotic maps have lower computational complexity and higher security. Wang et al. [
21] proposed a lightweight authentication scheme for electric vehicle charging, but it was proved that the scheme had errors in the registration and key agreement stages, and could not achieve secure communication [
22]. In [
23], for the Internet of Vehicles environment, a group key agreement scheme based on chaotic map and bilinear pairing was designed which can support batch authentication. In [
24,
25], an efficient authentication and group authentication protocol based on chaotic mapping was designed for the Internet of Vehicles. In [
26], a three-factor authentication scheme based on the chaotic map was designed for mobile devices, which can meet the corresponding security evaluation criteria. However, the above schemes do not conform to the architecture and message transmission mode of the AMI and cannot be directly applied to the advanced metering infrastructure.
1.1. Motivation
In [
27], the important role of authentication and key agreement mechanism in smart grid environment, especially in AMI system, is expounded, which can effectively protect entities from adversary attacks and threats of unauthorized illegal entities and ensure the reliable operation of the whole system. In [
28], the potential risks in the AMI system are evaluated by the OCTAVE Allegro method. According to [
10,
28], the key agreement scheme designed for the AMI system needs to be able to resist impersonation, man-in-the-middle, replay and other attacks in addition to mutual authentication, ensuring session key security, providing anonymity and forward confidentiality. These are the main requirements of smart grid security. At the same time, because the smart meter equipment has very limited resources, such as computing, communication and power supply, the scheme also needs to be as lightweight as possible to adapt to the increasing traffic in the AMI system.
Through the above analysis of the existing key agreement schemes in AMI or smart grid scenarios, it can be found that most of the existing schemes have been proven to have some security problems and cannot meet the security requirements well. Secondly, the existing key agreement schemes in AMI are basically based on cryptosystems with high computational complexity, such as bilinear pairings, elliptic curves, etc., which require high energy overheads, while ultra-lightweight hash operations cannot provide good security. Last but not least, most of the above schemes do not take into account the message transmission mode in the AMI and cannot adapt well to the actual AMI system. Therefore, in order to ensure secure communication between legitimate entities in the AMI system, the designed scheme needs to establish an appropriate balance between security and efficiency. Based on the premise of satisfying the required security, the overhead should be reduced as much as possible to adapt to the equipment with limited resources, and the architecture and message transmission mode of the AMI system should be fully considered.
1.2. Contribution
The main contributions of this article are as follows.
- (1)
In order to ensure the secure communication between entities in AMI, a lightweight authentication and key agreement scheme based on Chebyshev chaotic map is proposed.
- (2)
The chaotic map with a short key length, low memory occupation and a high secret strength is used to replace the time-consuming bilinear pairing and elliptic curve point multiplication operation, without additional storage certificate and key escrow, which saves the computation and communication overheads based on the premise of realizing the establishment of secure channel.
- (3)
According to the AMI architecture and message transmission mode, the authentication and key agreement mechanism between entities is designed, which establishes a secure channel for message transmission between entities. In addition, in order to solve the problem of the repeated transmission of data and repeated occupation of bandwidth, we also design a multicast key generation mechanism.
- (4)
The security analysis results show that the proposed scheme satisfies the security characteristics such as anonymity and forward secrecy and can resist common attacks such as replay, impersonation and man-in-the-middle. The performance analysis results show that compared with the related schemes, the proposed scheme requires lower computation and communication costs and allows more entities to participate in the same hardware and software environment. The proposed scheme is more suitable for the AMI with limited resources.
1.3. Organization
In
Section 2, the concept of Chebyshev chaotic map and the hypothesis of its difficult problem are given.
Section 3 introduces the AMI architecture.
Section 4 introduces the algorithm design of the proposed scheme in detail.
Section 5 presents a formal and informal analysis of the proposed scheme and compares it with related representative schemes.
Section 6 compares and summarizes the proposed scheme and related work from the perspective of calculation cost and communication cost.
Section 7 discusses the limitations of the proposed scheme and the prospect of future work. Finally,
Section 8 summarizes the article and puts forward the future research directions.
