Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends
Abstract
:1. Introduction
2. A Systematic Literature Review
2.1. Review Methodology
2.1.1. Aim and Objectives
- Survey of cyber-attack incidents in the civil aviation sector over the last 20 years;
- Analysis and review of state-of-the-art cyber-attack trends, threat actors and their motivation;
- Identification of the most common types of attacks and targeted infrastructures;
- Providing cyber-security professionals with information on the current and future trends of cyber-attack incidents in the context of the evolution of the civil aviation sector.
2.1.2. Classification and Research Criteria
2.2. Cyber-Threats and Automation in Civil Aviation Industry
2.3. Threat Actors and Their Motivations
3. Documented Cyber-Attacks in Aviation Industry (2001–2021)
Analysis and Critical Reviews of Cyber-Attacks in the Civil Aviation Industry
4. Cyber-Attack Surfaces and Vulnerabilities in the Civil Aviation Industry
4.1. Aerospace and Avionic Systems
4.1.1. Aircraft Communications Addressing and Reporting System (ACARS)
4.1.2. Automatic Dependent Surveillance-Broadcast (ADS-B)
4.2. Electronic Flight Bag
4.3. Attack Surfaces in the Civil Aviation Industry
5. Mitigation of Cyber-Security Challenges within the Civil Aviation Industry
6. The Future Civil Aviation Industry and Its Cyber-Security Challenges
6.1. Smart Airports
6.2. E-Enabled Aircraft
| Domain | Ref | Experimental Tests/Scenarios | Tools |
|---|---|---|---|
| IoT | [91] | Network mapping attack/implementation of profiling module (training and testing algorithm) | TestStad/Machine Learning Algorithm |
| [92] | Discrete-time Markov chain model (DTMC): Analysing the capacity of the block chain | Block mining algorithm and Ethereum protocol | |
| [93] | Manual test: Analysis and attacks of each device, Automated test: process testing of different IoT device | Open-Source MS | |
| [94] | DoS massif traffic/Transfer Data/Abnormal code/System crash | DTM by Triangle Micro Works | |
| [95] | Real-world attack scenarios: internal and external network attacks | SDN/network function virtualisation | |
| [96] | Anomaly intrusion/attacks traffic | Machine learning algorithm/feature extraction | |
| [97] | Command injection attack | Machine learning algorithm/PLC programming by Ladder language | |
| [98] | SWaT/WADI datasets: Normal and attack scenario | Machine learning algorithm | |
| [99] | Man-in-the-middle attack | SDN /Python | |
| [100] | LAUP algorithm(authentication)/key distribution test | COOJA simulator | |
| Smart Grid | [101] | Offline co-simulation Test-bed: DoS/FDI attacks | OMNET++ |
| [102] | Access to communication link ([103]) attack model | OPAL-RT | |
| [104] | Deep packet inspection | Software-Defined Networks/OpenFMB | |
| [105] | Power supply interruption Attack/Physical damage attack | Real world power system/Machine learning | |
| [106] | MMS/GOOSE/SV implementation | IEC 61850 Protocol/Ethernet RaspberryPi 3B+ | |
| [107] | HIL simulation/proof-of-concept validation | Python | |
| [108] | DoS/Man in the middle attacks/TCP SYN Flood Attack | DeterLab/Security Experimentation EnviRonment (SEER) | |
| [109] | Recording network traffic/poisoning attack | Real-Time Digital Simulator (RTDS) | |
| [110] | Timing Intrusion Attack | Field End-to-End Calibrator/Gold PMU | |
| [111] | Test of cyber-physical sensor: IREST | Idaho CPS SCADA Cybersecurity (ISAAC) testbed | |
| [112] | MITM attack/DoS attack | Open-source software/Raspberry Pis. FLEP-SGS | |
| Cloud | [113] | Flood malicious traffic (ICMP/HTTP/SYN) | VMware Esxi hypervisor/A vCenter server/VMs |
| [114] | Considering small messages (about1–2 KBytes): Fast filling of the buffers | MOM4Cloud architectural model. | |
| [115] | UNM database: Malicious tracing logs | KVM2.6.27 hypervisor/Python3.4 | |
| [116] | Test of memory usage before or after instance creation | OpenStack: Open-Source cloud operating system | |
| [117] | Evaluation of performance metrics of NDN/edge cloud computing | Cloud VM | |
| [118] | Adding defaults: broken interconnection/abnormal extruder | MTComm: Online Machine Tool Communication | |
| [119] | Side-channel attacks/stealthy data exfiltration | DHCP server/TFTP Server/HTTP Server/MQTT Server | |
| [120] | SQL Injection attack | OpenStack implementation/Python | |
| [121] | Testing traffic scenarios | Openflow controller/OpenvSwitch/Network virtualization agent | |
| [122] | Time-inference attacks | Software-Defined Network | |
| [123] | DDoS attack | OpenStack environment |
7. Conclusions
8. Open Challenges and Research Opportunities
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Duchamp, H.; Bayram, I.; Korhani, R. Cyber-Security, a new challenge for the aviation and automotive industries. In Seminar in Information Systems: Applied Cybersecurity Strategy for Managers; 2016; pp. 1–4. Available online: https://blogs.harvard.edu/cybersecurity/files/2017/01/Cybersecurity-aviation-strategic-report.pdf (accessed on 20 September 2020).
- Monteagudo, J. Aviation Cybersecurity—High Level Analysis, Major Challenges and Where the Industry Is Heading. 2020. Available online: https://cyberstartupobservatory.com/aviation-cybersecurity-major-challenges/ (accessed on 26 September 2020).
- Bellekens, X.; Jayasekara, G.; Hindy, H.; Bures, M.; Brosset, D.; Tachtatzis, C.; Atkinson, R. From cyber-security deception to manipulation and gratification through gamification. In International Conference on Human-Computer Interaction; Springer: Berlin/Heidelberg, Germany, 2019; pp. 99–114. [Google Scholar]
- ICAO. Security and Facilitation Strategic Objective: Aviation Cybersecurity Strategy. 2019. Available online: https://www.icao.int/cybersecurity/Documents/AVIATIONCYBERSECURITYSTRATEGY.EN.pdf (accessed on 6 December 2021).
- Okoli, C.; Schabram, K. A Guide to Conducting a Systematic Literature Review of Information Systems Research. 2010. Available online: https://asset-pdf.scinapse.io/prod/1539987097/1539987097.pdf (accessed on 6 December 2021).
