Abstract
Transforming data into ciphertexts and storing them in the cloud database is a secure way to simplify data management. Public key encryption with keyword search (PEKS) is an important cryptographic primitive as it provides the ability to search for the desired files among ciphertexts. As a variant of PEKS, certificateless public key authenticated encryption with keyword search (CLPAEKS) not only simplifies certificate management but also could resist keyword guessing attacks (KGA). In this paper, we analyze the security models of two recent CLPAEKS schemes and find that they ignore the threat that, upon capturing two trapdoors, the adversary could directly compare them and distinguish whether they are generated using the same keyword. To cope with this threat, we propose an improved security model and define the notion of strong trapdoor indistinguishability. We then propose a new CLPAEKS scheme and prove it to be secure under the improved security model based on the intractability of the DBDH problem and the DDH problem in the targeted bilinear group.
1. Introduction
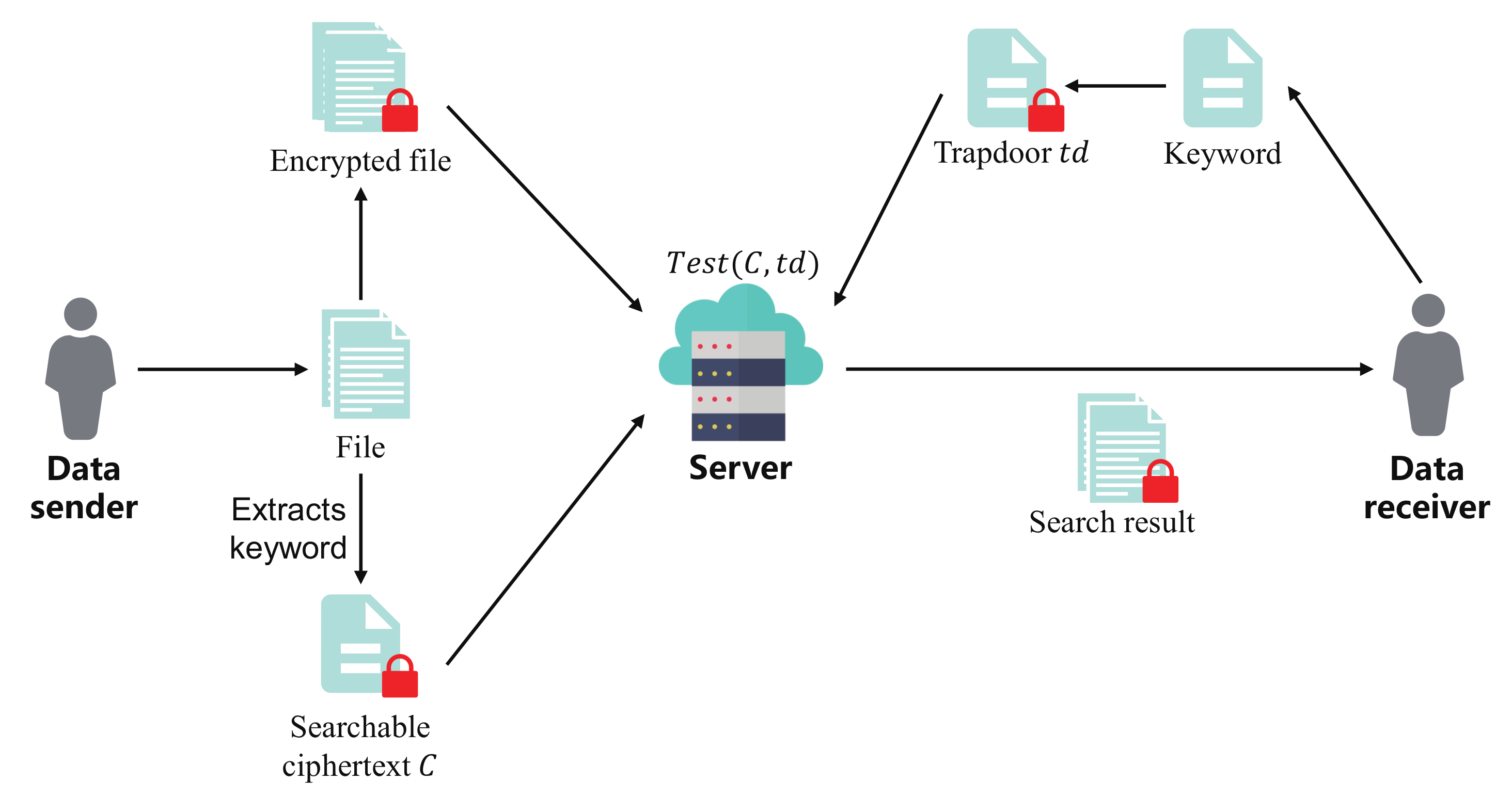
Boneh et al. [1] first proposed the notion of public key encryption with keyword search (PEKS). As shown in Figure 1, the workflow of PEKS includes:
- 1.
