FeRHA: Fuzzy-Extractor-Based RF and Hardware Fingerprinting Two-Factor Authentication
Abstract
1. Introduction
2. Related Work
| Ref. | Key Feature | Advantage | Disadvantage |
|---|---|---|---|
| [25] | PUF-based authentication | Enables mutual authentication between IoT devices | Relies on an intermediary server to store CRPs and generate secure tokens |
| [26] | PUF-based authentication | No stored explicit CRPs in the verifier database | Introduces additional complexity due to encrypted CRPs |
| [27] | PUF-based authentication | Develops a security solution to address counterfeit products | Utilizes Rabin public-key encryption |
| [28] | PUF-based authentication | No partial/full CRPs are stored | Incorporates AES-128-based encryption and require an intermediary server |
| [29] | Authentication using PUFs and blockchain | Utilizes blockchain smart contracts | Computationally heavy due to the use of Diffie–Hellman protocol |
| [30] | Multifactor authentication using PUFs | Suitable for telehealth system for mobile and IoT edge devices | Relies on user passwords during the authentication |
| [31] | PUF-based authentication and key generation | Use simple cryptographic primitives | Vulnerable to machine learning attacks. |
| [32] | PUF-based authentication | No explicit CRP storage in the verifier database | Overhead of cryptographic operations (geometric threshold secret sharing) |
| [33] | PUF-based authentication | Applies challenge obfuscation and uses a subset of response bits | Susceptible to impersonation attacks due to CRP disclosure |
| [34] | PUF-based authentication | Obfuscates challenge bit-strings to counter modeling attacks | Use of hash functions introduces a significant computational overhead |
| [35] | PUF-based authentication | Relies on secret sharing to minimize exposure of raw PUF responses | Susceptible to impersonation attacks due to increased CRP disclosure |
| [13] | PUF-based mutual authentication | Mitigates modeling attacks using unique binary operations | Attacker can access challenge bits; dependant on secrecy of binary operations |
| [36] | Three-factor authentication | Combines passwords, biometrics, and PUFs without storing node IDs | Introduces a significant computational overhead and requires the involvement of a server for mutual authentication |
| [37] | PUF-based authentication | Integrates secret sharing with PUF for authentication | Introduces computational overhead and requires the involvement of a server for mutual authentication |
| [38,39,40] | IoT authentication using RF fingerprinting | Utilizes unique characteristics of wireless signals and avoids complex cryptography | Vulnerable to adversarial attacks |
| [21,42,43] | Two-factor authentication | Leverages RFFs and PUF for authenticating wireless nodes | Susceptible to modeling attacks; no mitigation of the noise impact on biometric data |