- Okoli, C. A Guide to Conducting a Standalone Systematic Literature Review. 2015. Available online: https://aisel.aisnet.org/cais/vol37/iss1/43/ (accessed on 6 December 2021).
- IATA. Compilation of Cyber Security Regulations, Standards, and Guidance Applicable to Civil Aviation. 2020. Available online: https://www.iata.org/contentassets/4c51b00fb25e4b60b38376a4935e278b/compilationofcyberregulationsstandardsandguidanceapr212.0.pdf (accessed on 6 December 2021).
- Haass, J.; Sampigethaya, R.; Capezzuto, V. Aviation and cybersecurity: Opportunities for applied research. TR News 2016, 304, 39. [Google Scholar]
- Lykou, G.; Anagnostopoulou, A.; Gritzalis, D. Implementing cyber-security measures in airports to improve cyber-resilience. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; pp. 1–6. [Google Scholar]
- Lykou, G.; Anagnostopoulou, A.; Gritzalis, D. Smart airport cybersecurity: Threat mitigation and cyber resilience controls. Sensors 2019, 19, 19. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Gopalakrishnan, K.; Govindarasu, M.; Jacobson, D.W.; Phares, B.M. Cyber security for airports. Int. J. Traffic Transp. Eng. 2013, 3, 365–376. [Google Scholar] [CrossRef]
- Mathew, A.R. Airport Cyber Security and Cyber Resilience Controls. arXiv 2019, arXiv:1908.09894. [Google Scholar]
- Suciu, G.; Scheianu, A.; Vulpe, A.; Petre, I.; Suciu, V. Cyber-attacks–The impact over airports security and prevention modalities. In World Conference on Information Systems and Technologies; Springer: Berlin/Heidelberg, Germany, 2018; pp. 154–162. [Google Scholar]
- Corretjer, P.J. A Cybersecurity Analysis of Today’s Commercial Aircrafts and Aviation Industry Systems. Master’s Thesis, Utica College, Utica, NY, USA, 2018; p. 22. [Google Scholar]
- Kagalwalla, N.; Churi, P.P. Cybersecurity in Aviation: An Intrinsic Review. In Proceedings of the 2019 5th International Conference On Computing, Communication, Control And Automation (ICCUBEA), Pune, India, 19–21 September 2019; pp. 1–6. [Google Scholar]
- Lehto, M. Cyber Security in Aviation, Maritime and Automotive. In Computation and Big Data for Transport; Springer: Berlin/Heidelberg, Germany, 2020; pp. 19–32. [Google Scholar]
- CyberRisk, I. Cyber Threats to the Aviation Industry. 2020. Available online: https://cyberriskinternational.com/2020/04/06/cyber-threats-to-the-aviation-industry/ (accessed on 19 September 2020).
- Fireeye. Cyber Threats to the Aerospace and Defense Industries. 2016. Available online: https://www.fireeye.com/content/dam/fireeye-www/current-threats/pdfs/ib-aerospace.pdf (accessed on 24 September 2020).
- Varonis. 9 Infamous APT Groups: Fast Fact Trading Cards. 2020. Available online: https://www.varonis.com/blog/apt-groups (accessed on 6 December 2021).
- Kessler, G.C.; Craiger, J.P. Aviation Cybersecurity: An Overview. 2018. Available online: https://commons.erau.edu/ntas/2018/presentations/37/ (accessed on 6 December 2021).
- Abeyratne, R. Aviation and Cybersecurity in the Digital World. In Aviation in the Digital Age; Springer: Berlin/Heidelberg, Germany, 2020; pp. 173–211. [Google Scholar]
- Arampatzis, A. The State of Civil Aviation Cybersecurity. 2020. Available online: https://www.tripwire.com/state-of-security/security-data-protection/civil-aviation-cybersecurity/ (accessed on 30 September 2020).
- Viveros, C.A.P. Analysis of the Cyber Attacks against ADS-B Perspective of Aviation Experts. Master’s Thesis, University of Tartu, Tartu, Estonia, 2016. [Google Scholar]
- Gross, G. FAA: Slammer Didn’t Hurt Us, but Other Attacks Coming. 2003. Available online: https://www.networkworld.com/article/2339600/faa–slammer-didn-t-hurt-us–but-other-attacks-coming.html (accessed on 19 September 2020).
- Goodin, D. US Air Traffic Faces ‘Serious Harm’ from Cyber Attackers. 2009. Available online: Https://www.theregister.com/2009/05/07/air-traffic-cyber-attack/ (accessed on 19 September 2020).
- Ellinor, M. Report: Hackers Broke into FAA Air Traffic Control Systems. 2009. Available online: https://www.cnet.com/tech/services-and-software/report-hackers-broke-into-faa-air-traffic-control-systems/ (accessed on 19 September 2020).
- Paganini, P. Istanbul Ataturk International Airport Targeted by a Cyber-Attack. 2013. Available online: https://securityaffairs.co/wordpress/16721/hacking/istanbul-ataturk-international-airport-targeted-by-cyber-attack.html (accessed on 19 September 2020).
- Welsh, W. Phishing Scam Targeted 75 US Airports. 2014. Available online: https://www.informationweek.com/?1 (accessed on 19 September 2020).
- Brewster, T. Attack On LOT Polish Airline Grounds 10 Flights. 2015. Available online: https://www.forbes.com/sites/thomasbrewster/2015/06/22/lot-airline-hacked/?sh=6e4015fe124e (accessed on 19 September 2020).
- Kirkliauskaite, K. Main Cyber-Security Challenges in Aviation. 2020. Available online: https://www.aerotime.aero/25150-main-cyber-security-challenges-in-aviation (accessed on 19 September 2020).
- Polityuk, P.; Prentice, A. Ukraine Says to Review Cyber Defenses after Airport Targeted from Russia. 2016. Available online: https://www.reuters.com/article/us-ukraine-cybersecurity-malware-idUSKCN0UW0R0 (accessed on 6 October 2020).
- Park, K. Cathay Pacific Cyber Attack Is World’s Biggest Airline Data Breach. 2018. Available online: https://www.insurancejournal.com/news/international/2018/10/26/505699.html (accessed on 19 September 2020).