- The data sender uses the file’s keyword to generate the searchable ciphertext C and uploads it along with the encrypted file to the cloud server.
- 2.
- The data receiver uses its desired keyword to generate the trapdoor and sends it to the cloud server.
- 3.
- The cloud server runs an algorithm called to check whether C and contain the same keyword and returns the corresponding file to the receiver if it does. During the search, the cloud server is unable to know the keyword as well as the content of the file.
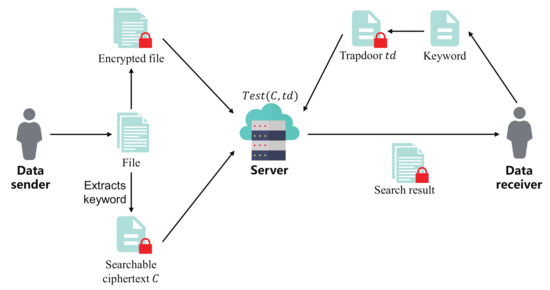
Figure 1.
The general framework of PEKS.
Figure 1.
The general framework of PEKS.
PEKS could be applied to encrypted instant messaging apps. The client-side archive of chat logs may suffer from mistaken deletion and limited storage space. Therefore, some instant messaging apps (e.g., Google Talk and Yahoo Messenger 11 Beta) support saving chat logs on a server for future retrieval. Encrypting chat logs before uploading is a proactive defense against cyber attacks and data breaches. However, encryption destroys the original features of data and thus invalidates the traditional searching methods. Downloading and decrypting all chat logs before searching seems like a solution, but this process incurs unnecessary transmission overhead. As mentioned earlier, PEKS provides an efficient way for users to search for their desired files among encrypted chat logs.
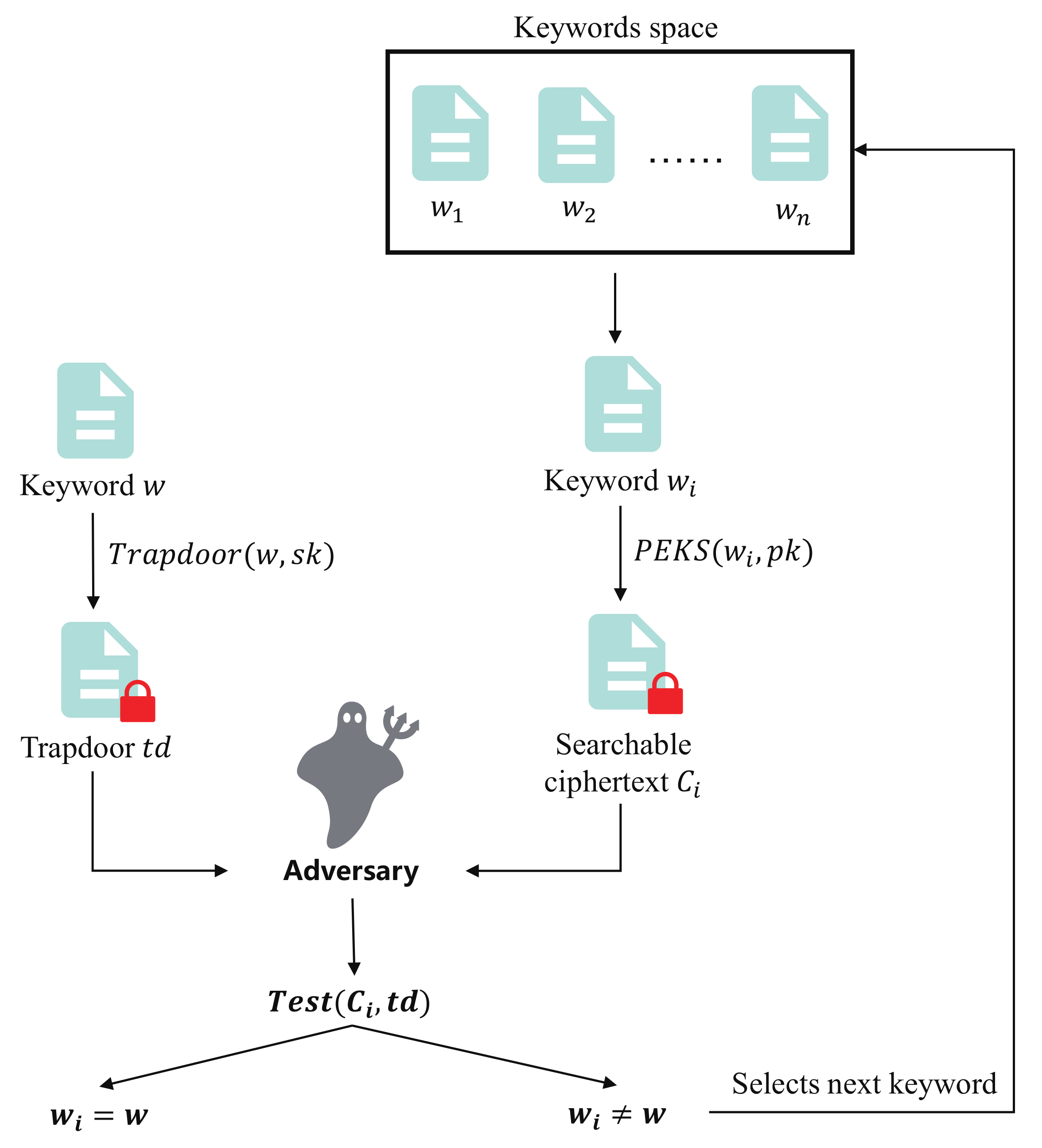
Ideally, the distribution of keywords is assumed to be uniform, and the size of keywords space is assumed to be super-polynomial. However, in practice, the distribution of keywords may be uneven, and keywords space may be much smaller. Therefore, it may be feasible for the adversary to guess the keyword of a file by launching keyword guessing attacks (KGA) [2,3]. As shown in Figure 2, upon capturing the trapdoor, the adversary guesses the keyword w concealed in the trapdoor by encrypting every possible keyword and running algorithm. There are two types of KGA: the first type is outside KGA, launched by anyone other than the cloud server; the second type is inside KGA, launched by the cloud server. A searchable encryption scheme that could resist KGA should simultaneously satisfy ciphertext indistinguishability and trapdoor indistinguishability [4].
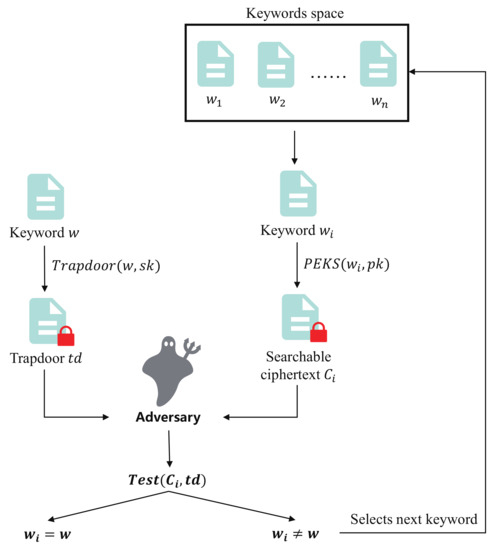
Figure 2.
Keyword guessing attacks.
1.1. Related Works
