Governance, Risk, and Compliance in Cloud Scenarios
Abstract
:Featured Application
Abstract
1. Introduction
- (a)
- The act or process of complying to a desire, demand, proposal, or regimen or to coercion and;
- (b)
- conformity in fulfilling official requirements.
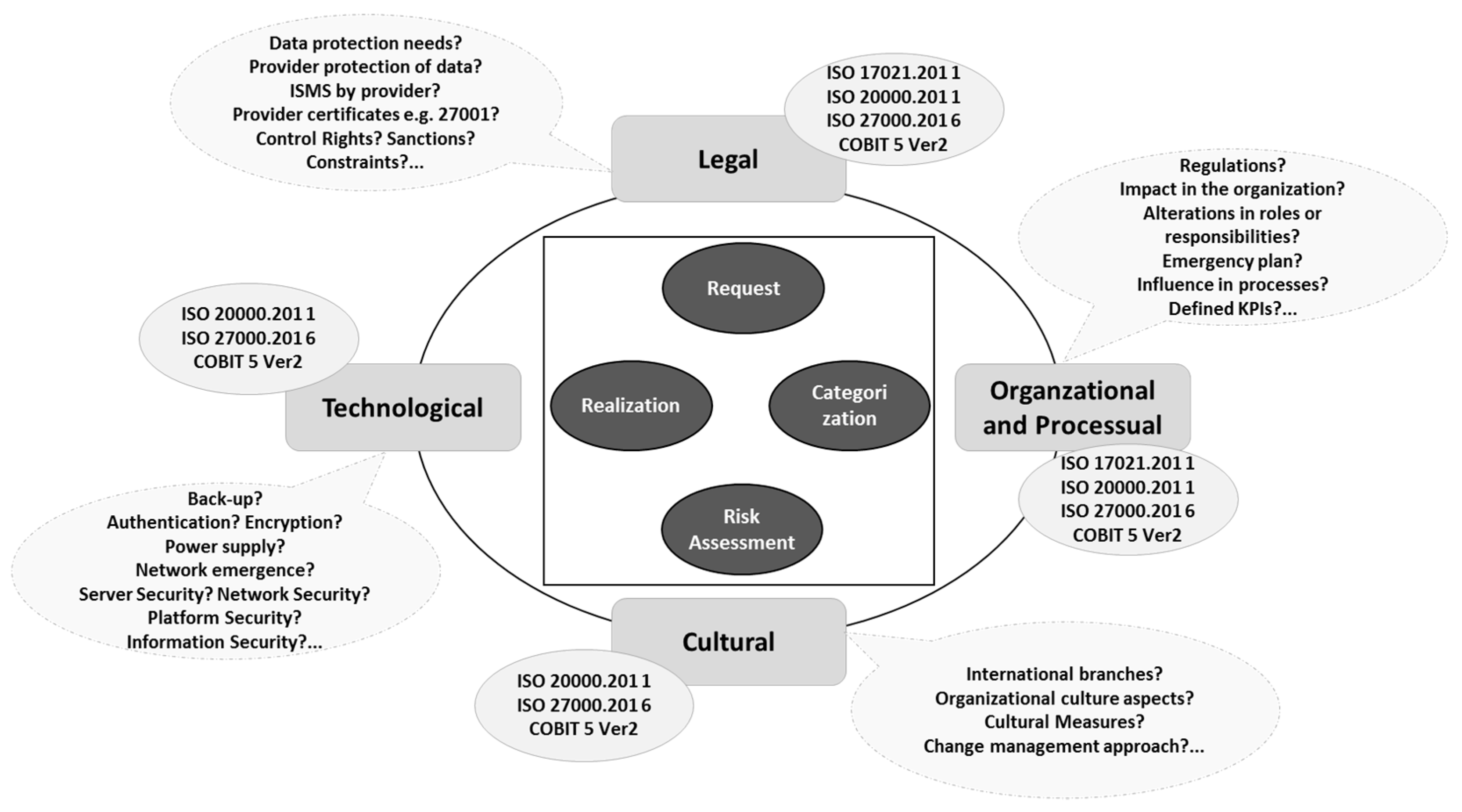
2. The Framework
2.1. Rationale and Summary
2.1.1. Legal
- What types of data are influenced by the subcontracting approach? Significant data, such as health, social, or private clinical data?
- What types of legitimate outlines can be used?
- What are the possibilities if subcontracting takes place: Either of data being available, confidential, or integrable?
- What are the necessities to protect the data? Deciding on suitable security architecture, encryption and cryptography of data, authorization management, managing potential risks, management of the occurrences of security issues, measuring and planning of contingency, and other concerns regarding the data protection.
