A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing
Abstract
1. Introduction
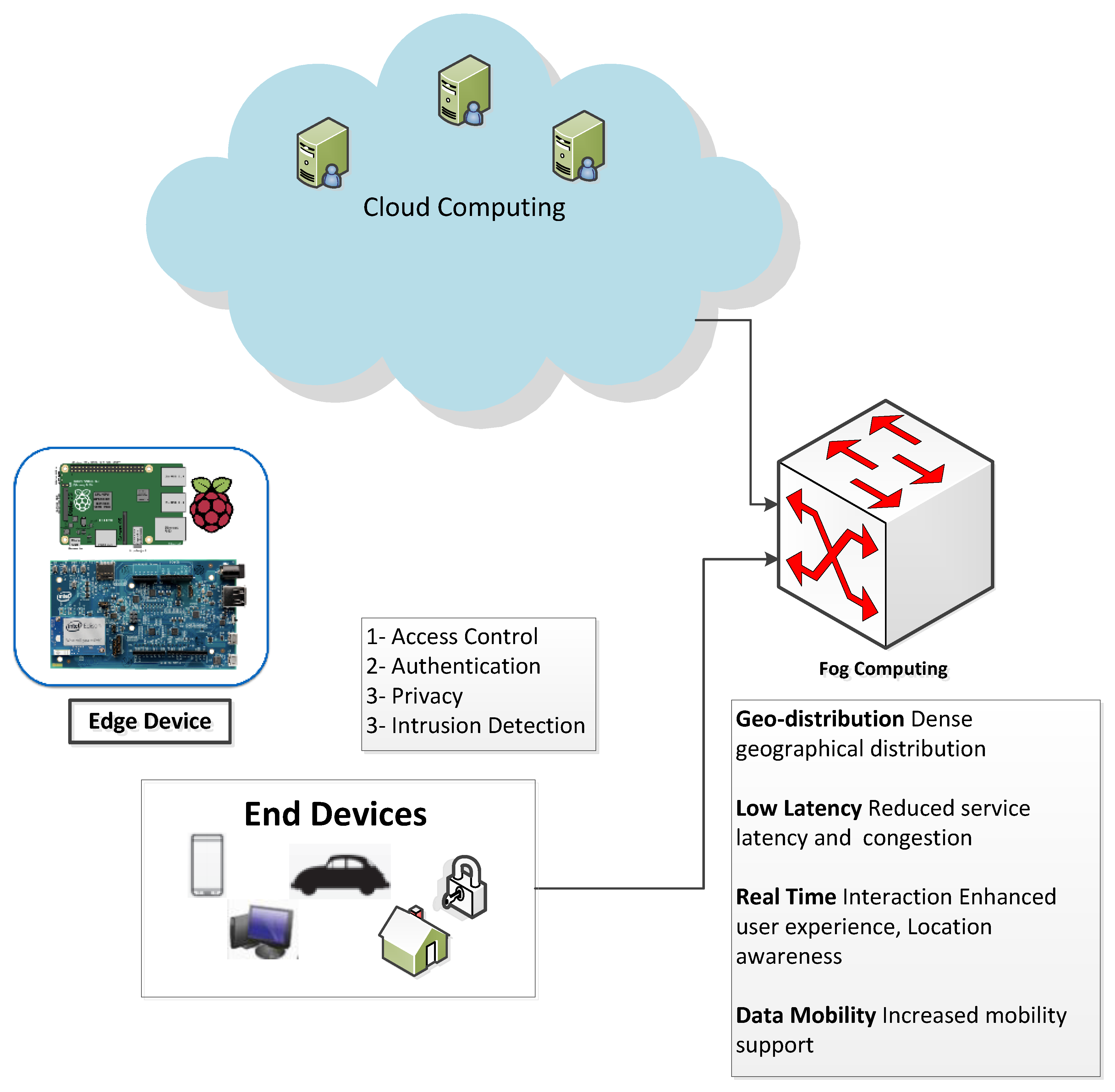
1.1. Fog Computing and IoT
- Internet of Things (IoT) and Internet of Everything (IoE) verticals: use cases include smart city, smart grid, smart connected vehicle, healthcare, and medical IoT etc.
- Orchestration Layer: it provides dynamic, policy-based life-cycle management and supports data aggregation, decisions, data sharing and migration.
- Abstraction Layer: the role of this layer is to expose a uniform and programmable interface for efficient management and hide the platform heterogeneity.
