CAPTIVE: Constrained Adversarial Perturbations to Thwart IC Reverse Engineering
Abstract
:1. Introduction
- We propose RecoG-Net, a convolutional neural network model, to fully recognize the gates from single/multiple layer(s) of SEM or the layout image(s) with approximately 100% accuracy.
- We propose CAPTIVE as a method to add DRC-complaint perturbation to layout images to thwart IC-RE. We perform different experiments to validate the efficiency of CAPTIVE.
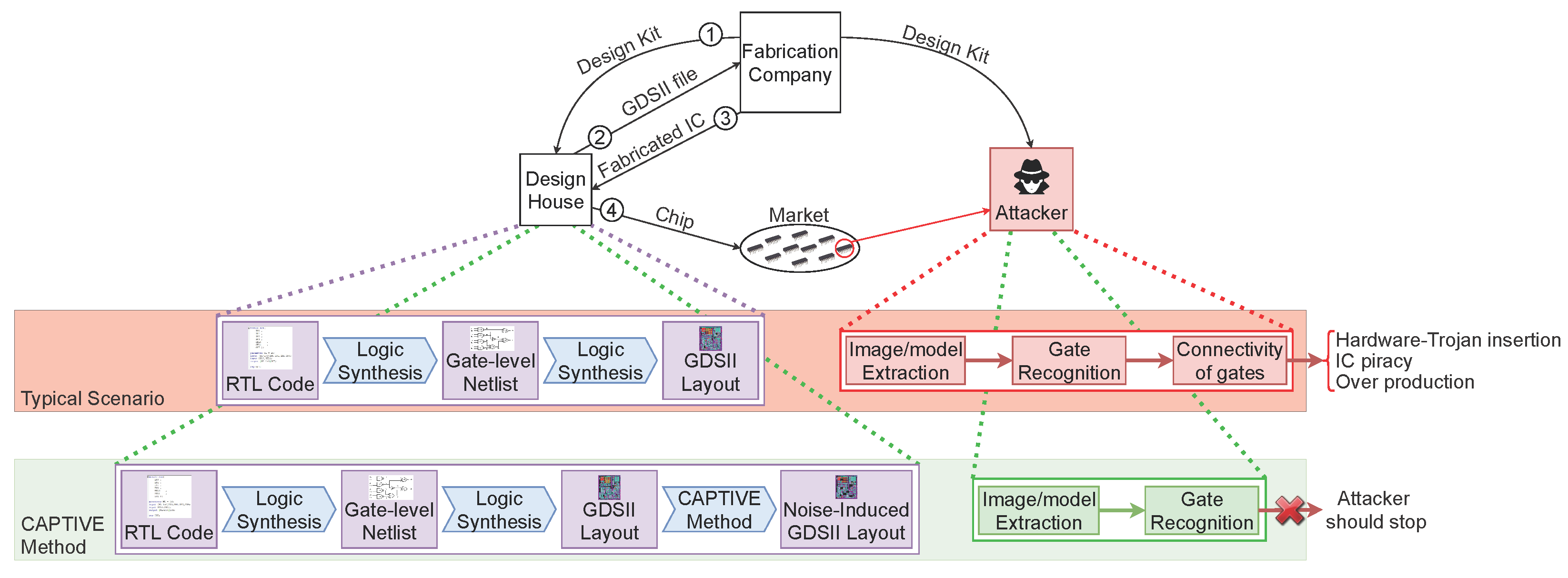
2. IC Reverse Engineering Attack
2.1. Attack Model
2.2. RecoG-Net: Surrogate Reverse Engineering Model
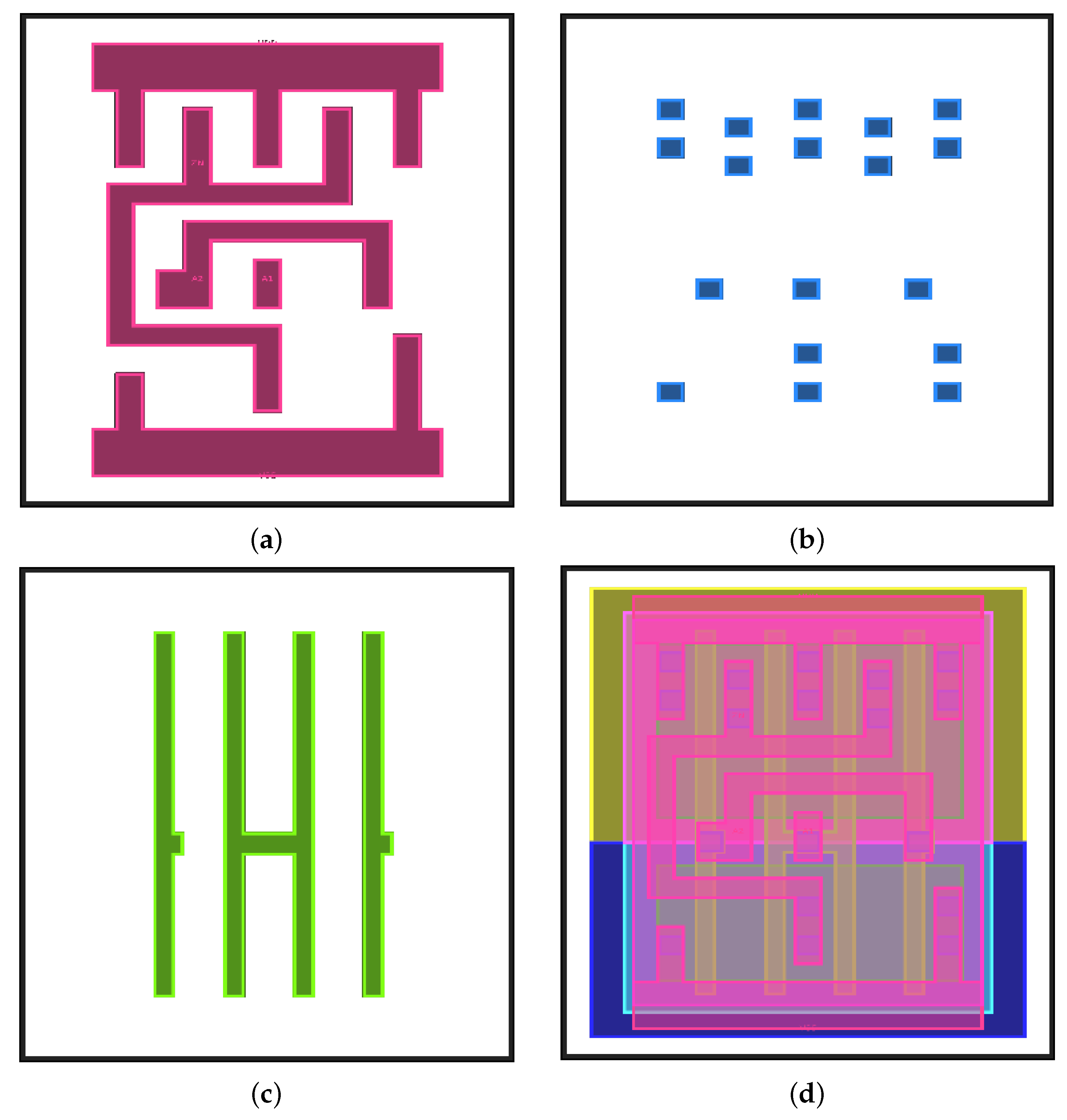
2.3. Training Dataset
2.4. Fabrication Impact
3. Adversarial Perturbation Methodology