- Whether the legal and data protection necessities are met by the provider?
- Whether the supplier has the required information security management system (ISMS)?
- Measuring the extent to which the ISMS is assessed with respect to the suitability of the technical and organizational level and how are the outcomes are documented?
- Whether the supplier has the required up-to-date and international certificates (for example, ISO 27001)?
- Whether the cloud computing service is formulated neatly and obviously or not?
- Whether the control rights of the organization using the cloud along with the required obligations for the supplier of the cloud service are specified or not?
- Are there some rules supporting the probable operations and the retrieval of data if the cloud service provider commits any bankruptcy?
- Whether any explicit and appropriate service-level agreement are available? If yes, whether they ensure the requirement of availability and dependability, deadlines for restoration and response, computing power, and support specifics?
- In case of disastrous failures, are there any particular business community management (BCM) guidelines?
- Whether controls are carried out regularly? Additionally, whether there exists any evaluations of the agreed upon technical and organizational measures?
- Whether the security aspects are being assessed regularly and whether they are up-to-date and belong to the recent state of the art?
- Whether the international data communication is influenced by the adjustments?
- Whether sanctions are foretasted?
- Whether any access points exist for state agencies (e.g., National Security Agency, NSA)?
- Whether there exist any specific constraints?
2.1.2. Organizational and Processual
- What effects do the alterations have over other processes?
- What effects do these alterations have over the corporate strategy?
- Whether the consideration of security concepts is assured when the alterations are taking place?
- Whether the changes are well planned, evaluated, accepted, and documented?
- Whether the alternative solutions are produced before the development of the changes?
- Whether the information security management is taken into consideration in all the alterations?
- What is the level of data availability?
- What is its influence on other activities?
- Evaluation of the most recent emergency tests documents.
- Security aspects.
- Regular security valuations at the Content Security Policy (CSP) and other suppliers by a qualified third party.
- Authentication, authorization, administration, inspections, and attentiveness access control.
- Processing the data is only permitted based on the guidelines of the cloud user and the usage of data by the CSP for their own purposes is not allowed.
- Test of influence of the CSP and other providers.
- The cloud user should be able to monitor and they should be able to prove the service level agreement (SLA) fulfilment.
- The administrative processes should be monitored and logged.
- Four-eyes-principle at the time of significant administration processes.
- CSP preparation of log files.
- Information about security events.
- Round the clock response group available for security event management and troubleshooting.
- Round the clock handling of cloud services and a rapid response to security events.
- Employment of appropriate measures in contradiction of domestic intimidations that are characteristic of a multi-tenant architecture.
- Formation of transparency and trust by the establishment of thorough information anticipated for the cloud user.
- Measures at the employees’ level.
- Police certificate/clean criminal record.
- Educational history, qualifications, and present and previous affiliations.
- Personal setting (e.g., party membership).
- IT security courses.
- Social engineering courses.
- Control and education for the purpose of understanding.
- Assessment of workers (e.g., technicians, facility managers).
- Agreement for data security and non-disclosure.
- Corresponding to their fields, e.g., “governance activities”,” customer-facing activities”, “core activities”, and “support activities”;
- Corresponding to their inevitability and significance, e.g., “must do”, “nice-to-have”, “delighter”.
2.1.3. Technological
- Host protection (firewall, intrusion detection, integrity examination).
- Secure standard configuration (strengthen operating system).
- Sandboxed environment for each virtual machine.
- Certified hypervisors (at least CC EAL4, IT SEC E3), avoiding hyperjacking and including embedded hypervisors.
- Superfluous images/services of the provider.
- A protected sandbox environment in the case of Infrastructure as a Service (IaaS) to avoid the harnessing of host systems.
- Systems ready for valuation of system documentation, status, and log files.
- Superfluous network links.
- Protections against attacks, malware, and viruses.
- Safe configuration of all cloud components, network division.
- Encrypted remote supervision.
- Encrypted communication between Content Security Policy (CSP) and the cloud user.
- Encrypted communication between various Cloud Computing (CC) sites.
- Encrypted communication to and from third-party servicers.
- Encrypted transmission of network management information.
- Evaluation of virtual private network (VPN) infrastructure and end-to-end encryption (E2EE) chain (including man-in-the-middle attacks and backdoors).
- Incorporation of security in various activities namely, software life cycle, security gateways, vulnerability evaluation, code reviews, and audits.
- The isolation of application and monitoring of the interface.
- Automatically monitoring and assessing the user applications.
- Management of the patch and change and the compatibility test of patch.
- Checking if the secure application development is carried out according to the guidelines or not.
- Management of patch and change.
- Customer data life cycle definition.
- Isolating securely.