1.2. The Work Contribution
- Using a modern dataset, ADFA-LD and ADFA-WD, instead of the out-dated KDD Cup 99 dataset.
- Implementing algorithms with low computational complexity for feature extraction and selection.
- Using a single hidden layer MLP for practical detection time.
- Achieving a good detection rate relative to models used on the cloud.
- Testing the performance on a fog node (Raspberry Pi 3).
2. Related Work
2.1. Security Challenges
- Access Control: Issues in access control can result from a normal user being allowed to access sensitive data or having administrative privileges to change the system configurations. This issue could occur due to poor management and the distributive nature of the fog makes this task more challenging.
- Authentication: Authentication is the task of allowing only authorized users to access the fog system and it is more critical since the fog services are offered to a large number of end users. For instance, using biometric authentication, such as fingerprint, face, and touch-based authentications could prove to be very useful in the fog systems authentication. The resource-constrained IoT devices can delegate the authentication process to a fog device which in turn performs the cryptographic operations needed by the authentication protocol.
- Privacy: Users typically are concerned about their data privacy, usage pattern, and location privacy. Since fog nodes are located in the vicinity with the end users there is a significant risk of breaching the privacy using the information collected regarding identity, usage, and location.
- Intrusion Detection: Fog systems are also vulnerable to classical network attacks such as man-in-the-middle attack, flooding attack, and port scanning. In fog computing, it is essential to deploy IDS in the nodes to facilitate the intrusion detection on both the client’s side and the centralized cloud’s side.
2.2. Work in IoT Security
3. Proposed Method
- Phase 1: this phase is about the data preprocessing which includes the feature extraction and selection.
- Phase 2: this is the model selection phase.
- Phase 3: it is about the performance evaluation in terms of detection rate and CPU time on a Raspberry Pi.
3.1. Phase 1: Preprocessing
3.1.1. Feature Extraction
3.1.2. Feature Selection
- Filter method: It is performed by ranking the features based on their relevance using criteria like correlation, χ2 or information value.
- Wrapper method: It evaluates different subset of features and chooses the one with best performance.
- Embedded method: It allows the algorithm to choose the best subset of features and then performs classification.
3.2. Phase 2: Modeling
4. Experimental Setup
4.1. ADFA-LD and ADFA-WD Dataset
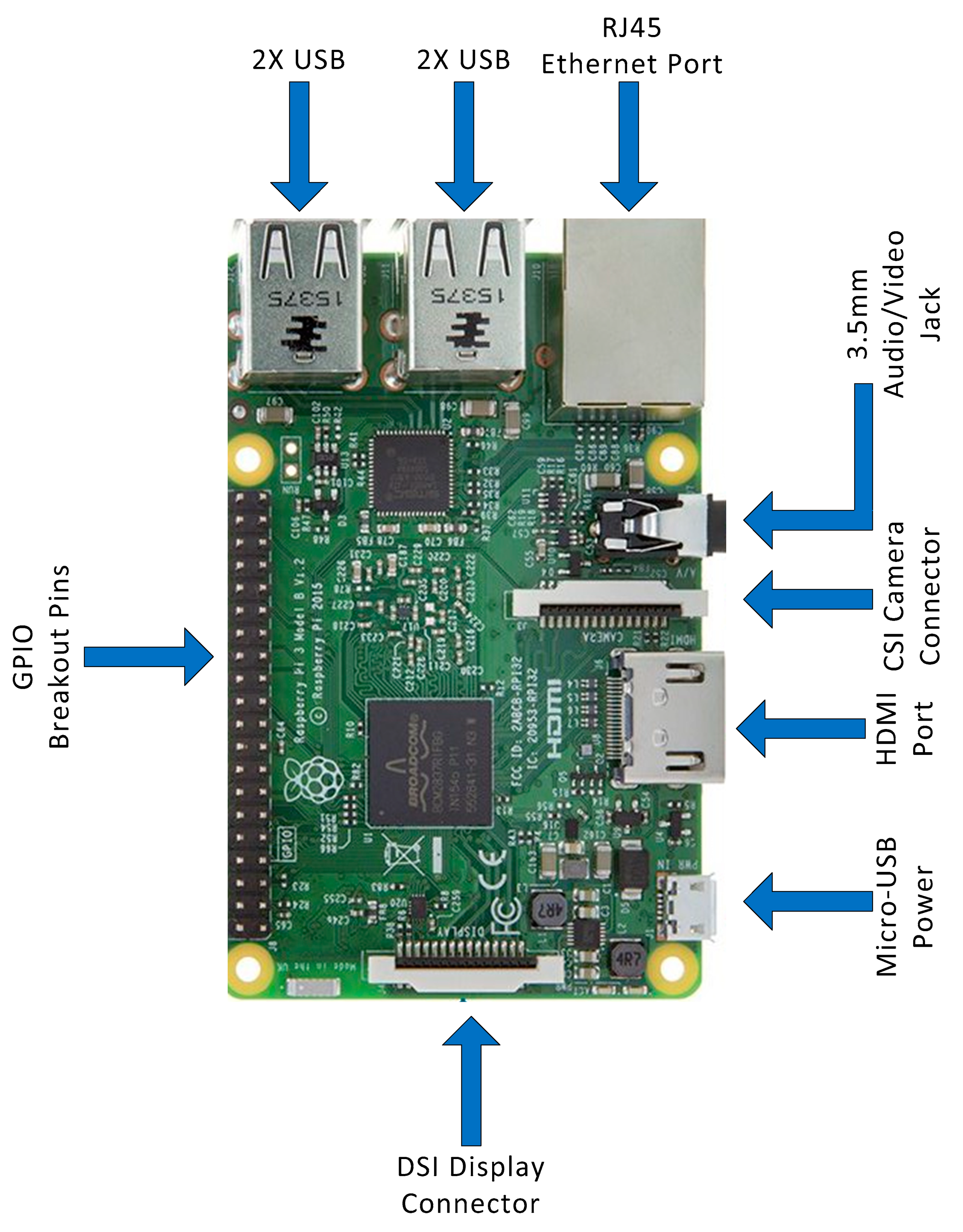
4.2. Software and Platform
- A 1.2 GHz 64-bit quad-core ARMv8 CPU.
- 1 GB of RAM.
- SD card, 16GB, class 10.
- 4 USB ports.
- 40 GPIO pins.
- Full HDMI port and Ethernet port.
- Video Core IV 3D graphics core.
4.3. Evaluation Metrics
- True Positive (TP): Number of positive (attack) traces detected as positive (attack) traces.
- True Negative (TN): Number of negative (normal) traces detected as negative (normal) traces.