3. Preliminaries
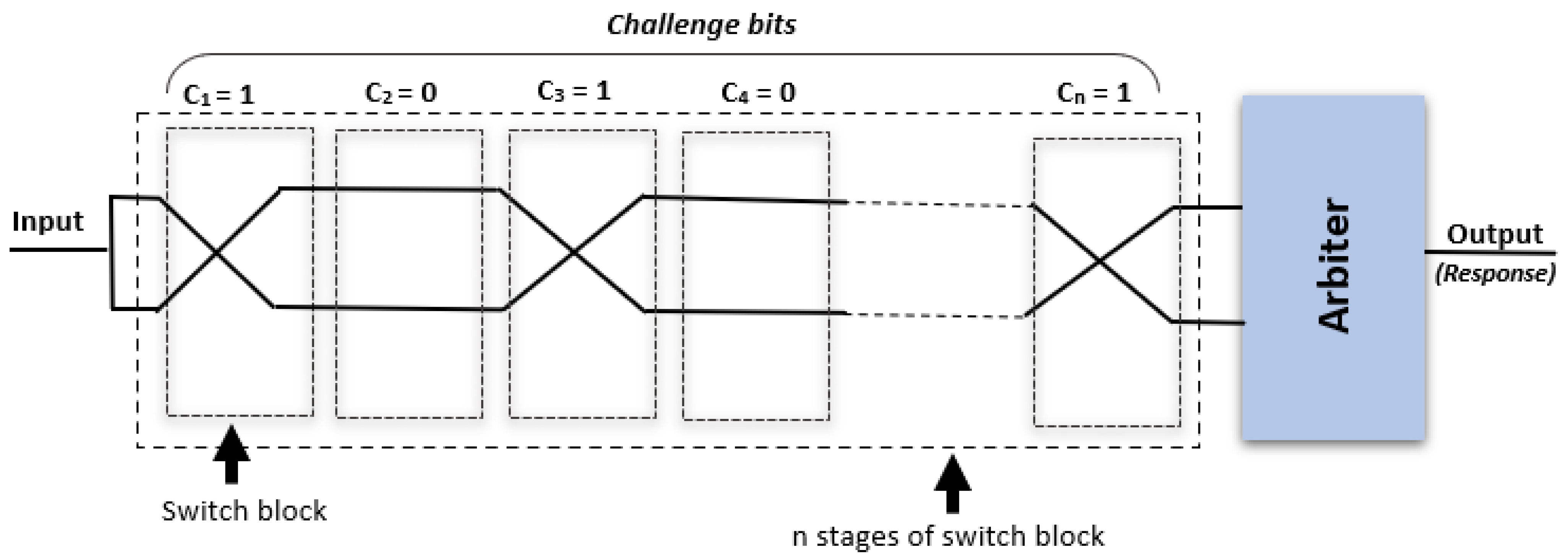
3.1. Physical Unclonable Functions
3.2. Radio Frequency Fingerprinting
3.3. Fuzzy Extractor
4. System Model and Approach Overview
4.1. System and Attack Models
4.2. Approach Overview
- Develop a novel lightweight PUF-based mechanism for authenticating IoT devices. Rather than applying encryption, our mechanism pursues two-factor authentication by combining the benefits of PUFs and RF fingerprinting.
- Given the dynamic nature of IoT systems, intermediaries should be avoided, and authentication should be conducted in a decentralized manner.
- The system should resist attempts by adversaries to eavesdrop and gain knowledge of many CRPs of the embedded PUF to model it using machine learning techniques.
- To ensure accurate authentication, it is essential to mitigate the noise in biometric data.
5. Combined PUF- and RFF-Based Authentication
5.1. Enrollment Phase
5.2. Operation Phase
| Algorithm 1 FeRHA(,) |
|
5.3. Replay Attack Mitigation
- Initializing the counter: the initialization value of is established through the application of to the helper string . The mathematical representation of this initialization process is . This method assures that the initial state of the counter is unpredictable and associated with the hardware characteristics of the involved devices, providing a robust foundation for the counter’s integrity.
- Counter obfuscation: to mitigate the risk of interception or exploitation of , we factor in the token that is shared between the prover and verifier. To obscure the counter value, an operation is employed to mask with the , resulting in , as shown in Figure 5. The value is chosen from the token list through a pre-agreement between the prover, , and the verifier, ; such a pre-agreement could be simply determined by the server by setting a default entry in the pairwise challenge-token lists for the entire IoT network, as noted in Section 5.1. It should be noted that will not be used as an authentication token, but rather assigned and selected to be the . This mechanism is dependent on the verifier side, thereby rendering an adversary who attempts to eavesdrop over multiple links to target unsuccessful, since , as illustrated in Figure 4. This operation is instrumental in ensuring that the actual counter value transmitted over the network remains indiscernible and cannot be directly leveraged by an adversary.
- Verification operation: upon receiving a packet, the is used to perform an operation, enabling the recovery of the original counter value, . Thereafter, the verifier performs a counter value check, ensuring that it is new and has not been previously utilized during the session.