- Information access based on role, for example, based on Lightweight Directory Access Protocol (LDAP).
- Routine backups (extent, intervals, storage concept, times, and durations).
- Secure and complete removal.
- Every element of the system can be aimed at by an attack; hence, weaknesses and protection analysis.
- Measures are required (end-to-end security).
- Methods to be used are supposed to be assured and encrypted securely.
- Keys should be randomly generated with enough key length.
- The exchange of keys should be secure and asynchronous.
- The length of the keys should be short and their storage should be secure.
- Destruction of keys, for example, using Security Assertion Markup Language (SAML).
- Rigor verification of users in the cloud (two-factor authentication).
- The customer should make sure the service supplier utilizes standardized technology and interfaces; this should be stated in its early stage of contract.
- Mix cloud methods to prevent compatibility issues between the cloud and IT systems in the customer’s organization.
2.1.4. Cultural
- What are the countries in which the main offices and branches of the organization are based?
- What are the countries that the main accounts of the organization are included?
- To what extent does the organization reach to the markets (regional, national, international, and world-wide)?
- What are the existing cultural aspects to consider (e.g., a religious or non-profit organization, military, or other certain organizational surroundings)?
- What are the related cultural aspects (based on Hofstede and following works) for the organization?
- What are the measures for the related cultural aspects that may be required?
- How are the required measures of the related cultural aspect accumulated?
- What is the relevancy of every related cultural aspect for change management?
- How are the related measures supposed to be considered while the change is carried out?
- What are the related national cultural aspects to consider?
- What are the most relevant organizational culture aspects?
2.1.5. The Inner Works
- Identifying the significant information and procedures as main assets of the organization.
- Identifying the secondary assets for the association along with metrics (inheritance).
- Description of security requirements for reflected information in cloud computing as well as the definition of total risk according to the potential harm and possibility.
- Present status: Measures that already existed.
- Assessment of risk of current measures and of reflected alteration (total risk).
- Steps remaining and new measures or controls.
- Low. The effect of possible damage or harm is partial and foreseeable.
- Medium. The effect of possible damage or harm may be substantial.
- High. The effect of possible damage or harm may be of disastrous extents, which could intimidate the very existence of the organization.
- Legal: Disruptions of rules, guidelines, or agreements. Damage of the right to informational self-determination.
- Organizational/processual: Damaged ability to carry out the ongoing tasks, damage of business processes or activities, physical harm.
- Technical: Removal of a certain technology from the accepted assets list due to compromised security.
- Cultural: Negative external or internal impacts, cultural confusions.
- Financial penalties.
2.2. Validation of the Framework by Experts
2.2.1. Validation of the Items
- Whether the provided framework is an adequate tool to describe risks?
- Whether there are other fields for affections or risks for cloud computing/cloud services?
- If yes, what are these other fields?
- What is the significance of each of the provided fields from the point of view of the experts?
- Are questionnaires sufficient to find inputs in the certain subject area for the goal of risk evaluation of the framework?
- Whether there are any questions that are imprecisely expressed or other explanations are necessary?
- Whether there are any questions that are not essential or unnecessary and hence should be deleted from the questionnaire?
- Are there any related questions that have not been taken into account until now and should therefore be added to the questionnaire?
- Are there any more comments or recommendations.
- There is a need for concise description of the legal fields considered by the experts, e.g., the description of “change”.
- The professionals from the processual and organizational field focused on the requirement of precise procedure classifications from the organizational point of view (e.g., “governance processes”, “core processes”, “support processes”) and from the point of view of their essentiality (“must-do”, “nice-to-have”, “delighter”). Adding to that, they underlined the significance of KPIs relevant to particular techniques and suggested an extended quantification-oriented method of the questionnaire.
- The experts from the technological field emphasized the significance of technological developments and advancements and of particular employment and implementation methods.
- The experts from the cultural field identified additional potential fields of affection (military, politics) and emphasized the significance of particular cultural aspects in certain countries or cultures.
2.2.2. Validation of the Framework as a Whole
- Correctness in the focus of the framework.
- Opinion on the methodology adopted.
- Opinion on the theoretical contribution of the framework.
- Opinion on the applicability of the framework.
- Opinion on the artefacts (questionnaires) included.
- Framework goals: All chosen professionals have encouragingly evaluated the main objective of the framework. The experts know that because of the generalization of cloud computing and the rising stress on compliance management, research to encourage an awareness and exercise of compliance is essential.
- Methodology: Experts have decided that the design and usage of qualitative methodological methods and literature reviews guarantee the building of a suitable framework.
