Multiple-Valued Logic, Vocabulary Structure, and Linked List for Data Verification in Dialog Communications of Agents
Abstract
Featured Application
Abstract
1. Introduction
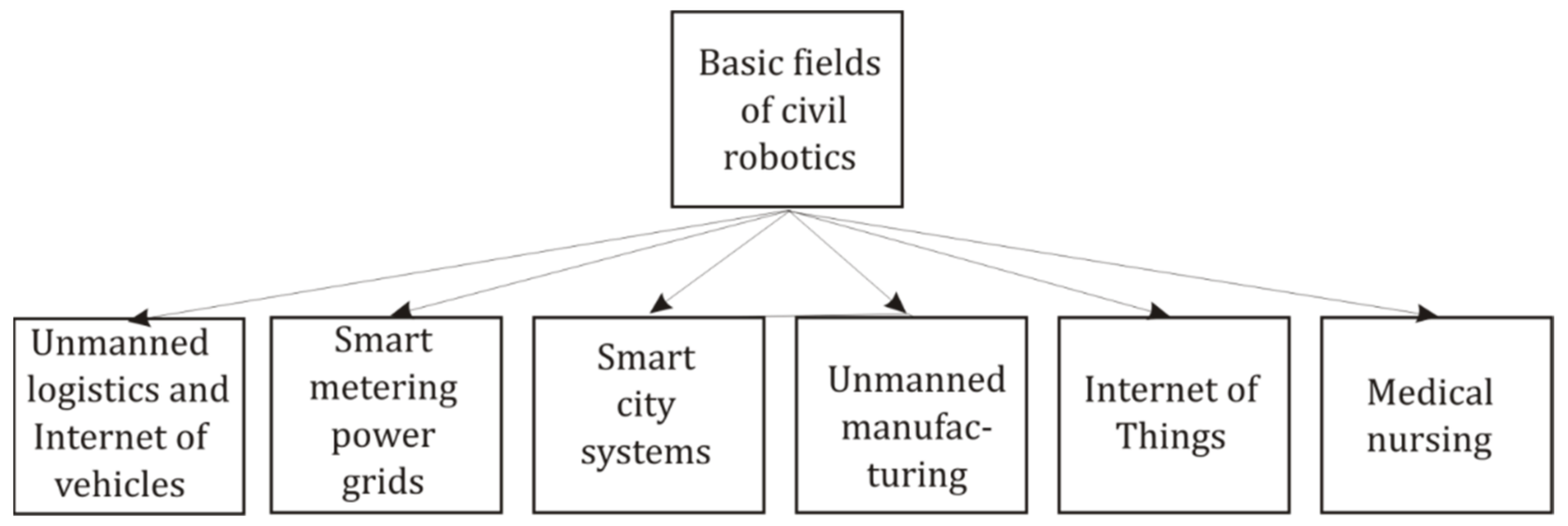
1.1. Verification Tasks and Methods in Modern Robotics
- The use of too general estimation parameters and the absence of methods to take into account the specifics of the domain knowledge,
- The absence of realistic schemes to evaluate the applicability of the chosen criteria,
- The lack of specialized languages to model domain knowledge,
- The insufficient development of methods for runtime verification.
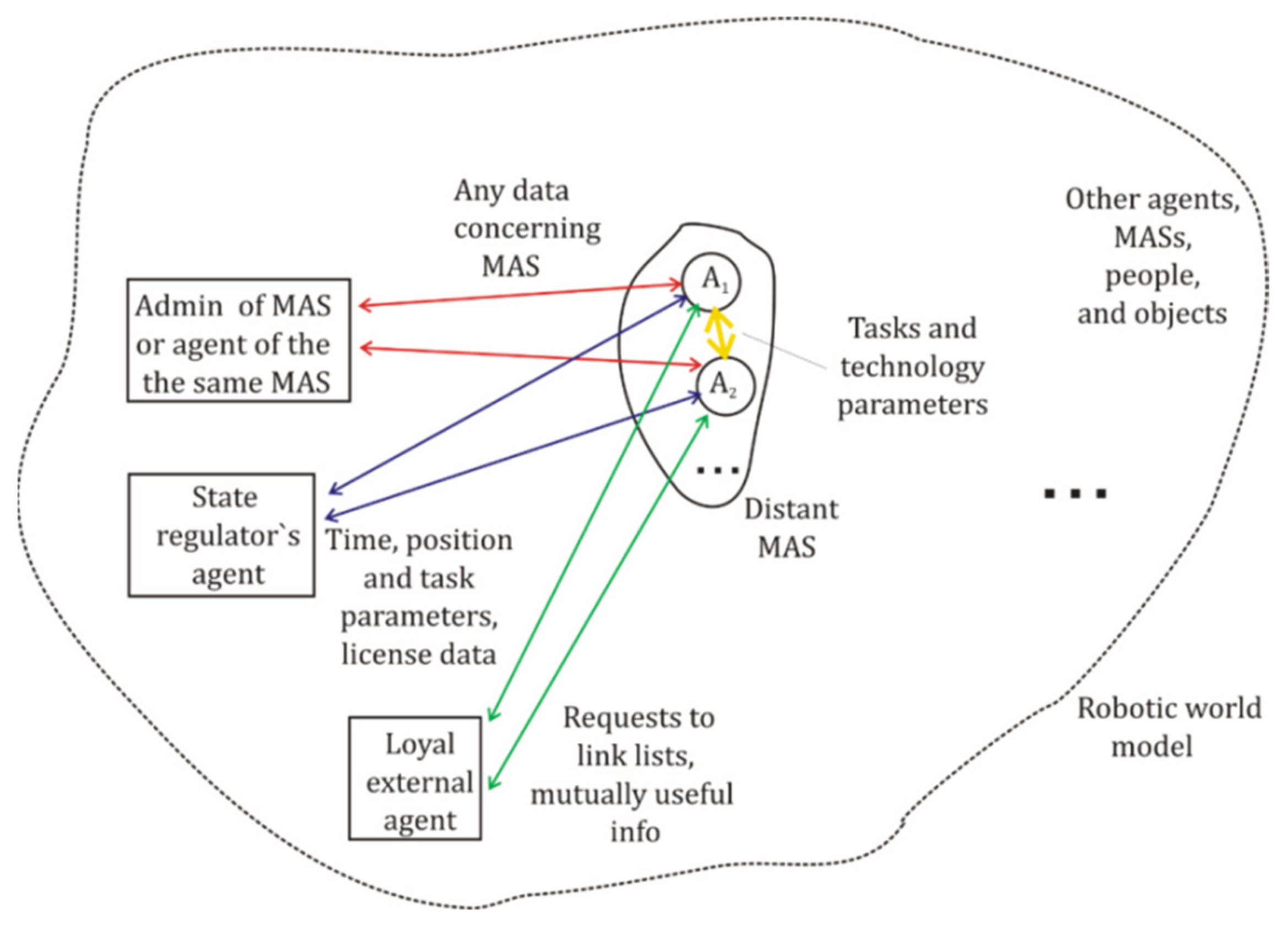
1.2. Dialog Data Exchange in a Collective of Network Agents
1.3. The Methodology and the Possibilities of Multiple-Valued Logic Modeling
1.4. The Aim of the Paper
- ✓
- The formal model for verification in the robotic system should have high capacity and describe in detail the properties of a large-scale collective of agents;
- ✓
- Verification procedures should be integrated into the holistic model of the scene of action, describing robots, tasks, people, and various objects;
- ✓
- The interaction of agents is to provide dialog mode of communications, where formal language phrases can be continued and should use content-based addressing, excluding disclosing of physical addresses in data storages;
- ✓
- The model of system description should be unified for various platforms, including simple 8-bit ones;
- ✓
- Reference data for verification procedures are to be written to protected local data storages, using LL scheme and unpredictably located in collaborating devices;
- ✓
- As AGA multiple-valued logic calculus provides a substantial set of tools for data coding in large-scale systems of agents, it should be used in verification procedures.
- To design new AI procedures for a robotic agent, based on AGA;
- To create the holistic and the detailed formal logic structure of parameters, terminology, and coded logic variables for further modeling of autonomous agents;