6. Results and Performance Analysis
6.1. FeRHA Implementation
6.2. Performance Results
- Single-link attack: in this scenario, we focus on the authentication of a prover, , by a verifier, , where an adversary may intercept transmissions between them. It is important to note that the adversary’s primary objective is to capture as many CRPs as possible for during the operation phase of FeRHA. Specifically, the adversary aims to obtain the maximum number of CRPs for the prover’s . Recall, FeRHA utilizes two primitives, PUFs and RFF, to generate an authentication token. Notably, the PUF response, R, is not included in the verifier’s request. Instead, the obfuscation function, , is applied to produce an authentication token, , for every challenge bit-string, , where factors in the pairwise link between and . Thus, an adversary will record the exchanged as the PUF response and, consequently, will use these tokens as input to the machine learning model, with the aim of mapping the challenge bits to the corresponding token. The results of the modeling attack under FeRHA are depicted in Figure 7. We performed the modeling attack using the ML models applied earlier in Figure 6 to model the PUF with the application of FeRHA. As demonstrated by the results, an adversary cannot achieve an accuracy of more than 53% and 56% using CNN and XGBoost, respectively. Such an accuracy is equivalent to a random guess, given the binary nature of the PUF response. The effectiveness of FeRHA in preventing modeling attacks is clearly evident from the comparison of the results in Figure 7 with those in Figure 6.
- Multi-link attack: in this scenario, we assume that an adversary is actively eavesdropping on all links that the prover, , has with other nodes. The adversary’s primary objective is to collect as many CRPs of as possible, with the ultimate goal of modeling and impersonating . It is worth noting that, in contrast to the single-link scenario, the adversary will intercept the exchanged packets between and multiple verifiers, such as , , , and so on. Hence, the applied function, , will be varied among the intercepted packet (since ). Despite the adversary’s ability to capture more data, the semantic of such data is not coherent since the tokens are derived from the PUF response differently for the various verifiers. The results depicted in Figure 8 illustrate the outcomes of utilizing CNN and XGBoost models in conjunction with a 64-bit PUF integrated into . It is important to note that the CNN and XGBoost models have demonstrated the ability to model the 64-bit arbiter-PUF with an accuracy of over 90% (see Figure 6). However, Figure 8 indicates that neither CNN nor XGBoost was successful in defeating FeRHA. The results reflect the accuracy of the modeling attack when applying intercepted packets over connections containing varying numbers of verifiers. The results of such a modeling attack confidently indicate that the adversary cannot gain any advantages from eavesdropping on additional links, as the accuracy remains unchanged compared with that of a single link.
6.3. Formal Security Analysis
6.4. Fuzzy Extractor Performance
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Elijah, O.; Rahman, T.A.; Orikumhi, I.; Leow, C.Y.; Hindia, M.N. An overview of Internet of Things (IoT) and data analytics in agriculture: Benefits and challenges. IEEE Internet Things J. 2018, 5, 3758–3773. [Google Scholar] [CrossRef]
- Younis, M. Internet of everything and everybody: Architecture and service virtualization. Comput. Commun. 2018, 131, 66–72. [Google Scholar] [CrossRef]