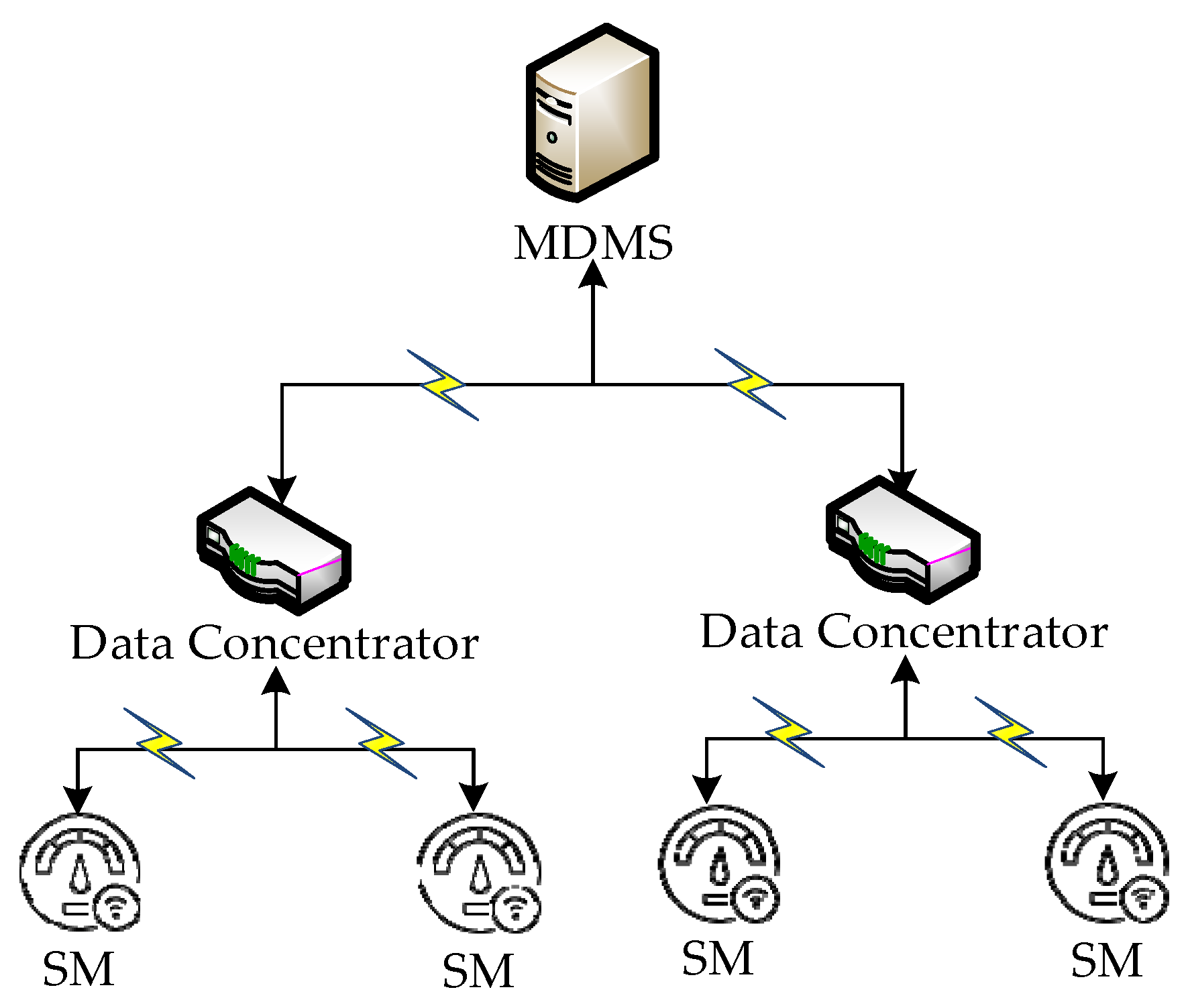
3. AMI System Model
In the AMI, the smart meter is located at the user side, and the collected measurement, illegal power consumption, fault and other data are uploaded to the data concentrator through RS485, PLC and other communication media. It is an intelligent instrument with a microprocessor as the core, and its memory and computing power are relatively limited. The data concentrator is generally installed in the substation, which processes and packages the collected data and forwards it to the measurement data management system through optical fibers, GPRS and other communication media. The measurement data management system is located in the power grid company to store, analyze and use all the data recorded by the smart meter. The communication mode in the uplink network is generally unicast communication, such as smart meter sending measurement data to a data concentrator. In the downlink network, there is also a multicast message transmission method, such as the measurement data management system sending the electricity price information to multiple smart meters simultaneously through the data concentrator. The architecture of the AMI system is shown in
Figure 1.
