A Private Strategy for Workload Forecasting on Large-Scale Wireless Networks
Abstract
:1. Introduction
- Modeling large-scale wireless network access as a Markovian chain;
- Predicting the workload of each network access point in a timely, resource-efficient, and private way using a commercial cloud infrastructure;
- Identifying and forecasting accurate users’ behaviors that are important to plan network infrastructure expansion and maintenance.
2. Related Works
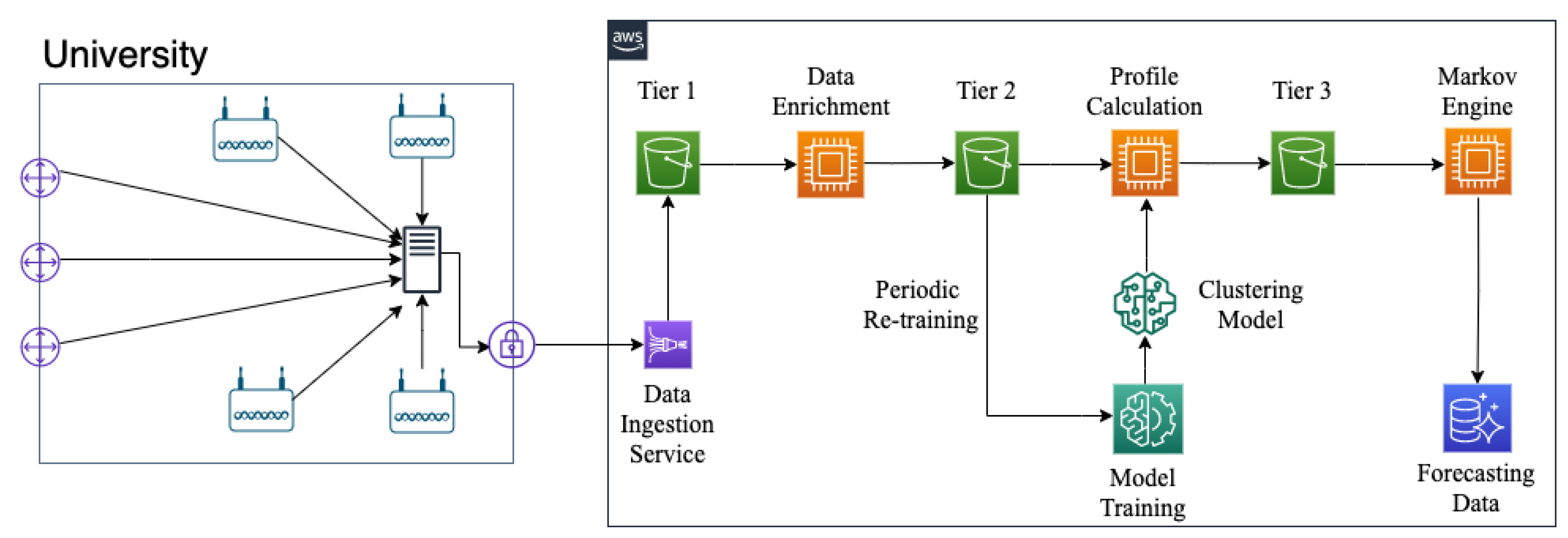
3. Network Load Forecasting and Profile Identification Strategy
- Large volume of data originated from a large-scale network;
- Variety of data sources represented by the various access points and network users;
- Adaptability of the model to the executed network applications;
- Variability of applications and uses of the network to which the load forecasting model should anticipate proactively;
- Need for high-quality historic data to train or fit the model;
- Complexity of the proposed forecasting method that should be insignificant for time and space;
- Data granularity with which the network usage is measured;
- Pattern length that is selected to fit the most popular patterns and behaviors in the network.