| Algorithm 1: Experimental validation Setup |
 |
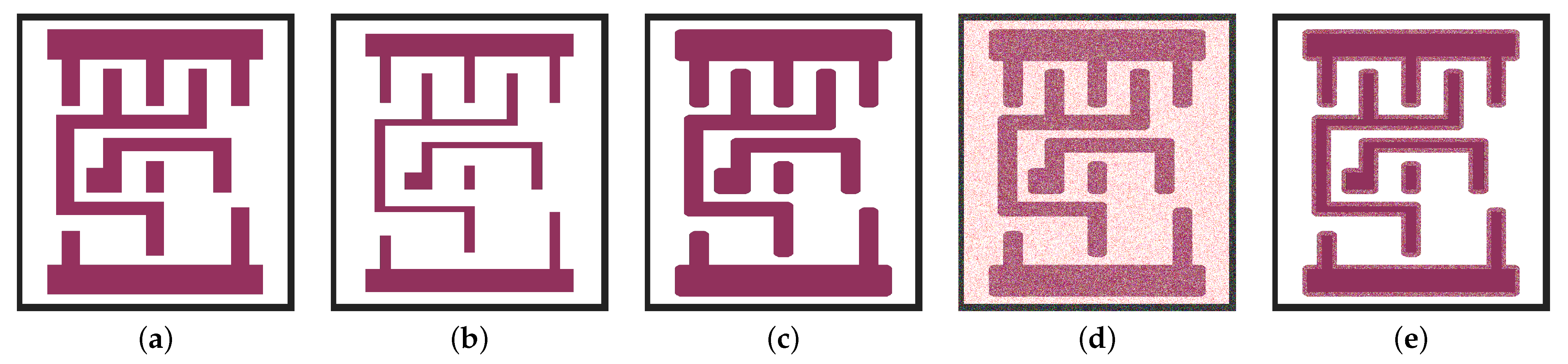
3.1. Perturbation Generation
3.2. Machine Learning Validation
3.3. DRC and LVS Validation
4. Results and Discussion
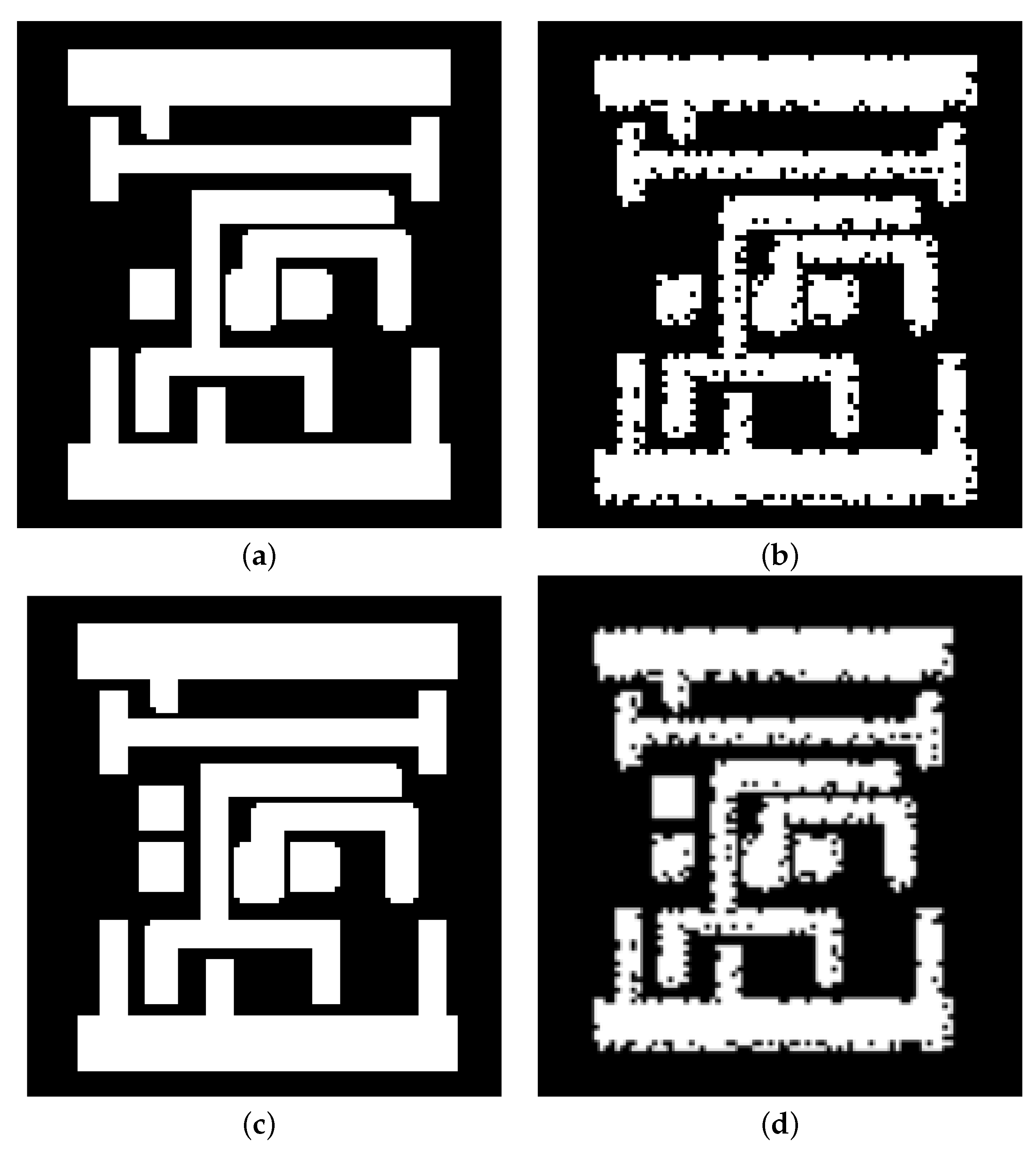
4.1. RecoG-Net Results
4.2. CAPTIVE Results
4.3. Related Work
5. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
Appendix A.1. Jacobian-Based Saliency Map Attack (JSMA)
Appendix A.2. DeepFool
Appendix A.3. Square-Box Attack
References
- Chen, J.C.; Rau, H.; Sun, C.J.; Stzeng, H.W.; Chen, C.H. Workflow design and management for IC supply chain. In Proceedings of the International Conference on Networking, Sensing and Control, Okayama, Japan, 26–29 March 2009. [Google Scholar]