- Halperin, D.; Heydt-Benjamin, T.S.; Ransford, B.; Clark, S.S.; Defend, B.; Morgan, W.; Fu, K.; Kohno, T.; Maisel, W.H. Pacemakers and implantable cardiac defibrillators: Software radio attacks and zero-power defenses. In Proceedings of the 2008 IEEE Symposium on Security and Privacy (sp 2008), Oakland, CA, USA, 18–22 May 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 129–142. [Google Scholar]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and security in internet of things and wearable devices. IEEE Trans.-Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Papp, D.; Ma, Z.; Buttyan, L. Embedded systems security: Threats, vulnerabilities, and attack taxonomy. In Proceedings of the 2015 13th Annual Conference on Privacy, Security and Trust (PST), Izmir, Turkey, 21–23 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 145–152. [Google Scholar]
- Al-Naji, F.H.; Zagrouba, R. A survey on continuous authentication methods in Internet of Things environment. Comput. Commun. 2020, 163, 109–133. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT security: Challenges and solution using machine learning, artificial intelligence and blockchain technology. Internet Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Williams, P.; Dutta, I.K.; Daoud, H.; Bayoumi, M. A survey on security in internet of things with a focus on the impact of emerging technologies. Internet Things 2022, 19, 100564. [Google Scholar] [CrossRef]
- Halak, B.; Zwolinski, M.; Mispan, M.S. Overview of PUF-based hardware security solutions for the internet of things. In Proceedings of the 2016 IEEE 59th International Midwest Symposium on Circuits and Systems (MWSCAS), Abu Dhabi, United Arab Emirates, 16 October–19 October 2016; pp. 1–4. [Google Scholar]
- McGrath, T.; Bagci, I.E.; Wang, Z.M.; Roedig, U.; Young, R.J. A puf taxonomy. Appl. Phys. Rev. 2019, 6, 011303. [Google Scholar] [CrossRef]
- Suh, G.E.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the 44th Annual Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Lounis, K.; Zulkernine, M. Lessons learned: Analysis of PUF-based authentication protocols for IoT. Digit. Threat. Res. Pract. 2023, 4, 1–33. [Google Scholar] [CrossRef]
- Alkanhal, M.; Younis, M. P-MAP: PUF-based Mutual Authentication Protocol. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 3424–3429. [Google Scholar]
- Rojas, P.; Alahmadi, S.; Bayoumi, M. Physical Layer Security for IoT Communications—A Survey. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021; pp. 95–100. [Google Scholar]
- Zhang, Z.; Guo, X.; Lin, Y. Trust Management Method of D2D Communication Based on RF Fingerprint Identification. IEEE Access 2018, 6, 66082–66087. [Google Scholar] [CrossRef]
- Xu, Q.; Zheng, R.; Saad, W.; Han, Z. Device Fingerprinting in Wireless Networks: Challenges and Opportunities. IEEE Commun. Surv. Tutor. 2016, 18, 94–104. [Google Scholar] [CrossRef]
- Ellis, K.; Serinken, N. Characteristics of radio transmitter fingerprints. Radio Sci. 2001, 36, 585–597. [Google Scholar] [CrossRef]
- Xie, F.; Wen, H.; Li, Y.; Chen, S.; Hu, L.; Chen, Y.; Song, H. Optimized coherent integration-based radio frequency fingerprinting in Internet of Things. IEEE Internet Things J. 2018, 5, 3967–3977. [Google Scholar] [CrossRef]
- Shao, Y.; Liu, J.; Zeng, Y.; Gong, Y. A Radio Frequency Fingerprinting Scheme Using Learnable Signal Representation. IEEE Commun. Lett. 2024, 28, 73–77. [Google Scholar] [CrossRef]
- Gu, H.; Su, L.; Zhang, W.; Ran, C. Attention is Needed for RF Fingerprinting. IEEE Access 2023, 11, 87316–87329. [Google Scholar] [CrossRef]
- Ashtari, A.; Shabani, A.; Alizadeh, B. A new RF-PUF based authentication of internet of things using random forest classification. In Proceedings of the 2019 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Mashhad, Iran, 28–29 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 21–26. [Google Scholar]