- Sandle, P. British Airways Says ‘Sophisticated’ Hacker Stole Data on 380,000 Customers. 2018. Available online: https://www.insurancejournal.com/news/international/2018/09/10/500566.htm (accessed on 19 September 2020).
- Singh, K. Delta, Sears Report Data Breach by Service Provider. 2018. Available online: https://www.insurancejournal.com/news/national/2018/04/05/485440.htm (accessed on 19 September 2020).
- Leyden, J. Brit Airport Pulls Flight info System Offline after Attack by ‘Online Crims’. 2018. Available online: https://www.theregister.com/2018/09/17/bristol-airport-cyber-attack/ (accessed on 19 September 2020).
- Sandle, T. Air Canada Suffers Major App Data Breach of 20,000 Customers. 2018. Available online: https://www.digitaljournal.com/business/air-canada-in-major-app-data-breach/article/530763 (accessed on 19 September 2020).
- Gibbs, B. Potential Personally Identifiable Information (PII) Compromise of NASA Servers. 2018. Available online: Http://spaceref.com/news/viewsr.html?pid=52074/ (accessed on 22 September 2020).
- Gates, D. Boeing Hit by WannaCry Virus, but Says Attack Caused Little Damage. 2018. Available online: https://www.seattletimes.com/business/boeing-aerospace/boeing-hit-by-wannacry-virus-fears-it-could-cripple-some-jet-production/ (accessed on 22 September 2020).
- Solomon, S. Israeli Airports Fend Off 3 Million Attempted Attacks a Day, Cyber Head Says. 2019. Available online: https://www.timesofisrael.com/israeli-airports-fend-off-3-million-attempted-attacks-a-day-cyber-head-says/ (accessed on 19 September 2020).
- Duvelleroy, M. Airbus Statement on Cyber Incident. 2019. Available online: https://www.airbus.com/en/newsroom/press-releases/2019-01-airbus-statement-on-cyber-incident (accessed on 22 September 2020).
- Goud, N. Ransomware Attack on Albany Airport on Christmas 2019. 2019. Available online: https://www.cybersecurity-insiders.com/ransomware-attack-on-albany-airport-on-christmas-2019/ (accessed on 25 September 2020).
- Team, N. Cryptocurrency Miners Infected More than 50% of the European Airport Workstations. 2019. Available online: https://www.cyberdefensemagazine.com/cryptocurrency-miners-infected-more-than-50-of-the-european-airport-workstations/ (accessed on 25 September 2020).
- Narendra, M. Privacy: Air New Zealand Experiences Data Breach. 2019. Available online: https://www.grcworldforums.com/news/2019/08/16/privacy-air-new-zealand-experiences-data-breach/ (accessed on 25 September 2020).
- Montalbano, E. DoppelPaymer Ransomware Used to Steal Data from Supplier to SpaceX, Tesla. 2020. Available online: https://threatpost.com/doppelpaymer-ransomware-used-to-steal-data-from-supplier-to-spacex-tesla/153393/ (accessed on 22 September 2020).
- Chua, A. Ransomware Attack hits ST Engineering’s USA Aerospace Unit. 2020. Available online: https://www.flightglobal.com/aerospace/ransomware-attack-hits-st-engineerings-usa-aerospace-unit/138722.article (accessed on 23 September 2020).
- Claburn, T. Airline Software Super-Bug: Flight Loads Miscalculated Because Women Using ‘Miss’ Were Treated as Children. 2021. Available online: https://www.theregister.com/2021/04/08/tuisoftwaremistake/ (accessed on 9 April 2021).
- Mazareanu, E. Number of Public and Private Airports in the United States from 1990 to 2019*. 2020. Available online: https://www.statista.com/statistics/183496/number-of-airports-in-the-united-states-since-1990/ (accessed on 28 November 2020).
- Paganini, P. Cyber Threats against the Aviation Industry. 2014. Available online: https://resources.infosecinstitute.com/topic/cyber-threats/ (accessed on 19 September 2020).
- Thales. Overcoming the Cyber Threat in Aviation. 2016. Available online: https://onboard.thalesgroup.com/overcoming-cyber-threat-aviation/ (accessed on 24 September 2020).
- Zetter, K. Feds Say that Banned Researcher Commandeered a Plane. 2015. Available online: https://www.wired.com/2015/05/ (accessed on 18 January 2022).
- Freiherr, G. Will Your Airliner Get Hacked? 2021. Available online: https://www.smithsonianmag.com/air-space-magazine/will-your-airliner-get-hacked-180976752/ (accessed on 18 January 2022).
- Efe, A.; Tuzlupınar, B.; Cavlan, A.C. Air Traffic Security against Cyber Threats. Bilge Int. J. Sci. Technol. Res. 2021, 3, 135–143. Available online: https://dergipark.org.tr/en/pub/bilgesci/issue/49118/405074 (accessed on 18 January 2021).
- Santamarta, R. A Wake-Up Call for SATCOM Security. Technical White Paper. 2014. Available online: https://www.secnews.gr/wp-content/uploads/Files/Satcom_Security.pdf (accessed on 19 September 2020).
- Biesecker, C. Boeing 757 Testing Shows Airplanes Vulnerable to Hacking, DHS Says; Avionics International: New York, NY, USA, 2017. [Google Scholar]
- Dessiatnikoff, A.; Deswarte, Y.; Alata, E.; Nicomette, V. Potential attacks on onboard aerospace systems. IEEE Secur. Priv. 2012, 10, 71–74. [Google Scholar] [CrossRef]
- Papp, D.; Ma, Z.; Buttyan, L. Embedded systems security: Threats, vulnerabilities, and attack taxonomy. In Proceedings of the 2015 13th Annual Conference on Privacy, Security and Trust (PST), Izmir, Turkey, 21–23 July 2015; pp. 145–152. [Google Scholar]
- GAO. Aviation Cybersecurity. 2020. Available online: https://www.gao.gov/assets/gao-21-86.pdf (accessed on 12 May 2020).
- Encyclopedia of Physical Science and Technology; Academic Press: Cambridge, MA, USA, 1987.