Song et al. [5] proposed a searchable symmetric encryption scheme. However, it suffers from problematic key distribution in symmetric key cryptography. To solve this problem, Boneh et al. [1] proposed public key encryption with keyword search (PEKS). However, the initial PEKS scheme [1] is vulnerable to KGA [2,3]. Rhee et al. [4] first formally defined trapdoor indistinguishability and proved that trapdoor indistinguishability is a necessary condition for a PEKS scheme to be secure against KGA. They also proposed a designated-tester PEKS (dPEKS) scheme that could resist outside KGA. Later, some improved dPEKS schemes [6,7] were proposed, but none of them could resist inside KGA.
To resist both outside and inside KGA, Wang and Tu [8] proposed a PEKS scheme based on a dual-server setting. However, their scheme is still vulnerable inside KGA if two servers collude. Huang and Li [9] proposed the first public key authenticated encryption with keyword search (PAEKS) scheme, which is similar to [10]. In PAEKS, the sender’s secret key is involved in the ciphertext generation. As a result, the cloud server cannot launch inside KGA successfully unless it obtains either the sender’s secret key or the receiver’s secret key. Later, some PAEKS schemes with stronger ciphertext indistinguishability were proposed [11,12]. Pan and Li [13] proposed a PAEKS scheme with stronger trapdoor indistinguishability. However, their scheme cannot provide stronger ciphertext indistinguishability [14].
The aforementioned schemes are based on public key infrastructure and thus suffer from complicated certificate management. To solve this problem, Abdalla et al. [15] proposed the notion of identity-based encryption with keyword search (IBEKS), which integrates search function into identity-based encryption [16]. Li et al. [17] proposed the first IBEKS scheme that could resist both outside and inside KGA.
To solve the key escrow problem in IBEKS, Peng et al. [18] proposed the first searchable encryption scheme based on certificateless public key cryptography [19]. However, Peng et al.’s scheme are vulnerable to both outside and inside KGA. Therefore, some certificates PAEKS (CLPAEKS) schemes [20,21,22] were proposed. Pakniat et al. [23] analyzed the flaws of the security models defined in [20,21,22] and proposed an improved security model. They also presented a new CLPAEKS scheme with provable security in the proposed security model. Shiraly et al. [24] proposed an efficient CLPAEKS scheme that gets rid of the time-consuming Hash-To-Point [25] computation and bilinear pairing [16] computation.