- False Positive (FP): Number of positive (attack) traces detected as negative (normal) traces.
- False Negative (FN): Number of negative (normal) traces detected as positive (attack) traces.
5. Results
Performance on the Raspberry Pi
6. Conclusions
7. Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Computing, F. The internet of things: Extend the cloud to where the things are. In Cisco White Paper; Cisco: Charlotte, NC, USA, 2015. [Google Scholar]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog computing: A platform for internet of things and analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Springer: Cham, UAE, 2014; pp. 169–186. [Google Scholar]
- Dsouza, C.; Ahn, G.-J.; Taguinod, M. Policy-driven Security Management for Fog Computing: Preliminary Framework and a Case Study. In Proceedings of the 2014 IEEE 15th International Conference on Information Reuse and Integration (IRI), Redwood City, CA, USA, 13–15 August 2014; pp. 16–23. [Google Scholar]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M.; Al-Bahri, M. A Lightweight Anomaly Detection Technique for Low-resource IoT Devices: A Game-theoretic Methodology. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- An, X.; Zhou, X.; Lü, X.; Lin, F.; Yang, L. Sample selected extreme learning machine based intrusion detection in fog computing and MEC. Wirel. Commun. Mob. Comput. 2018, 2018, 7472095. [Google Scholar] [CrossRef]
- Hosseinpour, F.; Vahdani Amoli, P.; Plosila, J.; Hämäläinen, T.; Tenhunen, H. An intrusion detection system for fog computing and IoT based logistic systems using a smart data approach. Int. J. Digit. Content Technol. Appl. 2016, 10, 34–46. [Google Scholar]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog computing for the internet of things: Security and privacy issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S. The Fog Computing Paradigm: Scenarios and Security Issues. In Proceedings of the 2014 Federated Conference on Computer Science and Information Systems (FedCSIS), Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar]
- Lee, K.; Kim, D.; Ha, D.; Rajput, U.; Oh, H. On Security and Privacy Issues of Fog Computing Supported Internet of Things Environment. In Proceedings of the 2015 6th International Conference on the Network of the Future (NOF), Montreal, QC, Canada, 30 September–2 October 2015; pp. 1–3. [Google Scholar]
- Wang, Y.; Uehara, T.; Sasaki, R. Fog Computing: Issues and Challenges in Security and Forensics. In Proceedings of the 2015 IEEE 39th Annual Computer Software and Applications Conference (COMPSAC), Taichung, Taiwan, 1–5 July 2015; pp. 53–59. [Google Scholar]
- Chiang, M.; Zhang, T. Fog and IoT: An overview of research opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Markakis, E.K.; Karras, K.; Sideris, A.; Alexiou, G.; Pallis, E. Computing, caching, and communication at the edge: the cornerstone for building a versatile 5G ecosystem. IEEE Commun. Mag. 2017, 55, 152–157. [Google Scholar] [CrossRef]
- Calabretta, M.; Pecori, R.; Vecchio, M.; Veltri, L. MQTT-Auth: A token-based solution to endow MQTT with authentication and authorization capabilities. J. Commun. Softw. Syst. 2018, 14, 320–331. [Google Scholar] [CrossRef]