- Smith, B. System and Method for Data Collection in an Avionics Network. U.S. Patent App. 11/092,470, 28 September 2006. [Google Scholar]
- Akram, R.N.; Markantonakis, K.; Holloway, R.; Kariyawasam, S.; Ayub, S.; Seeam, A.; Atkinson, R. Challenges of security and trust in avionics wireless networks. In Proceedings of the 2015 IEEE/AIAA 34th Digital Avionics Systems Conference (DASC), Prague, Czech Republic, 13–17 September 2015; pp. 777–780. [Google Scholar]
- Akram, R.N.; Markantonakis, K.; Mayes, K.; Bonnefoi, P.F.; Sauveron, D.; Chaumette, S. An efficient, secure and trusted channel protocol for avionics wireless networks. In Proceedings of the 2016 IEEE/AIAA 35th Digital Avionics Systems Conference (DASC), Sacramento, CA, USA, 25–29 September 2016; pp. 1–10. [Google Scholar]
- Akram, R.N.; Markantonakis, K.; Mayes, K.; Bonnefoi, P.F.; Sauveron, D.; Chaumette, S. Security and performance comparison of different secure channel protocols for Avionics Wireless Networks. In Proceedings of the 2016 IEEE/AIAA 35th Digital Avionics Systems Conference (DASC), Sacramento, CA, USA, 25–29 September 2016; pp. 1–8. [Google Scholar]
- Markantonakis, K.; Akram, R.N.; Holloway, R. A secure and trusted boot process for avionics wireless networks. In Proceedings of the 2016 Integrated Communications Navigation and Surveillance (ICNS), Herndon, VA, USA, 19–21 April 2016; pp. 1C3-1–1C3-9. [Google Scholar]
- Bellamy, W., III. How ACARS Will Evolve, Not Disappear, With Transition to IPS. 2018. Available online: https://www.aviationtoday.com/2018/06/12/acars-will-evolve-not-disappear-transition-ips/ (accessed on 28 September 2020).
- Smith, M.; Moser, D.; Strohmeier, M.; Lenders, V.; Martinovic, I. Analyzing privacy breaches in the aircraft communications addressing and reporting system (acars). arXiv 2017, arXiv:1705.07065. [Google Scholar]
- Smith, M.; Moser, D.; Strohmeier, M.; Lenders, V.; Martinovic, I. Undermining privacy in the aircraft communications addressing and reporting system (ACARS). Proc. Priv. Enhancing Technol. 2018, 2018, 105–122. [Google Scholar] [CrossRef] [Green Version]
- Ali, B.S. A Safety Assessment Framework for Automatic Dependent Surveillance Broadcast (ADS-B) and Its Potential Impact on Aviation Safety. Ph.D. Thesis, Centre for Transport Studies, Department of Civil and Environmental, Imperial College London, London, UK, 2013. [Google Scholar]
- Ali, B.S.; Schuster, W.; Ochieng, W.Y. Evaluation of the capability of automatic dependent surveillance broadcast to meet the requirements of future airborne surveillance applications. J. Navig. 2017, 70, 49. [Google Scholar] [CrossRef] [Green Version]
- Ali, B.S.; Ochieng, W.Y.; Schuster, W.; Majumdar, A.; Chiew, T.K. A safety assessment framework for the Automatic Dependent Surveillance Broadcast (ADS-B) system. Saf. Sci. 2015, 78, 91–100. [Google Scholar] [CrossRef]
- Manesh, M.R.; Kaabouch, N. Analysis of vulnerabilities, attacks, countermeasures and overall risk of the Automatic Dependent Surveillance-Broadcast (ADS-B) system. Int. J. Crit. Infrastruct. Prot. 2017, 19, 16–31. [Google Scholar] [CrossRef]
- Tabassum, A. Performance Analysis of Automatic Dependent Surveillance-Broadcast (ADS-B) and Breakdown of Anomalies. 2017. Available online: https://www.proquest.com/openview/8e29fdfcd2afbe8ce28f760d0a314248/1?pq-origsite=gscholar&cbl=18750 (accessed on 28 September 2020).
- Strohmeier, M.; Lenders, V.; Martinovic, I. On the security of the automatic dependent surveillance-broadcast protocol. IEEE Commun. Surv. Tutor. 2014, 17, 1066–1087. [Google Scholar] [CrossRef] [Green Version]
- Wolf, M.; Minzlaff, M.; Moser, M. Information technology security threats to modern e-enabled aircraft: A cautionary note. J. Aerosp. Inf. Syst. 2014, 11, 447–457. [Google Scholar] [CrossRef] [Green Version]
- Howard, E. Dell and Airbus deliver Electronic Flight Bag Services to Airlines Worldwide. 2013. Available online: https://www.intelligent-aerospace.com/commercial/article/16539972/dell-and-airbus-deliver-electronic-flight-bag-services-to-airlines-worldwide (accessed on 12 February 2021).
- Keller, J. Fokker Services Certifies iPad Electronic Flight Bag (EFB) for Bombardier Dash 8 Twin-Engine Passenger Turboprop. 2013. Available online: https://www.intelligent-aerospace.com/commercial/article/16539248/fokker-services-certifies-ipad-electronic-flight-bag-efb-for-bombardier-dash-8-twinengine-passenger-turboprop (accessed on 12 February 2021).
- Taleqani, A.R.; Nygard, K.E.; Bridgelall, R.; Hough, J. Machine Learning Approach to Cyber Security in Aviation. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018; pp. 0147–0152. [Google Scholar]
- Ugwoke, F.; Okafor, K.; Chijindu, V. Security QoS profiling against cyber terrorism in airport network systems. In Proceedings of the 2015 International Conference on Cyberspace (CYBER-Abuja), Abuja, Nigeria, 4–7 November 2015; pp. 241–251. [Google Scholar]
- Delain, O.; Ruhlmann, O.; Vautier, E.; Johnson, C.; Shreeve, M.; Sirko, P.; Prozserin, V. Cyber-Security Application for SESAR OFA 05.01.01—Final Report. 2016. Available online: https://www.sesarju.eu/sites/default/files/documents/news/AddressingairportcybersecurityFull0.pdf (accessed on 3 April 2020).