1.2. Motivation and Contribution
We notice that in Pakniat et al.’s work [23] and Shiraly et al.’s work [24], in the games that formally define trapdoor indistinguishability, the adversary cannot query to trapdoor oracle, in which is the challenge sender, is the challenge receiver, and is the challenge keyword.
However, in practice, the same keyword may be used for different searches. As a result, the trapdoor corresponding to may appear repeatedly. For privacy protection, it would be necessary to prevent the adversary from successfully determining whether two trapdoors are generated using the same keyword. Therefore, it is necessary to get rid of the aforementioned limitation when defining trapdoor indistinguishability.
Following are the contributions we make in this paper:
- 1.
- We propose an improved security model, in which the notion of strong trapdoor indistinguishability is defined.
- 2.
- We propose a new CLPAEKS scheme and prove it to be secure under the improved security model based on the intractability of the DBDH problem and the DDH problem in the targeted bilinear group.
2. Preliminaries
Suppose that is a probabilistic-polynomial-time (PPT) adversary, and are cyclic groups with the same prime order p.
2.1. Bilinear Pairing
A bilinear pairing has the following features:
- Bilinearity: For any and any , .
- Non-degeneracy: Suppose that is a generator of , .
- Computability: For any , can be computed in polynomial time.
2.2. Decisional Diffie–Hellman (DDH) Assumption in
Given , in which is a generator of , . ’s aim is to determine whether or , in which r is randomly selected from . The DDH assumption in holds if ’s advantage
is negligible.
2.3. Decisional Bilinear Diffie–Hellman (DBDH) Assumption
Given and , in which . ’s aim is to determine whether or , in which r is randomly selected from . The DBDH assumption holds if ’s advantage
is negligible.
3. Definition of CLPAEKS
3.1. System Model
The following three types of entities are involved in our CLPAEKS scheme.
- Key generation center (KGC): KGC generates the master secret key, the public parameters, and every user’s partial secret key.
- Users: Include the sender and the receiver, which have been introduced in Section 1. Every user randomly selects a secret value and then generates its secret key using its partial secret key and the secret value.
- Cloud Server: It is a semi-trusted party managing the encrypted cloud database and responding to search requests.
3.2. Algorithms
The frequently used symbols are defined in Table 1. Our CLPAEKS scheme consists of the following algorithms.

Table 1.
Notations.
- 1.
- : Run by KGC.
- Input: .
- Output: and .
- 2.
- : Run by KGC.
- Input: , , and .
- Output: .
- 3.
- : Run by the user .
- Input: , .
- Output: .
- 4.
- : Run by the user .
- Input: , , .
- Output: .
- 5.
- : Run by the user .
- Input: , .
- Output: .
- 6.
- : Run by the sender .
- Input: , , , , , and a keyword w.
- Output: C.
- 7.
- : Run by the receiver .
- Input: , , , , , w.
- Output: .
- 8.
- : Run by the cloud server.
- Input: and .
- Output: 1 will be output if , and 0 otherwise.
3.3. Security Model
The following two types of PPT adversaries are considered:
- Type-1 adversary: Denote this type of adversary with . can replace any user’s public key but cannot get the master secret key.
- Type-2 adversary: Denote this type of adversary with . can get the master secret key but cannot replace any user’s public key.
We consider two security properties, ciphertext indistinguishability and trapdoor indistinguishability. Since there are two types of adversaries in certificateless cryptosystems, we define the semantic security of CLPAEKS via four games. In Game and Game , we formally define ciphertext indistinguishability in the same way as [23,24]. In Game and Game , we formally define a stronger version of trapdoor indistinguishability. Different from [23,24], the adversary against trapdoor indistinguishability could freely access the trapdoor oracle in the games, which makes our definition of trapdoor indistinguishability stronger.
3.3.1. Game
- 1.
- Setup: The challenger sends to .
- 2.
- Phase 1: is allowed to access the following oracles.
- : Given , returns .
- : Given , returns .
- : Given , returns . cannot occur in if ’s public key has been replaced.
- : Given and a new public key , replaces with .
- : Given , and w, returns .
- : Given , and w, returns , .
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither nor has been submitted to ; (3) Neither (, , ) nor (, , ) has been submitted to . randomly selects and sends to .
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins the game. ’s advantage is defined as
Definition 1.
Our scheme satisfies ciphertext indistinguishability under adaptive chosen-keyword attacks (CT-IND-CKA) against Type-1 adversary if is negligible.
3.3.2. Game
- 1.
- Setup: The challenger sends and to .
- 2.
- Phase 1: can is allowed to access the following oracles.
- : Same as in Game .
- : Same as in Game .
- : Given , returns .
- : Same as in Game .
- : Same as in Game .
- 3.
- Challenge: selects , , and two keywords (, ) for challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither (, , ) nor (, , ) has been submitted to . randomly selects and sends to .
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins the game. ’s advantage is defined as
Definition 2.