- To propose AGA-based communication language, convenient for extended dialogs of agents in scalable large-scale robotic system;
- To adapt the LL scheme to minimalistic local data storages in collaborating network agents and to provide integrity checks of transferred messages;
- To provide the clear control of verification schemes within the heterogeneous logic architecture of agent.
- ▪
- High-capacity logic modeling method, based on AGA;
- ▪
- The ordered structure of coded vocabularies for the comprehensive description of terminology, objects, and events in the multi-parametric logic model, operating with large space and time bands;
- ▪
- The formal AGA language for robot’s communications and phrase design;
- ▪
- The adaptation of AGA-based LL for verification in low-throughput platforms.
2. Method: Basic Multiple-Valued Logic Model
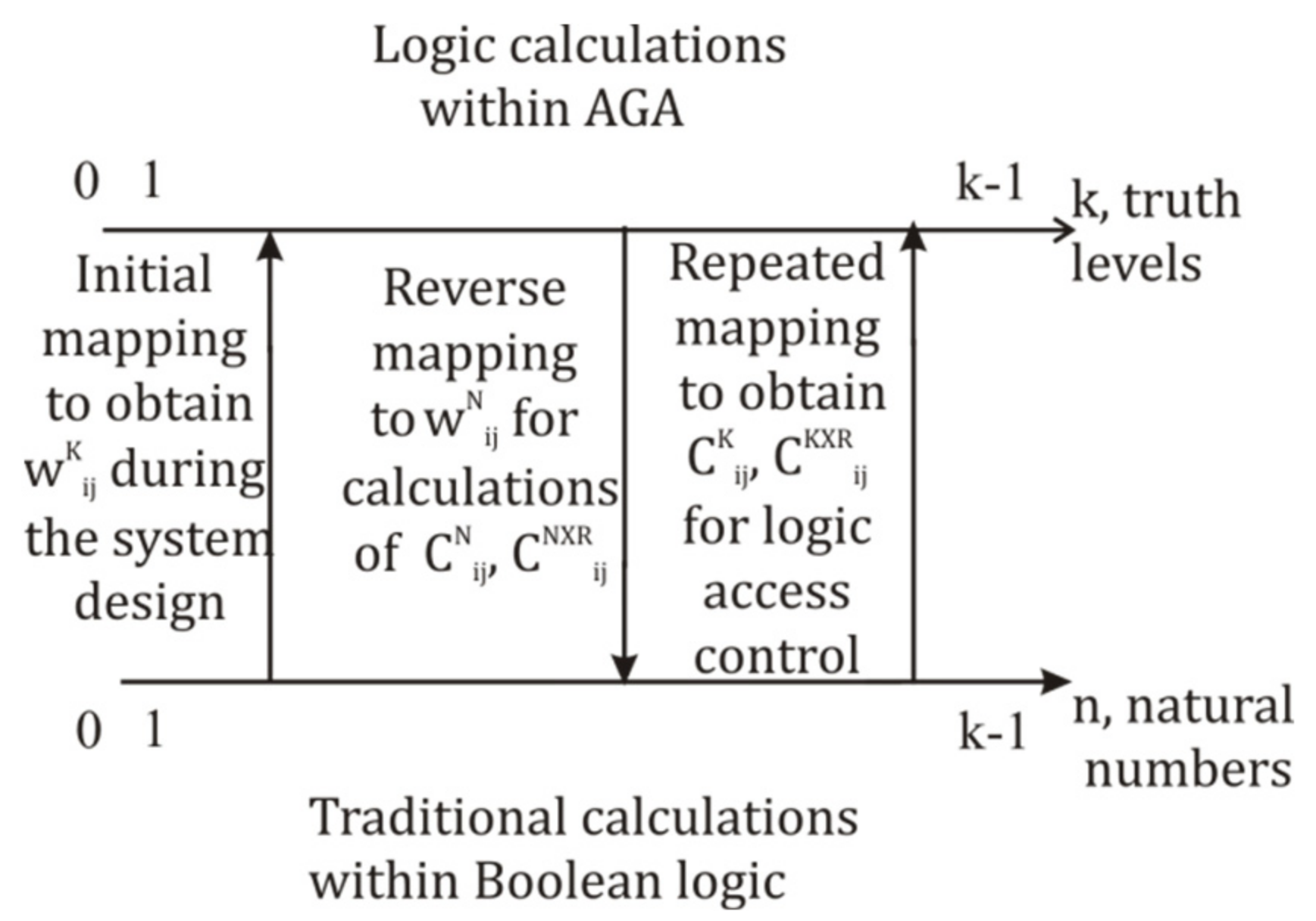
2.1. Multiple-Valued Allen–Givone Algebra
- Logic constants ;
- Operators Min() or , marked by * selects the minimal truth level in the pair and ;
- Operators Max() or , marked by +, selects the maximal truth level in the pair and ;
- Operators Literal , given by Eq. (2):where for any X(a, b), always and
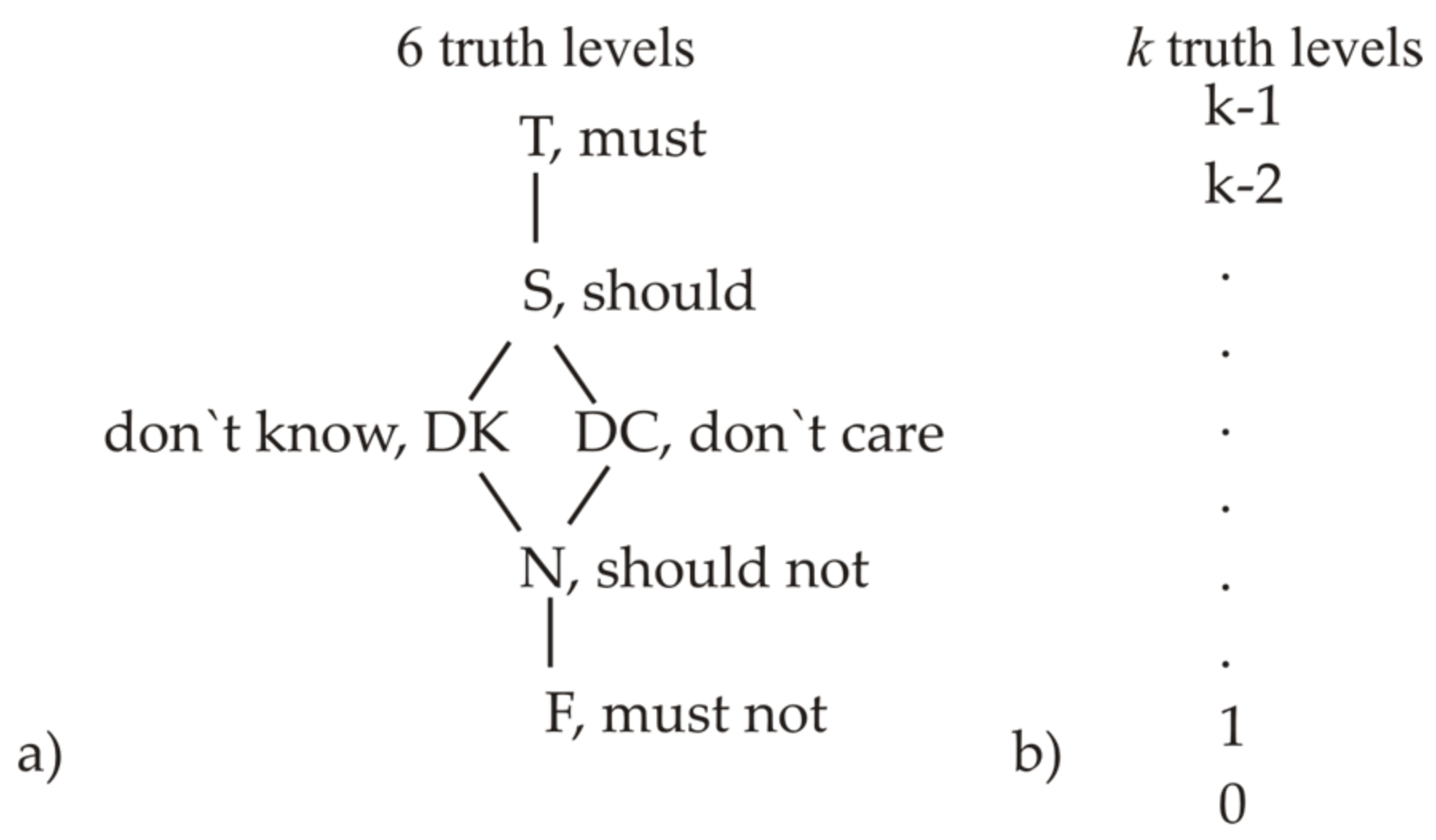
2.2. Possible Discrete Scales for Mapping of Truth Levels
2.3. Formation of AGA Functions
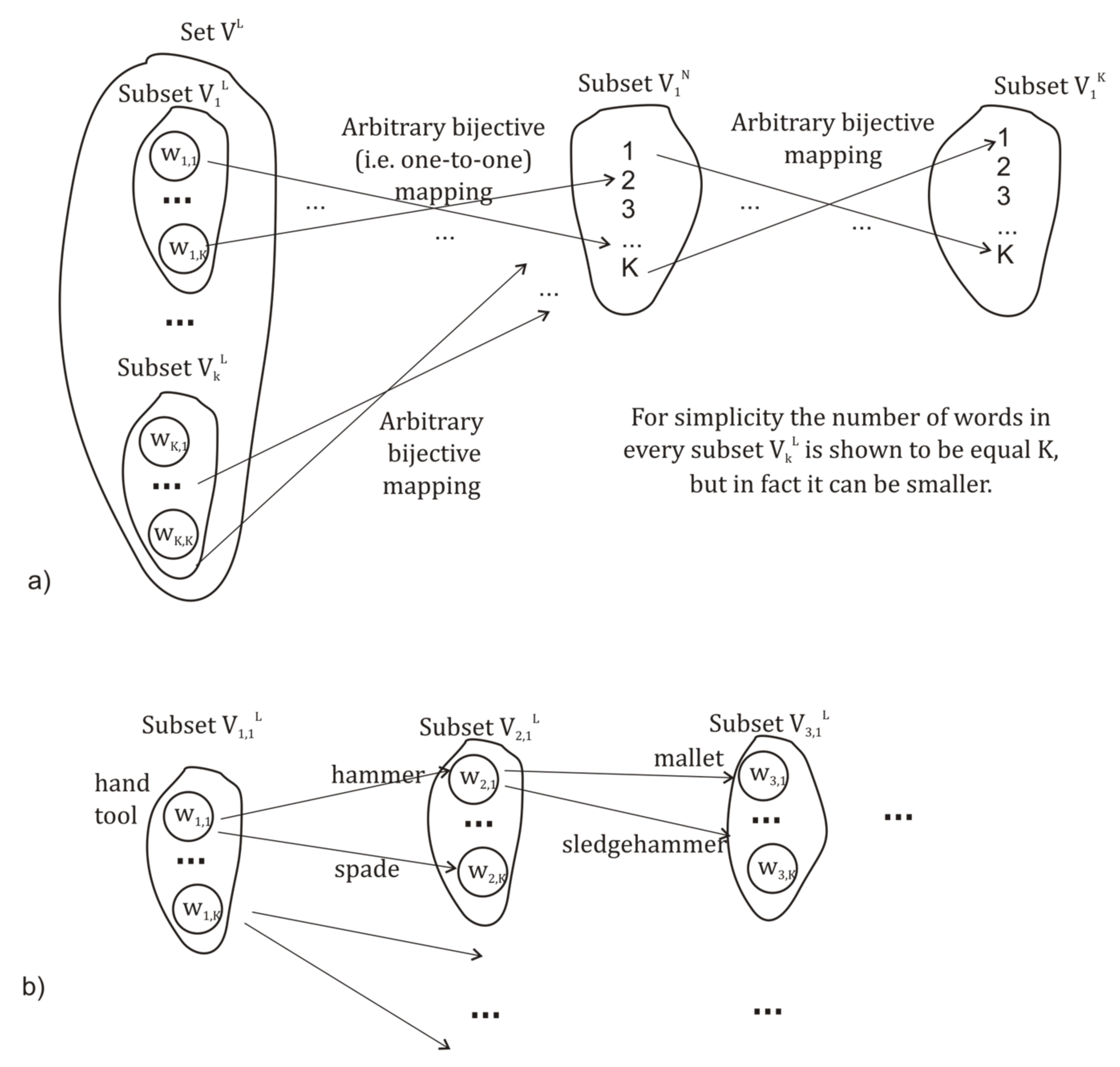
2.4. Correlated Variables for the Description of Large-Scale Space and Time Bands
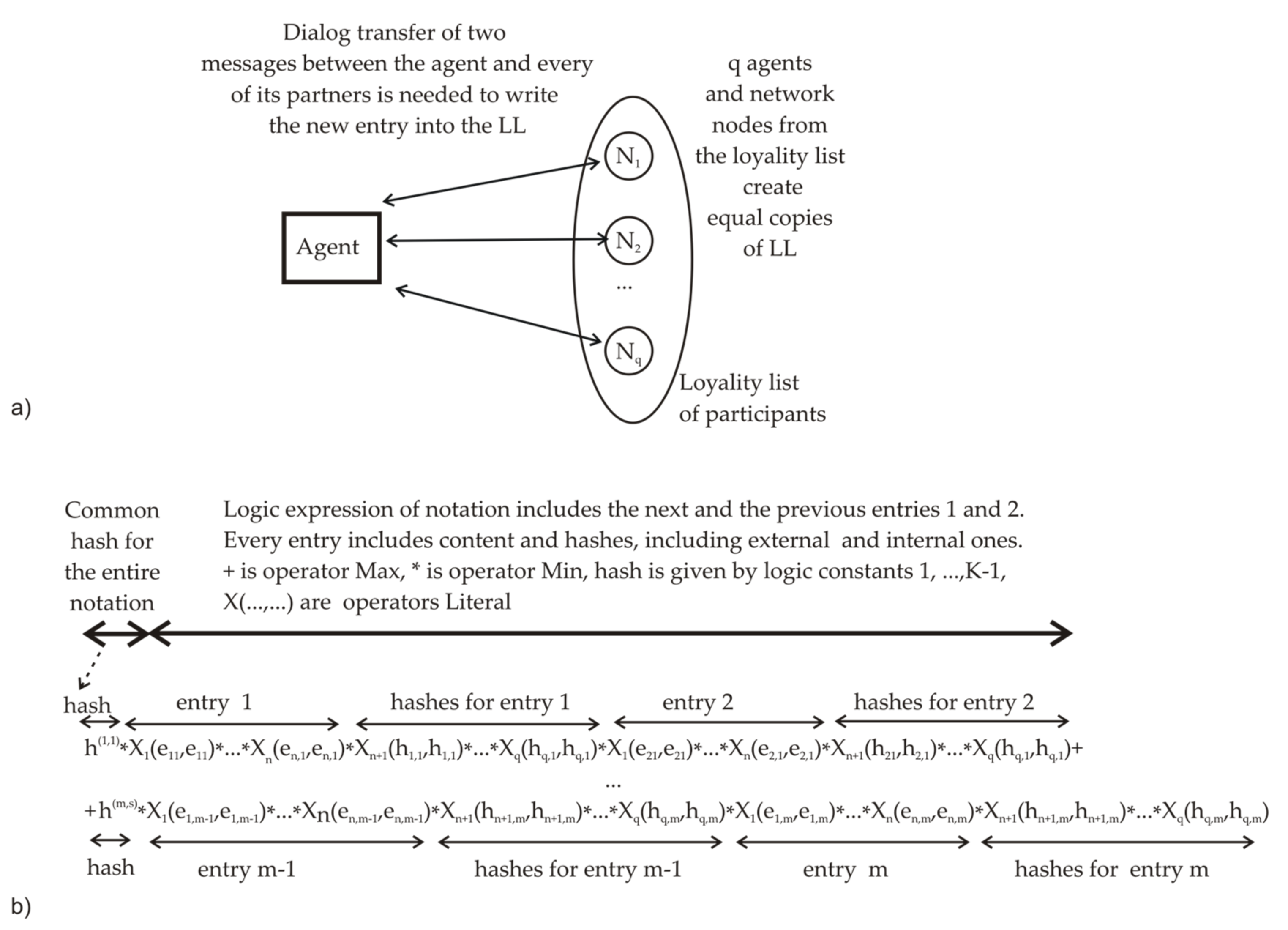
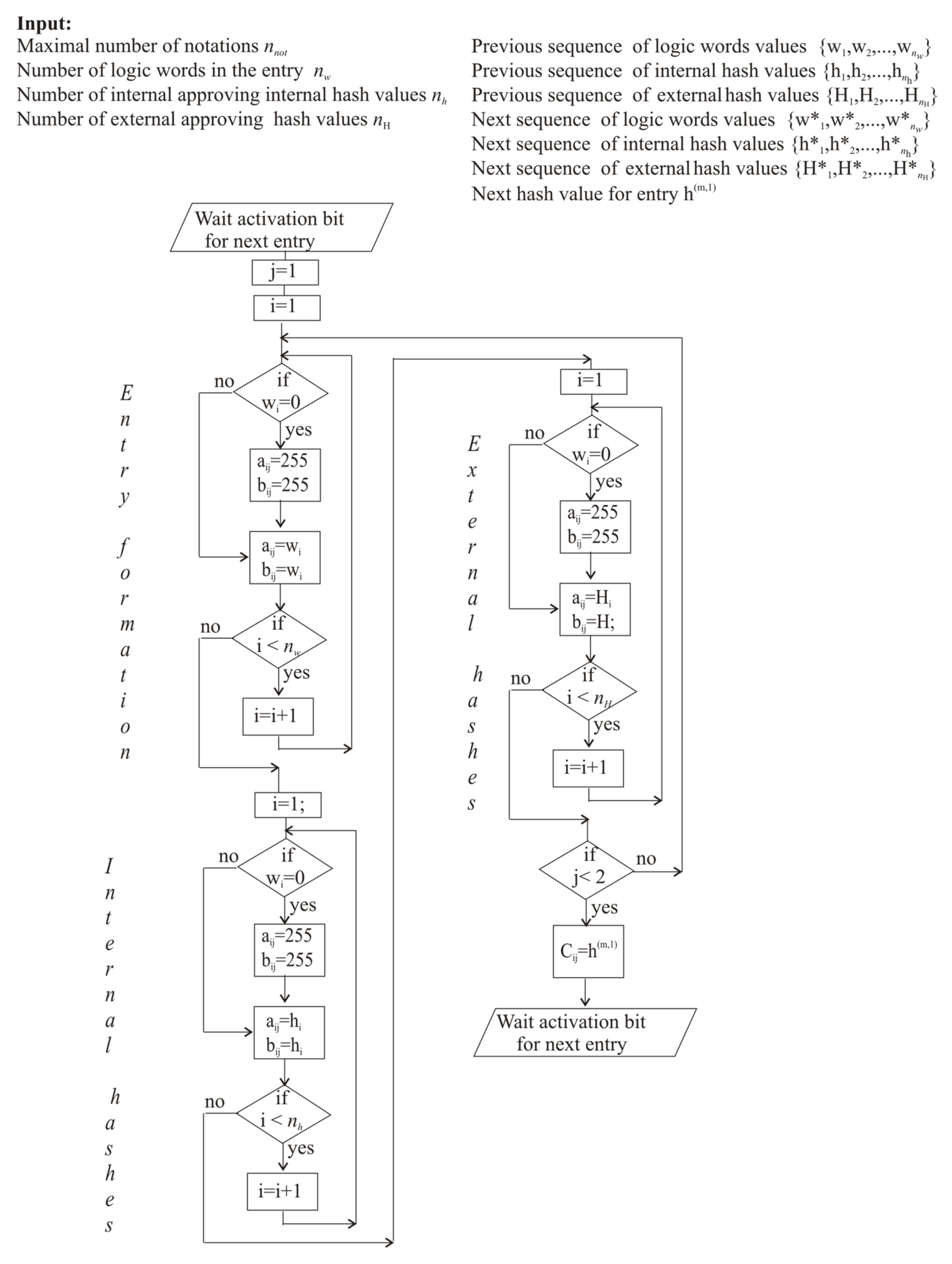
2.5. AGA-Based Versions of the Linked List Scheme for Logic Data Protection
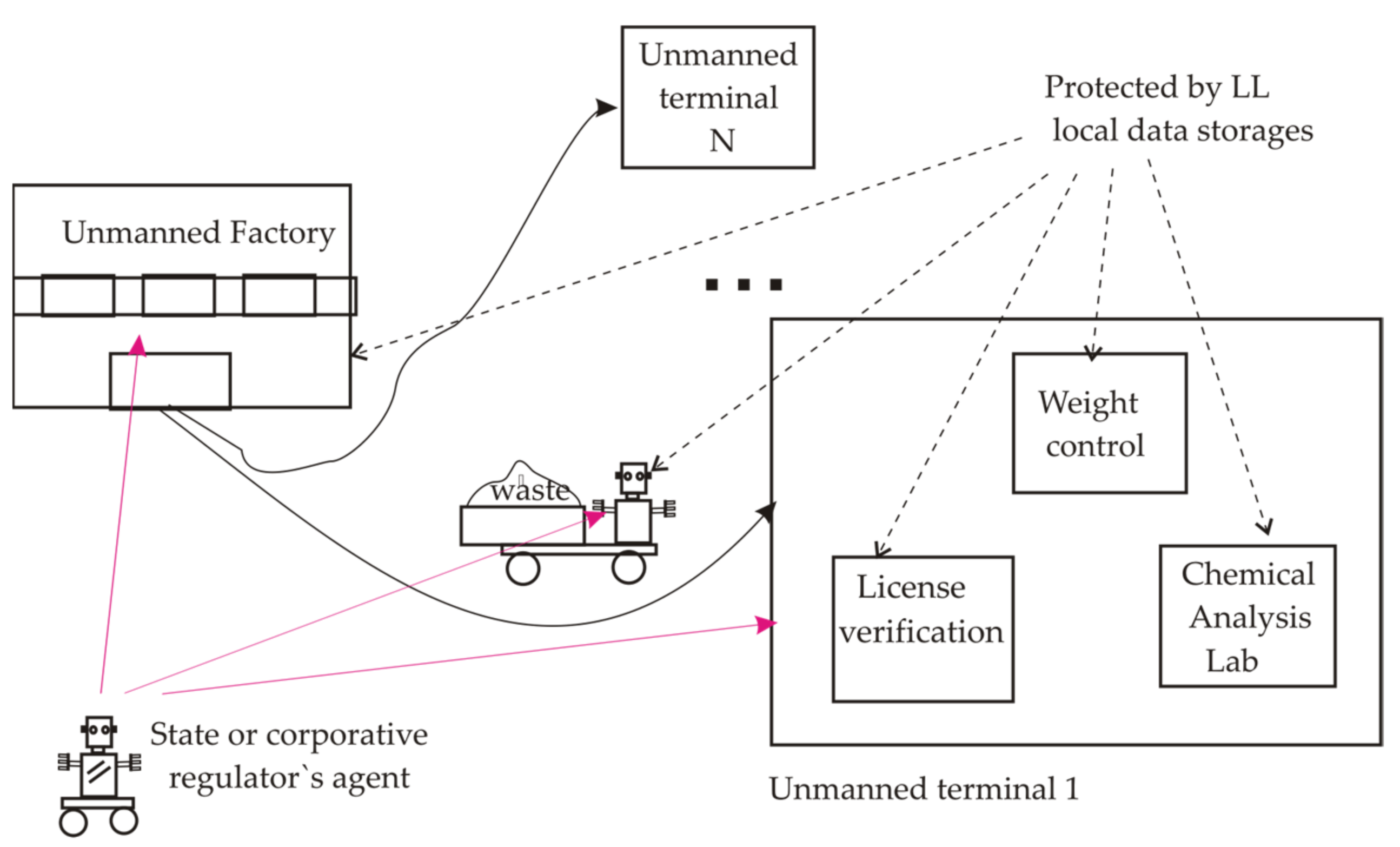
- Approval of requested numbers of licenses and permissions,
- Following restrictions declared for cargo parameters and route passing,
- Monitoring of visits only to legal zones of the geographical map,
- Loading/uploading at legal terminals,
- Compliance with the standards of ecology and transport.