- Clark, R.M.; Hakim, S. Cyber-Physical Security: Protecting Critical Infrastructure at the State and Local Level; Springer: Berlin/Heidelberg, Germany, 2016; Volume 3. [Google Scholar]
- Martellini, M. Cyber Security: Deterrence and IT Protection for Critical Infrastructures; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Singer, P.W.; Friedman, A. Cybersecurity: What Everyone Needs to Know; OUP USA: New York, NY, USA, 2014. [Google Scholar]
- Zamorano, M.M.; Fernández-Laso, M.C.; de Esteban Curiel, J. Smart Airports: Acceptance of Technology by Passengers. Cuad. Tur. 2020, 45, 567–570. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Schiliro, F.; Gauravaram, P.; Janicke, H. A Holistic Review of Cybersecurity and Reliability Perspectives in Smart Airports. IEEE Access 2020, 8, 209802–209834. [Google Scholar] [CrossRef]
- Akar, I.N.; Yaqoobi, M.H. Smart Airport: How IOT and New Technologies Shaping the Future of Airport Industry. Available online: https://hadiyaqoobi.github.io/Graduation-project/documents/Thesis202.1.pdf (accessed on 3 April 2020).
- Mahmoud, M.S.B.; Larrieu, N.; Pirovano, A.; Varet, A. An adaptive security architecture for future aircraft communications. In Proceedings of the 29th Digital Avionics Systems Conference, Salt Lake City, UT, USA, 3–7 October 2010; pp. 3.E.2-1–3.E.2-16. [Google Scholar] [CrossRef] [Green Version]
- Neumann, P.G. Computer security in aviation: Vulnerabilities, threats, and risks. In International Conference on Aviation Safety in the 21st Century; White House Commission on Safety and Security and George Washington University: Washington, DC, USA, 1997. [Google Scholar]
- Sampigethaya, K.; Poovendran, R.; Bushnell, L. Secure operation, control, and maintenance of future e-enabled airplanes. Proc. IEEE 2008, 96, 1992–2007. [Google Scholar] [CrossRef] [Green Version]
- Sampigethaya, K.; Poovendran, R.; Shetty, S.; Davis, T.; Royalty, C. Future e-enabled aircraft communications and security: The next 20 years and beyond. Proc. IEEE 2011, 99, 2040–2055. [Google Scholar] [CrossRef]
- Kaloudi, N.; Li, J. The ai-based cyber threat landscape: A survey. ACM Comput. Surv. (CSUR) 2020, 53, 1–34. [Google Scholar] [CrossRef] [Green Version]
- Brundage, M.; Avin, S.; Clark, J.; Toner, H.; Eckersley, P.; Garfinkel, B.; Dafoe, A.; Scharre, P.; Zeitzoff, T.; Filar, B.; et al. The malicious use of artificial intelligence: Forecasting, prevention, and mitigation. arXiv 2018, arXiv:1802.07228. [Google Scholar]
- Siboni, S.; Sachidananda, V.; Shabtai, A.; Elovici, Y. Security Testbed for the Internet of Things. arXiv 2016, arXiv:1610.05971. [Google Scholar]
- Wang, X.; Yu, G.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Zheng, K.; Niu, X. Capacity of blockchain based internet-of-things: Testbed and analysis. Internet Things 2019, 8, 100109. [Google Scholar] [CrossRef]
- Waraga, O.A.; Bettayeb, M.; Nasir, Q.; Talib, M.A. Design and implementation of automated IoT security testbed. Comput. Secur. 2020, 88, 101648. [Google Scholar] [CrossRef]
- Lee, S.; Lee, S.; Yoo, H.; Kwon, S.; Shon, T. Design and implementation of cybersecurity testbed for industrial IoT systems. J. Supercomput. 2018, 74, 4506–4520. [Google Scholar] [CrossRef]
- Kim, Y.; Nam, J.; Park, T.; Scott-Hayward, S.; Shin, S. SODA: A software-defined security framework for IoT environments. Comput. Netw. 2019, 163, 106889. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Zolanvari, M.; Teixeira, M.A.; Jain, R. Effect of imbalanced datasets on security of industrial IoT using machine learning. In Proceedings of the 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, FL, USA, 9–11 November 2018; pp. 112–117. [Google Scholar]
- Elnour, M.; Meskin, N.; Khan, K.; Jain, R. A Dual-Isolation-Forests-Based Attack Detection Framework for Industrial Control Systems. IEEE Access 2020, 8, 36639–36651. [Google Scholar] [CrossRef]
- Molina Zarca, A.; Bernal Bernabe, J.; Farris, I.; Khettab, Y.; Taleb, T.; Skarmeta, A. Enhancing IoT security through network softwarization and virtual security appliances. Int. J. Netw. Manag. 2018, 28, e2038. [Google Scholar] [CrossRef]
- Arockia Baskaran, A.G.R.; Nanda, P.; Nepal, S.; He, S. Testbed evaluation of Lightweight Authentication Protocol (LAUP) for 6LoWPAN wireless sensor networks. Concurr. Comput. Pract. Exp. 2019, 31, e4868. [Google Scholar] [CrossRef]
- Hammad, E.; Ezeme, M.; Farraj, A. Implementation and development of an offline co-simulation testbed for studies of power systems cyber security and control verification. Int. J. Electr. Power Energy Syst. 2019, 104, 817–826. [Google Scholar] [CrossRef]
- Poudel, S.; Ni, Z.; Malla, N. Real-time cyber physical system testbed for power system security and control. Int. J. Electr. Power Energy Syst. 2017, 90, 124–133. [Google Scholar] [CrossRef]
- Hahn, A.; Ashok, A.; Sridhar, S.; Govindarasu, M. Cyber-physical security testbeds: Architecture, application, and evaluation for smart grid. IEEE Trans. Smart Grid 2013, 4, 847–855. [Google Scholar] [CrossRef]