- Theoretical innovation: Up to now, there is little literature devoted to the improvement of efficiency of the compliance procedure in cloud computing settings. The outcomes acquired from the implementation of the framework will signify an improvement in the knowledge of the management of compliance issues. Accordingly, experts expect that the implementation of the framework will approve the relevance of the procedure and, at the same time, approve the requirement for frameworks to guide the management of these procedures.
- Applicability: It is possible to apply the result of implementing the framework to other projects and there is even the potential to generate the need to develop frameworks in order to guide other main processes in a cloud computing environment.
- Suggestions for improvement: According to the areas for development or manipulation, the following facets should be considered:
- One expert records the time taken in the questionnaires and the need to consider certain support for the implementation of the framework. He comments that to increase the effect of a potential future commercialization, there is a need for more automated support.
- Another expert is taking care of the maintainability of various dimensions of the framework. This subject thinks that some of the characteristics of the framework will experience volatility and obsolescence.
- A number of characteristics of the framework were stated by experts that will lead to the improvement of the questionnaires in terms of language to improve the readability. Therefore, the process led to several phrases that were rewritten based on the experts’ opinions.
3. Evaluation
- Increasing expenses for IT compliance because of the loss of the IT compliance function in the organization; and
- excessive risks linked with non-compliance that cannot be quantified at the moment.
- Increased capability in articulating its own IT compliance to present and potential customers; and
- to assure compliance of IT processes for customers with uppermost essentials, e.g., defense and intelligence agencies.
- To prevent the so called “conformity-gaps” between requirements and their real implementation in IT;
- implementing the changes in holistic, risk-oriented concerns of IT compliance;
- to govern the requirements and a higher level of standardization during the process of implementation (increase in maturity levels);
- to ensure the compliance of IT processes, for example, by closing existing non-compliance outcomes and an established compliance with current regulations; and
- decrease the probability of an occurrence and the possible harm of risks.
- Typical data on participant:
- ○
- Sex;
- ○
- age;
- ○
- position;
- ○
- years of professional experience; and
- ○
- years of experience in the position.
- Management of compliance.
- Level of overall satisfaction with compliance management in CC (Very satisfied; Satisfied; Neither; Dissatisfied; Very dissatisfied).
- Level of overall satisfaction with CC service (Very satisfied; Satisfied; Neither; Dissatisfied; Very dissatisfied).
- Level of overall insight on the influence of compliance management in CC on the quality of service of IT (Very High; Above Average; Average; Below Average; Very Low).
- Level of overall insight on the influence of compliance management in CC to the organizational compliance management procedures (Very High; Above Average; Average; Below Average; Very Low).
- Average time gap between identification of external compliance problems and resolution;
- number of compliance problems in which employees request direction or support;
- number of reports of unproven or actual compliance violations;
- percentage of compliance enhancement opportunities which are implemented; and
- frequency (in days) in reviews of compliance.
3.1. Case Study 1: Organization A
3.2. Case Study 2: Organization B
3.3. Inter Case
4. Discussion, Limitations, Conclusions, and Future Works
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Lunardi, G.L.; Becker, J.L.; Maçada, A.C.G.; Dolci, P.C. The impact of adopting IT governance on financial performance: An empirical analysis among Brazilian firms. Int. J. Account. Inf. Syst. 2014, 15, 66–81. [Google Scholar] [CrossRef]
- Mohamad, S.; Toomey, M. A survey of information technology governance capability in five jurisdictions using the ISO 38500:2008 framework. Int. J. Discl. Gov. 2016, 13, 53–74. [Google Scholar] [CrossRef]
- Juiz, C.; Toomey, M. To govern IT, or not to govern IT? Commun. ACM 2015, 58, 58–64. [Google Scholar] [CrossRef]
- Weill, P.; Ross, J.W. IT Governance: How Top Performers Manage IT Decision Rights for Superior Results; Harvard Business Press: Boston, MA, USA, 2004; ISBN 978-1-59139-253-8. [Google Scholar]
- Xue, Y.; Liang, H.; Boulton, W.R. Information Technology Governance in Information Technology Investment Decision Processes: The Impact of Investment Characteristics, External Environment, and Internal Context. MIS Q. 2008, 32, 67–96. [Google Scholar] [CrossRef]
- Luftman, J. Assessing It/Business Alignment. Inf. Syst. Manag. 2003, 20, 9–15. [Google Scholar] [CrossRef]
- Henderson, J.C.; Venkatraman, H. Strategic alignment: Leveraging information technology for transforming organizations. IBM Syst. J. 1993, 32, 472–484. [Google Scholar] [CrossRef]
- De Haes, S.; Van Grembergen, W.; Debreceny, R.S. COBIT 5 and Enterprise Governance of Information Technology: Building Blocks and Research Opportunities. J. Inf. Syst. 2013, 27, 307–324. [Google Scholar] [CrossRef]
- Banker, R.D.; Hu, N.; Pavlou, P.A.; Luftman, J. CIO Reporting Structure, Strategic Positioning, and Firm Performance. MIS Q. 2011, 35, 487–504. [Google Scholar] [CrossRef]
- Wu, S.P.-J.; Straub, D.W.; Liang, T.-P. How information technology governance mechanisms and strategic alignment influence organizational performance: Insights from a matched survey of business and IT managers. MIS Q. 2015, 39, 497–518. [Google Scholar] [CrossRef]
- Chi, M.; Zhao, J.; George, J.F.; Li, Y.; Zhai, S. The influence of inter-firm IT governance strategies on relational performance: The moderation effect of information technology ambidexterity. Int. J. Inf. Manag. 2017, 37, 43–53. [Google Scholar] [CrossRef]
- Alreemy, Z.; Chang, V.; Walters, R.; Wills, G. Critical success factors (CSFs) for information technology governance (ITG). Int. J. Inf. Manag. 2016, 36, 907–916. [Google Scholar] [CrossRef]
- COBIT 5: A Business Framework for the Governance and Management of Enterprise IT. Available online: http://www.isaca.org/cobit/ (accessed on 15 March 2017).