Our scheme satisfies CT-IND-CKA against Type-2 adversary if is negligible.
3.3.3. Game
- 1.
- Setup: The challenger sends to .
- 2.
- Phase 1: Same as Phase 1 in Game .
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither nor has been submitted to ; (3) Neither (, , ) nor (, , ) has been submitted to . randomly selects and sends to .
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins the game. ’s advantage is defined as
Definition 3.
Our scheme satisfies strong trapdoor indistinguishability under adaptive chosen-keyword attacks (S-TD-IND-CKA) against Type-1 adversary if is negligible.
3.3.4. Game
- 1.
- Setup: The challenger sends and to .
- 2.
- Phase 1: Same as Phase 1 in Game .
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither (, , ) nor (, , ) has been submitted to . randomly selects and sends to .
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins the game. ’s advantage is defined as
Definition 4.
Our scheme satisfies S-TD-IND-CKA against Type-2 adversary if is negligible.
4. The Proposed CLPAEKS Scheme
The frequently used symbols have been defined in Table 1. Following are the details of our CLPAEKS scheme.
- 1.
- : Run by KGC.
- Input: Security parameter .
- Select two cyclic groups and with the same prime order and a bilinear pairing . Randomly select two generators and .
- Define 3 collision-resistant hash functions:
- −
- . It takes the user’s identity as input.
- −
- . It takes the keyword as input.
- −
- .
- Randomly select . Set master secret key and master public key .
- Output: .
- 2.
- : Run by KGC.
- Input: , , and a user’s identity .
- Output: ’s partial secret key .
- 3.
- : Run by the user .
- Input: , .
- Output: ’s secret value , which is randomly selected from .
- 4.
- : Run by the user .
- Input: , , .
- Output: ’s secret key .
- 5.
- : Run by the user .
- Input: , .
- Output: ’s public key .
- 6.
- : Run by the sender .
- Input: , , , , , and a keyword w.
- Randomly select .
- Compute :in which
- Output: .
- 7.
- : Run by the receiver .
- Input: , , , , , and a keyword w.
- Randomly select .
- Compute :in which
- Output: .
- 8.
- : Run by the cloud server.
- Input: and .
- Output: Check whetherholds, if it holds then output 1, and 0 otherwise.
5. Security Analysis
5.1. CT-IND-CKA against Type-1 Adversary
Theorem 1.
Our scheme satisfies CT-IND-CKA against Type-1 adversary in the random oracle model if the DBDH assumption holds.
Proof.
Suppose that . Given a DBDH instance . Denoted by that , and by that Z is random. In the following, we construct a simulator that runs as a subroutine to correctly guess the value of .
- 1.
- Setup: sets , implying that , in which is unknown to . Then sends to .
- 2.
- Phase 1: is allowed to access the following oracles.
- : Suppose that there are distinct queries to . randomly selects as its guess of the identities selected by for challenge. For :
- −
- If , adds to list and returns to .
- −
- If , adds to list and returns to .
- −
- Otherwise, randomly selects , adds to list , and returns to .
If the repeated queries are submitted, the answer that already exists in will be returned. - : Given , randomly selects , adds to list , and returns . If the repeated queries are submitted, the answer that already exists in will be returned.
- : Given . randomly selects , adds to list , and returns . If the repeated queries are submitted, the answer that already exists in will be returned.
- : randomly selects , then:
- −
- If , calls , retrieves from , setsadds to list , and returns .
- −
- Otherwise, calls and setsadds to list , and returns .
If the repeated queries are submitted, the answer that already exists in will be returned. - :
- −
- If , aborts.
- −
- Otherwise, calls , retrieves from , and returns .
- :
- −
- If , aborts.
- −
- Otherwise, calls , retrieves from , and returns .
cannot occur in if ’s public key has been replaced. - : calls and replaces with .
- : randomly selects and returnsin which k is different based on the following cases.
- −
- If , .
- −
- If , .
- −
- Otherwise, it means that .
- ∗
- If , retrieves from and computes .
- ∗
- Otherwise, retrieves from and computes .
- : randomly selects and returnsin which k is different based on the following cases.
- −
- If , .
- −
- If , .
- −
- Otherwise, it means that .
- ∗
- If , retrieves from and computes .
- ∗
- Otherwise, retrieves from and computes .
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither nor has been submitted to ; (3) Neither (, , ) nor (, , ) has been submitted to . If , aborts and randomly returns . Otherwise, randomly selects and sends to , in which
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins, and returns . Otherwise, loses, and returns .
If , perfectly simulates Section 3.3.1, and ’s probability of winning is . Otherwise, is independent of , and ’s probability of winning is . aborts and randomly returns if its guess of the identities selected by for challenge is wrong. Denote ’s abortion with , we have
’s advantage in solving the DBDH problem is
is negligible due to the intractability of the DBDH problem. This completes the proof. □
5.2. CT-IND-CKA against Type-2 Adversary
Theorem 2.