3.1. Model for Predicting the Expected Load on Each Access Point
3.2. Model for Identification of Usage Profiles
3.3. Model for Predicting Expected User Behavior and Expected Usage on Access Points
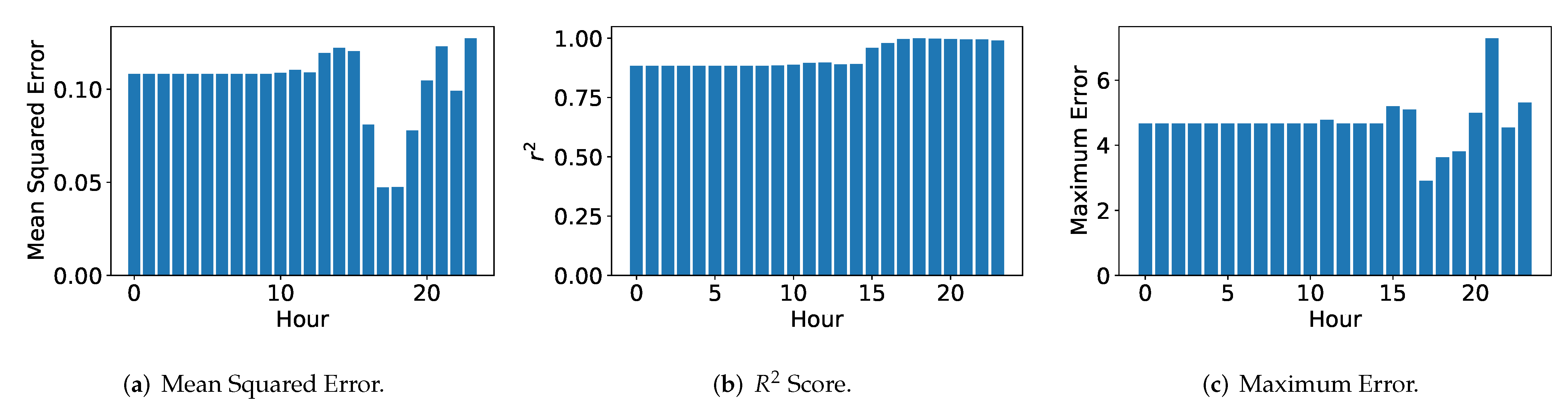
4. Experimental Analysis of the Proposed Strategy
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Forecast, C.V. Cisco Visual Networking Index: Global Mobile Data Traffic Forecast Update, 2017–2022 White Paper; Wiley: Hoboken, NJ, USA, 2019. [Google Scholar]
- Divgi, G.; Chlebus, E. Characterization of user activity and traffic in a commercial nationwide Wi-Fi hotspot network: Global and individual metrics. Wirel. Netw. 2013, 19, 1783–1805. [Google Scholar] [CrossRef]
- Biswas, S.; Bicket, J.; Wong, E.; Musaloiu-E, R.; Bhartia, A.; Aguayo, D. Large-scale Measurements of Wireless Network Behavior. In Proceedings of the 2015 ACM Conference on Special Interest Group on Data Communication, London, UK, 17–21 August 2015; ACM: London, UK, 2015; pp. 153–165. [Google Scholar] [CrossRef]
- Balbi, H.; Fernandes, N.; Souza, F.; Carrano, R.; Albuquerque, C.; Muchaluat-Saade, D.; Magalhães, L. Centralized channel allocation algorithm for IEEE 802.11 networks. In Proceedings of the 2012 Global Information Infrastructure and Networking Symposium (GIIS), Choroni, Venezuela, 17–19 December 2012; pp. 1–7. [Google Scholar]
- Ferraz, L.H.G.; Mattos, D.M.F.; Duarte, O.C.M.B. A two-phase multipathing scheme based on genetic algorithm for data center networking. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 2270–2275. [Google Scholar]
- Masdari, M.; Khoshnevis, A. A survey and classification of the workload forecasting methods in cloud computing. Clust. Comput. 2020, 23, 2399–2424. [Google Scholar] [CrossRef]
- Ghosh, A.; Jana, R.; Ramaswami, V.; Rowland, J.; Shankaranarayanan, N.K. Modeling and characterization of large-scale Wi-Fi traffic in public hot-spots. In Proceedings of the 2011 Proceedings IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 2921–2929. [Google Scholar] [CrossRef]
- Qian, F.; Wang, Z.; Gerber, A.; Mao, Z.; Sen, S.; Spatscheck, O. Profiling Resource Usage for Mobile Applications: A Cross-layer Approach. In Proceedings of the 9th International Conference on Mobile Systems, Applications, and Services, Washington, DC, USA, 28 June–1 July 2011; ACM: Bethesda, MD, USA, 2011; pp. 321–334. [Google Scholar] [CrossRef]
- Shye, A.; Scholbrock, B.; Memik, G.; Dinda, P.A. Characterizing and modeling user activity on smartphones: Summary. In Proceedings of the ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems, New York, NY, USA, 14–18 June 2010; Volume 38, pp. 375–376. [Google Scholar]
- Oliveira, L.; Obraczka, K.; Rodríguez, A. Characterizing User Activity in WiFi Networks: University Campus and Urban Area Case Studies. In Proceedings of the 19th ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Malta, 13–17 November 2016; pp. 190–194. [Google Scholar] [CrossRef]
- Medeiros, D.S.V.; Cunha Neto, H.N.; Lopez, M.A.; Magalhães, L.C.S.; Fernandes, N.C.; Vieira, A.B.; Silva, E.F.; Mattos, D.M. A survey on data analysis on large-Scale wireless networks: Online stream processing, trends, and challenges. J. Internet Serv. Appl. 2020, 11, 6. [Google Scholar] [CrossRef]
- Lopez, M.A.; Mattos, D.M.; Duarte, O.C.M.; Pujolle, G. A fast unsupervised preprocessing method for network monitoring. Ann. Telecommun. 2019, 74, 139–155. [Google Scholar] [CrossRef]
- Reis, L.H.A.; Magalhães, L.C.S.; de Medeiros, D.S.V.; Mattos, D.M.F. An Unsupervised Approach to Infer Quality of Service for Large-Scale Wireless Networking. J. Netw. Syst. Manag. 2020, 28, 1228–1247. [Google Scholar] [CrossRef]
- Meireles, R.; Rodrigues, A.; Stanciu, A.; Aguiar, A.; Steenkiste, P. Exploring Wi-Fi Network Diversity for Vehicle-To-Infrastructure Communication. In Proceedings of the 2020 IEEE Vehicular Networking Conference (VNC), New York, NY, USA, 16–18 December 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Lyu, F.; Ren, J.; Cheng, N.; Yang, P.; Li, M.; Zhang, Y.; Shen, X.S. Big Data Analytics for User Association Characterization in Large-Scale WiFi System. In Proceedings of the IEEE ICC 2019—Empowering Intelligent Communications (ICC’19), Shanghai, China, 20–24 May 2019. [Google Scholar]