- Napiah, M.N.; Idris, M.Y.I.B.; Ramli, R.; Ahmedy, I. Compression header analyzer intrusion detection system (CHA-IDS) for 6LoWPAN communication protocol. IEEE Access 2018, 6, 16623–16638. [Google Scholar] [CrossRef]
- Goeschel, K. Reducing False Positives in Intrusion Detection Systems Using Data-mining Techniques Utilizing Support Vector Machines, Decision Trees, and Naive Bayes for Off-line Analysis. In Proceedings of the SoutheastCon 2016, Norfolk, VA, USA, 30 March–3 April 2016; pp. 1–6. [Google Scholar]
- Kim, G.; Lee, S.; Kim, S. A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Syst. Appl. 2014, 41, 1690–1700. [Google Scholar] [CrossRef]
- Alharbi, S.; Rodriguez, P.; Maharaja, R.; Iyer, P.; Subaschandrabose, N.; Ye, Z. Secure the Internet of Things with Challenge Response Authentication in Fog Computing. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–2. [Google Scholar]
- Ham, H.-S.; Kim, H.-H.; Kim, M.-S.; Choi, M.-J. Linear SVM-based android malware detection for reliable IoT services. J. Appl. Math. 2014, 2014, 594501. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Machine learning methods for attack detection in the smart grid. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 1773–1786. [Google Scholar] [CrossRef]
- Pajouh, H.H.; Javidan, R.; Khayami, R.; Ali, D.; Choo, K.-K.R. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Trans. Emerg. Top. Comput. 2016. [Google Scholar] [CrossRef]
- Meidan, Y.; Bohadana, M.; Shabtai, A.; Guarnizo, J.D.; Ochoa, M.; Tippenhauer, N.O.; Elovici, Y. ProfilIoT: A Machine Learning Approach for IoT Device Identification based on Network Traffic Analysis. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 506–509. [Google Scholar]
- Lee, S.-Y.; Wi, S.-R.; Seo, E.; Jung, J.-K.; Chung, T.-M. ProFiOt: Abnormal Behavior Profiling (ABP) of IoT Devices based on a Machine Learning Approach. In Proceedings of the 2017 27th International Telecommunication Networks and Applications Conference (ITNAC), Melbourne, Australia, 22–24 November 2017; pp. 1–6. [Google Scholar]
- Ge, M.; Hong, J.B.; Guttmann, W.; Kim, D.S. A framework for automating security analysis of the internet of things. J. Netw. Comput. Appl. 2017, 83, 12–27. [Google Scholar] [CrossRef]
- Shen, S.; Huang, L.; Zhou, H.; Yu, S.; Fan, E.; Cao, Q. Multistage signaling game-based optimal detection strategies for suppressing malware diffusion in fog-cloud-based IoT networks. IEEE Internet Things J. 2018, 5, 1043–1054. [Google Scholar] [CrossRef]
- Borisaniya, B.; Patel, D. Evaluation of modified vector space representation using adfa-ld and adfa-wd datasets. J. Inf. Secur. 2015, 6, 250. [Google Scholar] [CrossRef]
- Xie, M.; Hu, J.; Yu, X.; Chang, E. Evaluating Host-based Anomaly Detection Systems: Application of the Frequency-based Algorithms to Adfa-ld. In Proceedings of the International Conference on Network and System Security, Xiamen, China, 19–21 August 2014; pp. 542–549. [Google Scholar]
- Xie, M.; Hu, J.; Slay, J. Evaluating Host-based Anomaly Detection Systems: Application of the One-class Svm Algorithm to Adfa-ld. In Proceedings of the 2014 11th International Conference on Fuzzy Systems and Knowledge Discovery (FSKD), Xiamen, China, 19–21 August 2014; pp. 978–982. [Google Scholar]