- De La Torre, G.; Rad, P.; Choo, K.K.R. Implementation of deep packet inspection in smart grids and industrial Internet of Things: Challenges and opportunities. J. Netw. Comput. Appl. 2019, 135, 32–46. [Google Scholar] [CrossRef]
- Adepu, S.; Kandasamy, N.K.; Mathur, A. Epic: An electric power testbed for research and training in cyber physical systems security. In Computer Security; Springer: Berlin/Heidelberg, Germany, 2018; pp. 37–52. [Google Scholar]
- Fujdiak, R.; Blazek, P.; Chmelar, P.; Dittrich, P.; Voznak, M.; Mlynek, P.; Slacik, J.; Musil, P.; Jurka, P.; Misurec, J. Communication Model of Smart Substation for Cyber-Detection Systems. In International Conference on Computer Networks; Springer: Berlin/Heidelberg, Germany, 2019; pp. 256–271. [Google Scholar]
- Cheng, Z.; Chow, M.Y. The Development and Application of a DC Microgrid Testbed for Distributed Microgrid Energy Management System. In Proceedings of the IECON 2018-44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 300–305. [Google Scholar]
- Liu, R.; Srivastava, A. Integrated simulation to analyze the impact of cyber-attacks on the power grid. In Proceedings of the 2015 Workshop on Modeling and Simulation of Cyber-Physical Energy Systems (MSCPES), Seattle, WA, USA, 13 April 2015; pp. 1–6. [Google Scholar]
- Oyewumi, I.A.; Jillepalli, A.A.; Richardson, P.; Ashrafuzzaman, M.; Johnson, B.K.; Chakhchoukh, Y.; Haney, M.A.; Sheldon, F.T.; de Leon, D.C. ISAAC: The idaho CPS smart grid cybersecurity testbed. In Proceedings of the 2019 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 7–8 February 2019; pp. 1–6. [Google Scholar]
- Kezunovic, M.; Qian, C.; Seidl, C.; Ren, J. Testbed for Timing Intrusion Evaluation and Tools for Lab and Field Testing of Synchrophasor System. In Proceedings of the 2019 International Conference on Smart Grid Synchronized Measurements and Analytics (SGSMA), College Station, TX, USA, 21–23 May 2019; pp. 1–8. [Google Scholar]
- Marino, D.L.; Wickramasinghe, C.S.; Amarasinghe, K.; Challa, H.; Richardson, P.; Jillepalli, A.A.; Johnson, B.K.; Rieger, C.; Manic, M. Cyber and Physical Anomaly Detection in Smart-Grids. IEEE Resil. Week (RWS) 2019, 2019, 187–193. [Google Scholar] [CrossRef]
- Konstantinou, C.; Sazos, M.; Maniatakos, M. FLEP-SGS 2: A Flexible and Low-cost Evaluation Platform for Smart Grid Systems Security. In Proceedings of the 2019 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–21 February 2019; pp. 1–5. [Google Scholar]
- Patil, R.; Dudeja, H.; Modi, C. Designing an efficient security framework for detecting intrusions in virtual network of cloud computing. Comput. Secur. 2019, 85, 402–422. [Google Scholar] [CrossRef]
- Celesti, A.; Fazio, M.; Galletta, A.; Carnevale, L.; Wan, J.; Villari, M. An approach for the secure management of hybrid cloud–edge environments. Future Gener. Comput. Syst. 2019, 90, 1–19. [Google Scholar] [CrossRef]
- Mishra, P.; Verma, I.; Gupta, S. KVMInspector: KVM Based introspection approach to detect malware in cloud environment. J. Inf. Secur. Appl. 2020, 51, 102460. [Google Scholar] [CrossRef]
- Van, V.N.; Chi, L.M.; Long, N.Q.; Nguyen, G.N.; Le, D.N. A performance analysis of openstack open-source solution for IaaS cloud computing. In Proceedings of the Second International Conference on Computer and Communication Technologies; Springer: Berlin/Heidelberg, Germany, 2016; pp. 141–150.
- Ullah, R.; Rehman, M.A.U.; Kim, B.S. Design and Implementation of an Open Source Framework and Prototype for Named Data Networking-Based Edge Cloud Computing System. IEEE Access 2019, 7, 57741–57759. [Google Scholar] [CrossRef]
- Al Sunny, S.N.; Liu, X.; Shahriar, M.R. Remote Monitoring and Online Testing of Machine Tools for Fault Diagnosis and Maintenance Using MTComm in a Cyber-Physical Manufacturing Cloud. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 532–539. [Google Scholar]
- Sanatinia, A.; Deshpande, S.; Munshi, A.; Kohlbrenner, D.; Yessaillian, M.; Symonds, S.; Chan, A.; Noubir, G. Hyperdrive: A flexible cloud testbed for research and education. In Proceedings of the 2017 IEEE International Symposium on Technologies for Homeland Security (HST), Waltham, MA, USA, 25–26 April 2017; pp. 1–4. [Google Scholar]
- Frank, M.; Leitner, M.; Pahi, T. Design Considerations for Cyber Security Testbeds: A Case Study on a Cyber Security Testbed for Education. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 38–46. [Google Scholar]
- Gao, H.; Peng, Y.; Jia, K.; Wen, Z.; Li, H. Cyber-physical systems testbed based on cloud computing and software defined network. In Proceedings of the 2015 International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Adelaide, SA, Australia, 23–25 September 2015; pp. 337–340. [Google Scholar]
- Khorsandroo, S.; Tosun, A.S. Time Inference Attacks on Software Defined Networks: Challenges and Countermeasures. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018; pp. 342–349. [Google Scholar]
- Kalliola, A.; Lal, S.; Ahola, K.; Oliver, I.; Miche, Y.; Holtmanns, S. Testbed for security orchestration in a network function virtualization environment. In Proceedings of the 2017 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Berlin, Germany, 6–8 November 2017; pp. 1–4. [Google Scholar]