Our scheme satisfies CT-IND-CKA against Type-2 adversary in the random oracle model if the DDH assumption in holds.
Proof.
Suppose that . Given a DDH instance . Denoted by that , and by that Z is random. In the following, we construct a simulator that runs as a subroutine to correctly guess the value of .
- 1.
- Setup: sends and to .
- 2.
- Phase 1: is allowed to access the following oracles:
- : randomly selects , adds to list , and returns . If the repeated queries are submitted, the answer that already exists in will be returned. Suppose that there are distinct queries to . randomly selects as its guess of the identities selected by for challenge.
- : Same as in the proof of Theorem 1.
- : Same as in the proof of Theorem 1.
- : calls and retrieves from , then:
- −
- If , setsadds to list , and returns to .
- −
- If , setsadds to list , and returns to .
- −
- Otherwise, randomly selects , setsadds to list , and returns to .
If the repeated queries are submitted, the answer that already exists in will be returned. - : calls , retrieves from , and returns to .
- :
- −
- If , aborts.
- −
- Otherwise, calls , retrieves from , and returns .
- : randomly selects and returnsin which k is different based on the following cases.
- −
- If , .
- −
- If , .
- −
- Otherwise, it means that .
- ∗
- If , retrieves from and computes .
- ∗
- Otherwise, retrieves from and computes .
- : randomly selects and returnsin which k is different based on the following cases.
- −
- If , .
- −
- If , .
- −
- Otherwise, it means that .
- ∗
- If , retrieves from and computes .
- ∗
- Otherwise, retrieves from and computes .
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither (, , ) nor (, , ) has been submitted to . If , aborts and randomly returns . Otherwise, randomly selects and sends to , in which
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins, and returns . If , loses, and returns .
If , perfectly simulates Section 3.3.2, and ’s probability of winning is . Otherwise, is independent of , and ’s probability of winning is . aborts and randomly returns if its guess of the identities selected by for challenge is wrong. Denote ’s abortion with , we have
’s advantage in solving the DDH problem in is
is negligible due to the intractability of the DDH problem in . This completes the proof. □
5.3. S-TD-IND-CKA against Type-1 Adversary
Theorem 3.
Our scheme satisfies S-TD-IND-CKA against Type-1 adversary in the random oracle model if the DBDH assumption holds.
Proof.
Suppose that . Given a DBDH instance . Denoted by that , and by that Z is random. In the following, we construct a simulator that runs as a subroutine to correctly guess the value of .
- 1.
- Setup: sets , implying that , in which is unknown to . Then sends to .
- 2.
- Phase 1: Same as Phase 1 in the proof of Theorem 1.
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither nor has been submitted to ; (3) Neither (, , ) nor (, , ) has been submitted to . If , aborts and randomly returns . Otherwise, randomly selects and sends to , in which
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins, and returns . Otherwise, loses, and returns .
If , perfectly simulates Section 3.3.3, and ’s probability of winning is . Otherwise, is independent of , and ’s probability of winning is . aborts and randomly returns if its guess of the identities selected by for challenge is wrong. Denote ’s abortion with , we have
’s advantage in solving the DBDH problem is
is negligible due to the intractability of the DDH problem. This completes the proof. □
5.4. S-TD-IND-CKA against Type-2 Adversary
Theorem 4.
Our scheme satisfies S-TD-IND-CKA against Type-2 adversary in the random oracle model if the DDH assumption in holds.
Proof.
Suppose that . Given a DDH instance . Denoted by that , and by that Z is random. In the following, we construct a simulator that runs as a subroutine to correctly guess the value of .
- 1.
- Setup: sends and to .
- 2.
- Phase 1: Same as Phase 1 in the proof of Theorem 2.
- 3.
- Challenge: selects , , and two keywords (, ) for the challenge, with the following restrictions: (1) Neither nor has been submitted to ; (2) Neither (, , ) nor (, , ) has been submitted to . If , aborts and randomly returns . Otherwise, randomly selects and sends to , in which
- 4.
- Phase 2: is allowed to access the oracles as in Phase 1, with the following restrictions:
- Neither nor can be submitted to .
- Neither (, , ) nor (, , ) can be submitted to .
- 5.
- Guess: submits . If , wins, and returns . If , loses, and returns .
If , perfectly simulates Section 3.3.4, and ’s probability of winning is . Otherwise, is independent of , and ’s probability of winning is . aborts and randomly returns if its guess of the identities selected by for challenge is wrong. Denote ’s abortion with , we have
’s advantage in solving the DDH problem in is
is negligible due to the intractability of the DDH problem in . This completes the proof. □
6. Performance Evaluation and Discussion
We compare our scheme with two related schemes [23,24]. The comparison includes storage overhead, computation overhead, and security. For simplicity, we only consider the following time-consuming operations:
- E: An exponentiation operation in .
- : An exponentiation operation in .
- : An exponentiation operation in .