3. Results: AGA Logic Variables for Scene Description and Dialog Communications
3.1. Representation of the Scene of Action by Natural Language, Numerical Codes, and Truth Levels
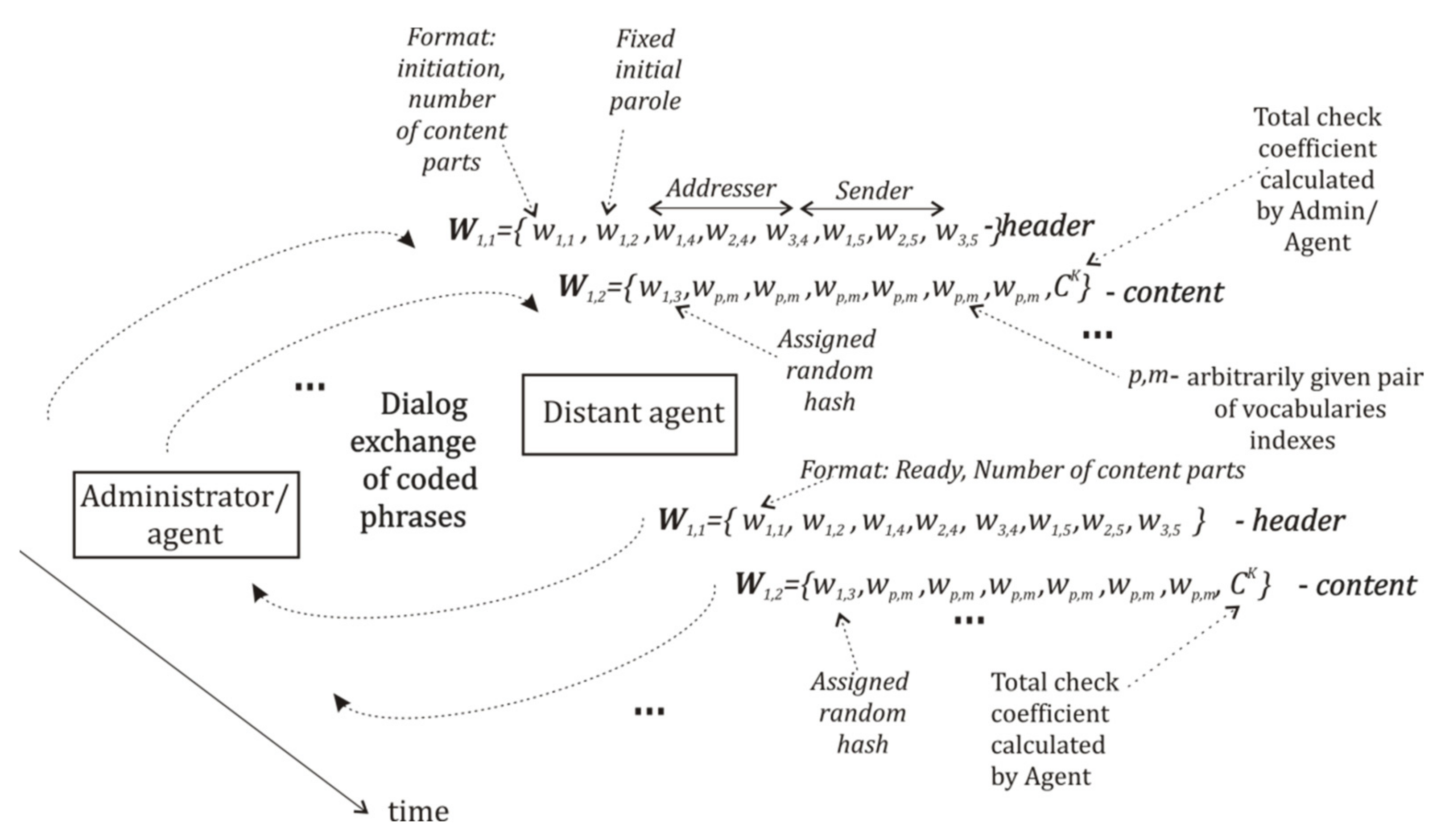
3.2. Communication Phrase
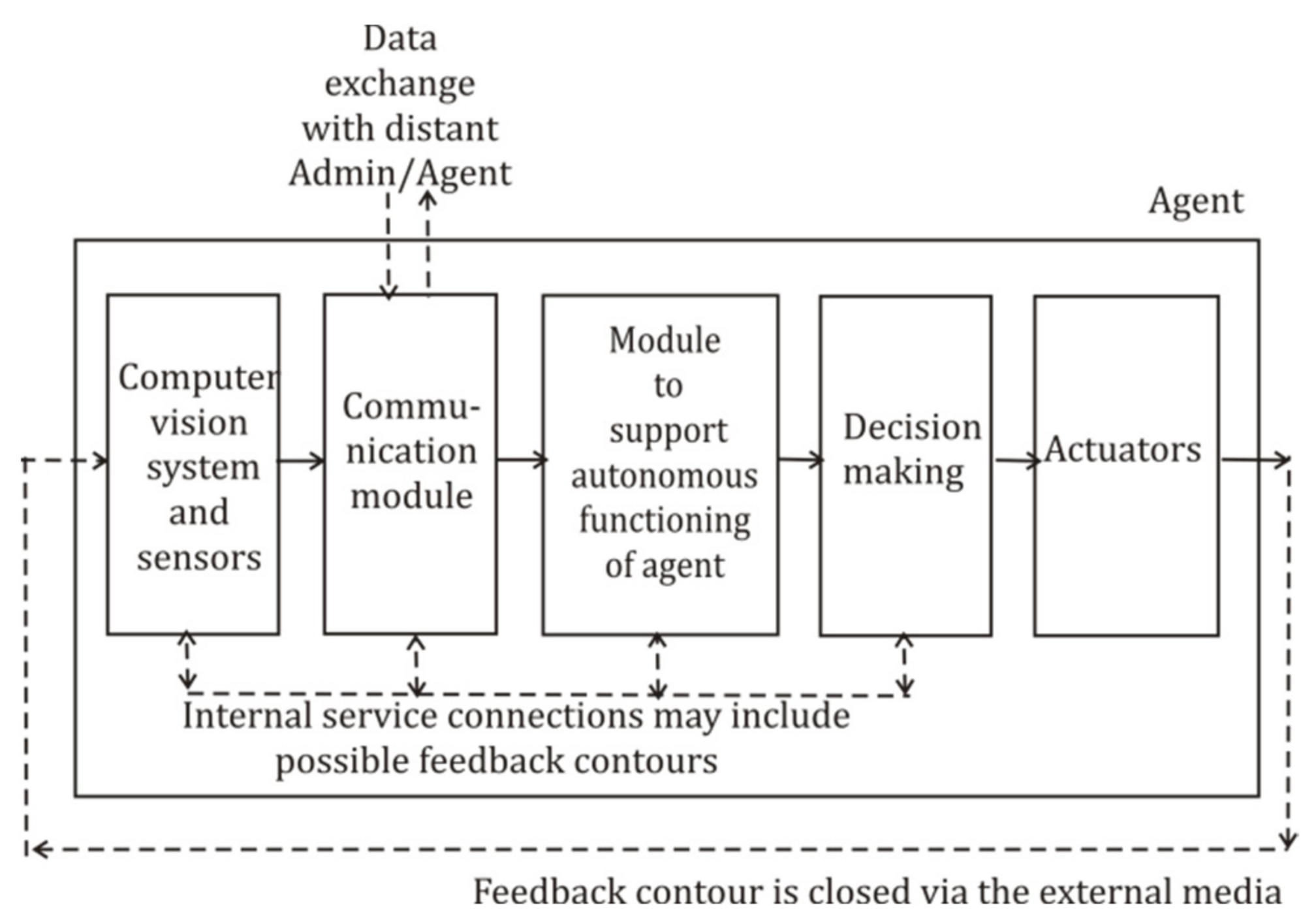
3.3. Communication Module and the Dialog Protocol
- Sensors and computer vision system, which are to detect objects and dangers, providing the agent’s reactivity to the external world and space positioning;
- Module for the procession of messages, coming from radiofrequency, acoustic, and optics data lines, complemented by devices for secret coding and data verification;
- Homeostasis supporting system [87], providing autonomous operation of devices for energy supply, time clocking, sensors operability control, and space positioning;
- Modules for decision making and work planning;
- Set of actuators.
- To check the received initial parole in the list of fixed and additionally generated ones;
- To extract potentially danger data to be immediately sent to homeostasis module,
- To check the presence of the declared sender name and its authority in the AGA function, describing allowed classes of actions for the contacting agent,
- To verify the presence of all declared content parts in the received phrase;
- To compare the requested by external agent set of vocabularies with the allowed one;
- Either to begin the new dialog or to continue the already opened one; if necessary, to send denial reply;
- To send content of the received phrase to the decision-maker and to wait for its reply;
- To work out the reply phrase and to assign a one-time random hash value to it, using the reserve list of hash values, preliminarily filled in by quasi-random numbers;
- To analyze the reason for errors in the dialog and to choose adequate actions.