- Joshi, A.; Bollen, L.; Hassink, H.; De Haes, S.; Van Grembergen, W. Explaining IT governance disclosure through the constructs of IT governance maturity and IT strategic role. Inf. Manag. 2018, 55, 368–380. [Google Scholar] [CrossRef]
- Weill, P.; Ross, J. A matrixed approach to designing IT governance. MIT Sloan Manag. Rev. 2005, 46, 26–34. [Google Scholar]
- CMMI Product Team. CMMI for Service, Version 1.3, CMMI-SVC v1. 3; CMU/SEI-2010-TR-034, Technical Report; Software Engineering Institute: Pittsburgh, PA, USA, 2010. [Google Scholar]
- Bianchi, I.S.; Sousa, R.D. IT Governance Mechanisms in Higher Education. Procedia Comput. Sci. 2016, 100, 941–946. [Google Scholar] [CrossRef] [Green Version]
- Khouja, M.; Rodriguez, I.B.; Halima, Y.B.; Moalla, S. IT Governance in Higher Education Institutions: A Systematic Literature Review. Int. J. Hum. Cap. Inf. Technol. Prof. IJHCITP 2018, 9, 52–67. [Google Scholar] [CrossRef]
- Coen, M.; Kelly, U. Information management and governance in UK higher education institutions: Bringing IT in from the cold. Perspect. Policy Pract. High. Educ. 2007, 11, 7–11. [Google Scholar] [CrossRef]
- Grembergen, W.V.; Haes, S.D. IT Governance Structures, Processes and Relational Mechanisms: Achieving IT/Business Alignment in a Major Belgian Financial Group. In Proceedings of the 38th Annual Hawaii International Conference on System Sciences (HICSS), Big Island, HI, USA, 6 January 2005; Volume 8, p. 237b. [Google Scholar]
- Robb, A.; Parent, M. Understanding IT Governance: A Case of Two Financial Mutuals. J. Glob. Inf. Manag. JGIM 2009, 17, 59–77. [Google Scholar] [CrossRef]
- Pereira, R.; Almeida, R.; da Silva, M.M. IT Governance Patterns in the Portuguese Financial Industry. In Proceedings of the 2014 47th Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 6–9 January 2014; pp. 4386–4395. [Google Scholar]
- Campbell, J.; McDonald, C.; Sethibe, T. Public and private sector IT governance: Identifying contextual differences. Australas. J. Inf. Syst. 2010, 16, 5–18. [Google Scholar] [CrossRef]
- Wilkin, C.L.; Campbell, J.; Moore, S. Creating value through governing IT deployment in a public/private-sector inter-organisational context: A human agency perspective. Eur. J. Inf. Syst. 2013, 22, 498–511. [Google Scholar] [CrossRef]
- Ali, S.; Green, P. IT Governance Mechanisms in Public Sector Organisations: An Australian Context. J. Glob. Inf. Manag. JGIM 2007, 15, 41–63. [Google Scholar] [CrossRef]
- Pang, M.-S. IT governance and business value in the public sector organizations—The role of elected representatives in IT governance and its impact on IT value in U.S. state governments. Decis. Support Syst. 2014, 59, 274–285. [Google Scholar] [CrossRef]
- Andersen, K.V.; Larsen, M.H.; Pedersen, M.K. IT Governance: Reviewing 17 IT Governance Tools and Analysing the Case of Novozymes A/S. In Proceedings of the 39th Annual Hawaii International Conference on System Sciences (HICSS’06) (HICSS), Kauia, HI, USA, 4–7 January 2006; Volume 8, p. 195c. [Google Scholar]
- Dzombeta, S.; Stantchev, V.; Colomo-Palacios, R.; Brandis, K.; Haufe, K. Governance of Cloud Computing Services for the Life Sciences. IT Prof. 2014, 16, 30–37. [Google Scholar] [CrossRef]
- Deschoolmeester, D.; Devos, J.; Van Landeghem, H. Rethinking IT governance for SMEs. Ind. Manag. Data Syst. 2012, 112, 206–223. [Google Scholar] [Green Version]
- Garbarino-Alberti, H. IT Governance and Human Resources Management: A Framework for SMEs. Int. J. Hum. Cap. Inf. Technol. Prof. IJHCITP 2013, 4, 40–57. [Google Scholar] [CrossRef]
- Shiau, W.-L.; Chau, P.Y.K. Understanding behavioral intention to use a cloud computing classroom: A multiple model comparison approach. Inf. Manag. 2016, 53, 355–365. [Google Scholar] [CrossRef]