- Creech, G. Developing a High-Accuracy Cross Platform Host-Based Intrusion Detection System Capable of Reliably Detecting Zero-Day Attacks. Ph.D. Thesis, University of New South Wales, Canberra, Australia, 2014. [Google Scholar]
- Creech, G.; Hu, J. A semantic approach to host-based intrusion detection systems using contiguousand discontiguous system call patterns. IEEE Trans. Comput. 2014, 63, 807–819. [Google Scholar] [CrossRef]
- Manning, C.D.; Raghavan, P.; Schütze, H. Introduction to Information Retrieval; Cambridge University Press: Cambridge, UK, 2008; Volume 1. [Google Scholar]
- Leslie, C.; Eskin, E.; Noble, W.S. The spectrum kernel: A string kernel for SVM protein classification. In Biocomputing 2002; World Scientific: Singapore, 2001; pp. 564–575. [Google Scholar]
- Wang, J.T.-L.; Ma, Q.; Shasha, D.; Wu, C.H. New techniques for extracting features from protein sequences. IBM Syst. J. 2001, 40, 426–441. [Google Scholar] [CrossRef]
- Data, L.F.; Course, A.S.; Abu-Mostafa, Y.S.; Magdon-Ismail, M.; Lin, H.-T.I. Scholarly Activity. In Proceedings of the 12th Conference on Electronic Commerce (EC), Valencia, Spain, 4–8 June 2012. [Google Scholar]
- Creech, G.; Hu, J. Generation of a New IDS Test Dataset: Time to Retire the KDD Collection. In Proceedings of the 2013 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 4487–4492. [Google Scholar]
- Haider, W.; Creech, G.; Xie, Y.; Hu, J. Windows based data sets for evaluation of robustness of host based intrusion detection systems (IDS) to zero-day and stealth attacks. Future Internet 2016, 8, 29. [Google Scholar] [CrossRef]
- Xie, M.; Hu, J. Evaluating Host-based Anomaly Detection Systems: A Preliminary Analysis of Adfa-ld. In Proceedings of the 2013 6th International Congress on Image and Signal Processing (CISP), Hangzhou, China, 16–18 December 2013; pp. 1711–1716. [Google Scholar]
- Abubakar, A.I.; Chiroma, H.; Muaz, S.A.; Ila, L.B. A review of the advances in cyber security benchmark datasets for evaluating data-driven based intrusion detection systems. Procedia Comput. Sci. 2015, 62, 221–227. [Google Scholar] [CrossRef]
- Borthakur, D.; Dubey, H.; Constant, N.; Mahler, L.; Mankodiya, K. Smart Fog: Fog Computing Framework for Unsupervised Clustering Analytics in Wearable Internet of Things. In Proceedings of the 2017 IEEE Global Conference on Signal and Information Processing (GlobalSIP), Montreal, QC, Canada, 14–16 November 2017; pp. 472–476. [Google Scholar]
- Constant, N.; Borthakur, D.; Abtahi, M.; Dubey, H.; Mankodiya, K. Fog-assisted wiot: A smart fog gateway for end-to-end analytics in wearable internet of things. arXiv, 2017; arXiv:1701.08680. [Google Scholar]
- Lavassani, M.; Forsström, S.; Jennehag, U.; Zhang, T. Combining fog computing with sensor mote machine learning for industrial IoT. Sensors 2018, 18, 1532. [Google Scholar] [CrossRef] [PubMed]
- Learning U. Raspberry Pi 3: Get Started with Raspberry Pi 3 a Simple Guide TO Understanding and Programming Raspberry Pi 3 (Raspberry Pi 3 User Guide, Python Programming, Mathematica Programming); CreateSpace Independent Publishing Platform: Scotts Valley, CA, USA, 2016.