- Hassan, R.; Kohle, G.; Rafatirad, S.; Homayoun, H.; Dinakarrao, S.M.P. A Cognitive SAT to SAT-Hard Clause Translation-based Logic Obfuscation. In Proceedings of the ACM/EDAA/IEEE Design Automation and Test in Europe, Grenoble, France, 1–5 February 2021. [Google Scholar]
- Torrance, R.; James, D. The state-of-the-art in semiconductor reverse engineering. In Proceedings of the 48th Design Automation Conference, San Diego, CA, USA, 5–9 June 2011; pp. 333–338. [Google Scholar]
- Akkaya, N.E.C.; Erbagci, B.; Mai, K. Combatting IC counterfeiting using secure chip odometers. In Proceedings of the IEEE International Electron Devices Meeting (IEDM), San Francisco, CA, USA, 2–6 December 2017. [Google Scholar]
- Dhavlle, A. Reverse Engineering of Integrated Circuits: Tools and Techniques. arXiv 2022, arXiv:2208.08689. [Google Scholar]
- Quadir, S.E.; Chen, J.; Forte, D.; Asadizanjani, N.; Shahbazmohamadi, S.; Wang, L.; Chandy, J.; Tehranipoor, M. A survey on chip to system reverse engineering. Acm J. Emerg. Technol. Comput. Syst. (JETC) 2016, 13, 1–34. [Google Scholar] [CrossRef]
- Yang, L.; Shi, C.J. FROSTY: A fast hierarchy extractor for industrial CMOS circuits. In Proceedings of the International Conference on Computer Aided Design, San Jose, CA, USA, 9–13 November 2003. [Google Scholar]
- Gate-Level Netlist Reverse Engineering Tool Set for Functionality Recovery and Malicious Logic Detection. In International Symposium for Testing and Failure Analysis; ASM International: Almere, The Netherlands, 2016.