- P: A bilinear pairing operation.
- H: A Hash-To-Point operation.
The comparison of storage overhead, computation overhead, and security is shown in Table 2, Table 3 and Table 4, respectively. Our scheme has higher storage and computation overhead. However, our scheme achieves stronger security. Besides, in practice, users may not need to encrypt all files but only a small part of files that contain sensitive information. Therefore, we consider that the storage and computation overhead paid for stronger security is affordable.

Table 2.
Storage overhead comparison.

Table 3.
Computation overhead comparison.

Table 4.
Security comparison.
7. Conclusions and Future Works
In this paper, we proposed an improved security model, in which a stronger version of trapdoor indistinguishability is defined. Then we proposed a new CLPAEKS scheme, which differs from the existing CLPAEKS schemes mainly in that the trapdoor is generated using two random elements in . As far as we know, this is the first CLPAEKS scheme with provable security under the improved security model.
In the future, we will try to extend our scheme to make it support multi-receiver settings in order to cope with the scenario of group chat. Besides, considering that a file may contain multiple keywords, it would be valuable to extend our scheme to make it support multi-keyword settings. Furthermore, as quantum computing is emerging, traditional intractable problems, e.g., discrete logarithm problems, could be solved with a powerful quantum computer. Some quantum-safe cryptographic primitives were proposed (e.g., lattice-based cryptography, code-based cryptography, multivariate-based cryptography, and hash-based cryptography). Among the mentioned candidates, lattice-based cryptography is an attractive choice because it offers provable security and a good trade-off between efficiency and security [26,27,28]. Therefore, it is advisable to design a lattice-based CLPAEKS scheme to resist quantum computing attacks.
Author Contributions
Conceptualization, J.L., H.L., J.H. and Q.H.; methodology, J.L., H.L. and J.H.; writing—original draft preparation, J.L.; writing—review and editing, Q.H., S.M. and M.H.A.A.; supervision, Q.H., S.M. and M.H.A.A.; project administration, Q.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by National Natural Science Foundation of China (No. 62272174, 61872152), Major Program of Guangdong Basic and Applied Research (No. 2019B030302008), Science and Technology Program of Guangzhou (No. 201902010081).
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| PEKS | Public key encryption with keyword search |
| CLPAEKS | Certificateless public key authenticated encryption with keyword search |
| KGA | Keyword guessing attacks |
| DDH | Decisional Diffie–Hellman (assumption) |
| DBDH | Decisional Bilinear Diffie–Hellman (assumption) |
| GBDH | Gap Bilinear Diffie–Hellman (assumption) |
| CDH | Computational Diffie–Hellman (assumption) |
| GDH | Gap Diffie–Hellman (assumption) |
| IBEKS | Identity-based encryption with keyword search |
| PPT | Probabilistic polynomial time |
| KGC | Key generation center |
| CT-IND-CKA | Ciphertext indistinguishability under adaptive chosen-keyword attacks |
| S-TD-IND-CKA | Strong trapdoor indistinguishability under adaptive chosen-keyword attacks |
| ROM | Random oracle model |
References
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public Key Encryption with Keyword Search. In Proceedings of the Advances in Cryptology—EUROCRYPT 2004, International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 506–522. [Google Scholar]
- Byun, J.W.; Rhee, H.S.; Park, H.; Lee, D.H. Off-Line Keyword Guessing Attacks on Recent Keyword Search Schemes over Encrypted Data. In Proceedings of the Secure Data Management, Third VLDB Workshop, Seoul, Korea, 10–11 September 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 75–83. [Google Scholar]
- Yau, W.; Heng, S.; Goi, B. Off-Line Keyword Guessing Attacks on Recent Public Key Encryption with Keyword Search Schemes. In Proceedings of the Autonomic and Trusted Computing, 5th International Conference, Oslo, Norway, 23–25 June 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 100–105. [Google Scholar]
- Rhee, H.S.; Park, J.H.; Susilo, W.; Lee, D.H. Trapdoor security in a searchable public-key encryption scheme with a designated tester. J. Syst. Softw. 2010, 83, 763–771. [Google Scholar] [CrossRef]
- Song, D.X.; Wagner, D.A.; Perrig, A. Practical Techniques for Searches on Encrypted Data. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; IEEE Computer Society: Washington, DC, USA; Los Alamitos, CA, USA, 2000; pp. 44–55. [Google Scholar]
- Rhee, H.S.; Park, J.H.; Lee, D.H. Generic construction of designated tester public-key encryption with keyword search. Inf. Sci. 2012, 205, 93–109. [Google Scholar] [CrossRef]