The AMI has terminal access to a large number of smart meters, which record the power consumption information of each user in real time and upload the power consumption data to the measurement data management system regularly. Once the data are eavesdropped on and tampered with by adversaries, this will lead to the leakage of the user’s privacy information and affect the normal charging of the power company, which will cause conflicts and disputes between the supply and demand sides. The measurement data management system remotely controls the smart meter by transmitting control instructions, such as determining whether to cut off the power according to the user’s electricity bill balance, configuring parameters during the installation of the smart meter, and rewriting the electricity price parameter. Once the control instruction is issued wrongly, it will cause disorders in the power system and affect people’s normal life. In addition, attackers can impersonate legitimate entities and inject false messages into the channel to disrupt the normal operation of the system and even control the entire AMI system.
To sum up, in order to enable entities in AMI to transmit data and exchange information through a secure channel, a lightweight key agreement scheme based on chaotic map is designed in this article. Each entity generates a common session key through authentication and key agreement mechanisms and transmits information through encrypted channels to achieve secure data transmission, preventing unauthenticated devices from obtaining effective information. We also designed the generation of multicast keys to address the characteristics of multicast message transmission in AMI. In addition, the identity information of smart meters bound to users will not be leaked during the interaction process.
4. Proposed Scheme
Due to the use of the same key agreement scheme between MDMS and DC, as well as between DC and SM, for the convenience of description, this section describes the proposed scheme in detail by taking the interaction between DC and SM as an example.
We provide a preliminary explanation of the symbols and their meanings used in our scheme, as shown in Nomenclature part.
4.1. Initialization
The data concentrator is installed by the power company in the substation/distribution station, which is considered reliable. In order to achieve authentication and key agreement with the smart meter in the area under its jurisdiction, the data concentrator performs the following initialization process:
selects a Chebyshev polynomial function with seeds , a large prime number , selects collision-resistant hash functions and , and sets a time threshold to confirm the timeliness of the message. selects a random number and calculates , where is the private key and is the public key.
publishes the system parameters .
4.2. Registration
Smart meters within the jurisdiction of the data concentrator receive public parameters. The smart meter selects a random number as its private key, calculates the public key and publishes it. then computes the and sends to , where is the timestamp and is the unique identification of the smart meter, which is bound to the user’s identity, corresponding to their home address, bank account and IP of the smart meter, relating to absolute privacy.
Upon receiving
,
first verifies the timeliness of the message, and if
, it then proceeds to the next step of calculation:
. After obtaining the
,
selects the random number
and computes
where
is the pseudo identity of the smart meter
, and
sends
to
and saves
.
4.3. Mutual Authentication and Session Key Agreement
and authenticate and negotiate to establish each other’s session key SK.
(1) The smart meter
selects a random number
and a current timestamp
, and calculates
Then, sends to .
(2) After receiving , first verifies the timeliness of the message. If , performs the next operation. Otherwise, terminates the session.
① After the message’s timeliness is verified,
calculates
retrieves , and performs the following steps after successful retrieval; otherwise, terminates the session.
②
performs the following calculation:
and checks whether the equations
and
are established. After successful verification,
performs the next operation; otherwise, the session will be terminated.
③
selects
and calculates:
④
selects
and a current timestamp
, then computes:
⑤ sends to .
(3) After receiving , first verifies the timeliness of the message. If , performs the next step. Otherwise, the session will be terminated.
① After the message timeliness is verified,
calculates:
② In order to prevent potential attacks, checks whether the equation is established. After successful verification, and share the session key ; otherwise, the session will be terminated.
③ updates to for periodic key updates.
(4) After mutual authentication, the smart meter
and data concentrator
use the common session key
for encrypted communication. DC and MDMS negotiate to establish a secure channel through the same steps. The message transmitted in the communication needs to meet the communication protocol. The information frame in the AMI generally contains seven parts, and each part contains several bytes. The format is shown in
Figure 2, where the data domain part is the main body of the communication content that needs to be encrypted.