- Azriel, L.; Speith, J.; Albartus, N.; Ginosar, R.; Mendelson, A.; Paar, C. A survey of algorithmic methods in IC reverse engineering. J. Cryptogr. Eng. 2021, 11, 219–315. [Google Scholar] [CrossRef]
- Dai, Y.Y.; Braytont, R.K. Circuit recognition with deep learning. In Proceedings of the IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Mclean, VA, USA, 1–5 May 2017. [Google Scholar]
- Fayyazi, A.; Shababi, S.; Nuzzo, P.; Nazarian, S.; Pedram, M. Deep Learning-Based Circuit Recognition Using Sparse Mapping and Level-Dependent Decaying Sum Circuit Representations. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 25–29 March 2019. [Google Scholar]
- Fyrbiak, M.; Strauß, S.; Kison, C.; Wallat, S.; Elson, M.; Rummel, N.; Paar, C. Hardware reverse engineering: Overview and open challenges. In Proceedings of the IEEE International Verification and Security Workshop (IVSW), Thessaloniki, Greece, 3–5 July 2017. [Google Scholar]
- Xiao, K.; Forte, D.; Jin, Y.; Karri, R.; Bhunia, S.; Tehranipoor, M. Hardware Trojans: Lessons Learned after One Decade of Research. ACM Trans. Des. Autom. Electron. Syst. 2016, 22, 1–23. [Google Scholar] [CrossRef]
- Torrance, R.; James, D. The state-of-the-art in IC reverse engineering. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2009; pp. 363–381. [Google Scholar]
- Botero, U.J.; Wilson, R.; Lu, H.; Rahman, M.T.; Mallaiyan, M.A.; Ganji, F.; Asadizanjani, N.; Tehranipoor, M.M.; Woodard, D.L.; Forte, D. Hardware Trust and Assurance through Reverse Engineering: A Tutorial and Outlook from Image Analysis and Machine Learning Perspectives. J. Emerg. Technol. Comput. Syst. 2021, 17, 1–53. [Google Scholar] [CrossRef]
- Holler, M.; Odstrcil, M.; Guizar-Sicairos, M.; Lebugle, M.; Müller, E.; Finizio, S.; Tinti, G.; David, C.; Zusman, J.; Unglaub, W.; et al. Three-dimensional imaging of integrated circuits with macro-to nanoscale zoom. Nat. Electron. 2019, 2, 464–470. [Google Scholar] [CrossRef]
- Ashrafiamiri, M.; Manoj Pudukotai Dinakarrao, S.; Afandizadeh Zargari, A.H.; Seo, M.; Kurdahi, F.; Homayoun, H. R2AD: Randomization and Reconstructor-based Adversarial Defense on Deep Neural Network. In Proceedings of the ACM/IEEE Workshop on Machine Learning for CAD, Canmore, AB, Canada, 2–4 September 2020. [Google Scholar]
- Yasaei, R.; Yu, S.Y.; Al Faruque, M.A. GNN4TJ: Graph Neural Networks for Hardware Trojan Detection at Register Transfer Level. In Proceedings of the IEEE/ACM Design Automation and Test in Europe Conference (DATE’21), Grenoble, France, 1–5 February 2021. [Google Scholar]
- Yasaei, R.; Yu, S.Y.; Kasaeyan Naeini, E.; Al Faruque, M.A. GNN4IP: Graph Neural Network for Hardware Intellectual Property Piracy Detection. In Proceedings of the IEEE/ACM Design Automation Conference (DAC’21), San Francisco, CA, USA, 5–9 December 2021. [Google Scholar]