| Algorithm 1. Phrase procession for dialogs administrator–agent and agent–agent from the same MAS. Total check coefficients, , are calculated by arithmetic summation or binary XOR operations performed for mapped truth levels. Phrase can initiate the new dialog or continue the already opened one. | |||||||||||||||||||||||
| Input: | Number of truth levels in AGA; | ||||||||||||||||||||||
| Vocabularies in truth levels representation; | |||||||||||||||||||||||
| Addresser code, given by the triple of coded truth levels in chain vocabularies; | |||||||||||||||||||||||
| Sender codes triple; | |||||||||||||||||||||||
| ( | Set of triples, representing content data given by decision-maker for transfer to addresser; and arbitrarily given enlarging values, p ≤ r, q ≤ s; | ||||||||||||||||||||||
| Welcome code {“Hi”} to begin new session; | |||||||||||||||||||||||
| Fixed parole for initial access to addresser; | |||||||||||||||||||||||
| Assigned hash value; | |||||||||||||||||||||||
| List of allowed contacters; | |||||||||||||||||||||||
| List of addressers with opened sessions; | |||||||||||||||||||||||
| List of accumulated quasi-random keys, , taken from QRNG; | |||||||||||||||||||||||
| N | Subject | Operation | Commentary | ||||||||||||||||||||
| 1 | Sender ); | Checks () , and if yes, go to step 2; otherwise, it goes to the procedure for unknown contacters | ; if list of allowed contacts contains addresser’s name triple: | ||||||||||||||||||||
| 2 | Assigns i = 1, for empty phrase header template { ; | ; begin new phrase and header | |||||||||||||||||||||
| 3 | Assigns j = 1 | ; number of content part | |||||||||||||||||||||
| 4 | Assigns format to phrase header part { | ; initiation of dialog | |||||||||||||||||||||
| 5 | Assigns fixed parole of Addresser to phrase header { | ; takes fixed from | |||||||||||||||||||||
| 6 | Assigns addresser’s triple name to the header { | ; insert triple | |||||||||||||||||||||
| 7 | Assigns own sender’s triple name ) to the header { | ; insert triple | |||||||||||||||||||||
| 8 | Maps truth levels onto natural numbers scale and calculates total check coefficient, , for the header ; | ||||||||||||||||||||||
| 9 | Calculates number of content parts: ; are taken from the received content data sequence {; | ; number of content parts is determined by 6 free fields in any of them | |||||||||||||||||||||
| 10 | Assigns v = p, m = q | ; set counters of chain vocabularies | |||||||||||||||||||||
| 11 | Assigns | ; begin content parts and set their counter | |||||||||||||||||||||
| 12 | Assigns g = 6 | ; counter of free fields in a content part | |||||||||||||||||||||
| 13 | Writes next hash from the list to the first field of phrase content part | ; begin new content part | |||||||||||||||||||||
| 14 | Goes to step 18 | ; next content part | |||||||||||||||||||||
| 15 | Checks if and if yes, it goes to step 23; otherwise, it goes to step 18. | ||||||||||||||||||||||
| 16 | Checks if and if yes, it goes to step 26; otherwise, it goes to step 18. | ;end of phrase formation | |||||||||||||||||||||
| 17 | Checks if and if yes, it goes to step 12; otherwise, it goes to step 25. | ||||||||||||||||||||||
| 18 | Write into the next vacancy in the content part, | ||||||||||||||||||||||
| 19 | g = g – 1 | ; check for free fields | |||||||||||||||||||||
| 20 | Checks if and if yes, it goes to step 25; otherwise, it goes to step 21. | ||||||||||||||||||||||
| 21 | |||||||||||||||||||||||
| 22 | Goes to step 15 | ||||||||||||||||||||||
| 23 | v = v + 1 | ; process next v | |||||||||||||||||||||
| 24 | Goes to step 16 | ||||||||||||||||||||||
| 25 | Maps truth levels onto the natural numbers scale and calculates total coefficient, , of the content part | ||||||||||||||||||||||
| 26 | Calculates total summation | ||||||||||||||||||||||
| 27 | Writes into the current content part of phrase | ||||||||||||||||||||||
| 28 | Sends the header and content parts to addresser | ||||||||||||||||||||||
| 29 | i = i + 1 | ; counter of phrases for continued dialog | |||||||||||||||||||||
| 30 | Waits reply from addresser | ||||||||||||||||||||||
| 31 | Addresser | Writes message parts in the buffer: … | ; indexes indicate arbitrarily given words | ||||||||||||||||||||
| 32 | Reads word in the Format field of the phrase header | ||||||||||||||||||||||
| 33 | Assigns the number of content part | ||||||||||||||||||||||
| 34 | Checks if list of opened sessions contains addresser’s name () declared in the header : Checks if and if yes, it goes to step 38; otherwise, it goes to step 35. | ||||||||||||||||||||||
| 35 | Checks if list of allowed contacters contains addresser’s name ): Checks if and if yes, it goes to step 37; otherwise, it goes to step 36. | ||||||||||||||||||||||
| 36 | Send denial of service message | ||||||||||||||||||||||
| 37 | Maps truth levels onto natural-number scale and calculate total coefficient for the header ; | ; check received external coefficients | |||||||||||||||||||||
| 38 | Maps truth levels onto natural-number scale and calculate total coefficient for content parts | ||||||||||||||||||||||
| 39 | Compares the received and the declared values: Checks if ; if yes, goes to step 40. Otherwise, it goes to step 36. | ||||||||||||||||||||||
| 40 | Sends received phrase content to decision-maker | ; excluding hashes and check coefficients | |||||||||||||||||||||
| 41 | Waits for reply from decision-maker | ||||||||||||||||||||||
| 42 | Receives reply ( from decision-maker | ; for the sake of simplicity, indexes are the same as in step 32 | |||||||||||||||||||||
| 43 | Assigns next quasi-random hash from the list to | ||||||||||||||||||||||
| 44 | Assigns i = 1 for empty phrase template { | ; form reply phrase | |||||||||||||||||||||
| 45 | Assigns j = 1 | ||||||||||||||||||||||
| 46 | Assigns Format “Received” to phrase header { | ; format differs from request | |||||||||||||||||||||
| 47 | Assigns fixed parole, , of sender to phrase header { | ; takes fixed from | |||||||||||||||||||||
| 48 | Assigns sender’s triple to phrase header part { | ||||||||||||||||||||||
| 49 | Assigns own code ) to phrase header part { | ||||||||||||||||||||||
| 50 | Assigns j = j + 1 | ||||||||||||||||||||||
| 51 | Maps truth levels onto natural number scale and calculates total check coefficient, , for the header, ; | ||||||||||||||||||||||
| 52 | Calculates number of content parts: ; are taken from the received content data sequence {; | ; number of content parts is determined by 6 free fields in a content part | |||||||||||||||||||||
| 53 | Assigns v = p, m = q | ; set counters of chain vocabularies | |||||||||||||||||||||
| 54 | Assigns | ; begin content parts and set their counter | |||||||||||||||||||||
| 55 | Assigns g = 6 | ; counter of free fields in a content part | |||||||||||||||||||||
| 56 | Writes next hash from the list to the first field of phrase content part | ; begin new content part | |||||||||||||||||||||
| 57 | Goes to step 61 | ; begin next content part | |||||||||||||||||||||
| 58 | Checks if , and if yes, it goes to step 66. Otherwise, it goes to step 61. | ; check counter | |||||||||||||||||||||
| 59 | Checks if , and if yes, it goes to step 60. Otherwise, goes to step 61. | ; end of phrase formation | |||||||||||||||||||||
| 60 | Checks if and if yes, it goes to step 55. Otherwise, it goes to step 68. | ; check counter | |||||||||||||||||||||
| 61 | Writes set of into the next vacancy in the content part | ||||||||||||||||||||||
| 62 | Assigns g = g − 1 | ; free fields control | |||||||||||||||||||||
| 63 | Checks if and if yes, it goes to step 68; Otherwise, it goes to step 64. | ||||||||||||||||||||||
| 64 | Assigns | ||||||||||||||||||||||
| 65 | Goes to step 58 | ||||||||||||||||||||||
| 66 | Assigns v = v + 1 | ; process next v | |||||||||||||||||||||
| 67 | Goes to step 59 | ||||||||||||||||||||||
| 68 | Maps truth levels onto natural numbers scale and calculate total coefficient of content part | ||||||||||||||||||||||
| 69 | Calculate total summation | ||||||||||||||||||||||
| 70 | Writes into the current content part of phrase | ||||||||||||||||||||||
| 71 | Replies to sender and transfer the header and content part | ||||||||||||||||||||||
| 72 | i = i + 1 | ||||||||||||||||||||||
| 73 | Waits for the next dialog phrase | ||||||||||||||||||||||
| Output: → | Formation and transfer of the request to addresser, and procession of reply to sender, saving total check coefficients in memory for the continuation of the dialog. | ||||||||||||||||||||||
| Algorithm 2. The procedure to find correct content part, corresponding to the given header, based on check coefficients. | |||||||||||
| Input: | ,,,,,}, ,,,,,}, ……….. (up to 30 parts in the buffer) | ← Header ← Content parts | |||||||||
| Step | Procedure | Example from Table 6 | |||||||||
| 1. | Find header part of phrase in the buffer memory | - | |||||||||
| 2. | Calculate with 8-bit overflow for the header | 138 (<255) | |||||||||
| 3. | Find nearest content part | - | |||||||||
| 4. | Calculate with 8-bit overflow for the content part | 209 + 196 + 3 + 12 + 6 + 221 + 147 = 794 (overflow: >255) = = 794 − 3 × 255 = 29; | |||||||||
| 5. | Calculate with 80bit overflow:+ | 138 + 29 = 167 (<255) | |||||||||
| 6. | Compare, if the calculated result is equal to the declared one in the last field of the content part: +=+; If yes, then write header and content part in the buffer; otherwise, then find and process next content part. | - 167 = 167 yes | |||||||||
| Output: | → Correct pair of header–content part of phrase is in the buffer. | ||||||||||
4. Results: Adaptation of LL to Dialog Verification Procedures
4.1. Step 1: Definition of Necessary Coded Words
4.2. Step 2: Formation of Request Phrases, Compatible with the LL Format
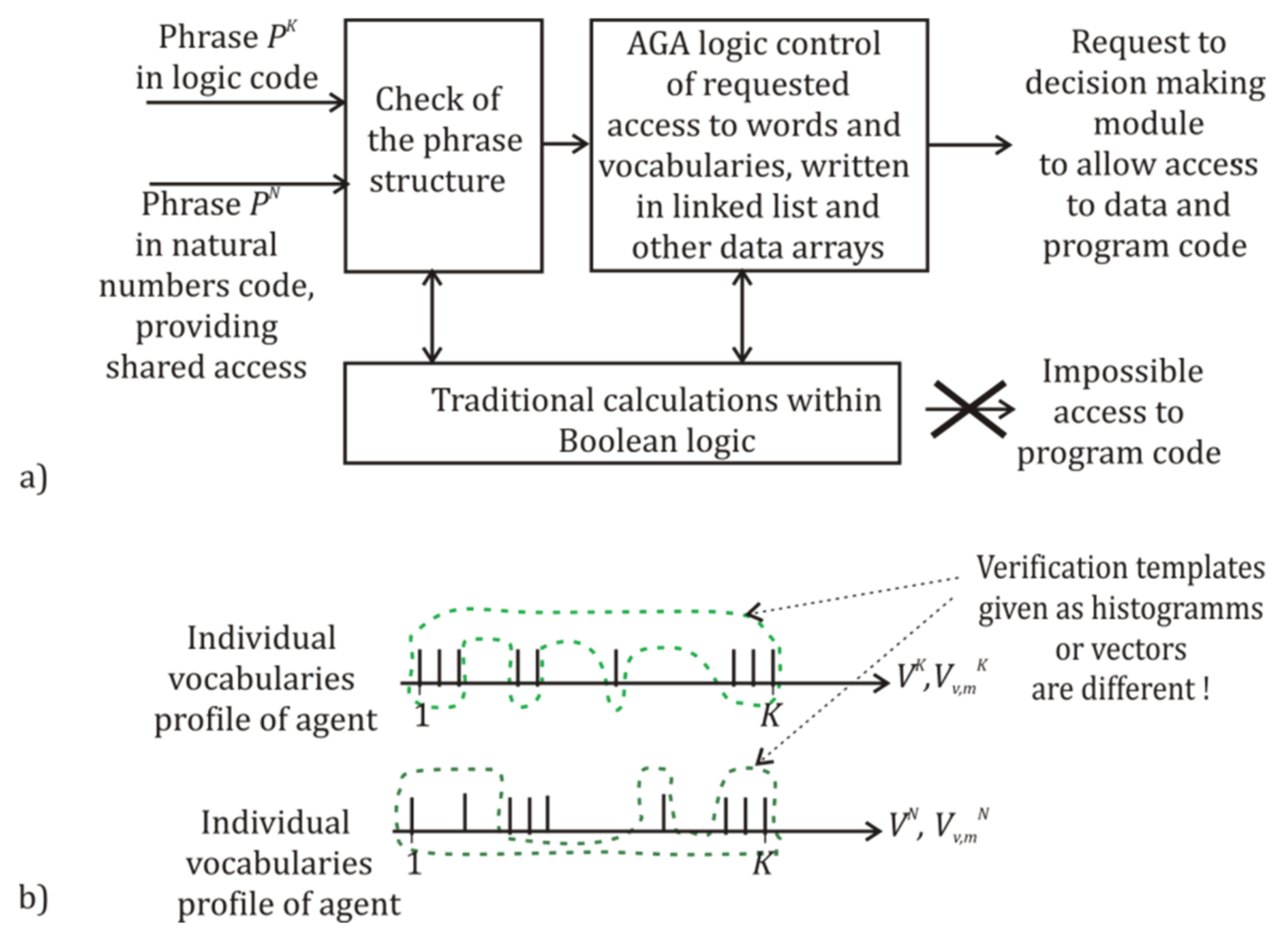
4.3. Step 3: Choice of LL Function and Its Adapted Versions
4.4. Step 4: Software Modeling of Phrase Procession, Adapted LL, and Actual Hardware Platform
4.5. Alternative Versions of AGA-Based LL
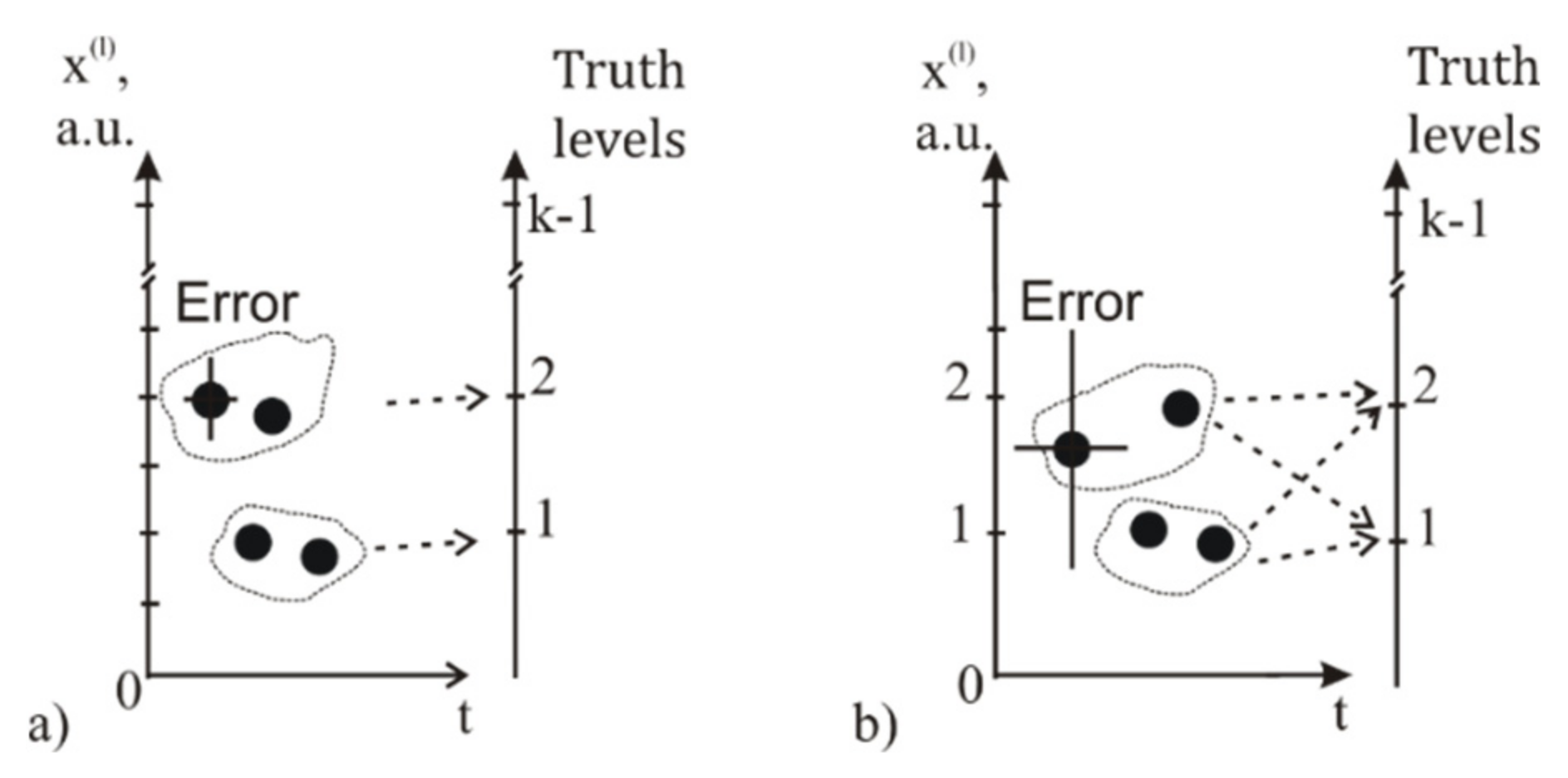
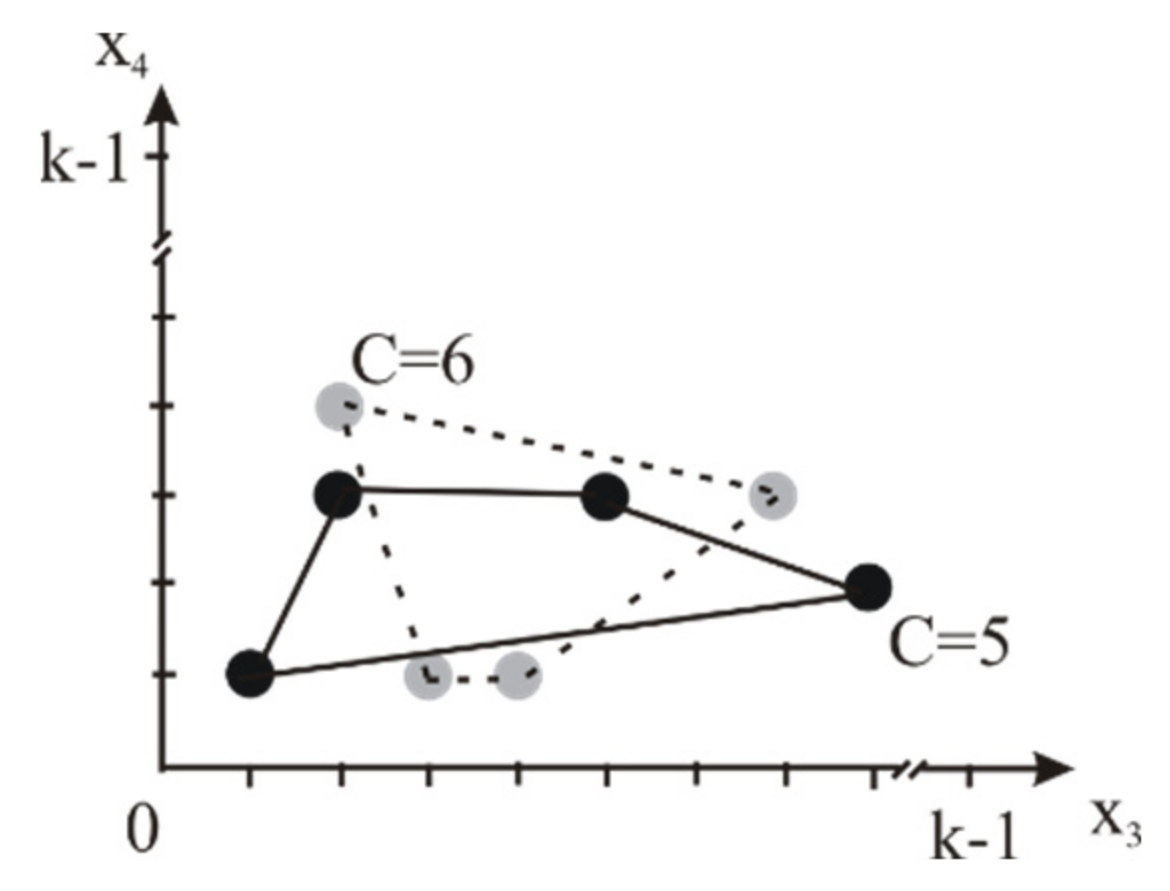
5. Results: Fragmentation of AGA Function into Diagrams of Logic States for Verification
- (1)
- , l, and (i.e., the mapping shortens the number of initially taken input variables);
- (2)
- Truth tables of the mapping function and the mapped one have the following:
- (a)
- Identical data in columns for coinciding input variables ;
- (b)
- Identical logic constants in columns for output variables and .