The data concentrator receives control instructions from the MDMS through the secure channel, such as tripping and closing, and then transmits them to the corresponding smart meter through the secure channel. The information frame format transmitted in this process is shown in
Figure 3, where the address field contains the address of DC and SM,
stands for the secret level, and the data field
will be filled with ciphertext.
4.4. Multicast Key Generation
In the downlink communication network, according to the communication protocol, one or more bytes of the address domain can be replaced by , so as to achieve the effect that the current bytes are multicast addresses and realize the function of broadcasting a message to all eligible smart meters. In order to better adapt to the AMI message transmission mode, the multicast key agreement process is also designed after authentication and unicast key agreement. There are multiple smart meters within the jurisdiction of , and the multicast key agreement process will be described by using the interaction between , and as an example.
① After realizing the unicast key agreement,
selects a current timestamp
and performs the following calculations:
where
is the encrypted ciphertext using the key
between
and
.
sends
to
.
② After receiving the ciphertext,
decrypts
with the session key to obtain
, and then verifies the timeliness of the message. If
,
performs the following calculation; otherwise, it terminates the session.
③ verifies whether the equation is established. If successful, encrypts the instruction information using the group key and sends it to multiple smart meters. decrypts and performs the corresponding operation using the group key ; otherwise, will terminate the session. The MDMS and DC implement multicast key agreement through the same steps as above.
5. Security Analysis and Comparison
In this section, we prove that the proposed scheme can meet the security requirements and can resist common attacks.
5.1. Adversary Model
In the AMI, entities often communicate and transmit data through insecure channels, which are vulnerable to various attacks. In this paper, we choose the well-known and widely accepted CK adversarial model, which defines the adversary A that can completely control the channel during the entire communication process. Its attack capabilities include listening, modifying, deleting and injecting messages. In addition, the adversary can further obtain the private secret value of the entity. In order to prove the security of this scheme under the CK model, we establish the following definition:
: The scheme includes two entities, SM and DC. Any other entity is recorded as .
Queries: Opponent A can query participants to achieve the interaction between the two. The following queries are used to simulate the attack ability of A.
,: A can obtain all communication records between and through the query, which simulates passive attacks (such as an eavesdropping attack).
: A carries out an active attack through the query. Adversary A sends a forged message to entity , and responds to A, where can be obtained by means of interception.
: A can obtain the session key owned by I through the query.
: Through the query, A requests and obtains its long-term secret value.
: This query measures the semantic security of the session key. The adversary A sends a single test query to the oracle, and the oracle begins to toss a coin after receiving the query. If b is 0, a random key of the same size as SK is returned to A. If b is 1, the real SK is passed to A.
: After receiving the query from A, I sends the hash value of the message replaced by the random number as a response to A.
Partnering: Entities and are partners, when they verify each other and negotiate a consistent key.
Freshness: For a session held by participant I, if the session has generated a session key, and A does not issue a query, and at most one query is performed, the session is fresh.
5.2. Formal Security Proof
According to [
2], we rigorously test the security of the proposed scheme via formal security analysis under the widely accepted random oracle model, and prove that the proposed scheme can effectively resist the adversary A defined in the adversarial model.
Definition 3. We use to simulate the security of the scheme. Though the game,
A can send multiple queries to participant I,
but A can perform query at most once,
and I returns . The goal of A is to correctly guess the value of b in the session. The probability that A wins in is defined as . The advantage that A destroys the semantic security of the proposed scheme in polynomial time is defined as:This scheme is secure if adversary A’s advantage of destroying semantic security can be ignored.
Lemma 1. Suppose that are events defined in a probability distribution, and assume that . This means that .
Theorem 1. Assuming that A can perform at most queries,
queries,
and queries,
then the advantage of A iswhere is the length of the hash value. Proof. The proof consists of the game order . For each game, A wins the game when A guesses the value of successfully. □
: The game simulates attacks which are carried out under the standard model, therefore
: Through the query of
,
A can obtain all the messages
and
exchanged between
and
.