| Year | Database | Journal | Conference | Total |
|---|---|---|---|---|
| 2021 | Scopus | 1 | 2 | 3 |
| 2020 | Scopus | 5 | 2 | 7 |
| 2019 | Scopus | 3 | 3 | 6 |
| 2018 | Scopus | 1 | 2 | 3 |
| 2017 | Scopus | 0 | 3 | 3 |
| 2016 | Scopus | 1 | 1 | 2 |
| 2015 | Scopus | 1 | 1 | 2 |
| 2013 | Scopus | 1 | 1 | 2 |
| 2012 | Scopus | 0 | 1 | 1 |
| Summary | 13 | 16 | 29 |
| Class | Ref | Year | Incident | Source | Location | Description |
|---|---|---|---|---|---|---|
| C | [24] | 2003 | Slammer Worm attack | OTR | USA | One of the FAA’s administrative servers was compromised through a slammer worm attack. Internet services were shut down in some parts of Asia as a result of this attack and this slowed down connections worldwide. |
| A | [25] | 2006 | Cyber-Attack | OTR | Alaska, USA | Two separate attacks on US Federal Aviation Administration (FAA) internet services that forced it to shut down some of its air traffic control systems. |
| C | [25] | 2008 | Malicious hacking attack | OTR | Oklahoma, USA | Hackers stole the administrative password of FAA’s interconnected networks when they took control of their system. By gaining access to the domain controller in the Western Pacific region, they were able to access more than 40,000 login credentials used to control part of the FAA’s mission-support network. |
| C | [26] | 2009 | Malicious hacking attack | OTR | USA | A malicious hacking attack on FAA’s computer, through which hackers gained access to personal information of 48,000 current and former FAA employees. |
| C | [27] | 2013 | Malware attack | OTR | Istanbul, Turkey | Shutting down of passport control system at the departure terminals of Istanbul Ataturk and Sabiha Gokcen airports due to a malware attack, leading to the delay of many flights. |
| C | [28] | 2013 | Hacking and phishing attacks | OTR | USA | Malicious hacking and phishing attacks that targeted about 75 airports. These major cyber-attacks were alleged to have been carried out by an undisclosed nation-state that sought to breach US commercial aviation networks. |
| A | [29] | 2015 | DDoS attack | OTR | Poland | A Distributed Denial-of-Service (DDoS) attack by cyber-criminals that affected LOT Polish Airlines flight-plan IT Network systems at the Warsaw Chopin airport. The attack rendered LOT’s system computers unable to send flight plans to the aircraft, thus grounding at least 10 flights, leaving about 1400 passengers stranded. |
| I | [30] | 2016 | Hacking, phishing attacks | OTR | Vietnam | The defacement of a website belonging to Vietnam airlines and flight information screens at Ho Chi Minh City and the capital, Hanoi, displaying messages supportive of China’s maritime claims in the South China Sea by Pro-Beijing hackers. |
| A | [31] | 2016 | Cyber-attack | OTR | Boryspil, Ukraine | A malware attack was detected in a computer in the IT network of Kyiv’s main airport, which includes the airport’s air traffic control system. |
| A | [30] | 2017 | Human error | OTR | United Kingdom | British flag-carrier computer systems failure caused by disconnection and re-connection of the data-center power supply by a contracted engineer. This accident left about 75,000 passengers of British Airways stranded. |
| C | [32] | 2018 | Data breach | OTR | Hong Kong | Cathay Pacific Airways data breach of about 9.4 million customers’ personal identifiable information. |
| C | [33] | 2018 | Data breach | OTR | United Kingdom | British Airways Data breach of about 380,000 customers’ personal identifiable information. |
| C | [34] | 2018 | Data breach | OTR | USA | Delta Air Lines Inc. and Sears Departmental stores reported a data breach of about 100,000 customers’ payment information through a third party. |
| A | [35] | 2018 | Ransomware attack | OTR | Bristol Airport, UK | An attack on electronic flight information screens at Bristol Airport. This resulted in the screen being taken offline and replaced with whiteboard information. There was no known adverse effect from this attack. |
| C | [36] | 2018 | Mobile app data breach | OTR | Air Canada, Canada | Air Canada reported a mobile app data breach affecting the personal data of 20,000 people. |
| C | [37] | 2018 | Data breach | OTR | Washington DC, USA | Data breach on a NASA server that led to possible compromise of stored personally identifiable information (PII) of employees on 23 October 2018. |
| C | [38] | 2018 | Ransomware attack | OTR | Chicago, USA | Boeing was hit by the WannaCry computer virus, but the attack was reported to have minimal damage to the company’s internal systems. |
| A | [20] | 2018 | Cyber-attack | TP | Sweden | Cyber-attack launched by Russian APT group (APT28) that blocked Sweden’s air traffic control capabilities, grounding hundreds of flights over a 5-day period. |
| A | [39] | 2019 | Bot attacks | OTR | Ben Gurion Airport, Israel | About 3 million bots attacks were blocked in a day by Israel’s airport authority, as they attempted to breach airport systems. |