- Gartner Forecasts Worldwide Public Cloud Revenue to Grow 17.3 Percent in 2019. Available online: https://www.gartner.com/en/newsroom/press-releases/2018-09-12-gartner-forecasts-worldwide-public-cloud-revenue-to-grow-17-percent-in-2019 (accessed on 29 November 2018).
- Chang, V.; Ramachandran, M. Towards Achieving Data Security with the Cloud Computing Adoption Framework. IEEE Trans. Serv. Comput. 2016, 9, 138–151. [Google Scholar] [CrossRef]
- Ramachandran, M. Software security requirements management as an emerging cloud computing service. Int. J. Inf. Manag. 2016, 36, 580–590. [Google Scholar] [CrossRef] [Green Version]
- Huygh, T.; De Haes, S.; Joshi, A.; Van Grembergen, W. Answering key global IT management concerns through IT governance and management processes: A COBIT 5 View. In Proceedings of the 51st Hawaii International Conference on System Sciences, Hawaii, HI, USA, 3 January 2018; pp. 5335–5344. [Google Scholar]
- Kim, S. IT compliance of industrial information systems: Technology management and industrial engineering perspective. J. Syst. Softw. 2007, 80, 1590–1593. [Google Scholar] [CrossRef]
- Yimam, D.; Fernandez, E.B. A survey of compliance issues in cloud computing. J. Internet Serv. Appl. 2016, 7, 5. [Google Scholar] [CrossRef] [Green Version]
- van de Weerd, I.; Mangula, I.S.; Brinkkemper, S. Adoption of software as a service in Indonesia: Examining the influence of organizational factors. Inf. Manag. 2016, 53, 915–928. [Google Scholar] [CrossRef]
- Papanikolaou, N.; Pearson, S.; Mont, M.C.; Ko, R.K.L. A toolkit for automating compliance in cloud computing services. Int. J. Cloud Comput. 2014, 3, 45–68. [Google Scholar] [CrossRef]
- Hamdaqa, M.; Hamou-Lhadj, A. An approach based on citation analysis to support effective handling of regulatory compliance. Future Gener. Comput. Syst. 2011, 27, 395–410. [Google Scholar] [CrossRef]
- Kure, H.I.; Islam, S.; Razzaque, M.A. An Integrated Cyber Security Risk Management Approach for a Cyber-Physical System. Appl. Sci. 2018, 8, 898. [Google Scholar] [CrossRef]
- Wheeler, B.C. NEBIC: A Dynamic Capabilities Theory for Assessing Net-Enablement. Inf. Syst. Res. 2002, 13, 125–146. [Google Scholar] [CrossRef] [Green Version]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989, 13, 319–340. [Google Scholar] [CrossRef]
- Kluckhohn, F.R.; Strodtbeck, F.L. Variations in Value Orientations; Row, Peterson: Evanston, IL, USA, 1961; ISBN 978-0-8371-6740-4. [Google Scholar]
- Hofstede, G. Culture’s Consequences: Comparing Values, Behaviors, Institutions and Organizations Across Nations, 2nd ed.; SAGE Publications, Inc.: Thousand Oaks, CA, USA, 2003; ISBN 978-0-8039-7324-4. [Google Scholar]
- Taylor, S.; Lacy, S.; Macfarlane, I. ITIL Version 3 Service Transition; The Office of Government Commerce: San Diego, CA, USA, 2011. [Google Scholar]
- Shanteau, J. Competence in experts: The role of task characteristics. Organ. Behav. Hum. Decis. Process. 1992, 53, 252–266. [Google Scholar] [CrossRef]
- Aloqaily, M.; Kantarci, B.; Mouftah, H.T. A Generalized Framework for Quality of Experience (QoE)-Based Provisioning in a Vehicular Cloud. In Proceedings of the 2015 IEEE International Conference on Ubiquitous Wireless Broadband (ICUWB), Montreal, QC, Canada, 4–7 October 2015; pp. 1–5. [Google Scholar]
- Ridhawi, I.A.; Ridhawi, Y.A. QoS-Aware Service Composition in Mobile Cloud Networks. In Proceedings of the 2015 IEEE 7th International Conference on Cloud Computing Technology and Science (CloudCom), Vancouver, BC, Canada, 30 November–3 December 2015; pp. 448–453. [Google Scholar]
- Baker, T.; Asim, M.; Tawfik, H.; Aldawsari, B.; Buyya, R. An energy-aware service composition algorithm for multiple cloud-based IoT applications. J. Netw. Comput. Appl. 2017, 89, 96–108. [Google Scholar] [CrossRef]