- Aqajari, S.A.H.; Cao, R.; Naeini, E.K.; Calderon, M.D.; Zheng, K.; Dutt, N.; Liljeberg, P.; Salanterä, S.; Nelson, A.M.; Rahmani, A.M. Pain assessment tool with electrodermal activity for postoperative patients: Method validation study. JMIR mHealth uHealth 2021, 9, e25258. [Google Scholar] [CrossRef]
- Yasaei, R.; Hernandez, F.; Al Faruque, M.A. IoT-CAD: Context-aware adaptive anomaly detection in IoT systems through sensor association. In Proceedings of the 2020 IEEE/ACM International Conference On Computer Aided Design (ICCAD), Virtual Event, 2–5 November 2020; pp. 1–9. [Google Scholar]
- Moosavi-Dezfooli, S.M.; Fawzi, A.; Frossard, P. Deepfool: A simple and accurate method to fool deep neural networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 26 June–1 July 2016; pp. 2574–2582. [Google Scholar]
- Papernot, N.; McDaniel, P.; Jha, S.; Fredrikson, M.; Celik, Z.B.; Swami, A. The limitations of deep learning in adversarial settings. In Proceedings of the 2016 IEEE European Symposium on Security and Privacy (EuroS&P), Saarbruecken, Germany, 21–24 March 2016; pp. 372–387. [Google Scholar]
- Andriushchenko, M.; Croce, F.; Flammarion, N.; Hein, M. Square attack: A query-efficient black-box adversarial attack via random search. In European Conference on Computer Vision; Springer: Berlin/Heidelberg, Germany, 2020; pp. 484–501. [Google Scholar]
- Lippmann, B.; Werner, M.; Unverricht, N.; Singla, A.; Egger, P.; Dübotzky, A.; Gieser, H.; Rasche, M.; Kellermann, O.; Graeb, H. Integrated Flow for Reverse Engineering of Nanoscale Technologies. In Proceedings of the Asia and South Pacific Design Automation Conference, Tokyo, Japan, 21–24 January 2019. [Google Scholar]
- Vijayakumar, A.; Patil, V.C.; Holcomb, D.E.; Paar, C.; Kundu, S. Physical Design Obfuscation of Hardware: A Comprehensive Investigation of Device and Logic-Level Techniques. IEEE Trans. Inf. Forensics Secur. 2017, 12, 64–77. [Google Scholar] [CrossRef]
- Gascón, A.; Subramanyan, P.; Dutertre, B.; Tiwari, A.; Jovanović, D.; Malik, S. Template-based circuit understanding. In Proceedings of the Formal Methods in Computer-Aided Design (FMCAD), Lausanne, Switzerland, 21–24 October 2014. [Google Scholar]
- Degate: VLSI-Reverse Engineering of Digital Logic in Integrated Circuits (ICs). Available online: https://www.degate.org/ (accessed on 5 December 2023).
- Dinakarrao, S.M.P.; Amberkar, S.; Rafatirad, S.; Homayoun, H. Enhancing Adversarial Training towards Robust Machine Learners and its Analysis. In Proceedings of the International Conference on Computer-Aided Design (ICCAD), San Diego, CA, USA, 5–8 November 2018. [Google Scholar]
- Biggio, B.; Nelson, B.; Laskov, P. Poisoning Attacks Against Support Vector Machines. In Proceedings of the International Conference on Machine Learning, Edinburgh, UK, 26 June–1 July 2012. [Google Scholar]
- Feinman, R.; Curtin, R.R.; Shintre, S.; Gardner, A.B. Detecting Adversarial Samples from Artifacts. arXiv 2017, arXiv:1703.00410. [Google Scholar]