- Román-Castro, R.; López, J.; Gritzalis, S. Evolution and trends in IoT security. Computer 2018, 51, 16–25. [Google Scholar] [CrossRef]
- Mall, P.; Amin, R.; Das, A.K.; Leung, M.T.; Choo, K.K.R. PUF-based authentication and key agreement protocols for IoT, WSNs, and Smart Grids: A comprehensive survey. IEEE Internet Things J. 2022, 9, 8205–8228. [Google Scholar] [CrossRef]
- Alkanhal, M.; Alali, A.; Younis, M. A Distributed Lightweight PUF-Based Mutual Authentication Protocol for IoV. IoT 2024, 5, 1–19. [Google Scholar] [CrossRef]
- Yoon, S.; Kim, B.; Kang, Y.; Choi, D. Puf-based authentication scheme for iot devices. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 21–23 October 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1792–1794. [Google Scholar]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF based authentication and key exchange protocol for IoT without explicit CRPs in verifier database. IEEE Trans. Dependable Secur. Comput. 2018, 16, 424–437. [Google Scholar] [CrossRef]
- Yilmaz, Y.; Do, V.H.; Halak, B. ARMOR: An anti-counterfeit security Mechanism for lOw cost Radio frequency identification systems. IEEE Trans. Emerg. Top. Comput. 2020, 9, 2125–2138. [Google Scholar] [CrossRef]
- Qureshi, M.A.; Munir, A. PUF-IPA: A PUF-based identity preserving protocol for Internet of Things authentication. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–7. [Google Scholar]
- Patil, A.S.; Hamza, R.; Hassan, A.; Jiang, N.; Yan, H.; Li, J. Efficient privacy-preserving authentication protocol using PUFs with blockchain smart contracts. Comput. Secur. 2020, 97, 101958. [Google Scholar] [CrossRef]
- Fakroon, M.; Gebali, F.; Mamun, M. Multifactor authentication scheme using physically unclonable functions. Internet Things 2021, 13, 100343. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V. HARCI: A two-way authentication protocol for three entity healthcare IoT networks. IEEE J. Sel. Areas Commun. 2020, 39, 361–369. [Google Scholar] [CrossRef]
- Nimmy, K.; Sankaran, S.; Achuthan, K. A novel lightweight PUF based authentication protocol for IoT without explicit CRPs in verifier database. J. Ambient. Intell. Humaniz. Comput. 2023, 14, 6227–6242. [Google Scholar] [CrossRef]
- Majzoobi, M.; Rostami, M.; Koushanfar, F.; Wallach, D.S.; Devadas, S. Slender PUF protocol: A lightweight, robust, and secure authentication by substring matching. In Proceedings of the 2012 IEEE Symposium on Security and Privacy Workshops, San Francisco, CA, USA, 24–25 May 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 33–44. [Google Scholar]
- Farha, F.; Ning, H.; Ali, K.; Chen, L.; Nugent, C. SRAM-PUF-based entities authentication scheme for resource-constrained IoT devices. IEEE Internet Things J. 2020, 8, 5904–5913. [Google Scholar] [CrossRef]
- Nozaki, Y.; Yoshikawa, M. Secret sharing schemes based secure authentication for physical unclonable function. In Proceedings of the 2019 IEEE 4th International Conference on Computer and Communication Systems (ICCCS), Piscataway, NJ, USA, 23–25 February 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 445–449. [Google Scholar]
- Jiang, Q.; Zhang, X.; Zhang, N.; Tian, Y.; Ma, X.; Ma, J. Three-factor authentication protocol using physical unclonable function for IoV. Comput. Commun. 2021, 173, 45–55. [Google Scholar] [CrossRef]
- Mahalat, M.H.; Karmakar, D.; Mondal, A.; Sen, B. Puf based secure and lightweight authentication and key-sharing scheme for wireless sensor network. ACM J. Emerg. Technol. Comput. Syst. (JETC) 2021, 18, 1–23. [Google Scholar] [CrossRef]