- Aloqaily, M.; Balasubramanian, V.; Zaman, F.; Al Ridhawi, I.; Jararweh, Y. Congestion Mitigation in Densely Crowded Environments for Augmenting QoS in Vehicular Clouds. In Proceedings of the 8th ACM Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications, Montreal, QC, Canada, 28 October–2 November 2018; pp. 49–56. [Google Scholar]
- Baker, T.; Ugljanin, E.; Faci, N.; Sellami, M.; Maamar, Z.; Kajan, E. Everything as a resource: Foundations and illustration through Internet-of-things. Comput. Ind. 2018, 94, 62–74. [Google Scholar] [CrossRef]
- Roque, J.; Chauvel, L.; Aloqaily, M.; Kantarci, B. A Feasibility Study on Sustainability-Driven Infrastructure Management in Cloud Data Centers. In Proceedings of the 2018 IEEE Canadian Conference on Electrical Computer Engineering (CCECE), Quebec City, QC, Canada, 13–16 May 2018; pp. 1–4. [Google Scholar]
- Ridhawi, I.A.; Aloqaily, M.; Kotb, Y.; Ridhawi, Y.A.; Jararweh, Y. A collaborative mobile edge computing and user solution for service composition in 5G systems. Trans. Emerg. Telecommun. Technol. 2018, 29, e3446. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. Detection of Known and Unknown Intrusive Sensor Behavior in Critical Applications. IEEE Sens. Lett. 2017, 1, 1–4. [Google Scholar] [CrossRef]
- García-Crespo, Á.; Gómez-Berbís, J.M.; Colomo-Palacios, R.; Alor-Hernández, G. SecurOntology: A semantic web access control framework. Comput. Stand. Interfaces 2011, 33, 42–49. [Google Scholar] [CrossRef]
- Ghafir, I.; Saleem, J.; Hammoudeh, M.; Faour, H.; Prenosil, V.; Jaf, S.; Jabbar, S.; Baker, T. Security threats to critical infrastructure: The human factor. J. Supercomput. 2018, 74, 4986–5002. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. Mitigating False Negative intruder decisions in WSN-based Smart Grid monitoring. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 153–158. [Google Scholar]
- Stantchev, V.; Colomo-Palacios, R.; Niedermayer, M. Cloud Computing Based Systems for Healthcare. Sci. World J. 2014, 2014, e692619. [Google Scholar] [CrossRef] [PubMed]
- Otoum, S.; Kantarci, B.; Mouftah, H. Adaptively Supervised and Intrusion-Aware Data Aggregation for Wireless Sensor Clusters in Critical Infrastructures. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]

| Low | Medium | High | |
|---|---|---|---|
| Legal | Disruptions of guidelines and rules with slight consequences (slight breaks of agreement which result in at most inconsiderable contractual consequences). | Disruptions of guidelines and rules with considerable consequences (major breaks of agreement with high contractual consequences). | Major disruptions of guidelines and rules (breaks of contract with disastrous damage liabilities). |
| Organizational | Damage with no or few effects on business purposes, customers, or business partners. | Damage of the ability to carry out the tasks, so one or more business purposes will not succeed and there is a negative impact on customers and business partners. | Damage of the ability to carry out tasks was evaluated as unbearable and one or more major business purposes will not succeed and long term negative effects on customers and business partners. |
| Technical | There is no significant infrastructure or technology impacted. No key assets involved. | There is a single significant infrastructure or technology impacted. Single vulnerability of a standard infrastructural asset involved. | There are several significant infrastructures or technologies impacted. There are several vulnerabilities of standard infrastructural assets involved. |
| Cultural | There is no or little impact on cultural mentality in the organization or the customer base. | There is expected negative effects in 1-2 related aspects of the cultural mentality in the organization or the customer base. | There is an expected negative impact in more than two related aspects of the cultural mentality in the organization or the customer base. |