- Mattos, D.M.; Duarte, O.C.M.; Pujolle, G. Profiling software defined networks for dynamic distributed-controller provisioning. In Proceedings of the 2016 7th International Conference on the Network of the Future (NOF), Buzios, Brazil, 16–18 November 2016; pp. 1–5. [Google Scholar]
- Marques, H.; Torres, P.M.B.; Marques, P.; Dionísio, R.; Rodriguez, J. Load Forecasting in WiFi Access Points over the LTE Network. In Proceedings of the International Conference of Mechatronics and Cyber-MixMechatronics—2017; Gheorghe, G.I., Ed.; Springer International Publishing: Cham, Switzerland, 2018; pp. 132–137. [Google Scholar]
- Son, T.A.; Linh, N.T.T.; Dang, N.N. Solving Resource Forecasting in Wifi Networks by Hybrid AR-LSTM Model. In Intelligent Systems and Networks; Tran, D.T., Jeon, G., Nguyen, T.D.L., Lu, J., Xuan, T.D., Eds.; Springer: Singapore, 2021; pp. 327–336. [Google Scholar]
- Barbosa, G.; Andreoni Lopez, M.; Medeiros, D.; Mattos, D.M.F. An Entropy-based Hybrid Mechanism for Large-Scale Wireless Network Traffic Prediction. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC): Wireless and Mobile Networks (ISNCC-2021 WMN), Dubai, United Arab Emirates, 1–3 June 2021. [Google Scholar]
- Chatzoglou, E.; Kambourakis, G.; Kolias, C. Empirical Evaluation of Attacks Against IEEE 802.11 Enterprise Networks: The AWID3 Dataset. IEEE Access 2021, 9, 34188–34205. [Google Scholar] [CrossRef]
- Claise, B. Cisco Systems Netflow Services Export Version 9; Technical Report; IETF: Fremont, CA, USA, 2004. [Google Scholar]
- Singh, V.K.; Dutta, K. Dynamic price prediction for Amazon spot instances. In Proceedings of the 2015 48th Hawaii International Conference on System Sciences, Kauai, HI, USA, 5–8 January 2015; pp. 1513–1520. [Google Scholar]
- Papadopouli, M.; Shen, H.; Spanakis, M. Modeling client arrivals at access points in wireless campus-wide networks. In Proceedings of the 2005 14th IEEE Workshop on Local Metropolitan Area Networks, Chania, Greece, 18–21 September 2005; p. 6. [Google Scholar] [CrossRef]
- Sculley, D. Web-scale k-means clustering. In Proceedings of the 19th International Conference on World Wide Web, ACM, Raleigh, NC, USA, 26–30 April 2010; pp. 1177–1178. [Google Scholar]
- Bholowalia, P.; Kumar, A. EBK-means: A clustering technique based on elbow method and k-means in WSN. Int. J. Comput. Appl. 2014, 105, 17–24. [Google Scholar]
- Syakur, M.; Khotimah, B.; Rochman, E.; Satoto, B. Integration K-Means Clustering Method and Elbow Method for Identification of The Best Customer Profile Cluster. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2018; Volume 336, p. 012017. [Google Scholar]




| Feature | Experimental Set-Up Value |
|---|---|
| Access Points | 363 |
| Internet Gateways | 5 |
| Collected Days | 8 |
| Unique Devices Detected | 6770 |
| Peak network traffic | 100 Mb/s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pisa, P.S.; Costa, B.; Gonçalves, J.A.; Varela de Medeiros, D.S.; Mattos, D.M.F. A Private Strategy for Workload Forecasting on Large-Scale Wireless Networks. Information 2021, 12, 488. https://doi.org/10.3390/info12120488
Pisa PS, Costa B, Gonçalves JA, Varela de Medeiros DS, Mattos DMF. A Private Strategy for Workload Forecasting on Large-Scale Wireless Networks. Information. 2021; 12(12):488. https://doi.org/10.3390/info12120488
Chicago/Turabian StylePisa, Pedro Silveira, Bernardo Costa, Jéssica Alcântara Gonçalves, Dianne Scherly Varela de Medeiros, and Diogo Menezes Ferrazani Mattos. 2021. "A Private Strategy for Workload Forecasting on Large-Scale Wireless Networks" Information 12, no. 12: 488. https://doi.org/10.3390/info12120488
APA StylePisa, P. S., Costa, B., Gonçalves, J. A., Varela de Medeiros, D. S., & Mattos, D. M. F. (2021). A Private Strategy for Workload Forecasting on Large-Scale Wireless Networks. Information, 12(12), 488. https://doi.org/10.3390/info12120488