- Fang, L.; Susilo, W.; Ge, C.; Wang, J. Public key encryption with keyword search secure against keyword guessing attacks without random oracle. Inf. Sci. 2013, 238, 221–241. [Google Scholar] [CrossRef]
- Wang, C.h.; Tu, T.y. Keyword search encryption scheme resistant against keyword-guessing attack by the untrusted server. J. Shanghai Jiaotong Univ. Sci. 2014, 19, 440–442. [Google Scholar] [CrossRef]
- Huang, Q.; Li, H. An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks. Inf. Sci. 2017, 403, 1–14. [Google Scholar] [CrossRef]
- Zheng, Y. Digital Signcryption or How to Achieve Cost(Signature & Encryption) << Cost(Signature) + Cost(Encryption). In Proceedings of the Advances in Cryptology—CRYPTO 1997, 17th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Noroozi, M.; Eslami, Z. Public key authenticated encryption with keyword search: Revisited. IET Inf. Secur. 2019, 13, 336–342. [Google Scholar] [CrossRef]
- Qin, B.; Chen, Y.; Huang, Q.; Liu, X.; Zheng, D. Public-key authenticated encryption with keyword search revisited: Security model and constructions. Inf. Sci. 2020, 516, 515–528. [Google Scholar] [CrossRef]
- Pan, X.; Li, F. Public-key authenticated encryption with keyword search achieving both multi-ciphertext and multi-trapdoor indistinguishability. J. Syst. Archit. 2021, 115, 102075. [Google Scholar] [CrossRef]
- Cheng, L.; Meng, F. Security analysis of Pan et al.’s “Public-key authenticated encryption with keyword search achieving both multi-ciphertext and multi-trapdoor indistinguishability”. J. Syst. Archit. 2021, 119, 102248. [Google Scholar] [CrossRef]
- Abdalla, M.; Bellare, M.; Catalano, D.; Kiltz, E.; Kohno, T.; Lange, T.; Malone-Lee, J.; Neven, G.; Paillier, P.; Shi, H. Searchable Encryption Revisited: Consistency Properties, Relation to Anonymous IBE, and Extensions. In Proceedings of the Advances in Cryptology—CRYPTO 2005, 25th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 205–222. [Google Scholar]
- Boneh, D.; Franklin, M.K. Identity-Based Encryption from the Weil Pairing. In Proceedings of the Advances in Cryptology—CRYPTO 2001, 21st Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 213–229. [Google Scholar]
- Li, H.; Huang, Q.; Shen, J.; Yang, G.; Susilo, W. Designated-server identity-based authenticated encryption with keyword search for encrypted emails. Inf. Sci. 2019, 481, 330–343. [Google Scholar] [CrossRef]
- Yanguo, P.; Jiangtao, C.; Changgen, P.; Zuobin, Y. Certificateless public key encryption with keyword search. China Commun. 2014, 11, 100–113. [Google Scholar] [CrossRef]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography. In Proceedings of the Advances in Cryptology—ASIACRYPT 2003, 9th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- He, D.; Ma, M.; Zeadally, S.; Kumar, N.; Liang, K. Certificateless Public Key Authenticated Encryption With Keyword Search for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3618–3627. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Ma, M.; Kumar, N.; He, D. Certificateless searchable public key authenticated encryption with designated tester for cloud-assisted medical Internet of Things. Ann. Telecommun. 2019, 74, 423–434. [Google Scholar] [CrossRef]
- Liu, X.; Li, H.; Yang, G.; Susilo, W.; Tonien, J.; Huang, Q. Towards Enhanced Security for Certificateless Public-Key Authenticated Encryption with Keyword Search. In Proceedings of the Provable Security—13th International Conference, Cairns, Australia, 1–4 October 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 113–129. [Google Scholar]
- Pakniat, N.; Shiraly, D.; Eslami, Z. Certificateless authenticated encryption with keyword search: Enhanced security model and a concrete construction for industrial IoT. J. Inf. Secur. Appl. 2020, 53, 102525. [Google Scholar] [CrossRef]
- Shiraly, D.; Pakniat, N.; Noroozi, M.; Eslami, Z. Pairing-free certificateless authenticated encryption with keyword search. J. Syst. Archit. 2022, 124, 102390. [Google Scholar] [CrossRef]
- Icart, T. How to Hash into Elliptic Curves. In Proceedings of the Advances in Cryptology—CRYPTO 2009, 29th Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 303–316. [Google Scholar]
- Ni, Z.; Kundi, D.; O’Neill, M.; Liu, W. A High-Performance SIKE Hardware Accelerator. IEEE Trans. Very Large Scale Integr. Syst. 2022, 30, 803–815. [Google Scholar] [CrossRef]
- Bisheh-Niasar, M.; Azarderakhsh, R.; Kermani, M.M. High-Speed NTT-based Polynomial Multiplication Accelerator for CRYSTALS-Kyber Post-Quantum Cryptography. IACR Cryptol. EPrint Arch. 2021, 2021, 563. [Google Scholar]
- Tian, J.; Wu, B.; Wang, Z. High-Speed FPGA Implementation of SIKE Based on an Ultra-Low-Latency Modular Multiplier. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 68, 3719–3731. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).