A can verify whether the calculated key
SK is real by executing the query. It can be seen that the security of the key cannot be disclosed from the exchanged information. Therefore
: The game simulates all types of queries, and as in
, the game is suspended when the following two situations occur: (1)
Hash queries conflict in output, and (2)
and
are not uniformly distributed. From the birthday paradox, therefore,
: When
A successfully guesses
and
without querying the participants, the game will be suspended, which is different from other games. Therefore,
: In this game, the key
SK can be guessed without querying for the corresponding random oracle. The game is no different from the above games, except that
A performs a hash query on the random oracle on the
, where
. Therefore,
where
A queries the random tuple
from the
oracle to calculate
, where
.
:
A executes the
query in this game, which is different from the above game. If
A performs a hash query on
, the probability that
A can obtain
SK does not exceed
. If
A executes the
query, it can be inferred from the definition of freshness that the probability of
A obtaining
does not exceed
. Therefore,
Due to
A’s inability to distinguish between a real and random session key without using the correct input to perform
queries,
According to the game and Lemma 1, Theorem 1 can be verified. □
The above proof process means that the probability of attacker A winning in the game is negligible, so the proposed scheme is safe under the random oracle model. This protocol can guarantee the security of the session key in the process of authenticated key exchange when communicating between entities in AMI.
5.3. Informal Security Analysis
5.3.1. Mutual Authentication
In the proposed scheme, authenticates by confirming whether the equation is established, and authenticates by confirming whether the equation is established. After mutual authentication, SM and DC negotiate the session key to build a secure channel.
5.3.2. Anonymity and Un-Traceability
In the proposed scheme, if the adversary obtains and in the interaction process of and by means of eavesdropping, the is generated by a one-way hash function and updated periodically. is generated by random numbers, is constantly changing with , and is also variable. The adversary cannot derive or track the real , so the scheme provides anonymity and non-traceability for users.
5.3.3. Forward Secrecy
Even if all secret values of smart meters and data concentrators are obtained by the adversary, all previous session keys must remain secure. If and are obtained by means of eavesdropping, the adversary can calculate and , but must obtain to calculate the previous key . Due to the computational difficulties of CMDL and CMDH problems, it is not feasible for to obtain random numbers and from and . So, cannot successfully calculate , and the scheme achieves forward secrecy.
5.3.4. SM Impersonation Attack Resistance
Adversary needs to obtain the value of to forge message in order to impersonate a legitimate smart meter. can be calculated by two means: (1) the legitimate smart meter can compute it; and (2) the data concentrator knows and can calculate it. It is computationally impossible for to compute these parameters, so does not have the ability to impersonate smart meters within the scope of . So, the scheme can effectively resist smart meter impersonation attack.
5.3.5. DC Impersonation Attack Resistance
In order to impersonate a legitimate data concentrator, adversary must compute a valid . and are calculated by and computed by the hash function. Therefore, cannot directly obtain these parameters and cannot guess the values successfully in polynomial time. In order to calculate the above parameters, must obtain , but it is impossible to obtain the private values in polynomial time, and because of the anonymity and un-traceability of the scheme, cannot obtain . Therefore, cannot calculate a valid response message, so the scheme can effectively resist data concentrator impersonation attack.
5.3.6. Replay Attack Resistance
In the proposed scheme, messages and transmitted between entities all contain timestamps. In addition, before each interaction, the entity checks the timeliness of the received message, and only messages that arrive within the specified time will be received. Therefore, the scheme can effectively resist replay attack.
5.3.7. Man-in-the-Middle Attack Resistance
Suppose that intercepts the request message and response message ; in order for the attack to succeed, the new information flow and need to be forged by A, or the previous information flows need to be replayed. As mentioned above, the scheme can resist replay attack and impersonation attack, so cannot authenticate through both smart meters and data concentrators simultaneously. Therefore, the scheme can resist man-in-the-middle attack.
5.3.8. ESL (Ephemeral Secret Leakage) Attack Resistance
Assuming that the secret value is obtained by the adversary , can calculate and . In order to obtain , must be able to calculate and the real . However, cannot calculate the correct that needs to be calculated using the long-term secret value in polynomial time. Therefore, the scheme can resist the ESL attack.