- Nouichi, D.; Abdelsalam, M.; Nasir, Q.; Abbas, S. IoT Devices Security Using RF Fingerprinting. In Proceedings of the 2019 Advances in Science and Engineering Technology International Conferences (ASET), Dubai, United Arab Emirates, 26 March–10 April 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Zhang, J.; Shen, G.; Saad, W.; Chowdhury, K. Radio Frequency Fingerprint Identification for Device Authentication in the Internet of Things. IEEE Commun. Mag. 2023, 61, 110–115. [Google Scholar] [CrossRef]
- Tian, Q.; Lin, Y.; Guo, X.; Wen, J.; Fang, Y.; Rodriguez, J.; Mumtaz, S. New Security Mechanisms of High-Reliability IoT Communication Based on Radio Frequency Fingerprint. IEEE Internet Things J. 2019, 6, 7980–7987. [Google Scholar] [CrossRef]
- Peng, L.; Zhang, J.; Liu, M.; Hu, A. Deep Learning Based RF Fingerprint Identification Using Differential Constellation Trace Figure. IEEE Trans. Veh. Technol. 2020, 69, 1091–1095. [Google Scholar] [CrossRef]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT security through authentication of wireless nodes using in-situ machine learning. IEEE Internet Things J. 2018, 6, 388–398. [Google Scholar] [CrossRef]
- Bari, M.F.; Chatterjee, B.; Sivanesan, K.; Yang, L.L.; Sen, S. High accuracy RF-PUF for EM security through physical feature assistance using public Wi-Fi dataset. In Proceedings of the 2021 IEEE MTT-S International Microwave Symposium (IMS), Los Angeles, CA, USA, 18–27 June 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 108–111. [Google Scholar]
- Rührmair, U.; Holcomb, D.E. PUFs at a glance. In Proceedings of the 2014 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 24–28 March 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–6. [Google Scholar]
- Maes, R.; Verbauwhede, I. Physically unclonable functions: A study on the state of the art and future research directions. In Towards Hardware-Intrinsic Security: Foundations and Practice; Springer: Berlin/Heidelberg, Germany, 2010; pp. 3–37. [Google Scholar] [CrossRef]
- Guo, Y.; Dee, T.; Tyagi, A. Multi-block APUF with 2-Level Voltage Supply. In Proceedings of the 2018 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Hong Kong, China, 8–11 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 327–332. [Google Scholar]
- Hemavathy, S.; Bhaaskaran, V.K. Arbiter PUF-A Review of Design, Composition, and Security Aspects. IEEE Access 2023, 11, 33979–34004. [Google Scholar] [CrossRef]
- Rehman, S.U.; Sowerby, K.W.; Alam, S.; Ardekani, I. Radio frequency fingerprinting and its challenges. In Proceedings of the 2014 IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 496–497. [Google Scholar]
- Parmaksız, H.; Karakuzu, C. A review of recent developments on secure authentication using RF fingerprints techniques. Sak. Univ. J. Comput. Inf. Sci. 2022, 5, 278–303. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the Advances in Cryptology-EUROCRYPT 2004: International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Proceedings 23. Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Wen, Y.; Lao, Y. Efficient fuzzy extractor implementations for PUF based authentication. In Proceedings of the 2017 12th International Conference on Malicious and Unwanted Software (MALWARE), Nancy, France, 19–20 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 119–125. [Google Scholar]
- Liu, W.; Zhang, Z.; Li, M.; Liu, Z. A trustworthy key generation prototype based on DDR3 PUF for wireless sensor networks. Sensors 2014, 14, 11542–11556. [Google Scholar] [CrossRef]
- Huffman, W.C.; Pless, V. Fundamentals of Error-Correcting Codes; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar]