- Liu, Y.; Chen, X.; Liu, C.; Song, D. Delving into Transferable Adversarial Examples and Black-box Attacks. In Proceedings of the International Conference on Learning Representations (ICLR), Toulon, France, 24–26 April 2017. [Google Scholar]
- Lowd, D.; Meek, C. Adversarial Learning. In Proceedings of the ACM SIGKDD International Conference on Knowledge Discovery in Data Mining, Chicago, IL, USA, 21–24 August 2005. [Google Scholar]
- Matsumoto, T.; Matsumoto, H.; Yamada, K.; Hoshino, S. Impact of Artificial “Gummy” Fingers on Fingerprint Systems. In Proceedings of the Optical Security and Counterfeit Deterrence Techniques IV, San Jose, CA, USA, 23–25 January 2002; Volume 26. [Google Scholar]
- Muñoz-González, L.; Biggio, B.; Demontis, A.; Paudice, A.; Wongrassamee, V.; Lupu, E.; Roli, F. Towards Poisoning of Deep Learning Algorithms with Back-gradient Optimization. In Proceedings of the ACM Workshop on Artificial Intelligence and Security, Dallas, TX, USA, 27–38 November 2017. [Google Scholar]
- Cheng, K.L.; Wu, C.C.; Wang, Y.P.; Lin, D.W.; Chu, C.M.; Tarng, Y.Y.; Lu, S.Y.; Yang, S.J.; Hsieh, M.H.; Liu, C.M.; et al. A highly scaled, high performance 45 nm bulk logic CMOS technology with 0.242 μm2 SRAM cell. In Proceedings of the IEEE International Electron Devices Meeting, Washington, DC, USA, 10–12 December 2007. [Google Scholar]
- Yasin, M.; Sinanoglu, O. Transforming between logic locking and IC camouflaging. In Proceedings of the International Design Test Symposium (IDT), Amman, Jordan, 14–16 December 2015. [Google Scholar]
- Kolhe, G.; Kamali, H.M.; Naicker, M.; Sheaves, T.D.; Mahmoodi, H.; Sai Manoj, P.D.; Homayoun, H.; Rafatirad, S.; Sasan, A. Security and Complexity Analysis of LUT-based Obfuscation: From Blueprint to Reality. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019. [Google Scholar]
- Rajarathnam, R.S.; Lin, Y.; Jin, Y.; Pan, D.Z. ReGDS: A Reverse Engineering Framework from GDSII to Gate-level Netlist. In Proceedings of the IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 7–11 December 2020. [Google Scholar]
- Pix2Net Manual. Available online: http://micronetsol.net/html_manual/index.html# (accessed on 12 May 2023).

| Layer | Structure | Output |
|---|---|---|
| Conv2d + Relu | 32 × 3 × 3 | 256 × 1047 × 32 |
| Conv2d + Relu | 64 × 3 × 3 | 254 × 1045 × 64 |
| Max pooling2d | 3 × 3 | 84 × 348 × 64 |
| Dropout | 0.5 | 84 × 348 × 64 |
| Conv2d + Relu | 32 × 3 × 3 | 82 × 346 × 32 |
| Conv2d + Relu | 64 × 3 × 3 | 80 × 344 × 64 |
| Max pooling2d | 3 × 3 | 26 × 114 × 64 |
| Dropout | 0.5 | 26 × 114 × 64 |
| Flatten | 189,696 | |
| Dense + Relu | 250 | 250 |
| Dense + linear | 11 | 11 |
| Layer Name | Contact Layer | Poly Layer | Metal1 Layer | All Layers |
|---|---|---|---|---|
| Train Accuracy | 100% | 99% | 100% | 100% |
| Test Accuracy | 99% | 78% | 99% | 100% |
| Layer | Perturbation Method | Adversarial Accuracy | DRC-Compliant Accuracy | Improvement |
|---|---|---|---|---|
| Metal | JSMA | 57.5% | 63% | 36.8% |
| DeepFool | 50.1% | 62.7% | 37.1% | |