5.3.9. De-Synchronization Attack Resistance
Even if the first message flow is intercepted by the adversary during the key agreement phase, DC does not need to update the parameters in the database, which will not affect the consistency of the next communication. Even if the second message flow is intercepted by the adversary, it still cannot affect the consistency of communication between SM and DC. Only when is established will the communication parties update the data. Therefore, the scheme can resist de-synchronization attack.
5.3.10. DDoS (Distributed Denial of Service) Attack Resistance
DDoS attacks include replay, false data injection, de-synchronization, flooding, jamming, etc. The above security analysis shows that this scheme can achieve mutual authentication and session key security. Therefore, the proposed scheme can resist false message injection attacks, which are mainly against unauthenticated and unencrypted communication processes.
The above analysis shows that the proposed scheme can also resist the desynchronization attack. At each step, the entity verifies the validity of the received message, which ensures the consistency of the messages between the two sides of the communication. Consistency verification can also resist the jamming attack.
After receiving the authentication request, the data concentrator first checks the timeliness of the message, and directly discards the messages that do not meet the timeliness requirement, thus resisting the DoS attack by replaying the old message. Next, the data concentrator authenticates the smart meter. The verification of the authentication request only involves the Chebyshev polynomial and the hash operation with low computational overheads, which requires very few computing resources, and discards the packets that fail to verify and terminate the session at the same time, which can alleviate the impact of the flooding attack. A further defense scheme against DDoS attack is given in
Section 7. Therefore, the proposed scheme can resist or mitigate the above DDoS attacks.
5.3.11. Key-Compromise Impersonation Resistance
Even if the secret value stored in the SM is obtained by the adversary, since the session key of different smart meters is different, it will only cause the session key leakage between and in this period, and will not cause the session key leakage between and . So, the scheme can resist key-compromise impersonation attack.
We compared the proposed scheme with relevant representative schemes (i.e., Hu et al. [
2], Abbasinezhad-mood et al. [
13], Chaudhry et al. [
17], Baghestani et al. [
18], and Park et al. [
20]) in terms of security, and the comparison results can be seen in
Table 1. The symbol “
![Applsci 14 02299 i061]()
” represents that the scheme has this security feature, and “
![Applsci 14 02299 i062]()
” indicates that the scheme does not meet or does not mention this security feature. From
Table 1, it can be seen that the proposed scheme provides higher security and is more suitable for AMI scenarios.
6. Performance Evaluation
In this section, the performance of the proposed scheme is analyzed in terms of computation cost, communication cost and energy consumption, where the cost mainly depends on the authentication and key agreement phases. This section also compares the proposed scheme with related representative schemes (i.e., Hu et al. [
2], Abbasinezhad-mood et al. [
13], Chaudhry et al. [
17], Baghestani et al. [
18], and Park et al. [
20]) to evaluate the performance of our scheme.
6.1. Computation Cost
In order to measure the computational overheads of the proposed scheme in the key agreement process, according to [
25,
26], we conducted experiments on different encryption primitives using the big data computing library to measure their execution time. Our experimental environment was set as follows: (1) hardware environment: Inter Core I5-12500H processor (Intel, Santa Clara, America) with clock frequency of 2.50 GHz, 16 GB RAM Memory; (2) software configuration: Windows 10 operating system, Visual C++ 2017 Software, MIRACL (Multiprecision Integer and Rational Arithmetic C/C++ Library) big data library computing. We took the average value of one hundred operations as the execution time of the related operations to reduce the error. According to the migration experiment in [
29], the time cost required for smart meters equipped with microprocessor R5F212B8SDFP (Renesas, Tokyo, Japan) to perform corresponding operations can be obtained by migration experiments. The time cost corresponding to different operations is shown in
Table 2, and
Table 3 lists the computational costs required for the proposed scheme compared to other representative schemes. The computation costs for XOR and string concatenation operations can be ignored compared to the operations in
Table 2, so they were omitted.
Figure 4 shows the computation cost of the smart meter in different schemes, indicating that the computation cost of our scheme on the smart meter side is the lowest, which is mainly due to the time-consuming bilinear pairing and elliptic curve point multiplication operation replaced by the Chebyshev chaotic map. The overhead of the smart meter side was reduced by 77.35%, 69.37%, 68.89%, 53.42%, and 52.96%, respectively.