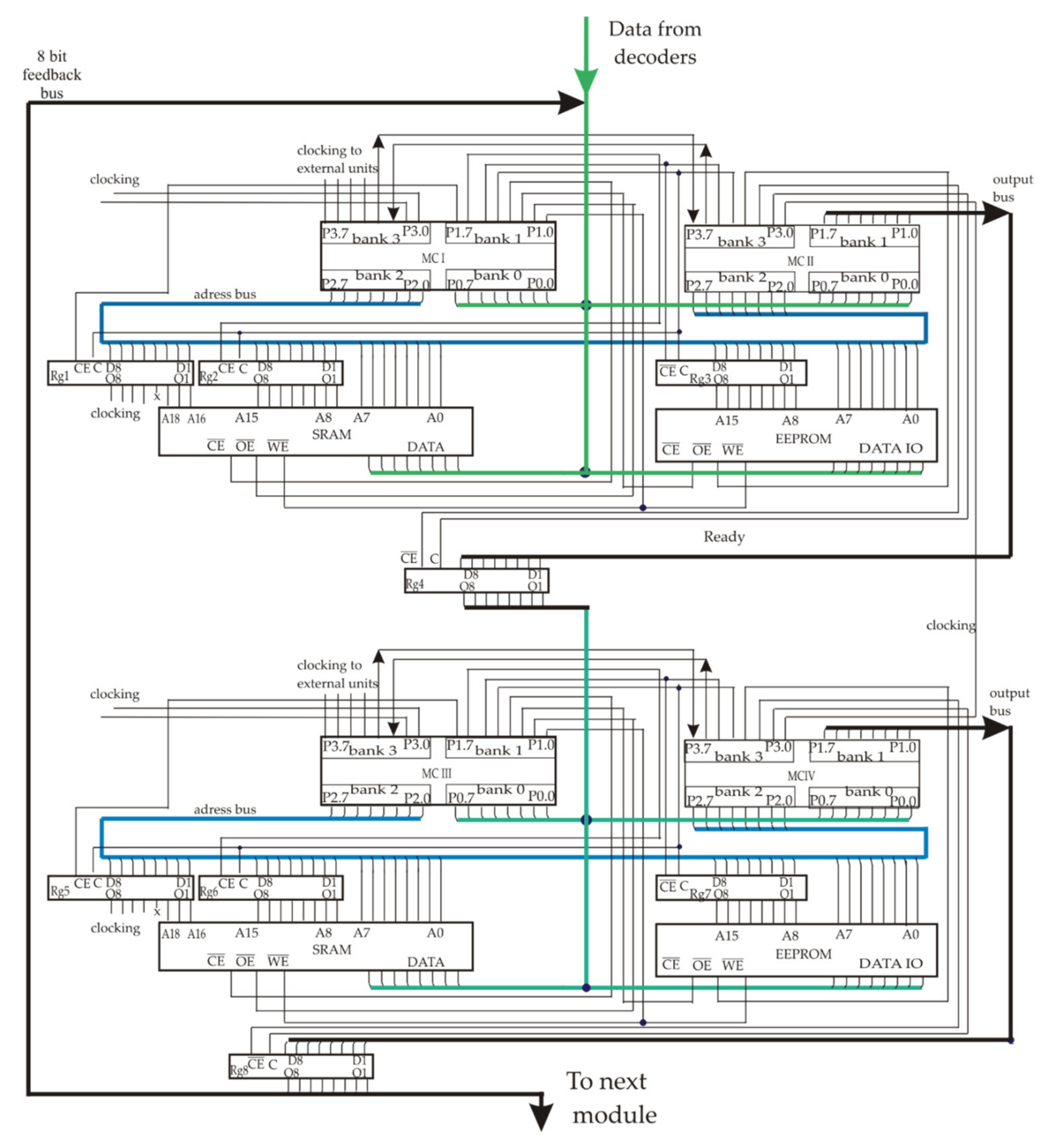
6. Results: Communication Module and Microassembler Software for the Verification
| Algorithm 3. Subroutine LLWRD is used to compute correct truth-level codes for the requested elements of vocabulary or . Procedure is to be carried out in MCS-III of 2D dual-chip and uses its pins. | |||
| , | INPUT Input variables | ||
| 1 | LLWRD: CLR P1.4; prepare pin | 2 | MOV P2, #000b; Assign #A18-A16 = #000b for SRAM |
| 3 | CLR P1.7; enable Rg1 by | 4 | SETB P1.4; Rg1 writes #A15-A8 = #000b |
| 5 | CLR P1.4; | 6 | SETB P1.7; lock Rg1 |
| 7 | CYCNT: MOV R2, #255; Set counter of notations | 8 | CYCVAR: MOV R3, #5; counter of input vars |
| 9 | LOAT:MOV P2, #009b; set #SB at to Rg3/7 ROM | 10 | CLR P1.5; enable Rg3/7 by |
| 11 | SETB P1.4; Rg3/7 writes #SB = #009b for a-template | 12 | CLR P1.4; |
| 13 | SETB P1.5; lock Rg3/7 | 14 | MOV P2, R2; set #A7-A0 = #255 for at ROM |
| 15 | CLR P1.2; enable ROM by | 16 | CLR P3.1; enable ROM output by |
| 17 | REAT:MOV R7, P0; read at from ROM | 18 | SETB P3.1; disable ROM output by |
| 19 | LOBT: MOV P2, #109; load #SB of bt in ROM | 20 | CLR P1.6; enable Rg3/7 by |
| 21 | SETB P1.4; Rg3/7 writes #SB = #109 of b-template | 22 | CLR P1.4; |
| 23 | SETB P1.6; lock Rg3/7 | 24 | MOV P2, #255; set #LB = #255 for ROM |
| 25 | CLR P1.2; enable chip ROM by | 26 | CLR P3.1; enables ROM output |
| 27 | REBT:MOV R6, P0; read b-template from ROM | 28 | SETB P3.1; disable ROM output |
| 29 | SETB P1.2; disable chip ROM | 30 | CLR P1.1; prepare pin for SRAM |
| 31 | LOAE: MOV P2, #0; set #SB = 0 in Rg1/5for SRAM | 32 | CLR P1.6; enables Rg2 |
| 33 | SETB P1.4; write #SB = #0 to Rg2 | 34 | CLR P1.4 |
| 35 | SETB P1.6; lock Rg2 | 36 | MOV P2, R3; #LB counter of variables |
| 37 | CLR P1.3; enables SRAM | 38 | CLR P1.1; enables output of SRAM |
| 39 | REAE:MOV R5, P0; read a-external from SRAM | 40 | SETB P1.1; disable output of SRAM |
| 41 | SETB P1.3; disable SRAM | 42 | LITERAL: MOV A, R7; load a-template to calc Lit. |
| 43 | CLR C; prepare carry bit | 44 | SUBB A, R5; at-ae = R7-R5 |
| 45 | JC CAB; jump if carry bit C = 1, i.e., a-ext. >a-templ. | 46 | AJMP PT0; Lit = 0 and the whole pt = 0 |
| 47 | CAB: CLR C | 48 | MOV A, R6; load bt to A to calc Literal |
| 49 | CLR C; prepare carry bit | 50 | SUBB A, R5; bt-ae = R6-R5 |
| 51 | JC PT0; jump PT0 if bit C = 1, i.e., ae > bt | 52 | DEC R3; counter of input variables |
| 53 | CJNE R3, #0, LOAT; process next variable | 54 | PT1: AJMP WRRES; write const in #SB = #003 |
| 55 | PT0: MOV R0, #0; product term = #0 | 56 | AJMP WRR0 |
| 57 | WRRES: MOV P2, #4; set #SB = #004 to read Const | 58 | SETB P1.4; write #SB = #004 into Rg2/6 |
| 59 | CLR P1.6; enable Rg2/6 | 60 | CLR P1.4; |
| 61 | MOV P2, R3; assign #LB to read Const | 62 | CLR P1.3; enables chip SRAM |
| 63 | CLR P1.1; enables output of SRAM | 64 | RECNST:MOV R0, P0; write Const in R0 |
| 65 | SETB P1.1; disable output of SRAM | 66 | SETB P1.6; disable Rg2/6 |
| 67 | WRR0: MOV P2, #3; set #SB = #003 to write Const | 68 | CLR P1.6; enable RG2/6 |
| 69 | SETB P1.4; write #SB = #003 to Rg2 | 70 | CLR P1.4; |
| 71 | SETB P1.6; lock Rg2 with #003 | 72 | MOV P2, R2; addressing of #LB for SRAM |
| 73 | MOV P0, R0; output next Const | 74 | CLR P1.3; enables chip SRAM |
| 75 | CLR P1.1; enables data of SRAM | 76 | CLR P1.0; write Const in #SB = 003, #LB = R2 |
| 77 | SETB P1.0; disables write in SRAM | 78 | disables data of SRAM |
| 79 | SETB P1.3; disables chip SRAM | 80 | DJNZ R2, #1,CYCVAR; process next notation |
| 81 | MAXPTS:MOV R1, #103; #SB103 for PTs | 82 | MOV R2, #255; counter of PTs |
| 83 | MOV P2,R1; addressing #SB = #103 | 84 | CLR P1.6; enable Rg2 by |
| 85 | SETB P1.4; write #SB = #103 to Rg2 | 86 | CLR P1.4 |
| 87 | SETB P1.6; lock Rg2 | 88 | MOV P2, R2; #LB is the counter of PTs |
| 89 | CLR P1.3; enable SRAM by | 90 | CLR P1.1; enables output of SRAM |
| 91 | MOV A, P0; read PT | 92 | SETB P1.1; disable output of SRAM |
| 93 | SETB P1.3; disable SRAM | 94 | DEC R2 |
| 95 | NEXTPT:MOV P2, R2 | 96 | CLR P1.3; enable SRAM by |
| 97 | CLR P1.1; enables output of SRAM | 98 | MOV R7, P0; read next PT |
| 99 | SETB P1.1; disable output of SRAM | 100 | SETB P1.3; disable SRAM |
| 101 | MOV R3, A; save value of Acc | 102 | CLR C |
| 103 | SUBB A, R7; | 104 | JNC MAX_N1 |
| 105 | MOV R0, R7 | 106 | MAX_N1:MOV R0, R3 |
| 107 | DJNZ R2, NEXTPT | 108 | RETI |
| OUTPUT: R0 → , truth-level code for the requested word from is written into the register R0. | |||
| Algorithm 4. The fragment of subroutine CHKPHR is to detect the header part of the phrase in the buffer memory and to calculate its total check coefficient. The register R7 is the counter for 30 parts in the buffer segment, R6 is the counter of parts in the phrase, R5 is the counter of #LB, and R4 is the counter of word values (limited by 16). | |||||||||||||
| Header of the received phrase parts | |||||||||||||
| Error 8-byte part | |||||||||||||
| Correct content part of phrase | |||||||||||||
| Words’ interpretation in the decoding table | |||||||||||||
| 1 | FINDHI: CLR P1.4; prepare pin | 2 | MOV P2, #00000111b; Assign #A18-A16 = #000b | ||||||||||
| 3 | CLR P1.7; enable Rg1 by | 4 | SETB P1.4; Rg1 writes #A15-A8 = #111b | ||||||||||
| 5 | CLR P1.4 | 6 | SETB P1.7; lock Rg1 | ||||||||||
| 7 | CYCPT: MOV R7, #1; counter of 30 parts in buffer | 8 | MOV P2, #00000111b; Assign #SB = #1 to read header | ||||||||||
| 9 | CLR P1.6; enable Rg2 by | 10 | SETB P1.4; Rg1 writes #SB = A15-A8 = #1 | ||||||||||
| 11 | CLR P1.4; | 12 | SETB P1.6; lock Rg2 | ||||||||||
| 13 | NXTPRT1:MOV R5, #0; counter of #LB | 14 | NXTPRT11:MOV P2, R5; set #LB | ||||||||||
| 15 | REWRD1: CLR P1.3; enable chip SRAM by | 16 | CLR P1.1; enable data output from SRAM | ||||||||||
| 17 | CHKHI1:MOV R3, P0; read 1st word from SRAM | 18 | MOV R0, R3; copy # of 1st word for further summation | ||||||||||
| 19 | SETB P1.1; disable output of SRAM | 20 | SETB P1.3; disable chip of SRAM | ||||||||||
| 21 | CHKHI11: CJNE R3, #7, CHKHI2; check if = 7 | 22 | MOV R6, #2; determines number of parts in phrase g = 2 | ||||||||||
| 23 | AJMP CHKPWD; | 24 | CHKHI2: CJNE R3, #123, CHKHI3; check if = 123 | ||||||||||
| 25 | MOV R6, #3; number of parts in phrase g = 3 | 26 | AJMP CHKPWD; | ||||||||||
| 27 | CHKHI3: CJNE R3, #209, NXTPRT2; check if =#209 | 28 | MOV R6, #4; number of parts in phrase g = 4 | ||||||||||
| 29 | CHKPWD: INC R5; #LB of 2d word-parole | 30 | MOV P2, R5; # to read password | ||||||||||
| 31 | CLR P1.3; enable chip SRAM by | 32 | CLR P1.1; enable data output from SRAM by | ||||||||||
| 33 | PWD:MOV R3, P0; output 2d word from SRAM | 34 | SETB P1.1; disable output of SRAM | ||||||||||
| 35 | SETB P1.3; disable chip of SRAM | 36 | CJNE R3, #131, NXTPRT2; password =131 | ||||||||||
| 37 | AJMP CHKNAME1; | 38 | NXTPRT2: DEC R5; return to the 1st word | ||||||||||
| 39 | NXTPRT21:MOV A, R5; | 40 | ADD A, #7; #LB for the 1st word in next part | ||||||||||
| 41 | MOV R5, A; #LB | 42 | MOV R1, A; copy #LB of word for further calc | ||||||||||
| 43 | CJNE R5, #240, NXTPRT11; check if buffer passed | 44 | RETI; buffer is fully processed | ||||||||||
| 45 | CHKNAME1: INC R5; #LB + 1 | 46 | INC R5; #LB increased by 2 for Addresser name 1 | ||||||||||
| 47 | MOV P2, R5; #LB to read name1 | 48 | NOP; | ||||||||||
| 49 | CLR P1.3; enable chip SRAM by | 50 | CLR P1.1; enable data output from SRAM | ||||||||||
| 51 | RENAME1:MOV R3, P0; read name1 | 52 | SETB P1.1; disable data output from SRAM | ||||||||||
| 53 | SETB P1.3; disable chip of SRAM | 54 | CJNE R3, #0, DEC2LB; name1 is =#0 | ||||||||||
| 55 | INC R1; #LB for Addresser name2 | 56 | CHKNAME2: MOV P2, R1; read name2 | ||||||||||
| 57 | CLR P1.3; enable chip SRAM by | 58 | CLR P1.1; enable data output from SRAM | ||||||||||
| 59 | RENAME2:MOV R3, P0; read name2 | 60 | SETB P1.1; disable data output from SRAM | ||||||||||
| 61 | SETB P1.3; disable chip of SRAM | 62 | CJNE R3, #0, DEC2LB; name2 is =#0 | ||||||||||
| 63 | INC R0; #LB for Addresser name 3 | 64 | CHKNAME3: MOV P2, R3; read name3 | ||||||||||
| 65 | CLR P1.3; enable chip SRAM by | 66 | CLR P1.1; enable data output from SRAM | ||||||||||
| 67 | RENAME3: MOV R3, P0; read next | 68 | SETB P1.1; disable data output from SRAM | ||||||||||
| 69 | SETB P1.3; disable chip of SRAM | 70 | CJNE R3, #3, DEC2LB; name 3 =#3 | ||||||||||
| 71 | AJMP CHKHSUM1 | 72 | DEC2LB: DEC R5; | ||||||||||
| 73 | DEC R5; | 74 | DEC R5; return #LB to 1st word in phrase | ||||||||||
| 75 | AJMP NXTPRT21 | 76 | CHKHSUM1:MOV R1, #0; counter of words | ||||||||||
| 77 | DEC R5; | 78 | DEC R5; | ||||||||||