| Square-box | 32.7% | 38.9% | 60.9% | |
| Contact | JSMA | 51% | 72.4% | 27.6% |
| DeepFool | 62.5% | 67.7% | 32.3% | |
| Square-box | 31.9% | 46% | 54% |
| Network “A” | Network “B” | ||
|---|---|---|---|
| Layer | Structure | Layer | Structure |
| Conv2d + Relu | 32 × 3 × 3 | Conv2d + Relu | 32 × 3 × 3 |
| Conv2d + Relu | 32 × 3 × 3 | Conv2d + Relu | 64 × 3 × 3 |
| Max pooling2d | 3 × 3 | Conv2d + Relu | 64 × 3 × 3 |
| Dropout | 0.7 | Max pooling2d | 3 × 3 |
| Conv2d + Relu | 32 × 3 × 3 | Dropout | 0.5 |
| Conv2d + Relu | 32 × 3 × 3 | Conv2d + Relu | 32 × 3 × 3 |
| Max pooling2d | 3 × 3 | Conv2d + Relu | 64 × 3 × 3 |
| Dropout | 0.7 | Max pooling2d | 3 × 3 |
| Dense + Relu | 250 | Dropout | 0.5 |
| Dense + linear | 11 | Dense + Relu | 250 |
| Dense + Relu | 120 | ||
| Dense + linear | 11 | ||
| Layer | Perturbation Method | Network “A” | Network “B” | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Noise-Free Accuracy | Adversarial Accuracy | DRC-Compliant Accuracy | Improvement | Noise-Free Accuracy | Adversarial Accuracy | DRC-Compliant Accuracy | Improvement | ||
| Metal | JSMA | 64% | 70.5% | 29.4% | 79% | 81.4% | 18% | ||
| DeepFool | 99.9% | 52.4% | 57.1% | 42.8% | 99.4% | 54% | 62.4% | 37% | |
| Square-box | 27% | 34.2% | 65.7% | 39.4% | 43% | 56.4% | |||
| Contact | JSMA | 51% | 67% | 32.4% | 67.4% | 84.5% | 15.5% | ||
| DeepFool | 99.4% | 60% | 67.4% | 32% | 100% | 68% | 75.4% | 24.6% | |
| Square-box | 24.5% | 29.6% | 69.8% | 30% | 36.4% | 63.6% | |||
| Layer | Perturbation Method | Adversarial Accuracy | DRC-Compliant Accuracy | Improvement |
|---|---|---|---|---|
| Metal | JSMA | 59.2% | 78.3% | 21.4% |
| DeepFool | 67.4% | 76.9% | 22.8% | |
| Square-box | 51% | 59.4% | 40.3% | |
| Contact | JSMA | 67% | 96.2% | 3% |
| DeepFool | 44.1% | 75.5% | 23.7% | |
| Square-box | 35.6% | 71.8% | 27.4% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zargari, A.H.A.; AshrafiAmiri, M.; Seo, M.; Pudukotai Dinakarrao, S.M.; Fouda, M.E.; Kurdahi, F. CAPTIVE: Constrained Adversarial Perturbations to Thwart IC Reverse Engineering. Information 2023, 14, 656. https://doi.org/10.3390/info14120656
Zargari AHA, AshrafiAmiri M, Seo M, Pudukotai Dinakarrao SM, Fouda ME, Kurdahi F. CAPTIVE: Constrained Adversarial Perturbations to Thwart IC Reverse Engineering. Information. 2023; 14(12):656. https://doi.org/10.3390/info14120656
Chicago/Turabian StyleZargari, Amir Hosein Afandizadeh, Marzieh AshrafiAmiri, Minjun Seo, Sai Manoj Pudukotai Dinakarrao, Mohammed E. Fouda, and Fadi Kurdahi. 2023. "CAPTIVE: Constrained Adversarial Perturbations to Thwart IC Reverse Engineering" Information 14, no. 12: 656. https://doi.org/10.3390/info14120656
APA StyleZargari, A. H. A., AshrafiAmiri, M., Seo, M., Pudukotai Dinakarrao, S. M., Fouda, M. E., & Kurdahi, F. (2023). CAPTIVE: Constrained Adversarial Perturbations to Thwart IC Reverse Engineering. Information, 14(12), 656. https://doi.org/10.3390/info14120656