Figure 5 shows the time required for this scheme and the comparison scheme to complete the key agreement when the number of smart meters is 100, 200, 300, 400 and 500, respectively. The time required of our scheme is much smaller than that of the comparison scheme, and the overhead is only about 1.1 s when the number of smart meters reaches 500, which accounts for only 22% of the message transmission time threshold (5 s) in AMI. Our scheme is better than the existing lightweight schemes. With the increase in the number of smart meters and the limited computing resources of the AMI network infrastructure, our scheme has the slowest growth rate in time overhead. It means that in the same hardware and software environment, this scheme allows more smart meters to access. Compared with other schemes, our scheme has better scalability.
6.2. Communication Cost
In our scheme, the size of a smart meter identity ID, a Chebyshev polynomial, a random number, a hash output, a timestamp, and a ciphertext in the symmetric encryption and decryption algorithm is assumed to be 64, 160, 64, 160, 16, 128 bits, respectively. In the process of key agreement, only two information interactions are carried out. Firstly, the smart meter sends to the data concentrator, with the communication cost of (64 + 160 + 160 + 160 + 16) = 560 bits; secondly, the data concentrator sends to the smart meter, with the communication cost of (160 + 160 + 160 + 16) = 496 bits. The total communication cost in the key agreement process of the proposed scheme is 1056 bits.
The communication costs between the scheme and other representative schemes are shown in
Table 3.
Figure 6 shows the comparison of communication costs among different schemes, indicating that the proposed scheme has the lowest communication cost.
6.3. Energy Consumption
Since the smart meter resources in the AMI are very limited and usually rely on limited power supply to operate, energy consumption is also the key to performance analysis. Here, we analyze the energy consumption of smart meters in sending/receiving messages. According to [
15], the energy consumed by the smart meter to send and receive 1 bit of data is
and
, respectively, so the energy consumption of the proposed scheme is about
. Through the above analysis of computing and communication overheads, it can be seen that this scheme also has advantages in energy consumption. Combined with
Table 3, it is easy to calculate the corresponding energy consumption.
Figure 7 shows the comparison of the proposed scheme with other related schemes in terms of energy consumption.
In summary, the proposed scheme achieves communication security of AMI with the minimum computation, communication cost and energy consumption, greatly improving performance and reducing the burden on smart meters. The improvement of performance means that the scheme can accommodate more access to smart meters, thereby reducing the cost of software and hardware iteration, which is of great significance in practical applications.
7. Discussion
In this article, our scheme relies on the reliability of DC, which may lead to the single-point failure problem. With the development of blockchain technology, the cost of hardware and software is gradually reduced, and the access volume of smart meters in AMI system is also increasing year by year. The average technical cost per user is also getting lower and lower. We are designing new solutions to solve the potential single-point failure problem by introducing decentralized blockchain into AMI.
In the traditional centralized structure, the resources of a single device are limited and the ability to resist attacks is weak, which may affect the entire network in the event of failure or in the face of new security threats. The introduction of blockchain can not only solve the problem of single point of failure, but also enhance the flexibility and anti-attack ability of the scheme, such as enhancing the system’s ability to resist flooding attacks. With the increase in the number of blockchain nodes, the total computing power is also growing, and the entire AMI network will become more and more difficult to be submerged or even paralyzed. In addition, the dynamic addition and revocation of devices are also allowed.
In our scheme, different entities of AMIs adopt the same cryptosystem. However, in the actual AMI system, due to the complexity of the communication network and the differences in resource capacity, different entities may adopt different cryptosystems. This provides ideas for our further research. In future research, we will consider the design and application of heterogeneous cryptosystems in the AMI to enhance the applicability of the AMI with different configurations.
In addition, we will further conduct testing on larger AMI networks to better evaluate the effectiveness of the proposed scheme, which will help us to identify actual security challenges and compatibility issues and make corresponding adjustments.
 ” represents that the scheme has this security feature, and “
” represents that the scheme has this security feature, and “ ” indicates that the scheme does not meet or does not mention this security feature. From Table 1, it can be seen that the proposed scheme provides higher security and is more suitable for AMI scenarios.
” indicates that the scheme does not meet or does not mention this security feature. From Table 1, it can be seen that the proposed scheme provides higher security and is more suitable for AMI scenarios.