| 79 | DEC R5; return #LB to 1st word in phrase | 80 | HSUM1: MOV R0, R5; copy #LB of word | ||||||||||
| 81 | MOV P2, R5; #LB 1st word of header | 82 | MOV A, #0; clear A for summation | ||||||||||
| 83 | CLR P1.3; enable chip SRAM by | 84 | CLR P1.1; enable data output from SRAM | ||||||||||
| 85 | MOV R3, P0; read from SRAM | 86 | MOV R1, #0; counter of words in phrase | ||||||||||
| 87 | SETB P1.1; disable output of SRAM | 88 | SETB P1.3; disable chip of SRAM | ||||||||||
| 89 | HSUM2: ADD A, R3; | 90 | INC R1; counter of words in part | ||||||||||
| 91 | INCR5:INC R5; increment #LB +1 | 92 | CJNE R1, #8,HSUM1; check counter of words | ||||||||||
| 93 | WRHSUM: MOV R4, A; save header check sum | 94 | CJNE R5, #240,RETI | ||||||||||
| 95 | WRCNTPT: MOV R1, #240; write check coef. to Reserve 1 | 96 | ADD R5,#8; # LB for next part | ||||||||||
| 97 | CJNE R5, #240,RETI | 98 | RECNTWD: P2, R5; #LB to read 1st content word | ||||||||||
| 99 | CLR P1.3; enables chip SRAM | 100 | CLR P1.1; enables output of SRAM | ||||||||||
| 101 | CLR P1.0 | 102 | MOV P0, R3; read sender name3 | ||||||||||
| 103 | SETB P1.0; disable write | 104 | SETB P1.1; disable chip SRAM | ||||||||||
| 105 | SETB P1.3 | … | … | ||||||||||
| … | RETI | … | … | ||||||||||
| Output: | buffer Reserve 1→ | R4 contains the total check coefficient for the adequate header and is ready for further use. | |||||||||||
- The proposed structure of coded vocabularies and the conjugated dialog protocol are tested by two designed microassembler programs, realized for the dual-chip module based on 8-bit MCS-51 microcontrollers.
- Subroutine LLWRD has approved the algorithm for data extraction from the proposed adapted version of LL module. It involves a short (100 operators) program. Subroutine CHKPHR has demonstrated the possibility to find correct content parts of dialog phrase for the given header part.
- The designed dialog phrase protocol for agents’ communication, involving 8-byte header and content parts, is compatible and convenient enough for the procession by 8-bit dual-chip module.
- Designed vocabulary structure can be used in simple 8-bit platforms with limited free memory resources, and the proposed dialog protocol can selectively transfer various combinations of logic words and verification coefficients.
- AGA vocabulary structure in 8-bit modeling provides 256 coded words,, and , creating the possibility to form complicated-enough terminology chains and to design tasks descriptions, providing distant exchange of data.
- An adapted version of LL with five input variables is the minimalistic possible tool for protected local storage of critical data, protected by paroles and hash values. If necessary, more complicated versions of LL can be extended by means of the enlarged number of hash values, approving the LL by other internal and external modules.
- Designed algorithms are applicable both for truth-level codes, , and natural number ones, , which can be further used for new and more exhausted verification schemes in the heterogeneous logic architecture of agent.
7. Discussion
8. Conclusions
- AGA logic modeling of communications in a large-scale robotic system;
- The proposed three-level ordered vocabulary structure, describing terminology for agents and the scene of action by coded words and collocations, represented by subsets given simultaneously in the natural language, ; natural-number codes,; and truth-level codes, ;
- The designed logic protocol of phrase formation and procession, using equal 8-byte headers and content parts;
- Distributed data storages in participating agents are proposed to use the adapted version of LL, providing the mixing of logic notations for 8-bit platforms.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- El Madani, S.; Motahhir, S.; El Ghzizal, A. Internet of vehicles: Concept, process, security aspects and solutions. Multimed. Tools Appl. 2022, 81, 16563–16587. [Google Scholar] [CrossRef]
- Daki, H.; El Hannani, A.; Aqqal, A.; Abdelfattah Haidine, A.; Dahbi, A. Big Data management in smart grid: Concepts, requirements and implementation. J. Big Data 2017, 4, 13. [Google Scholar] [CrossRef]
- Patrao, C.; Moura, P.S.; De Almeida, A.T. Review of Smart City Assessment Tools. Smart Cities 2020, 3, 1117–1132. [Google Scholar] [CrossRef]
- Zhang, K.; Chermprayong, P.; Xiao, F.; Tzoumanikas, D.; Dams, B.; Kay, S.; Kocer, B.B.; Burns, A.; Orr, L.; Alhinai, T.; et al. Aerial additive manufacturing with multiple autonomous robots. Nature 2022, 609, 709–717. [Google Scholar] [CrossRef]
- Khanna, A.; Kaur, S. Internet of Things (IoT), Applications and Challenges: A Comprehensive Review. Wirel. Pers. Commun. 2020, 114, 1687–1762. [Google Scholar] [CrossRef]
- Maalouf, N.; Sidaoui, A.; Elhajj, I.H.; Asmar, D. Robotics in Nursing: A Scoping Review. J. Nurs. Scholarsh. 2018, 50, 590–600. [Google Scholar] [CrossRef]
- Luckcuck, M.; Farrell, M.; Dennis, L.A.; Dixon, C.; Fisher, M. Formal Specification and Verification of Autonomous Robotic Systems: A Survey. ACM Comput. Surv. 2019, 52, 100. [Google Scholar] [CrossRef]
- Araujo, H.; Mousavi, M.R.; Varshosaz, M. Testing, Validation, and Verification of Robotic and Autonomous Systems: A Systematic Review. ACM Trans. Softw. Eng. Methodol. 2023, 32, 51. [Google Scholar] [CrossRef]
- You, K.Y. A Summary on 5G and Future 6G Internet of Things. In Opportunities and Challenges of Industrial IoT in 5G and 6G Networks; Yu, P., Hu, X., Prakash, A., Misuko, N.W., Haiyue, G., Eds.; IGI Global: Hershey, PA, USA, 2023; Volume 10, pp. 196–243. [Google Scholar] [CrossRef]
- Nikolic, G.; Dimitrijević, B.; Nikolic, T.; Stojcev, M. Fifty years of microprocessor evolution: From single CPU to multicore and manycore systems. Facta Univ.-Ser. Electron. Energetics 2021, 35, 155–186. [Google Scholar] [CrossRef]
- Shreyas, D.K.; Joshi, S.N.; Kumar, V.H.; Venkataramanan, V.; Kaliprasad, C.S. A Review on Neural Networks and its Applications. J. Comput. Technol. Appl. 2023, 14, 59–70. [Google Scholar] [CrossRef]
- Strzelecki, R.M.; Demidova, G.; Lukichev, D.; Poliakov, N.; Abdullin, A.; Lovlin, S. Survey on fuzzy logic methods in control systems of electromechanical plants. J. Sci. Tech. Inf. Technol. Mech. Opt. 2019, 19, 1–14. [Google Scholar] [CrossRef]
- Shelke, S.; Pathak, I.S.; Sangai, A.P.; Lunge, D.; Shahale, K.; Vyawahare, H.R. A Review Paper on Computer Vision. Int. J. Adv. Res. Sci. Commun. Techn. 2023, 3, 673–676. [Google Scholar] [CrossRef]
- Elyan, E.; Vuttipittayamongkol, P.; Johnston, P.; Martin, K.; McPherson, K.; Moreno-García, C.F.; Jayne, C.; Sarker, M.M.K. Computer vision and machine learning for medical image analysis: Recent advances, challenges, and way forward. Art. Int. Surg. 2022, 2, 24–45. [Google Scholar] [CrossRef]
- Basak, S.; Agrawal, H.; Jena, S.; Gite, S.; Bachute, M.; Pradhan, B.; Assiri, M. Challenges and Limitations in Speech Recognition Technology: A Critical Review of Speech Signal Processing Algorithms, Tools and Systems. Comput. Model. Eng. Sci. 2022, 135, 1053–1089. [Google Scholar] [CrossRef]
- García, S.; Ramírez-Gallego, S.; Luengo, J.; Benítez, J.M.; Herrera, F. Big data preprocessing: Methods and prospects. Big Data Anal. 2016, 1, 9. [Google Scholar] [CrossRef]
- Jency Rubia, J.; Babitha Lincy, R.; Ezhil, E.N.; Sherin Shibi, C.; Rosi, A. A Survey about Post Quantum Cryptography Methods. EAI Endorsed Trans. Internet Things 2024, 10, 9. [Google Scholar] [CrossRef]
- Bykovsky, A.Y.; Kompanets, I.N. Quantum cryptography and combined schemes of quantum cryptography communication networks. Quantum Electron. 2018, 48, 777–801. [Google Scholar] [CrossRef]
- Li, W.; Guo, H.; Nejad, M.; Shen, C.-C. Privacy-preserving traffic management: A Blockchain and zero-knowledge proof inspired approach. IEEE Access 2020, 8, 181733–181743. [Google Scholar] [CrossRef]
- Laghari, A.A.; Shah, H.; Laghari, R.A.; Kumar, K.; Waqan, A.A.; Jumani, A.K. A Review on Quantum Computing Trends & Future Perspectives. EAI Endorsed Trans. Cloud Syst. 2022, 7, e1. [Google Scholar] [CrossRef]
- Kebande, V.R.; Awaysheh, F.M.; Ikuesan, R.A.; Alawadi, S.A.; Alshehri, M.D. A Blockchain-Based Multi-Factor Authentication Model for a Cloud-Enabled Internet of Vehicles. Sensors 2021, 21, 6018. [Google Scholar] [CrossRef]
- Hasan, M.; Mohan, S.; Shimizu, T.; Lu, H. Securing Vehicle-to-Everything (V2X) Communication Platforms. IEEE Trans. Intell. Veh. 2020, 5, 693–713. [Google Scholar] [CrossRef]
- Cisco Annual Internet Report (2018–2023) White Paper Updated: 9 March 2020. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 12 November 2024).