- Zhu, Z.; Leung, H.; Huang, X. Challenges in reconfigurable radio transceivers and application of nonlinear signal processing for RF impairment mitigation. IEEE Circuits Syst. Mag. 2013, 13, 44–65. [Google Scholar]
- Zhang, J.; Woods, R.; Sandell, M.; Valkama, M.; Marshall, A.; Cavallaro, J. Radio frequency fingerprint identification for narrowband systems, modelling and classification. IEEE Trans. Inf. Foren. Secur. 2021, 16, 3974–3987. [Google Scholar] [CrossRef]
- Kang, H.; Hori, Y.; Katashita, T.; Hagiwara, M.; Iwamura, K. Cryptographie key generation from PUF data using efficient fuzzy extractors. In Proceedings of the 16th International Conference on Advanced Communication Technology, PyeongChang, Republic of Korea, 16–19 February 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 23–26. [Google Scholar]
- Böhm, C.; Hofer, M. Physical Unclonable Functions in Theory and Practice; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Herder, C.; Ren, L.; Van Dijk, M.; Yu, M.D.; Devadas, S. Trapdoor computational fuzzy extractors and stateless cryptographically-secure physical unclonable functions. IEEE Trans. Dependable Secur. Comput. 2016, 14, 65–82. [Google Scholar] [CrossRef]
- Teoh, A.B.J.; Kim, J. Error correction codes for biometric cryptosystem: An overview. Inf. Commun. Mag. 2015, 32, 39–49. [Google Scholar]
- Rührmair, U.; Sölter, J. PUF modeling attacks: An introduction and overview. In Proceedings of the 2014 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 24–28 March 2014; pp. 1–6. [Google Scholar]
- Wallrabenstein, J.R. Practical and secure IoT device authentication using physical unclonable functions. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and cloud (FiCloud), Vienna, Austria, 22–24 August 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 99–106. [Google Scholar]
- Sankhe, K.; Belgiovine, M.; Zhou, F.; Riyaz, S.; Ioannidis, S.; Chowdhury, K. ORACLE: Optimized Radio Classification through Convolutional neuraL Networks. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 370–378. [Google Scholar]
- Santikellur, P.; Bhattacharyay, A.; Chakraborty, R.S. Deep learning based model building attacks on arbiter PUF compositions. Cryptol. Eprint Arch. 2019. [Google Scholar]
- Kingma, D.P.; Ba, J. Adam: A method for stochastic optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]
- Armando, A.; Basin, D.; Cuellar, J.; Rusinowitch, M.; Viganò, L. Avispa: Automated Validation of Internet Security Protocols and Applications. ERCIM News, January 2006; p. 64. [Google Scholar]








| Index | N | L | t |
|---|---|---|---|
| 1 | 63 | 57 | 1 |
| 2 | 63 | 51 | 2 |
| 3 | 63 | 45 | 3 |
| 4 | 63 | 39 | 4 |
| 5 | 63 | 36 | 5 |
| 6 | 63 | 30 | 6 |
| 7 | 63 | 24 | 7 |
| 8 | 63 | 18 | 8 |
| 9 | 63 | 16 | 9 |
| 10 | 63 | 10 | 10 |
| 11 | 63 | 7 | 11 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alkanhal, M.; Younis, M.; Alali, A.; Mehjabin, S.S. FeRHA: Fuzzy-Extractor-Based RF and Hardware Fingerprinting Two-Factor Authentication. Appl. Sci. 2024, 14, 3363. https://doi.org/10.3390/app14083363
Alkanhal M, Younis M, Alali A, Mehjabin SS. FeRHA: Fuzzy-Extractor-Based RF and Hardware Fingerprinting Two-Factor Authentication. Applied Sciences. 2024; 14(8):3363. https://doi.org/10.3390/app14083363
Chicago/Turabian StyleAlkanhal, Mona, Mohamed Younis, Abdulaziz Alali, and Suhee Sanjana Mehjabin. 2024. "FeRHA: Fuzzy-Extractor-Based RF and Hardware Fingerprinting Two-Factor Authentication" Applied Sciences 14, no. 8: 3363. https://doi.org/10.3390/app14083363
APA StyleAlkanhal, M., Younis, M., Alali, A., & Mehjabin, S. S. (2024). FeRHA: Fuzzy-Extractor-Based RF and Hardware Fingerprinting Two-Factor Authentication. Applied Sciences, 14(8), 3363. https://doi.org/10.3390/app14083363