| C | [40] | 2019 | Cyber-Incident | OTR | Toulouse, France | A cyber incident that resulted in unauthorised access to Airbus “Commercial Aircraft business” information systems. There was no known impact according to the report on Airbus’ commercial operations. |
| C | [41] | 2019 | Ransomware attack | OTR | Albany, USA | Albany International Airport experienced a ransomware attack on Christmas of 2019. The attackers successfully encrypted the entire database of the airport forcing the authorities to pay a ransom in exchange of the decryption key to a threat actor. |
| C | [42] | 2019 | Crypto mining Malware infection | OTR | Europe | Cyberbit researchers discovered through their security software, known as EDR, a network infection of more than 50% of the European airport workstations by a cryptocurrency mining malware. |
| C | [43] | 2019 | Phishing attack | OTR | New Zealand | A phishing attack targeted at Air New Zealand Airpoints customers. This attack compromised the personal information of approximately 112,000 customers, with names, details and Airpoints numbers among the data exposed. |
| C | [44] | 2020 | Ransomware attack | OTR | Denver, USA | A cyber-incident that involved the attacker accessing and stealing company data, which were later leaked online. |
| C | [45] | 2020 | Ransomware attack | OTR | San Antonio, USA | Data breach suffered by ST Engineering’s aerospace subsidiary in the USA that later lead to a ransomware attack by Maze Cyber-criminal. |
| I | [46] | 2021 | Software Error | OTR | Birmingham, United Kingdom | A software error in the IT system that could not recognise mass discrepancies between loadsheet and the flight plan, leading to the aircraft having 1606 kg more take-off mass than required. |
| Year | No. of Persons Affected | Airports Shut Down | Lost Flight Hours |
|---|---|---|---|
| 2003 | Not Provided | Not Provided | Not Provided |
| 2006 | Not Provided | 2 | Not Provided |
| 2008 | 40,000 | Not Provided | Not Provided |
| 2009 | 48,000 | Not Provided | Not Provided |
| 2013 | Not Provided | 77 | Not Provided |
| 2015 | 1400 | Not Provided | Not Provided |
| 2016 | Not Provided | Not Provided | Not Provided |
| 2017 | 75,000 | Not Provided | Not Provided |
| 2018 | 94,500,000 | Not Provided | 120 |
| 2019 | 112,000 | Not Provided | Not Provided |
| 2020 | Not Provided | Not Provided | Not Provided |
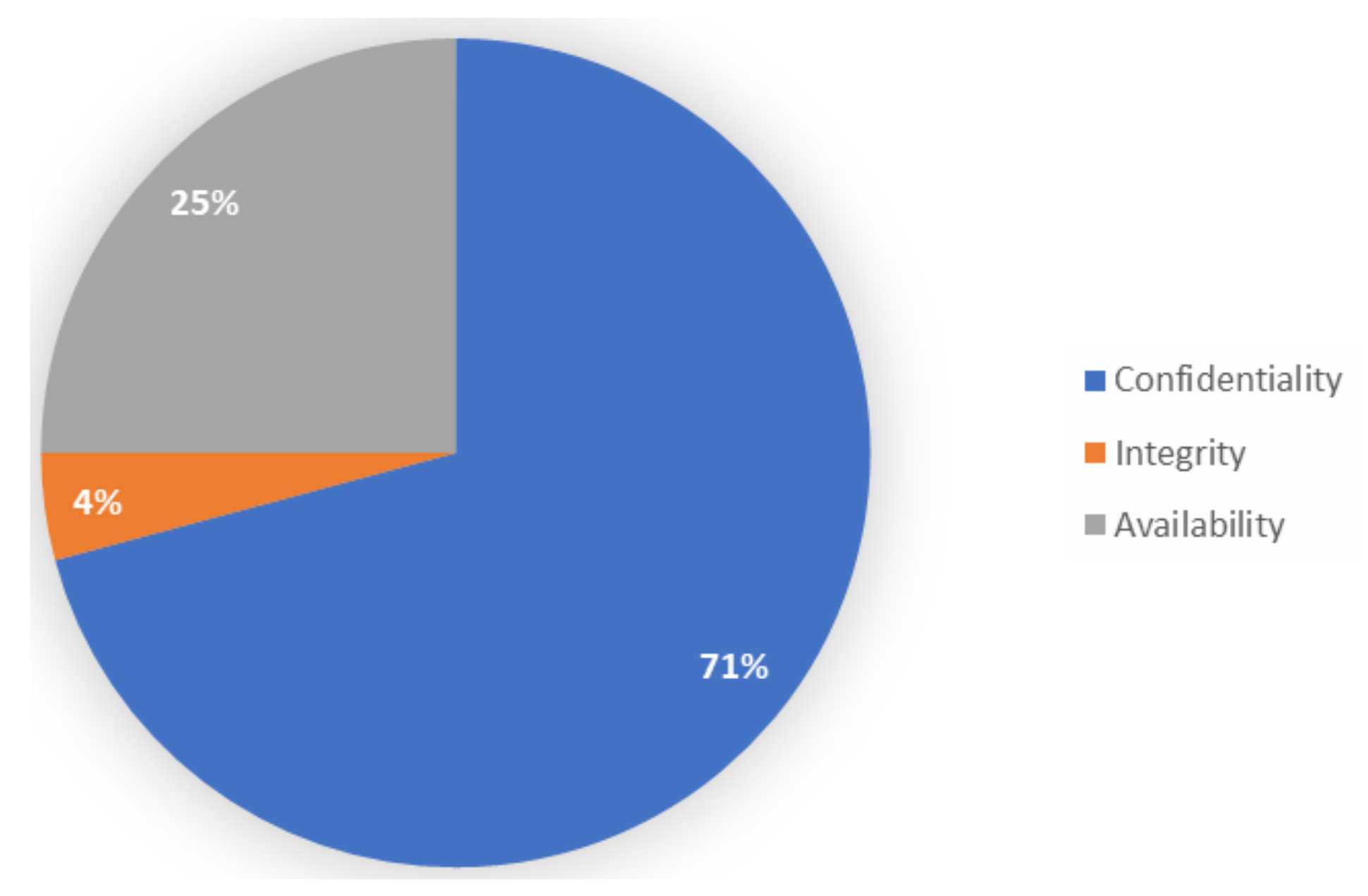
| Class | Ref | Component | Mitigation | Description |
|---|---|---|---|---|
| C,I | [53] | SATCOM terminals | Consistent patching and software updates, phasing out existing legacy encryption as soon as practicable and following current recommendations on the use of cryptographic algorithms and network protocols. | SATCOM terminals can be exploited through some design flaws in areas such as hardcoded credentials, insecure protocol, weak encryption algorithms. |
| C,I | [55,56] | Aerospace systems | Consistent patching of OS, phasing out existing legacy encryption as soon as practicable and following current recommendations on the use of cryptographic algorithms. | Attackers, based on skill level, can exploit issues with integration of OS in embedded systems, such as in OS kernel, context switching, protection mechanisms. |
| C,I | [65,66] | ACARS | Phasing out existing legacy encryption as soon as practicable and following current recommendations on the use of cryptographic algorithms and established policy measures. | The ACARS communication channel is susceptible to eavesdropping and privacy breach. |
| C,I | [71] | ADS-B | Phasing out existing legacy encryption as soon as practicable and following current recommendations on the use of cryptographic algorithms. | The ADS-B communication channel is prone to eavesdropping, jamming attacks, message injection, deletion and modification. |
| C,I | [62,63] | AWN | Phasing out existing legacy encryption as soon as practicable and following current recommendations on the use of cryptographic algorithms. | The Wireless Avionic Network communication channel is prone to data integrity problems such as data assurance, reliability and security. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ukwandu, E.; Ben-Farah, M.A.; Hindy, H.; Bures, M.; Atkinson, R.; Tachtatzis, C.; Andonovic, I.; Bellekens, X. Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends. Information 2022, 13, 146. https://doi.org/10.3390/info13030146
Ukwandu E, Ben-Farah MA, Hindy H, Bures M, Atkinson R, Tachtatzis C, Andonovic I, Bellekens X. Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends. Information. 2022; 13(3):146. https://doi.org/10.3390/info13030146
Chicago/Turabian StyleUkwandu, Elochukwu, Mohamed Amine Ben-Farah, Hanan Hindy, Miroslav Bures, Robert Atkinson, Christos Tachtatzis, Ivan Andonovic, and Xavier Bellekens. 2022. "Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends" Information 13, no. 3: 146. https://doi.org/10.3390/info13030146
APA StyleUkwandu, E., Ben-Farah, M. A., Hindy, H., Bures, M., Atkinson, R., Tachtatzis, C., Andonovic, I., & Bellekens, X. (2022). Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends. Information, 13(3), 146. https://doi.org/10.3390/info13030146