| Financial | The financial damage is substantial, but does not intimidate the existence of the organization. | The financial damage is significant, and could intimidate the existence of the organization. | The financial damage intimidates the existence of the organization. |
| Legal | Technological | Processual/Organizational | Cultural | |
|---|---|---|---|---|
| University Education | Master in Law or IT Management | Master in IT Management | Master in Management | Master in Management, Human Resource Management |
| Professional Knowledge | Business English Legal English | Business English Legal English (Optional) | Business English Legal English (Optional) | Business English Legal English (Optional) |
| Candidates contacted | 15 | 15 | 15 | 15 |
| Candidates selected | 4 | 3 | 5 | 3 |
| Phase I | Phase II | |||
|---|---|---|---|---|
| M | SD | M | SD | |
| Satisfaction on cloud services | 3.91 | .539 | 4.09 | .539 |
| Satisfaction on CM in cloud | 3.36 | .809 | 4.00 | .632 |
| CM contribution to IT quality of service | 3.09 | .701 | 3.73 | .786 |
| CM contribution to the organizational CM | 2.82 | .405 | 3.64 | .674 |
| Metric | Phase I | Phase II |
|---|---|---|
| Avg. time between identification of external compliance issues and resolution | 48 | 45 |
| # of compliance issues where employees seek guidance/assistance | 19 | 20 |
| # of reports of alleged or actual compliance violations | 89 | 60 |
| % of compliance opportunities implemented | 73 | 79 |
| Yearly compliance reviews | 6 | 6 |
| Phase I | Phase II | |||
|---|---|---|---|---|
| M | SD | M | SD | |
| Satisfaction on cloud services | 4.00 | .667 | 4.40 | .516 |
| Satisfaction on CM in cloud | 3.70 | .823 | 4.20 | .632 |
| CM contribution to IT quality of service | 3.10 | .568 | 3.80 | .632 |
| CM contribution to the organizational CM | 3.10 | .568 | 3.60 | .516 |
| Metric | Phase I | Phase II |
|---|---|---|
| Avg. time between identification of external compliance issues and resolution | 36 | 35 |
| # of compliance issues where employees seek guidance/assistance | 12 | 11 |
| # of reports of alleged or actual compliance violations | 76 | 58 |
| % of compliance opportunities implemented | 75 | 78 |
| Yearly compliance reviews | 12 | 12 |
| Phase I | Phase II | |||
|---|---|---|---|---|
| M | SD | M | SD | |
| Satisfaction on cloud services | 3.95 | .590 | 4.24 | .539 |
| Satisfaction on CM in cloud | 3.52 | .814 | 4.10 | .625 |
| CM contribution to IT quality of service | 3.10 | .625 | 3.76 | .700 |
| CM contribution to the organizational CM | 2.95 | .498 | 3.62 | .590 |
| Metric | Phase I | Phase II |
|---|---|---|
| Avg. time between identification of external compliance issues and resolution | 42 | 40 |
| # of compliance issues where employees seek guidance/assistance | 15.5 | 15.5 |
| # of reports of alleged or actual compliance violations | 82 | 59.5 |
| % of compliance opportunities implemented | 74.5 | 78.5 |
| Yearly compliance reviews | 9 | 9 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Brandis, K.; Dzombeta, S.; Colomo-Palacios, R.; Stantchev, V. Governance, Risk, and Compliance in Cloud Scenarios. Appl. Sci. 2019, 9, 320. https://doi.org/10.3390/app9020320
Brandis K, Dzombeta S, Colomo-Palacios R, Stantchev V. Governance, Risk, and Compliance in Cloud Scenarios. Applied Sciences. 2019; 9(2):320. https://doi.org/10.3390/app9020320
Chicago/Turabian StyleBrandis, Knud, Srdan Dzombeta, Ricardo Colomo-Palacios, and Vladimir Stantchev. 2019. "Governance, Risk, and Compliance in Cloud Scenarios" Applied Sciences 9, no. 2: 320. https://doi.org/10.3390/app9020320
APA StyleBrandis, K., Dzombeta, S., Colomo-Palacios, R., & Stantchev, V. (2019). Governance, Risk, and Compliance in Cloud Scenarios. Applied Sciences, 9(2), 320. https://doi.org/10.3390/app9020320