- Kanagasabai, T.; Thiruchchelvan, N. Data Verification and Validation Process in the Management System Development. Middle-East J. Sci. Res. 2017, 25, 902–911. Available online: https://www.researchgate.net/publication/318204712 (accessed on 12 February 2025).
- Caldas, R.; Piñera García, J.A.; Schiopu, M.; Pelliccione, P.; Rodrigues, G.; Berger, T. Runtime Verification and Field Testing for ROS-Based Robotic Systems. arXiv 2024, arXiv:2404.11498v1. [Google Scholar] [CrossRef]
- Bykovsky, A.Y. Multiple-Valued Logic and Neural Network in the Position-Based Cryptography Scheme. J. Russ. Laser Res. 2021, 42, 618–630. [Google Scholar] [CrossRef]
- Chen, J.; Micali, S. Algorand: A Secure and Efficient Distributed Ledger. Theor. Comput. Sci. 2019, 777, 155–183. [Google Scholar] [CrossRef]
- Ethan, B.; Jae, K. Cosmos Whitepaper: A Network of Distributed Ledgers. 2016. Available online: https://v1.cosmos.network/resources/whitepaper (accessed on 12 November 2024).
- Cardoso, R.C.; Farrell, M.; Luckcuck, M.; Ferrando, A.; Fisher, M. Heterogeneous Verification of an Autonomous Curiosity Rover. arXiv 2007, arXiv:2007.10045v1. [Google Scholar]
- Aminof, B.; Murano, A.; Rubin, S.; Zuleger, F. Verification of Asynchronous Mobile-Robots in Partially-Known Environments. In Proceedings of the PRIMA 2015: Principles and Practice of Multi-Agent Systems. PRIMA 2015, Bertinoro, Italy, 26–30 October 2015; Lecture Notes in Computer Science. Chen, Q., Torroni, P., Villata, S., Hsu, J., Omicini, A., Eds.; Springer: Cham, Switherland, 2015; Volume 9387, pp. 185–200. [Google Scholar] [CrossRef]
- Kouvaros, P.; Lomuscio, A. Formal verification of opinion formation in swarms. In Proceedings of the 15 International Conference on Autonomous Agents & Multiagent Systems (AAMAS 2016), Singapore, 9–13 May 2016; pp. 1200–1208. [Google Scholar]
- Foughali, M.; Berthomieu, B.; Dal Zilio, S.; Hladik, P.-E.; Ingrand, F.; Mallet, A. Formal verification of complex robotic systems on resource-constrained platforms. In Proceedings of the 2018 IEEE/ACM 6th International FME Workshop on Formal Methods in Software Engineering (FormaliSE), IEEE, Gothenburg, Sweden, 27 May–3 June 2018; pp. 2–9. [Google Scholar] [CrossRef]
- Kamali, M.; Dennis, L.A.; McAree, O.; Fisher, M.; Veres, S.M. Formal verification of autonomous vehicle platooning. Sci. Comp. Program. 2017, 148, 88–106. [Google Scholar] [CrossRef]
- Barbot, B.; Bérard, B.; Duplouy, Y.; Haddad, S. Statistical model-checking for autonomous vehicle safety validation. In Proceedings of the SIA Simulation Numérique, HAL-Inria, Montigny-le-Bretonneux, France, 16 March 2017. [Google Scholar]
- Luo, C.; Wang, R.; Jiang, Y.; Yang, K.; Guan, Y.; Li, X.; Shi, Z. Runtime verification of robots collision avoidance case study. In Proceedings of the IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018; IEEE: Piscataway, NJ, USA, 2018; Volume 1, pp. 204–212. [Google Scholar] [CrossRef]
- Lomuscio, A.; Michaliszyn, J. Verifying Multi-Agent Systems by Model Checking Three-valued Abstractions. In Proceedings of the 14th International Conference on Autonom, Agents and Multiagent Systems (AAMAS 2015), Istanbul, Turkey, 4–8 May 2015; Bordini, E., Weiss, Y., Eds.; Volume 15, pp. 189–198. [Google Scholar]
- Mansoor, N.; Saddler, J.A.; Silva, B.; Bagheri, H.; Cohen, M.B.; Farritor, S. Modeling and testing a family of surgical robots: An experience report. In Proceedings of the 26th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, ACM, Lake Buena Vista, FL, USA, 4–9 November 2018; pp. 785–790. [Google Scholar]
- Cavalcanti, A.; Miyazawa, A.; Sampaio, A.; Li, W.; Ribeiro, P.; Timmis, J. Modelling and verification for swarm robotics. In Proceedings of the International Conference on Integrated Formal Methods, Maynooth, Ireland, 5–7 September 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 1–19. [Google Scholar]
- Betts, K.M.; Petty, M.D. Automated search-based robustness testing for autonomous vehicle software. Model. Simul. Eng. 2016, 3, 5309348. [Google Scholar] [CrossRef]
- Available online: https://www.mathworks.com/ (accessed on 12 November 2024).
- Brambilla, M.; Brutschy, A.; Dorigo, M.; Birattari, M. Property-driven design for robot swarms: A design method based on prescriptive modeling and model checking. ACM Trans. Auton. Adapt. Syst. (TAAS) 2014, 9, 1–28. [Google Scholar] [CrossRef]
- O’Kelly, M.; Abbas, H.; Gao, S.; Shiraishi, S.; Kato, S.; Mangharam, R. APEX: Autonomous vehicle plan verification and execution. In Proceedings of the SAE 2016 World Congress and Exhibition, Detroit, MI, USA, 12–14 April 2016; SAE International: Washington, DC, USA, 2016; Volume 1, pp. 1–13. [Google Scholar]
- Desai, A.; Dreossi, T.; Seshia, S.A. Combining Model Checking and Runtime Verification for Safe Robotics. In Runtime Verification; Lahiri, S., Reger, G., Eds.; Springer International Publishing: Cham, Switherland, 2017; pp. 172–189. [Google Scholar]
- Lu, Y.; Niu, H.; Savvaris, A.; Tsourdos, A. Verifying collision avoidance behaviours for unmanned surface vehicles using probabilistic model checking. IFAC-Pap. 2016, 49, 127–132. [Google Scholar] [CrossRef]
- Foughali, M.; Berthomieu, B.; Dal Zilio, S.; Ingrand, F.; Mallet, A. Model checking real-time properties on the functional layer of autonomous robots. In Proceedings of the International Conference on Formal Engineering Methods ICFEM 2016, Tokyo, Japan, 14–18 November 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 383–399. [Google Scholar]
- Hagerman, S.; Andrews, A.; Oakes, S. Security testing of an unmanned aerial vehicle (UAV). In Proceedings of the 2016 Cybersecurity Symposium (CYBERSEC), IEEE, Coeur d’Alene, ID, USA, 18–20 April 2016; pp. 26–31. [Google Scholar] [CrossRef]
- Abdelsalam, M.; Khalil, K.; Stickley, J.; Salem, A.; Loye, B. Verification of advanced driver assistance systems (ADAS) and autonomous vehicles with hardware emulation-in-the-loop. Int. J. Automot. Eng. 2019, 10, 197–204. [Google Scholar] [CrossRef] [PubMed][Green Version]
- Ben Abdessalem, R.; Panichella, A.; Nejati, S.; Briand, L.C.; Stifter, T. Testing autonomous cars for feature interaction failures using many-objective search. In Proceedings of the 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE), IEEE, Montpellier, France, 3–7 September 2018; pp. 143–154. [Google Scholar] [CrossRef]
- Sieber, C.; Vieira da Silva, L.M.; Grünhagen, K.; Fay, A. Rule-Based Verification of Autonomous Unmanned Aerial Vehicles. Drones 2024, 8, 26. [Google Scholar] [CrossRef]
- Yaacoub, E.; Abualsaud, K.; Mahmoudm, M. Hybrid Encryption for Securing and Tracking Goods Delivery by Multipurpose Unmanned Aerial Vehicles in Rural Areas Using Cipher Block Chaining and Physical Layer Security. Drones 2024, 8, 111. [Google Scholar] [CrossRef]
- Ma, J.; Chen, P.; Xiong, X.; Zhang, L.; Yu, S.; Zhang, D. Research on Vision-Based Servoing and Trajectory Prediction Strategy for Capturing Illegal Drones. Drones 2024, 8, 127. [Google Scholar] [CrossRef]
- Gao, J.; Liu, Q.; Chen, H.; Deng, H.; Zhang, L.; Sun, L.; Huang, J. Digital Battle: A Three-Layer Distributed Simulation Architecture for Heterogeneous Robot System Collaboration. Drones 2024, 8, 156. [Google Scholar] [CrossRef]
- Sakagami, R.; Lay, F.S.; Dömel, A.; Schuster, M.J.; Albu-Schäffer, A.; Stulp, F. Robotic world models—Conceptualization, review, and engineering best practices. Front. Robot. AI 2023, 10, 1253049. [Google Scholar] [CrossRef]
- Zhuang, P.; Zamir, T.; Liang, H. Blockchain for Cybersecurity in Smart Grid: A Comprehensive Survey. IEEE Trans. Ind. Inform. 2021, 17, 3–19. [Google Scholar] [CrossRef]
- Prabadevi, B.; Deepa, N.; Pham, Q.-V.; Nguyen, D.C.; Praveen Kumar Reddy, M.; Thippa Reddy, G.; Pathirana, P.N.; Dobre, O. Toward Blockchain for Edge-of-Things: A New Paradigm, Opportunities, and Future Directions. IEEE Internet Things Mag. 2021, 4, 102–108. [Google Scholar] [CrossRef]
- Ankalkoti, P. A Relative Study on Bitcoin Mining. Imperial J. Interdiscip. Res. 2017, 3, 1757–1761. [Google Scholar]
- Russell, S.; Norvig, P. Artificial Intelligence: A Modern Approach, 4th ed.; Pearson: Hoboken, NJ, USA, 2021; Chapters 2, 7, 11, 18, 26. [Google Scholar]
- Gevers, M. Identification for Control: From the Early Achievements to the Revival of Experiment Design*. Eur. J. Control 2005, 11, 335–352. [Google Scholar] [CrossRef]
- Bruns, G.; Godefroid, P. Model Checking Partial State Spaces with 3-Valued Temporal Logics. In Proceedings of the Computer Aided Verification, 11th International Conference, CAV ’99, Trento, Italy, 6–10 July 1999; Halbwachs, N., Peled, D.A., Eds.; CAV 1999, LNCS. Springer: Berlin/Heidelberg, Germany, 1999; Volume 1633, pp. 274–287. [Google Scholar] [CrossRef]
- Gurfinkel, A.; Chechik, M. Multi-Valued Model Checking via Classical Model. Lect. Notes Comput. Sci. 2003, 2761, 266–280. [Google Scholar] [CrossRef]
- Chechik, M.; Gurfinkel, A.; Devereux, B.; Lai, A.; Easterbrook, S. Data structures for symbolic multi-valued model-checking. Form. Methods Syst. Des. 2006, 29, 295–344. [Google Scholar] [CrossRef]
- Winograd, T.; Flores, F. Understanding Computers and Cognition: A New Foundation for Design; Addison-Wesley Longman Publishing Co., Inc.: Boston, MA, USA, 1987. [Google Scholar]
- Gay, D.; Levis, P.; von Behren, R.; Welsh, M.; Brewer, E.; Culler, D. The nesC Language: A Holistic Approach to Networked Embedded Systems. In Proceedings of the ACM SIGPLAN 2003 Conference on Programming Language Design and Implementation, San Diego, CA, USA, 9–11 June 2003. Report number: IRB-TR-02-019. [Google Scholar] [CrossRef]
- Casey, A.; Davidson, E.; Poon, M.; Dong, H.; Duma, D.; Grivas Grover, A.C.; Suarez-Paniagua, V.; Tobin, R.; Whiteley, W.; Wu, H.; et al. A Systematic Review of Natural Language Processing Applied to Radiology Reports. BMC Med. Inform. Decis. Mak. 2021, 21, 179. [Google Scholar] [CrossRef] [PubMed]
- Gelvanovsky, G. Effective Application of Large Language Models in Teaching Academic Writing in English: The Case of ChatGPT 3.5. Presentation April. 2024. [Google Scholar] [CrossRef]
- Sun, C.; Sun, P.; Wang, J.; Guo, Y.; Zhao, X. Understanding LiDAR Performance for Autonomous Vehicles Under Snowfall Conditions. IEEE Trans. Intell. Transp. Syst. 2024, 25, 16462–16472. [Google Scholar] [CrossRef]
- Shahraji, M.H.; Larouche, C. Case Study: Rigorous Boresight Alignment of a Marine Mobile LiDAR System Addressing the Specific Demands of Port Infrastructure Monitoring. Mar. Geod. 2022, 45, 295–327. [Google Scholar] [CrossRef]
- Bykovsky, A.Y.; Vasiliev, N.A. Data Verification in the Agent, Combining Blockchain and Quantum Keys by Means of Multiple-Valued Logic. Appl. Syst. Innov. 2023, 6, 51. [Google Scholar] [CrossRef]
- Bykovsky, A. Multiple-Valued Logic Modelling for Agents Controlled via Optical Networks. Appl. Sci. 2022, 12, 1263. [Google Scholar] [CrossRef]
- Allen, C.M.; Givone, D.D. The Allen-Givone Implementation Oriented Algebra. In Computer Science and Multiple-Valued Logic: Theory and Applications; Rine, D.C., Ed.; North Holland: Amsterdam, The Netherlands, 1984; pp. 262–283. [Google Scholar]
- Miller, D.M.; Thornton, M.A. Multiple-Valued Logic. Concepts and Representations; Springer Nature: Cham, Switzerland, 2008. [Google Scholar] [CrossRef]
- Fitting, M.; Orłowska, E. (Eds.) Beyond Two: Theory and Applications of Multiple-Valued Logic; Physica: Heidelberg, Germany, 2010. [Google Scholar] [CrossRef]
- Antipov, A.L.; Bykovsky, A.Y.; Vasiliev, N.A.; Egorov, A.A. Multiple-valued logic-protected coding for an optical non-quantum communication line. J. Russ. Laser Res. 2006, 27, 492–505. [Google Scholar] [CrossRef]
- Optical Computing. Digital and Symbolic; Arrathoon, R., Ed.; Marcel Decker: New York, NY, USA; Basel, Switherland, 1989. [Google Scholar]
- Bykovsky, A.Y. Heterogeneous network architecture for integration of AI and quantum optics by means of multiple-valued logic. Quantum Rep. 2020, 2, 126–165. [Google Scholar] [CrossRef]
- Pykacz, J. The Many-Valued Logic of Quantum Mechanics. Int. J. Theor. Phys. 2021, 60, 677–686. [Google Scholar] [CrossRef]
- Bykovsky, A.Y.; Vasiliev, N.A. Parametrical T-Gate for Joint Processing of Quantum and Classic Optoelectronic Signals. J—Multidisc. Sci. J. 2023, 6, 384–410. [Google Scholar] [CrossRef]
- Ma, X.; Yuan, X.; Cao, Z.; Qi, B.; Zhang, Z. Quantum random number generation. Npj Quantum Inf. 2016, 2, 16021. [Google Scholar] [CrossRef]
- Bykovsky, A. A Multiple-Valued Logic for Implementing a Random Oracle and the Position-Based Cryptography. J. Russ. Laser Res. 2019, 40, 173–183. [Google Scholar] [CrossRef]
- Beebe, N.H. The Mathematical-Function Computation Handbook; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar] [CrossRef]
- Cyranski, J.F. Measurement theory for physics. Found. Phys. 1979, 9, 641–671. [Google Scholar] [CrossRef]
- Conti, M.; Dragoni, N.; Lesyk, V. A Survey of Man in the Middle Attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Hetmański, M. Expert Knowledge: Its Structure, Functions and Limits. Stud. Humana 2018, 7, 11–20. [Google Scholar] [CrossRef]
- Gua, H. A Mathematical Theory of Language. Int. J. Contemp. Educ. 2017, 1, 1–11. [Google Scholar] [CrossRef]
- MCS 51 Microcontrollers Family User’s Manual. Available online: https://web.mit.edu/6.115/www/document/8051.pdf (accessed on 12 November 2024).