| c | f(c) | w(c) |
|---|---|---|
| (6, 174) | 2 | 0.143 |
| (174, 174) | 3 | 0.214 |
| (174, 6) | 2 | 0.143 |
| (6, 45) | 1 | 0.071 |
| (45, 33) | 1 | 0.071 |
| (33, 192) | 2 | 0.143 |
| (192, 33) | 1 | 0.071 |
| (192, 174) | 1 | 0.071 |
| Dataset | No. of Traces ADFA-LD | No. of Traces ADFA-WD | Class of Traces |
|---|---|---|---|
| TRAINING_DATA_MASTER | 833 | 355 | Normal |
| VALIDATION_DATA_MASTER | 4372 | 1827 | Normal |
| ATTACK_DATA_MASTER | 746 | 5542 | Attack |
| Attack Type | Attack Payload Description | Vector | Traces Count |
|---|---|---|---|
| Adduser | Add new superuser using poisoned executables | Client side poisoned executable | 91 |
| Hydra-FTP | Bruteforce password guess on FTP port | FTP by Hydra | 162 |
| Hydra-SSH | Bruteforce password guess on SSH port | SSH by Hydra | 176 |
| Java-Meterpreter | Java based Meterpreter exploit | TikiWiki vulnerability exploit | 124 |
| Meterpreter | Linux Meterpreter exploit | Client side poisoned executable | 75 |
| Webshell | Privilege escalation using C100 Webshell | PHP remote file inclusion vulnerability | 118 |
| ID | Vulnerability | Program | Exploit Mechanism | Trace Count |
|---|---|---|---|---|
| V1 | CVE: 2006-2961 | CesarFTP 0.99g | Reverse Ordinal Payload Injection | 454 |
| V2 | EDB-ID: 18367 | XAMPP Lite v1.7.3 | Upload and execute malicious payload using Xampp_webdav | 470 |
| V3 | CVE: 2004-1561 | Icecast v2.0 | Metasploit exploit | 382 |
| V4 | CVE: 2009-3843 | Tomcat v6.0.20 | Metasploit exploit | 418 |
| V5 | CVE: 2008-4250 | OS SMB | Metasploit exploit | 355 |
| V6 | CVE: 2010-2729 | OS Print Spool | Metasploit exploit | 454 |
| V7 | CVE: 2011-4453 | PMWiki v2.2.30 | Metasploit exploit | 430 |
| V8 | CVE: 2012-0003 | Wireless Karma | DNS Spoofing using Pineapple Router | 487 |
| V9 | CVE: 2010-2883 | Adobe Reader 9.3.0 | Reverse Shell spawn through malicious PDF | 440 |
| V10 | ----- | Backdoor executable | Reverse Inline Shell spawned | 536 |
| V11 | CVE: 2010-0806 | IE v6.0.2900.2180 | Metasploit exploit | 495 |
| V12 | ----- | Infectious Media | Blind Shell spawned | 621 |
| No. of Nodes | ADFA-LD | ADFA-WD | ||
|---|---|---|---|---|
| CPU-Time (Testing) | Energy Joule | CPU-Time (Testing) | Energy Joule | |
| 2 hidden nodes | 751 μsec. | 0.001502037 | 741 μsec. | 0.00148201 |
| 3 hidden nodes | 756 μsec. | 0.001512051 | 746 μsec. | 0.001492023 |
| 4 hidden nodes | 753 μsec. | 0.001505852 | 769 μsec. | 0.001538277 |
| 5 hidden nodes | 704 μsec. | 0.0014081 | 684 μsec. | 0.001368046 |
| 6 hidden nodes | 817 μsec. | 0.001634121 | 779 μsec. | 0.001558304 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sudqi Khater, B.; Abdul Wahab, A.W.B.; Idris, M.Y.I.B.; Abdulla Hussain, M.; Ahmed Ibrahim, A. A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing. Appl. Sci. 2019, 9, 178. https://doi.org/10.3390/app9010178
Sudqi Khater B, Abdul Wahab AWB, Idris MYIB, Abdulla Hussain M, Ahmed Ibrahim A. A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing. Applied Sciences. 2019; 9(1):178. https://doi.org/10.3390/app9010178
Chicago/Turabian StyleSudqi Khater, Belal, Ainuddin Wahid Bin Abdul Wahab, Mohd Yamani Idna Bin Idris, Mohammed Abdulla Hussain, and Ashraf Ahmed Ibrahim. 2019. "A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing" Applied Sciences 9, no. 1: 178. https://doi.org/10.3390/app9010178
APA StyleSudqi Khater, B., Abdul Wahab, A. W. B., Idris, M. Y. I. B., Abdulla Hussain, M., & Ahmed Ibrahim, A. (2019). A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing. Applied Sciences, 9(1), 178. https://doi.org/10.3390/app9010178