- Gregersen, C. A Complete Guide to Microcontrollers for IoT (23 July 2020). Available online: https://www.nabto.com/iot-microcontroller-guide/ (accessed on 10 November 2024).
- Billman, G.E. Homeostasis: The Underappreciated and Far Too Often Ignored Central Organizing Principle of Physiology. Front. Physiol. 2020, 11, 200. [Google Scholar] [CrossRef]
- Zhao, W.; Li, B.; Li, X. A Star Pattern Recognition Algorithm Based on the Radial Companion-Circumferential Feature. Math. Probl. Eng. 2022, 2022, 1857481. [Google Scholar] [CrossRef]
- Arduino. Available online: https://www.arduino.cc (accessed on 12 November 2024).
- Sha, Z.; Li, Z.; Yu, N.; Zhang, Y. DE-FAKE: Detection and Attribution of Fake Images Generated by Text-to-Image Generation Models. In Proceedings of the CCS ’23: ACM SIGSAC Conference on Computer and Communications Security, ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; pp. 3418–3432. [Google Scholar] [CrossRef]
- Kumar, C.K.; Suyambulingom, C. Cryptographic of high Security HashFunctions. Int. J. Eng. Res. Technol. 2012, 1, 1–7. Available online: https://www.ijert.org/research/cryptographic-of-high-security-hash-functions-IJERTV1IS3074.pdf (accessed on 12 November 2024).
| row | Input Variables | Output Variable | |||||
|---|---|---|---|---|---|---|---|
| … | |||||||
| 0 | 0 | 0 | 0 | 0 | … | 0 | |
| 1 | 1 | 0 | 0 | 0 | … | 0 | |
| … | … | … | … | … | … | … | … |
| K − 1 | K − 1 | K − 1 | K − 1 | … | K − 1 | ||
| Notation | Definition |
|---|---|
| Finite set of truth levels, , is defined in AGA [70], where ,, , and N is the set of natural numbers. Only finite sets are intended for basic logic AGA modeling and the mapping of words vocabularies. | |
| Finite subset, , of the set of natural numbers, It is intended for auxilliary representation and mapping of words in vocabularies. | |
| The finite set (or the vocabulary) of all selected different robotic terms, given by words and word collocations of natural language. It describes the scene of action, robotic tasks, and mathematical and verification procedures. | |
| Modeling of the scene of action uses subsets of truth levels,, obtained by arbitrarily chosen bijective mapping, →, i.e., onto the scale of truth levels, , defined in AGA. | |
| Subsets of vocabulary are obtained by arbitrarily chosen mapping of →, i.e., onto the scale of natural numbers , where the set consists of subsets ; | |
| Subset of the vocabulary determines one of given classes of robotic terms, containing only different elements, where K is the maximal number of truth levels. In the majority of tasks, convenient classes of robotic terms correspond to classes of words (noun, verb, adverbial modifiers of place, time, etc.) | |
| Element of a subset (or vocabulary) can be given by a word or a collocation, representing in natural language some robotic term. | |
| Mapping of onto the subset of natural numbers , providing representation of a robotic term in natural-number code. | |
| Mapping of onto the set , providing equivalent logic representation of a robotic term. | |
| Word phrase is a vector, = (, , …, , with declared fixed position of elements according to their numbers, v = {1,..,Z}, Z. Word phrase is a sampling of only one word from the next vocabulary. For various types of processions, it can be written by elements of subsets , , . Note that the list of selected vocabularies and message format can differ for various classes of tasks. |
| N | Name of Vocabulary | Content | Class of Word in Natural Language | Natural Language Representation (Maximal Number of Words—K) |
|---|---|---|---|---|
| 1 | Initiation of dialog and format of message | Cardinal number | {one, two, …, } | |
| 2 | Fixed parole | Cardinal number | {one, two, …, } | |
| 3 | Hash value | Cardinal number | {one, two, …, } | |
| 4 | Addresser of message | Noun | {administrator, robot of MAS, external robot, man, vehicle, unidentified object} | |
| 5 | Sender of message | Noun | {administrator, robot of MAS, external robot, man, vehicle, unidentified object} | |
| 6 | Relative time of sending | Cardinal number | {one, two, …, } | |
| 7 | Time of action | Adverbial modifier of time | {immediately, now, near future, in an hour, at the specified time…} | |
| 8 | Action/task | Verb | {verify, measure, read, write, move to, upload, download, plugs/connectors check, software check, circuit board test, coating check, mechanics check, show word …} | |
| 9 | Object of action | Noun | {admin, addresser, robot of MAS, external robot, man, house, technical construction, vehicle, road, tree, animal, vocabulary, unidentified object, license ID…} | |
| 10 | Number of objects of action | Cardinal number | {one, two, …, } | |
| 11 | Place of action/objects of action | Noun, adverbial modifier of place | {robot, external object, vehicle, internal module, …} | |
| 12 | Reference object for relative coordinates | Noun | {robot of MAS, external robot, man, house, technical construction, vehicle, road, tree, bush, animal, pit, stone, …} | |
| 13 | Place of action/coordinate x | Cardinal number | {GPS coordinate x, relative coordinate one, two, …} | |
| 14 | Place of action/coordinate y | Cardinal number | {one, two, …} | |
| 15 | Linked list | Cardinal number | {one, two, …,} | |
| 16 | Natural-number code | Cardinal number | {one, two, …, } | |
| 17 | Truth-level code | Cardinal number | {one, two, …, } | |
| 18 | … | … | … | … |
| M | … | … | … | |
| … | Format of message | Cardinal number | {one, two, …, } | |
| … | Fixed parole | Cardinal number | {one, two, …, } | |
| … | Addresser of message | Noun | {administrator, robot of MAS, external robot, man, vehicle, unidentified object} | |
| … | … | … | … | … |
| 2M | … | … | … | |
| … | … | … | … | … |
| KxM | … | … | … |
| N | Natural Language Vocabulary | Natural-Number Code of Vocabulary | Truth-Level Code of Vocabulary | Content |
|---|---|---|---|---|
| 1 | Format of message | |||
| “SOS” | ||||
| “Hi, read 2parts message”; Initiation of the new phrase | ||||
| “Hi, read 3parts message”; | ||||
| … | … | … | … | |
| “Ready to continue” | ||||
| … | … | … | … | … |
| 2 | Fixed parole | |||
| … | … | … | … | … |
| K × M | Content given by expert |
| 1st 8-Byte Header Part | ||||||||
| Variable | ||||||||
| Name | Initiation of dialog/Format, | Fixed parole, | Addresser name 1, | Addresser name 2, | Addresser name 3, | Sender name 1, | Sender name 2, | Sender name 3, |
| Vocabulary (in Table 3) | ||||||||
| 2D 8-Byte Content Part | ||||||||
| Variable | ||||||||
| Name | Assigned hash, | Arbitrary word, | Arbitrary word, | … | … | Arbitrary word, | Arbitrary word, | Total check coefficient of all previous parts and the current one, or |
| Vocabulary | … | … | ||||||
| … | … | … | … | … | … | … | … | … |
| (KxM-4)/2th 8-byte part-content | ||||||||
| Variable | … | … | … | |||||
| Name | Assigned hash, | Arbitrary word, | Arbitrary word, | … | … | Arbitrary word, | Arbitrary word, | Total check coefficient of all previous parts and the current one or |
| Vocabulary | … | … | ||||||
| Header: | ||||||||
|---|---|---|---|---|---|---|---|---|
| Mapping to natural-number code | Hi = 2 | Fixed parole of addresser = 131 | Addresser name 1 = 0 | Addresser name 2 = 0 | Addresser name 3 = 3 | Sender name 1 = 0 | Sender name 2 = 0 | Sender name 3 = 2 |
| Content part 1: | = ∑ | |||||||
| Mapping to natural-number code | Assigned hash value = 209 | Action = Show K-code for word in = 196 | Number of objects = v = 3 | Number of objects = m = 12 | Number of objects = 6 | Questionable code name = 221 | Hash for access to vocabularies group, including = 147 | 138 + 209 + 196 + 3 + 12 + 6 + 221 + 147 = 932 (overflow: >255); 932 − 3 × 255 = 167 |
| “Extract Word” | ||||||
|---|---|---|---|---|---|---|
| Number of rows in vocabulary matrix, | Number of columns in vocabulary matrix, m = 8 | Word code in natural language = “Show variable” | Word code in natural-number code = 23 | Word code in truth levels = | Addresser’s approving = 34 | Sender’s approving hash |
| “License ID” | ||||||
| Number of rows in vocabulary matrix, | Number of columns in vocabulary matrix, m = 9 | Word code in natural language = “license ID” | Word code in natural-number code = 23 | Word code in truth levels = | Addresser’s approving hash = 11 | Sender’s approving hash |
| “Hash Value” | ||||||
| Number of rows in vocabulary matrix, | Number of columns in vocabulary matrix, m = 8 | Word code in natural language = “hash value” | Word code in natural-number code = 23 | Word code in truth levels = | Addresser’s approving hash = 83 | Sender’s approving hash |
| (a) Input Variables | Output Variable | ||||
| Word code in natural numbers, = {1 ÷ 16} | Number of rows in vocabulary matrix, | Number of columns in vocabulary matrix, m = {1 ÷ 16} | Word code in truth levels, {1 ÷ 256} | Sender approving hash, = {1 ÷ 256} | Addresser approving hash = {1 ÷ 256} |
| (b) Input Variables | Output Variable | ||||
| Word code in natural numbers, = {1 ÷ 16} | Number of rows in vocabulary matrix, | Number of columns in vocabulary matrix, m = {1 ÷ 16} | Addresser approving hash = {1 ÷ 256} | Sender approving hash, | Word code in truth levels, {1 ÷ 256} |
| (a) Number of input variables: 2 × (1 + p + q), p-number of words in entry, q- maximal number of verifying participants | ||||||||||||||||||||
| Input Variables | Output Variable | |||||||||||||||||||
| Common counters | Previous Entry (8 bytes) | Verifying hash | Last Entry (8 bytes) | Verifying hash | Output hash | |||||||||||||||
| m | … | … | … | … | ||||||||||||||||
| 1 | … | … | … | |||||||||||||||||
| … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | ||||||
| m − 1 | … | … | … | … | ||||||||||||||||
| m | … | … | … | … | ||||||||||||||||
| (b) Number of input variables: 2 × (2 + g), g-number of parts in the phrase. | ||||||||||||||||||||
| Common counters | Previous Entry (8 bytes) | Verifying hash | Last Entry (8 bytes) | Verifying hash | Output hash | |||||||||||||||
| Input variables | Output variable | |||||||||||||||||||
| m | … | … | ||||||||||||||||||
| 1 | … | … | ||||||||||||||||||
| … | … | … | … | … | … | … | … | … | … | … | … | … | ||||||||
| m − 1 | … | … | ||||||||||||||||||
| m | … | … | ||||||||||||||||||
 |
| N | Word Code in Natural Numbers, = {1 ÷ 16} | Number of Row in Vocabulary Matrix, | Number of Column in Vocabulary Matrix, m = {1 ÷ 16} | Addresser Approving Hash, = {1 ÷ 256} | Sender Approving Hash, | Word Code in Truth Levels, {1 ÷ 256} |
|---|---|---|---|---|---|---|
| #A18–A16: | #000b | #000b | #000b | #000b | #000b | #000b |
| #SB (A15–A8): | #109 | #108 | #107 | #106 | #105 | #104 |
| #LB: | #0 ÷ 255 | #0 ÷ 255 | #0 ÷ 255 | #0 ÷ 255 | #0 ÷ 255 | #0 ÷ 255 |
| Received Data Buffer | Reserve for Intermediate Calculations | |||||
|---|---|---|---|---|---|---|
| N | Part 1 | Part 2 | … | Part 30 | Results 1 | Results 2 |
| #A18–A16: | #000b | 000b | … | 000b | 000b | 000b |
| #SB (A15–A8): | #111b | #111b | … | #111b | #111b | #111b |
| #LB (A7–A0): | #0–7 | #8–15 | … | #233–239 | #240–247 | #248–255 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bykovsky, A. Multiple-Valued Logic, Vocabulary Structure, and Linked List for Data Verification in Dialog Communications of Agents. Appl. Sci. 2025, 15, 2427. https://doi.org/10.3390/app15052427
Bykovsky A. Multiple-Valued Logic, Vocabulary Structure, and Linked List for Data Verification in Dialog Communications of Agents. Applied Sciences. 2025; 15(5):2427. https://doi.org/10.3390/app15052427
Chicago/Turabian StyleBykovsky, Alexey. 2025. "Multiple-Valued Logic, Vocabulary Structure, and Linked List for Data Verification in Dialog Communications of Agents" Applied Sciences 15, no. 5: 2427. https://doi.org/10.3390/app15052427
APA StyleBykovsky, A. (2025). Multiple-Valued Logic, Vocabulary Structure, and Linked List for Data Verification in Dialog Communications of Agents. Applied Sciences, 15(5), 2427. https://doi.org/10.3390/app15052427





